Fingerprint sequential composition password authentification system
A combined password and fingerprint verification technology, which is applied in the field of fingerprint sequence combined password verification system, can solve the problems of not being able to fully guarantee the security of capital accounts, spying on transaction passwords, monitoring and stealing by Trojan horse programs on the Internet, and unable to guarantee verification security. Improve the effect of verification security, guarantee the effect of account and property security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
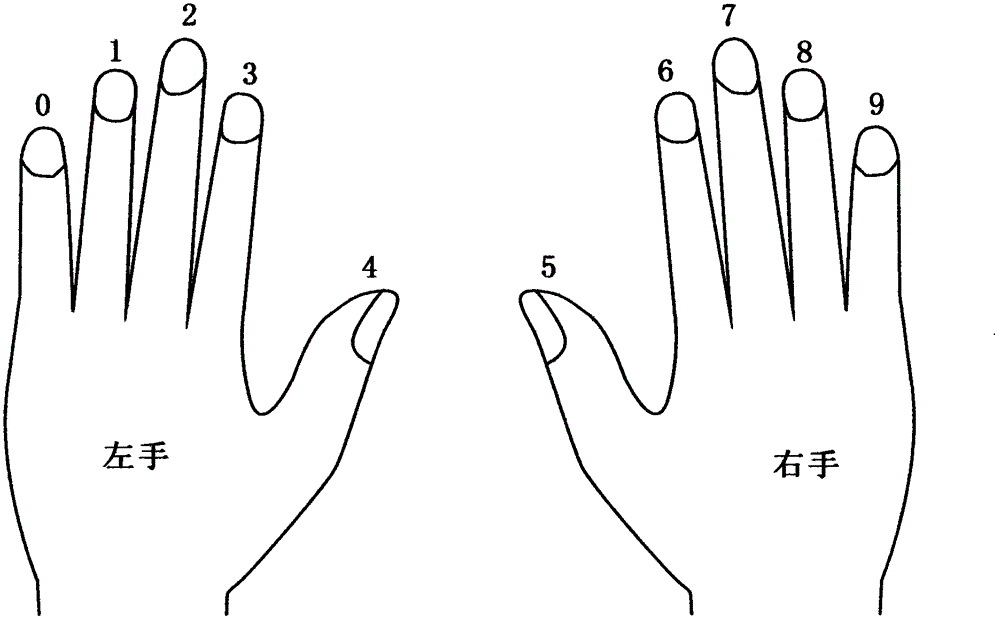
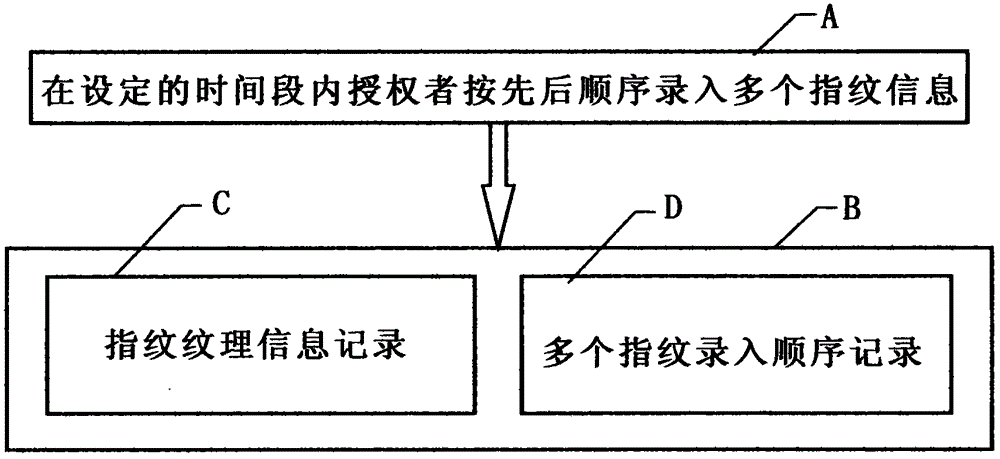
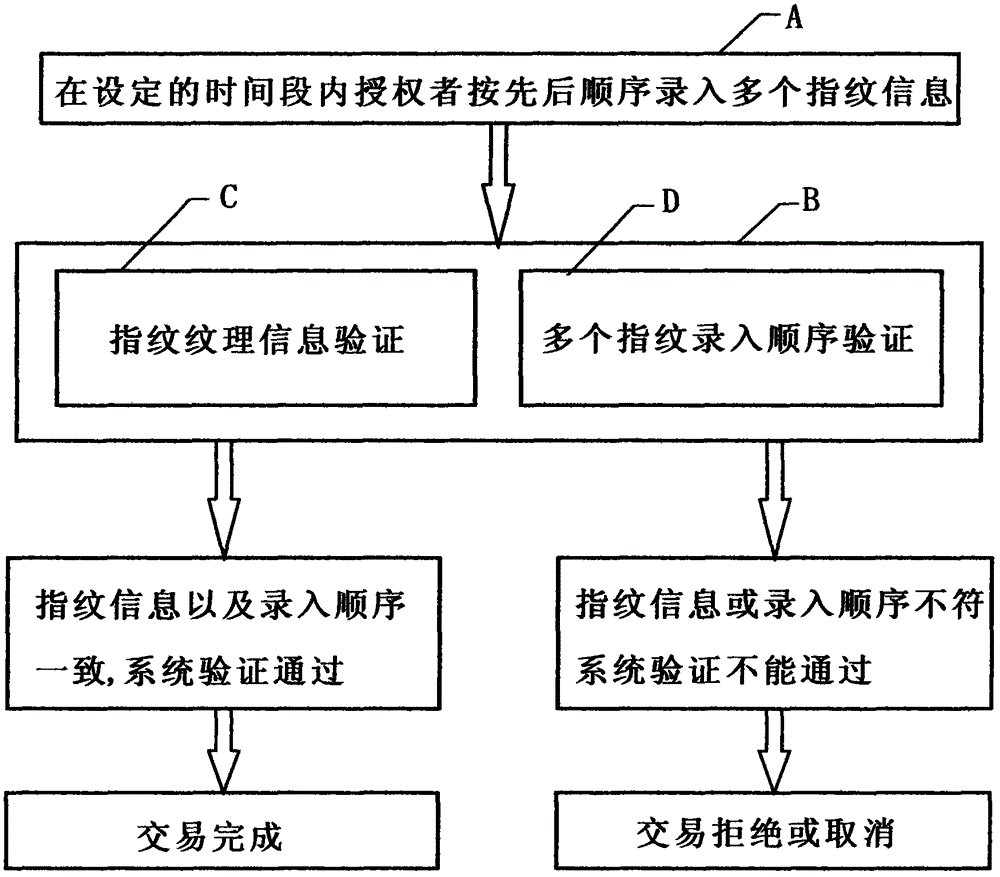
[0011] figure 1 In order to facilitate the example description, in this embodiment, the ten fingers of the authorizer are numbered from 0 to 9 respectively, figure 2 In the process, the authorizer enters the terminal A through the fingerprint at the bank counter or the bank self-service terminal, and within the set time, such as 100 seconds, presses and enters the fingerprints of his own 3 fingers, No. 8, No. 6, No. 2, according to the order of the finger number 862268. For fingerprint information, the fingerprint verification system B respectively records multiple fingerprint texture information entered by the authorizer and the sequence of each fingerprint information is 862268. image 3 Among them, when the authorizer conducts a transaction, the authorizer needs to input the fingerprint information of the terminal A through the fingerprint, and enter the fingerprint information of his own 3 fingers, No. 8, No. 6, No. 2, according to the pre-set sequence 862268 within the s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com