Terminal, identity authentication method, authentication method for authentication center and terminal and authentication system
A technology of identity authentication and authentication center, which is applied in the field of security authentication, can solve problems such as passwords are easy to lose and steal, authentication methods are easy to be forged, and security is not high, so as to improve security, improve authentication accuracy, and reduce error rates. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
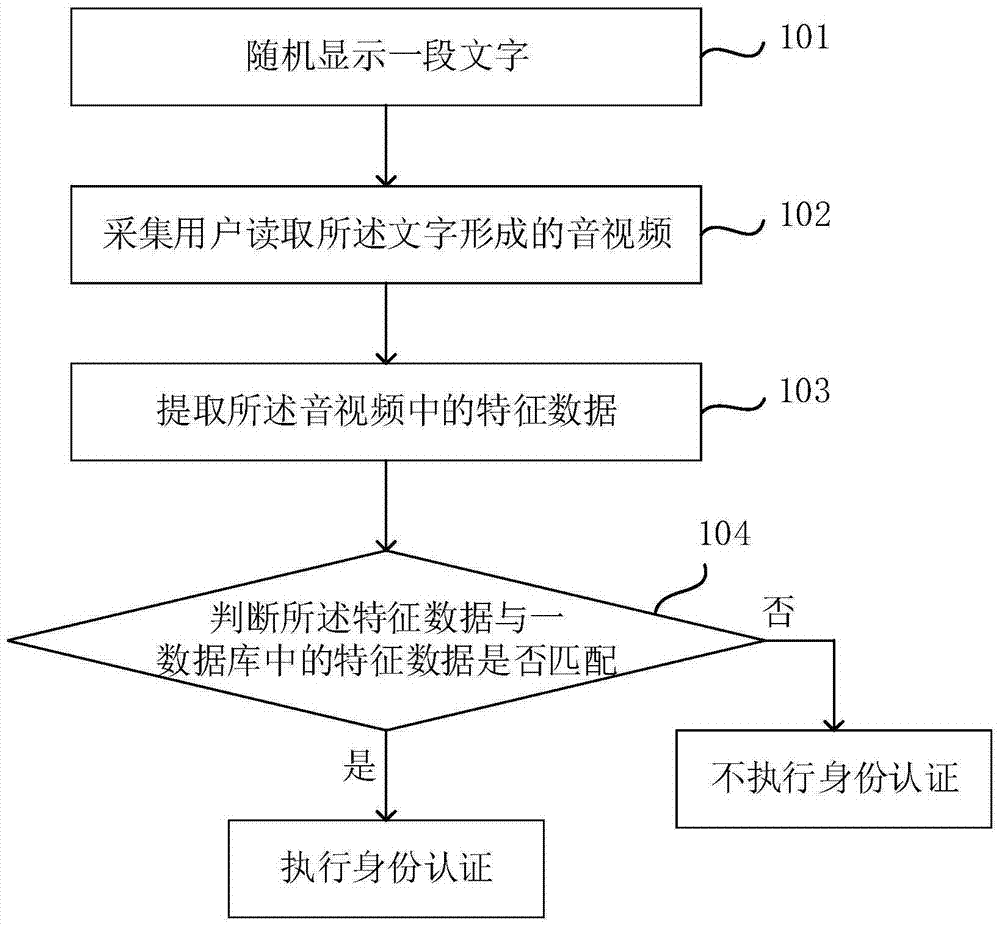
[0099] This embodiment provides a terminal identity authentication method, such as figure 1 As shown, the application situation can be: the user logs in his bank account on the terminal. After entering the account number, in order to avoid the login operation performed by criminals, the terminal needs to perform authentication on the identity of the logged-in user. Specifically, the identity authentication methods include:
[0100] Step 101, randomly display a paragraph of text;
[0101] Among them, the terminal can be mobile phone, tablet computer, PDA (Personal Digital Assistant, personal digital assistant), POS (Point of Sales, sales terminal), vehicle-mounted computer and other equipment, and the terminal can also be used as some admission equipment (such as access control equipment) to Authenticate user identity. The terminal has a display screen, and the text randomly displayed on the display screen is readable characters. The more characters, the better. In fact, the t...
