Data processing method and device, electronic equipment and computer readable storage medium
A technology of data processing and electronic equipment, which is applied in the field of computers, can solve problems such as data leakage and easy cracking of keys, and achieve the effect of increasing randomness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
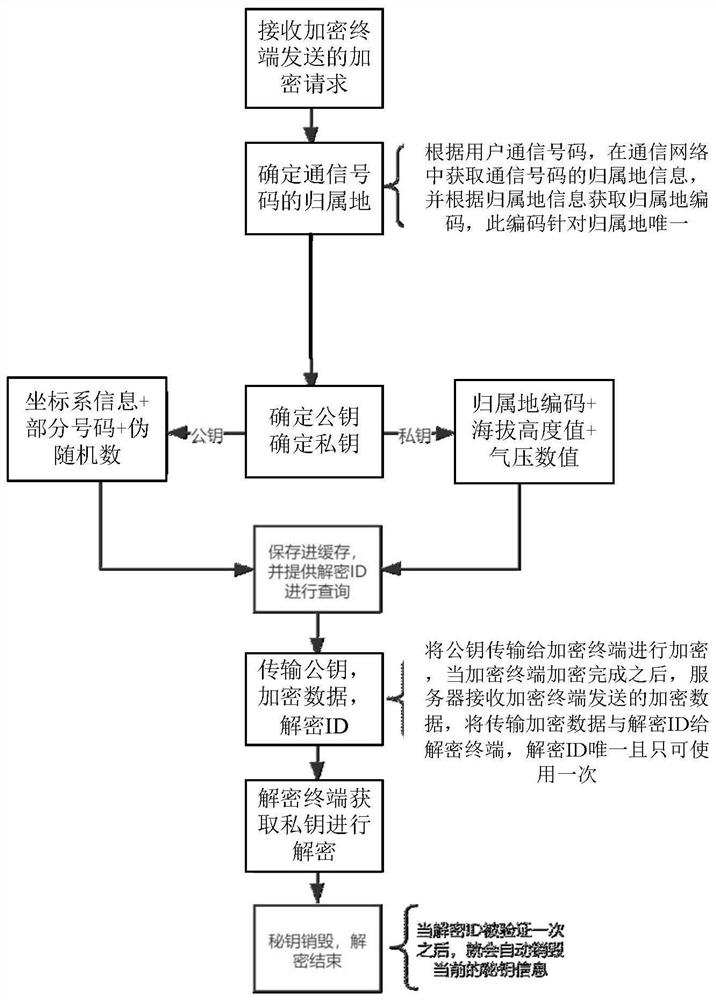
[0023] According to an embodiment of the present invention, an embodiment of a data processing method is provided. It should be noted that the steps shown in the flowcharts of the accompanying drawings can be executed in a computer system such as a set of computer-executable instructions, and, although A logical order is shown in the flowcharts, but in some cases the steps shown or described may be performed in an order different from that shown or described herein.
