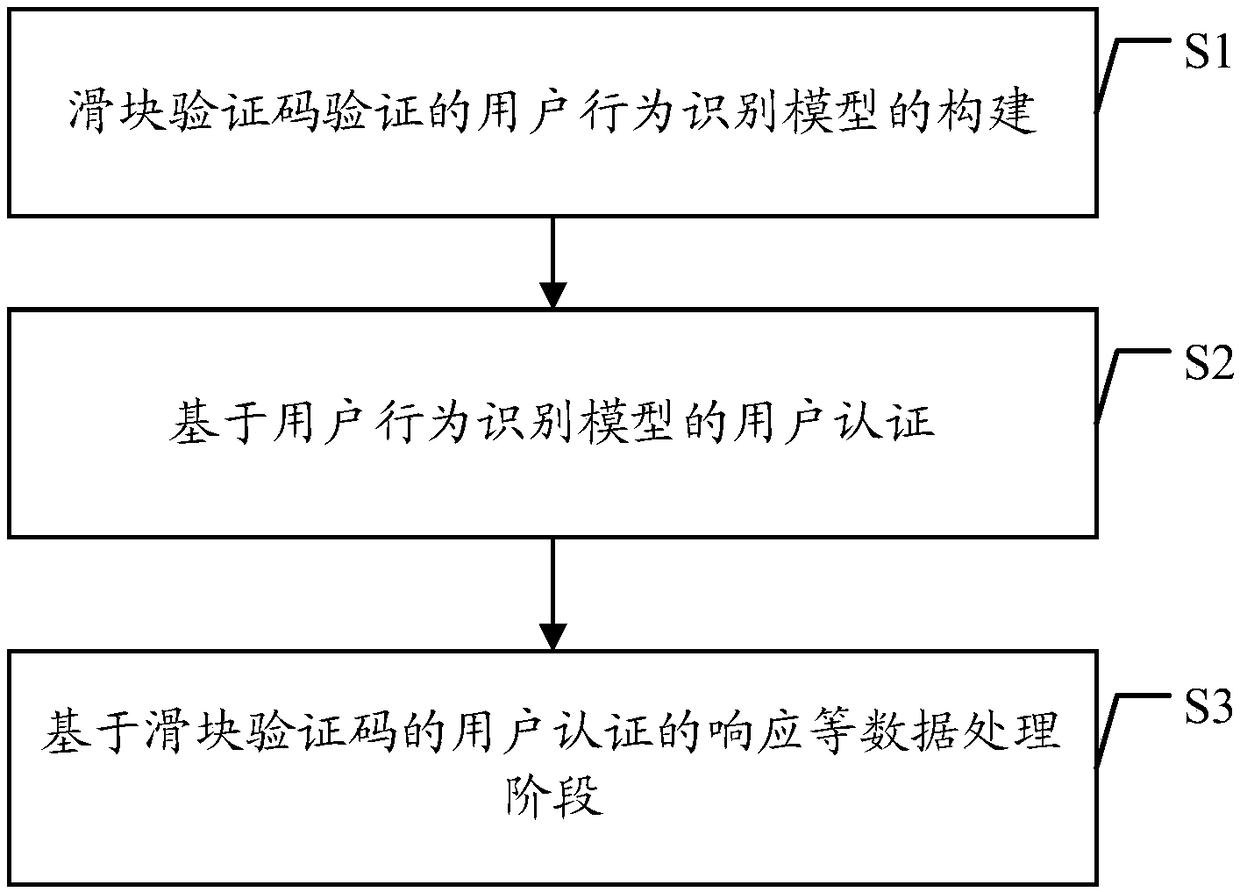
Patents
Literature
91results about How to "Improve authentication security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Method and system for authentication of a service request
InactiveUS6947727B1Improve authentication securityImprove securityUnauthorised/fraudulent call preventionEavesdropping prevention circuitsMemory circuitsDatabase
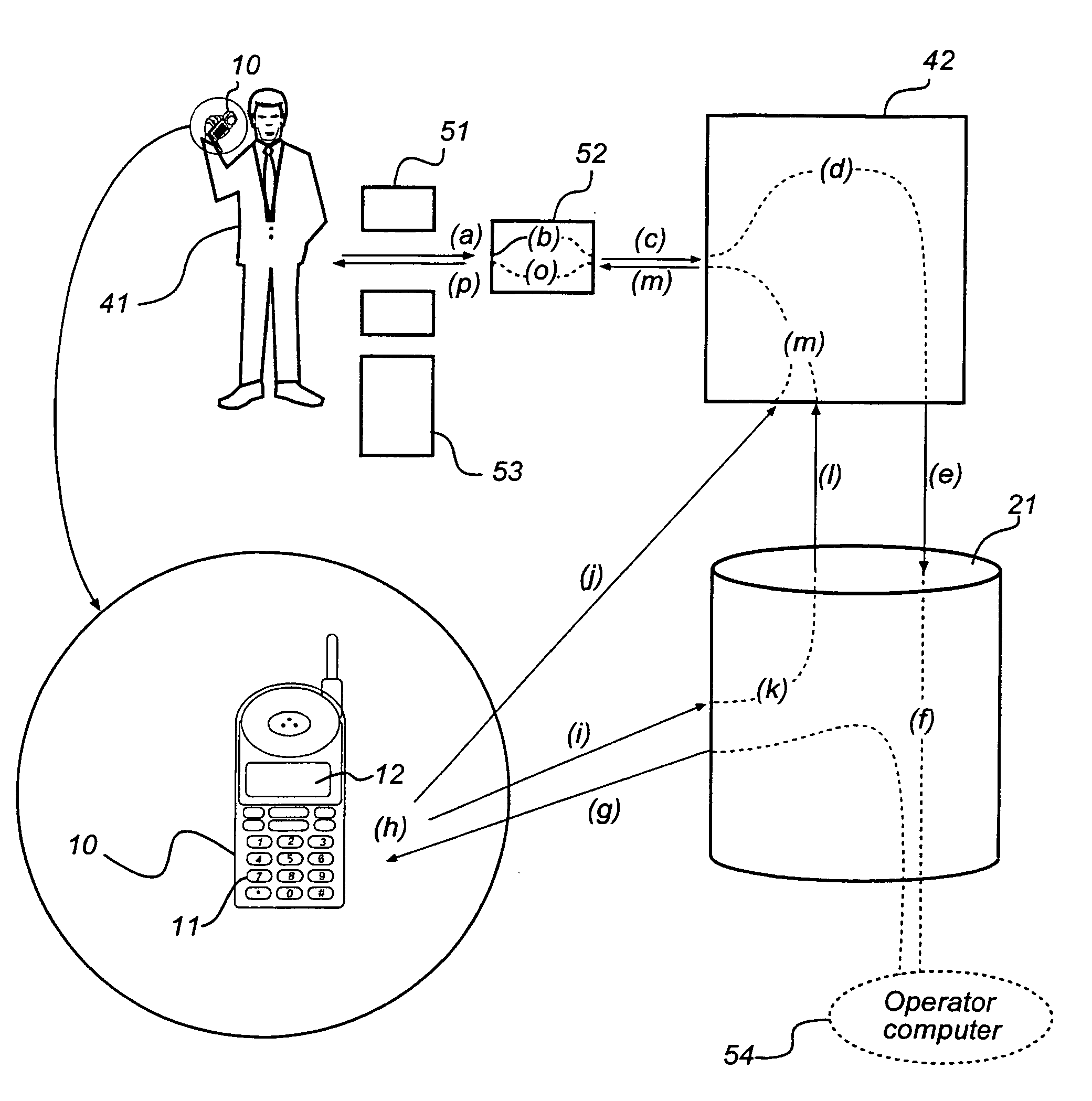
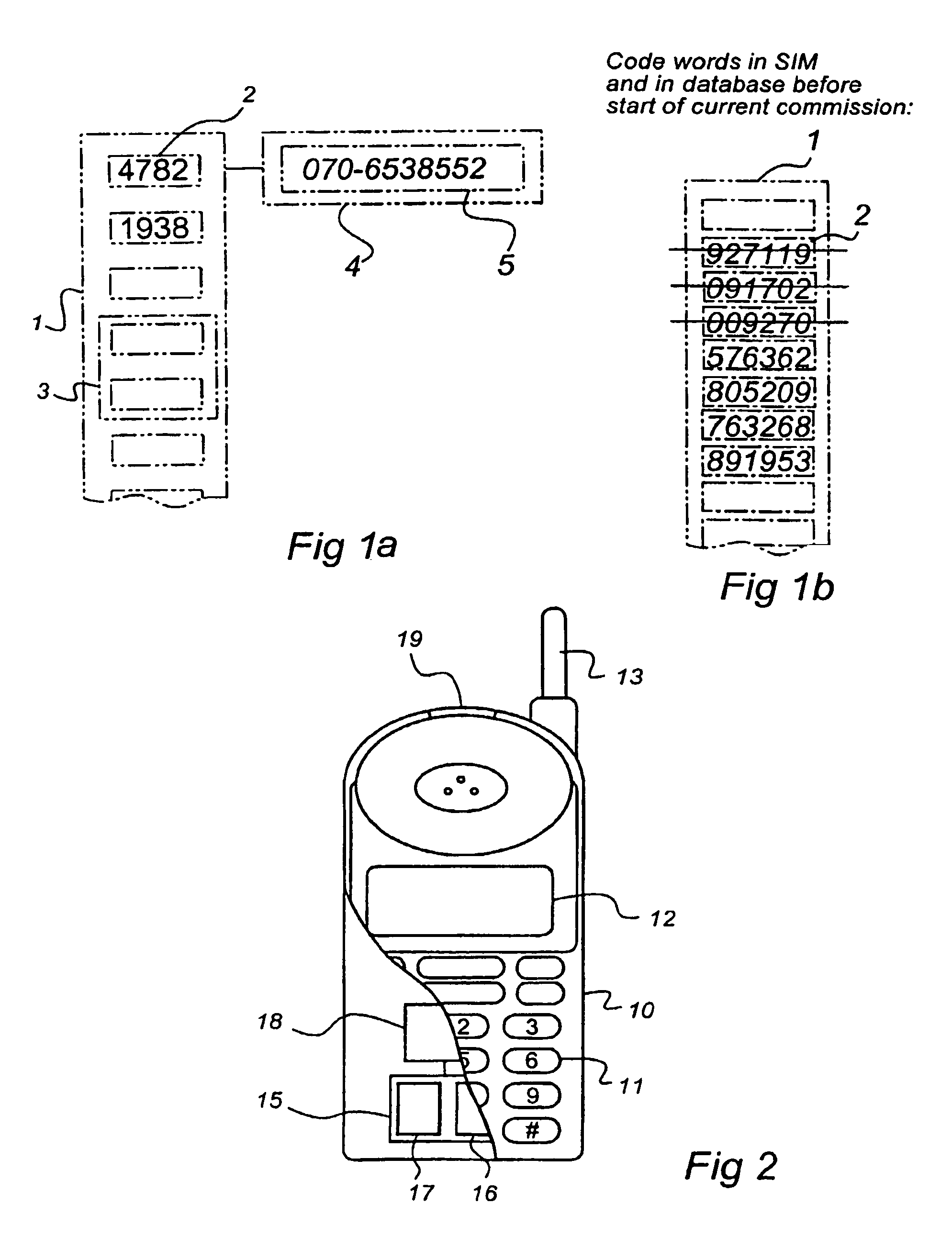
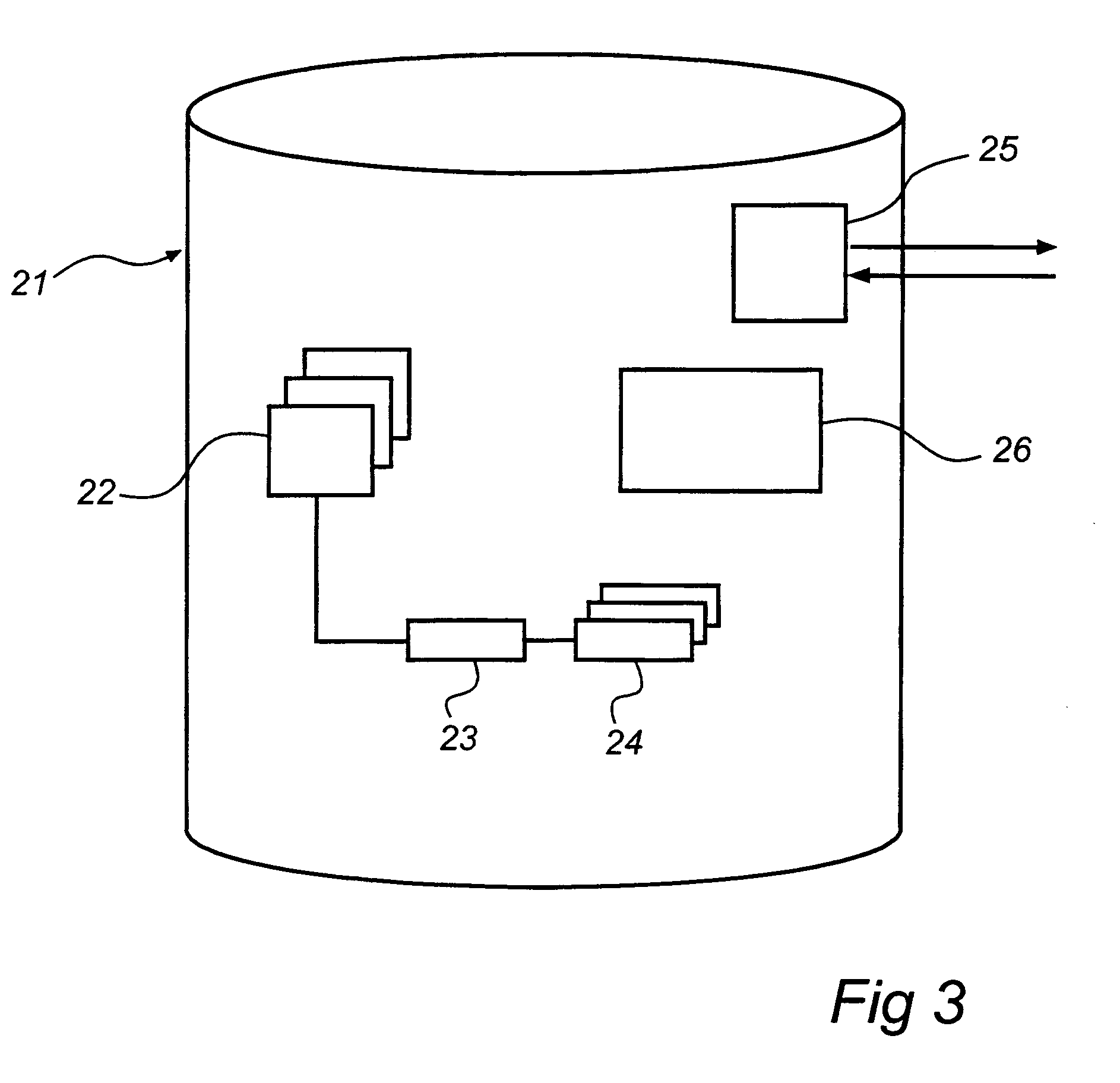
A method and a system is directed to authentication of a commission from a customer to a service provider. A set of randomly generated code words are stored in a memory circuit associated with a mobile-telephone subscription in a mobile telephone, as well as in a database together with an association to the mobile-telephone subscription. The method includes the steps of determining the identify of the customer, of identifying the mobile-telephone subscription on the basis of the identity of the customer, of retrieving a code word from the memory circuit, and of checking the presence of the code word in the code word set in the database that is associated with the mobile-telephone subscription, in order to thus authenticate the commission.
Owner:TRYGGIT
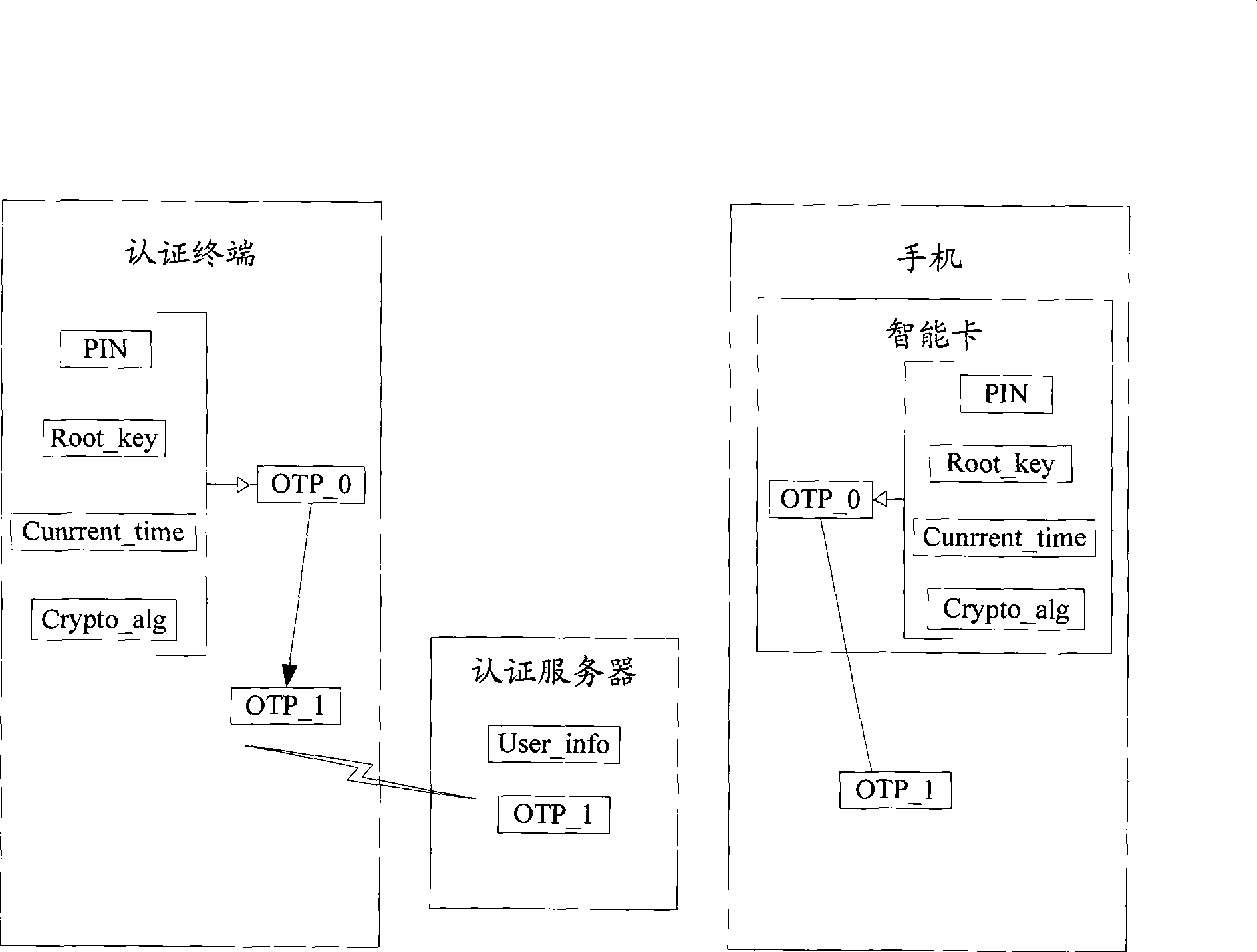
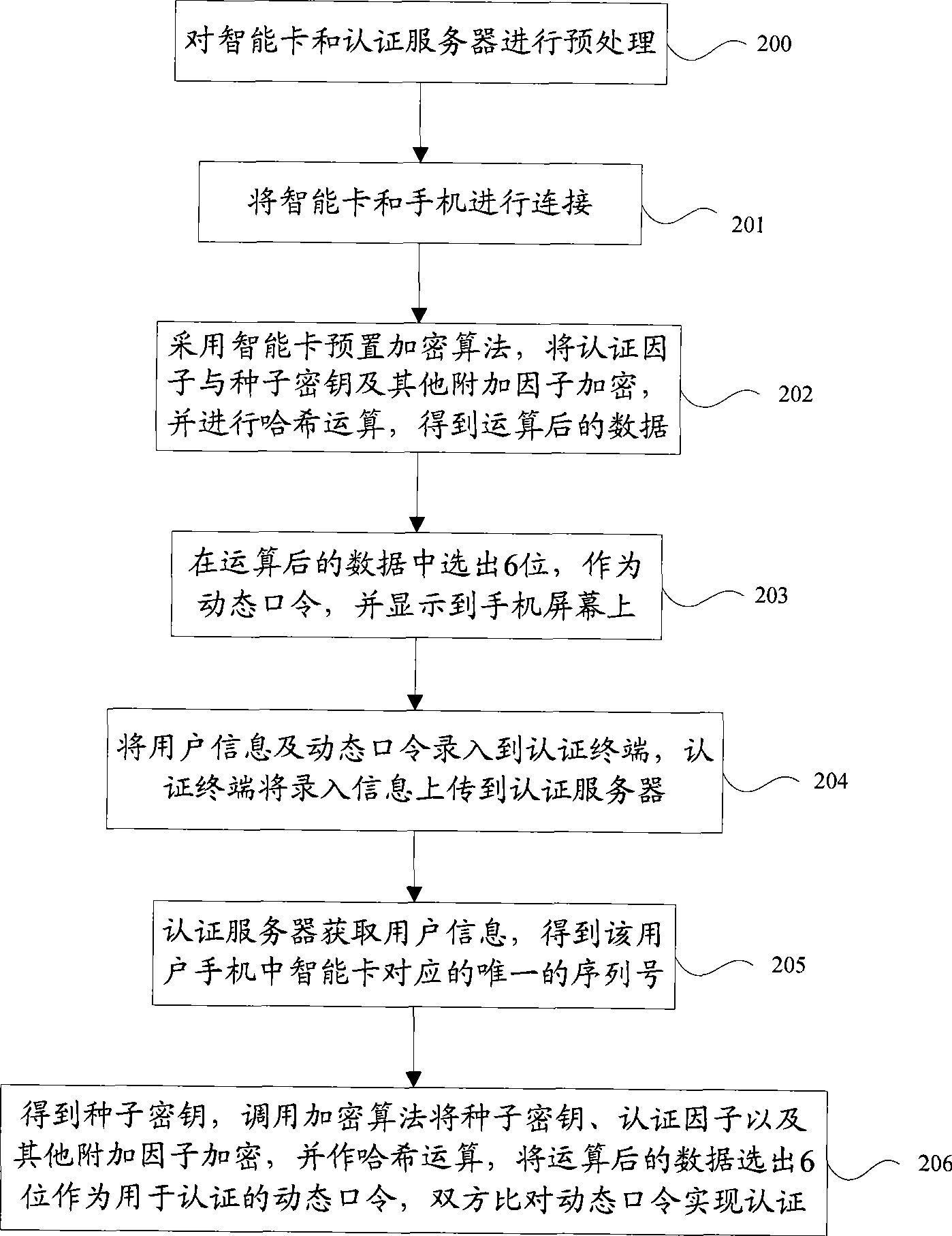
Method and system for implementing dynamic identity authentication
InactiveCN101500232ASolve the service lifeImprove authentication securityUser identity/authority verificationSecurity arrangementUser informationPassword
The invention discloses a system of realizing dynamic identification authentication, comprising an intelligent card, a cell phone, an authentication terminal and an authentication server. The invention further discloses a method for realizing the dynamic identification authentication, including the following steps: the intelligent card pre-stores a seed key and an algorithm; a dynamic password required by the authentication is generated by utilizing the algorithm, the seed key and an appointed authentication factor, and is sent to the cell phone which receives and displays the dynamic password; the user enters the dynamic password and user information into the authentication terminal and uploads the dynamic password and user information to an authentication server; the authentication server obtains the seed key of the user from the authentication server according to the user information and carries out the calculation of the seed key and the appointed authentication factor with the prestored algorithm, thus also generating the dynamic password; and comparison of the dynamic passwords at two terminals is carried out, thereby completing the authentication. The invention overcomes the existing defect that the identification authentication of the user is required, and the user additionally carries a dynamic password card and other identification authentication products, simultaneously, the problem about the service life of the password card is solved.