Embodiment 2
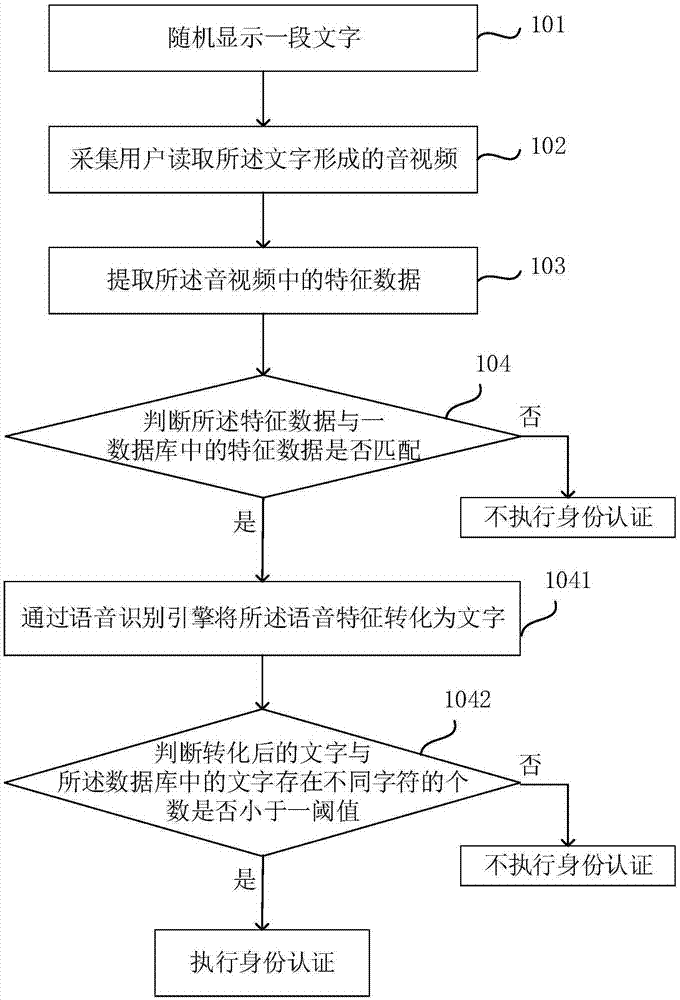
[0114] This embodiment provides a terminal identity authentication method, such as figure 2 As shown, the difference between the present embodiment and embodiment 1 is: the feature data extracted in step 103 also includes voice features, and step 104 includes:
[0115] Step 1041, converting the speech features into text through a speech recognition engine;
[0116] Step 1042: Determine whether the number of different characters between the converted text and the text in the database is less than a threshold, if so, perform identity authentication, otherwise, do not perform identity authentication.
[0117] In order to further verify the identity of the user, it is also possible to further verify the identity of the user by judging whether the pronunciation of the text is accurate, so as to more accurately exclude the situation that illegal users use forged audio and video to authenticate their identity. Among them, speech recognition is a speech recognition technology that e...
Embodiment 3
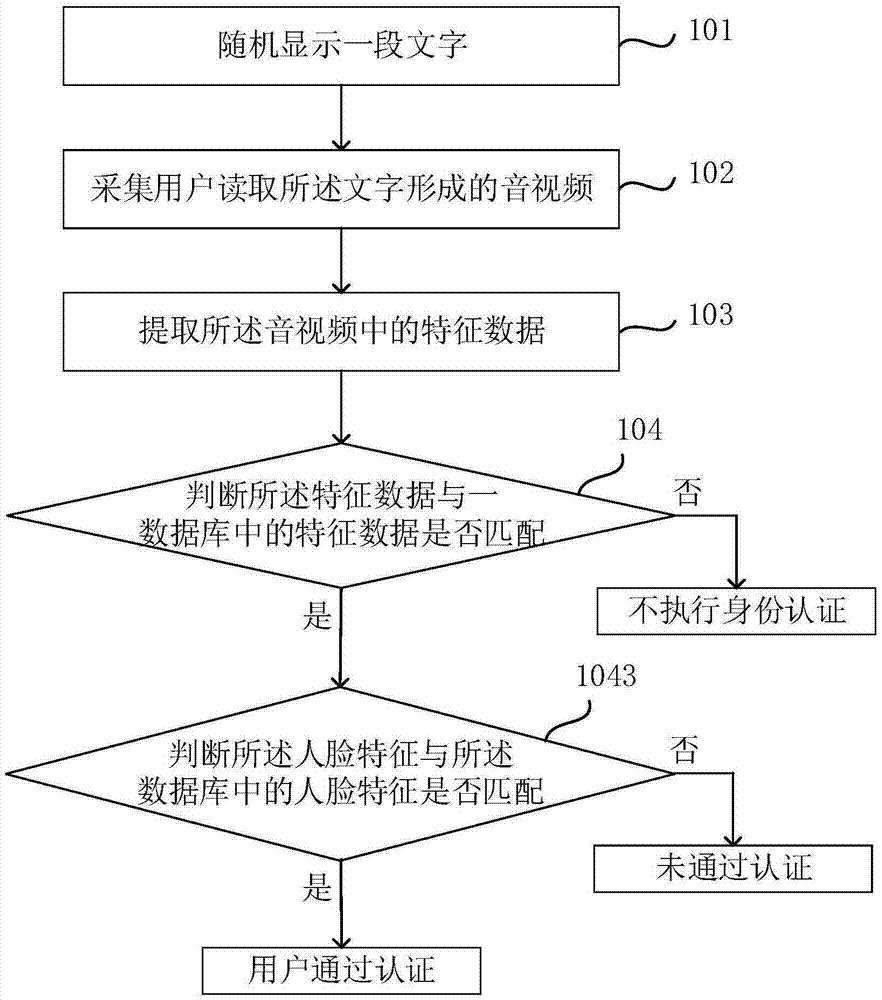
[0130] This embodiment provides a terminal, such as Figure 5 As shown, it includes a display module 1, an audio and video acquisition module 2, an extraction module 3 and a first judgment module 4;
[0131] The display module 1 is used to randomly display a paragraph of text, and the display module 1 may have the function of a display screen.
[0132] The audio and video acquisition module 2 is used to collect the audio and video that the user reads the text to form, and the audio and video acquisition module 2 can have the functions of a microphone and a camera;
[0133] The extraction module 3 is used to extract feature data in the audio and video, and the extraction module 3 can have the function of a processor to process the audio and video files obtained;
[0134] The first judging module 4 is used to judge whether the characteristic data matches the characteristic data in a database, if so, perform identity authentication, otherwise do not perform identity authenticati...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com