Authenticator and realization method thereof
An implementation method and an authenticator technology, which are applied in user identity/authority verification and key distribution, can solve the problems of authentication information leakage and insecure authentication data transmission, and achieve the effect of preventing leakage and enhancing authentication security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
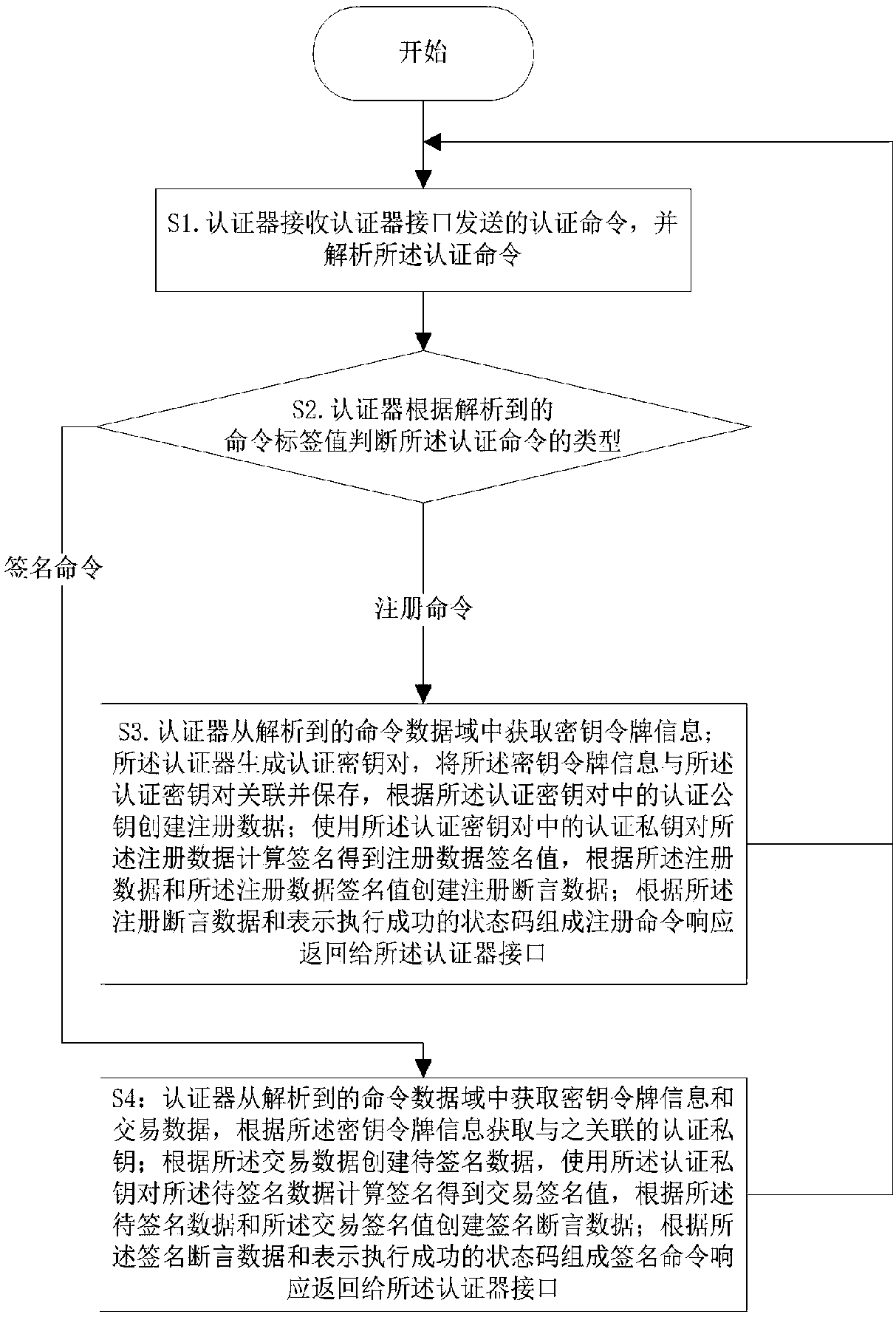
[0045] like figure 1 As shown, an implementation method of an authenticator provided in this embodiment includes the following steps:
[0046] Step S1: the authenticator receives the authentication command sent by the authenticator interface, and parses the authentication command;
[0047] Specifically, the authenticator parses the authentication command according to the TLV format, where T is the command tag value, L is the data length in the command data field, and V is the data in the command data field.
[0048] Step S2: The authenticator judges the type of the authentication command according to the parsed command tag value, if it is a registration command, execute step S3, and if it is a signature command, execute step S4;
[0049] Specifically, if the parsed command tag value is equal to 0x3402, the authentication command is a registration command, and if the parsed command tag value is equal to 0x3403, the authentication command is a signature command.
