Security authentication method for WEB service
A WEB service and security authentication technology, applied in the security authentication field of WEB service interface application, can solve the problems of cumbersome use, and achieve the effect of strengthening authentication security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] The present invention will be further described below in conjunction with the accompanying drawings.
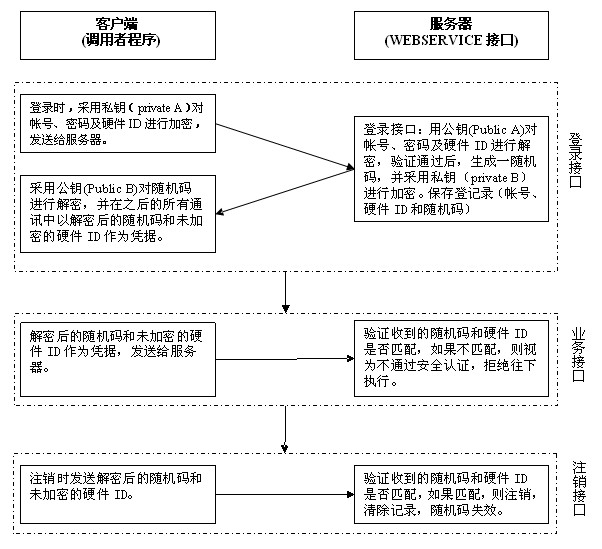
[0025] Please refer to the attached figure 1 , the WEBSERVICE interface exists as a server-side mode, and it is distributed with a login interface, a logout interface and several service interfaces. The application program that calls this WEBSERVICE interface exists in the form of a client, and various business functions are realized by calling the WEBSERVICE interface. All WEBSERVICE interfaces adopt a security authentication mechanism. The identity authentication mechanisms of the login interface, logout interface, and business interface are slightly different. Before calling the business interface, the client must first call the login interface to obtain the identity certificate. When the client exits the program, Call the logout interface to log out the identity certificate.
[0026] It can be implemented as follows:
[0027] 1. First, you need to determine an a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com