Owner:BEIJING HUADA ZHIBAO ELECTRONICS SYST
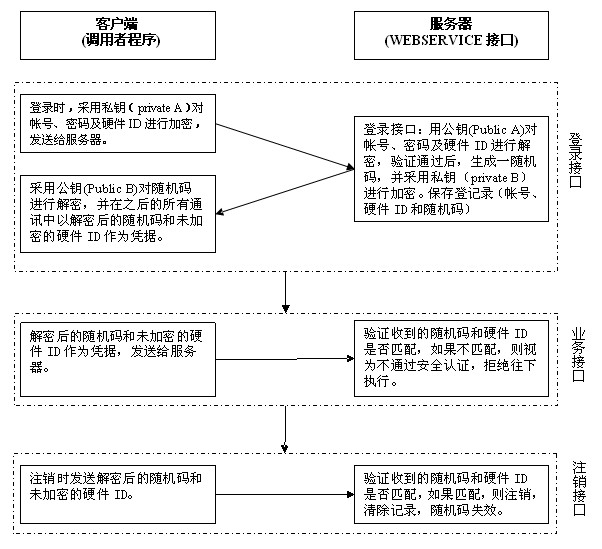
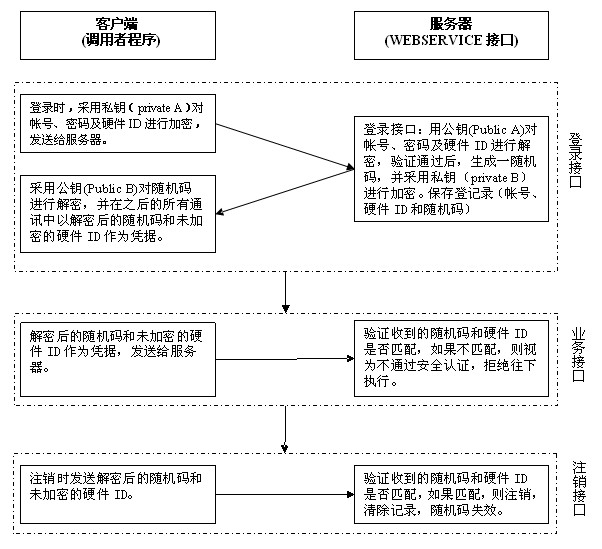
Security authentication method for WEB service
ActiveCN102006306AImprove authentication securityImprove securityUser identity/authority verificationPasswordWeb service
The invention belongs to the technical field of software security authentication, and particularly relates to a security authentication method for WEB service interface application. In the security authentication method for WEB service, the hardware comprises a server provided with WEB service interfaces and a client for calling the WEB service interfaces, wherein the WEB service interfaces comprise a login interface, a cancellation interface and a plurality of service interfaces. The method is characterized in that: a bidirectional asymmetrical encryption algorithm for encrypting account, password and hardware ID of the client is adopted between the client and the server, and the encrypted account, password and hardware ID are used as identity certificates in a random code mode; before calling the service interface, the client calls the login interface to acquire the identity certificates; and when the program exits, the client calls the cancellation interface to cancel the identity certificates. The method promotes the security of the WEB service interface, and has very positive significance for enterprise-level distributed application.
Owner:GOSUNCN TECH GRP
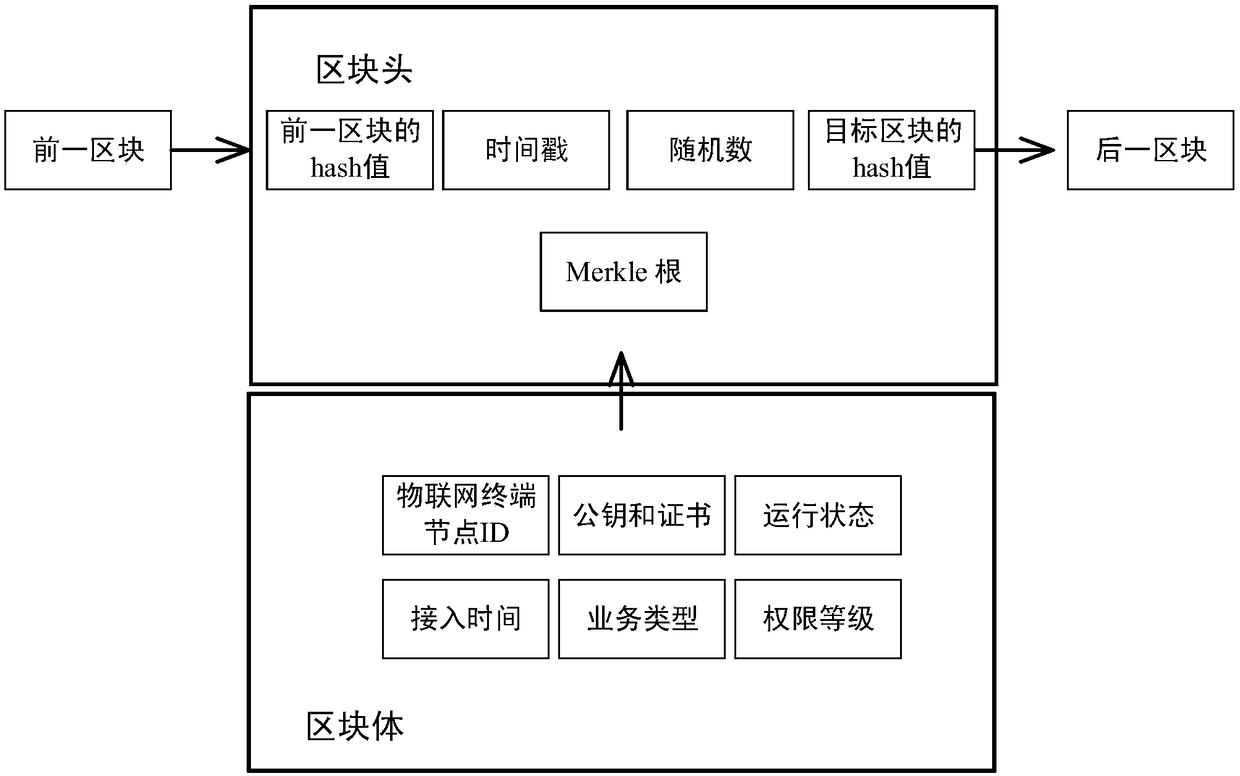
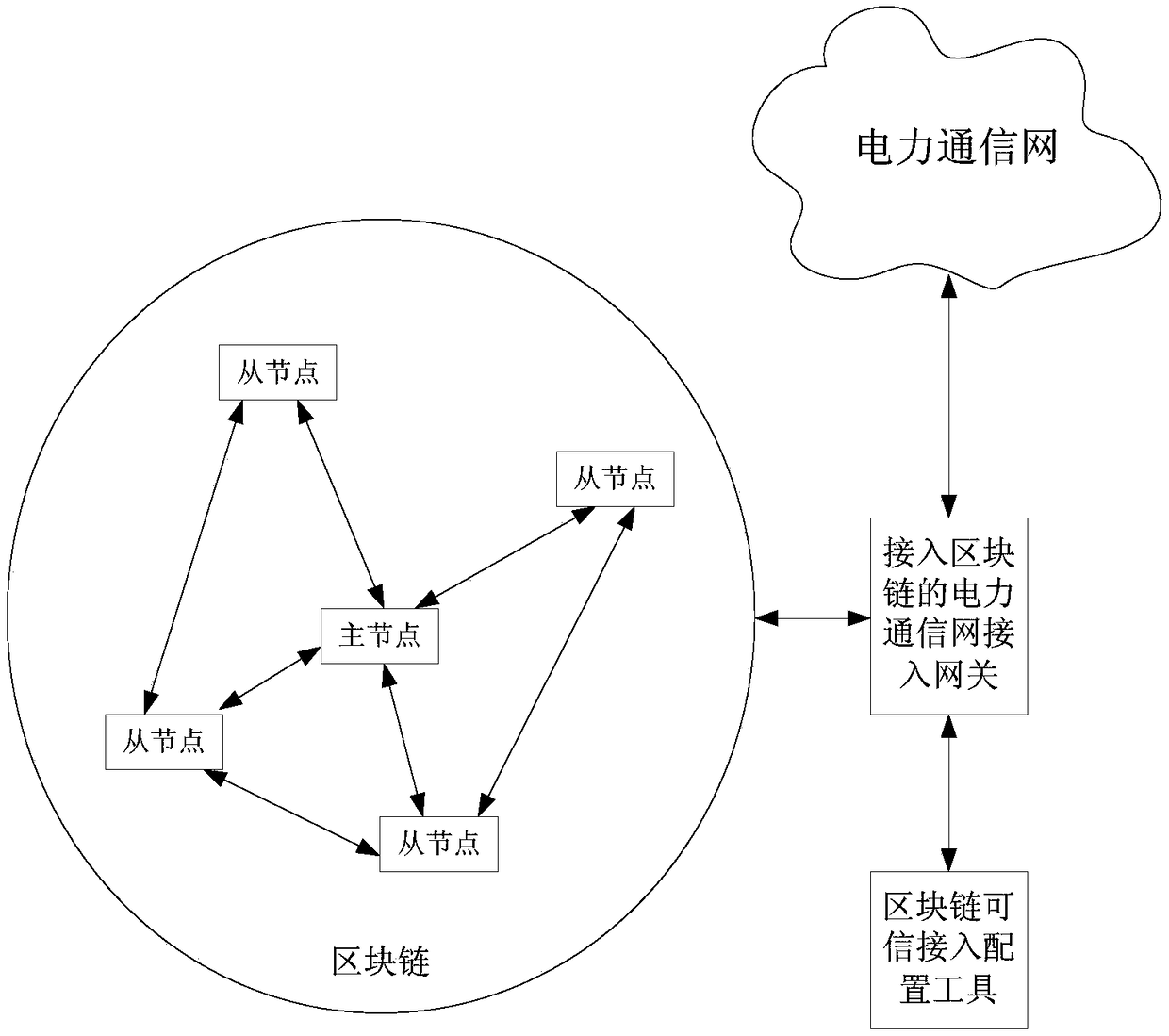
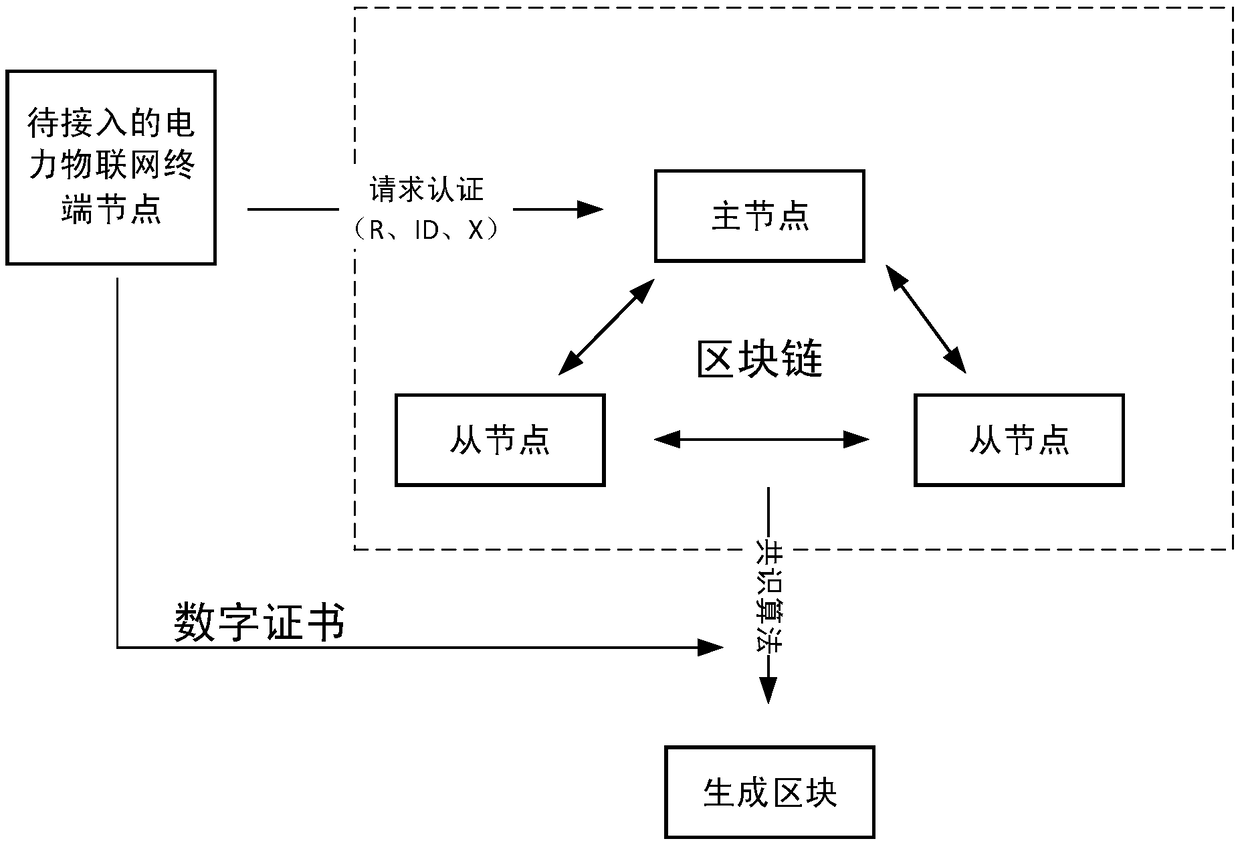
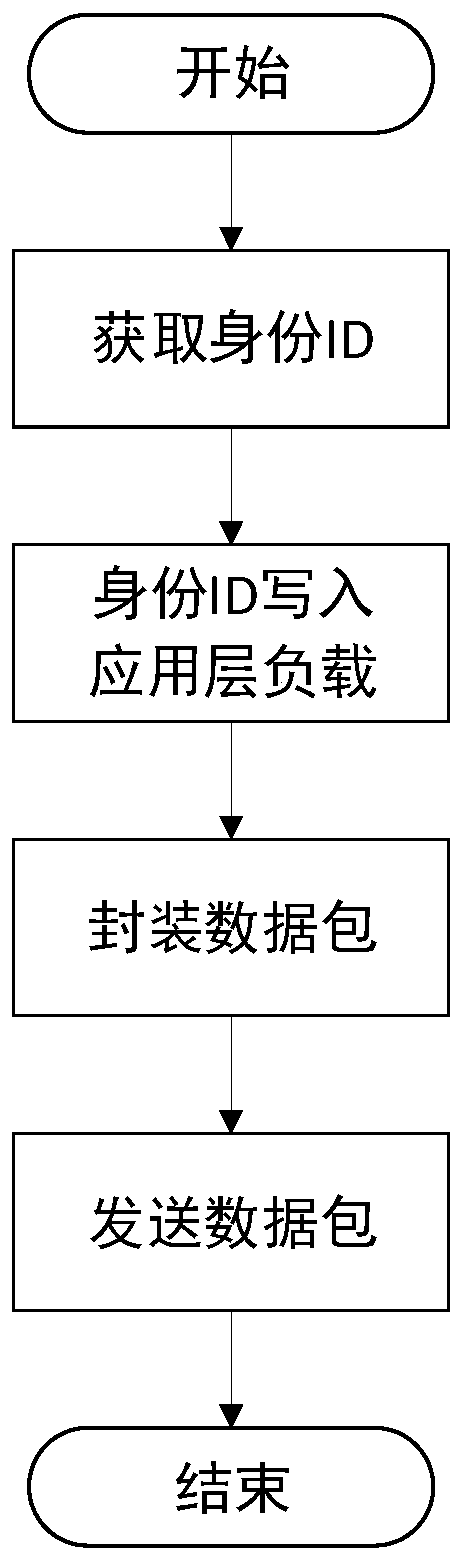
Block chain-based method for accessing power Internet of Things terminal
InactiveCN109495516AReduce communication pressureReduce computing pressureKey distribution for secure communicationUser identity/authority verificationAccess methodCiphertext
The invention provides a Block chain-based method for accessing a power Internet of Things terminal, comprising the steps of: connecting a to-be-accessed power Internet of Things terminal to a masternode, and initiating an authentication request; the master node responding to the authentication request, and randomly selecting nodes that meet the condition of a threshold number from the block chain to form an authentication group; encrypting a public key G and an identity ID of the to-be-accessed power Internet of Things terminal by using a private key to obtain a digital signature ciphertextX, and sending the identity ID, a terminal public value R and the digital signature ciphertext X to the master node; the master node encapsulating and sending the authentication request information toa member node of the authentication group; the authentication group running PBFT consensus algorithm, and obtaining an authentication result by performing distributed authentication through two-two exchanging of the authentication information between the nodes of the authentication group; generating a new block in the block chain, and returning confirmation information to the to-be-accessed powerInternet of Things terminal; and the power Internet of Things terminal returning encrypted confirmation information to an access gateway. The block chain-based power Internet of Things terminal access method can improve the security and efficiency of authentication.
Owner:JIANGSU ELECTRIC POWER CO
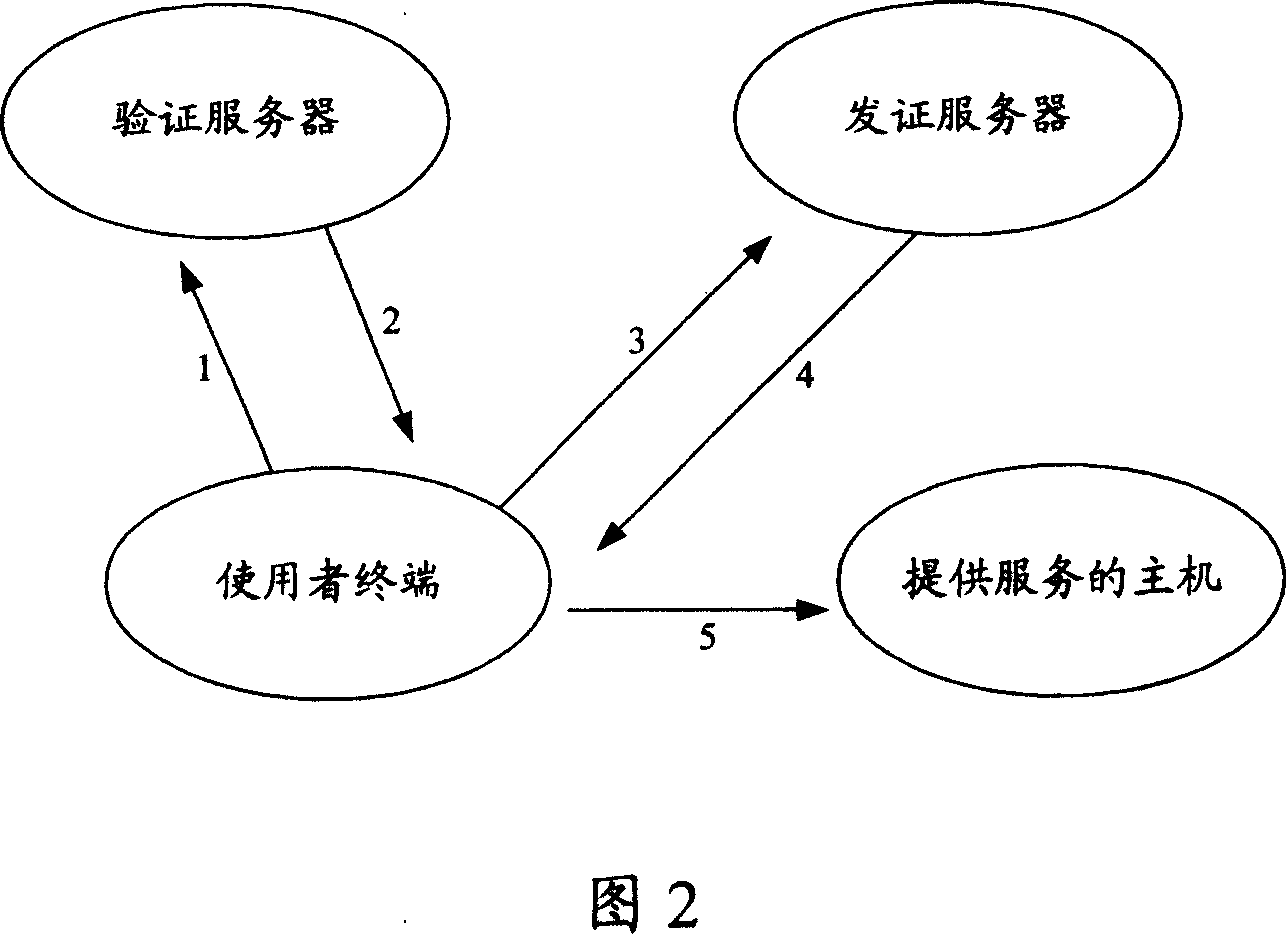
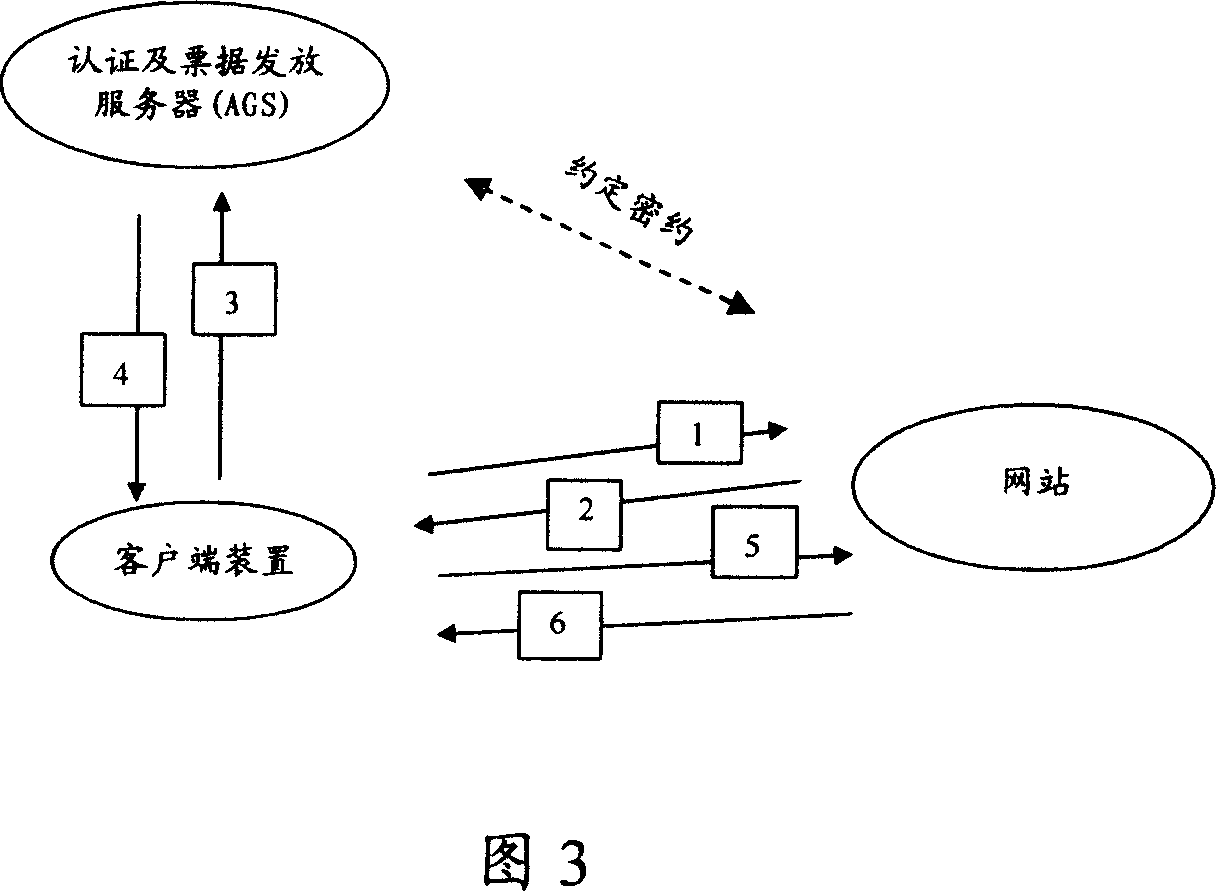
Network log-in authorization method and authorization system
ActiveCN101047504AKnow exactly when the event will take placePrevent counterfeitingUser identity/authority verificationClient-sideAuthentication system
A authentication method of network login includes issuing login request to network station (NS) by client device to obtain NS identification information returned back from NS, providing user account number and cipher as well as NS identification information to AGS for carrying out right-certification, generating service note for logging in NS and conversation cipher key by AGS according unique enciphering key appointed with NS, using said service note and said conversation cipher key to log in NS by client end. The authentication system used for realizing said method is also disclosed.
