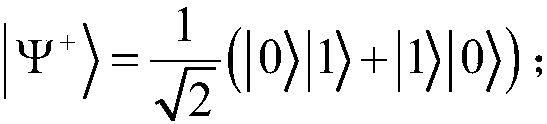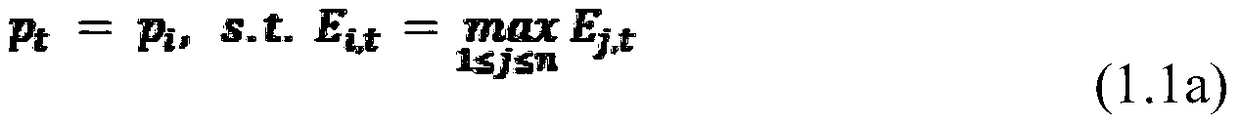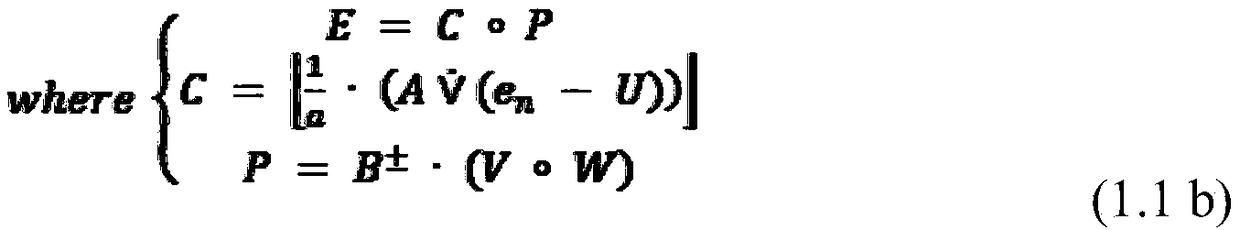Patents
Literature
95results about How to "Increase legitimacy" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
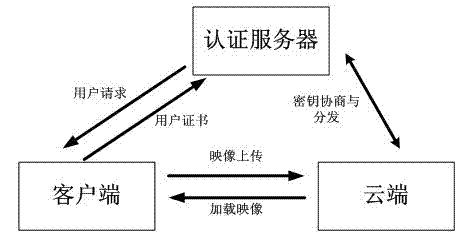
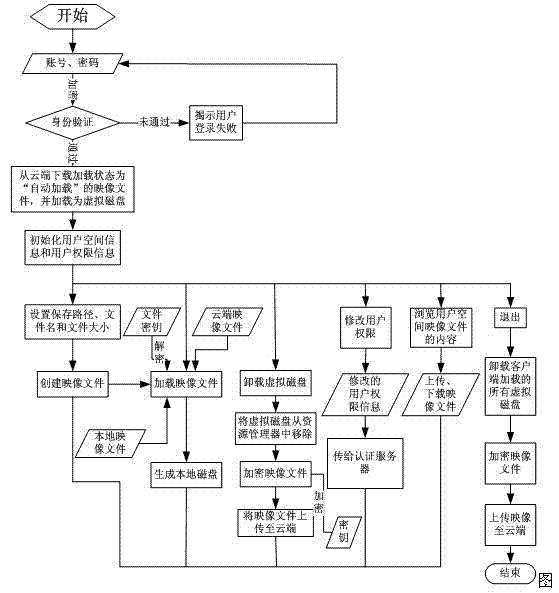
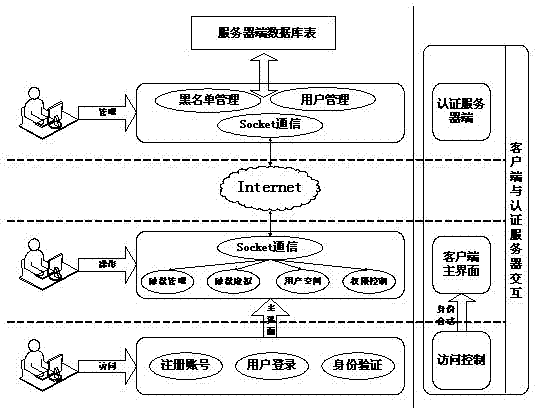
Network virtual disk file safety management method based on cloud computing
InactiveCN102394894AIncrease legitimacyImprove securityTransmissionCloud computingLoad balancing (computing)
The invention provides a network virtual disk file safety management method based on cloud computing, which achieves the functions of automatic load balancing and transparent space expanding and shrinking by adopting cloud computing thought. In order to overcome the defect that public cloud can not realize data safety isolation and authorization use, the method can take Hadoop cloud platform as a base to construct a seamless virtual disk transparent encryption environment and realize distribution storage, data isolation, safe data sharing and other functions.
Owner:WUHAN UNIV
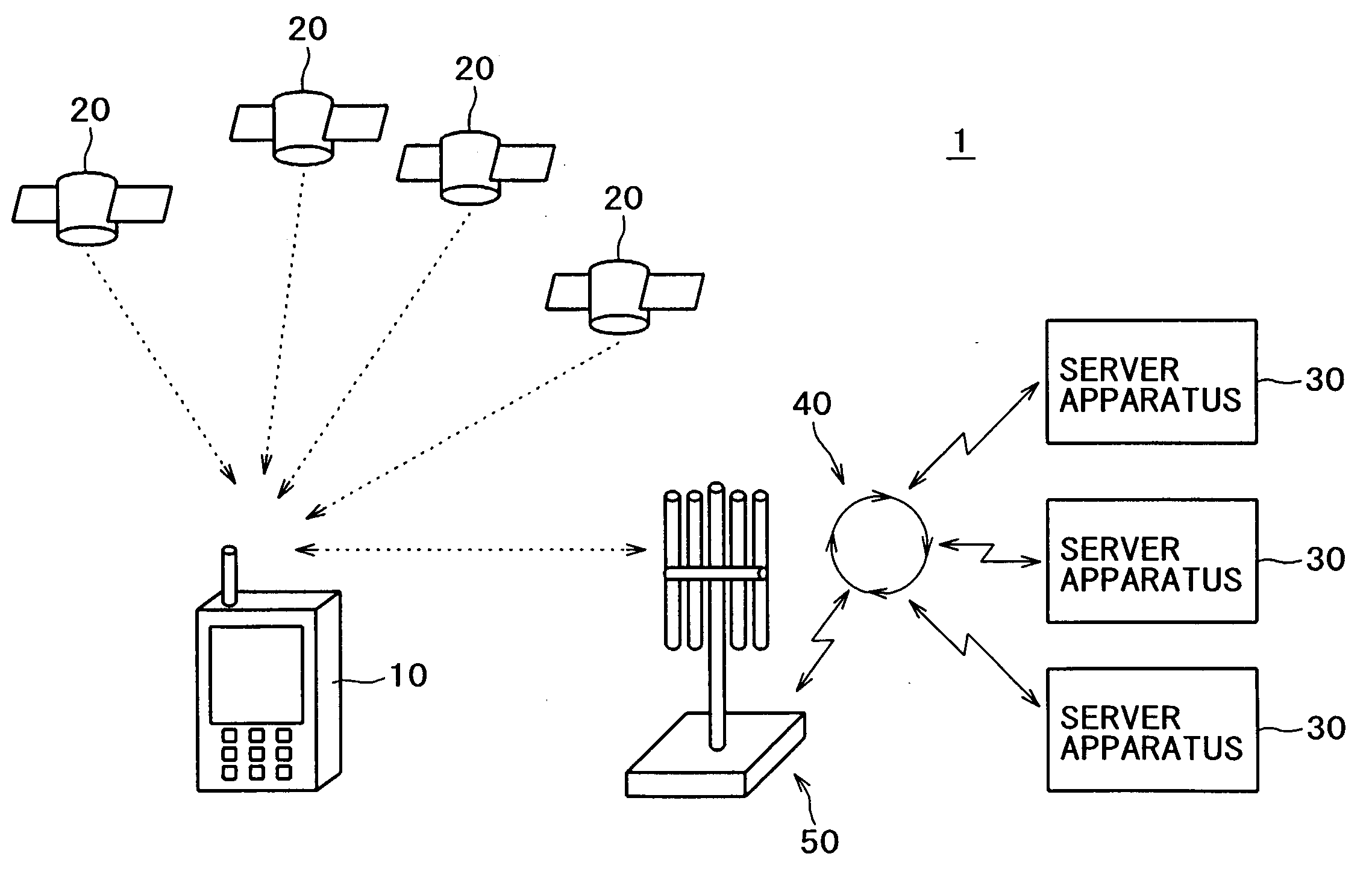
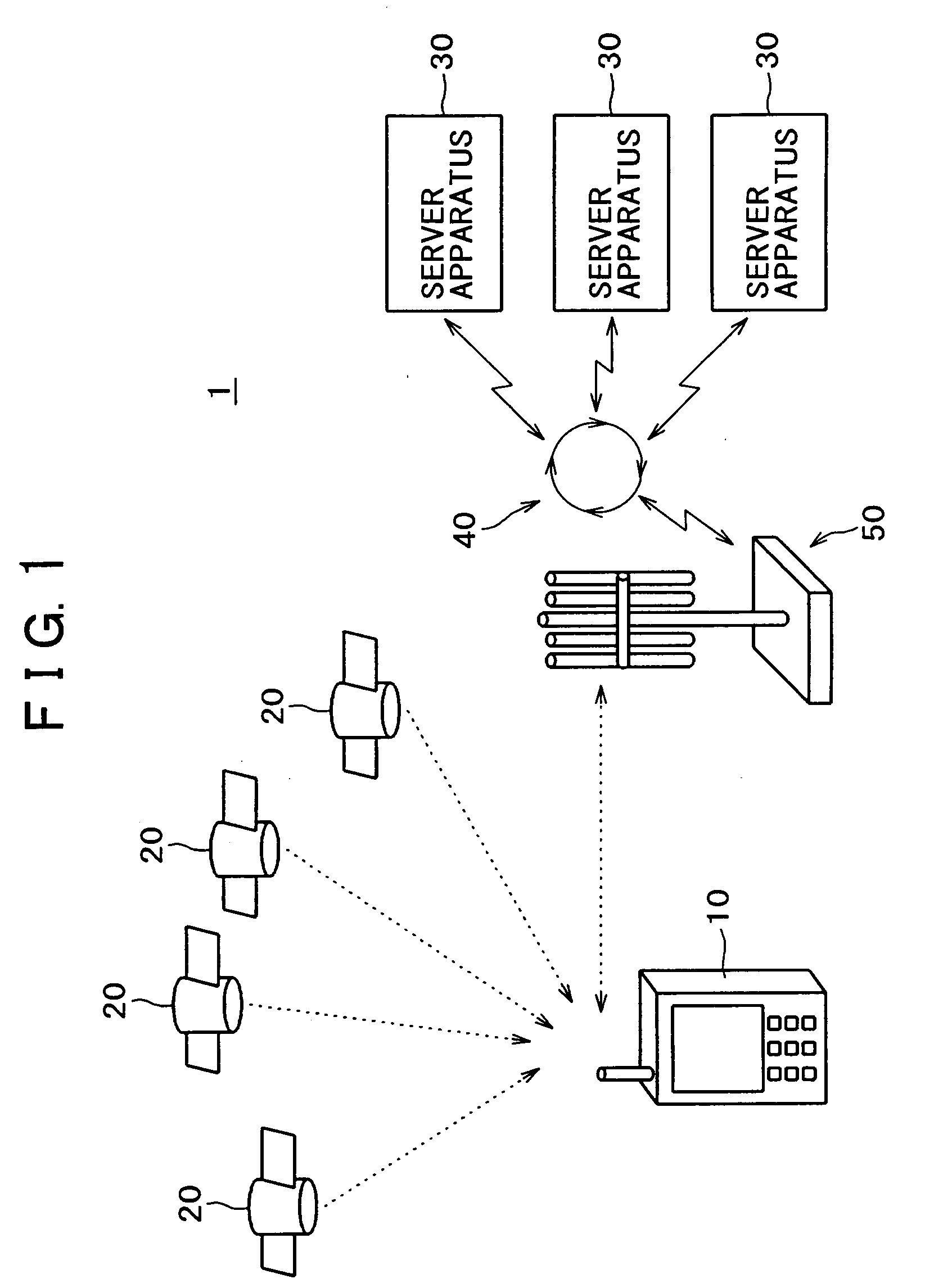
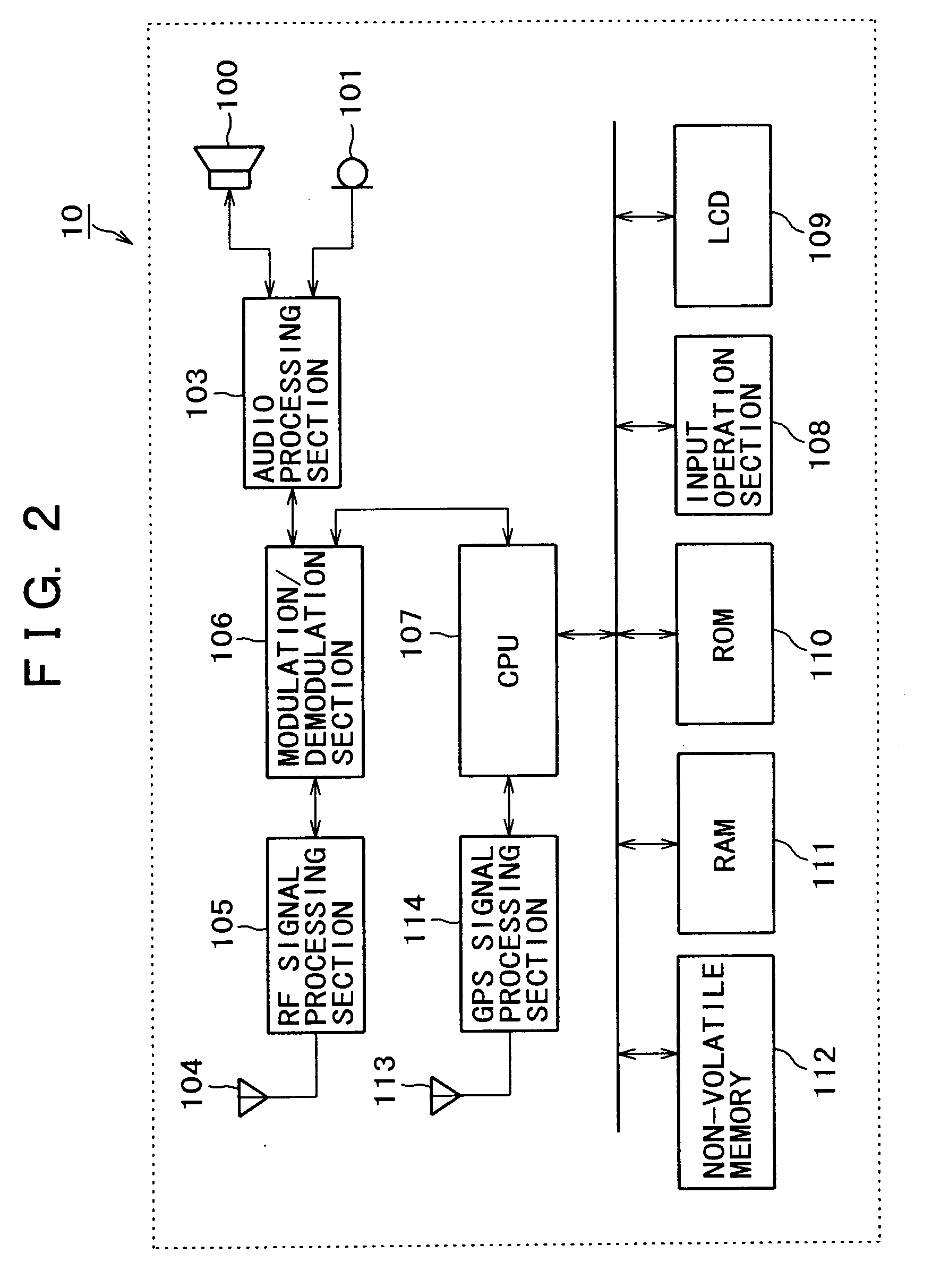
Information terminal apparatus, information processing apparatus and information communication system
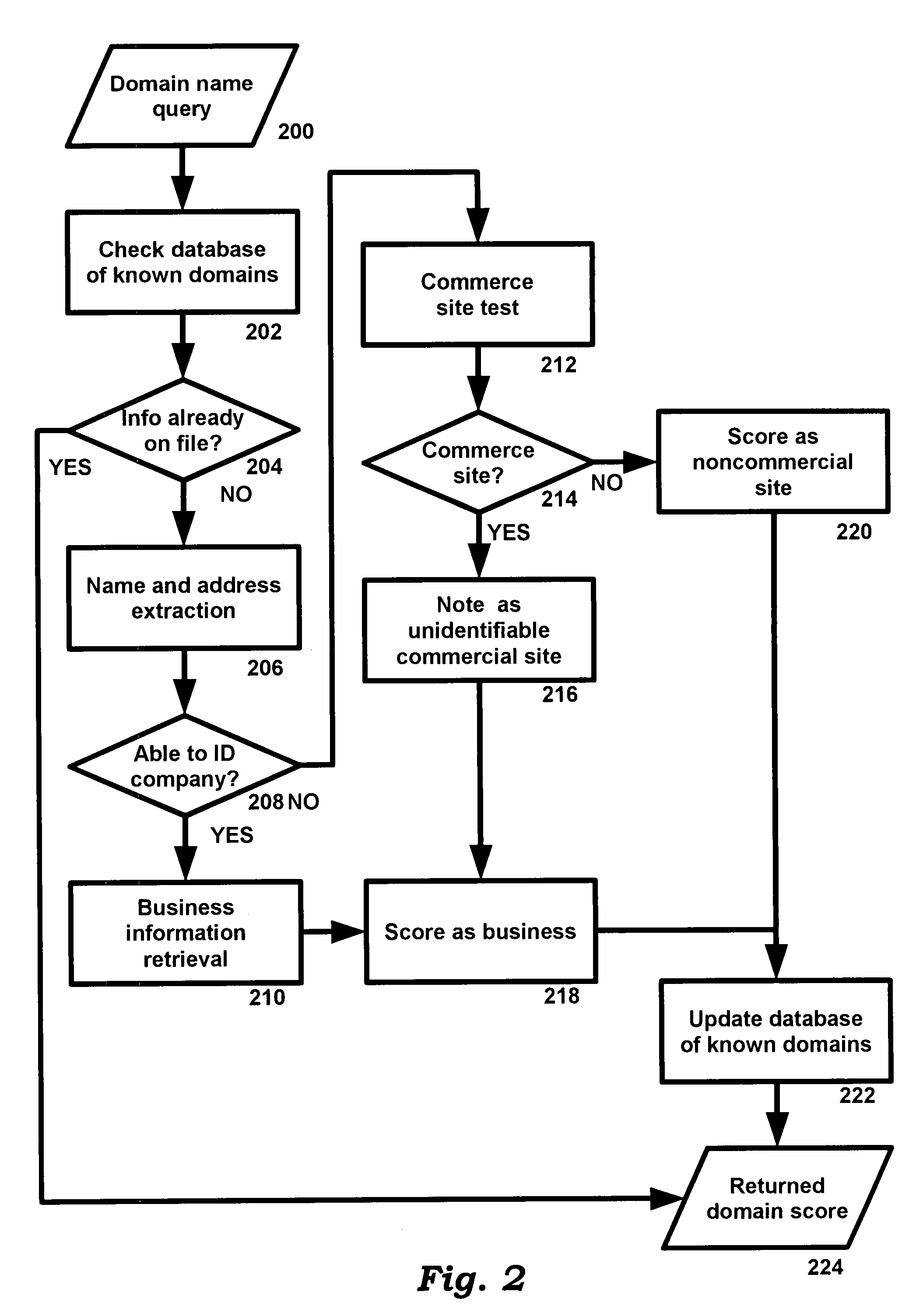
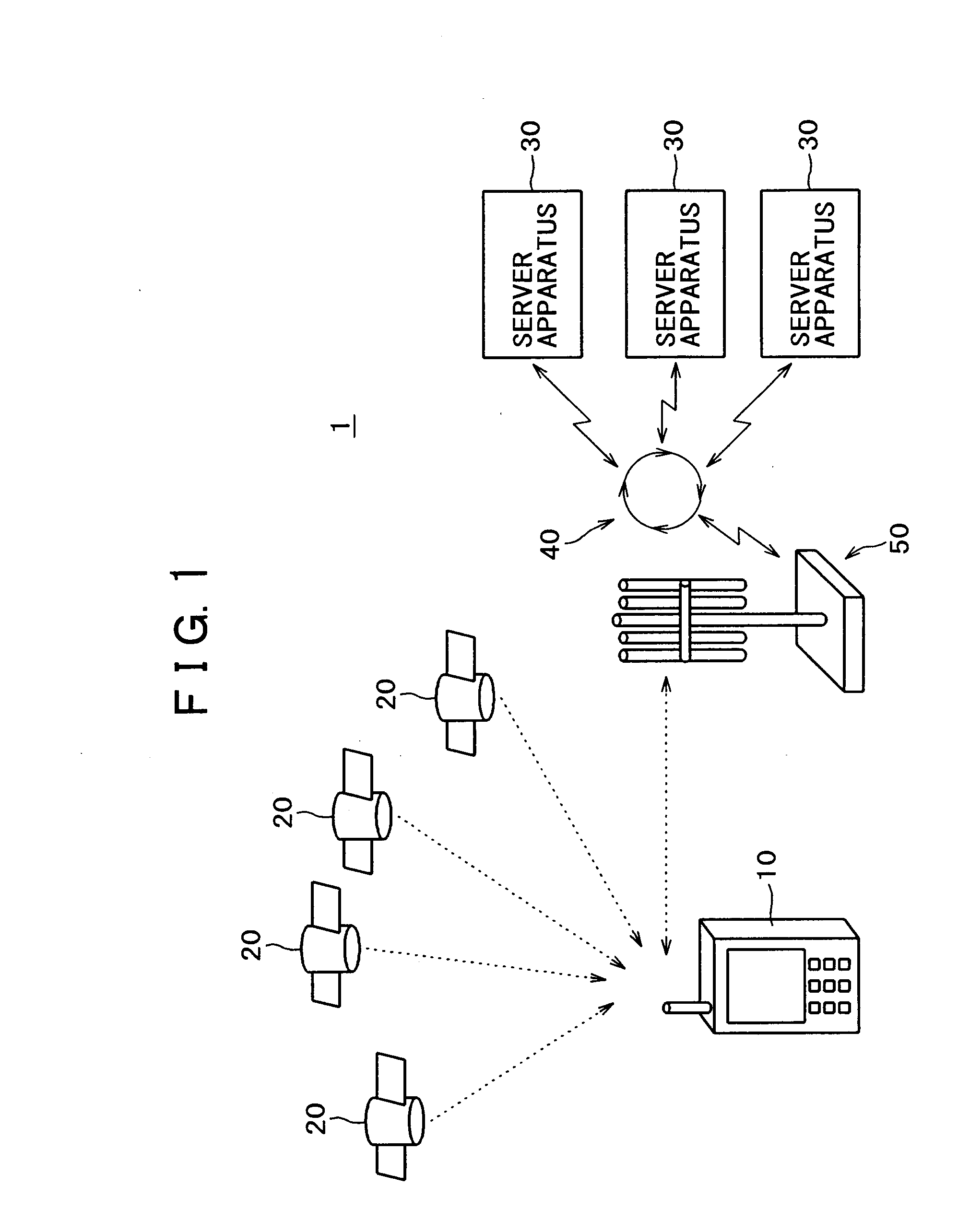
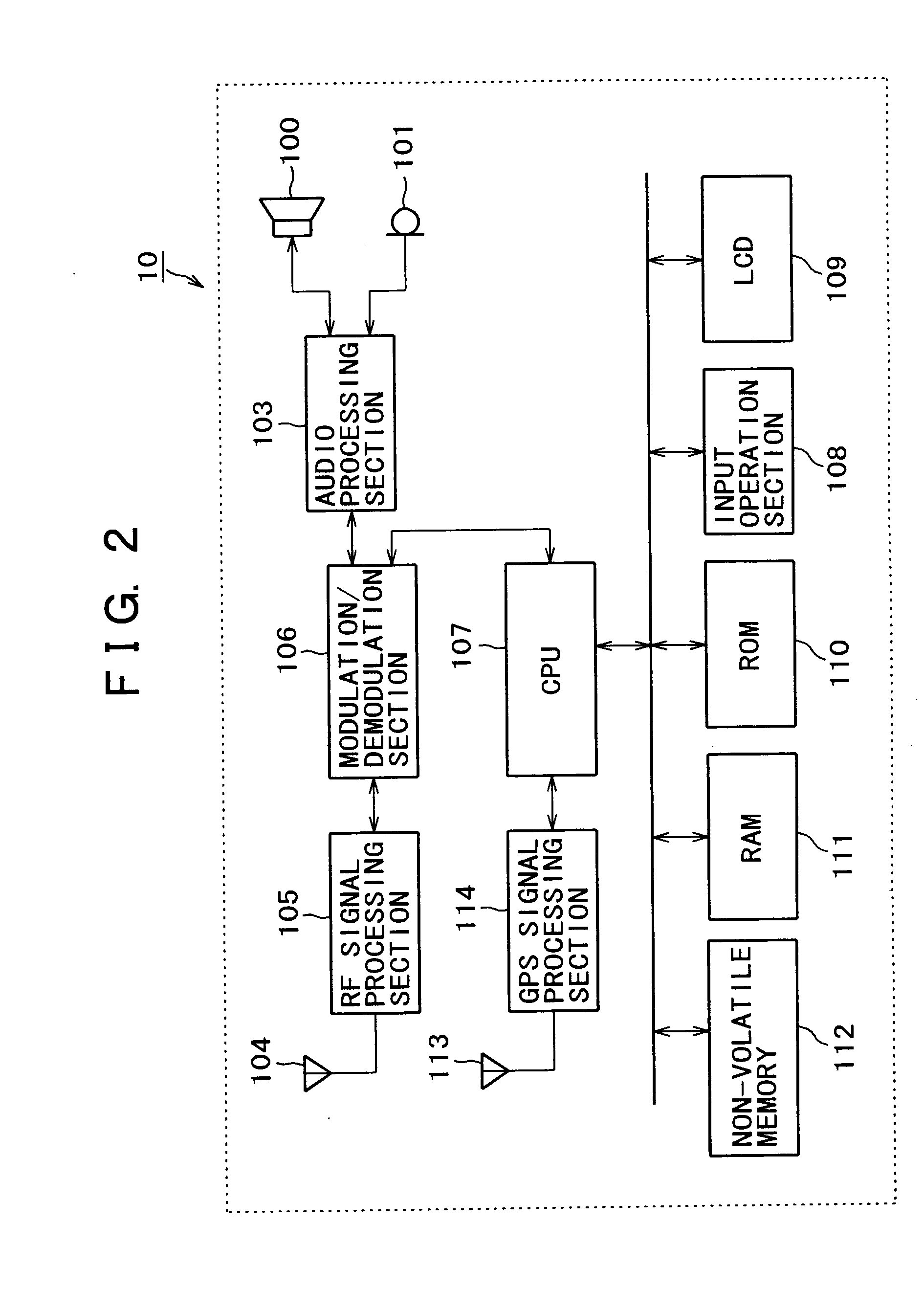
InactiveUS20080284648A1Safely and reliably communicatedIncrease legitimacyDigital data processing detailsUser identity/authority verificationTime informationInformation processing
Owner:SONY CORP
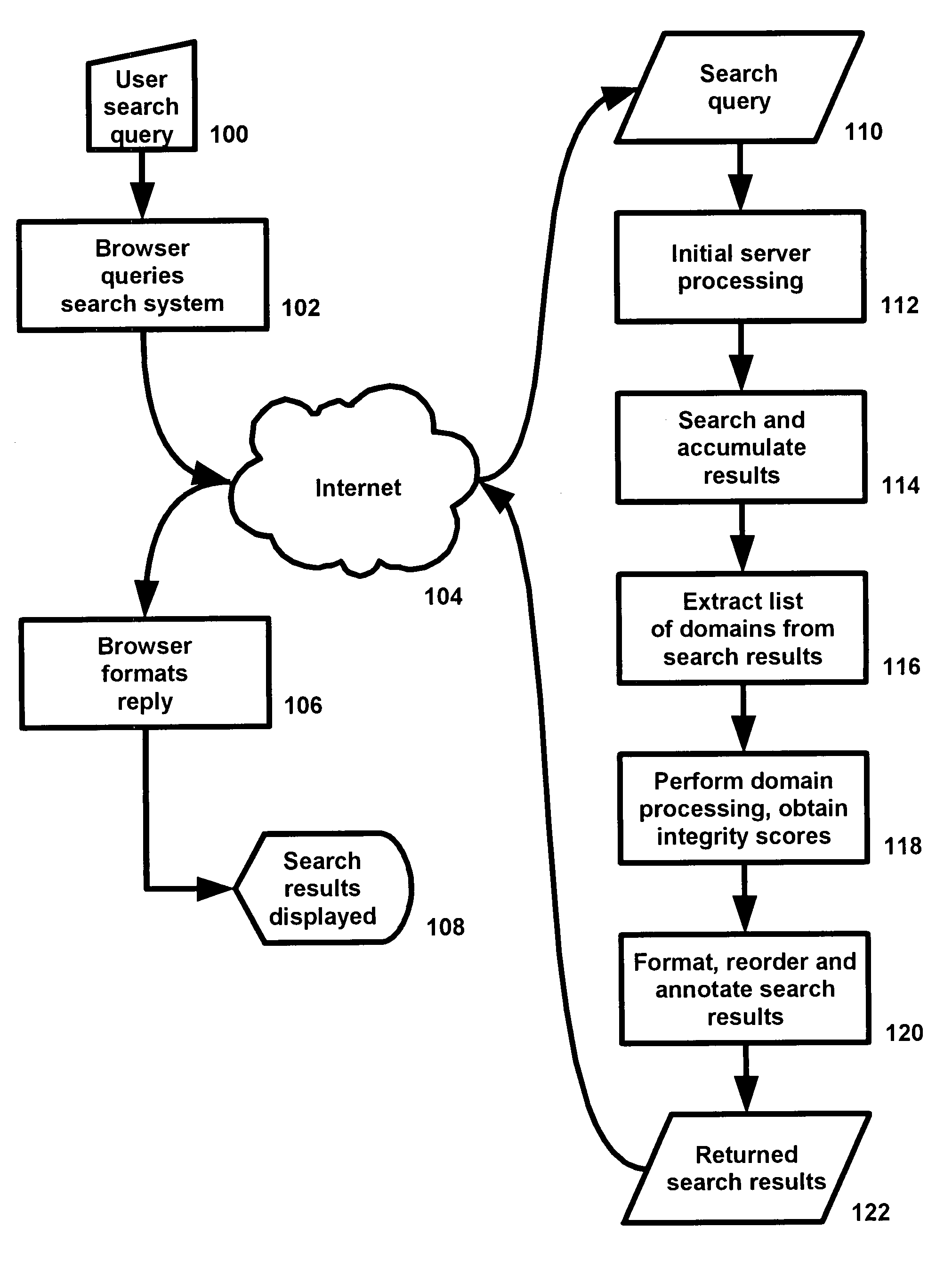
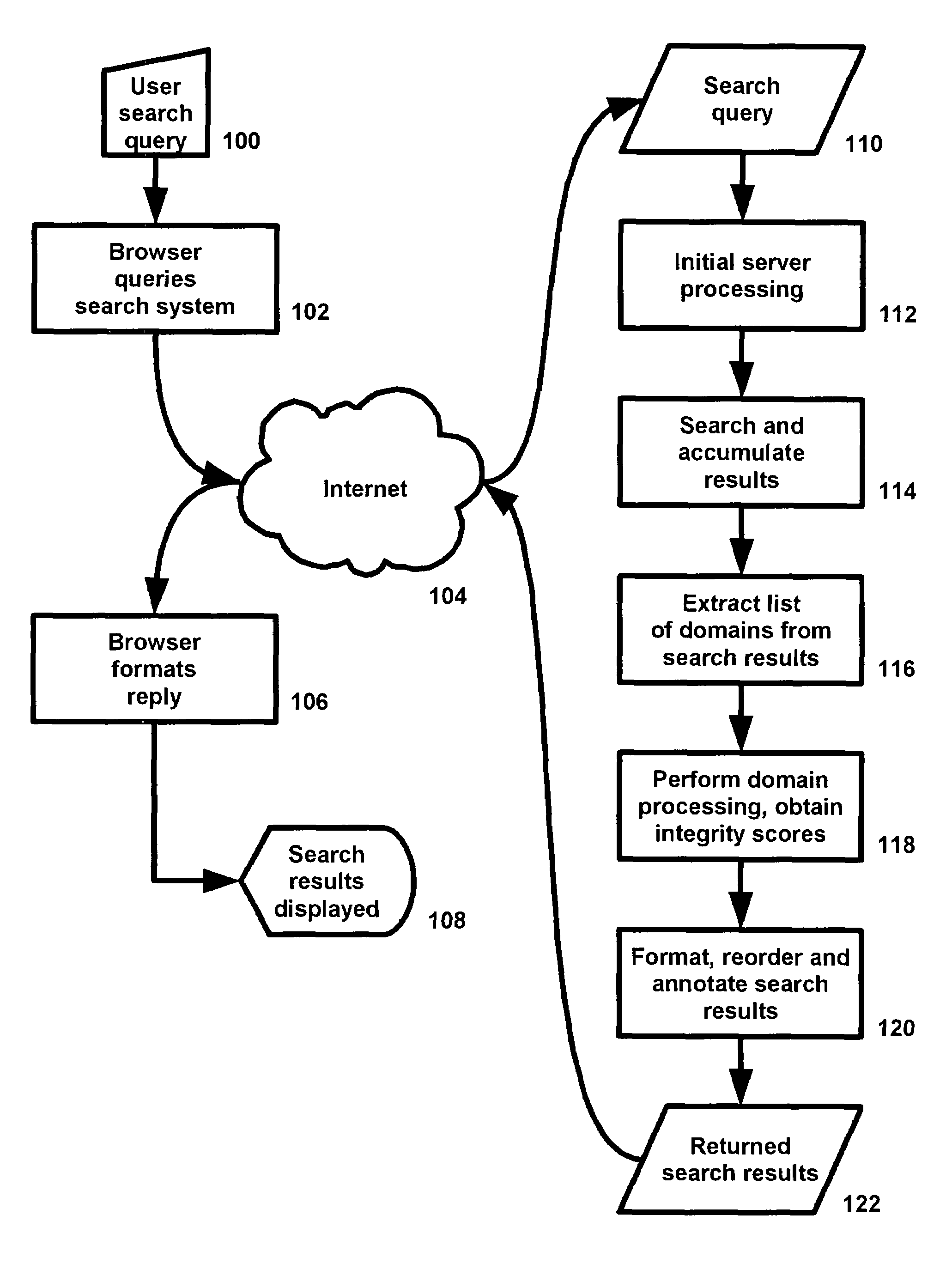
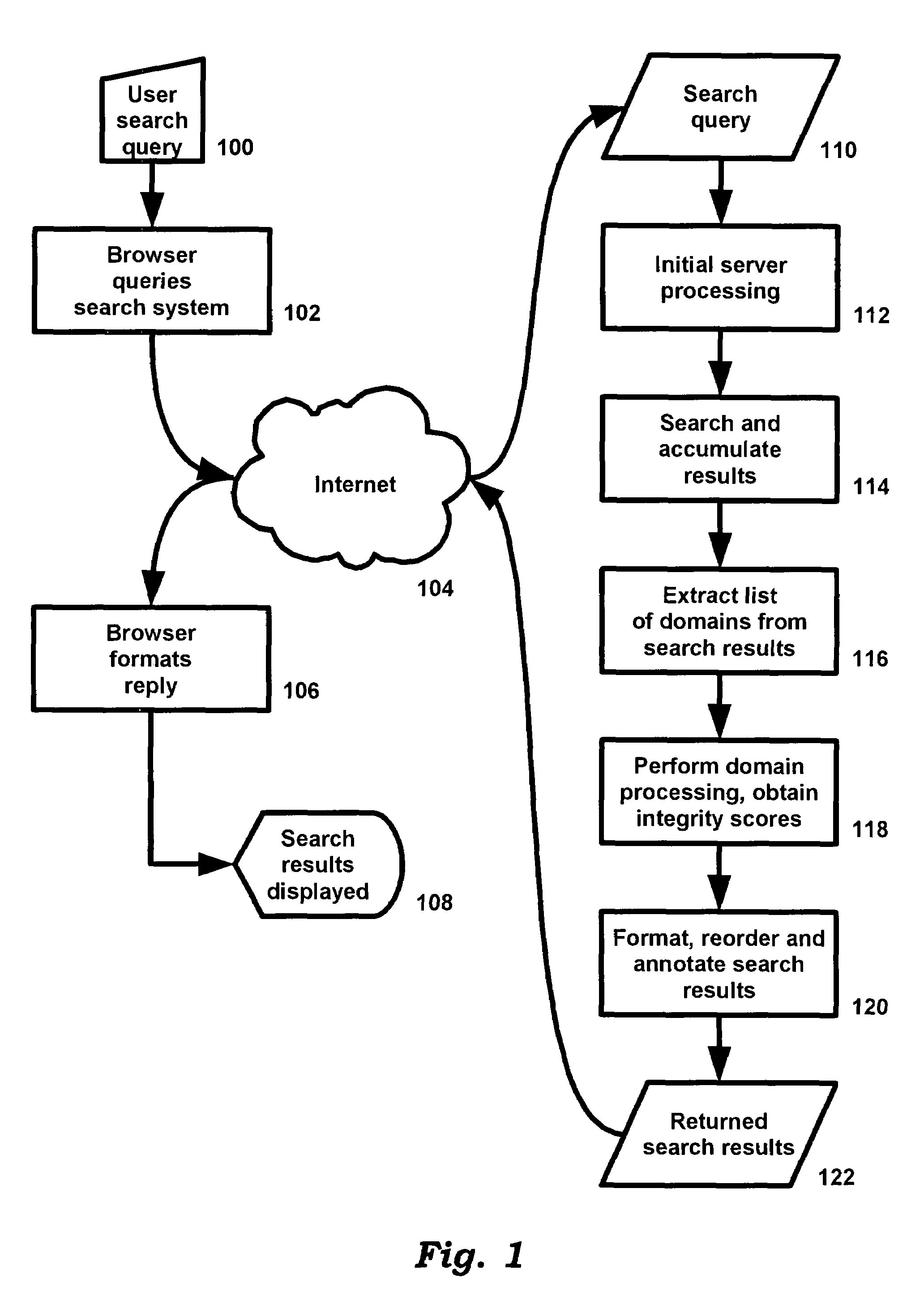
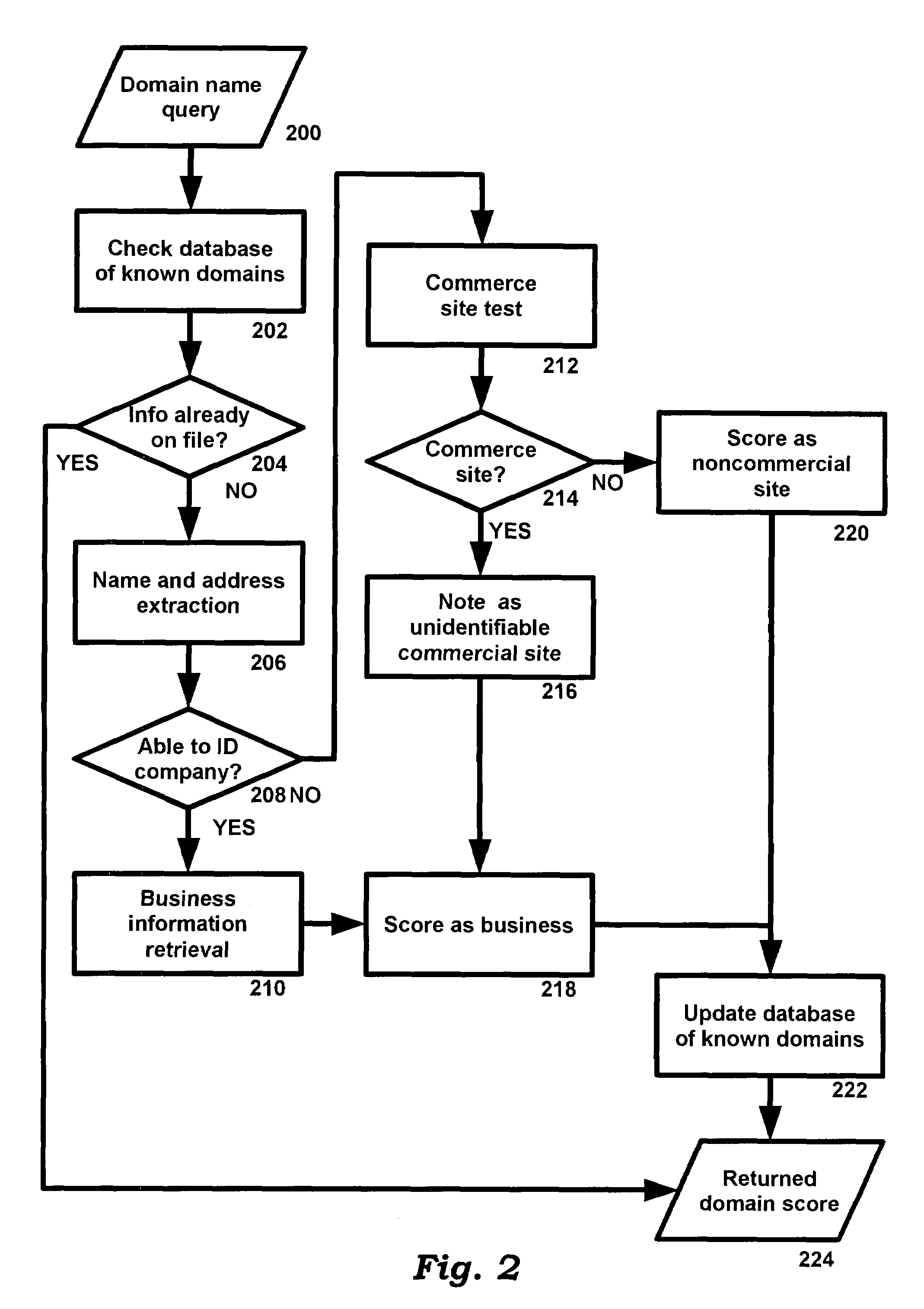
System and method for improving integrity of internet search
InactiveUS20080189263A1Reducing user frustrationReduce frustrationDiscounts/incentivesWeb data indexingWeb siteInternet searching
A system and method are provided to receive a search query from a user, typically via a web browser, the Internet, and a web server. A search engine obtains a set of potential search results based on the search query. For each Internet domain or web site mentioned in the search results, a set of data sources is accessed to obtain information concerning the legitimacy of the business associated with the Internet domain or web site. The legitimacy information is used to reorder or to change or to augment the appearance or presentation of the search result for the Internet domain or web site. The processed search results are returned to the user.
Owner:NAGLE JOHN
Information terminal apparatus, information processing apparatus and information communication system
