Method for preventing illegal transferring of interruption procedures of operating system
An operating system and process technology, which is applied in the field of computer science and malware protection to prevent attacks and ensure security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
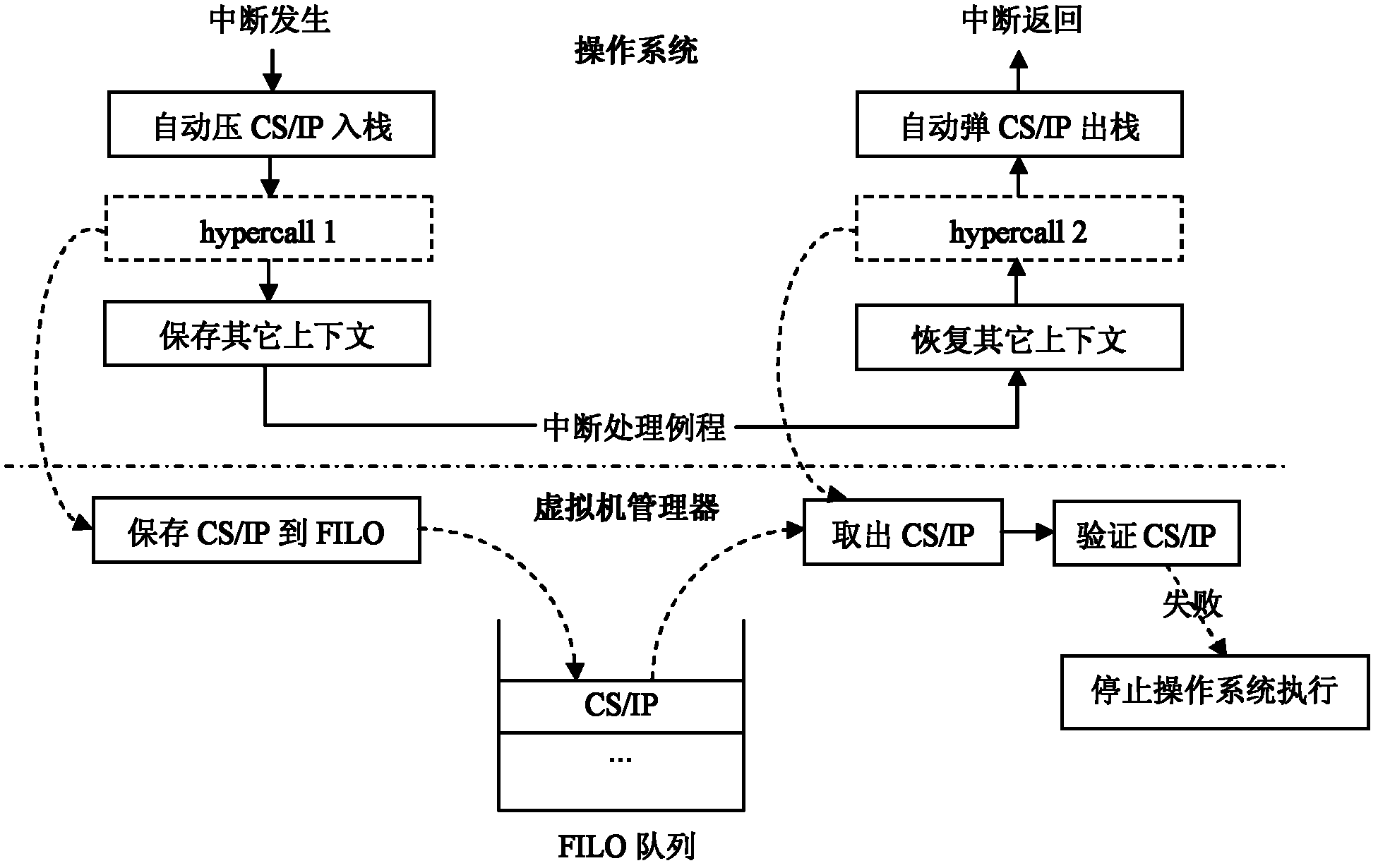
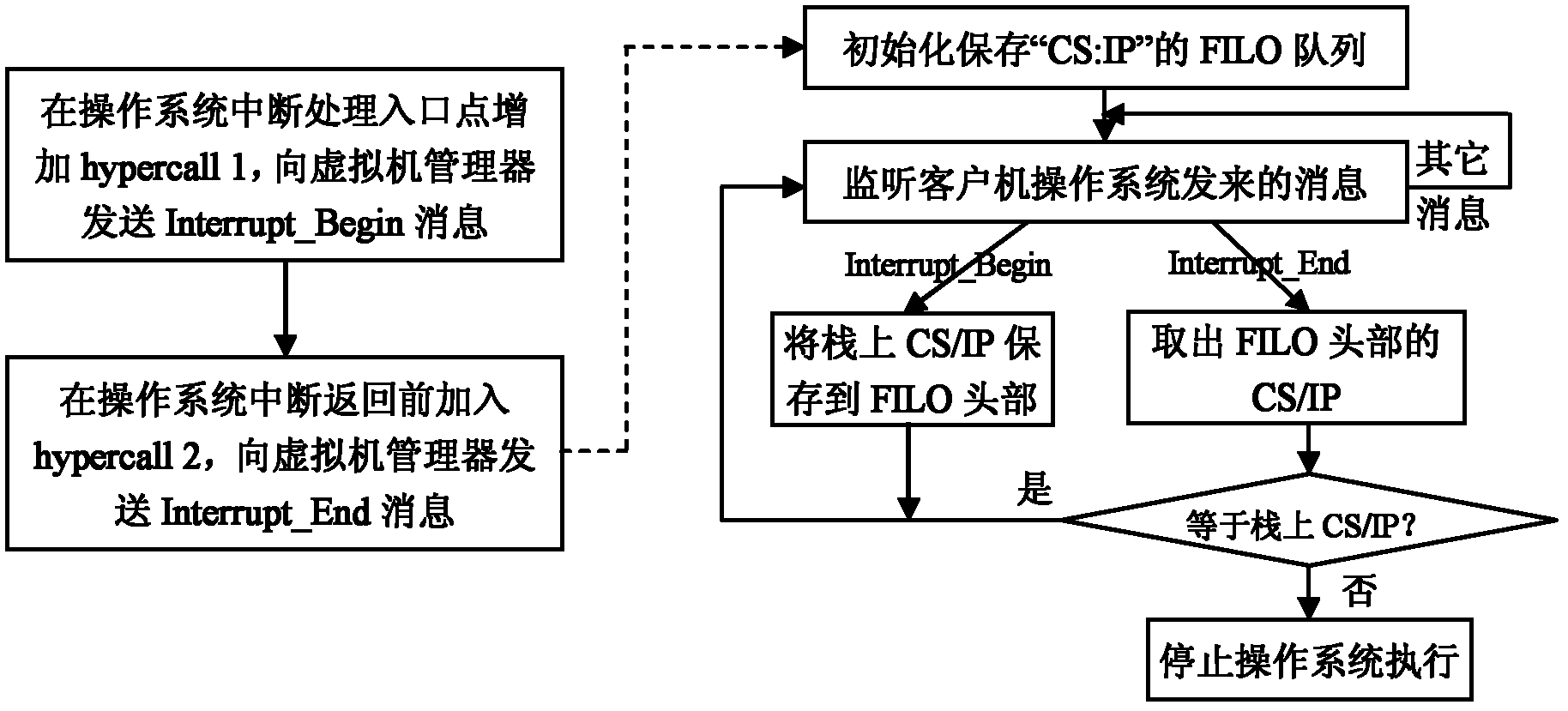
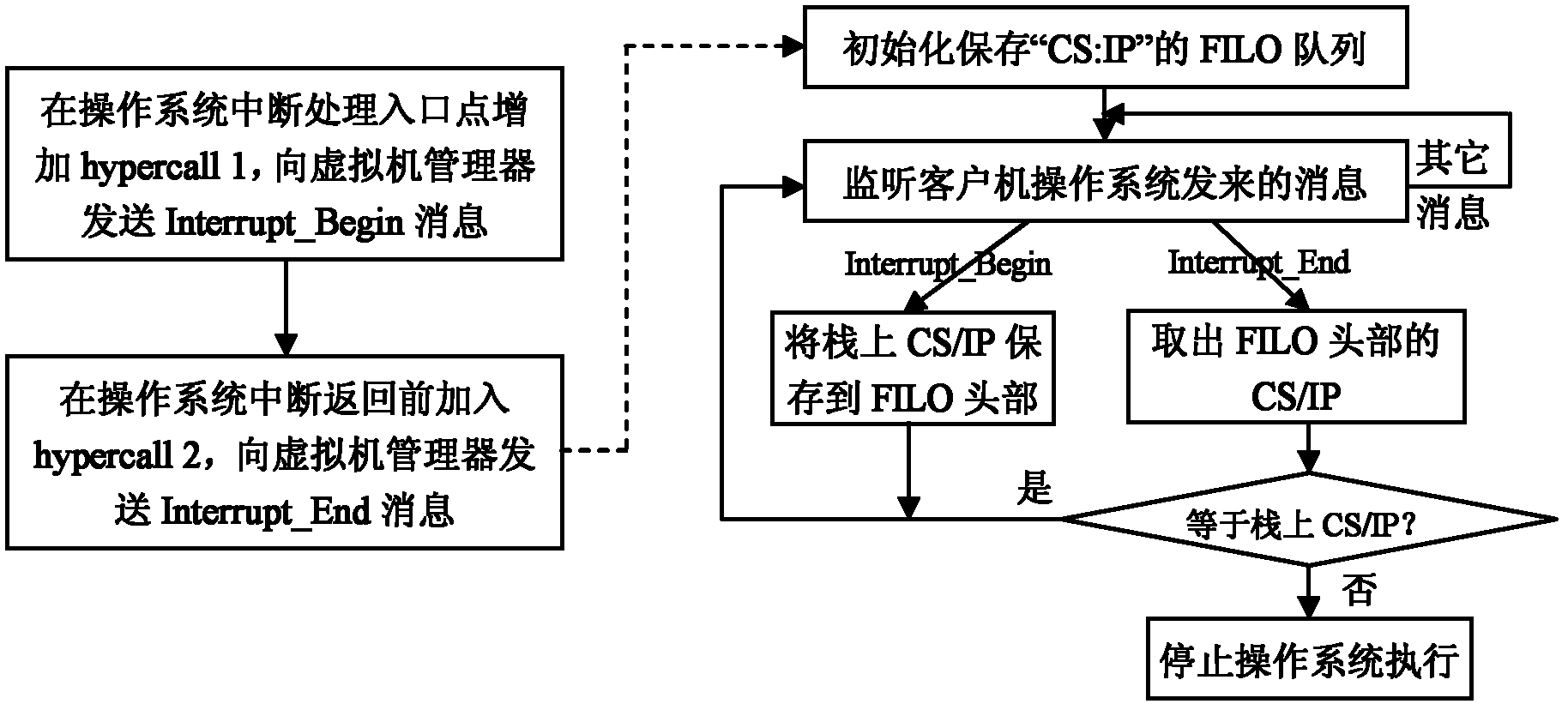
[0021] The principle of the present invention is as figure 1 shown. It is implemented based on virtual machine manager technology, and the operating system needs to be run on the virtual machine manager during specific implementation. A virtual machine manager, also known as a hypervisor, is a hardware virtualization technology that allows multiple clients to run on a computer host at the same time. The virtual machine manager is essentially a virtual layer introduced between the computer hardware and the operating system. It can provide an independent operating environment for each operating system, shield the dynamics, distribution, and heterogeneity of the hardware platform, and support hardware resources. sharing and multiplexing, and provide each client with an exclusive, independent and isolated operating environment. After the introduction of the virtual machine manager, the operating system no longer has the highest authority of the host, and all access to computer h...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com