Owner:SHENZHEN TENCENT COMP SYST CO LTD
Verificating method and device
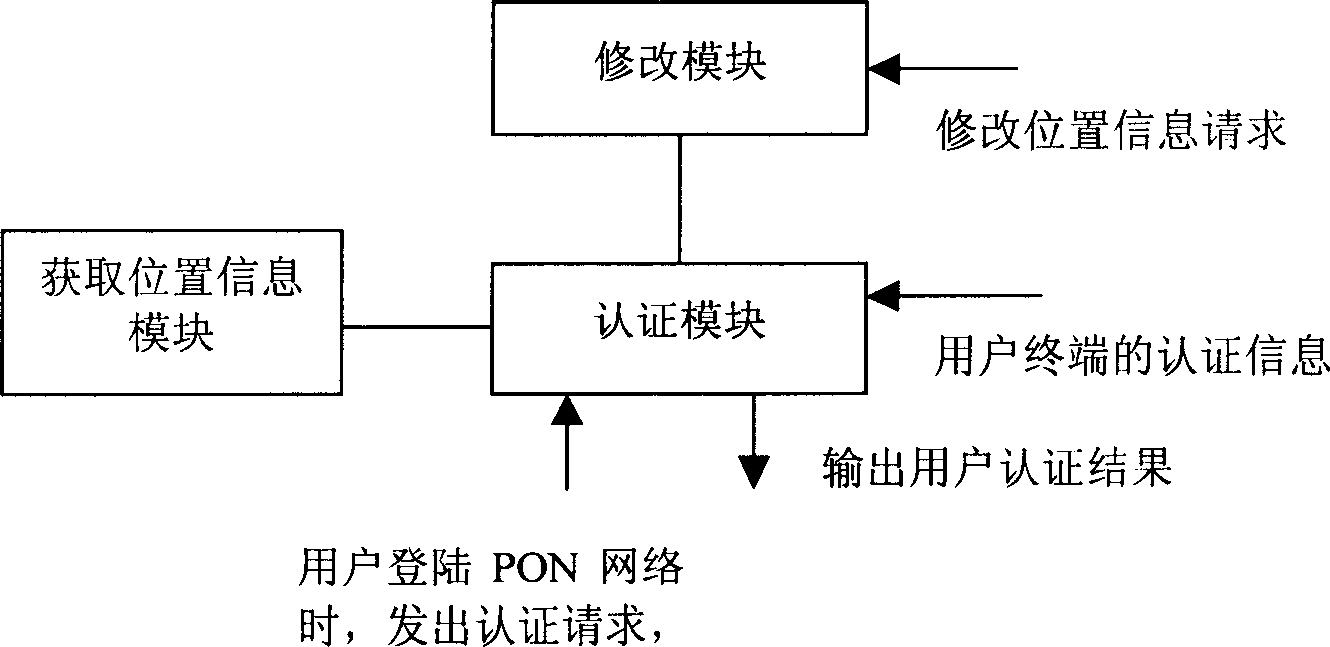
InactiveCN1855813AExclude access toEasy accessUser identity/authority verificationRadio/inductive link selection arrangementsInternet privacyAuthentication
The key-ideal of the invention is: getting the location information about user end; in term of the obtained location information and predetermined location information corresponding to the user end, making authentication for the use end. The invention uses parameters currently existed in PON technology such as RTT value used in the authentication process for user end in order to provide security protection for legal user end and avoid the usage of network resource by illegal user end.
Owner:HUAWEI TECH CO LTD
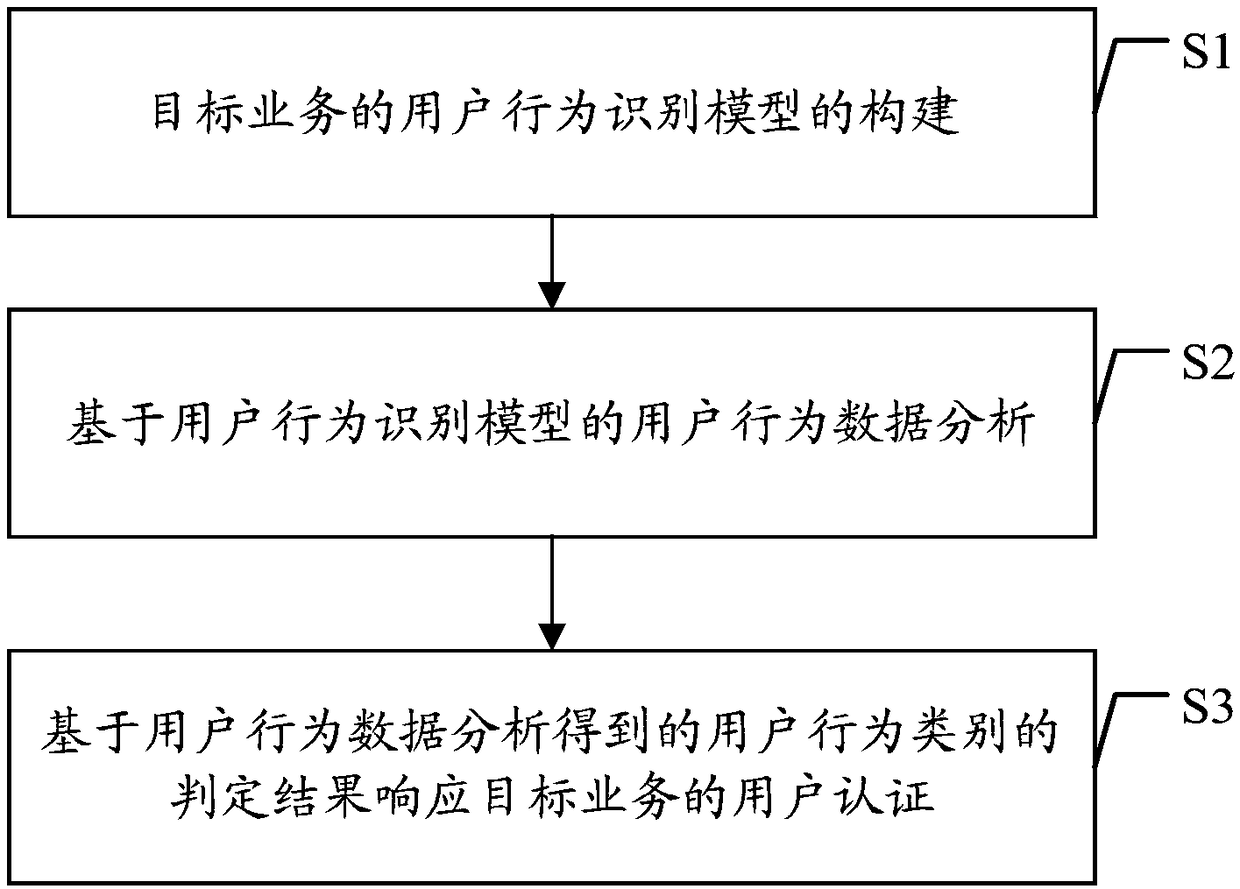
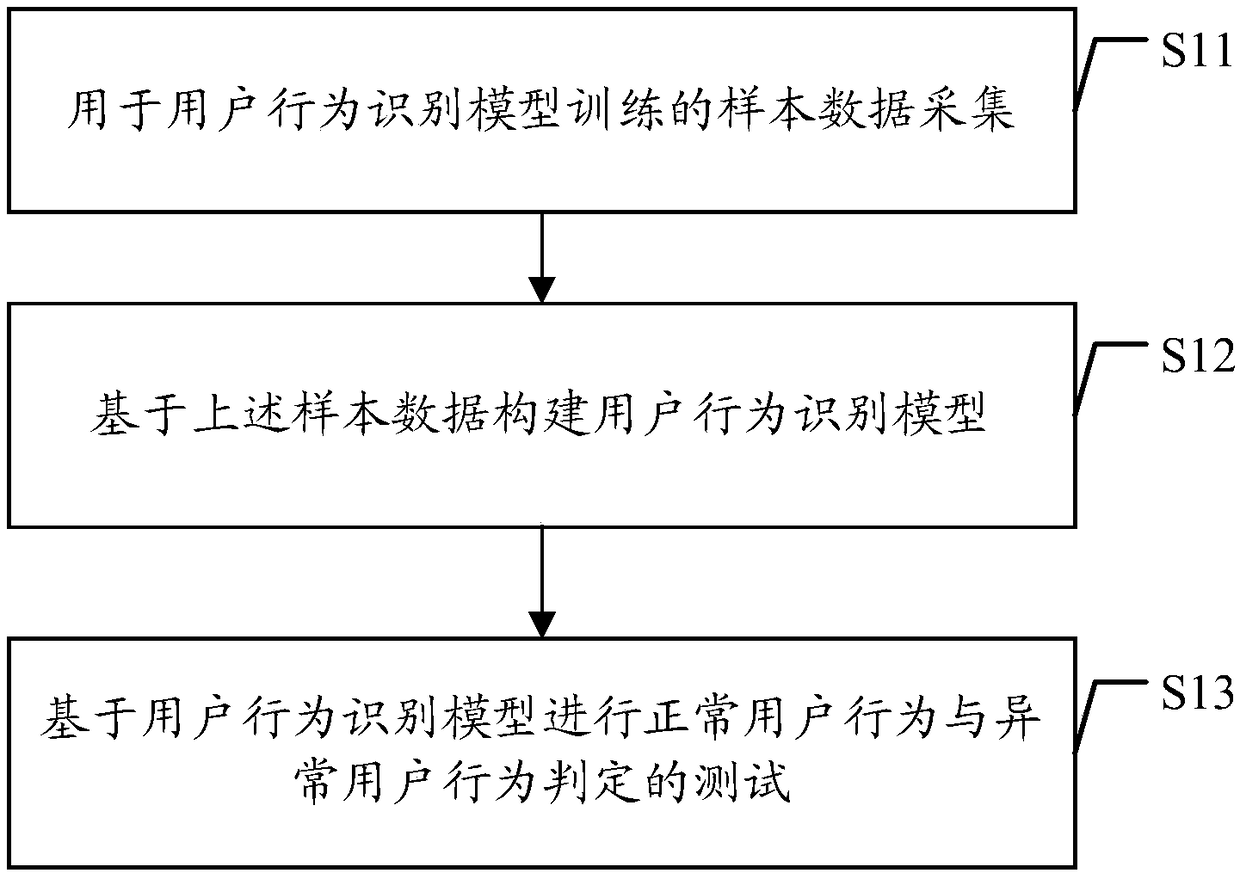
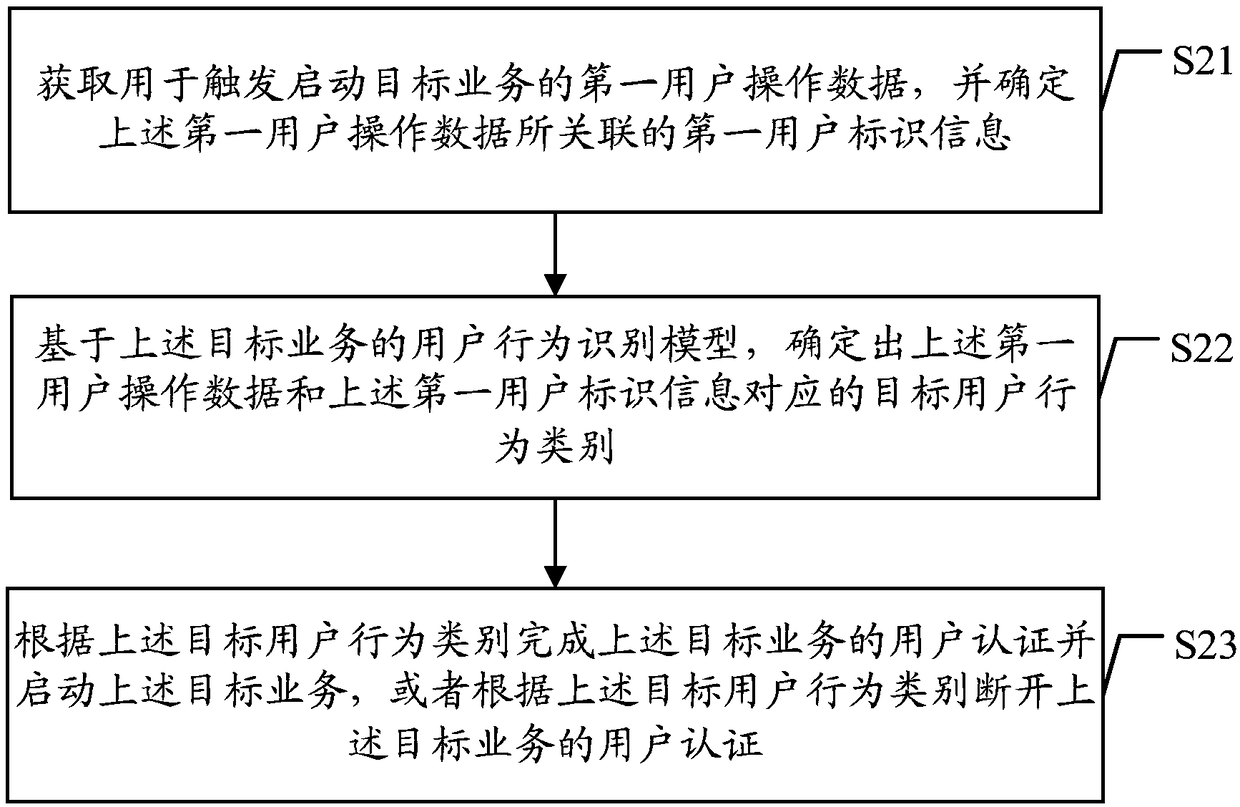
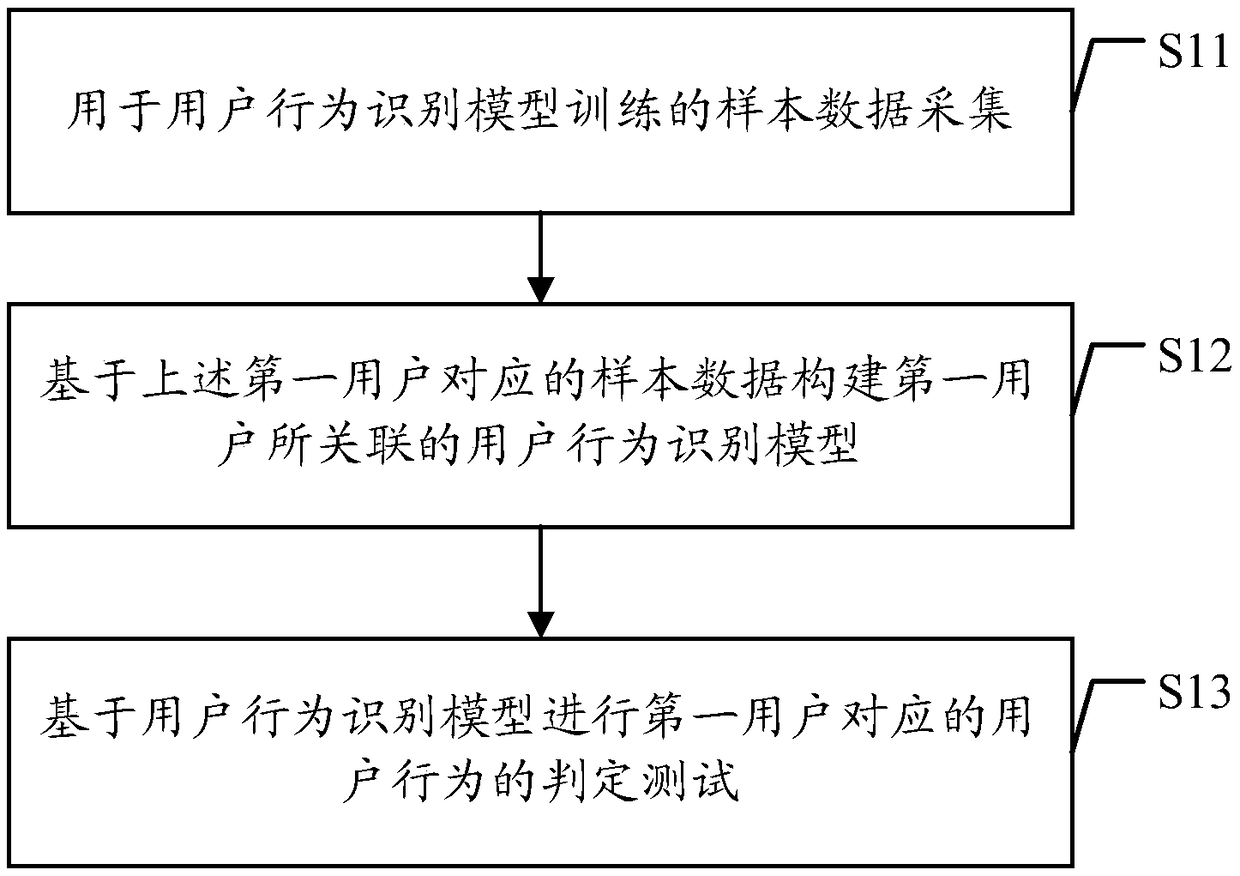
Method and device for recognizing user behavior based on prediction model
ActiveCN109241711AImprove authentication securityAuthentication Security GuaranteeForecastingCharacter and pattern recognitionUser authenticationData mining
Embodiments of the present application disclose a user behavior identification method and apparatus based on a prediction model. The method includes: first user operation data for triggering a start-up target service is obtained, and first user identification information associated with the first user operation data is determined; based on user behavior recognition model of the target service, a target us behavior class correspond to that first user operation data and the first user identification information is determined, the user behavior identification model is obtained by training sampledata for starting the target service, and the sample data includes at least the first user behavior sample data and the second user behavior sample data; the user authentication of the target serviceis completed according to the target user behavior category and the target service is started, or the user authentication of the target service is disconnected. By adopting the embodiment of the present application, the user behavior category can be determined based on the regression algorithm, the identification accuracy rate of the user behavior category starting the target service is improved,and the user data security of the target service is improved.
Owner:PING AN TECH (SHENZHEN) CO LTD
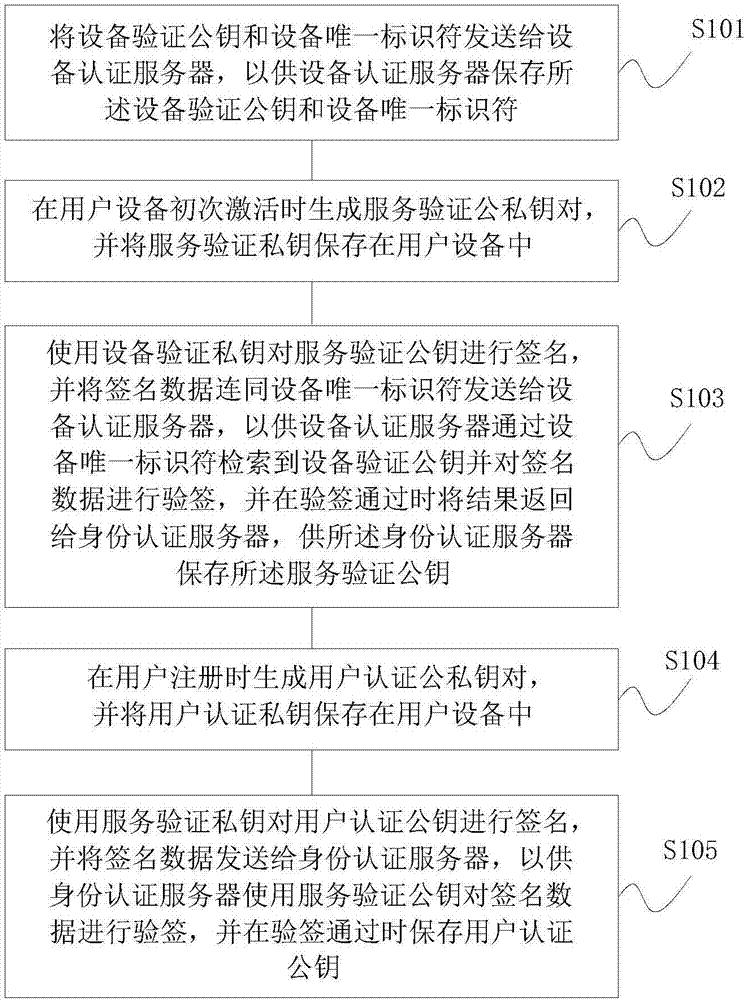
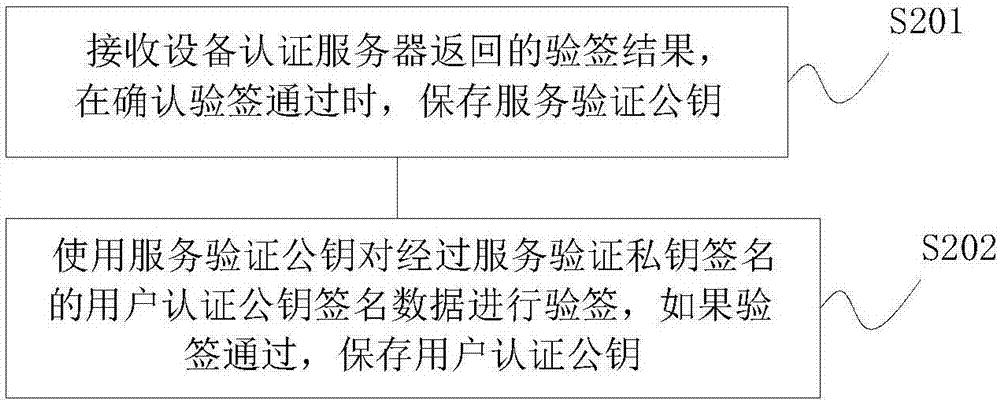
Identity authentication method, user equipment and server
ActiveCN107196922AImprove authentication securityImprove securityUser identity/authority verificationInternet Authentication ServiceUnique identifier
The invention discloses an identity authentication method, which is applied to a user equipment side, and comprises the steps of: sending an equipment authentication public key and an equipment unique identifier to an equipment authentication server for storage by the equipment authentication server; using an equipment authentication private key to sign a server authentication public key, and sending signature data and the equipment unique identifier to the equipment authentication server, so that the equipment authentication server retrieves the equipment authentication public key by means of the equipment unique identifier, performs signature authentication on the signature data, and returns a result to an identity authentication server for storage when the signature authentication passes; and using a service authentication private key for signing a user authentication public key, sending signature data to the identity authentication server so that the identity authentication server performs signature authentication by using the service authentication public key, and saving the user authentication public key when the signature authentication passes. The identity authentication method solves the security risk problem existing in registration of a user in the existing FIDO authentication standard. The invention further provides corresponding user equipment and servers.