InactiveUS20080232586A1Safely and reliably communicatedIncrease legitimacyDigital data processing detailsUser identity/authority verificationTime informationInformation processing
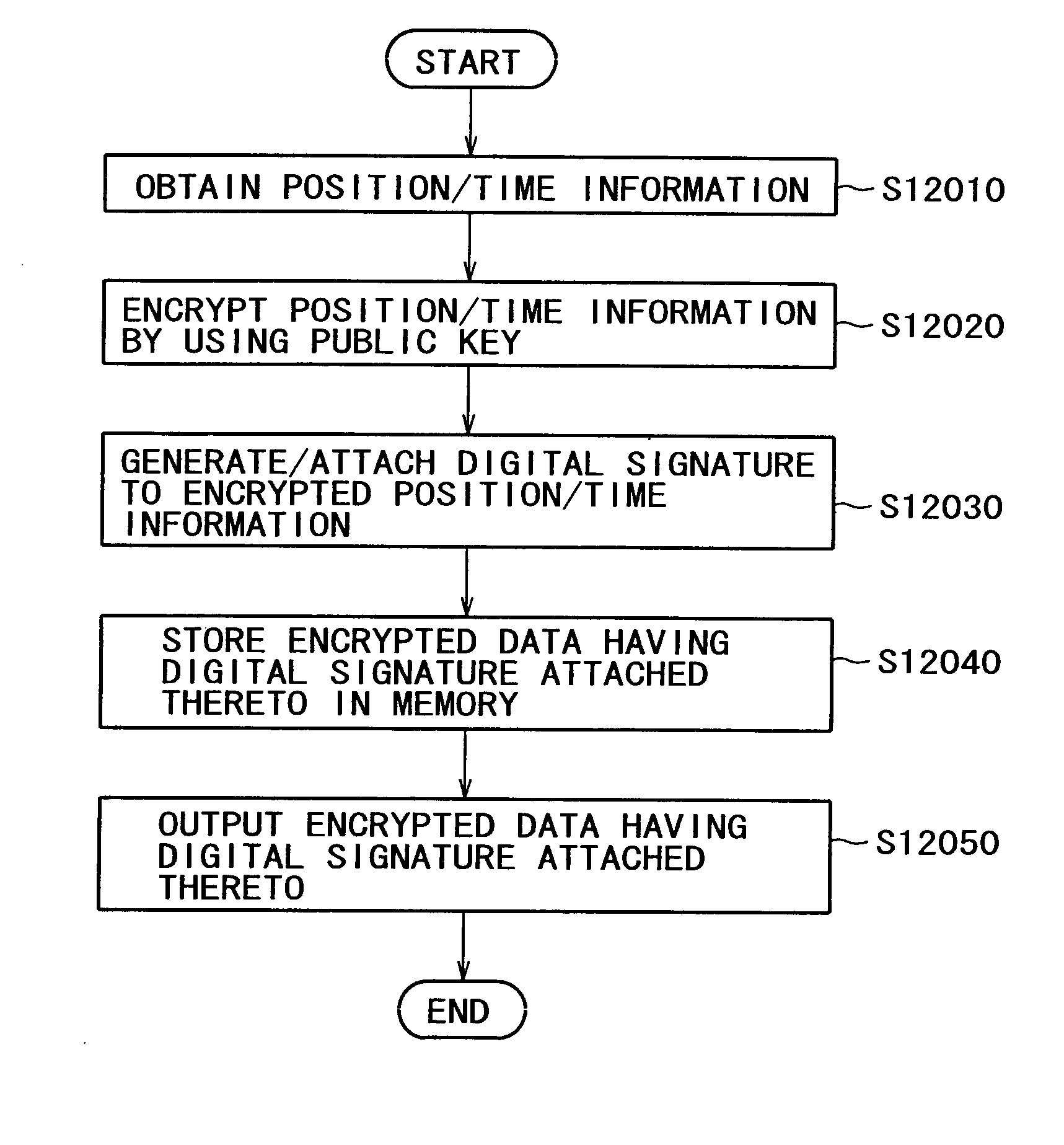
When transmitting position / time information calculated by means of a GPS function to a server apparatus, authentication is carried out with the server apparatus. The position / time information may be certified as legitimate measured by a portable apparatus with a GPS reception function employed by a user. When transmitting information related to the position and the time acquired from a portable phone terminal having the GPS function and a network function by means of the GPS function to the server apparatus, authentication is carried out between the portable phone terminal and the server apparatus. The position / time information is transmitted to the server apparatus, only if the server apparatus is authenticated as a legitimate counterpart for connection. A secret key holding section is provided for holding different secret keys for different apparatuses. The position / time information measured based on an electromagnetic wave received from a positioning satellite is digitally signed by means of the secret key. The identification information and the position / time information having the digital signature are then transmitted to a counterpart.
Owner:SONY CORP
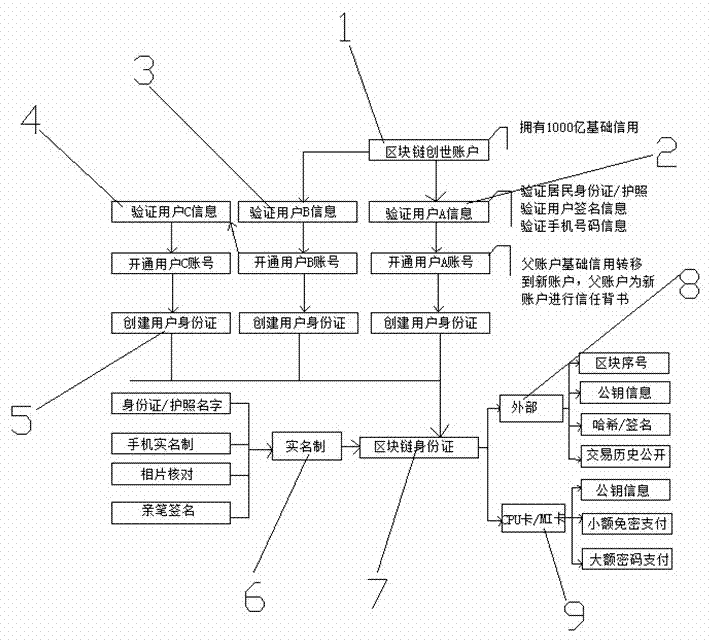
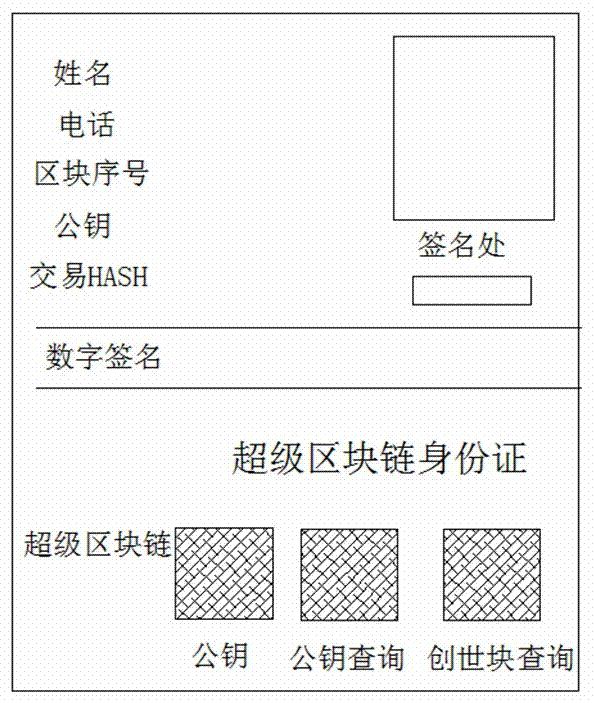
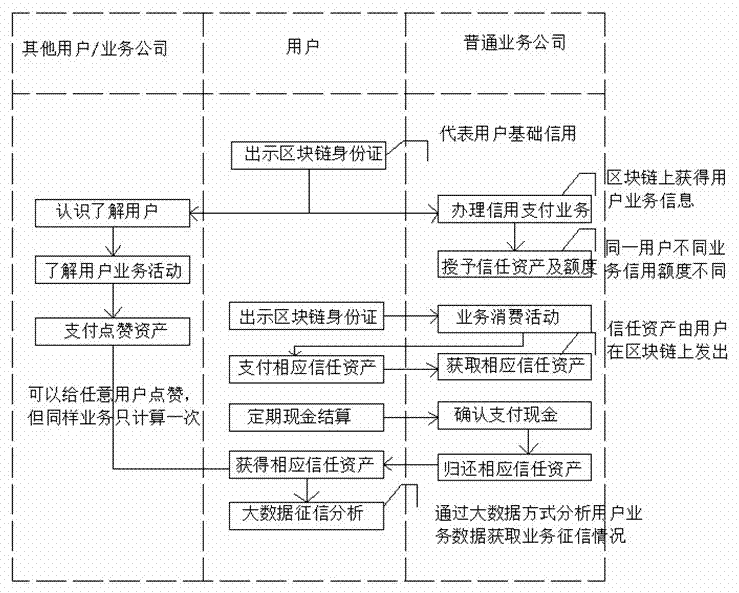
Distributed blockchain identity card
The invention discloses a distributed blockchain identity card, which comprises a blockchain identity card creating process and a blockchain identity card data relationship and blockchain identity card promotion business credit process. The first account of a blockchain is named as a blockchain creating account. The blockchain identity card data creating process comprises a user A, a user B and auser C; the user A puts forward an application from the blockchain creating account; after the blockchain creating account passes the information of the user A, a blockchain account is created for theuser A on the blockchain through the own account; the user B creates the blockchain identity card of the same type; the user B creates the blockchain identity card for the user C and transfers the credit endorsement of the user B to the user C; and finally, the blockchain identity card transfers the distributed credit to the user C to create the blockchain identity card, wherein the blockchain identity card comprises an external part and a card body (which includes a CPU (Central Processing Unit) card or a M1 card). By use of the identity card, data safety is guaranteed, and the reliability of blockchain information is improved.