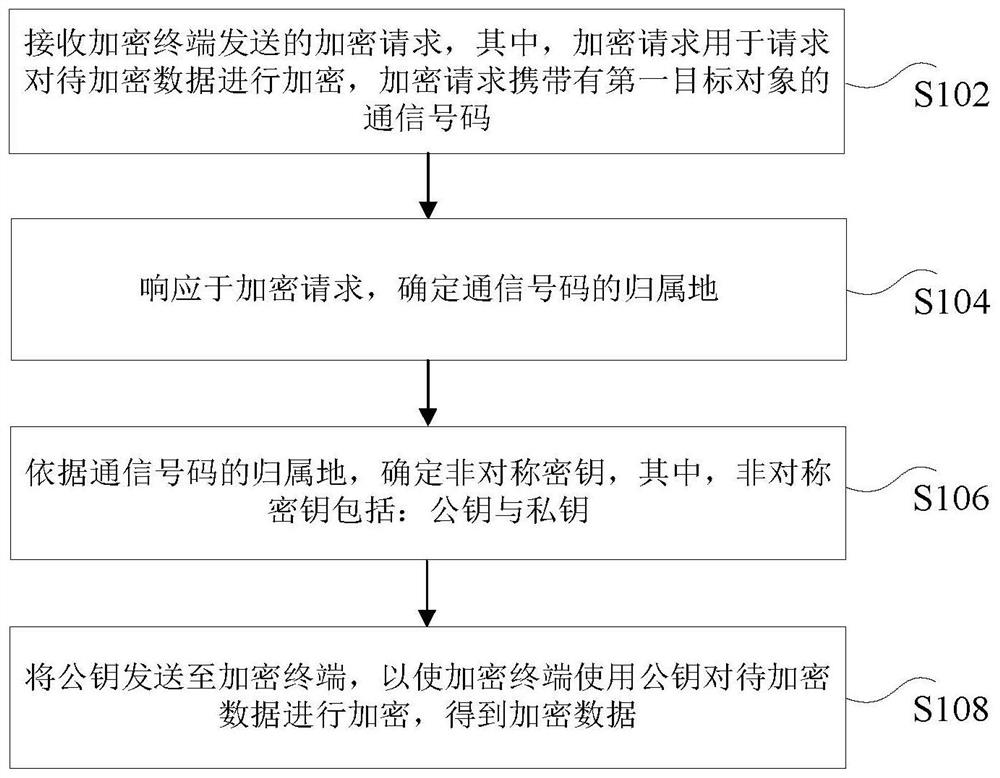
[0024] figure 1 is a flowchart of a data processing method according to an embodiment of the present invention, such as figure 1 As shown, the method includes the following steps:
[0025] Step S102, receiving an encryption request sent by the encryption terminal, wherein the encryption request is used to request encryption of the data to be encrypted, and the encryption request carries the communication number of the first target object;
[0026] Step S104, in response to the encryption request, determine the ...
Embodiment 2
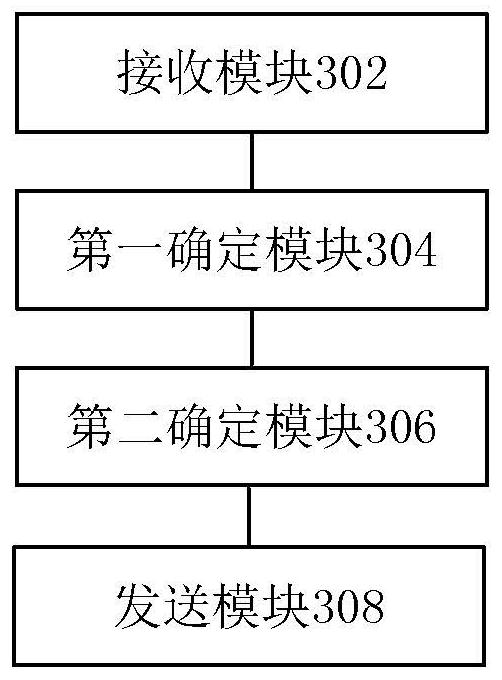
[0066] According to an embodiment of the present invention, a device for implementing the above data processing method is also provided, image 3 is a structural block diagram of a data processing device according to an embodiment of the present invention, such as image 3 As shown, the device includes: a receiving module 302, a first determining module 304, a second determining module 306 and a sending module 308, and the device will be described in detail below.
[0067] The receiving module 302 is used to receive the encryption request sent by the encryption terminal, wherein the encryption request is used to request to encrypt the data to be encrypted, and the encryption request carries the communication number of the first target object; the first determination module 304 is connected to the above receiving module 302, used to determine the attribution of the communication number in response to the encryption request; the second determination module 306, connected to the ...
Embodiment 3
[0070]According to another aspect of the embodiments of the present invention, there is also provided an electronic device, including: a processor; a memory for storing processor-executable instructions, wherein the processor is configured to execute instructions to achieve any of the above data processing method.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com