Method, apparatus and device for network attack behaviors prediction, and storage medium
A network attack and behavior technology, applied in the field of network security, can solve the problems of inability to effectively ensure the security of network equipment, low identification efficiency, and inability to predict network attack behaviors, so as to avoid network attack behaviors, ensure security, and improve analysis and performance. The effect of recognition efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
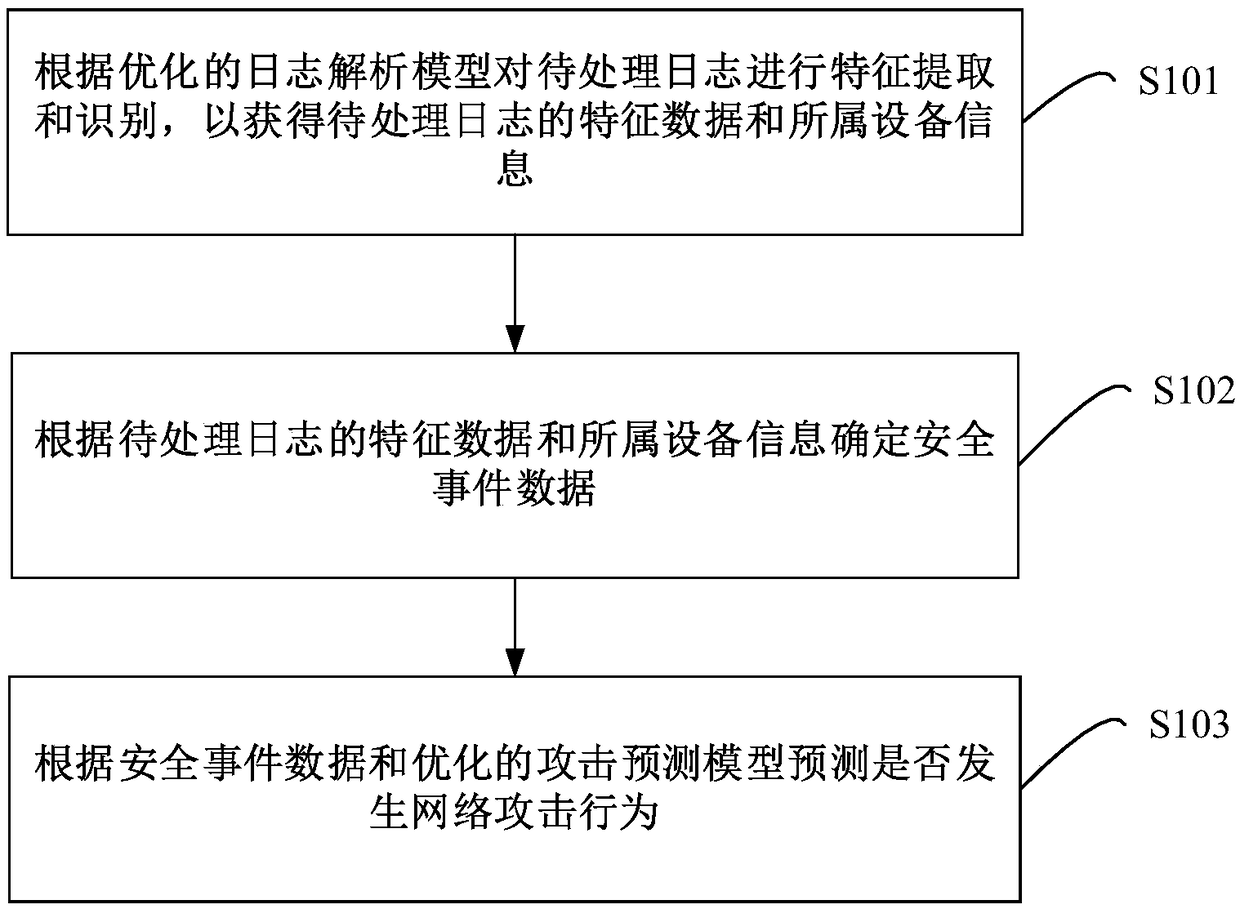
[0030] figure 1 It is a flowchart of a method for network attack behavior prediction provided by Embodiment 1 of the present invention. The embodiment of the present invention aims at the network attack behavior recognition method in the existing technology, because the selection of the regular expression is performed before each recognition, so the recognition efficiency is low, and the network attack behavior cannot be predicted. The problem that the security of network equipment cannot be guaranteed effectively provides a method for predicting network attack behavior.
[0031] Such as figure 1 As shown, the specific steps of the method are as follows:
[0032] Step S101 , perform feature extraction and identification on the log to be processed according to the log parsing model, so as to obtain feature data and equipment information of the log to be processed.
[0033] In this embodiment, when it is necessary to detect the security of the network device, the log of the n...
Embodiment approach
[0049] A feasible implementation manner is: the aggregation condition is the generation time of the log, and among the pending logs whose generation time is within a preset time range, duplicate logs with the same characteristic data and device information are merged into one piece of data. Wherein, the preset time range may be set by technicians according to actual needs, which is not specifically limited in this embodiment. For example, the preset time range may be the latest 5 minutes.