Owner:深圳超级区块链信息技术有限公司
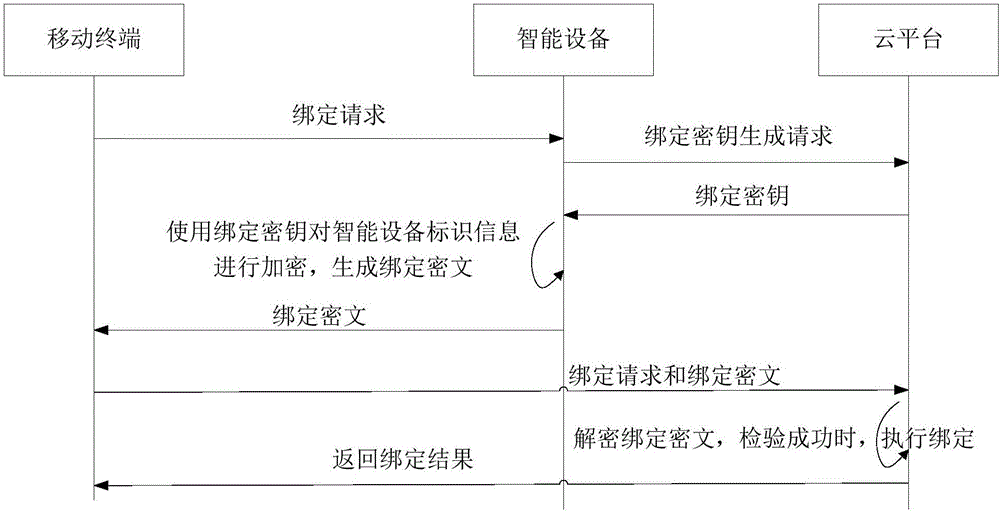
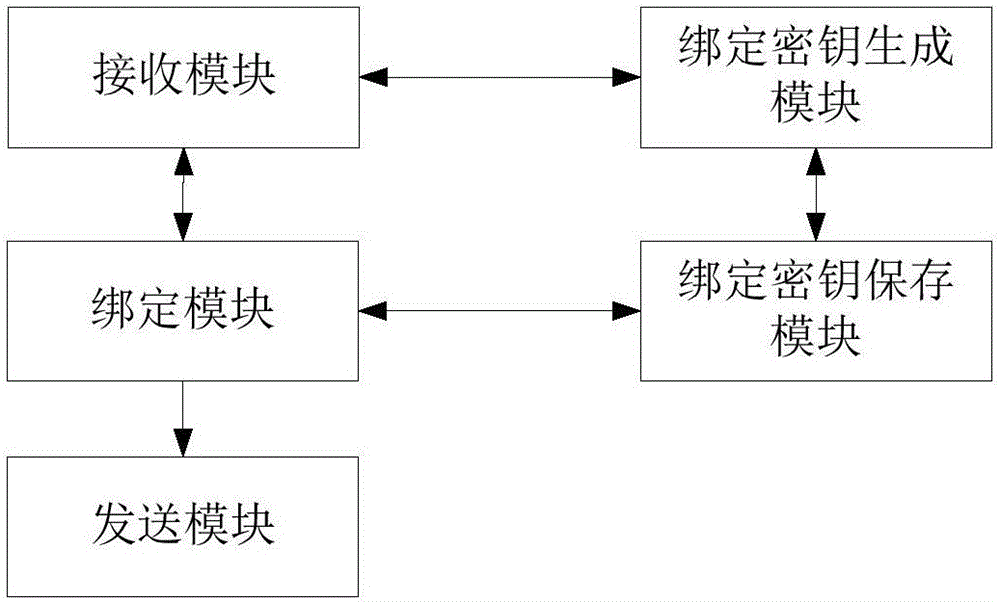
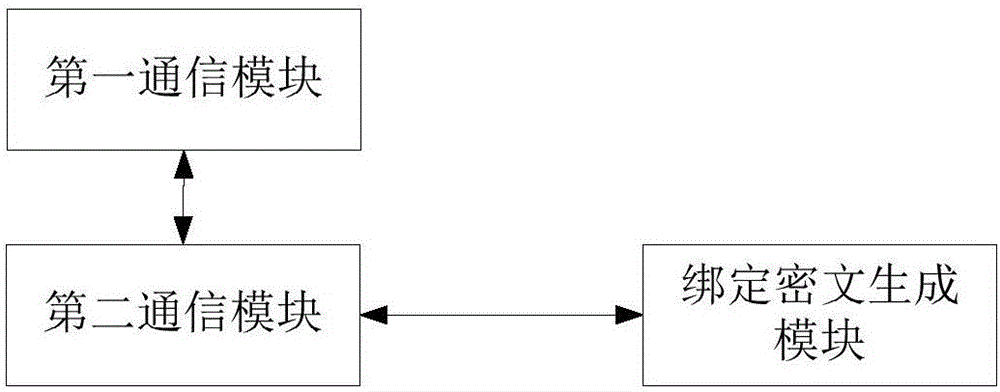
Intelligent equipment binding method and device
The invention discloses an intelligent equipment binding method and device. The method comprises steps as follows: a cloud platform generates binding keys and records the corresponding relation of intelligent equipment identification information and the binding keys in a corresponding relation table; when receiving a binding request carrying a client identification, the intelligent equipment identification information and a binding ciphertext from a mobile terminal, the cloud platform looks up the binding key corresponding to the intelligent equipment identification information carried in the binding request in the corresponding relation table, decodes the binding ciphertext through the binding key in a preset encryption algorithm and binds the intelligent equipment identification information and the client identification after decoding is successful or the decoded intelligent equipment identification information and the intelligent equipment identification information received from the mobile terminal are successfully matched. With the adoption of the intelligent equipment binding method and device, a false binding request can be prevented, the safety risk caused by unauthorized binding can be avoided, and the intelligent equipment control and operation safety is improved.
Owner:HAIER YOUJIA INTELLIGENT TECH BEIJING CO LTD
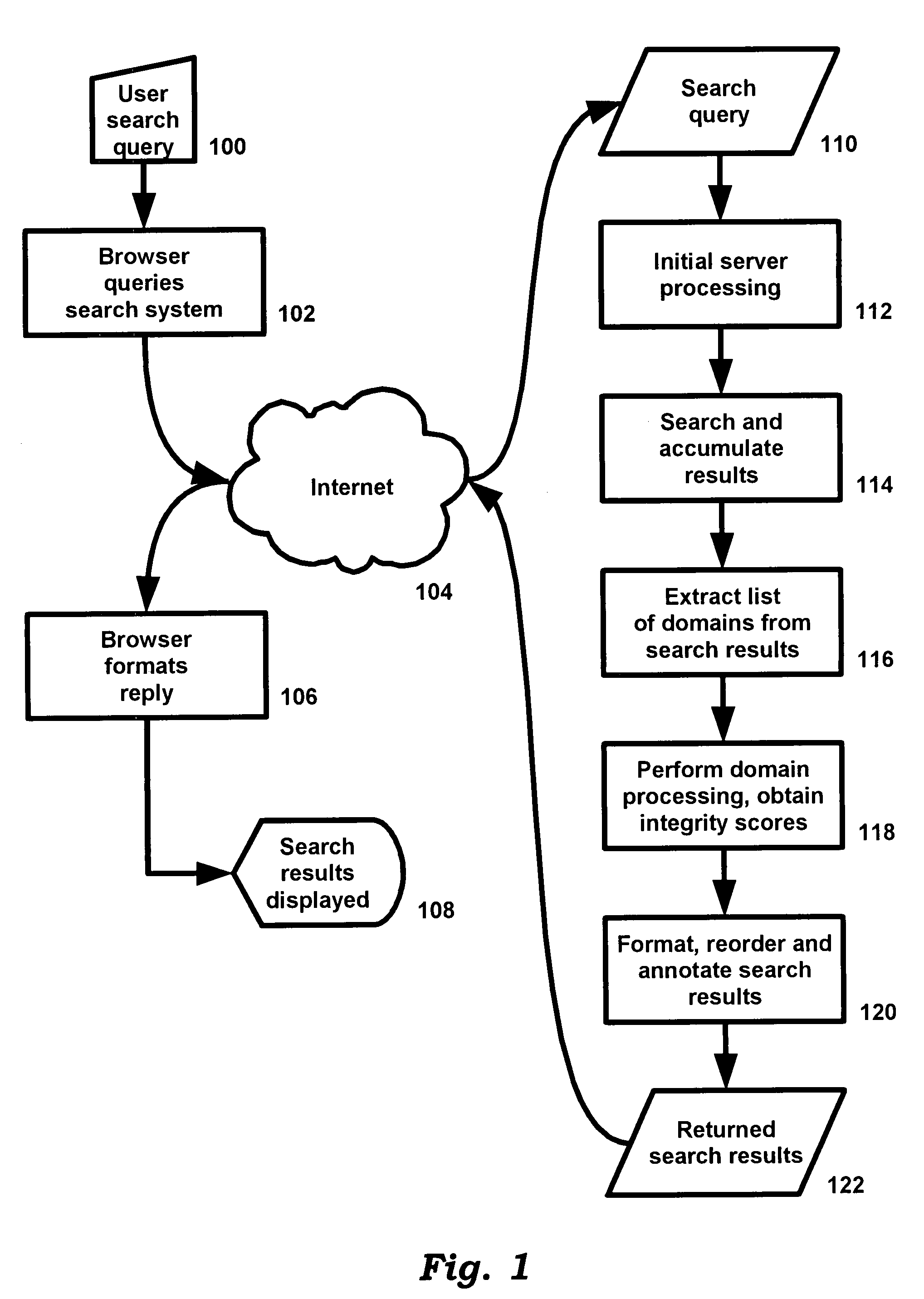
System and method for improving integrity of internet search
InactiveUS7693833B2Reduce frustrationIncrease legitimacyDiscounts/incentivesWeb data indexingWeb siteInternet searching
Owner:NAGLE JOHN
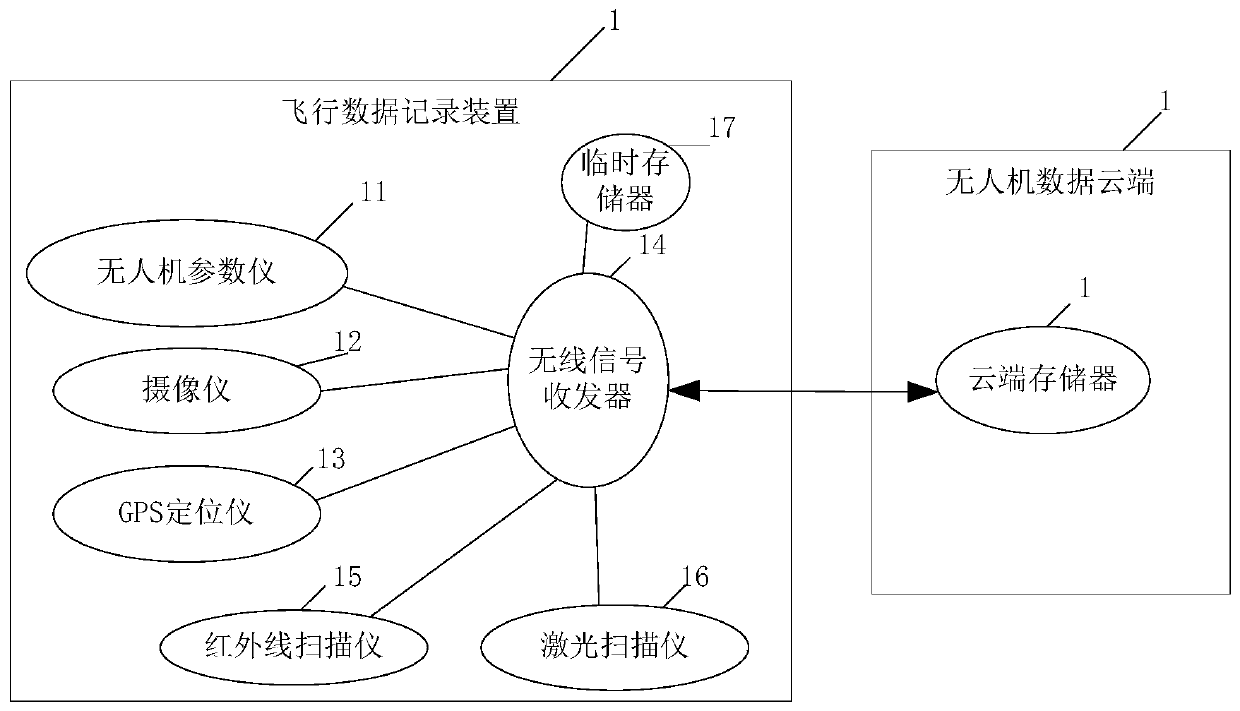
Intelligent management and control system for unmanned aerial vehicle inspection
InactiveCN110034816AIncrease legitimacyImprove securityRadio transmissionControl systemUncrewed vehicle
The invention discloses an intelligent management and control system for unmanned aerial vehicle routing inspection. The system comprises a flight data recording device, an unmanned aerial vehicle data cloud and an intelligent management and control platform. The flight data recording device is mounted on the unmanned aerial vehicle and is used for acquiring flight data and wirelessly sending theflight data to the unmanned aerial vehicle data cloud; the unmanned aerial vehicle data cloud is internally provided with a cloud memory, and the cloud memory is used for storing flight data of the unmanned aerial vehicle; and the intelligent management and control platform is in communication connection with the unmanned aerial vehicle data cloud end and is used for acquiring the flight data stored in the unmanned aerial vehicle data cloud end and carrying out analysis and calculation according to the flight data to form resources which can be directly accessed. According to the intelligent management and control system provided by the invention, the electric power inspection unmanned aerial vehicle can be comprehensively managed, the dynamic information of the unmanned aerial vehicle canbe monitored in real time, an operator can conveniently operate the unmanned aerial vehicle and timely find abnormity, and meanwhile, the use legality and safety of the unmanned aerial vehicle are enhanced.
Owner:云南电力试验研究院(集团)有限公司
Application program security verification method and terminal
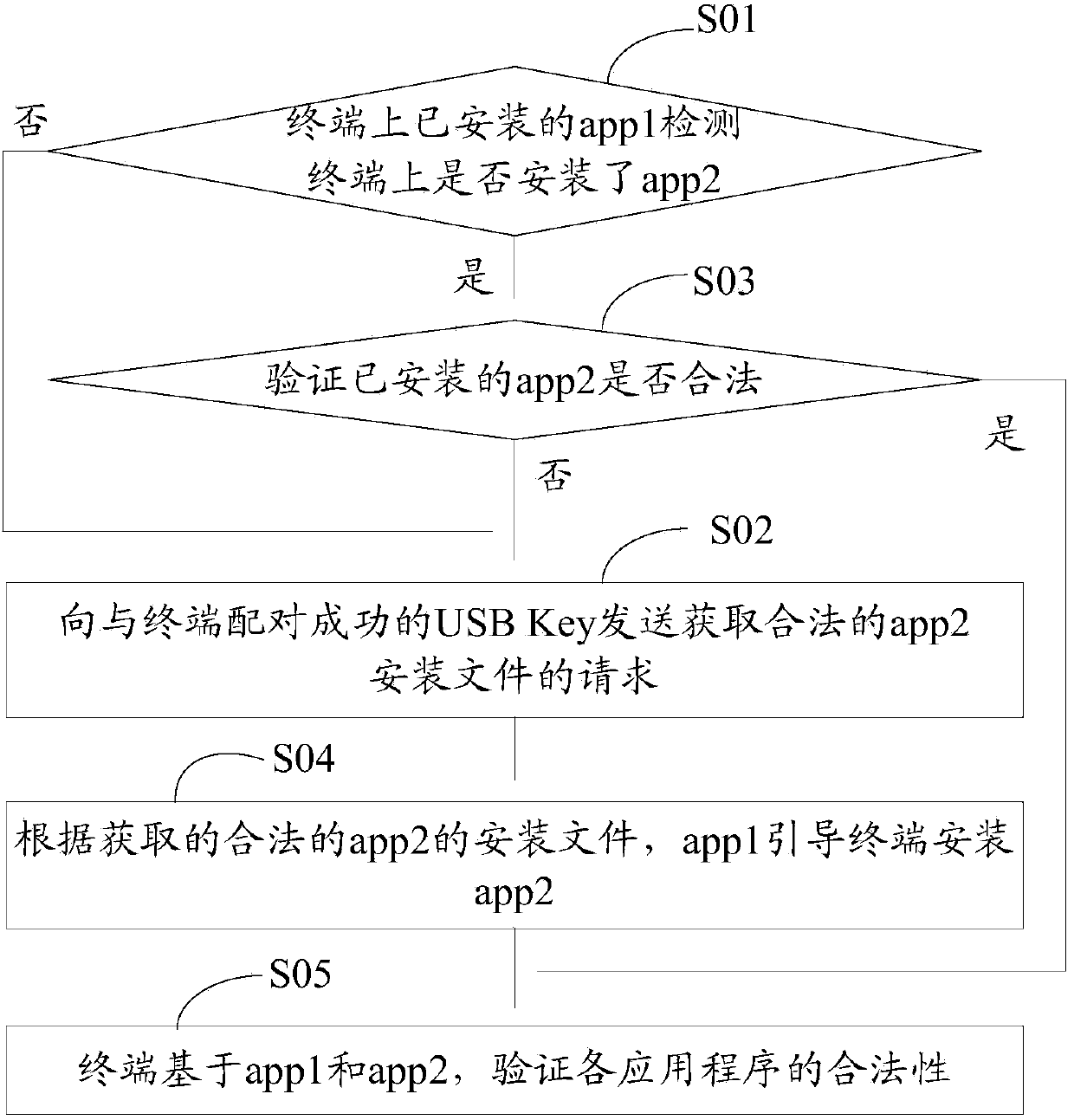
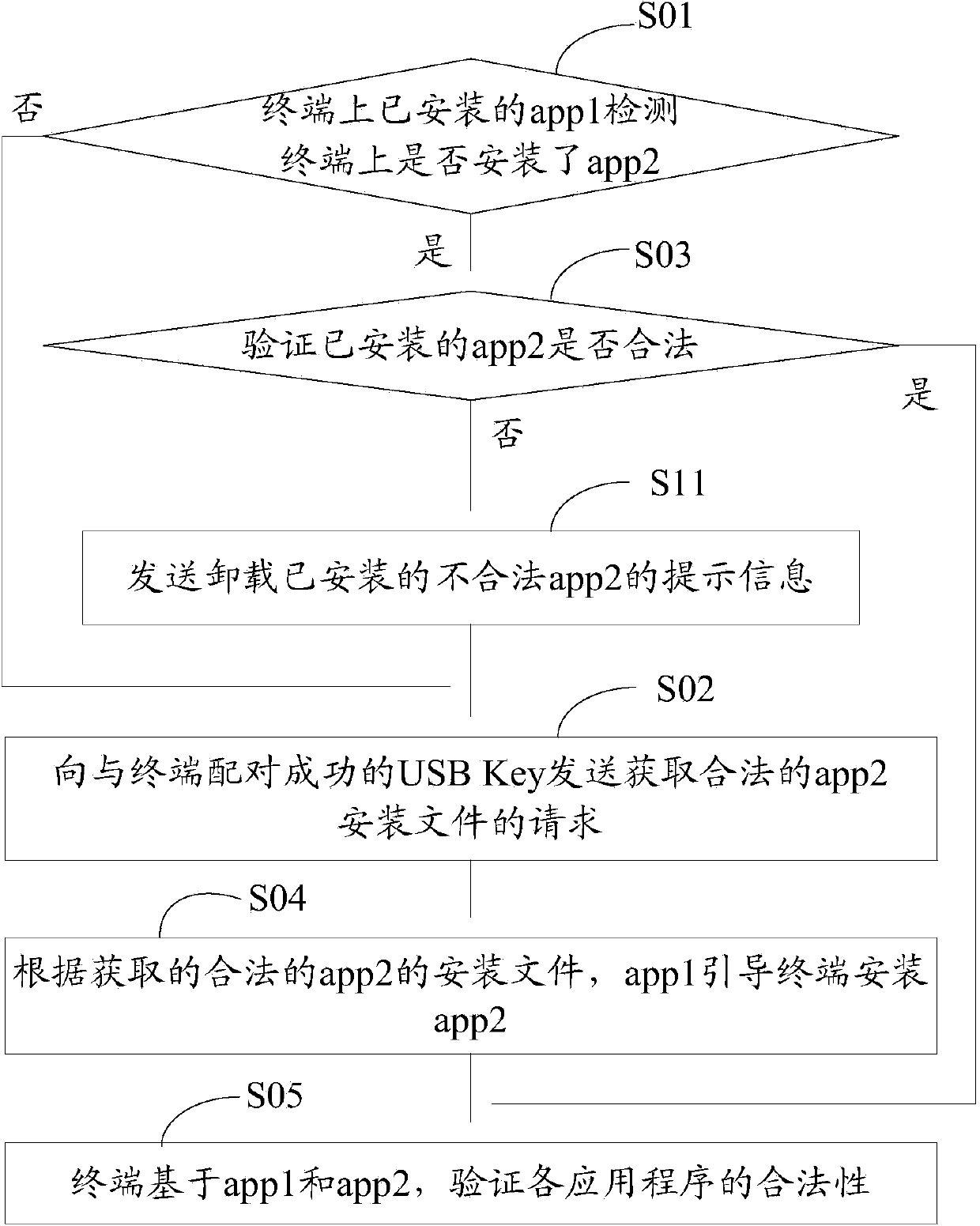
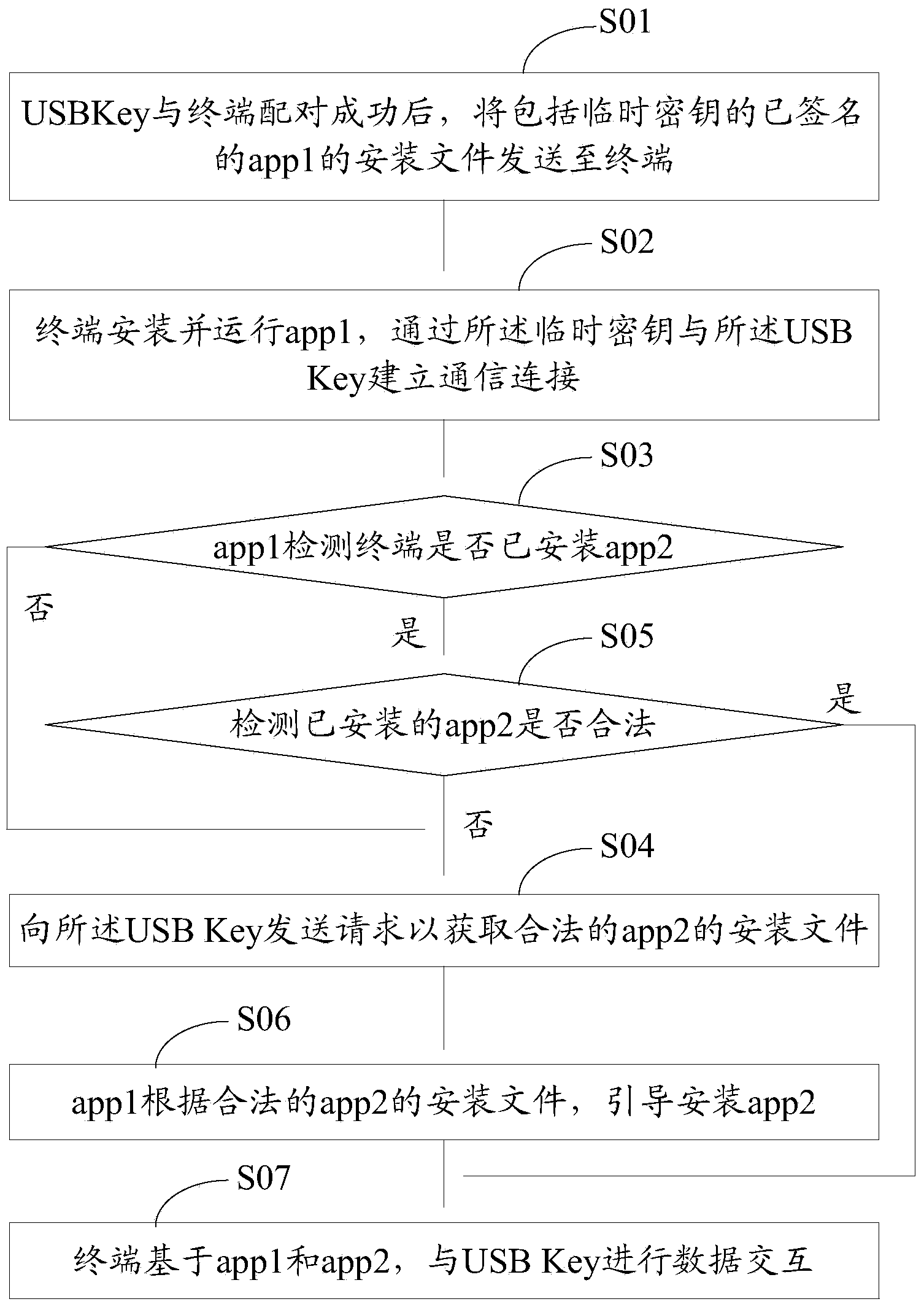
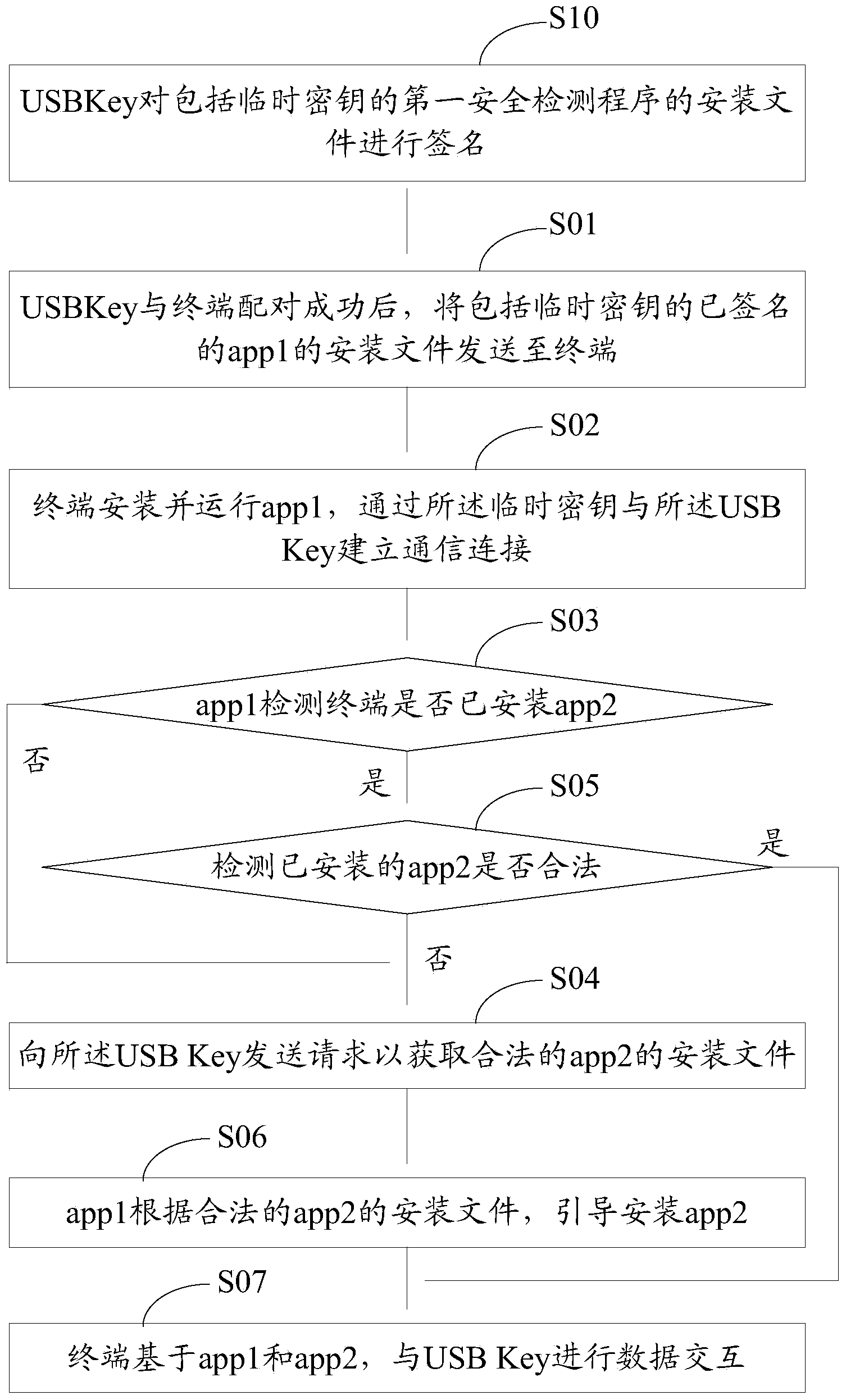
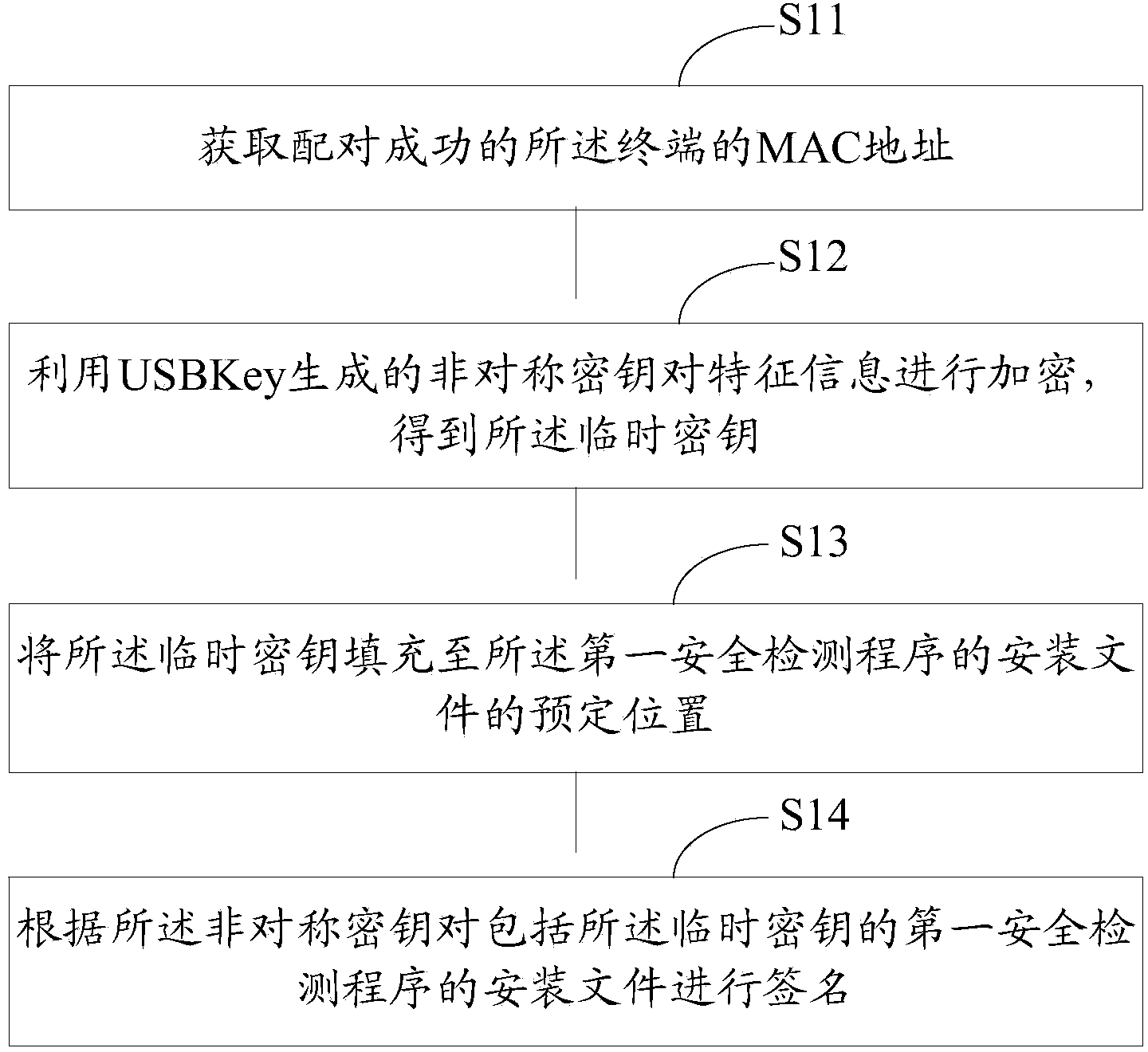
ActiveCN103473498AVerify legitimacyVerify securityDigital data authenticationTransmissionValidation methodsProgram security