Owner:GUOMIN RENZHENG TECH BEIJING CO LTD
Method and system for certifying the presence of an operator
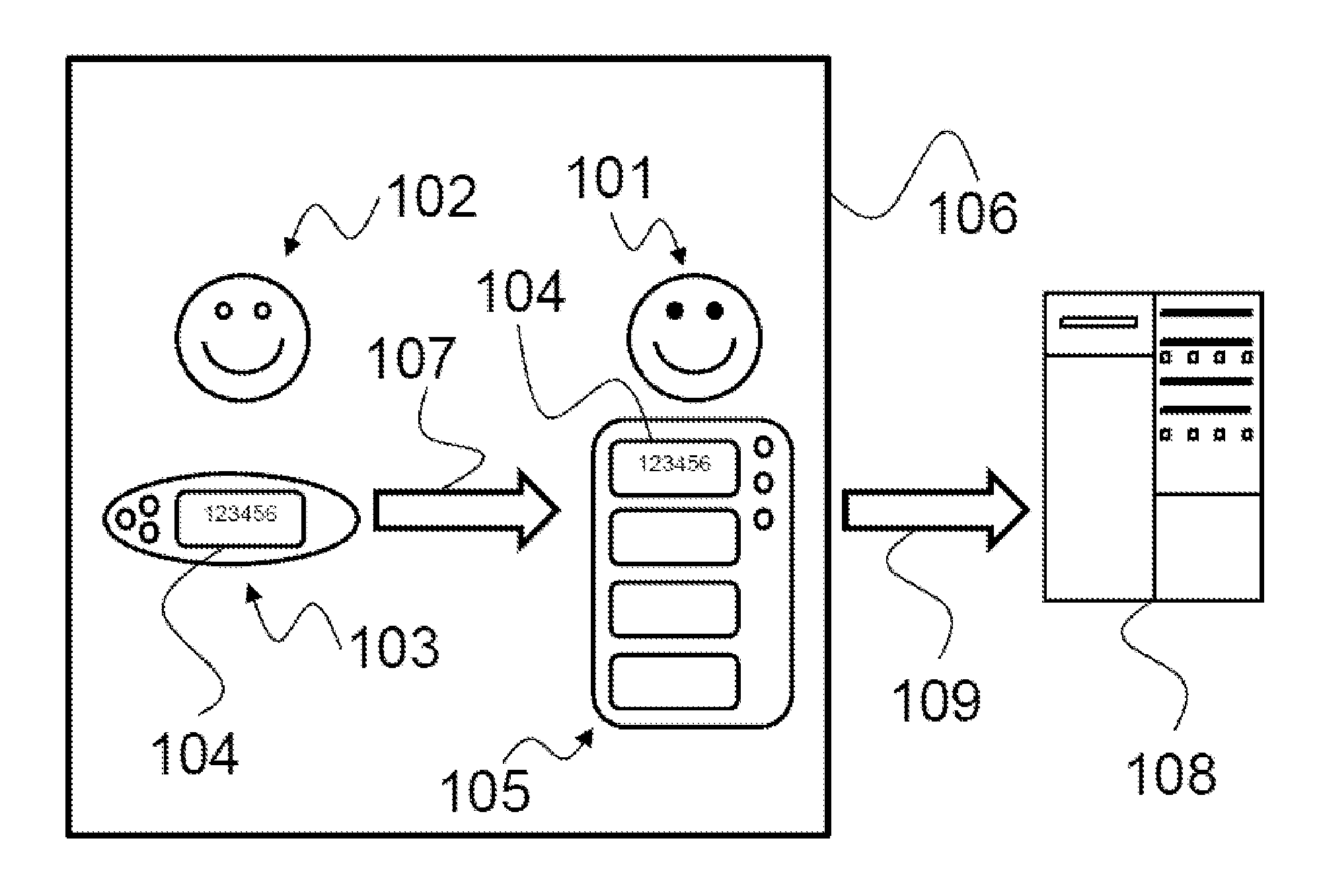
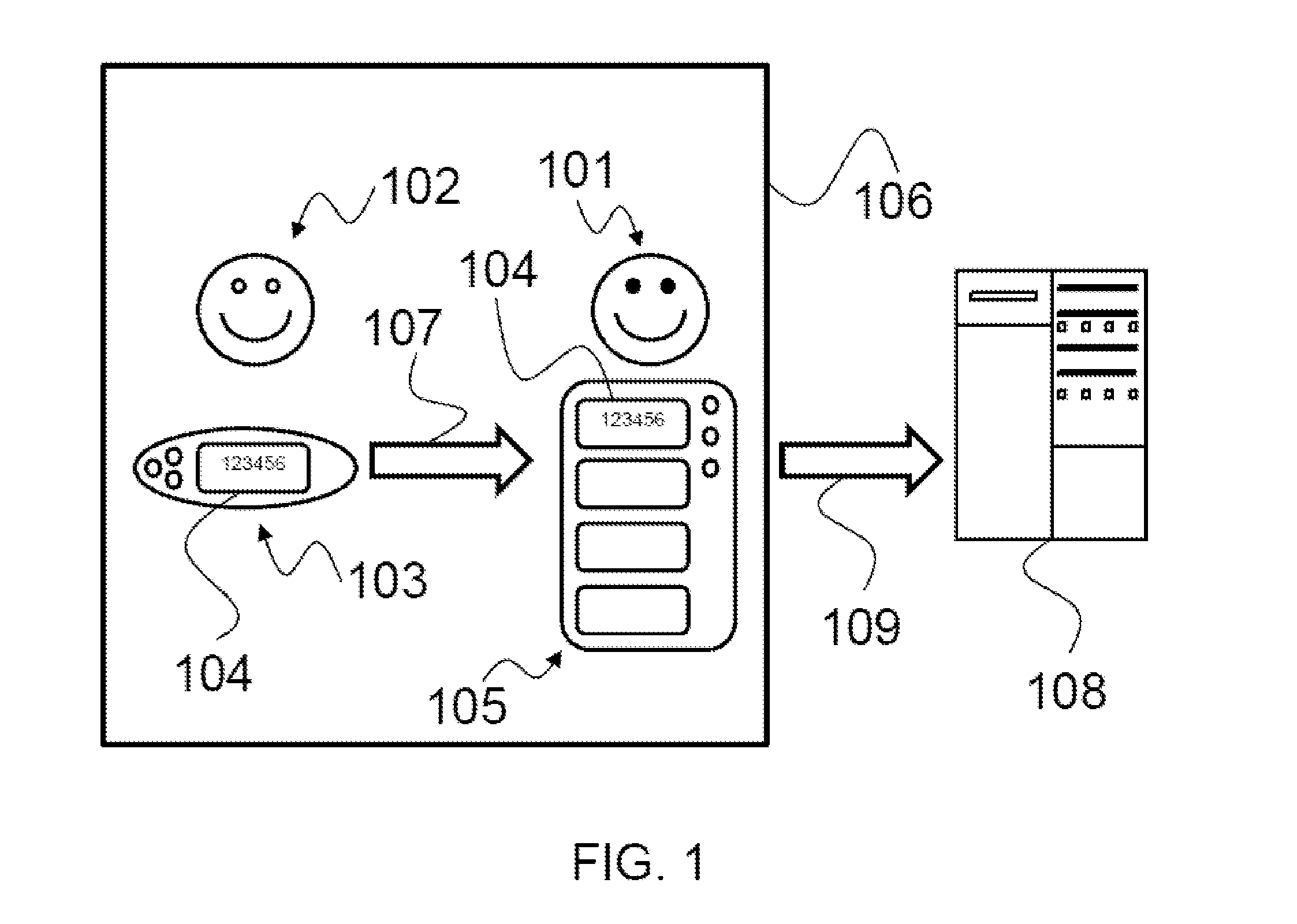
InactiveUS20150002261A1Simple transmissionEasy to storeProgramme controlElectric signal transmission systemsTime informationComputer network
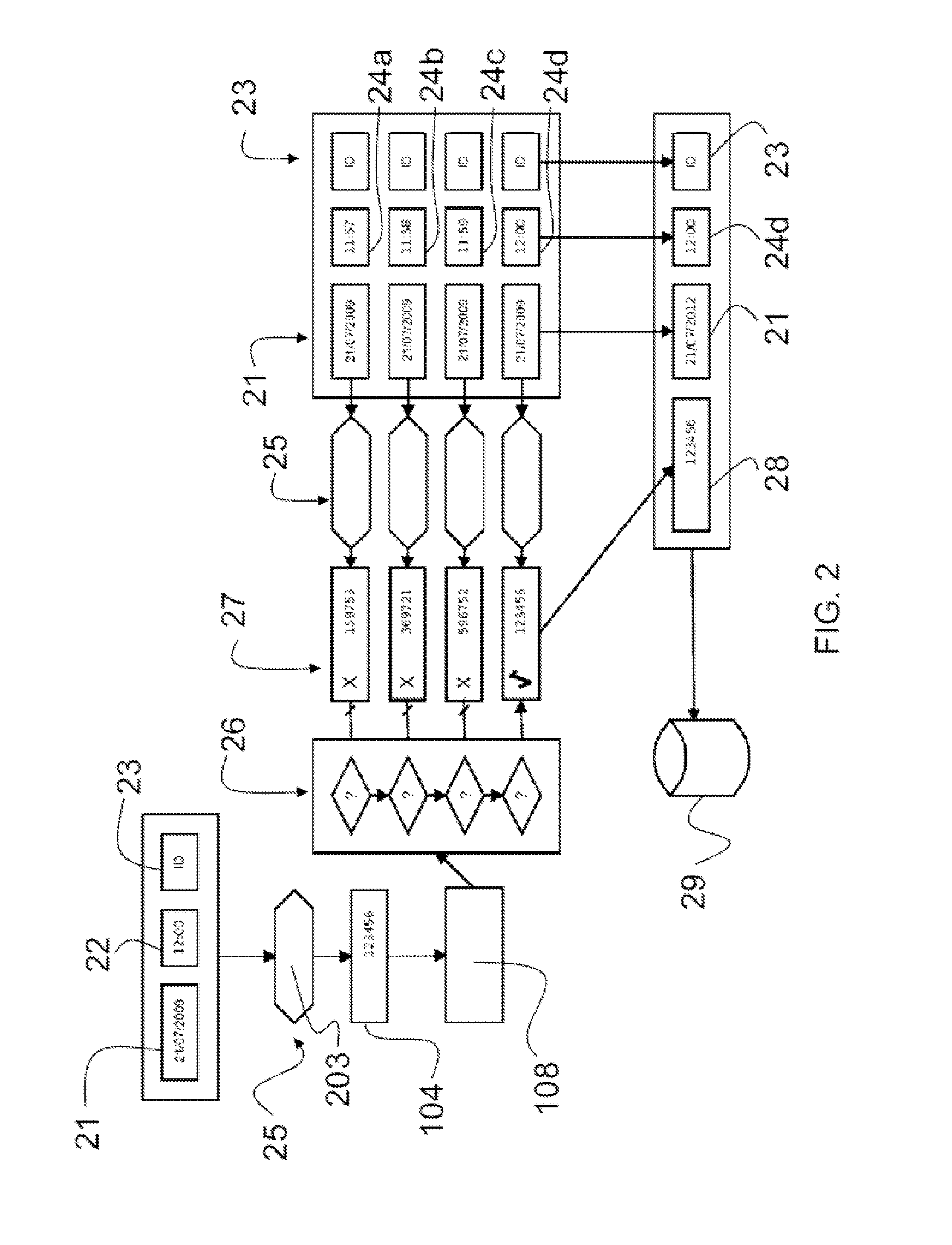
A method for certifying the presence of an operator includes a presence code (104) requested (202) at a given time instant (21, 22) to a first device (103) operable by a user (102); the first device (103) generates (203) the presence code (104), the presence code (104) including a portion generated according to an encoding algorithm (25), wherein the generated portion depends on the time instant (21, 22) and on an identifier (23) of the first device (103); a second device (105) operable by an operator (101) stores (204) the generated presence code (104); the presence code (104) is transmitted (109) to a third validation device (108); the third validation device (108) certifies (212) the presence of the operator (101) at the user (102) at the time instant (21, 22); the certification (212) including: providing the third validation device (108) with at least one piece of time information (21, 206, 306) about the time instant (21, 22), and further providing (205) the identifier (23) of the first device (103), wherein the presence code (104) is validated (208) by comparing it (26) with at least one second presence code (27) generated (25) by the third validation device (108) according to the same encoding algorithm (25) and according to the piece of time information (21, 206, 306) and according to the identifier (23), wherein certification (212) occurs if the comparison (26) shows a match between the presence code (104) and the second presence code (27).
Owner:SIXS S R L SOLUZIONI INFORMATICHE PER IL SOCIALE
Fingerprint sensor with force sensor
ActiveUS20170344782A1Improve authentication securityImproved authentication securityDigital data authenticationPrint image acquisitionFingerprintComputer hardware
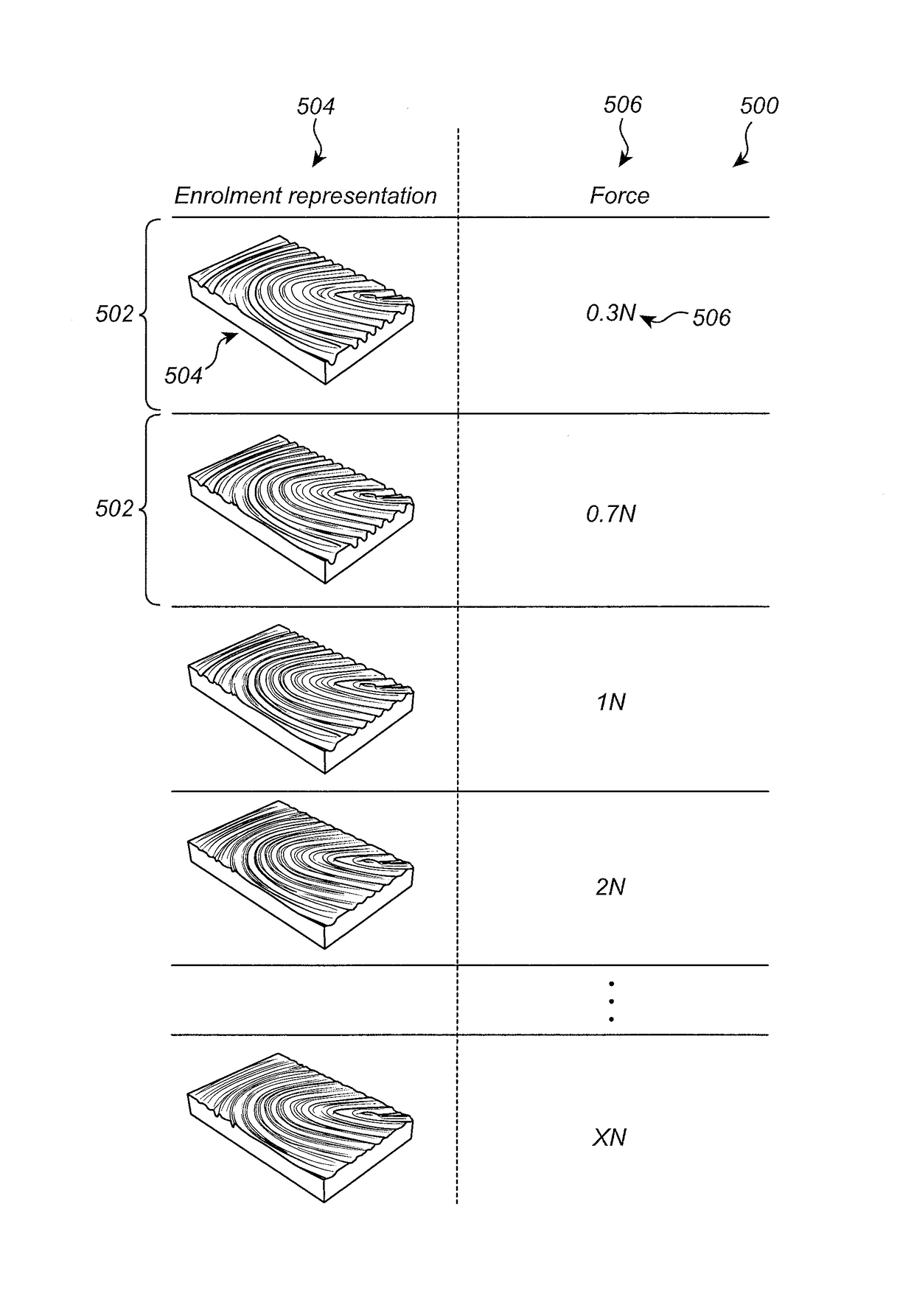
The present invention generally relates to a method for authenticating a user of an electronic device comprising a fingerprint sensor and a force sensor, the method comprising: retrieving a stored plurality of fingerprint enrolment templates comprising an enrolment representation of at least part of a user's finger and a corresponding enrolment force parameter, acquiring a first verification image of an object and determining a first verification representation, determining a first verification force parameter, performing a fingerprint authentication procedure based on the first verification template and the plurality of fingerprint enrolment templates, wherein when the first verification representation and the first verification force parameter comprised in the first verification template matches each of the enrolment representation and the enrolment force parameter comprised in the same fingerprint enrolment template providing a signal indicating successful authentication of the user. The invention also relates to a fingerprint sensing system and an electronic device.
Owner:FINGERPRINT CARDS ANACATUM IP AB
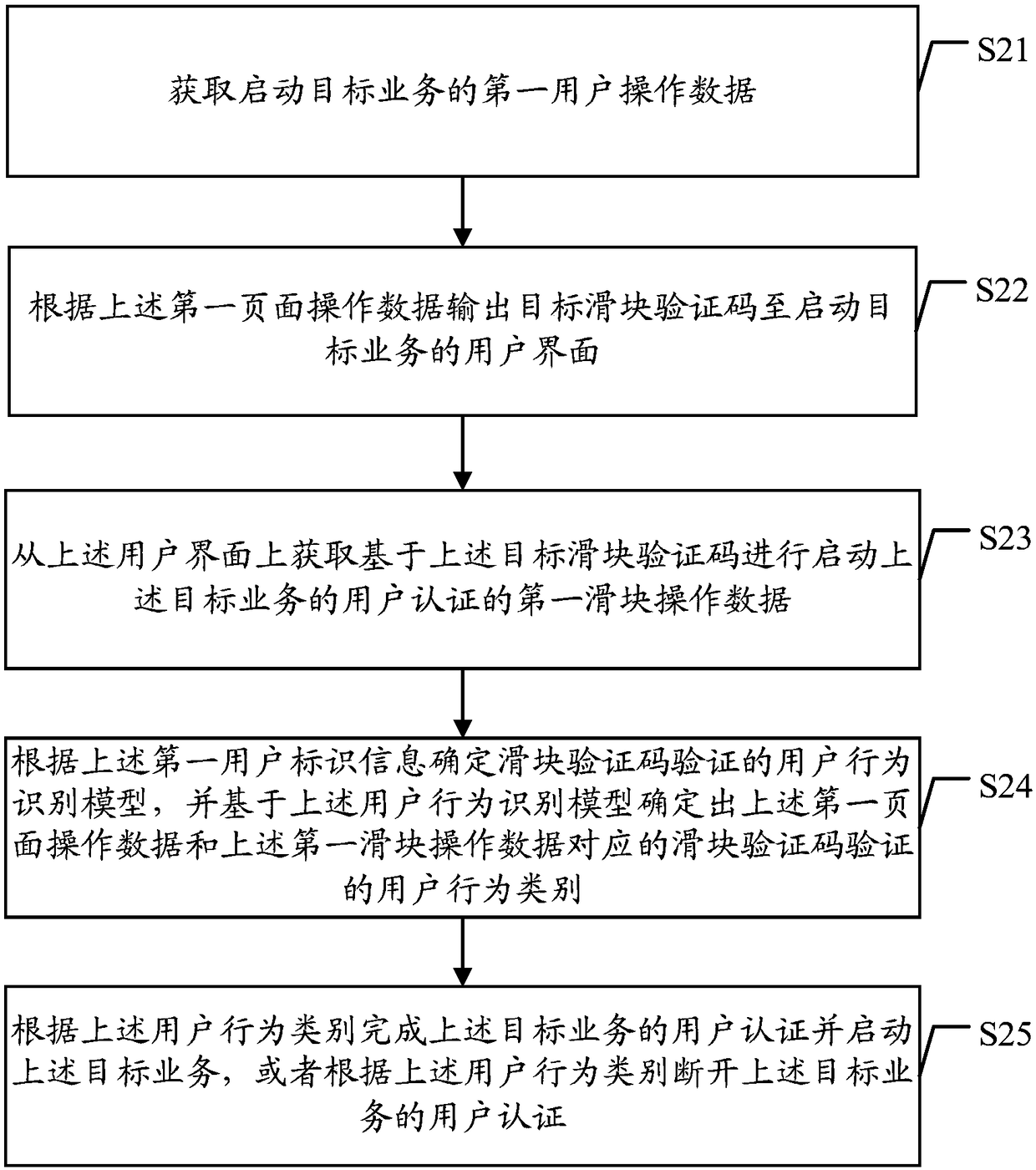
User behavior recognition method and device based on slider verification code verification
ActiveCN109241709AImprove authentication securityAvoid attackDigital data authenticationEnergy efficient computingInternet privacyUser authentication
The embodiment of the application discloses a method and a device for identifying user behavior based on slider authentication code verification. The method comprises the following steps: first user operation data for starting a target service is obtained, the first user operation data including first user identification information and first page operation data; A target slider verification codeis output to the user interface according to the first page operation data, and first slider operation data for user authentication based on the target slider verification code is obtained from the user interface; The user behavior identification model verified by the slider authentication code is determined according to the first user identification information, and a user behavior category corresponding to the first page operation data and the first slider operation data is determined based on the user behavior identification model; user authentication is completed or user authentication isdisconnected according to the user behavior category. By adopting the embodiment of the application, the user authentication security based on the slider authentication code authentication can be improved, the network attack of the slider authentication code authentication can be effectively prevented, and the security is higher.
Owner:PING AN TECH (SHENZHEN) CO LTD
Control method and system for internal and external network security access
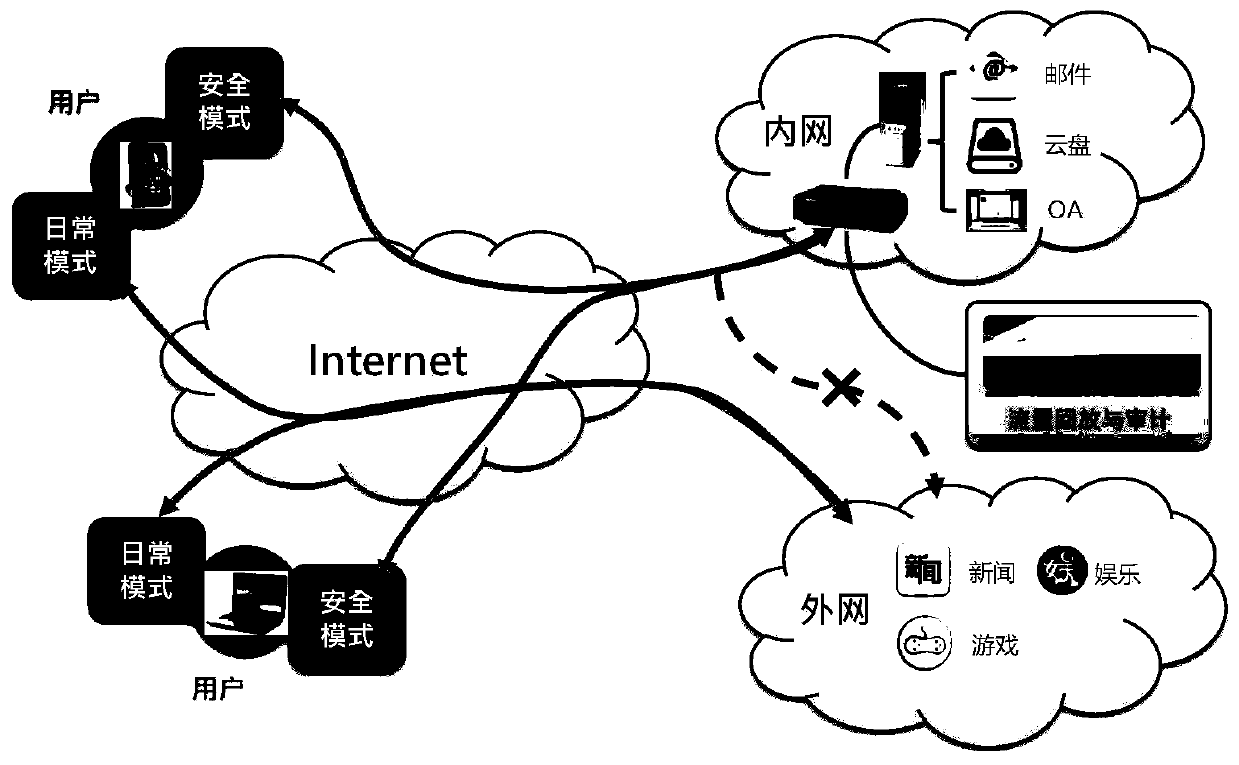
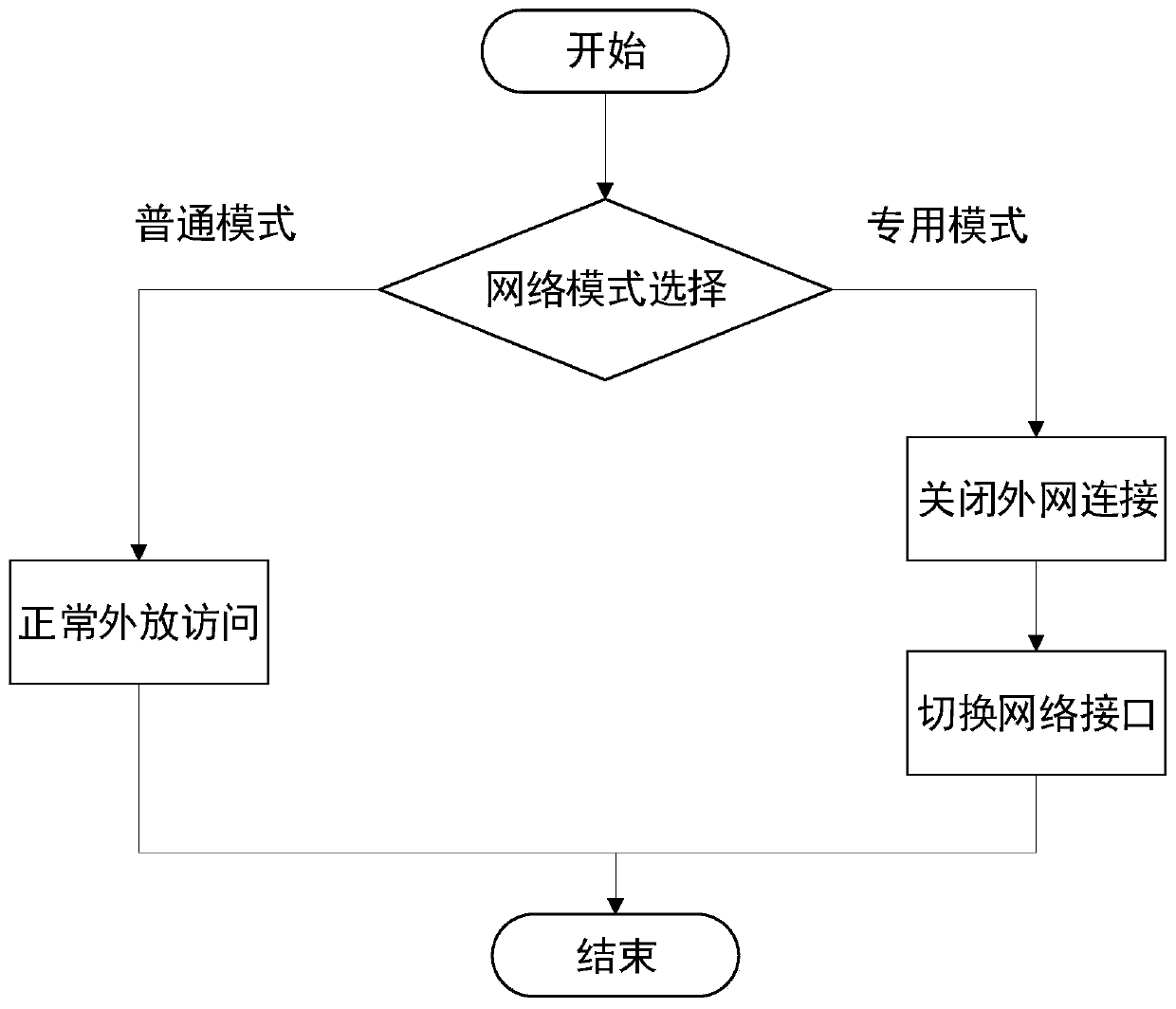
InactiveCN110430179AAchieve data security goalsImprove authentication securityTransmissionControl systemTerminal equipment
The invention discloses a control system for internal and external network security access. The system comprises a terminal security access subsystem and a gateway security access subsystem. The terminal security access subsystem solves the security problem encountered when the terminal accesses the intranet; access establishment process, providing unique recognition, communication process, data generated in the communication process is encrypted and stored in a partitioned manner; communication end process, securing in-time cleaning of caches, the gateway security access subsystem mainly realizes authentication auditing work for terminal access, can accurately authenticate terminal identity representation in the authentication process, and adopts different communication measures for the terminal according to an authentication result to ensure absolute security of the data. The invention further provides a corresponding control method which can be applied to an institution organizationwhich has high requirements for intranet data security and requires the terminal equipment to have a certain degree of flexibility.
