Financial terminal authentication method and device
A financial terminal and authentication method technology, applied in the field of financial terminal authentication methods and devices, can solve problems such as loss of security of other cards, hidden dangers of authentication information processing, hidden safety hazards, etc., to prevent authentication information from being embezzled, prevent embezzlement, and protect Privacy Effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0043] The present invention will be further described in detail below with reference to the accompanying drawings and specific embodiments. The examples are only used to illustrate the present invention, but do not limit the protection scope of the present invention. Considering that the current MD5 algorithm is one of the most widely used hash functions, and considering that the current fingerprint identification technology is a very mature biometric authentication technology, the following uses fingerprint and MD5 algorithm as examples to illustrate the implementation of the present invention.
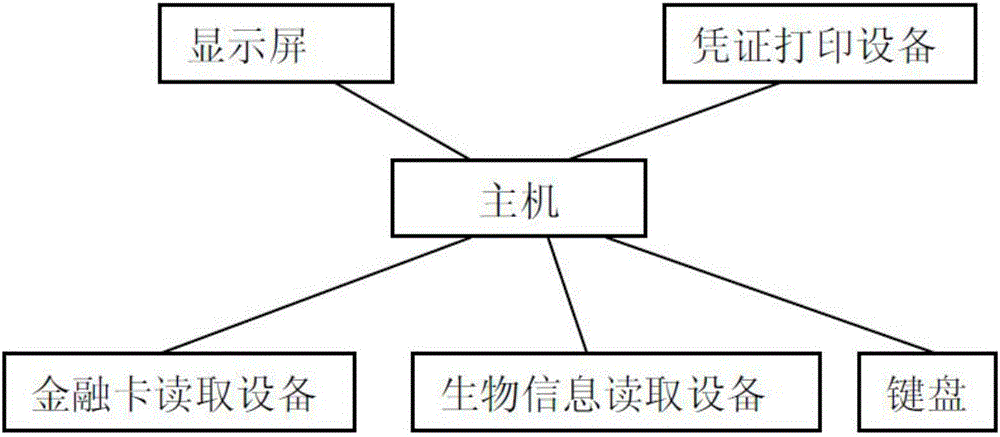
[0044] like figure 1 As shown, the present invention also discloses a financial terminal authentication device, which is arranged in the teller terminal and the self-service terminal; the authentication device includes: a host, a financial card reading device, a biological information reading device and a keyboard, the financial card reading device , The biological information readi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com