The invention discloses an application program security verification method and a terminal. A reliable application program, namely a service management program is provided by a USB (universal serial bus) Key and used for verifying other application programs such as a security detection program on the terminal, so that validity and security of the application programs on the terminal are effectively verified, and the problem of security risks due to incapability of verifying validity of traditional application program download and installation is solved. The method has the advantages that security of the application programs on the terminal is improved, and further, security of personal information of users is ensured.
Owner:北京明华联盟科技有限公司
Information safety protecting method and system
InactiveCN103491080AVerify legitimacyIncrease legitimacyProgram/content distribution protectionSecuring communicationApplication securityUSB
The invention discloses an information safety protecting method and system. According to the information safety protecting method and system, a reliable application program, namely a first safety detection program, is provided through a USB Key, other application programs on a terminal are verified through the reliable application program, then the legality of the application programs on the terminal is effectively verified, the problem that potential safety hazards exist due to the fact that the legality of downloading and installation of traditional application programs can not be verified is avoided, safety of the application programs on the terminal is improved, and furthermore safety of personal information of a user is guaranteed.
Owner:SHENZHEN EXCELSECU DATA TECH
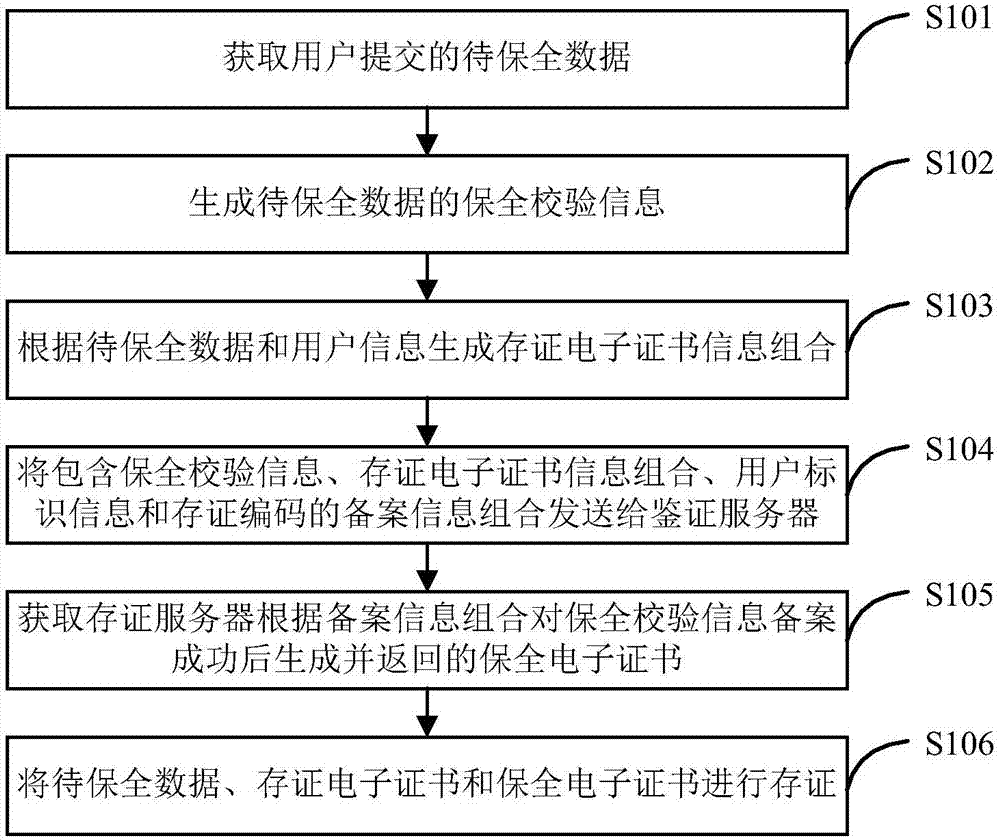
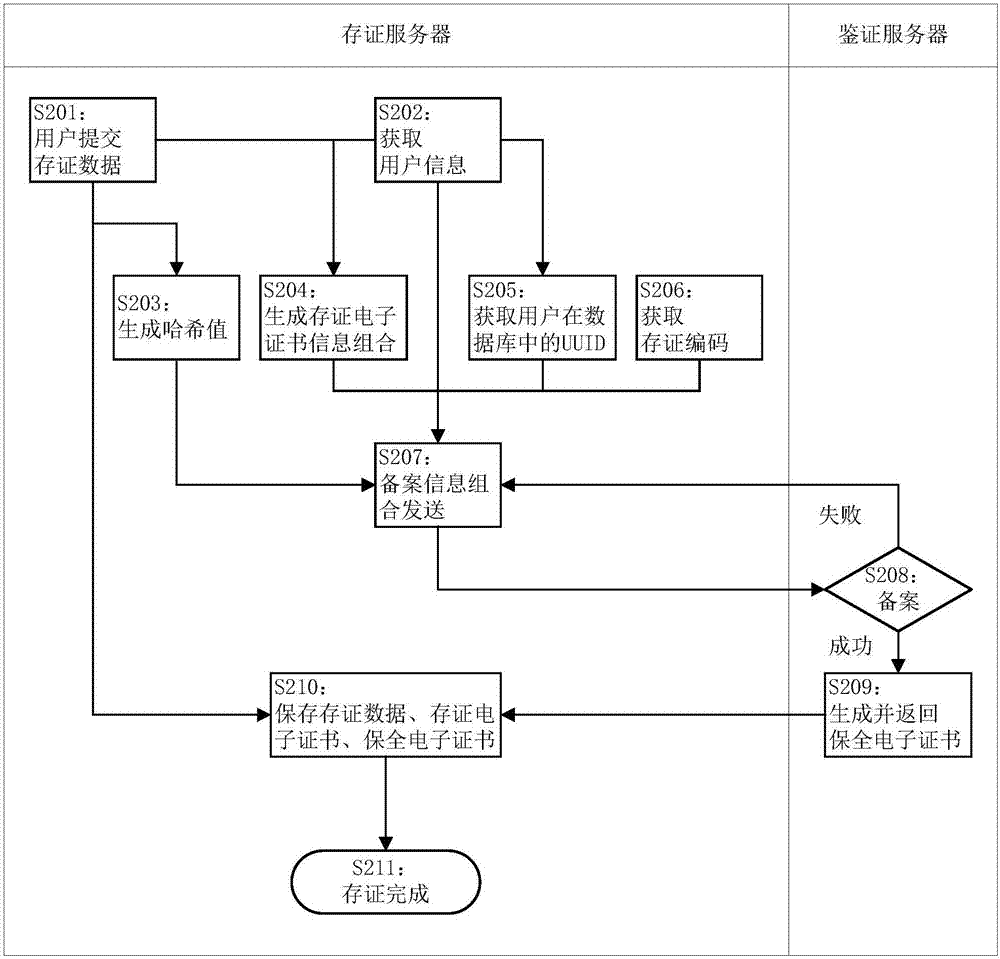
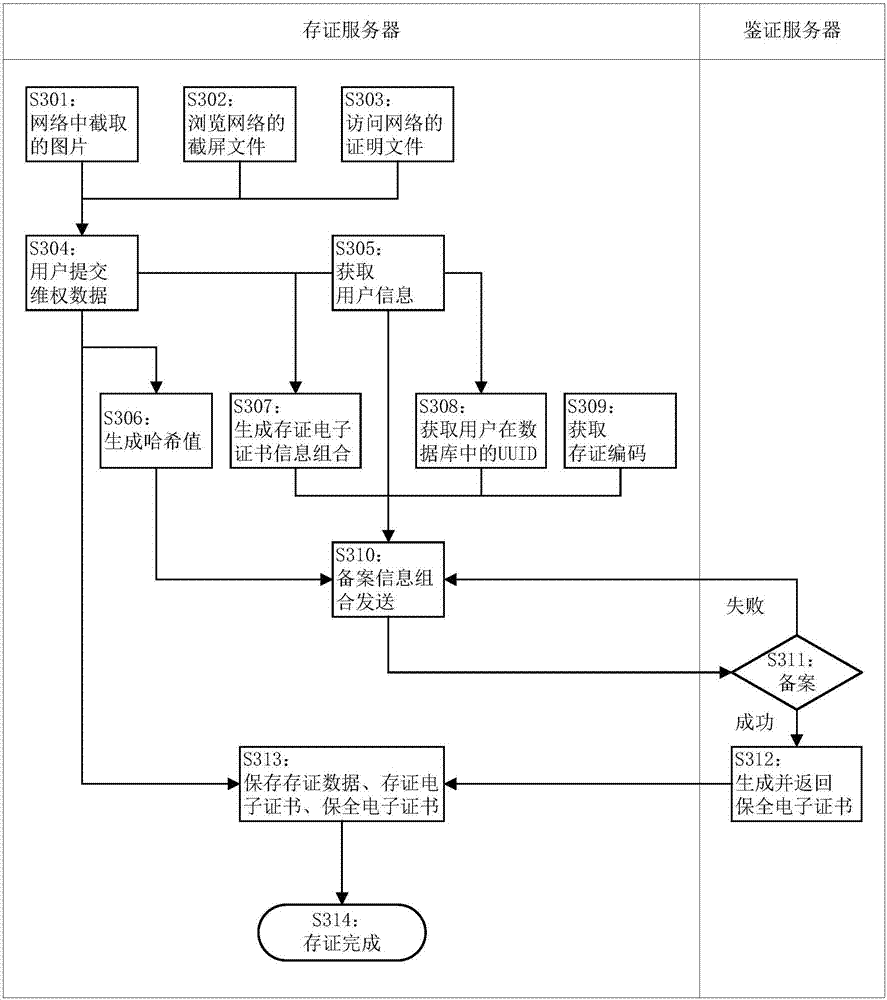
Method, system and device for internet data preservation
InactiveCN107070939AIncrease legitimacyImprove usabilityDigital data protectionTransmissionThe InternetAuthentication server
The invention discloses a method, a system and a device for internet data preservation. The method comprises the steps of obtaining to-be-preserved data submitted by a user and generating preservation verification information of the to-be-preserved data; generating storage electronic certificate information combination based on the to-be-preserved data and user information; sending a filing information combination including the preservation verification information, the storage electronic certificate information combination, user identification information and a preservation receipt code to an authentication server; obtaining a preservation electronic certificate which is generated and returned after the preservation verification information is filed successfully based on the filing information combination by the authentication server; and storing the to-be-preserved data, the storage electronic certification and the preservation electronic certificate. According to the method, the system and the device for internet data preservation, data issued by the user or obtained from the internet can be stored and preserved, the reliability of electronic evidences can be improved, and the electronic evidences can be stored and used conveniently.
Owner:国信嘉宁数据技术有限公司
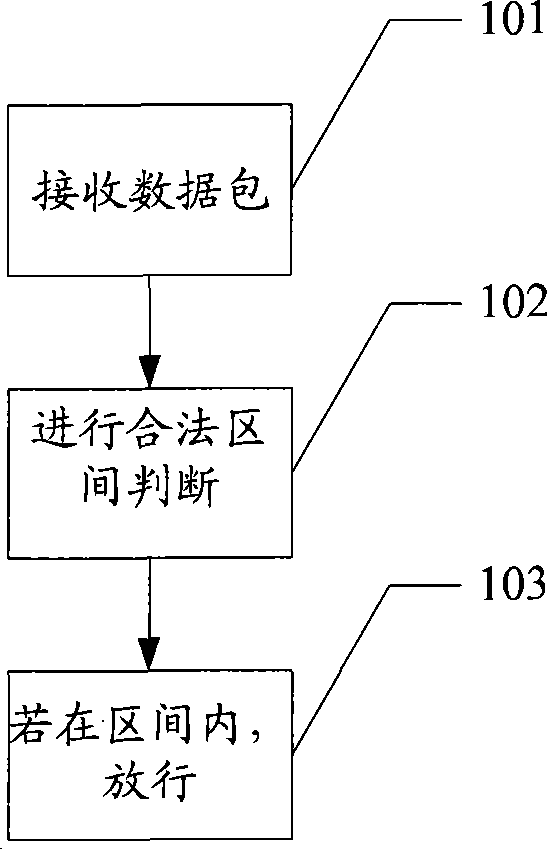
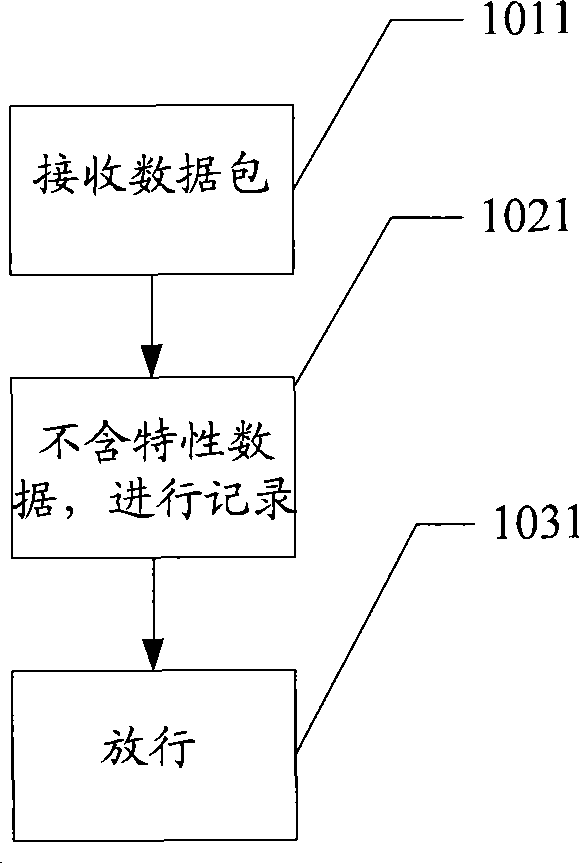
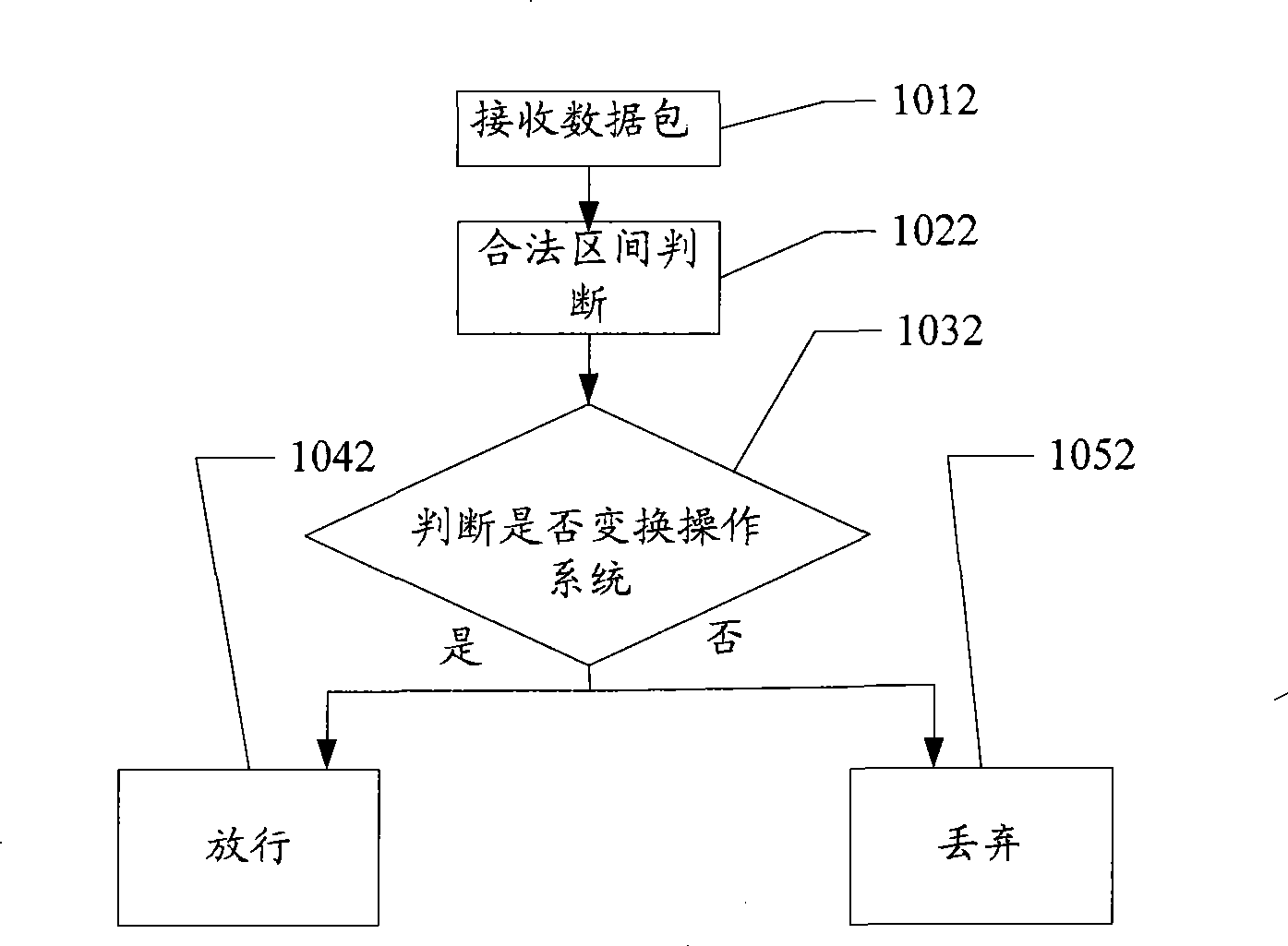
Security protection method, equipment and system for data packet
InactiveCN101453420AImprove reliabilityIncrease legitimacyData switching networksReal-time computingNetwork address translation
The invention provides a method, a device and a system for protecting a data packet safely. The method comprises the following steps: receiving the data packet sent by an outside network; judging whether the time to life (TTL) value of the data packet is in a legal interval or not if characteristic data of the data packet exists in a network address translation (NAT) protocol mapping table; and releasing the data packet if the TTL value of the data packet is in the legal interval. By adopting the method, the reliability for the security judging result of the data packet can be enhanced.