Owner:XI AN JIAOTONG UNIV
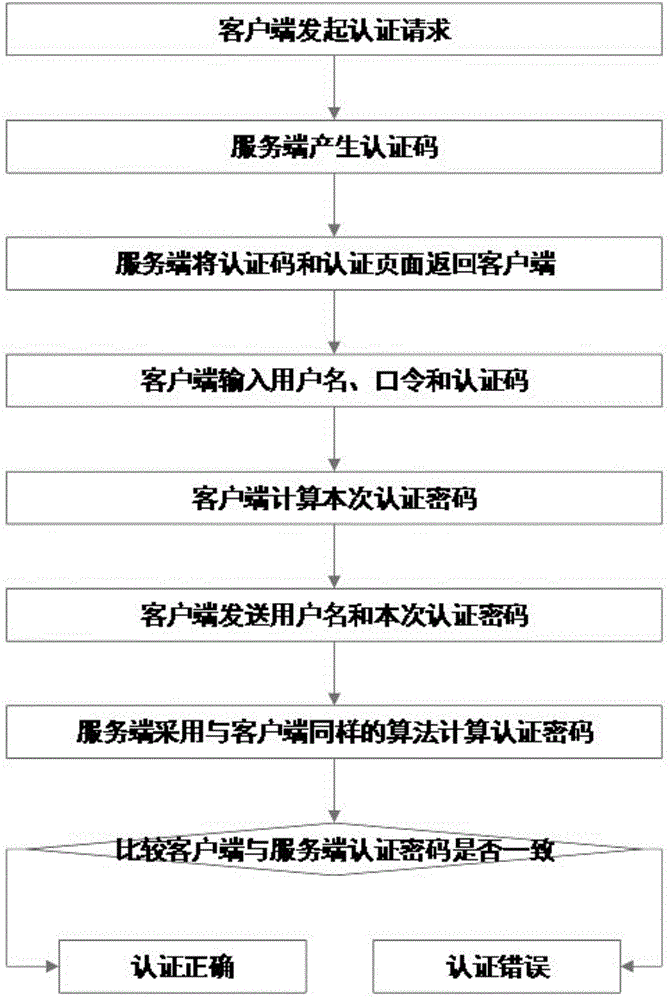
Method for authenticating network identity
ActiveCN104639331ASave bandwidthAvoid the risk of leakageUser identity/authority verificationPasswordUser input
The invention discloses a method for authenticating a network identity, comprising the following steps: a client side sends an authentication request to a server side; the server side generates authentication information according to the authentication request and feeds the authentication information back to the client side, wherein the authentication information includes dynamic instructions and an authentication interface; the client side obtains user information input by a user through the authentication interface; the client side generates an authentication password through the user information; the server side generates an authentication comparing code according to the user information; the server side compares the authentication password with the authentication comparing code; and if the authentication password is identical to the authentication comparing code, the authentication is successful. The method combines the username and the password with a password authentication of a verification code and replaces the verification code with a subscript for obtaining the authentication password, so that the risk of revealing the password and the verification code is avoided, the network bandwidth required by the authentication is reduced and the authentication safety is improved.
Owner:北京信安世纪科技股份有限公司
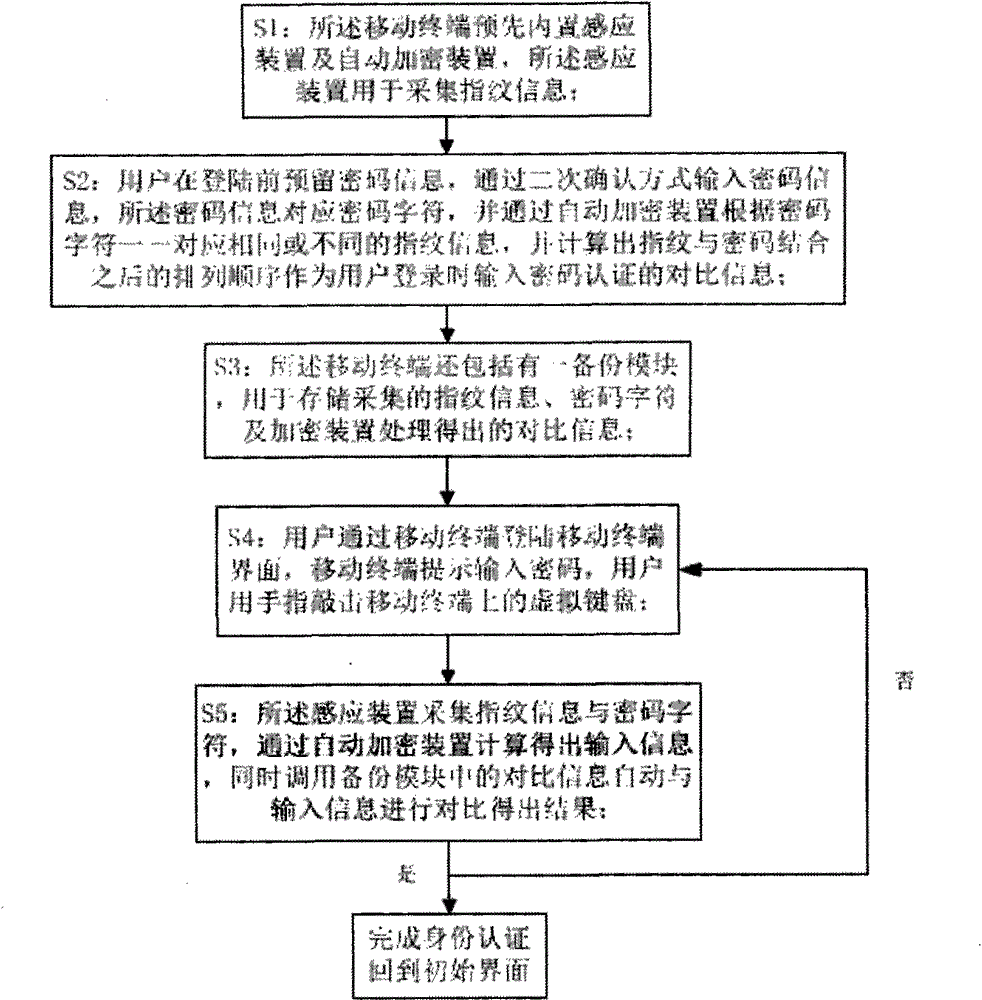
Method for achieving identity authentication on mobile terminal
InactiveCN104462911AImprove authentication securityDigital data authenticationComputer hardwareUser input
The invention discloses a method for achieving identity authentication on a mobile terminal. The mobile terminal is of a touch screen type. Comparison information is obtained by arranging an induction and encryption device in the mobile terminal to process reserved information, and then login is conducted, wherein code characters formed by a code and a fingerprint are input and compared with the comparison information. According to the method for achieving identity authentication on the mobile terminal, the code characters input by a user are combined with fingerprint information in an encryption mode so that the comparison information can be formed, dual encryption is achieved, and the authentication safety is higher due to the normal login and code input method.
Owner:南京神盾信息技术有限公司
Terminal, identity authentication method, authentication method for authentication center and terminal and authentication system
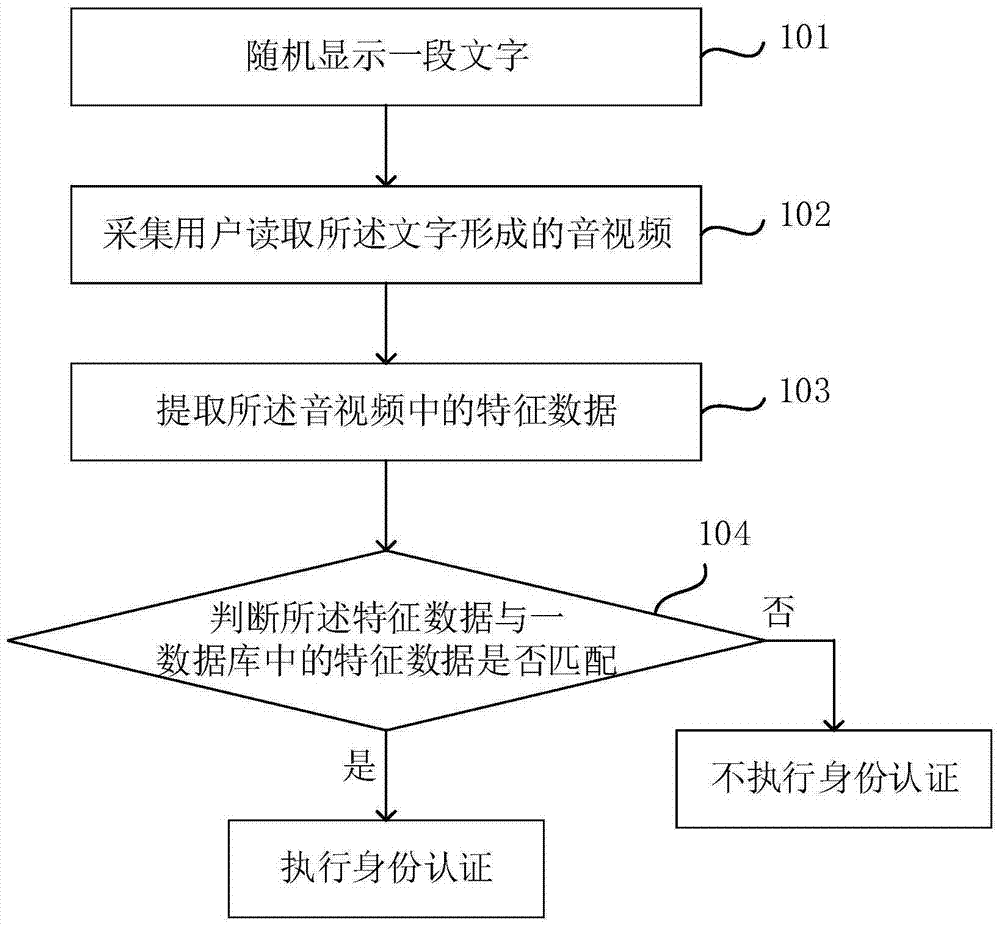
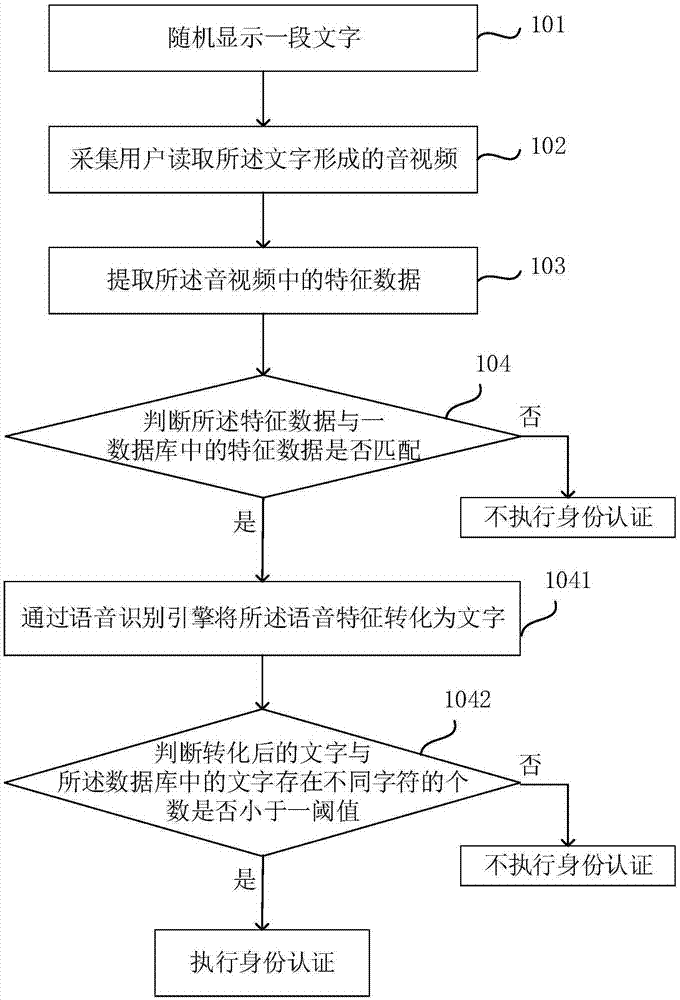
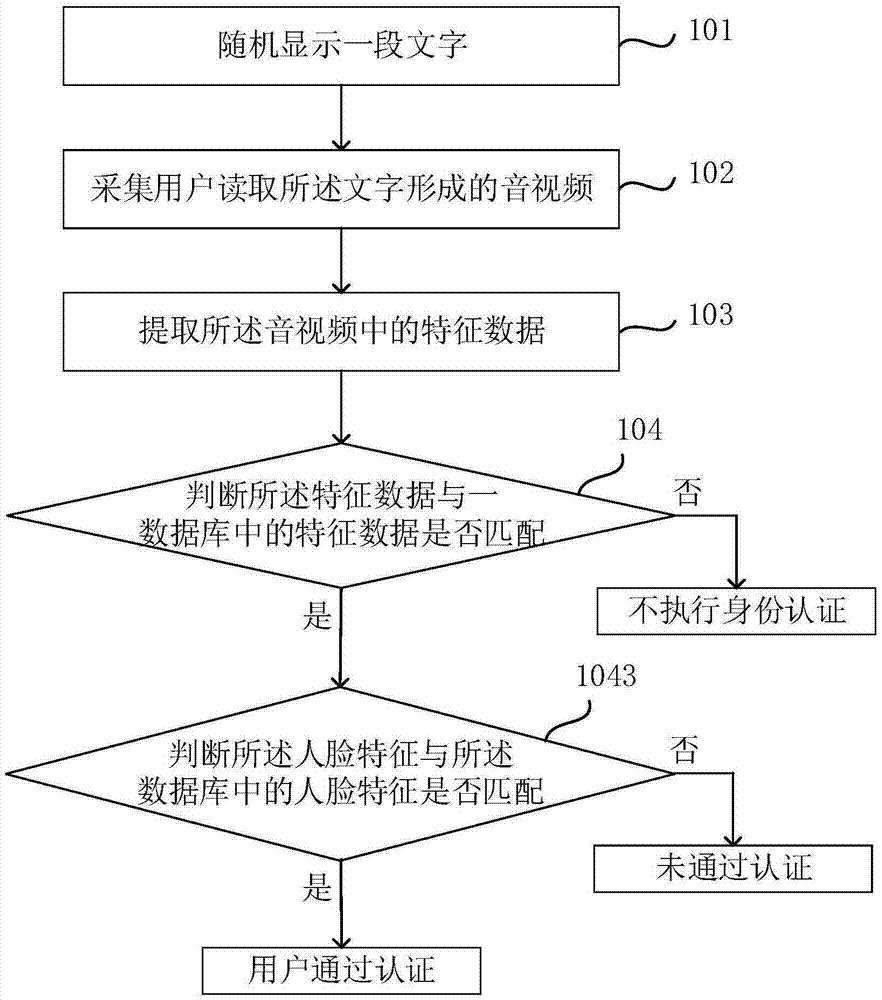
InactiveCN106911630AAvoid low securityImprove authentication securityTransmissionAuthentication systemMouth shape
The invention discloses a terminal, an identity authentication method, an authentication method for an authentication center and the terminal and an authentication system. The identity authentication method comprise the steps of randomly displaying a text; collecting an audio / video formed by reading the text, wherein the text is read by a user; extracting feature data in the audio / video; and judging whether the feature data matches the feature data in a database or not, if the feature data matches the feature data in the database, performing identity authentication, otherwise not performing the identity authentication. According to the terminal, the methods and the system, the text content displayed on the terminal is replaced continuously, so the audios / videos formed by reading the texts are different, wherein the texts are read by the user, the user can be authenticated according to the changed mouth shape feature data, and an illegal user is prevented from counterfeiting the same audio / video to simulate identity authentication. Compared with a mode of authenticating an identity through utilization of a cipher, the method has the advantages that the cipher does not need to be set, the defect that the security is low due to the fact that the cipher is liable to lose and steal is avoided, the authentication is assisted without configuring an extra device, only field authentication is carried out, and the authentication security is improved.
Owner:上海仪电数字技术股份有限公司
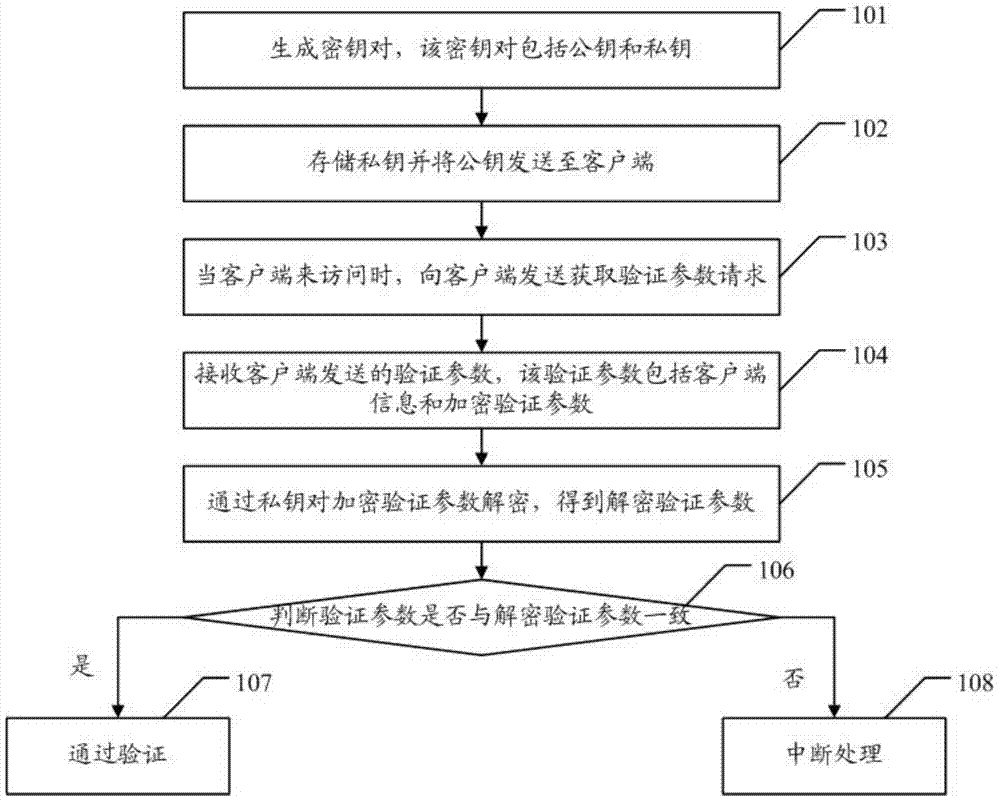
Web Service interface verification method, Web Service server and client side
The embodiment of the invention discloses a Web Service interface verification method, a Web Service server and a client side. Compared with the prior art, user names, passwords and access right contained in a user verification method are omitted, and the verification safety can be effectively enhanced. The Web Service interface verification method comprises the steps that firstly, the Web Service server generates a key pair including a public key and a private key, the private key is stored, the public key is sent to the client side, and when the client side has access to the Web Service server, a verification parameter request is sent to the client side, and verification parameters sent by the client side are received, wherein the verification parameters include client side information and encryption verification parameters; secondly, the private key is used for decrypting the encryption verification parameters, and decrypted verification parameters are obtained; finally, whether the verification parameters are consistent with the decrypted verification parameters or not is judged. According to the method, verification safety is improved through the key pair.
Owner:GUANGZHOU SHIYUAN ELECTRONICS CO LTD
Electronic apparatus with multi-finger fingerprint identifying function
ActiveUS20170083739A1Improve authentication securityImprove securitySubstation equipmentPrint image acquisitionComputer scienceFingerprint
An electronic apparatus with multi-finger fingerprint identifying function includes at least one multi-finger fingerprint sensor having a sensing electrode matrix with a side length of at least two centimeters such that the multi-finger fingerprint sensor can sense the fingerprints of at least two fingers simultaneously or sense user gesture. The electronic apparatus can authenticate the user fingerprint and sense user gesture and execute a predetermined operation according to the authentication result and the sensed user gesture.
Owner:SUPERC TOUCH CORP
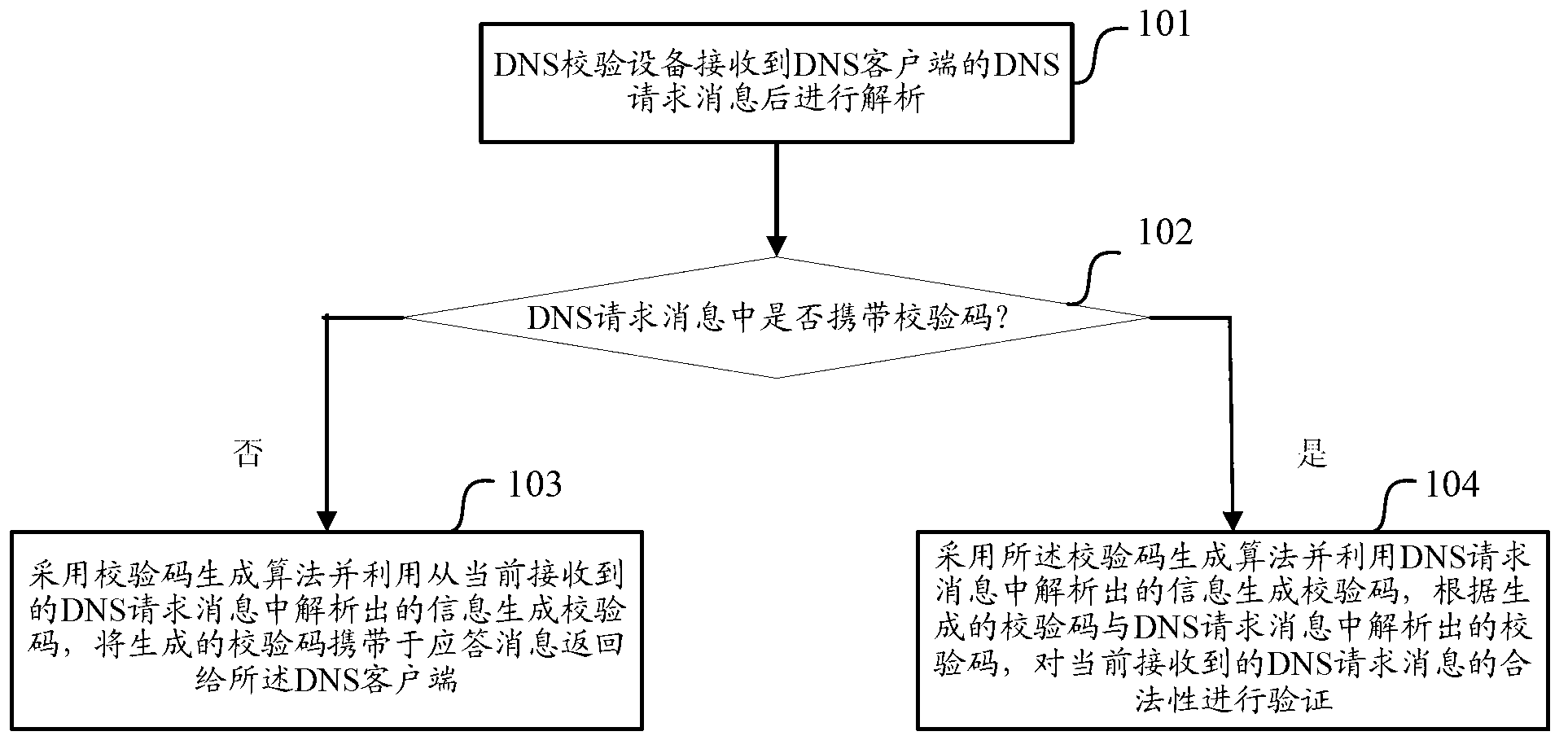
Domain name system (DNS) request authentication method and device
ActiveCN103312724ATo achieve the purpose of legality verificationAchieve legitimacyTransmissionClient-sideA domain
An embodiment of the invention discloses a domain name system (DNS) request authentication method and a device. The authentication method comprises the steps of enabling a DNS verification device to analyze DNS request messages after receiving the DNS request messages; if verification codes are not carried in the DNS request messages, adopting a verification code generating algorithm and utilizing information analyzed from the currently received DNS request messages to generate the verification codes, and returning the generated verification codes carried by answer messages to a DNS client-side; if the verification codes are carried in the DNS request messages, adopting the verification code generating algorithm and utilizing the information analyzed from the currently received DNS request messages to generate the verification codes, verifying validity of the currently received DNS request messages according to the generated verification codes and the verification codes analyzed from the currently received DNS request messages. DNS request authentication safety can be improved through the DNS request authentication method and the device.