[0050] Step ...
Embodiment 2
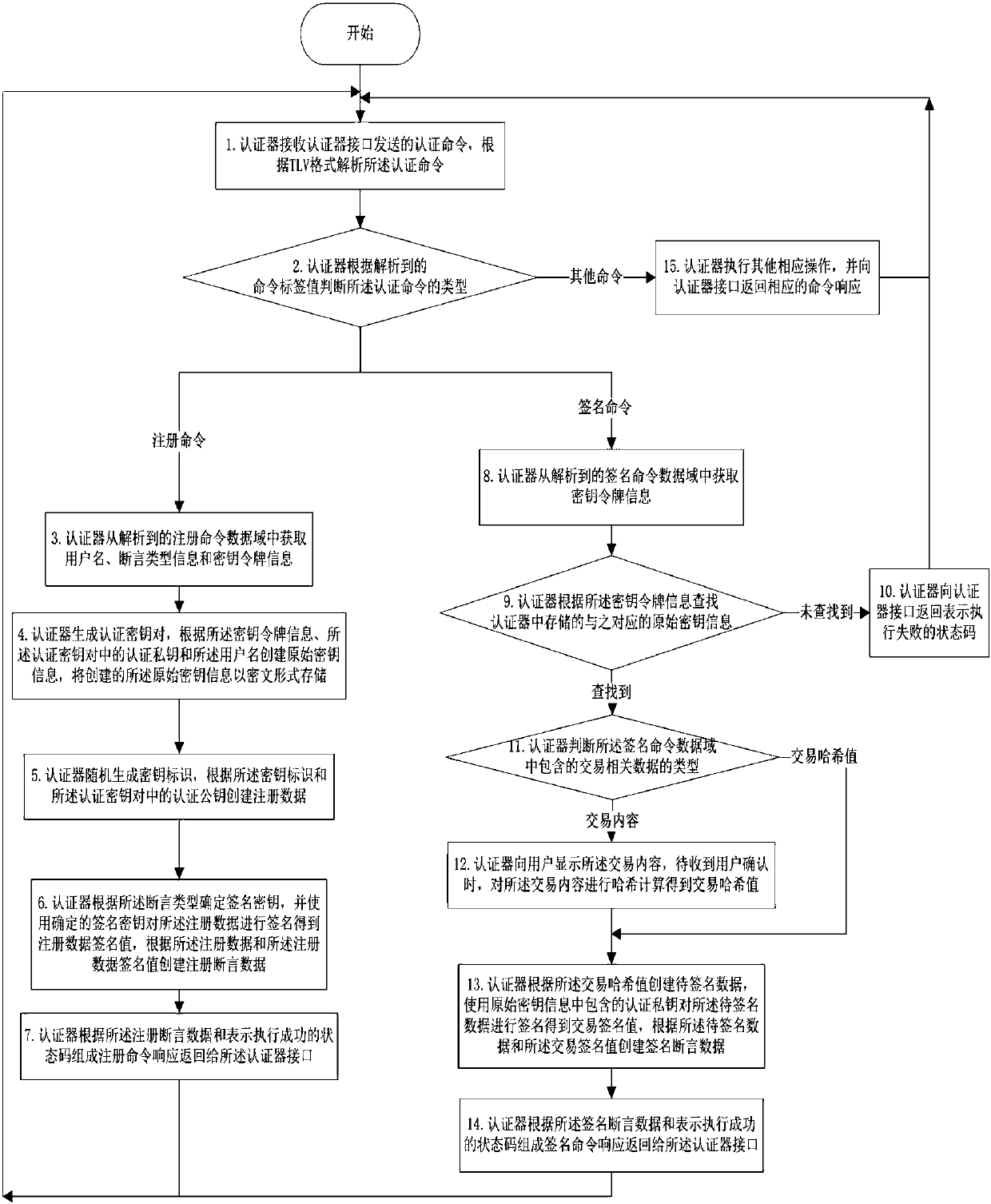
[0057] like figure 2 As shown, an implementation method of an authenticator provided in this embodiment includes the following content:
[0058] Step 1: The authenticator receives the authentication command sent by the authenticator interface, and parses the authentication command according to the TLV format;
[0059] Specifically, the authentication command adopts the TLV format, and the data field of the command (that is, V in the TLV) is also in the TLV format.
[0060] Preferably, this step also includes, when the authenticator receives the authentication command, parsing the authentication command according to the TLV format, and further judging whether the authentication command has passed the biometric verification when the format of the authenticated command is correct, and if so, execute the next step, otherwise it needs to The biometric verification is completed first; when the format of the authenticated command is incorrect, an error status code is returned to th...