Owner:HUAWEI DIGITAL TECH (CHENGDU) CO LTD
Method and system for preventing tampering with advertising content
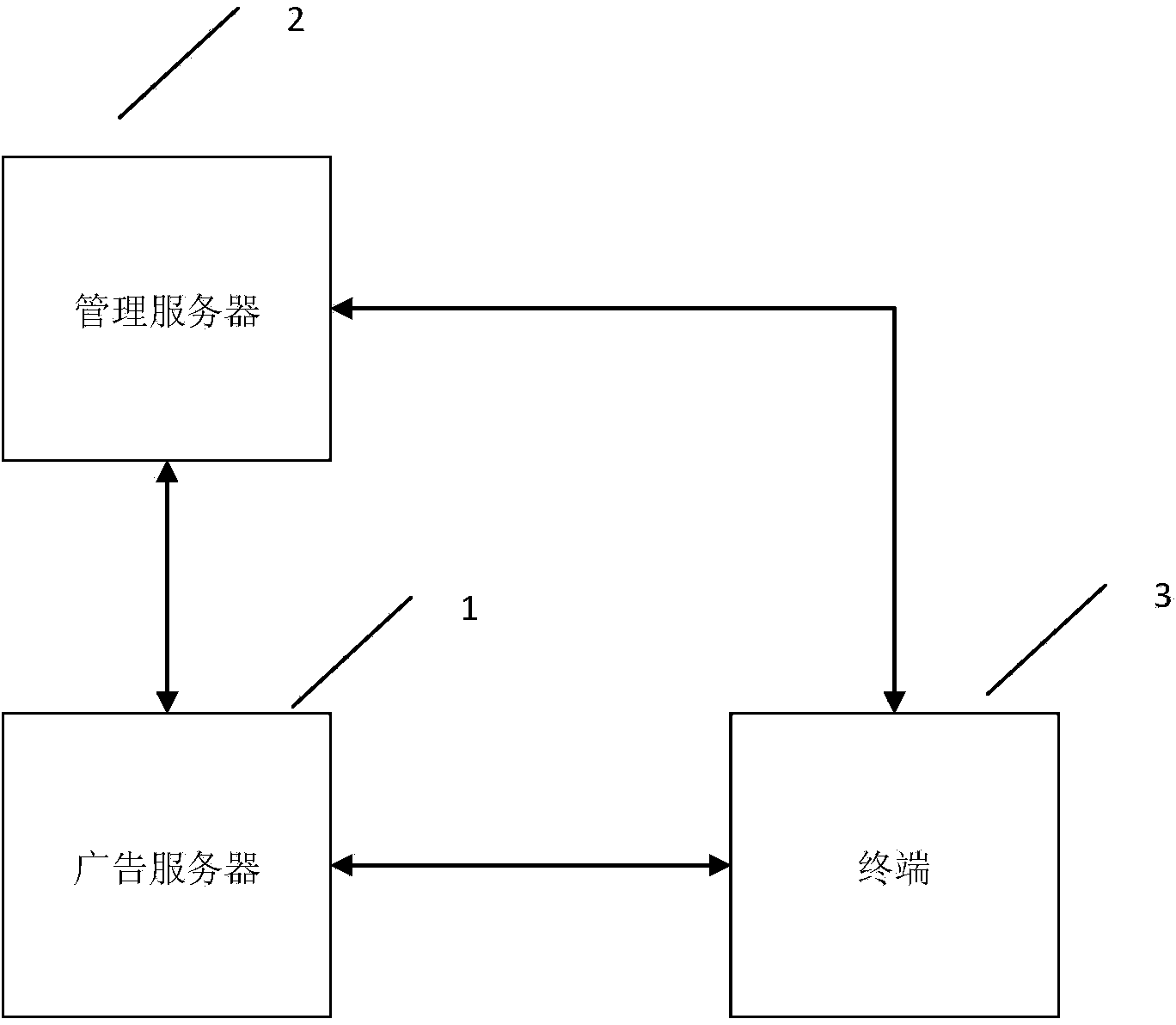
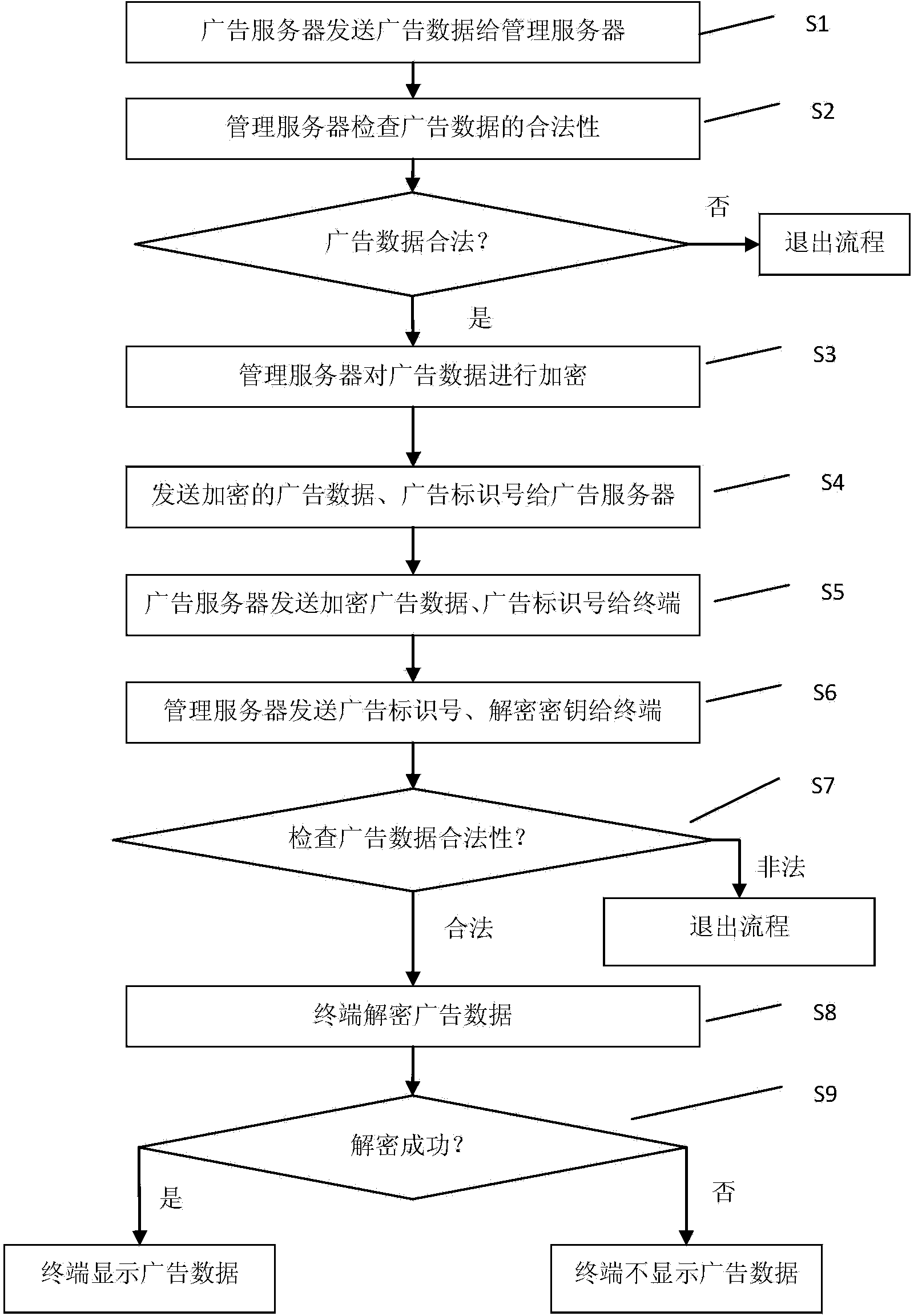
ActiveCN104244031AGuaranteed legalityIncrease legitimacySelective content distributionComputer terminalWorld Wide Web
The invention provides a method and system for preventing tampering with advertising content. The method includes the steps that first, an advertising server sends advertising data to a management server; second, the management server checks the legality of the advertising data; third, the management server encrypts the advertising data and generates encrypted advertising data, an advertising identification number and a decryption key; fourth, the management server sends the encrypted advertising data and the advertising identification number to the advertising server; fifth, the advertising server sends the encrypted advertising data and the advertising identification number to a terminal; sixth, the management server sends the advertising identification number and the decryption key to the terminal; seventh, the terminal checks the legality of the advertising data; eighth, the terminal decrypts the encrypted advertising data with the decryption key; ninth, the terminal displays the advertising data after successfully decrypting the advertising data. The method and system for preventing tampering with advertising content have the advantages of being capable of effectively preventing tampering with the advertising content and being high in safety performance.
Owner:SHANDONG TAIXIN ELECTRONICS CO LTD
Hamilton quantum arbitration signature and verification method based on quantum blind calculation
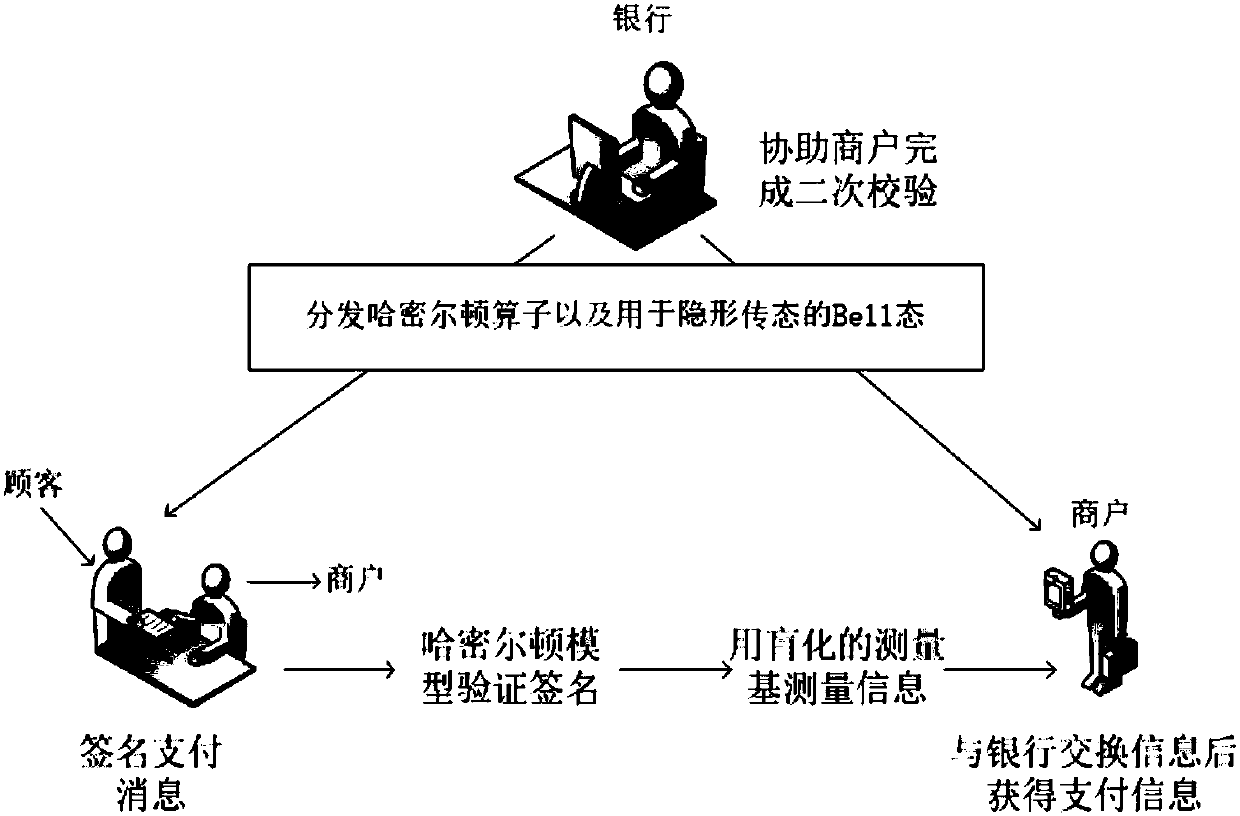
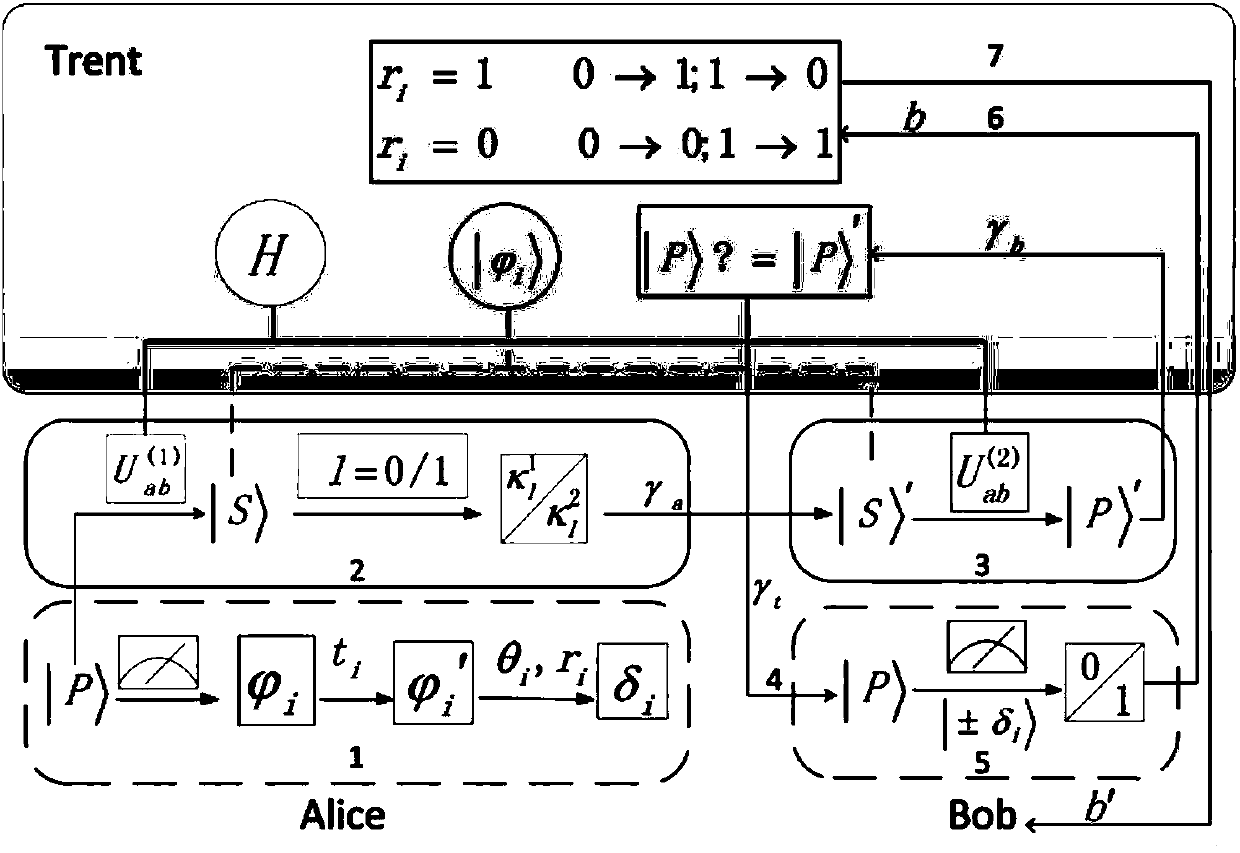
ActiveCN107947941AImprove securityEnhanced anonymityKey distribution for secure communicationUser identity/authority verificationPaymentValidation methods
The invention discloses a Hamilton quantum arbitration signature and verification method based on quantum blind calculation, which comprises the following steps that a third communicator distributes aHamilton model to a first communicator and a second communicator; the first communicator prepares to-be-signed information represented by n quantum bit strings; the first communicator conducts quantum blind calculation on the to-be-signed information to obtain a measurement base; the first communicator signs the to-be-signed information by utilizing the Hamilton model; the second communicator conducts un-signing by utilizing the Hamilton model to obtain a verification quantum bit string; the third communicator verifies whether the first communicator is legal or not by verifying whether the to-be-signed information and the verification quantum bit string are the same or not; if legal, the second communicator uses the measurement base to measure the verification quantum bit string so as toobtain a measurement result; and the third communicator controls whether the measurement result is transposed or not according to the stored control parameters to obtain binary mode payment information. According to the Hamilton quantum arbitration signature and verification method based on quantum blind, the safety of the signature verification process is improved, and a verifier verifies the signature without the need for restoring the original information.
Owner:CENT SOUTH UNIV
Demodulation decoding integrated digital television broadcasting program safety authentication method
InactiveCN101141618ABlock receptionTimely updatePulse modulation television signal transmissionAnalogue secracy/subscription systemsSoftware engineeringSecure authentication
The present invention relates to a method for the safety certification of a digital television broadcasting program. At present, the safety certification to the program is mainly realized through the software configuration, and the security is low. The method of the present invention has the procedures that a preset legal program name is wrote in a ROM; a PST chart is abstracted, and the mapping of a program number of each program and the PID value of a PMT chart are established; a SDT chart is abstracted, and the mapping between the program number and the program name of each program; the corresponding program number of each legal program is detected; the PMT chart of the legal program is abstracted, and the audio and video PID value is decoded; a corresponding TS package of the legal program is identified, and then transmitted to the back level. The method of the present invention integrates a safety certification filter in a digital television demodulator and a decoder, while the legality of program information is checked, the cost is low, therefore ensuring that the TS stream of a flow message source decoder only contains legal contents already checked and passed.
Owner:HANGZHOU NATCHIP SCI & TECH
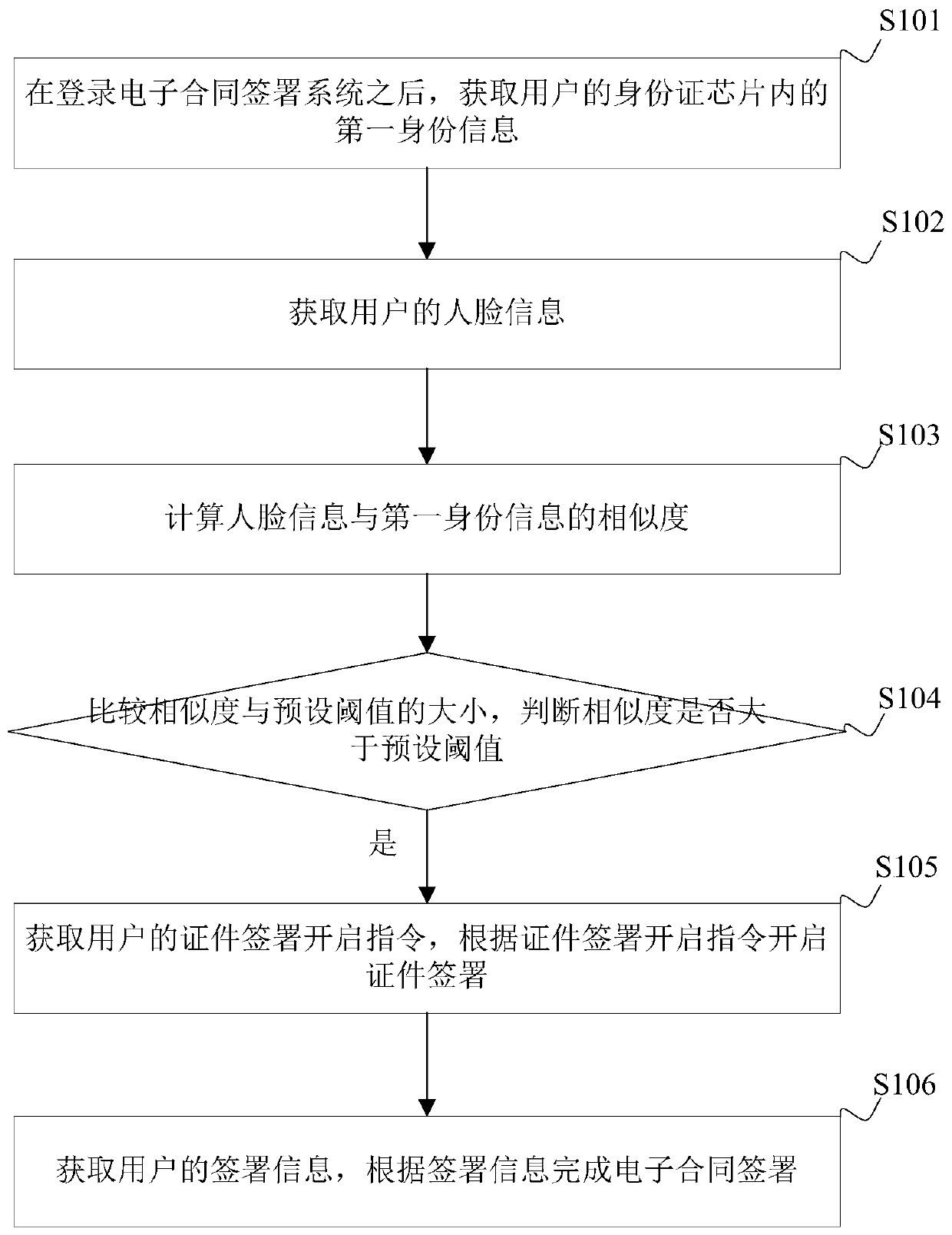
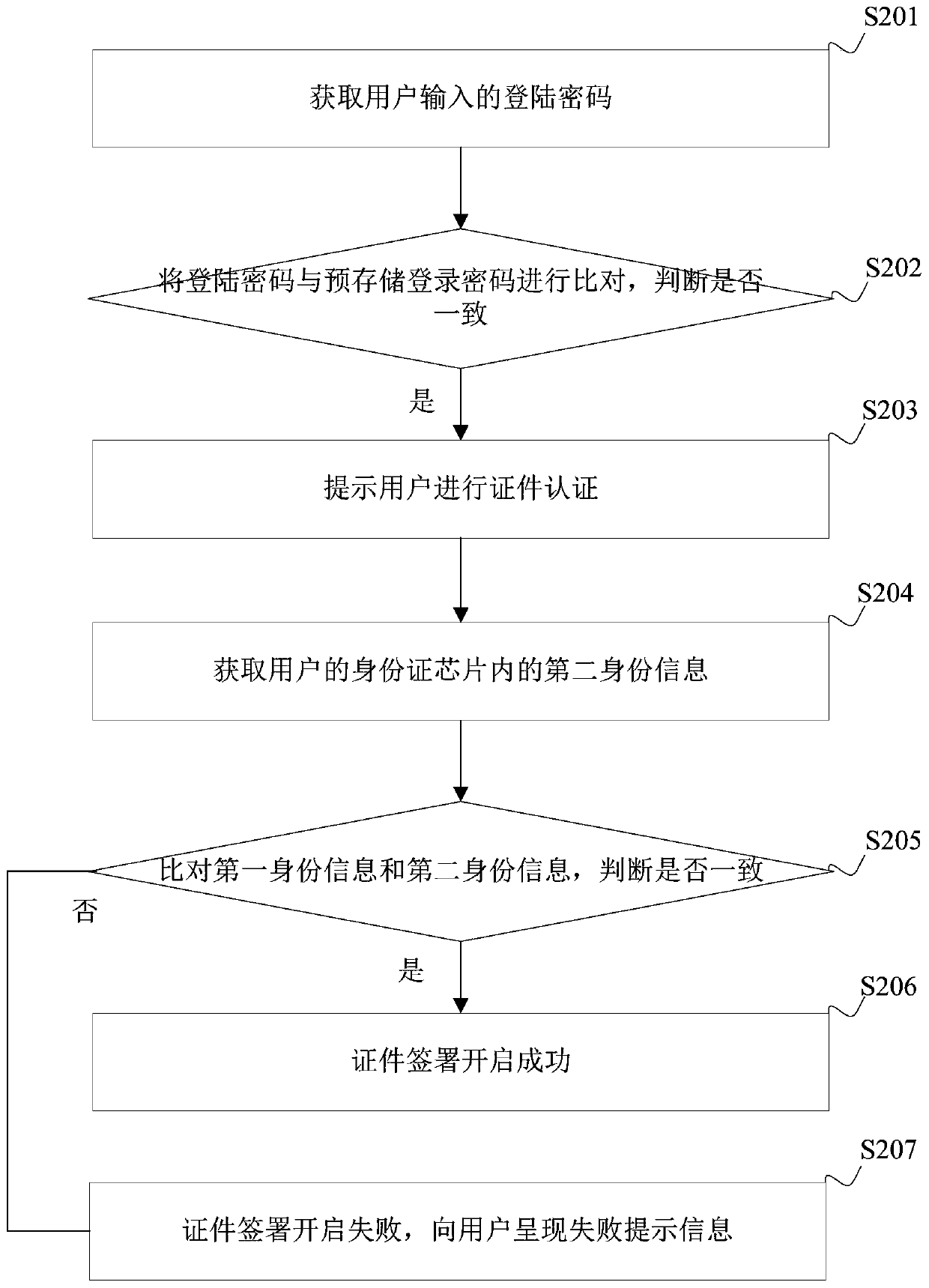
Electronic contract signing method and device, terminal device and storage medium
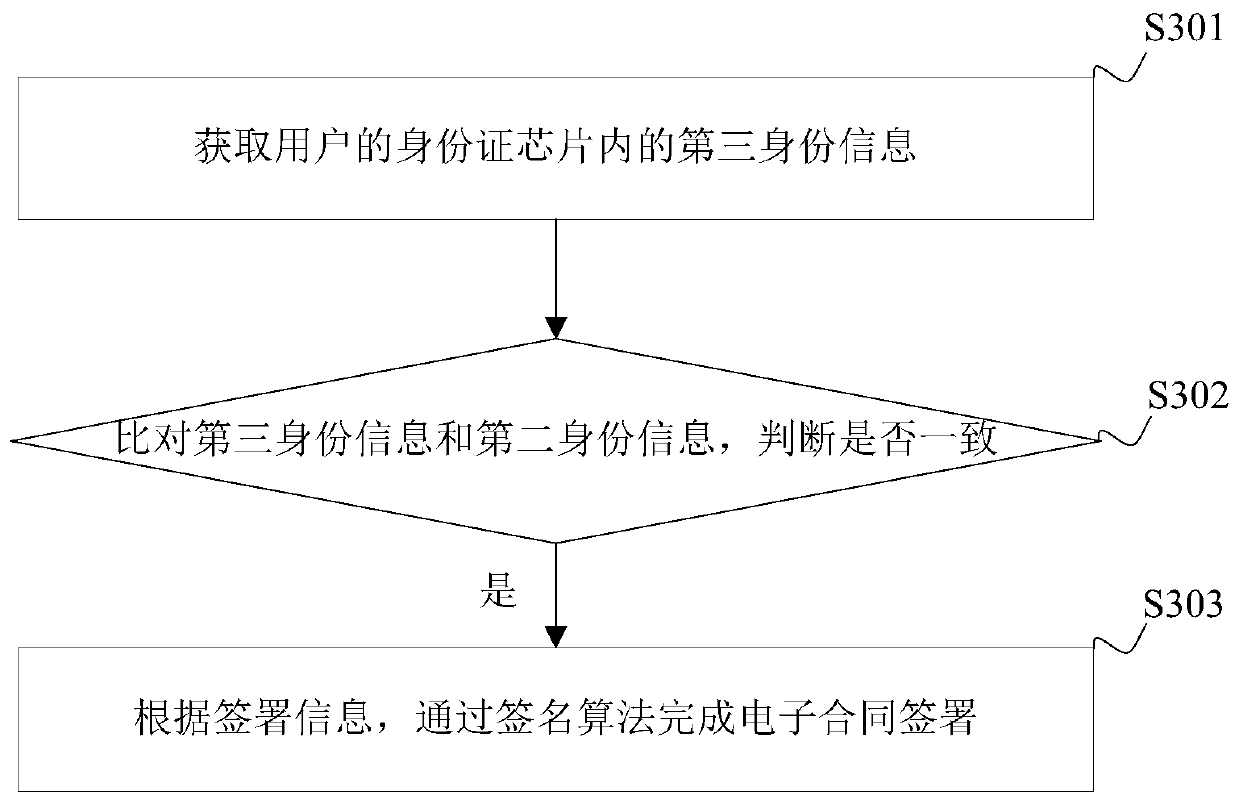
InactiveCN109858220AImprove securityIncrease credibilityData processing applicationsDigital data authenticationElectronic contractsTerminal equipment
The embodiment of the invention is applicable to the technical field of electronic commerce, and discloses an electronic contract signing method and device, a terminal device and a computer readable storage medium. The method comprises the steps: obtaining first identity information in an identity card chip of a user after logging in an electronic contract signing system; obtaining face information of a user; calculating the similarity between the face information and the first identity information; comparing the similarity with a preset threshold value; when the similarity is greater than a preset threshold, determining that the real-name authentication is successful; obtaining a certificate signing starting instruction of the user, and starting certificate signing according to the certificate signing starting instruction; signing information of the user is acquired, and electronic contract signing is completed according to the signing information. According to the embodiment of the invention, the security of electronic contract signing can be improved.