Owner:CHINACACHE INT HLDG
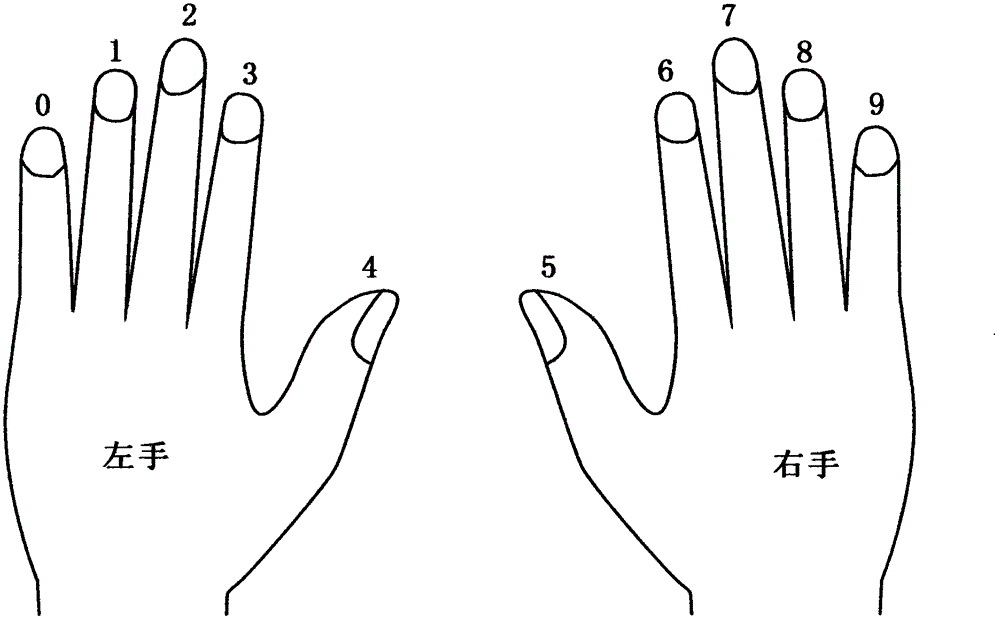
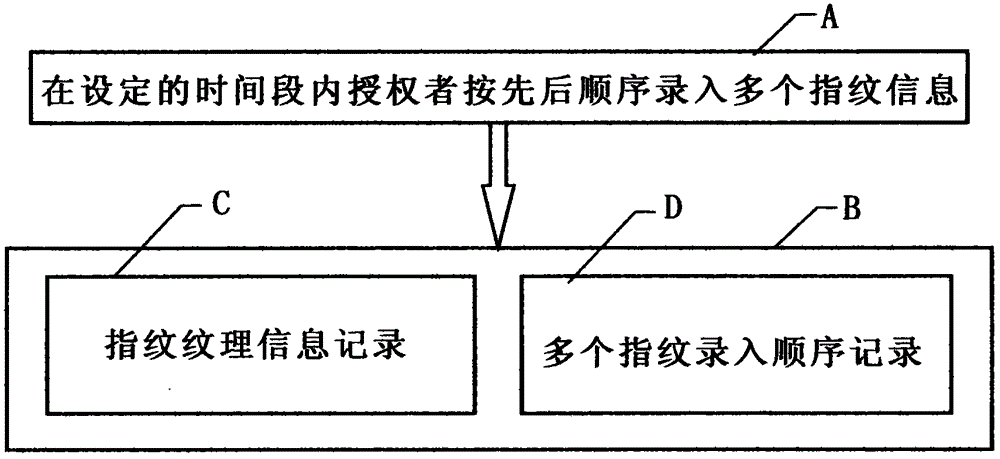
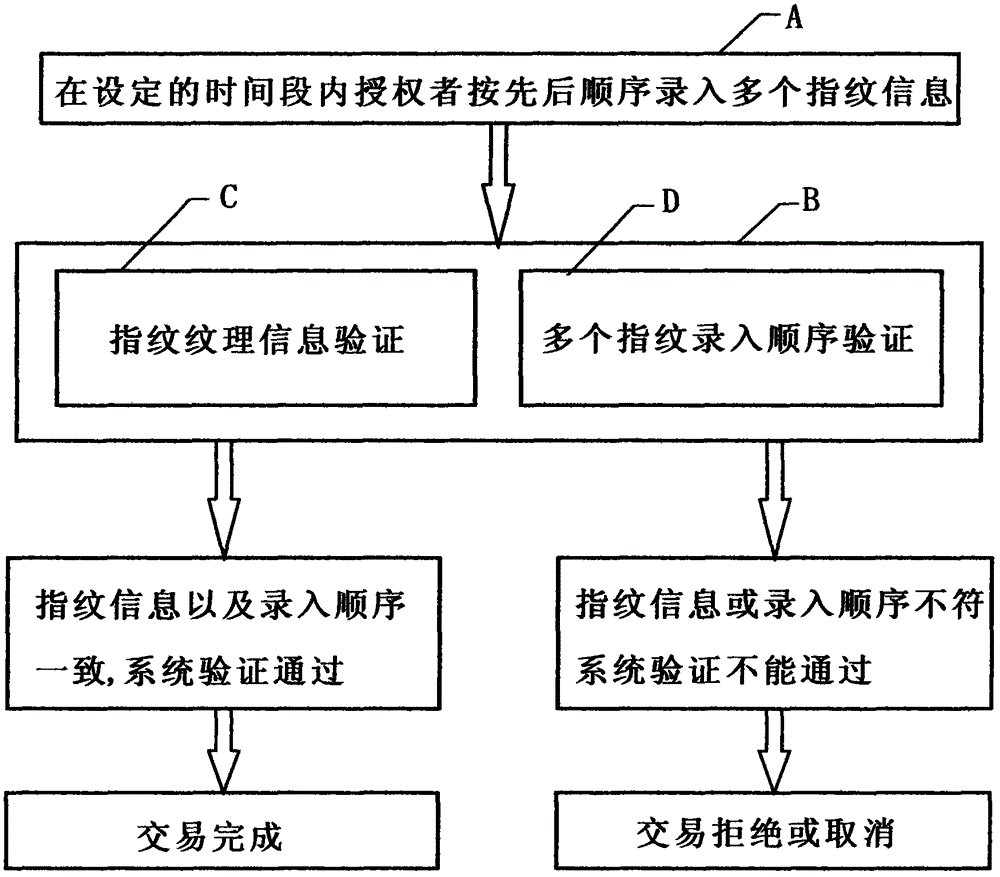
Fingerprint sequential composition password authentification system
InactiveCN105279478AImprove authentication securityEnsure account securityCharacter and pattern recognitionProtocol authorisationPasswordComputer terminal
The present invention provides a fingerprint sequential composition password authentification system. The system comprises a fingerprint input terminal and a fingerprint authentification system, and is technically characterized in that the fingerprint authentification system is provided with fingerprint information and sequence authentification procedures for recording information and an input sequence of over two fingerprints within a set period of time so as to carry out sequence authentification, and the sequence authentification procedure forms a group of specific fingerprint sequential composition password by using the input sequence of information of more than two fingerprints of a person. When applying for an account, a person can organize and combine the input sequence of several random fingers among the ten fingers through the fingerprint input terminal, the sequential composition password authentification system not only records information of every fingerprint input by the authorizer, but also records the input sequence of the fingerprint information, thereby forming a group of specific fingerprint sequential composition password, and when being required for authentification, the authorizer shall input the password on the fingerprint input terminal according to the preset input sequence of the fingerprints, thus to pass the system authentification. The system provided by the present invention is a novel authentification system which combines biological characteristics and mathematics probability at the same time.
Owner:谭荣兵
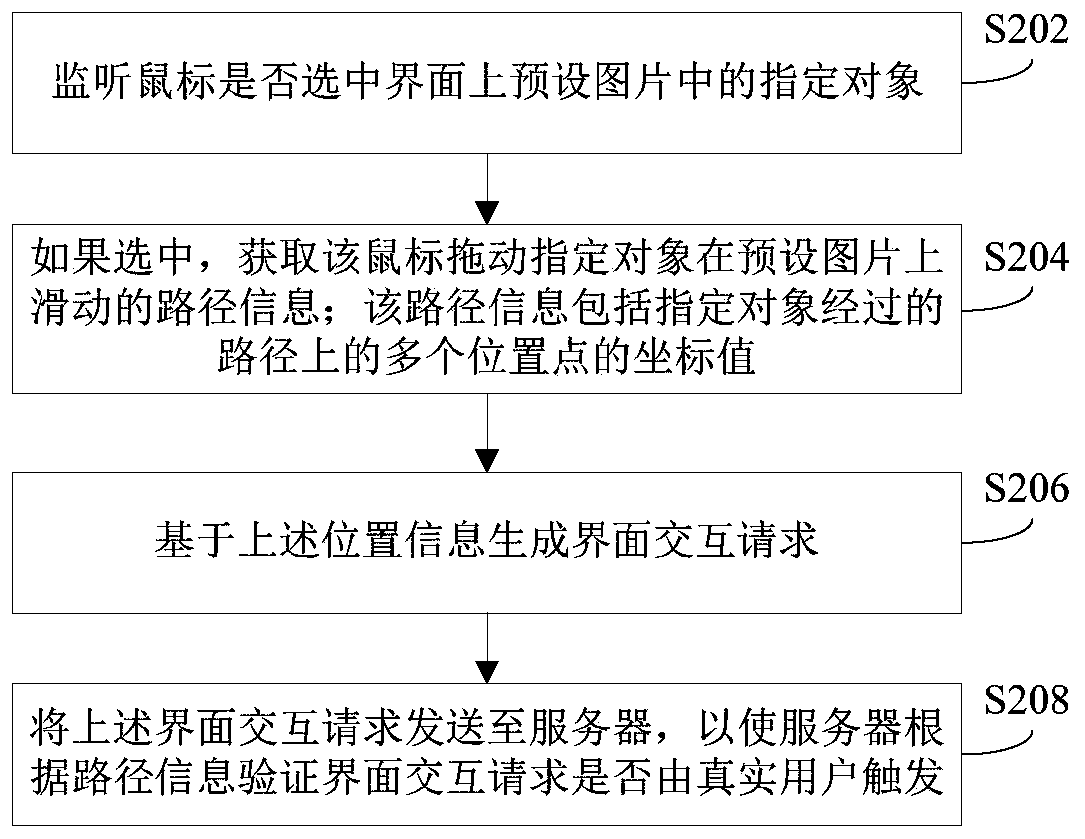
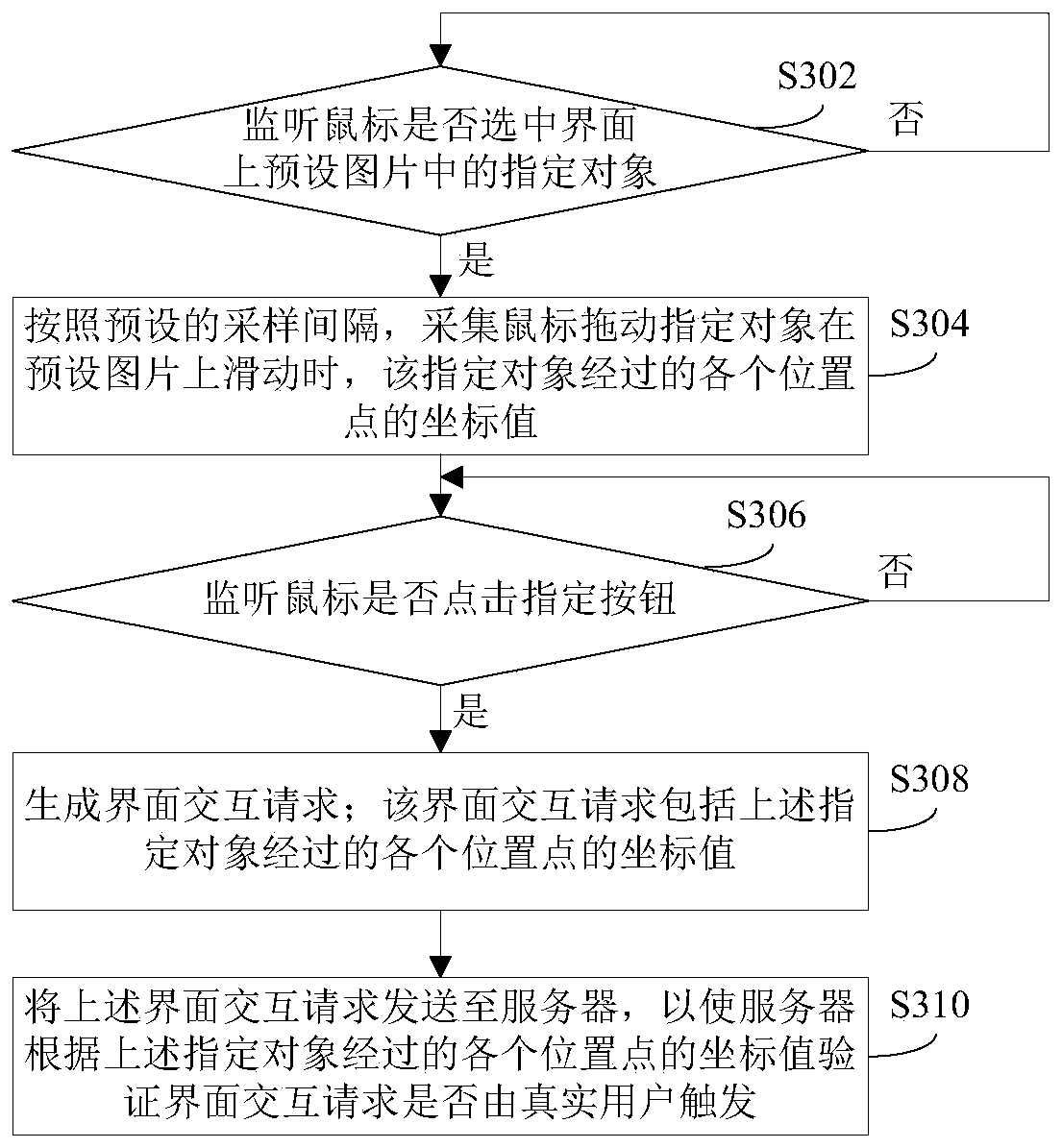
Interface interaction and verification method thereof, and login request generation and verification method and device
InactiveCN110138800AResist Aggressive BehaviorImprove authentication securityTransmissionInput/output processes for data processingValidation methodsHuman–computer interaction
The invention provides an interface interaction and verification method and device and a login request generation and verification method and device, and the method comprises the steps: monitoring whether a mouse selects a specified object in a preset picture on an interface or not; if the mouse drags the specified object, obtaining path information of the mouse dragging the specified object to slide on the preset picture; generating an interface interaction request based on the path information; and sending the interface interaction request to a server, so that the server verifies whether theinterface interaction request is triggered by a real user according to the path information. According to the method, whether the interface interaction request is triggered by a real user or not is verified based on the path information of the mouse dragging the appointed object to slide on the preset picture, the attack behavior of interface interaction by a machine simulator can be effectivelyresisted, and therefore the stability of the system is improved.
Owner:BEIJING KINGSOFT CLOUD NETWORK TECH CO LTD +1
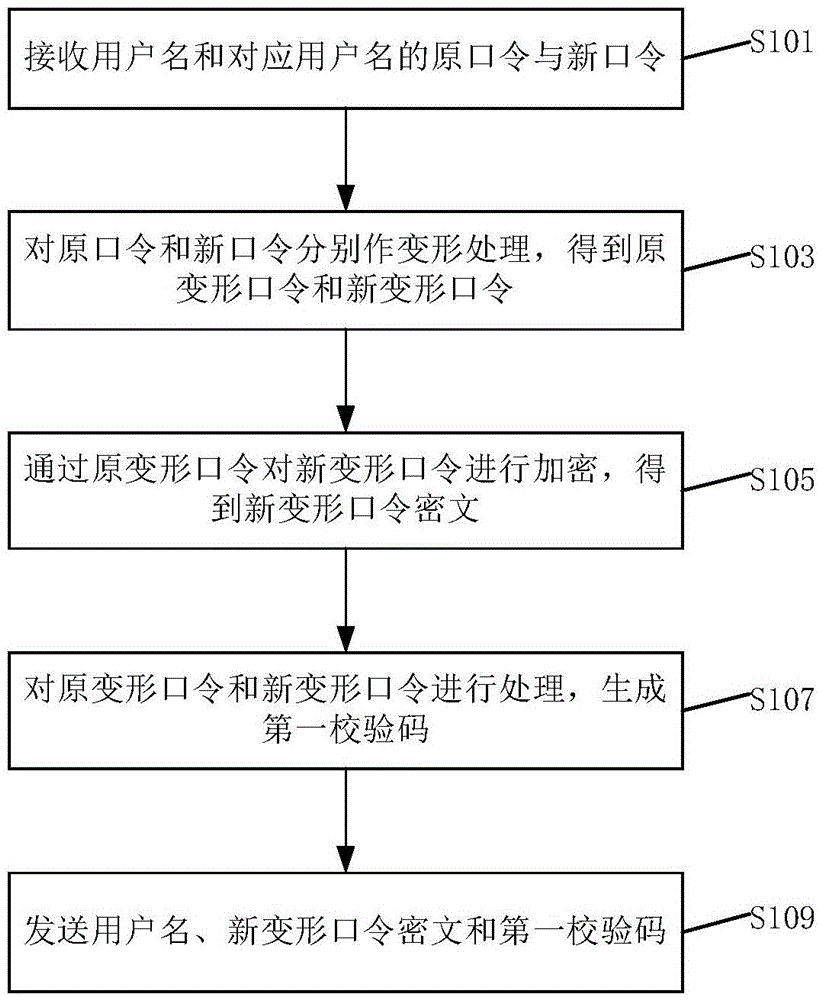
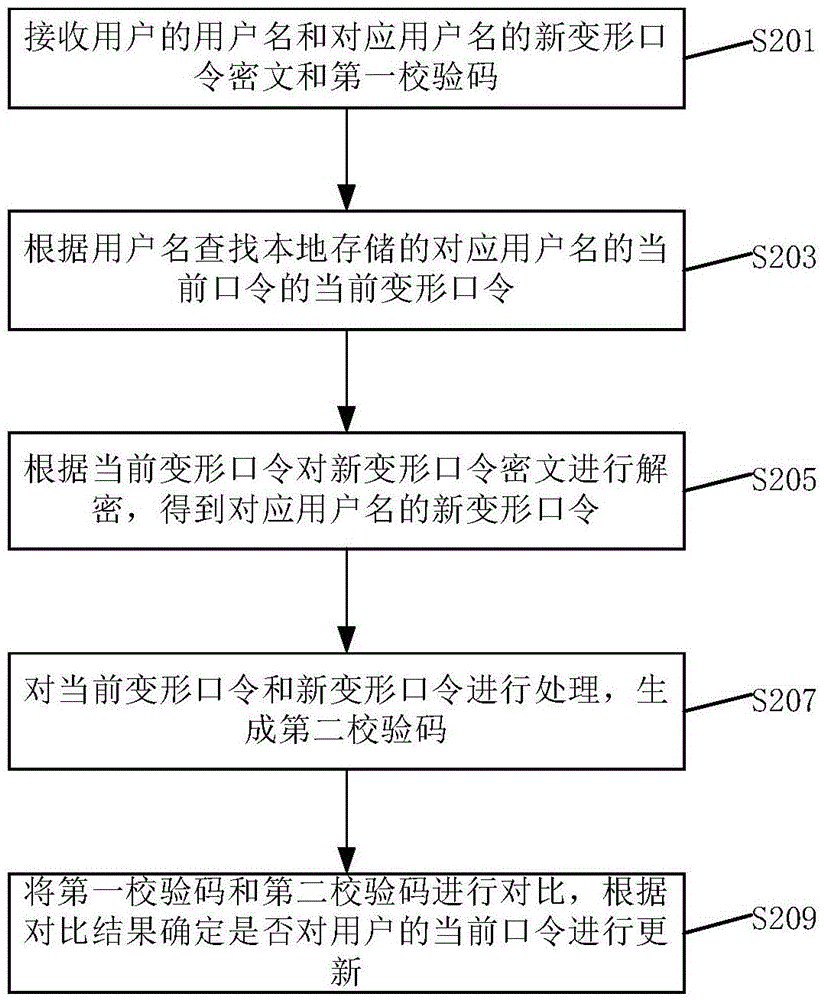
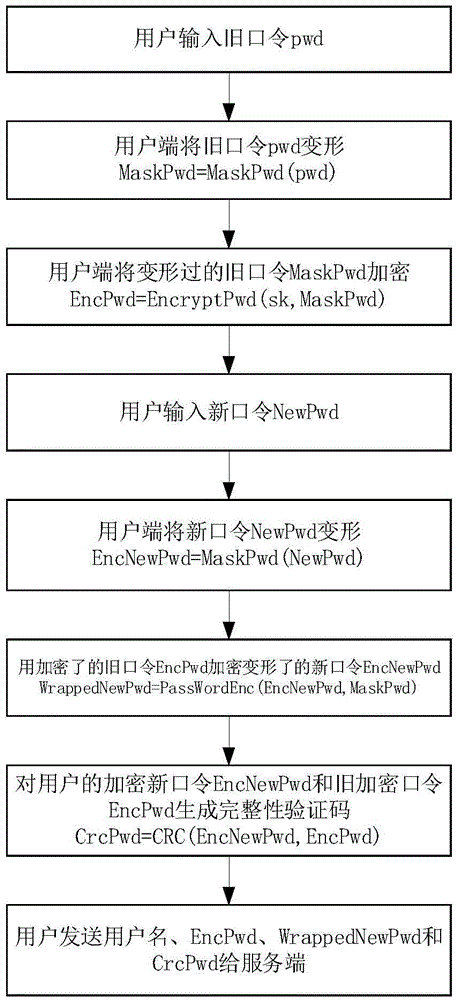
Password updating method
The invention discloses a password updating method and system. The method comprises: receiving a user name as well as an original password and a new password corresponding to the user name; separately modifying the original password and the new password to obtain an original modified password and a new modified password; encrypting the new modified password via the original modified password to obtain a new modified password ciphertext; processing the original modified password and the new modified password to generate a first check code; and sending the user name, the new modified password ciphertext and the first check code. According to the method, the new and old passwords are mutually associated for verification to prevent new and old password information from being divulged; the new password is protected by the old password, so that the risk caused by divulgence of the new password can be avoided, and the authentication security can be improved; meanwhile, the accuracy of the new password is ensured by adopting an additional verification code.
Owner:北京信安世纪科技股份有限公司
Method for realizing security key authentication of pure electric vehicle
ActiveCN110310397APrevent theftImprove authentication securityKey distribution for secure communicationAnti-theft devicesCiphertextKey authentication
The invention discloses a method for realizing the security key authentication of a pure electric vehicle. The method comprises the steps: waking up a smart key, feeding back a high-frequency key coordinate signal and a unique key ID of the smart key to a vehicle body controller; generating a first random number by the vehicle body controller and encrypting the Key ID, the first random number anda low-frequency wake-up signal by the vehicle body controller and the smart key based on an HITAG2 algorithm; completing authentication of the vehicle body controller and the smart key under the condition of consistence of the vehicle body controller and a ciphertext obtained by smart key encryption; generating a second random number Key and a third random number Key1 by the vehicle body controller and sending the second random number Key and the third random number Key1 to an overall vehicle controller; generating a fourth random number Key2 and a fifth random number Key3 by the overall vehicle controller and replying the fourth random number Key2 and the fifth random number Key3 to the vehicle body controller; and carrying out two-way authentication by the vehicle body controller and theoverall vehicle controller by using the second random number Key, the third random number Key1, the fourth random number Key2, the fifth random number Key3, and a conventional number A to realize starting of a pure electric vehicle.