[0050] Another feasible implementation mode is: the aggregation condition is the number of aggregation entries, and among the logs to be processed, the duplicate logs with the same characteristic data and the information of their devices that do not exceed the number of aggregation entries are merged into one piece of data. Wherein, the number of aggregated items can be set by technicians according to actual needs, which is not specifically limited in this embodiment. For example, the numb...
Embodiment 2
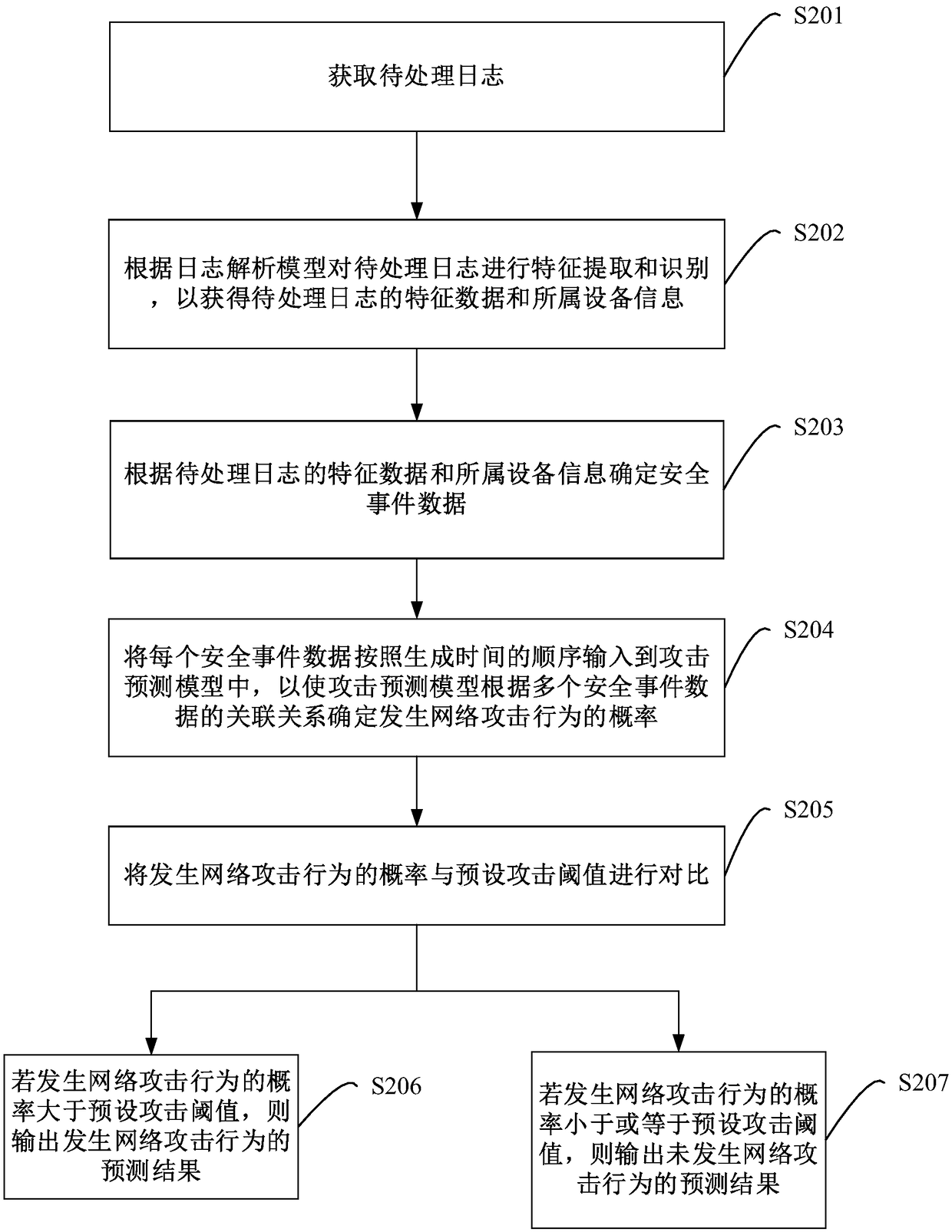
[0061] figure 2 It is a flow chart of a method for network attack behavior prediction provided by Embodiment 2 of the present invention. On the basis of the first embodiment above, in this embodiment, the characteristic data of the log to be processed includes the generation time, and predicts whether a network attack occurs according to the security event data and the attack prediction model, specifically including: The order of generation time is input into the attack prediction model, so that the attack prediction model can determine the probability of network attack behavior according to the correlation of multiple security event data; compare the probability of network attack behavior with the preset attack threshold; if it occurs If the probability of network attack behavior is greater than the preset attack threshold, the prediction result of network attack behavior will be output; if the probability of network attack behavior is less than or equal to the preset attack...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com