Owner:深圳法大大网络科技有限公司
Overall traceable high-voltage electric energy meter calibrating device
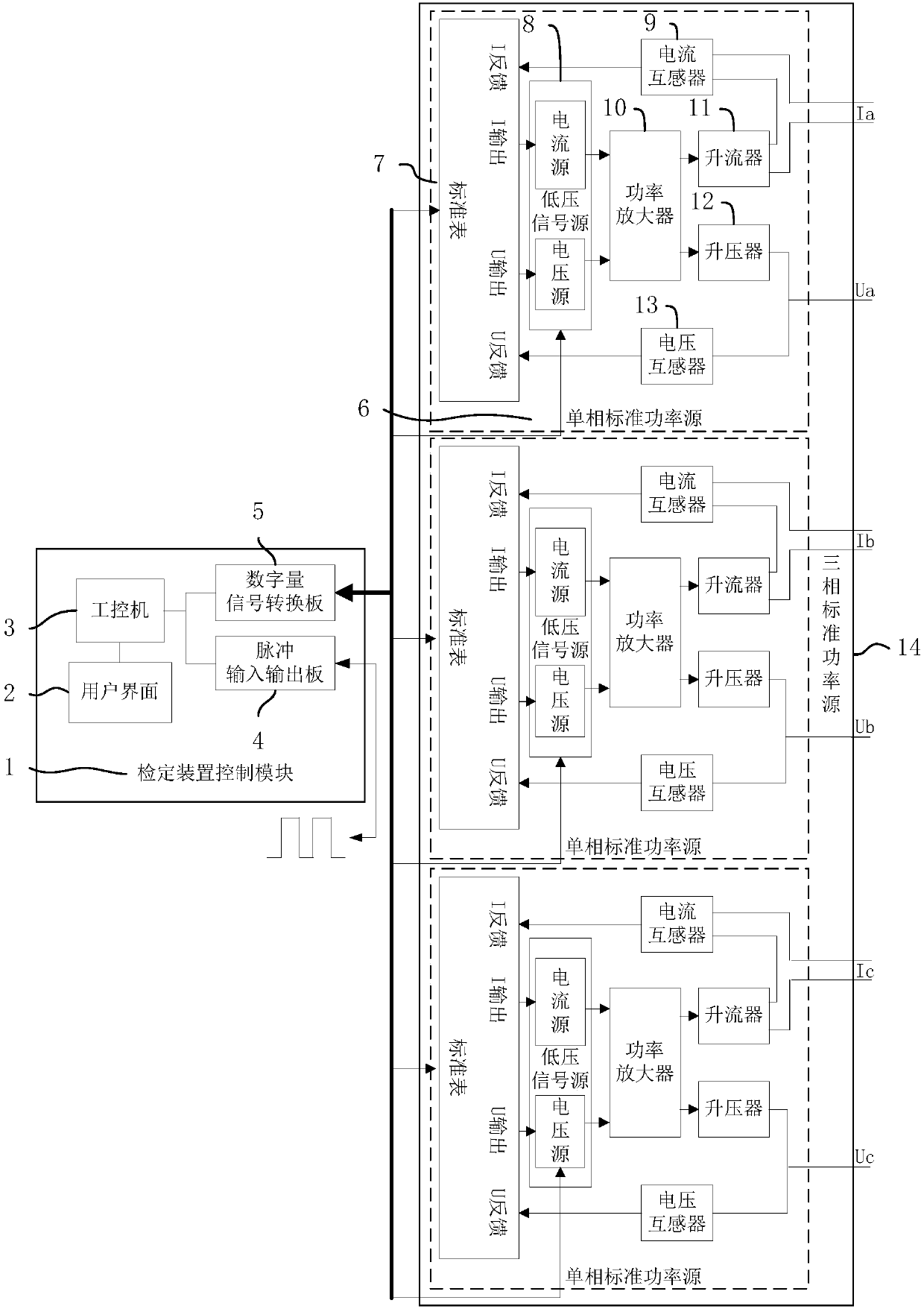
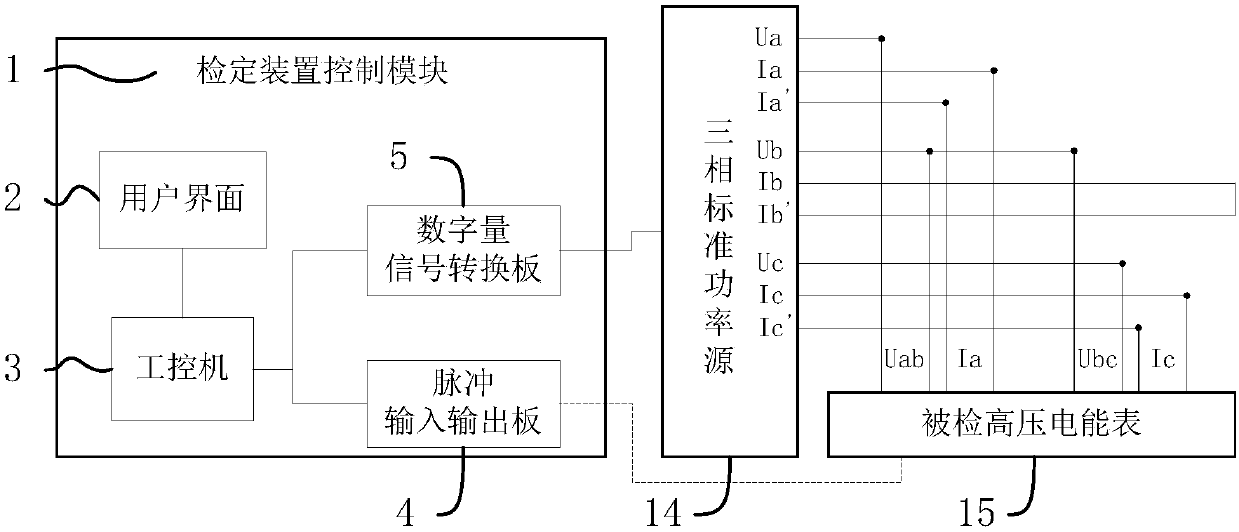
PendingCN107748348AAvoid cumbersome connectionsAvoid cumbersomeElectrical testingTerminal voltageLow voltage
An overall traceable high-voltage electric energy meter calibrating device disclosed by the present invention mainly comprises a calibrating device control module and a three-phase standard power source, the calibrating device control module mainly comprises an industrial control computer, a user interface connected with the industrial control computer, a digital signal converting board and a pulse input-output board, and the three-phase standard power source comprises three single-phase standard power sources which are mutually independent and of which the structures are same. Each single-phase standard power source mainly comprises a standard meter, a low-voltage signal source, a power amplifier, a strong current generator, a booster, a current transformer and a voltage transformer. Theoutput end of the strong current generator and the primary side of the current transformer form a current output loop, the secondary side of the current transformer is connected with the standard meter, the output end of the booster is used as a voltage output end and is connected with the standard meter via the voltage transformer, and the standard meters of each single-phase standard power source are all connected with the digital signal converting board mutually. According to the present invention, a high-voltage electric energy meter can be calibrated overall, and the precision of the calibrating device can be traced overall.
Owner:HUAINAN POWER SUPPLY CO OF STATE GRID ANHUI ELECTRIC POWER CORPORATIO +2
A sample generation method and device
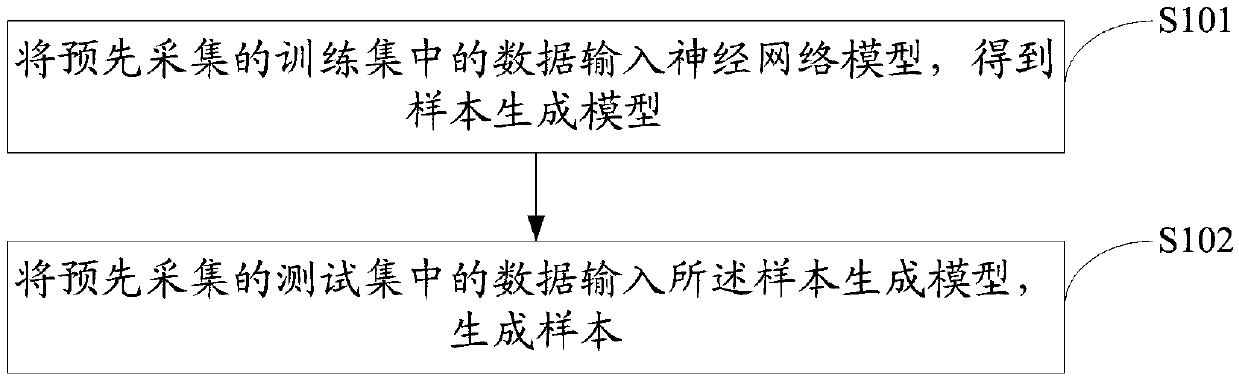
ActiveCN109598334ASmall training lossHigh legitimacy and diversitySoftware testing/debuggingNeural architecturesData entryNetwork model
The invention discloses a sample generation method and device. The method comprises the steps: inputting data in a pre-collected training set into a neural network model, obtaining a sample generationmodel, and enabling the neural network model to be a neural network model employing an attention mechanism; Inputting pre-collected data in the test set into the sample generation model to generate asample. According to the invention, a neural network model of an attention mechanism is adopted; the neural network model can endow characters in the input data with different weights; Therefore, data information in the input data can be learned more selectively, data with high correlation with the current output data in the input data can be found, a high-precision deep learning model can be finally obtained, training loss is low, and samples generated by the high-precision deep learning model are inevitably higher in legality and diversity.
Owner:CHINA INFORMATION TECH SECURITY EVALUATION CENT
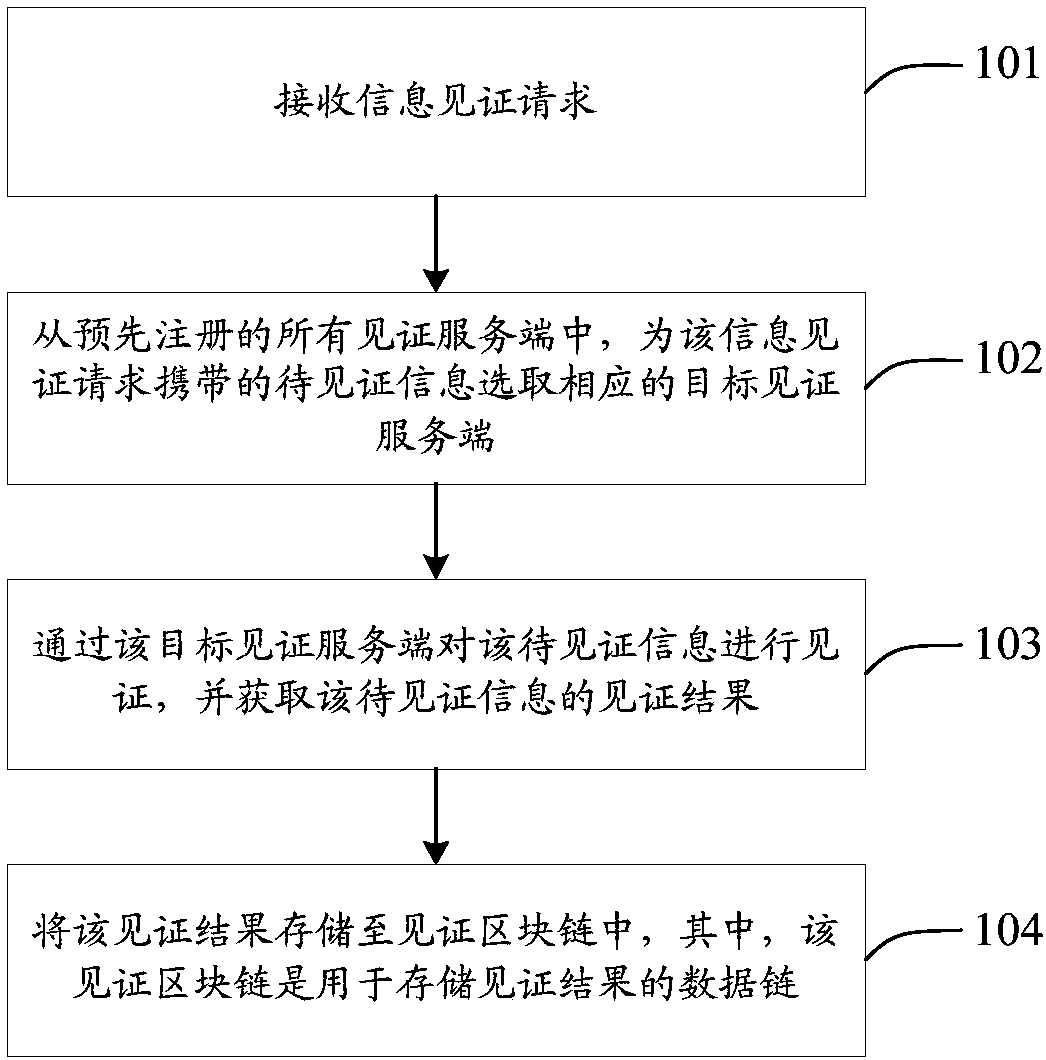
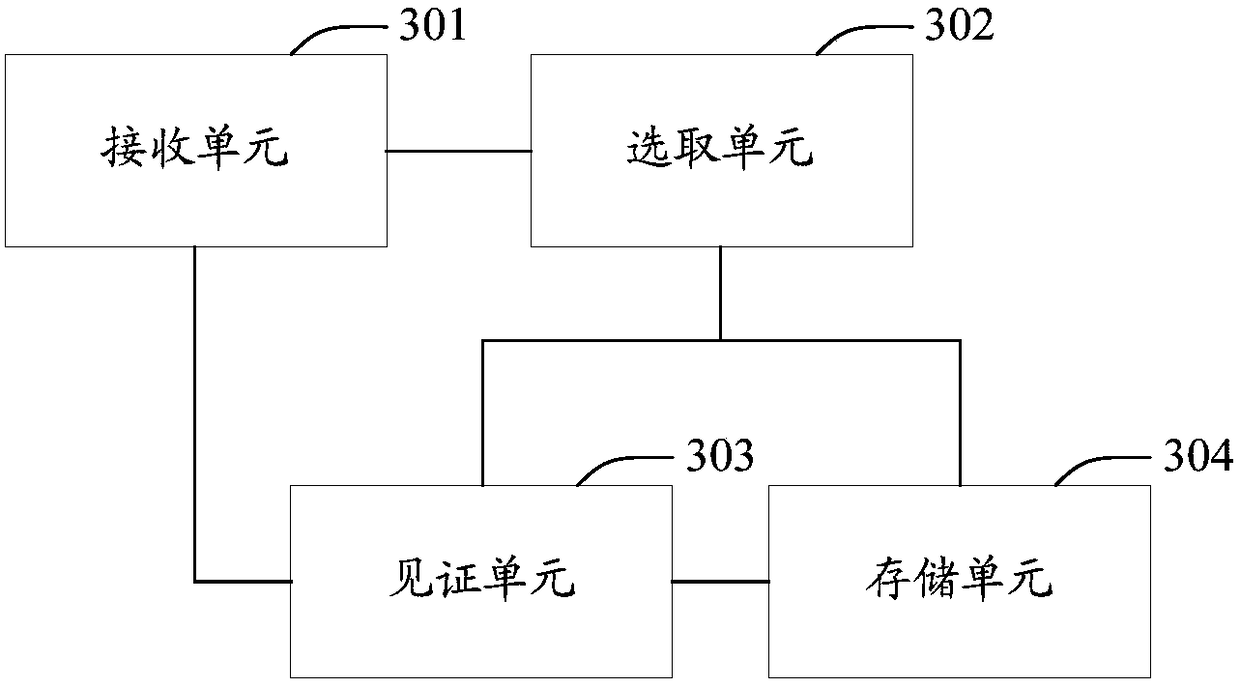
Information witness method and device
ActiveCN108390848AImprove securityImprove experienceUser identity/authority verificationInformation securityWorld Wide Web
The invention discloses an information witness method and device. The method specifically includes the following steps: enabling an information witness platform to receive an information witness request; selecting a target witness server for information to be witnessed carried in the information witness request from all witness servers that are registered in advance; witnessing the information tobe witnessed through the target witness server to obtain a witness result; and storing the witness result in a witness blockchain. Even if multiple information to be witnessed exists, users do not need to witness the information at different witness servers respectively, the operation of automatically selecting the target witness server can be triggered through the mode of initiating the information witness request, user operations can be reduced, the witness process can be simplified, and the witness efficiency and user experience can be improved; and in addition, the witness result is storedin the witness blockchain, and thus the witness result cannot be easily tampered with, the accuracy and legitimacy of the witness result can be ensured, and moreover, even if the witness servers areattacked, the witness result stored in the witness blockchain cannot be leaked, and the information security can be improved.
Owner:BEIJING 21VIANET DATA CENT +1
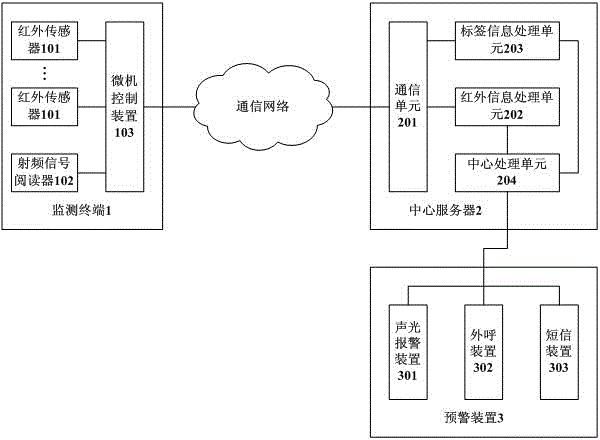
Power distribution room safety monitoring system based on infrared sensing
InactiveCN104361705AIncrease legitimacyRealize automatic monitoringBurglar alarm electric actuationBurglar alarm short radiation actuationRadio frequency signalEngineering
The invention relates to a power distribution room safety monitoring system based on infrared sensing. The system comprises a monitoring terminal, a center server and a pre-warning device. The monitoring terminal comprises an infrared sensor, a radio frequency signal reader and a microcomputer control device; the infrared sensor is used for detecting whether a person enters a power distribution room and transmitting detected infrared information to the microcomputer control device; the radio frequency signal reader is provided with a transmitting antenna and is used for detecting whether a recognizable tag exists in a work area and transmitting collected tag information to the microcomputer control device; the microcomputer control device is used for receiving information sent by the infrared sensor and the radio frequency signal reader and transmitting the information to the center server. The center server is used for receiving the information sent by the monitoring terminal, judging whether the person entering the power distribution room is authorized and carrying out related operations according to the judgment result. The pre-warning device is used for sending out prewarning information once triggered by the center server when an unauthorized person enters the power distribution room. The system can automatically monitor validity of the person entering the power distribution room and safety of the power distribution room is improved.