Owner:浙江新吉奥汽车有限公司
Mass Internet of Things equipment authentication method, storage medium and information data processing terminal
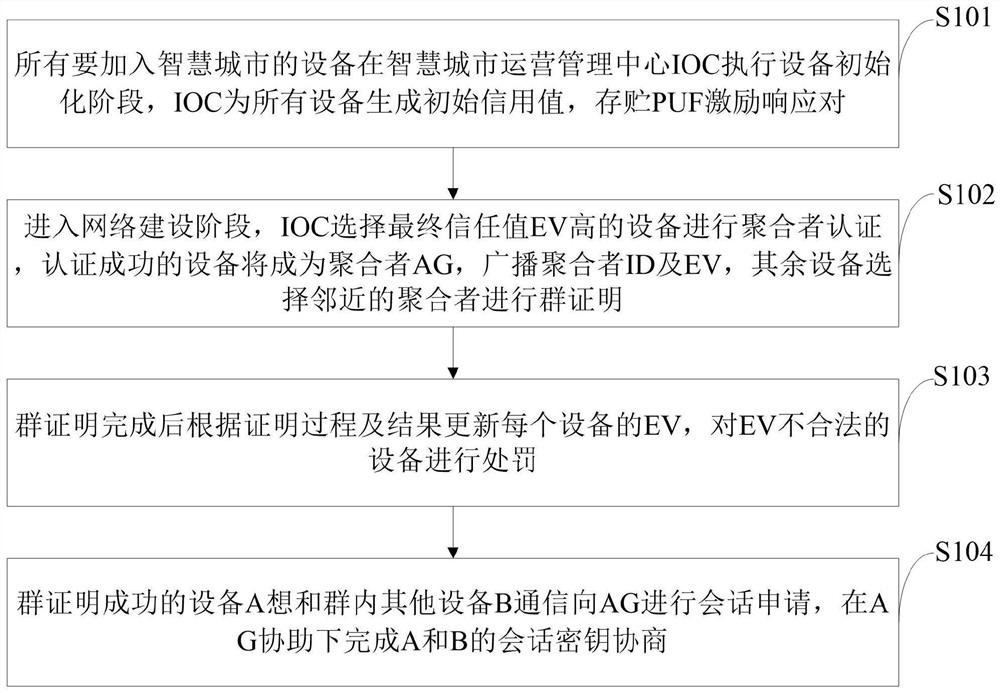
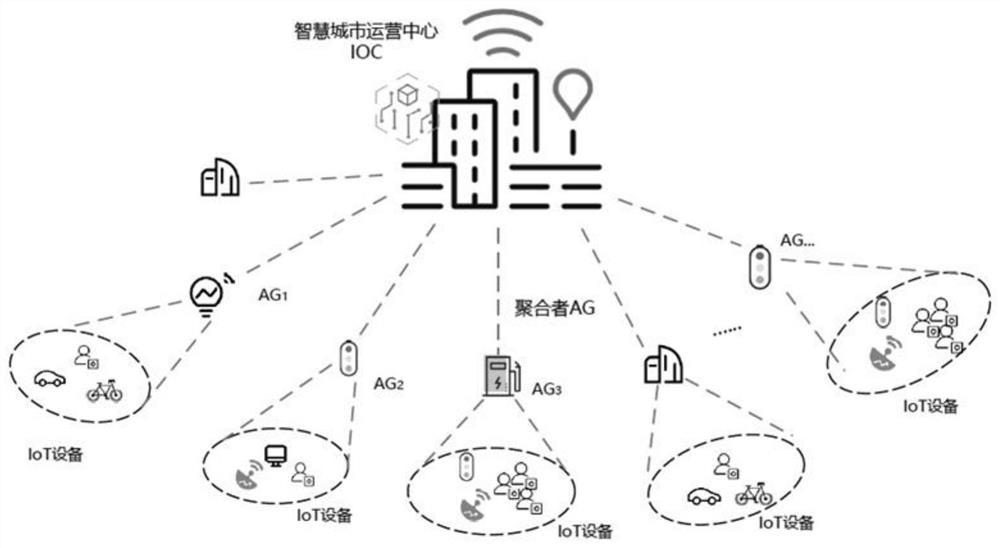
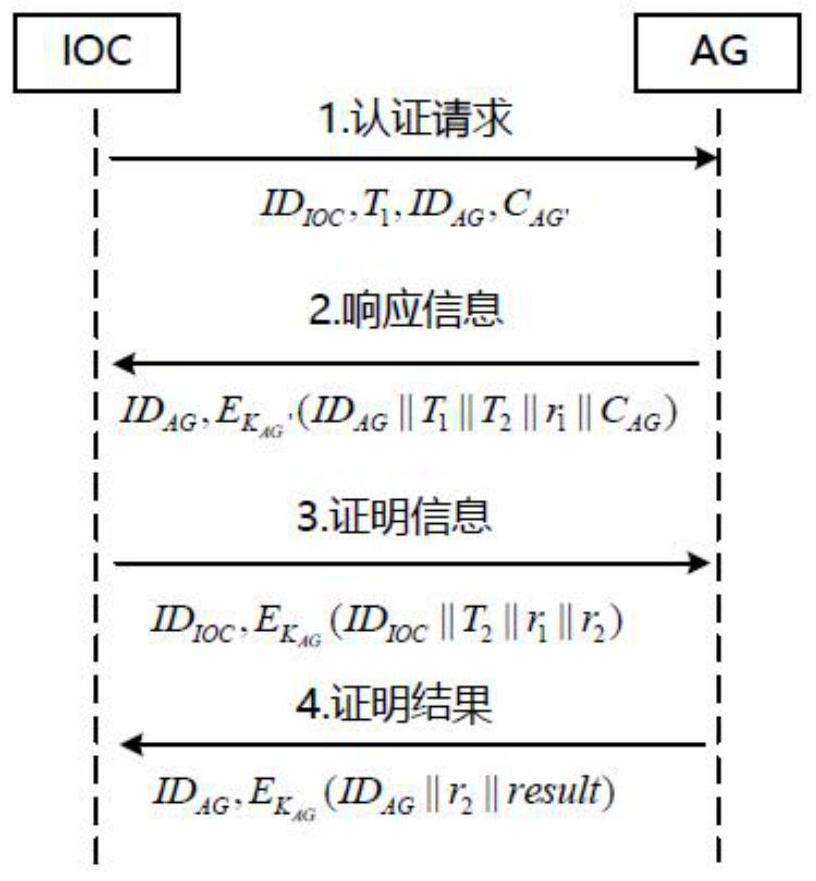
ActiveCN113079132ARemotely proven reliable and efficientEnsure safetyKey distribution for secure communicationUser identity/authority verificationEngineeringSmart city
The invention belongs to the technical field of Internet of Things security, and discloses a massive Internet of Things equipment authentication method, a storage medium and an information data processing terminal. The massive Internet of Things equipment authentication method comprises the steps: IOT equipment interacts with a smart city operation center IOC, and equipment initialization is completed through a secure channel; the equipment initialization stage is completed, and an aggregator AG is selected through the IOC to perform aggregator authentication; after the aggregator authentication is completed, the IOT equipment completes group authentication under the assistance of the AG; and after the group authentication is completed, the intra-group equipment completes session key negotiation under the assistance of the AG. According to the method, the equipment with the high trust value is selected as an aggregator to assist the IOC to carry out group certification on other equipment, so that remote certification of massive IOT equipment is more reliable and efficient. Meanwhile, a reputation mechanism is used for supervising the trust value of the equipment, and the situation that the whole system network is affected due to the fact that the successfully authenticated equipment is dealt with by an attacker is prevented.
Owner:XIDIAN UNIV
Financial terminal authentication method and device
ActiveCN106022037AAvoid Privacy LeakagePrevent theftDigital data authenticationProtocol authorisationHash functionPassword
The invention provides a financial terminal authentication method and a financial terminal authentication device. Authentication information is generated in combination with a bank card number, biological characteristics and a conventional password, specifically, the authentication information is generated in combination with three parameters including the bank card number, the biological characteristics and the conventional password of a user by using a one-way hash function through an operation; the authentication information stored in a bank system server is neither the password and the biological information of the user nor the information of the encrypted password and the encrypted biological information; if any of the three parameters is different, the entirely different authentication information is generated; and the generated authentication information cannot be falsified and cannot be obtained through a password cracking method. According to the financial terminal authentication method and the financial terminal authentication device, the safety problem that the authentication information is stolen and cracked can be prevented, and the final authentication information generated by the same original authentication information such as the same password and the same biological information in a bank system are completely different, and thus the method is high in authentication safety.
Owner:HUNAN UNIV OF FINANCE & ECONOMICS
Wireless verification system and method
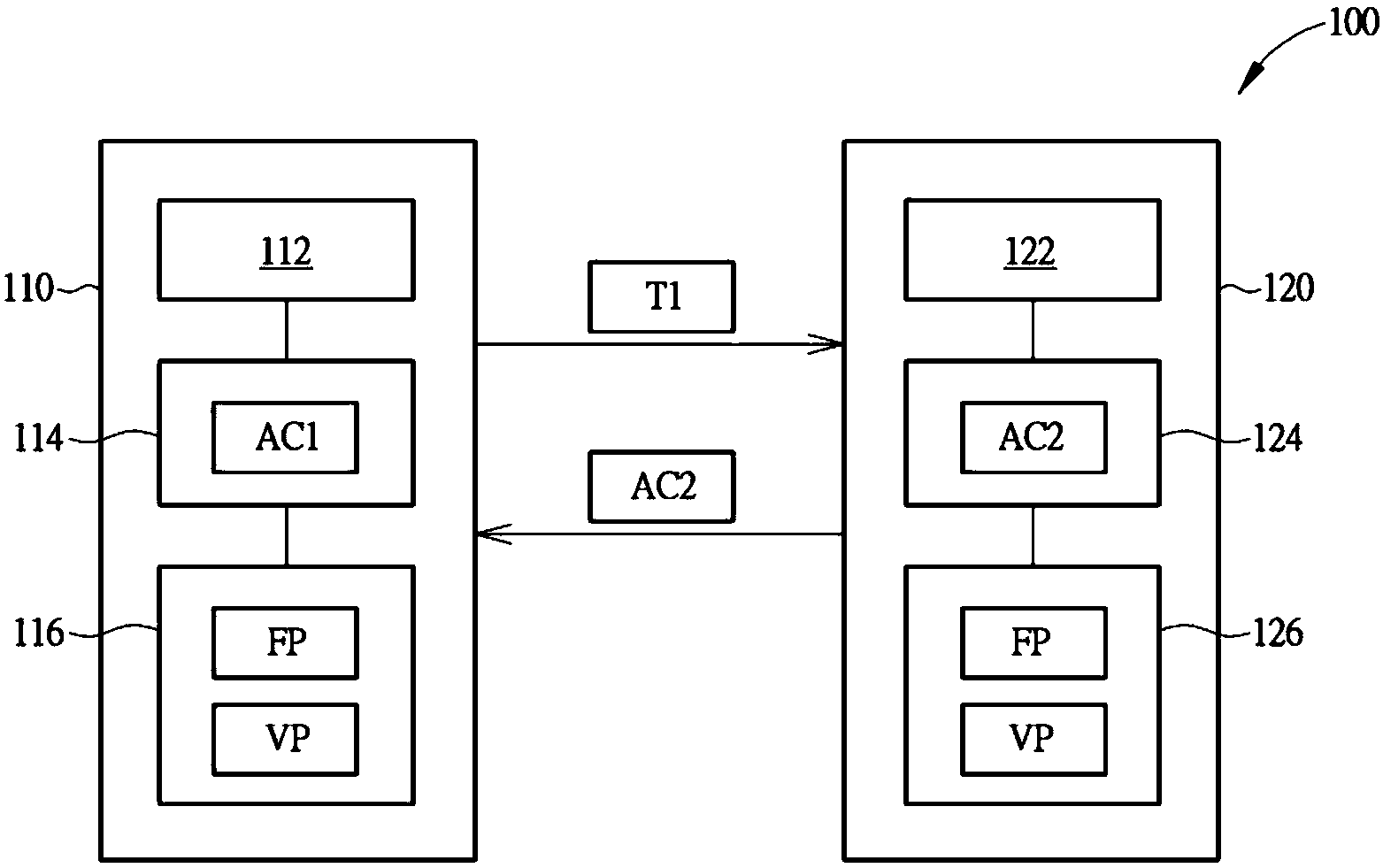
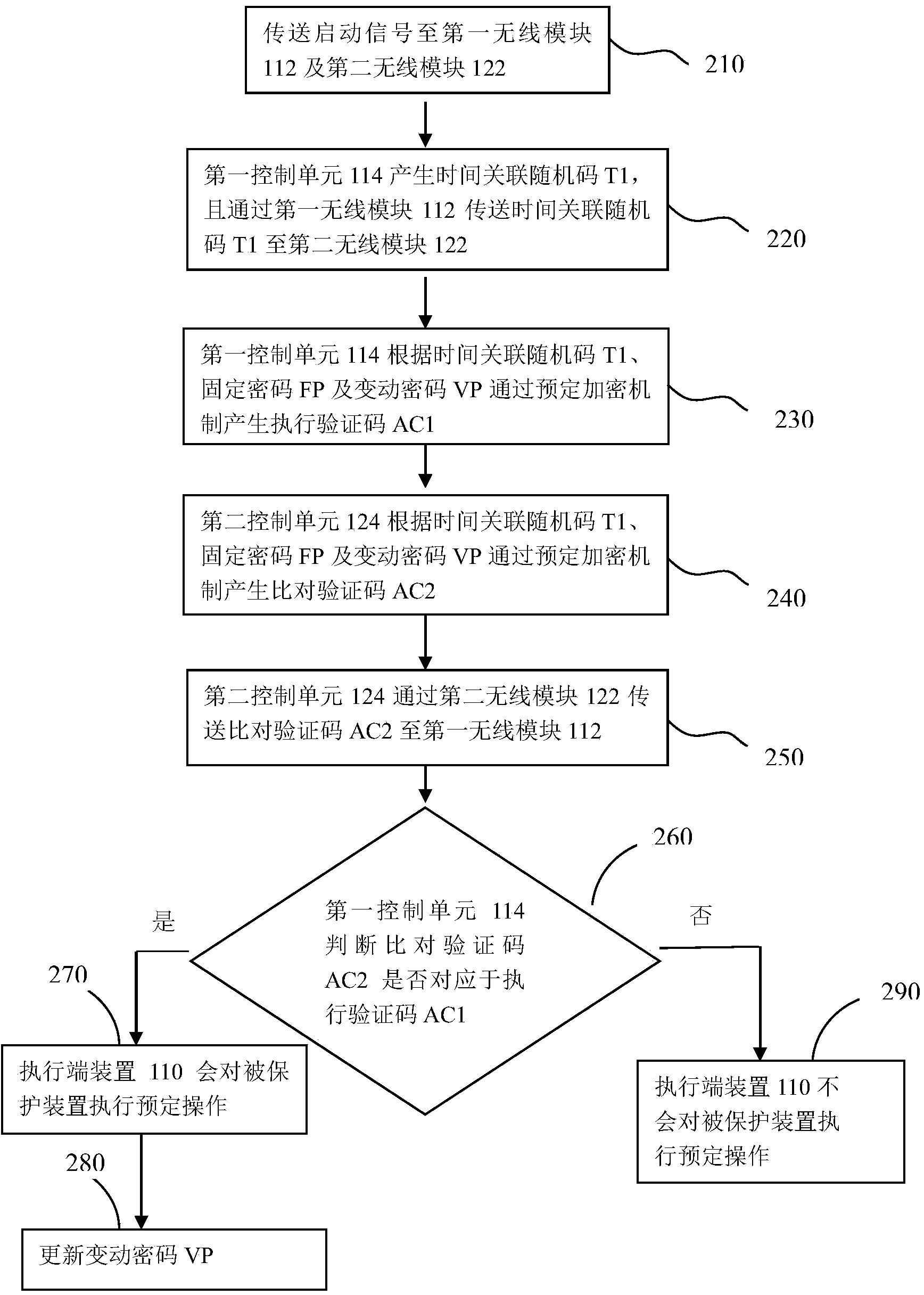
InactiveCN104283689AImprove authentication securityUser identity/authority verificationSecurity arrangementTime correlationPassword
A wireless verification system comprises an execution terminal device and a control terminal device. When the execution terminal device and the control terminal device receive a start signal, the execution terminal device produces a time correlation random code, and the execution terminal device transmits the time correlation random code to the control terminal device; the control terminal device produces a comparison verification code according to the time correlation random code, a fixed password and a variable password. When the execution terminal device judges that the comparison verification code corresponds to a set of data stored in the execution terminal, the execution terminal executes a predetermined operation, and meanwhile the variable password is updated.
Owner:USERSTAR INFORMATION SYST
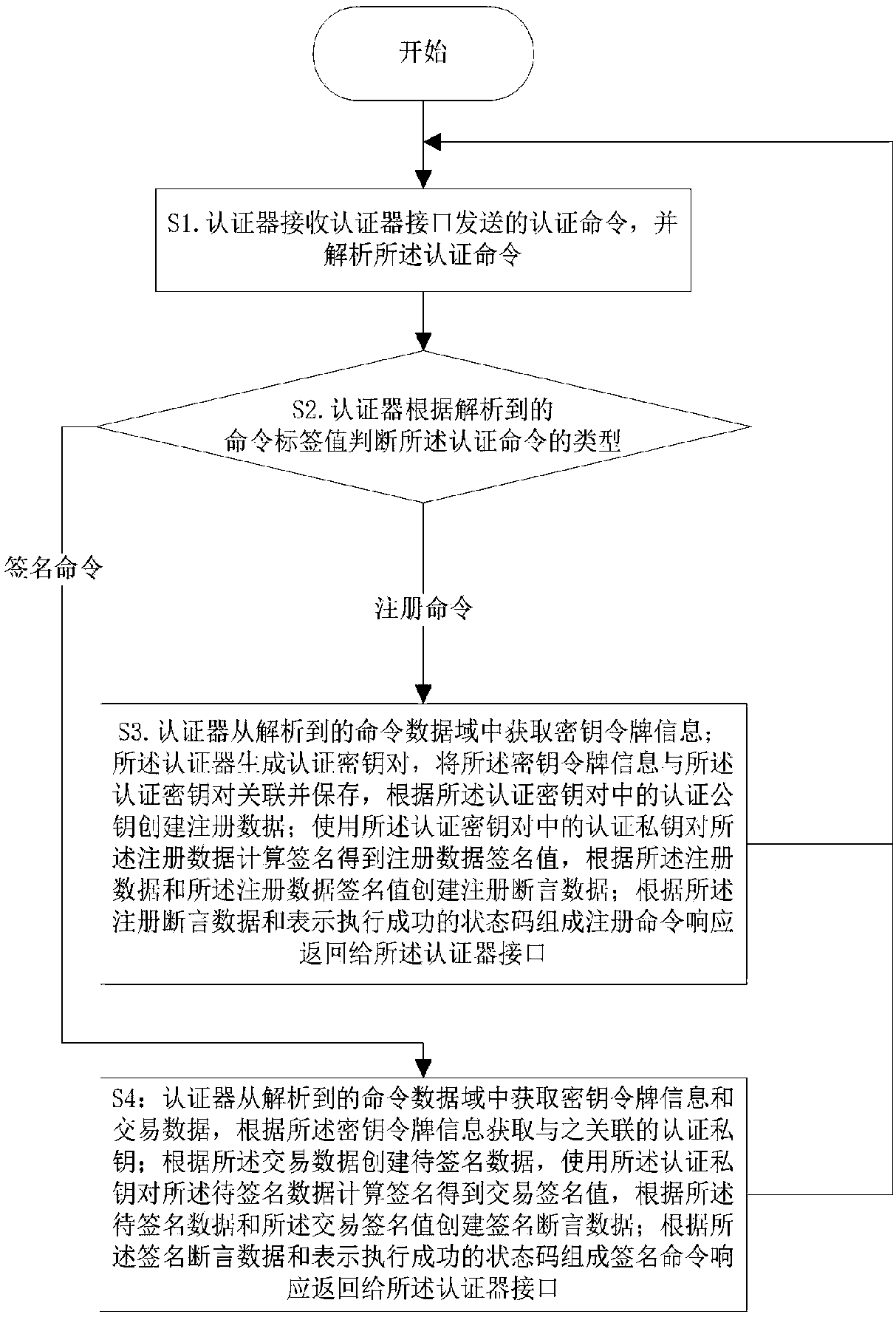
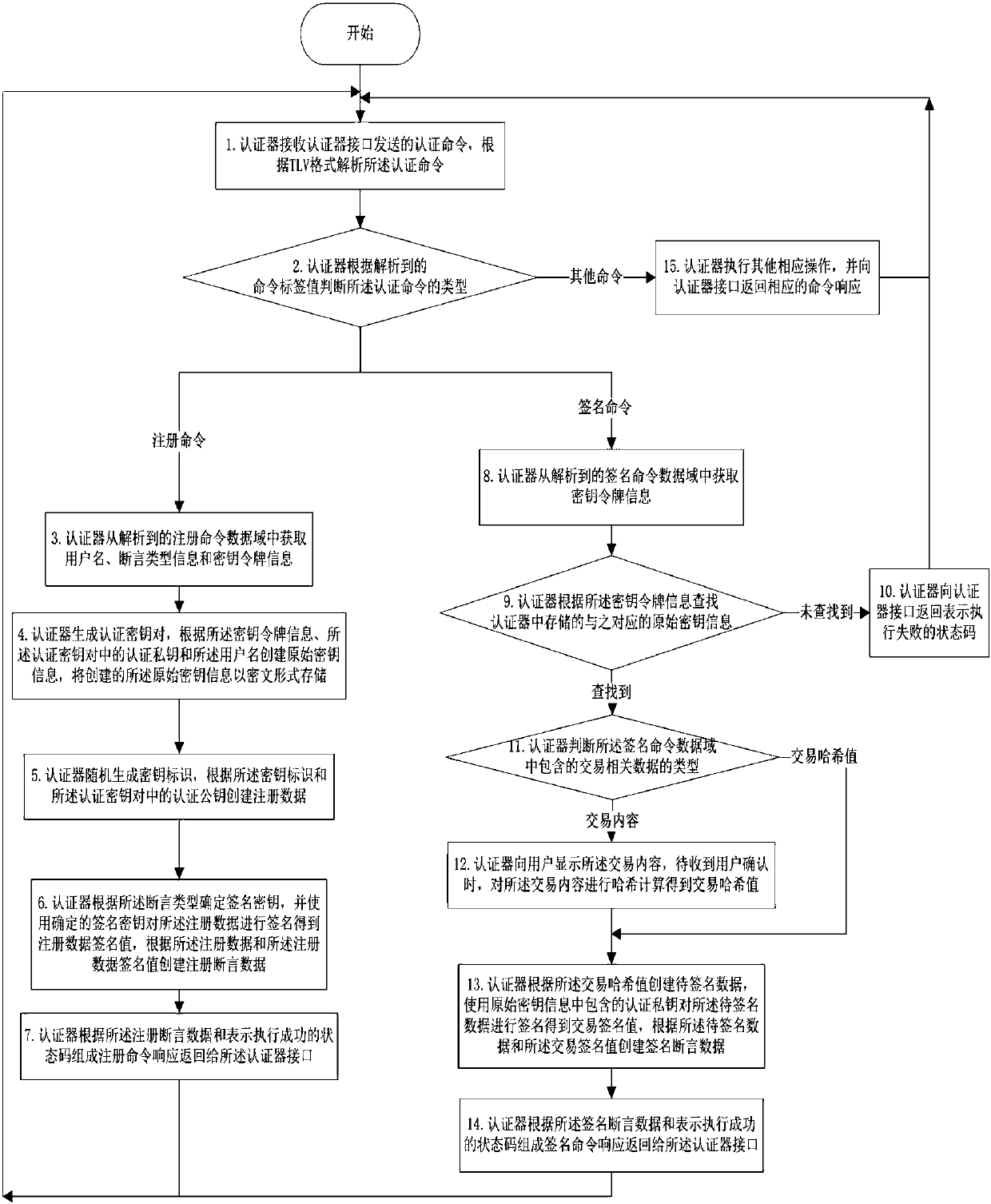
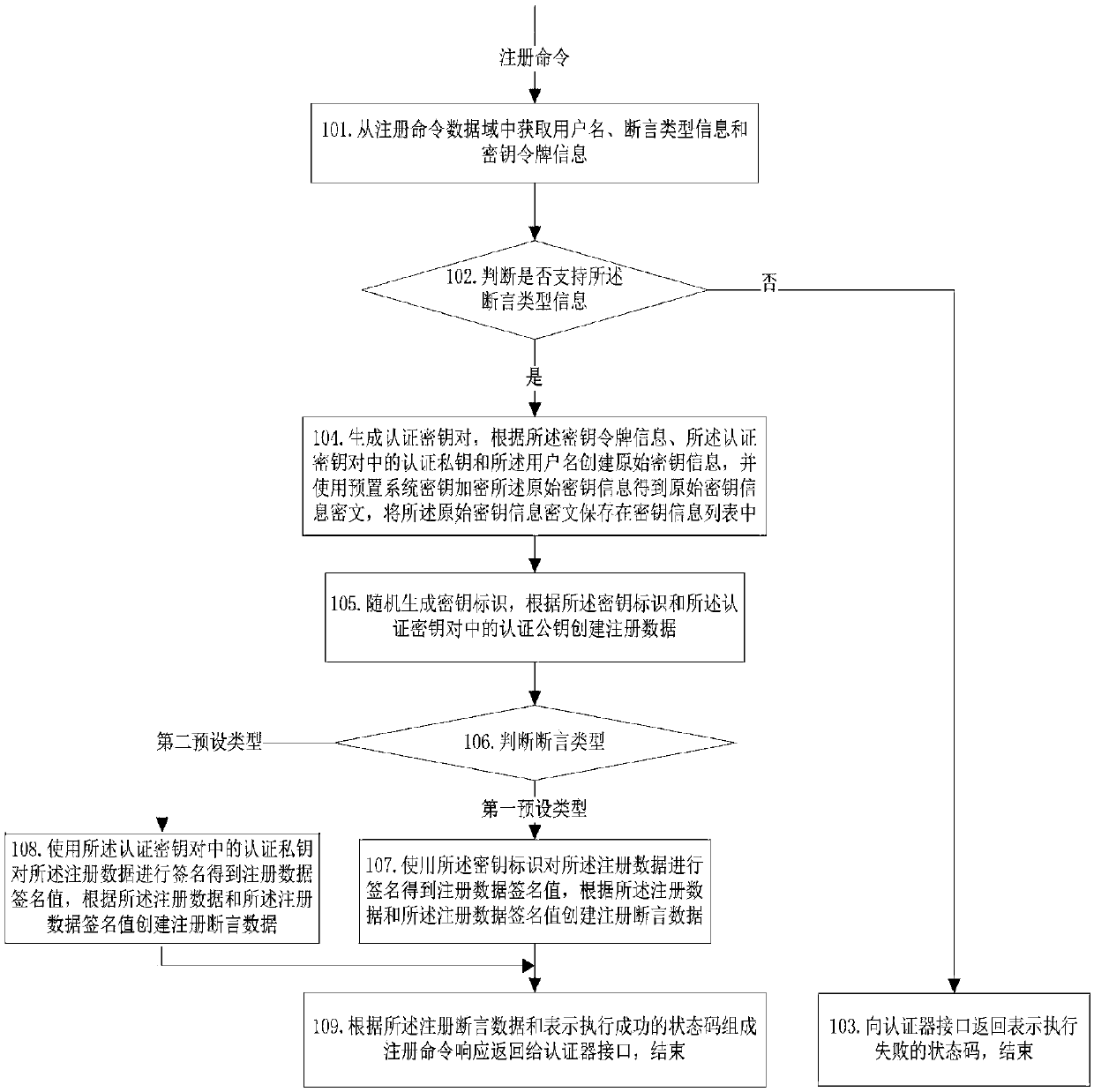
Authenticator and realization method thereof
ActiveCN107919963APrevent leakageImprove authentication securityKey distribution for secure communicationUser identity/authority verificationTransaction dataCommand response
The invention discloses an authenticator and a realization method thereof and belongs to the technical field of identity authentication. When the authenticator receives a registration command, the authenticator generates an authentication key pair, correlates and stores the authentication key pair and key token information contained in the registration command. The authenticator establishes registration assertion data according to the authentication key pair, forms registration command response according to the registration assertion data and a state code expressing performance success and returns the registration command response to an authenticator interface. When the authenticator receives a signing command, the authenticator obtains an authentication private key according to the key token information contained in the signing command, establishes signing assertion data according to transaction data contained in the signing command and the authentication private key, forms signing command response according to the signing assertion data and the state code expressing the performance success and returns the signing command response to the authenticator interface; and the authenticator interacts with a background server through the authenticator interface. The authentication private key does not appear in network transmission of an interaction process and does not need to be pre-stored at the background server, so the authentication information can be effectively prevented from being leaked.
