Man-machine identification method, device, server, client and storage medium
A human-machine identification and client-side technology, applied in the information field, can solve the problem of inability to accurately identify machine attacks, attacks, and deceive servers, etc., to achieve reliable user activity, prevent spike products, and prevent attacks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
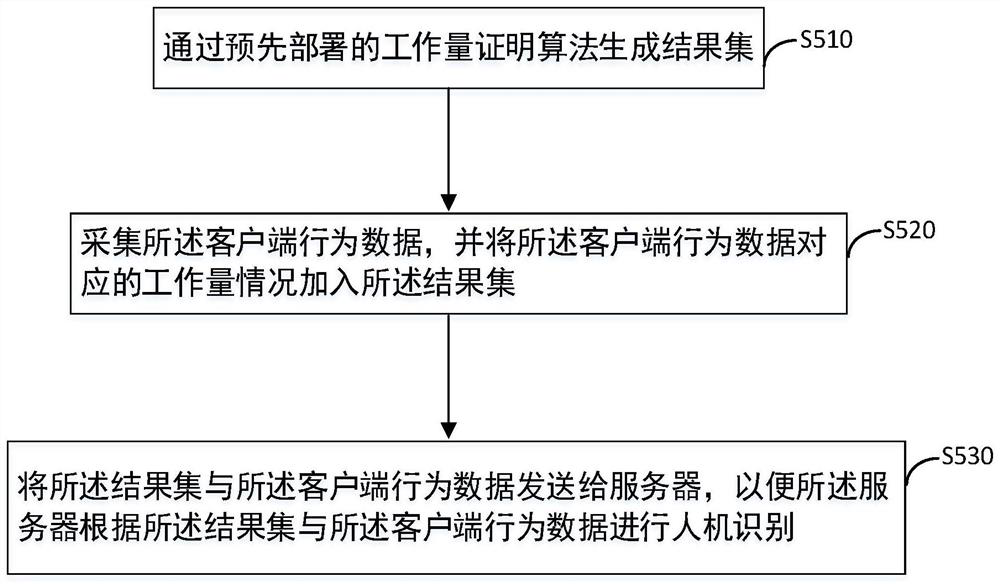
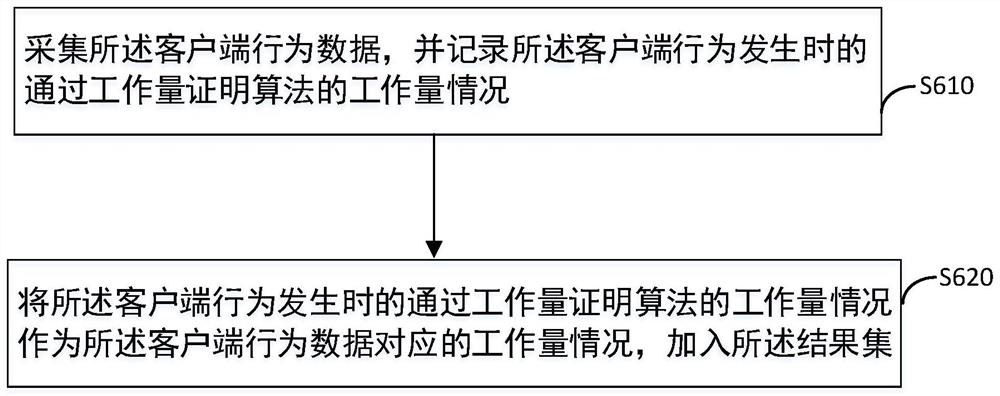
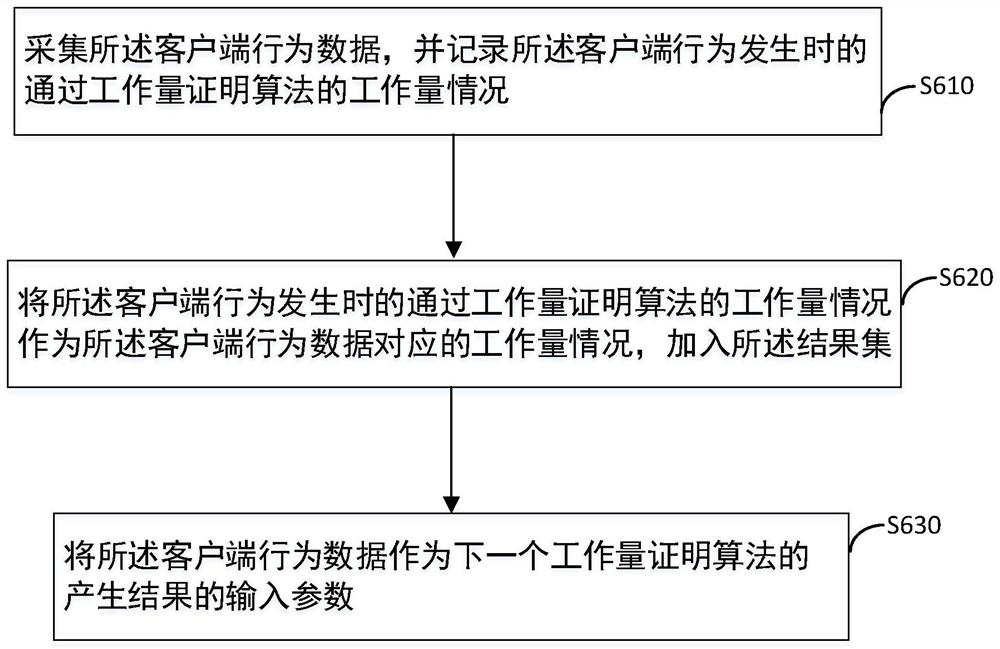
[0055] According to an embodiment of the method for identifying a human-machine based on a proof of work applied to a client in the present invention, the pre-deployed proof of work algorithm includes a proof of work algorithm that has undergone encryption and / or obfuscation.
[0056] The PoW algorithm of obfuscated encryption can be pre-deployed on the client. Due to PoW algorithm encryption, code obfuscation, and the limited computing power of a single device, attackers cannot use GPU (Graphic Processing Unit, Graphics Processing Unit) and other acceleration methods to simulate a large number of devices on a single device. Unlike a CPU, a GPU is a chip designed specifically to handle graphics tasks. The GPU contains more processing units than the CPU and has greater bandwidth, enabling it to exert greater performance in multimedia processing. In addition, in terms of hardware design, a CPU consists of a few cores optimized for sequential serial processing, while a GPU consist...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com