Owner:STATE GRID CORP OF CHINA +2
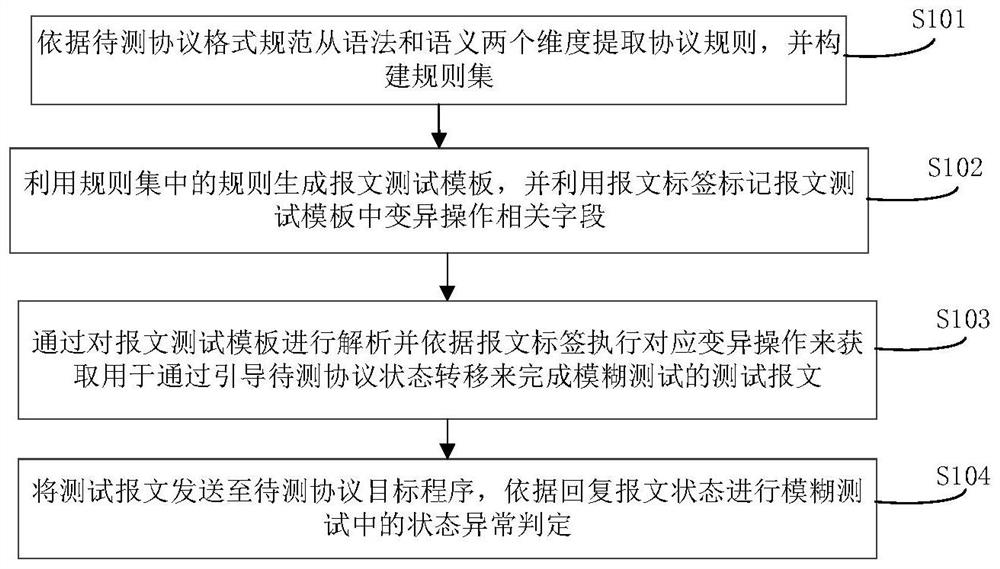
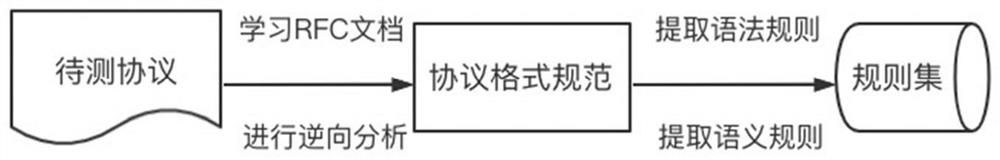
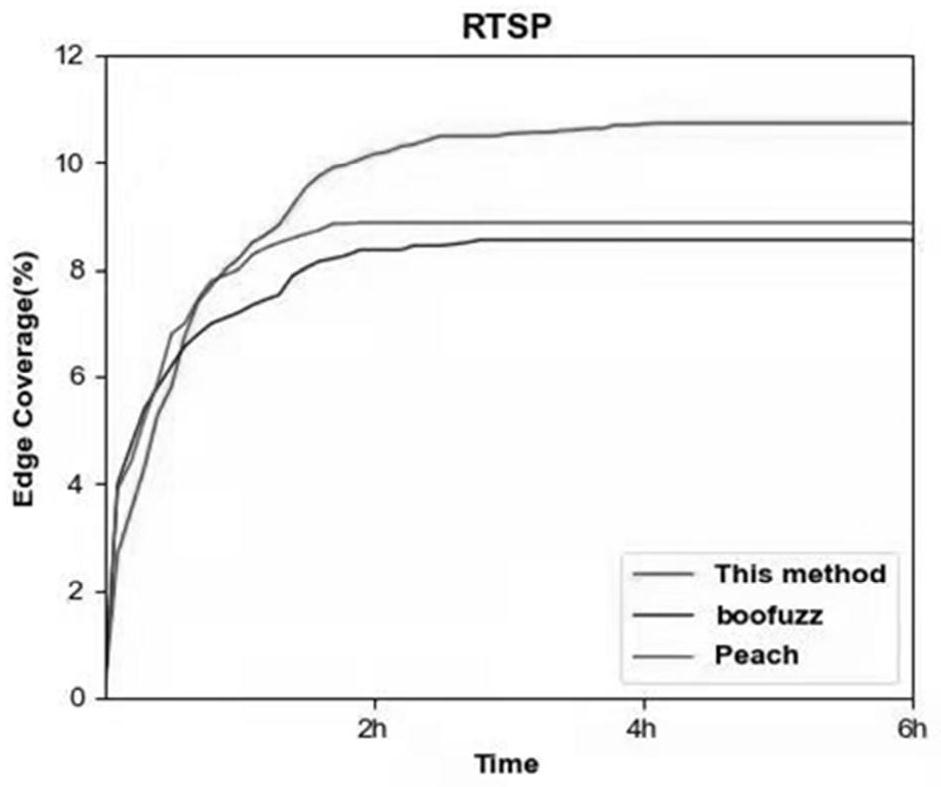
Fuzzy test method and system for stateful network protocol
ActiveCN114650163AIncrease legitimacyAvoid Program Validation FailuresSecuring communicationHigh level techniquesTest efficiencyNetworking protocol
The invention belongs to the technical field of network space security testing, and particularly relates to a stateful network protocol-oriented fuzzy testing method and system.The stateful network protocol-oriented fuzzy testing method comprises the steps of extracting protocol rules from grammar and semantic dimensions according to protocol format specifications to be tested, and constructing a rule set; generating a message test template by using rules in the rule set, and marking variation operation related fields in the message test template by using a message label; analyzing the message test template and executing a corresponding mutation operation according to the message label to obtain a test message for finishing a fuzzy test by guiding the state transition of the protocol to be tested; and sending the test message to the to-be-tested protocol target program, and performing state abnormity judgment in the fuzzy test according to the reply message state. According to the method and the device, the legality of the test message can be improved, the condition of program verification failure caused by variation of special fields is avoided, the test message can be used for testing and can also be used for replacing an auxiliary message to guide protocol state transition, the test efficiency is improved, and system resources are saved.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
Automatically maintained image updating system and method therefor
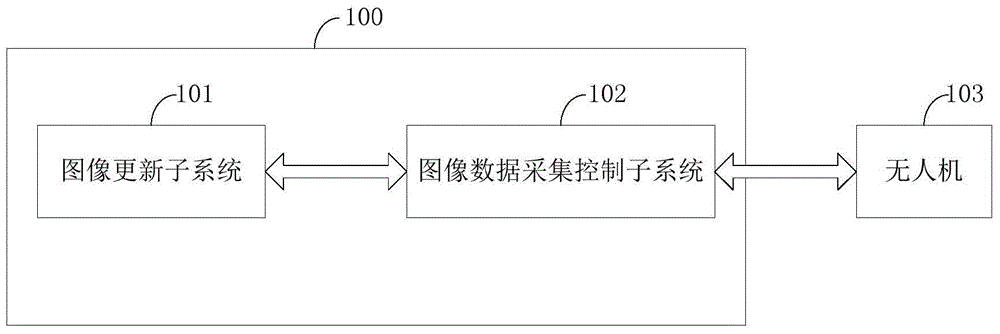
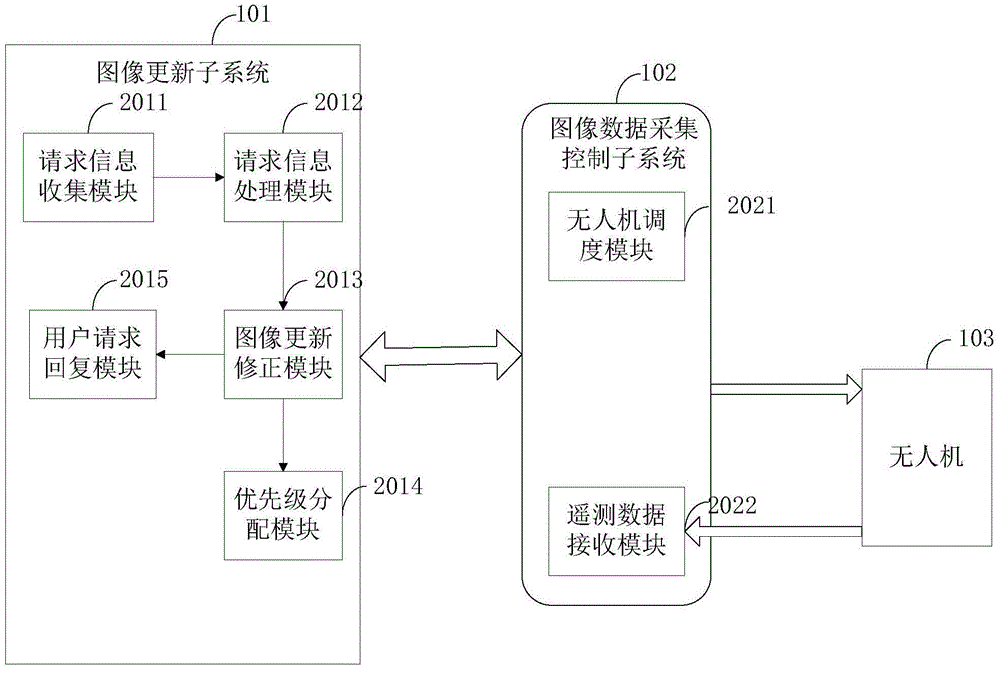
InactiveCN104992174ASolve the problem of data collectionIncrease legitimacyCharacter and pattern recognitionComputer visionData mining
The present invention discloses an automatically maintained image update system and a method therefor and belongs to the field of image information technologies. The system comprises an image updating subsystem and an image data collection control subsystem, wherein the image updating subsystem is used to collect request information of a user, perform classification processing on the request information according to a preset mechanism, and send a data updating demand to the image data collection control subsystem; and the image data collection control subsystem assigns image collection tasks to appropriate unmanned aerial vehicles according to the preset rule and receives returned telemetry data. According to the method, by combining an information feedback mechanism of the user with a checking mechanism of image data, in addition to receiving an instruction of an operator, the system also can respond to the feedback of the user and intelligently performs processing on sensitive image information, so that the legality, reliability and validity of image information collection are effectively improved.
Owner:高域(北京)智能科技研究院有限公司
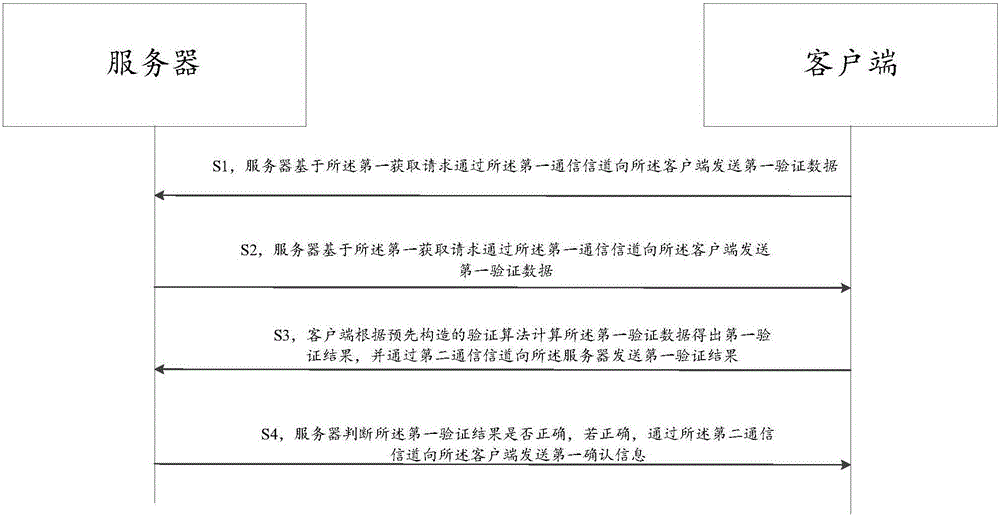
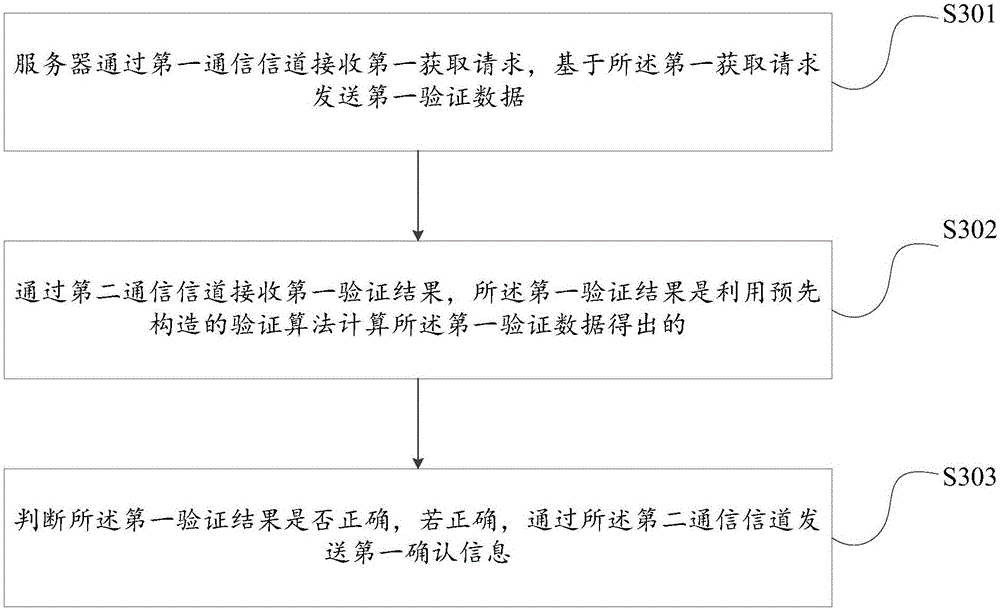
Verification method and system
InactiveCN106453418AIncreased complexityIncrease legitimacyTransmissionValidation methodsClient-side
The invention provides a verification method and system. The method comprises the following steps: receiving a first obtaining request by a server through a first communication channel, sending first verification data on the basis of the first obtaining request; receiving a first verification result through a second communication channel, wherein the first verification result is obtained by using pre-constructed verification algorithm to calculate the first verification data; judging whether the first verification result is correct, if the first verification result is correct, sending first confirmation information through the second communication channel, wherein the first communication channel and the second communication channel are established according to different communication protocols; and the verification algorithm contains logic of operation, circulation, skip and address change. In this way, the complexity of the verification algorithm is improved, HACK does not find out a code of the corresponding algorithm from the network easily, the validity of the client can be verified more accurately, and in the verification process, the safety of the verification process is further improved by using two different communication channels to perform the data interaction.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
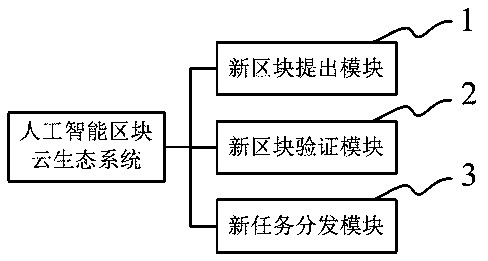
Artificial intelligence block cloud ecosystem based on DABFT consensus mechanism
ActiveCN109120437AIncrease legitimacyImprove fairnessData switching networksByzantine fault toleranceNODAL
The invention provides an artificial intelligence block cloud ecosystem based on a DABFT consensus mechanism. The artificial intelligence block cloud ecosystem based on a DABFT consensus mechanism includes a new block proposing module and a new block verification module, wherein the new block proposing module is used to allocate a set of task verification nodes and task processing nodes for a newtask when a new task issuing request is received, and the task processing nodes propose a new block; the new block verification module is used to verify the proposed new block by means of the DABFT consensus mechanism to determine the validity of the new block; through deep learning based on artificial intelligence, by means of a set of effectiveness evaluation algorithms, the DABFT consensus mechanism determines the optimal Byzantine fault tolerance mode of the new task; and DABFT is further enhanced by the addition of adaptive features, is a delegation mechanism with higher efficiency, and can select a BFT that is best suited for dynamic and parallel tasks. The adaptability is achieved through the deep learning technique, and selection of the real-time consistency algorithm for the new task is derived from a training model of previous tasks.
Owner:上海幼鸢网络科技有限公司
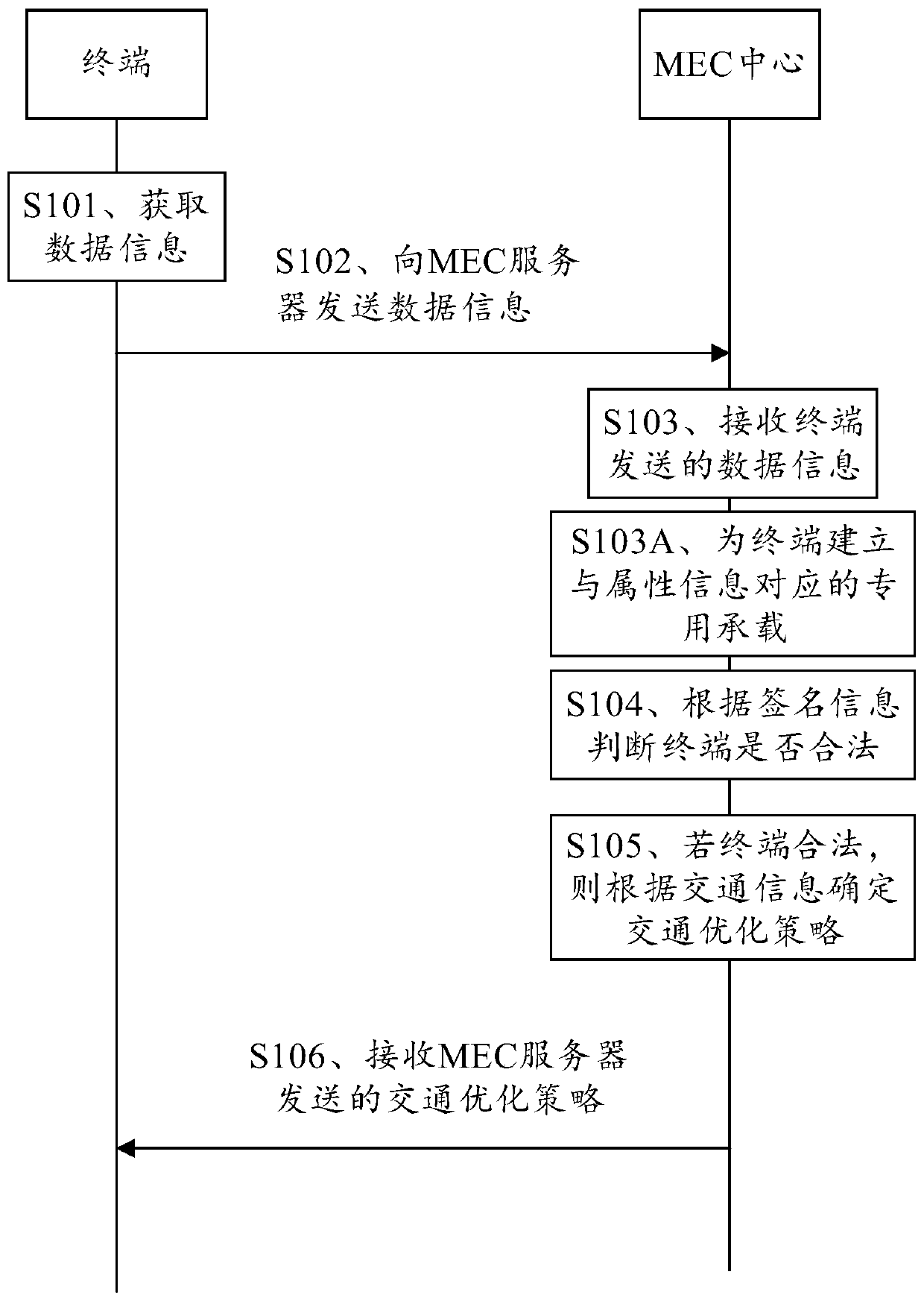
Vehicle-road cooperative management method, MEC server, terminal and system
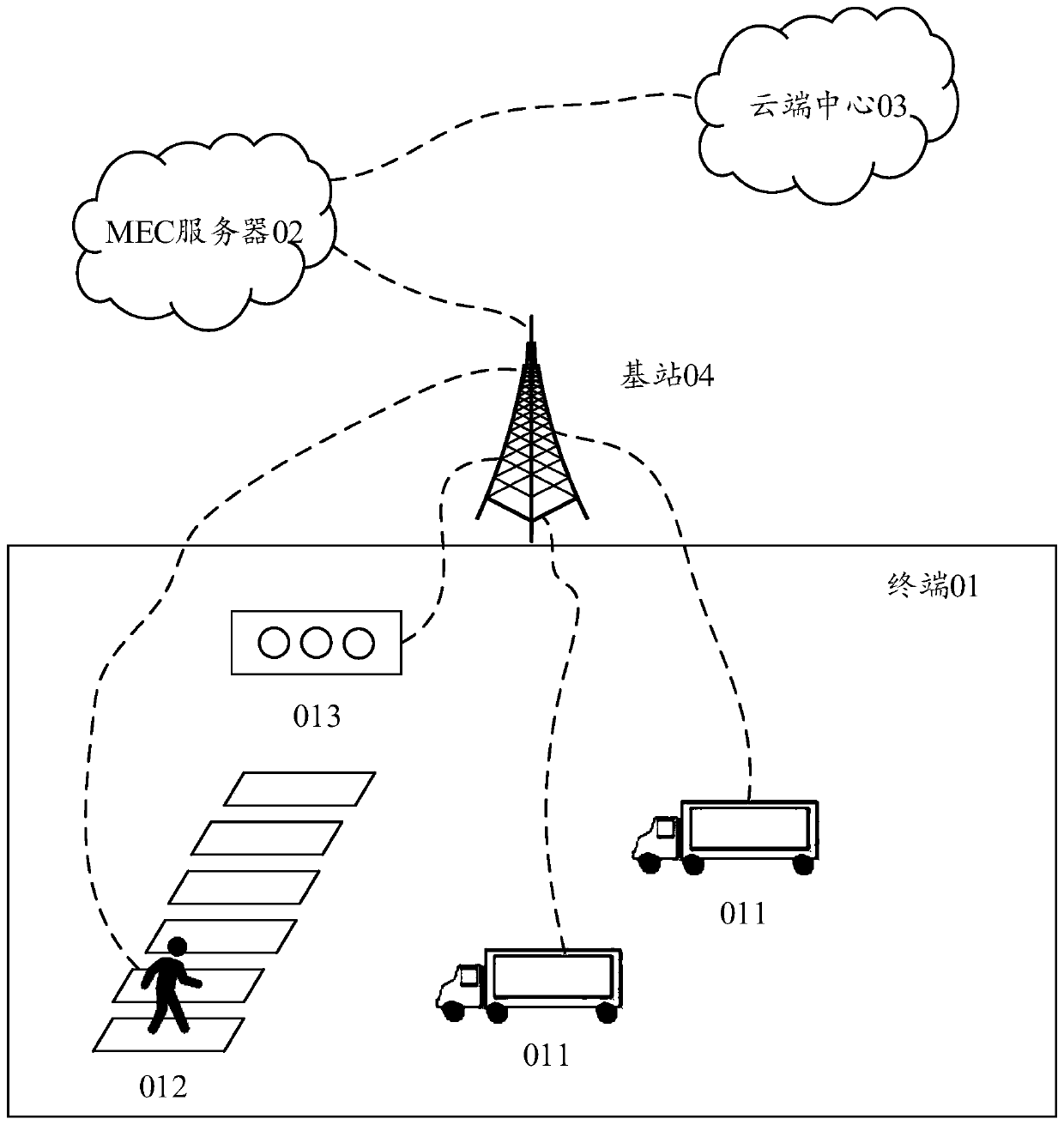
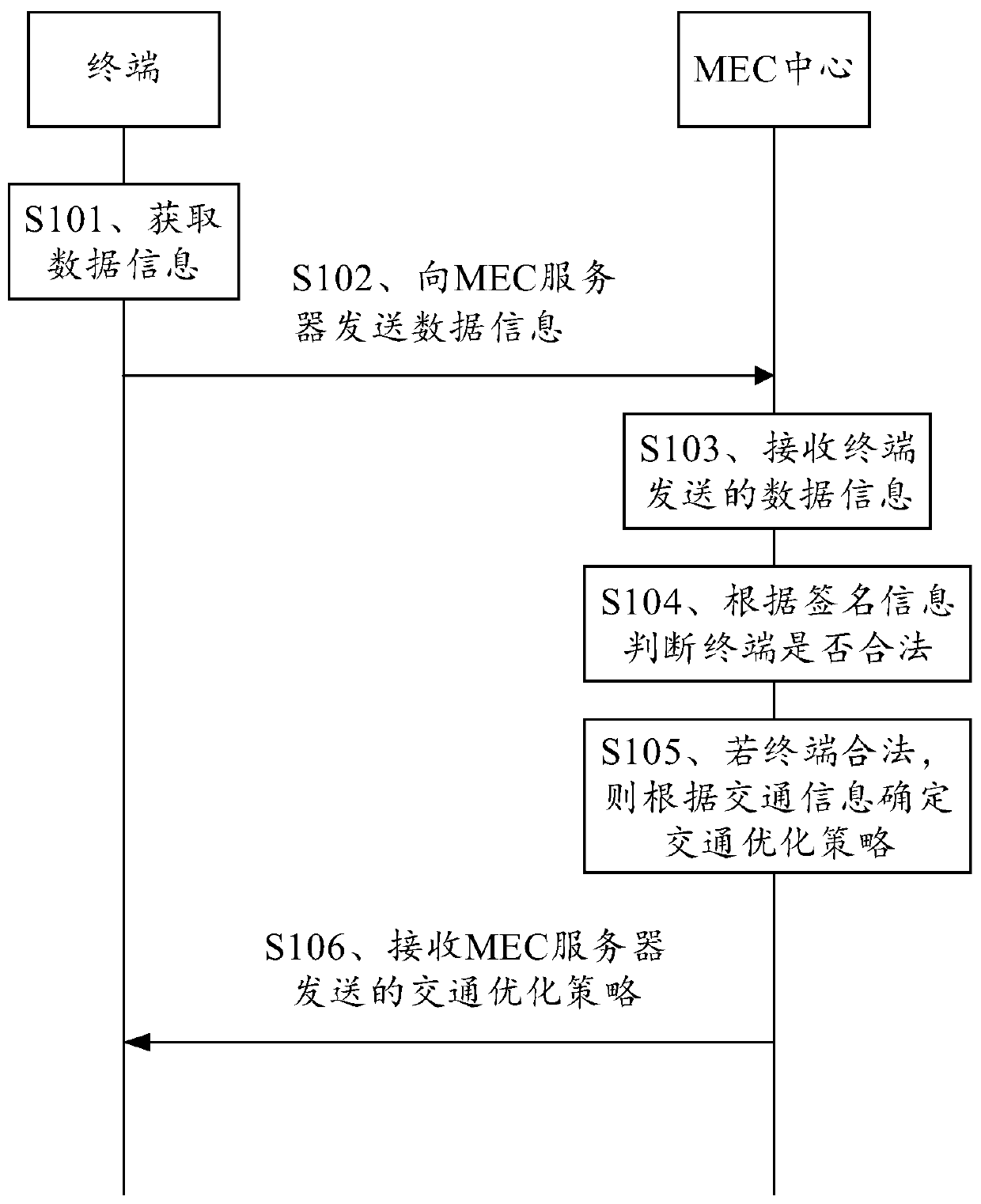
InactiveCN111462515AEnsure safetyIncrease legitimacyRoad vehicles traffic controlParticular environment based servicesData informationTraffic optimization
The embodiment of the invention provides a vehicle-road cooperative management method, an MEC server, a terminal and a system, relates to the field of intelligent transportation, and aims to avoid information leakage caused by access of an illegal terminal to a vehicle-road cooperative management system and enhance the safety of the vehicle-road cooperative management system. The method comprisesthe steps that a terminal acquires data information, wherein the data information comprises signature information, traffic information and attribute information of the terminal, the traffic information is used for indicating road conditions related to the terminal, the signature information is used for verifying the legality of the terminal, and the attribute information is used for indicating thetype of the terminal; the terminal sends the data information to an MEC server; the MEC server receives the data information sent by the terminal; the MEC server judges whether the terminal is legalor not according to the signature information; if the terminal is legal, the MEC server determines a traffic optimization strategy according to the traffic information; and the terminal receives the traffic optimization strategy sent by the MEC server. The method is used for optimizing the intelligent traffic.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
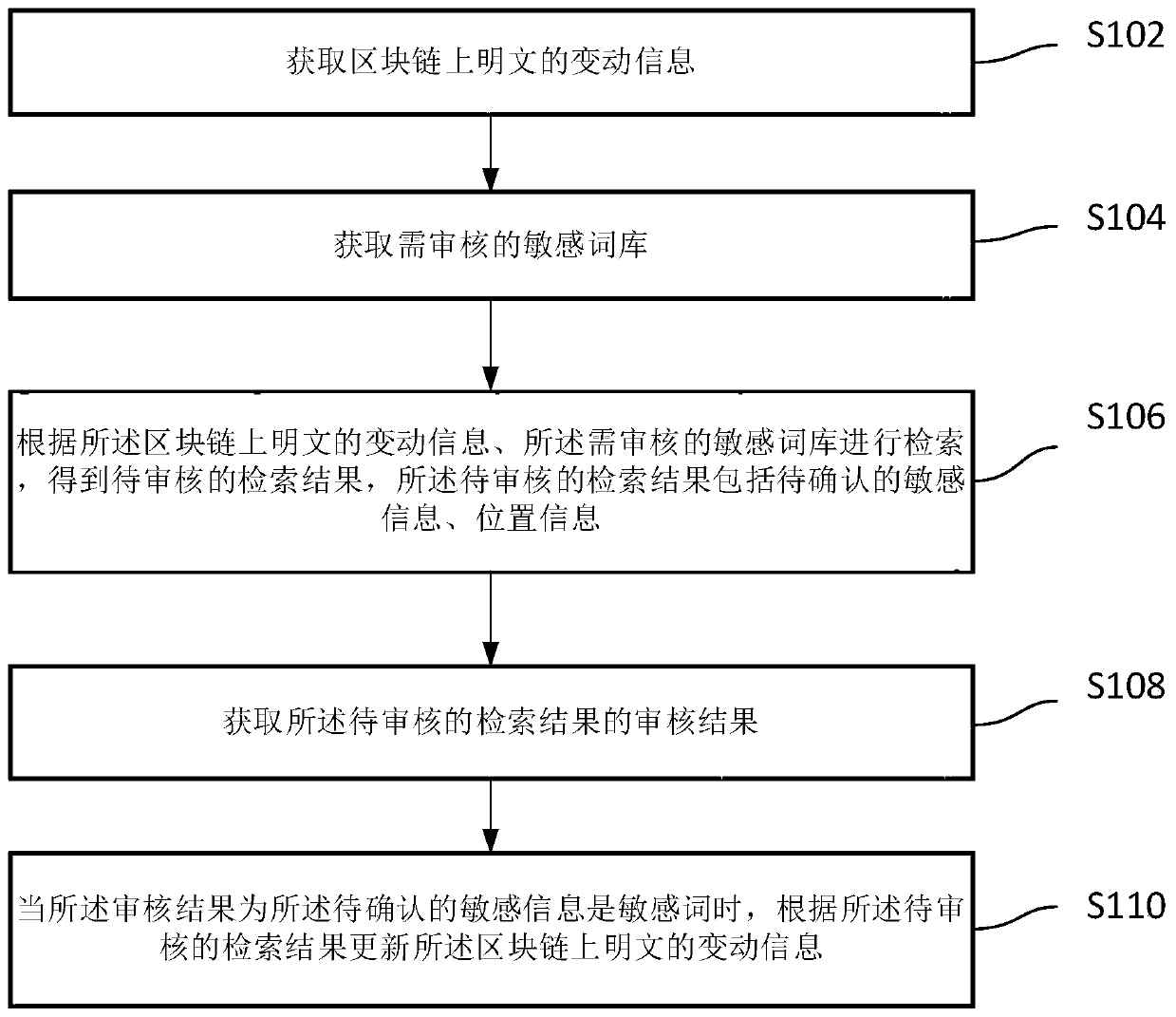
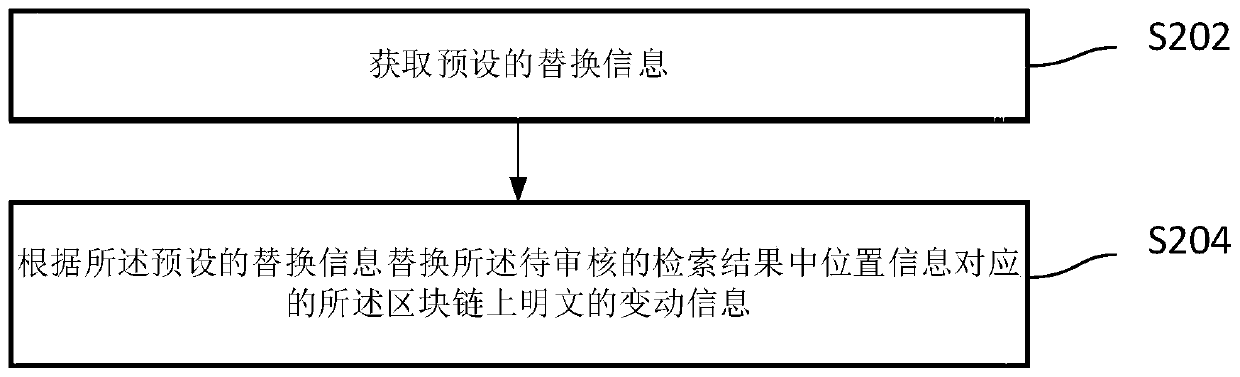
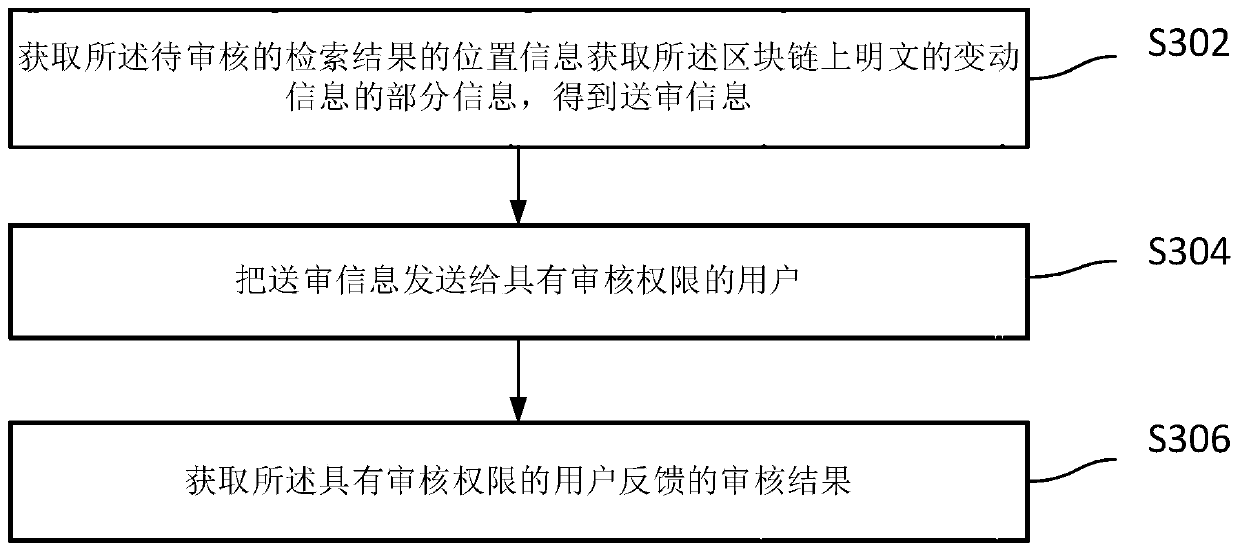
Block chain sensitive word processing method, device, storage medium and equipment
InactiveCN110472012AImprove securityIncrease legitimacyText database queryingSpecial data processing applicationsInformation processingPlaintext
The invention relates to the technical field of block chain information processing, in particular to a block chain sensitive word processing method, a block chain sensitive word processing device, a storage medium and equipment. The method comprises the steps of obtaining change information of a plaintext on a block chain; obtaining a sensitive word bank to be audited; searching according to the change information of the plaintext on the blockchain and the sensitive word bank to be audited to obtain a search result to be audited, the search result to be audited comprising sensitive informationto be confirmed and position information; obtaining an auditing result of the retrieval result to be audited; and when the audit result is that the sensitive information to be confirmed is a sensitive word, updating the change information of a plaintext on the block chain according to the retrieval result to be audited. According to the method, information forbidden by laws and administrative laws and regulations is effectively prevented from appearing in plaintexts on the block chain. The safety and legality of block chain information service are improved.