Owner:FEITIAN TECHNOLOGIES
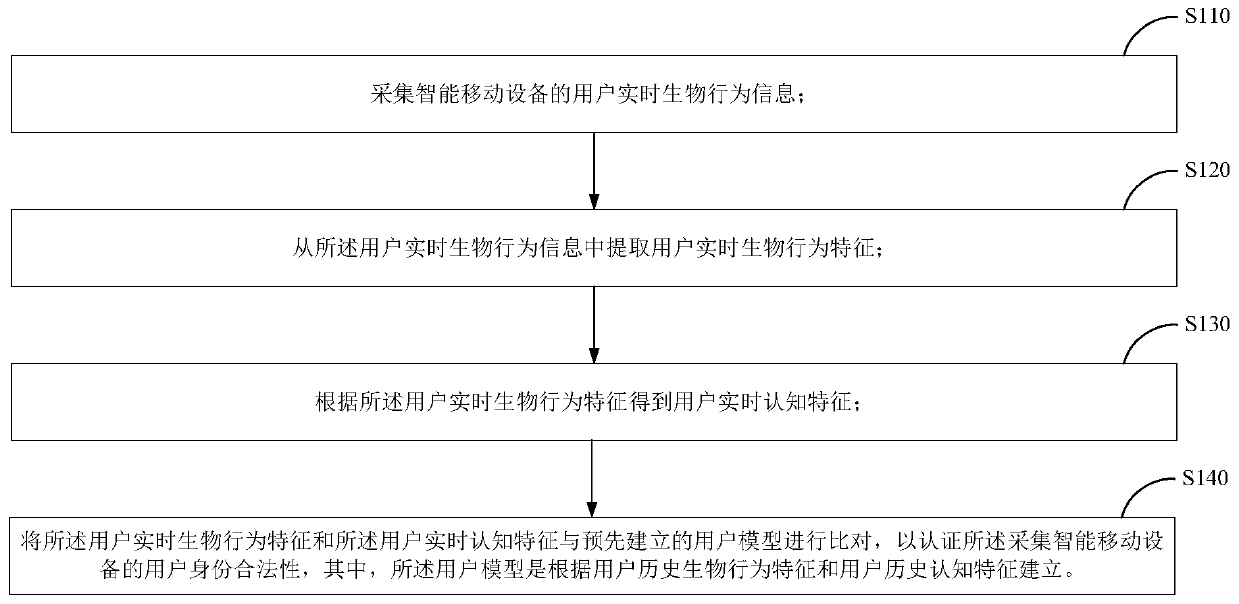
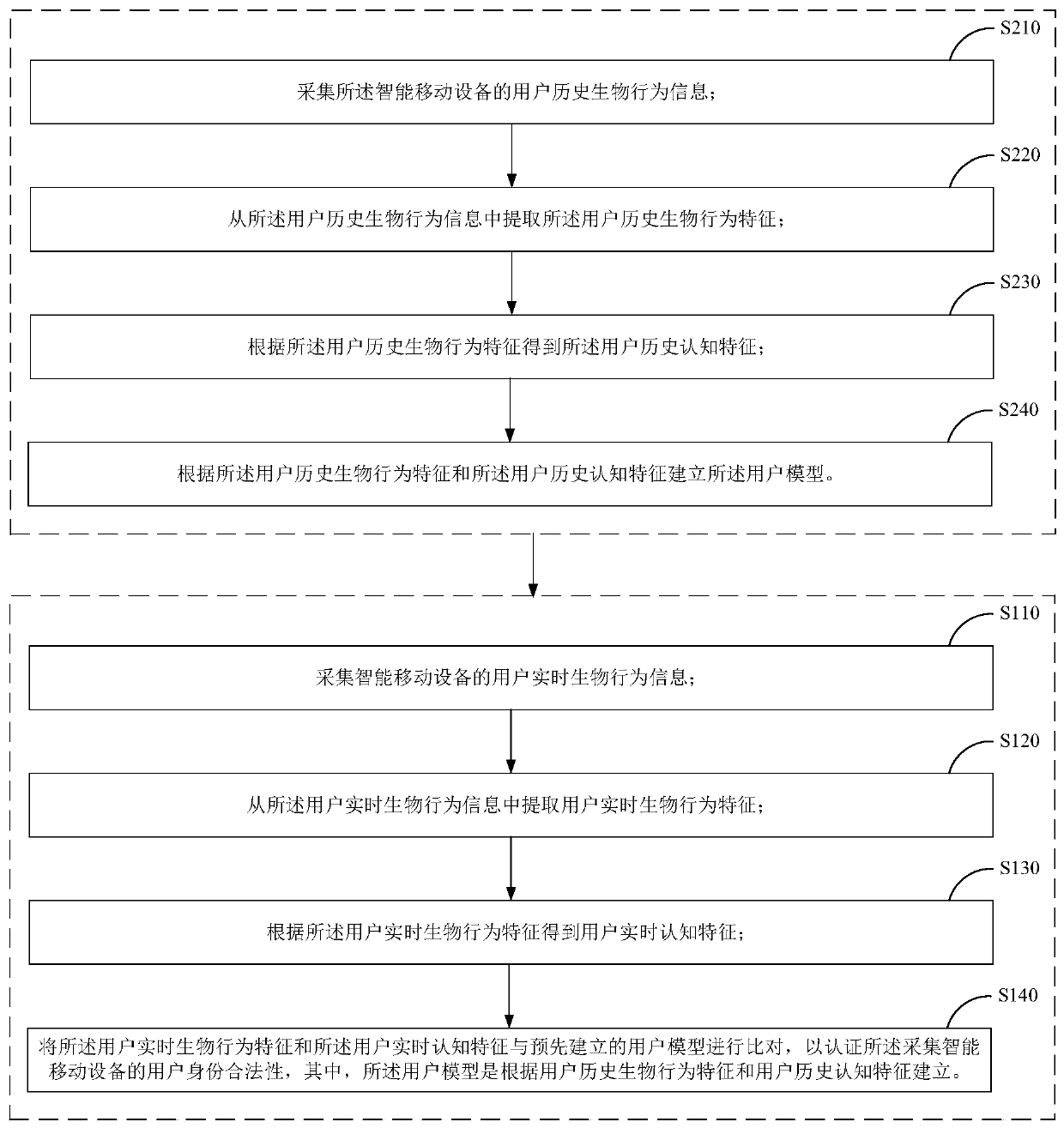
Identity authentication method and device
ActiveCN110418337AImprove accuracyImprove authentication securitySecurity arrangementMobile deviceComputer science
The invention provides an identity authentication method and device, and the method comprises the steps: collecting the real-time biological behavior information of a user of intelligent mobile equipment; extracting user real-time biological behavior characteristics from the user real-time biological behavior information; obtaining user real-time cognitive features according to the user real-timebiological behavior features; and comparing the user real-time biological behavior characteristics and the user real-time cognitive characteristics with a pre-established user model to authenticate the legality of the user identity of the collected intelligent mobile device, and establishing the user model according to user historical biological behavior characteristics and user historical cognitive characteristics. Through the scheme, the accuracy based on identity authentication can be improved.
Owner:BEIJING UNIV OF POSTS & TELECOMM
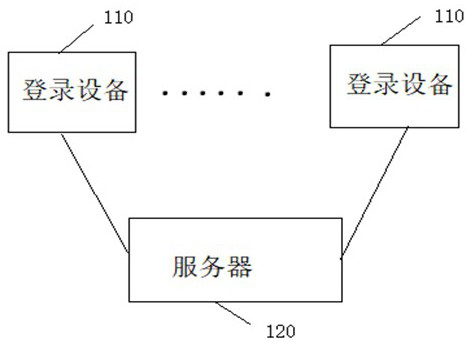
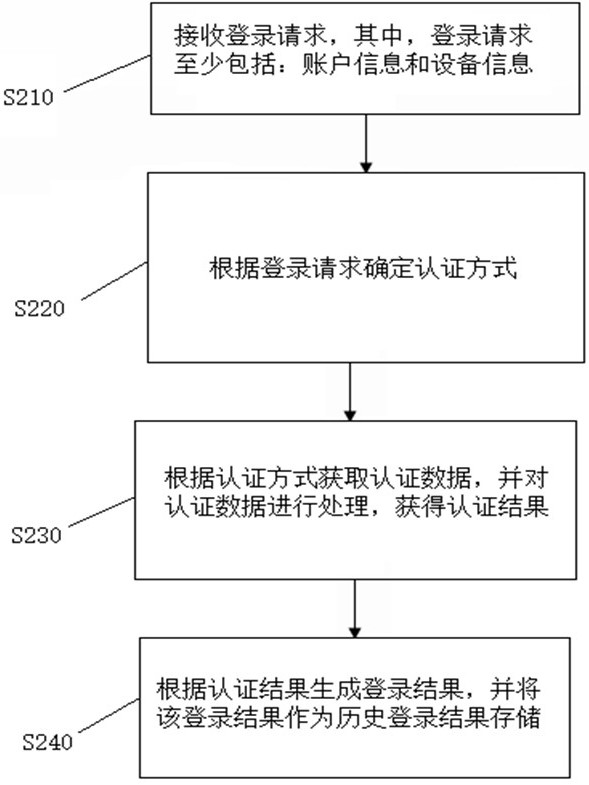
Authentication risk detection method and system
ActiveCN112464200AImprove authentication securityDigital data protectionDigital data authenticationInternet privacyEngineering
The invention discloses an authentication risk detection method and system, and the system comprises at least one piece of login equipment and a server. The at least one piece of login equipment is used for sending a login request, acquiring and receiving an authentication data acquisition instruction and sending authentication data to the server; the server is used for executing the following steps that a login request is received, and the login request at least comprises account information and equipment information; determining an authentication mode according to the login request; obtaining authentication data according to the authentication mode, and processing the authentication data to obtain an authentication result; and generating a login result according to the authentication result, and storing the login result as a historical login result. The invention has the technical effects that the authentication risk is dynamically identified, and further management and control measures are realized according to the authentication risk, so that the authentication security is improved.
Owner:北京安泰伟奥信息技术有限公司
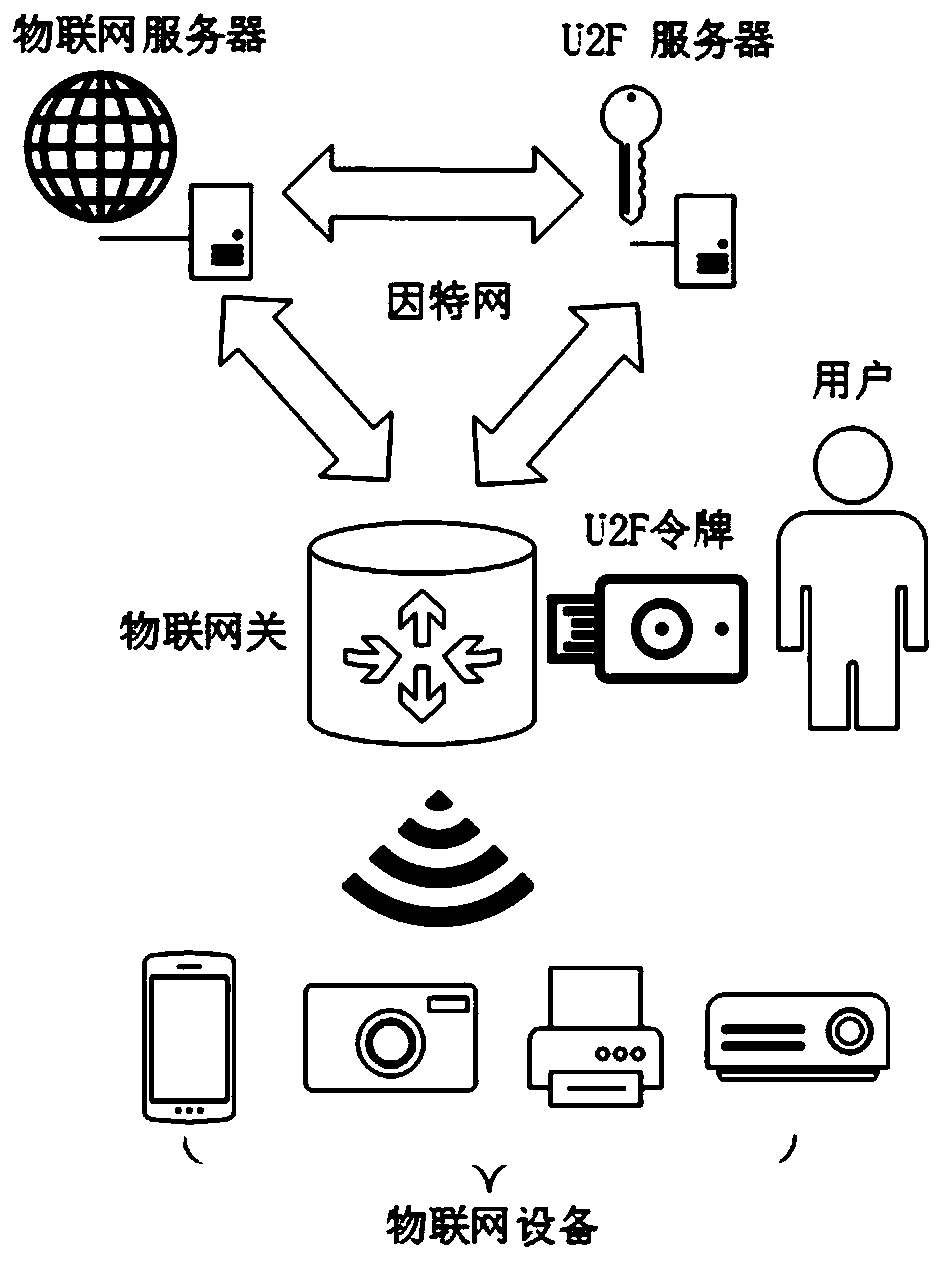
Centralized authentication system of Internet of Things equipment based on U2F physical token
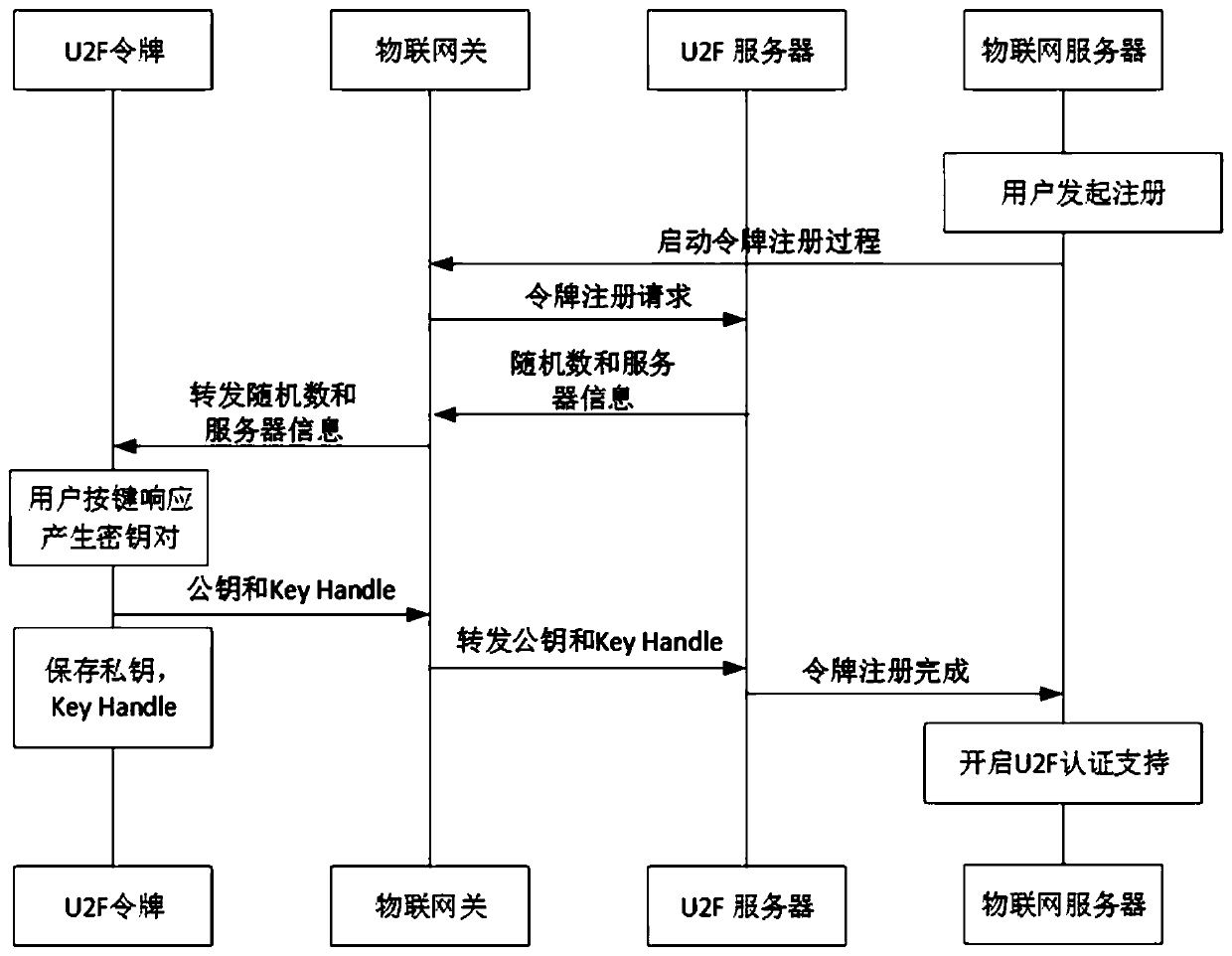
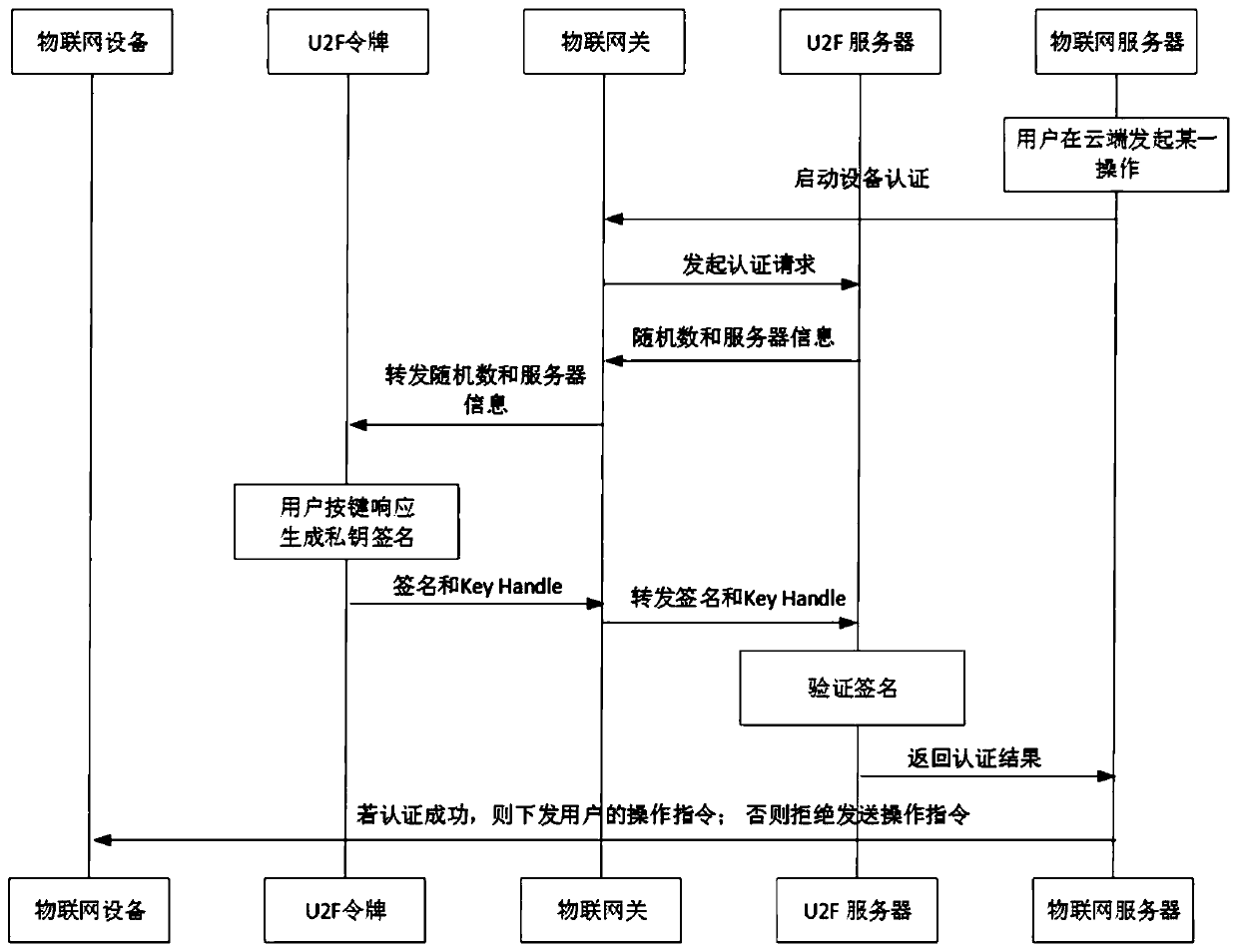
ActiveCN111585771ASimple and efficient operationReduce hardware costsKey distribution for secure communicationUser identity/authority verificationAuthentication systemInternet privacy
The invention discloses a centralized authentication system for Internet of Things equipment based on a physical token, and the system enables the authentication of the Internet of Things equipment onan end to be transferred to centralized authentication on an Internet of Things gateway, a user can respond to the Internet of Things gateway through a U2F token, and completes the authentication ofthe Internet of Things equipment. According to the system, an authenticated core is transferred from a plurality of scattered single Internet of Things terminals to a credible Internet of Things node;while the safety of the Internet of Things environment is enhanced, the defects of numerous Internet of Things devices, limited terminal resources, large authentication overhead, complex operation and the like are overcome, the safety of Internet of Things environment authentication is enhanced, and the efficiency of device authentication and management is improved.
Owner:ZHEJIANG UNIV
Method, device, server and system for improving user identity authentication safety
InactiveCN110704822AImprove authentication securityImprove securitySpeech analysisDigital data authenticationUser verificationInternet privacy
The invention relates to the field of identity authentication. The invention discloses a method, a device, a server and a system for improving user identity authentication safety. The method comprisesthe steps of sending verification information and prompt information to a terminal, wherein the prompt information is used for prompting a user to read the verification information according to corresponding requirements and then obtaining voice data, the voice data is collected by the terminal, voice features of the voice data are recognized to obtain voice features of the voice data, and finally an identity verification result is generated according to the voice features of the voice data and preset voice information. According to the method, the user must read the related verification information according to the requirement of the prompt information, and the voice characteristics of the generated voice data must be matched with the preset voice information, so that the user passes theverification, and therefore, the method can improve the safety of the user verification.
Owner:VOICEAI TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com