Embodiment 3
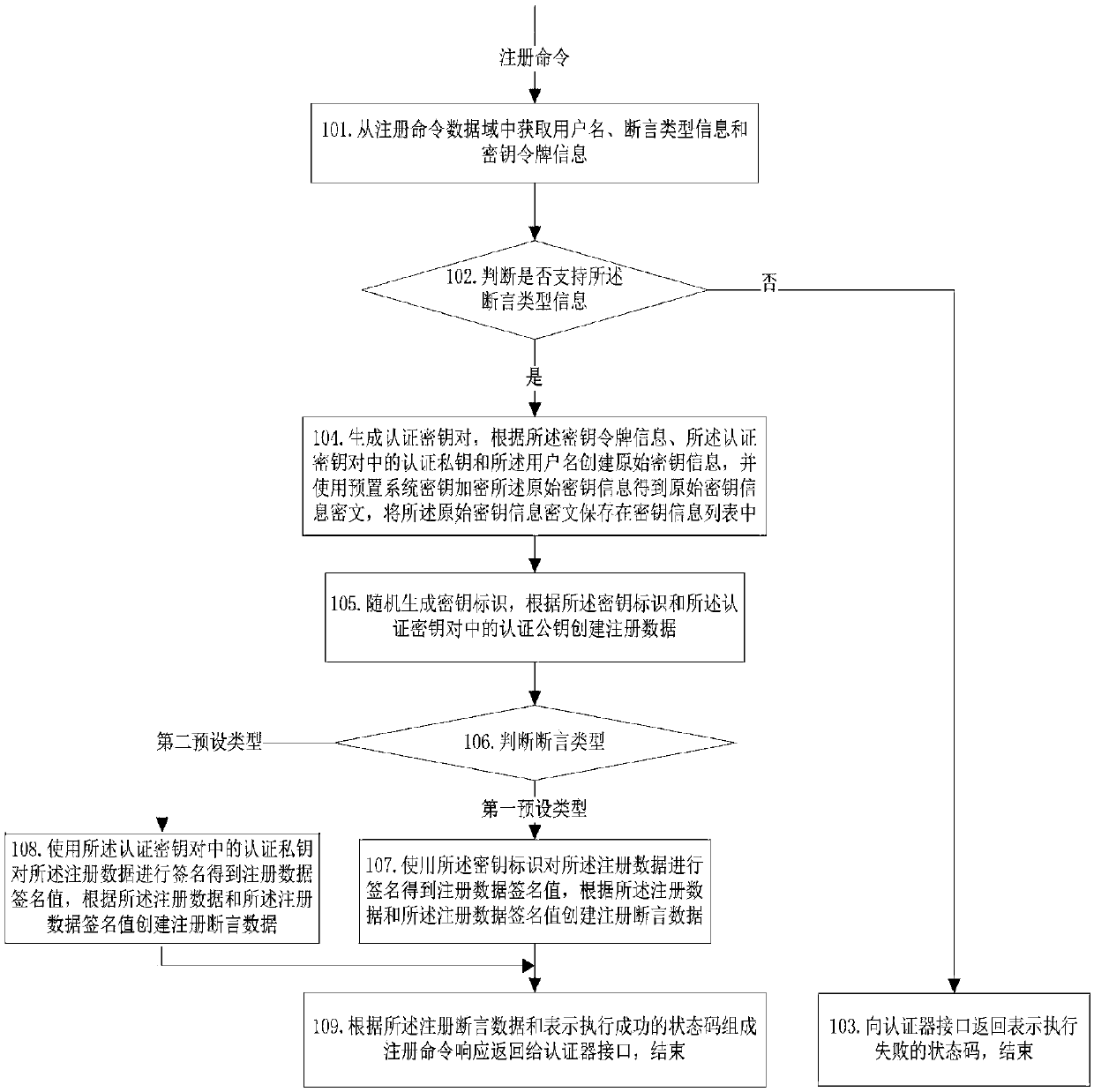
[0108] The implementation method of the authenticator provided in this embodiment includes the registration function and the signature function implemented by the authenticator. Preferably, the system on which the authenticator is implemented in this embodiment is referred to as the client for short. When the client receives the upper layer When a registration command or a signature command is issued, the authenticator receives the registration command or signature command through the authenticator interface of the client, and executes the following steps in this embodiment: image 3 and Figure 4 The operation process is shown, and finally the client returns the command response received by the authenticator interface to the upper layer.
[0109] Specifically, such as image 3 As mentioned above, the registration process implemented by the authenticator includes: when the authenticator receives the registration command issued by the authenticator interface, the following ste...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com