Owner:深圳市中农易讯信息技术有限公司
Method and device for voiceprint registration and method and device for voiceprint authentication
ActiveCN106100846AImprove reliabilityHigh precisionUser identity/authority verificationUser inputSoftware engineering
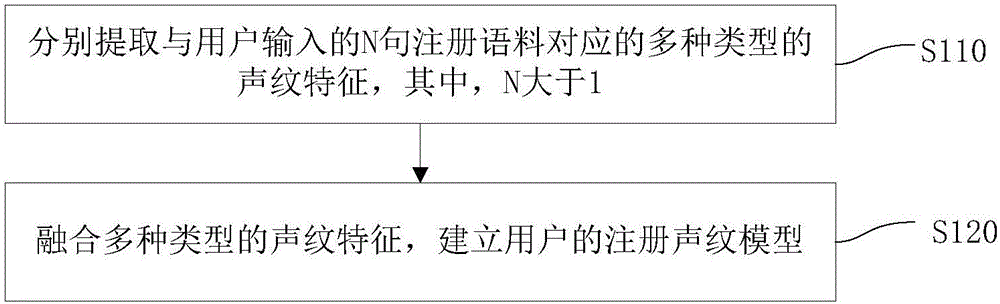
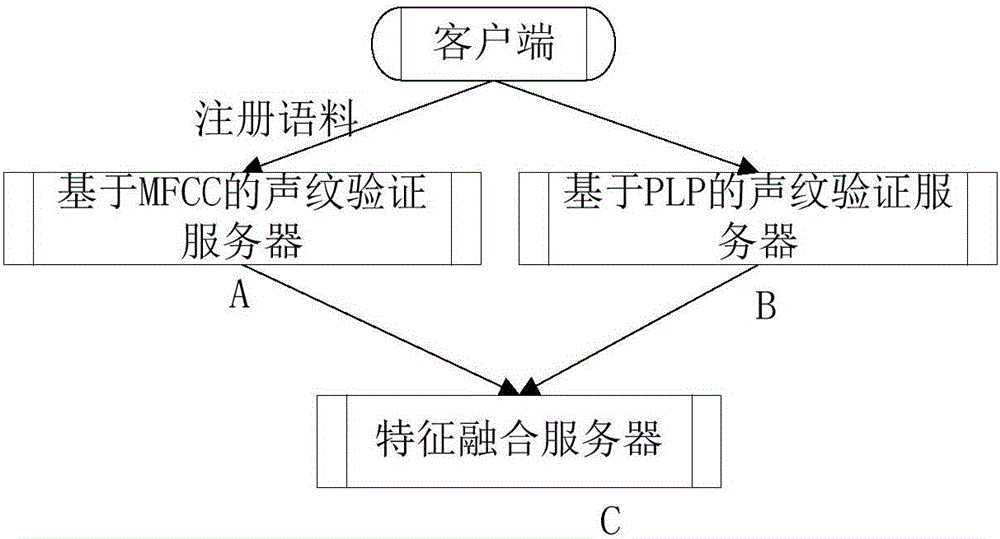
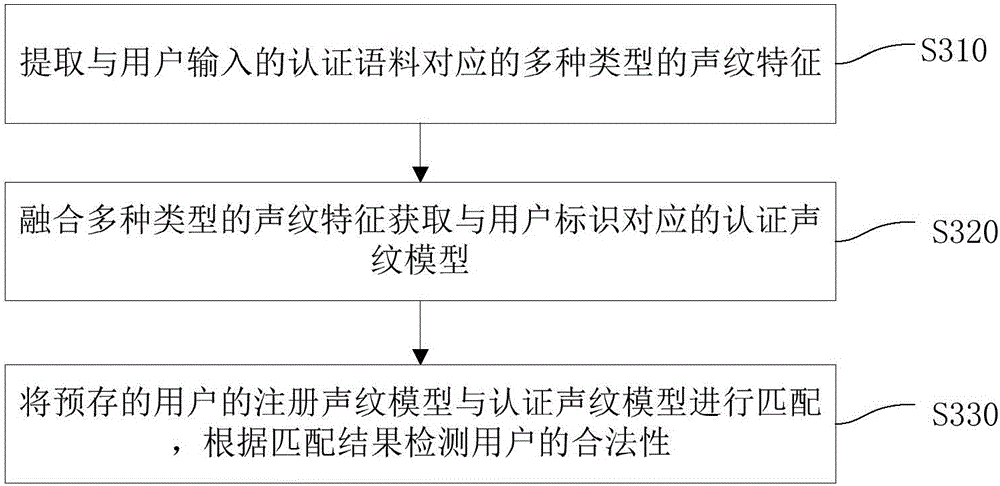
The invention discloses a method and a device for voiceprint registration and a method and a device for voiceprint authentication, wherein the method for voiceprint registration comprises the steps of: respectively extracting various types of voiceprint features corresponding to N registration corpora input by a user, wherein N is greater than 1; and fusing the various types of voiceprint features, and establishing a registration voiceprint model of the user. In the method, through fusing the various types of voiceprint features to establish the registration voiceprint model, reliability and accuracy of authenticating validity of the user through the registration voiceprint model are improved.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
Data transmission method, sending device and receiving device
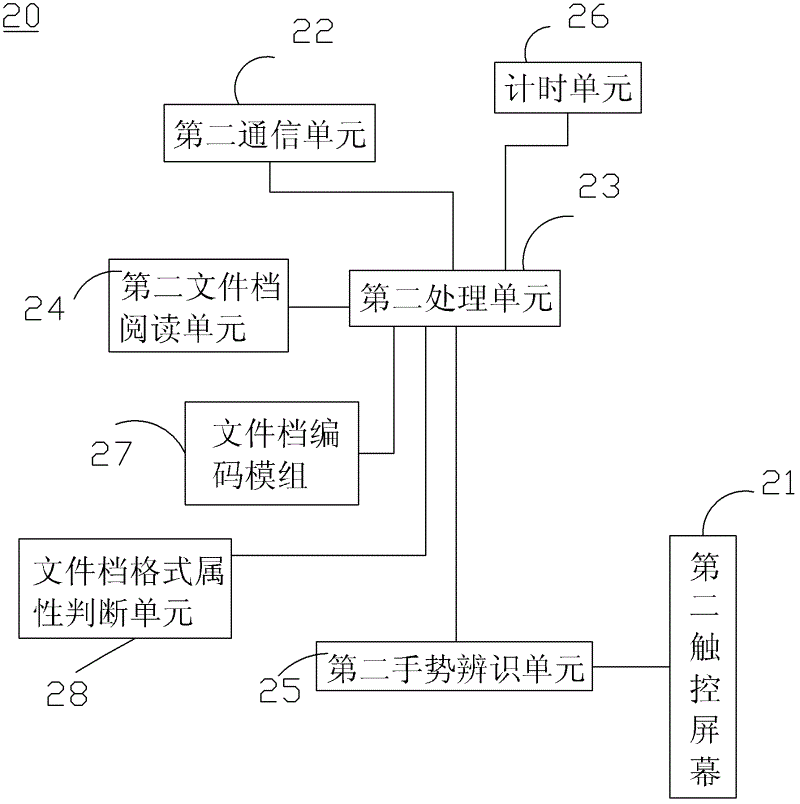
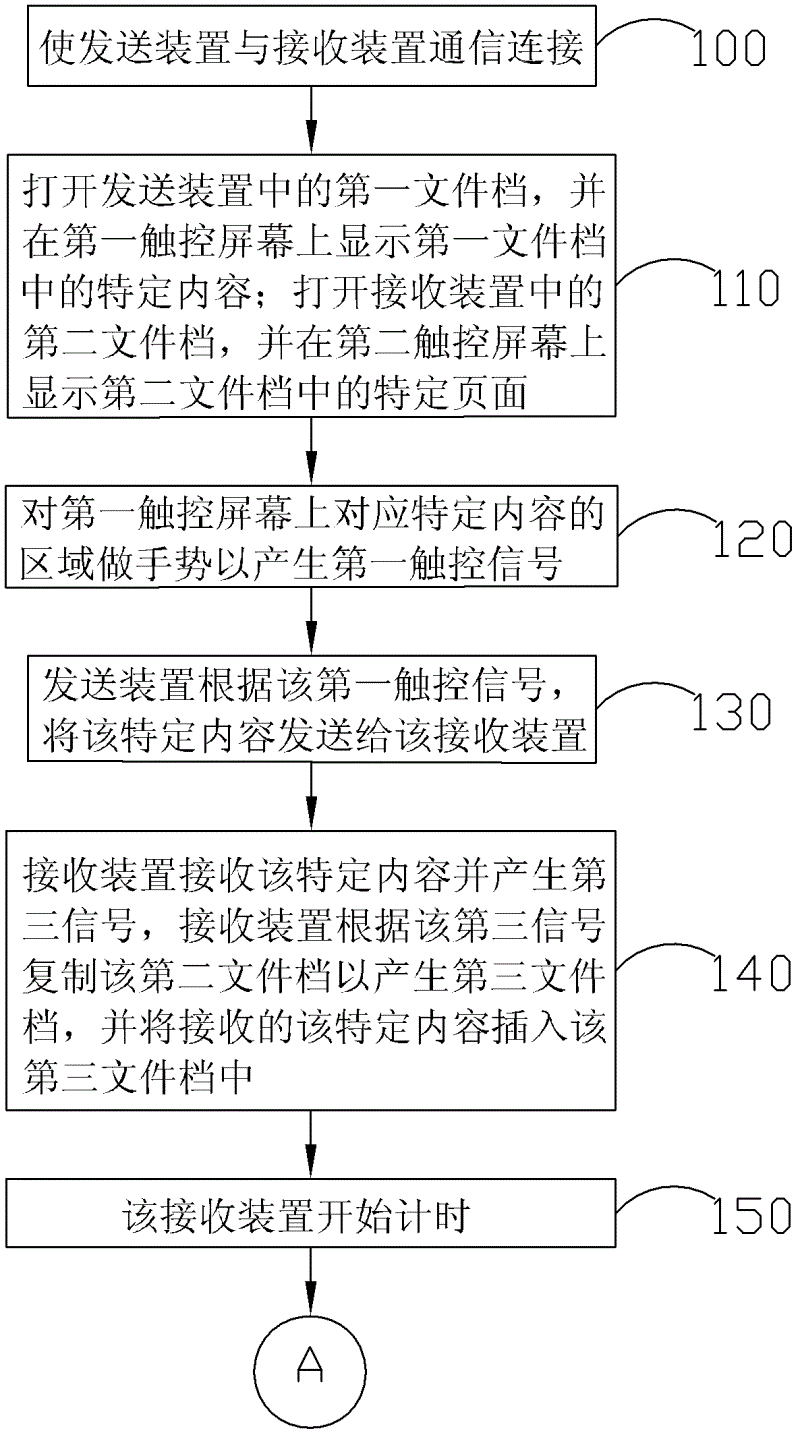
InactiveCN102622422AIncrease legitimacySpecial data processing applicationsInput/output processes for data processingHuman–computer interactionData transmission
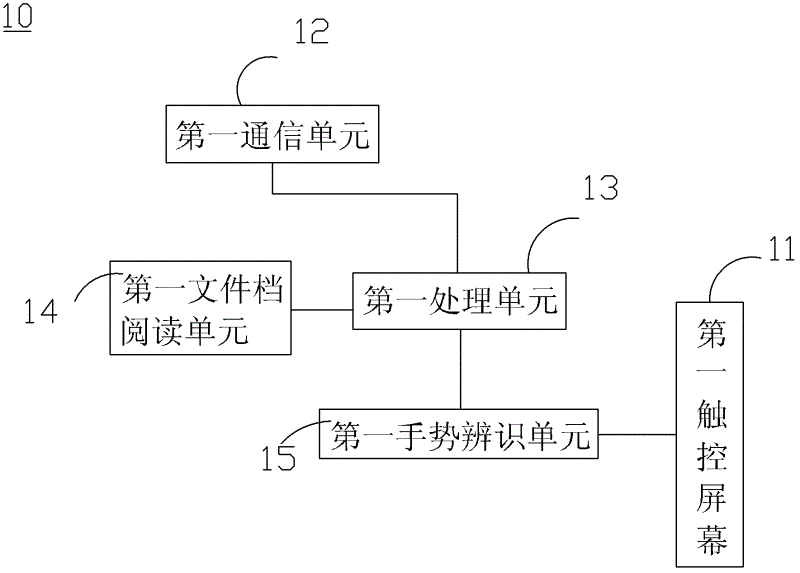
The invention discloses a data transmission method, a sending device and a receiving device. The sending device comprises a first touch screen. The data transmission method comprises the steps as follows: enabling the sending device to be connected with the receiving device in communication; opening a first document file in the sending device, and displaying the specific content in the first document file on the first touch screen; making a gesture in a region corresponding to the specific content on the first touch screen so as to generate a first touch signal; sending the specific content to the receiving device by the sending device according to the first touch signal; receiving a feedback signal from the receiving device by the sending device, and if the feedback signal is a first signal, deleting the specific content from the first document file by the sending device; and if the feedback signal is a second signal, reserving the specific content in the first document file by the sending device, wherein the data is moved to the receiving device by users through simple gestures.
Owner:QISDA SUZHOU +1
Method and device by using identity card of residents in second generation as medium of ID authentication
InactiveCN101093548AReduce duplication of investmentImprove reliabilityCo-operative working arrangementsChecking apparatusResidenceRelevant information
A device using the second-generation residence card as ID certification media is prepared for utilizing a miniaturized electronic unit supporting interactive information treatment function to bridge with the second-generation residence card reader and control subsystem of ID certification system for directly using the second-generation residence card reader as ID certification media fetching unit so as to realize to use the second-generation residence card as ID certification media.
Owner:ZHENGXIN IT TECH
Data operating method and device for intelligent card
ActiveCN101667258AImprove securityIncrease legitimacyCo-operative working arrangementsRecord carriers used with machinesRelevant informationData operations
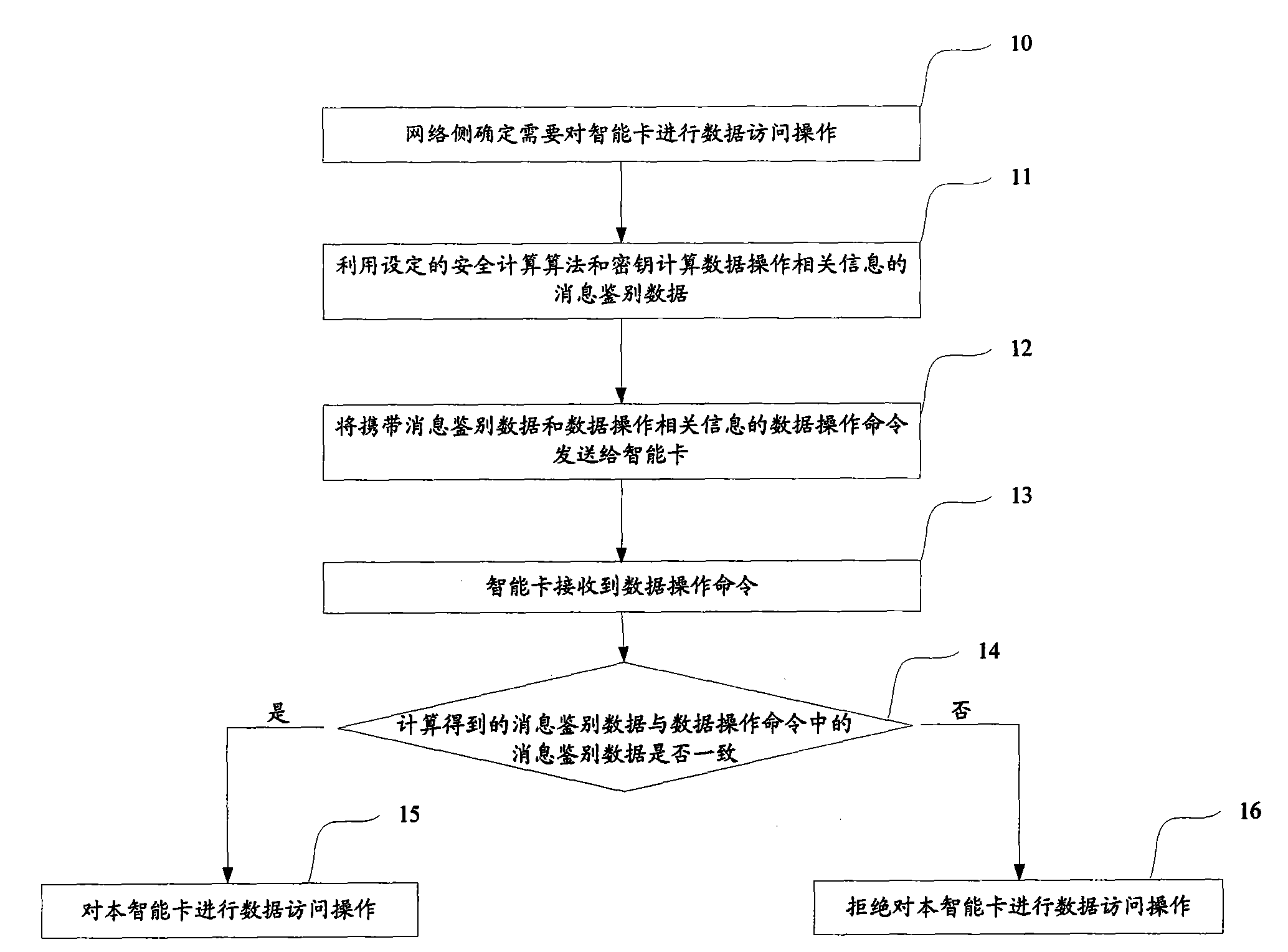
The embodiment of the invention discloses a data operating method for an intelligent card, which is characterized in that a network side utilizes a set safe calculating algorithm and a secret key to calculate the information identifying data of data operating relevant information after determining that data access operation is needed for an intelligent card, and a data operating command carrying the information identifying data and the data operating relevant information is sent to the intelligent card; the intelligent card reads the secret key saved therein after receiving the data operatingcommand and then utilizes the safe calculating algorithm and the read secret key to calculate the information identifying data of the data operating relevant information, if the calculated informationidentifying data is consistent with the information identifying data carried in the data operating command, the data access operation is performed on the intelligent card, and otherwise, the data access operation is refused to the intelligent card. The embodiment of the invention also discloses an intelligent card. By adopting the invention, the safety and the validity of the data access operation performed on the intelligent card can be effectively improved.
Owner:BEIJING WATCH DATA SYST
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com