Verification method and system
A verification method and verification algorithm technology, applied in the field of communication, can solve problems such as difficult verification of pseudo-clients
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
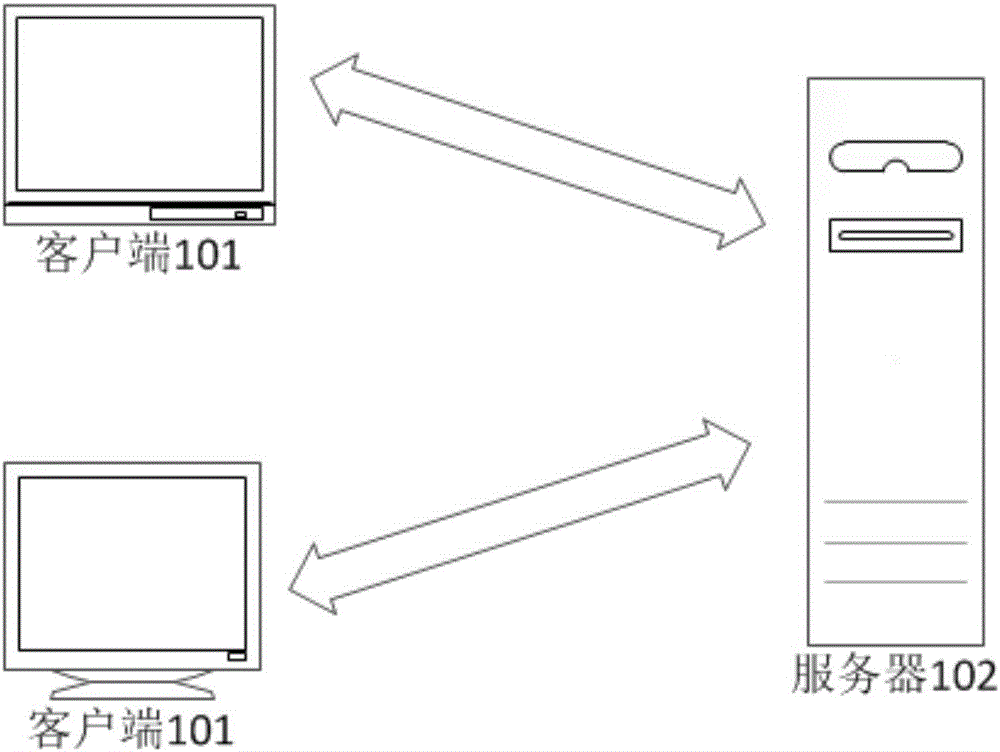
[0058] Before introducing the method embodiment of the present invention, first introduce the verification system architecture in the embodiment of the present invention, such as figure 1 As shown, the system includes: a client 101 and a server 102 . server 102 as figure 1 As shown, communication connections can be realized with N clients 101, and N is a natural number, wherein, the communication mode between the clients 101 and the server 102 can be wired communication or wireless communication, and the client 101 can specifically be A smart phone may also be a tablet computer, or a smart wearable device, etc., which are not limited in this application.
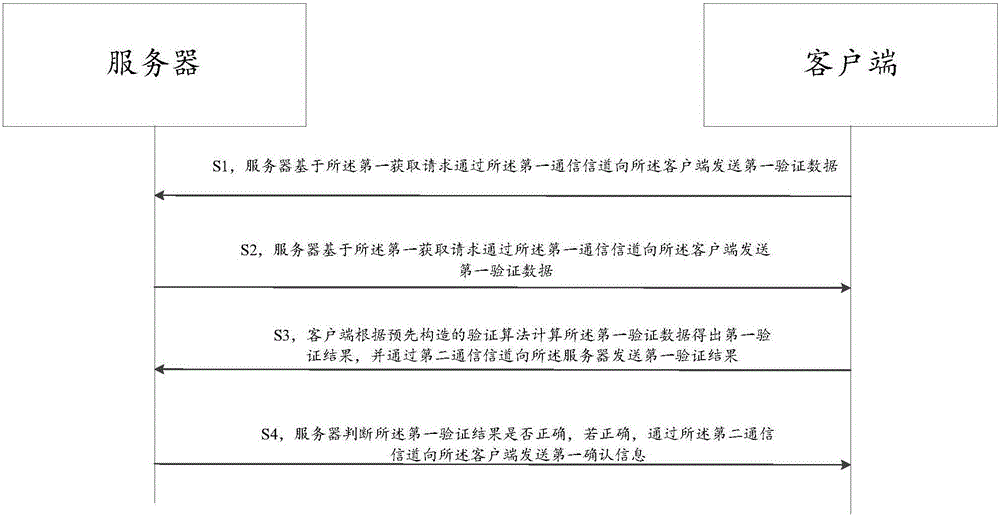
[0059] like figure 2 As shown, the data interaction process between the client 101 and the server 102 is as follows:
[0060] S1. The client sends a first acquisition request to the server through the first communication channel.
[0061] In this step, when verifying the legitimacy of the client, the client needs to sen...
Embodiment 2
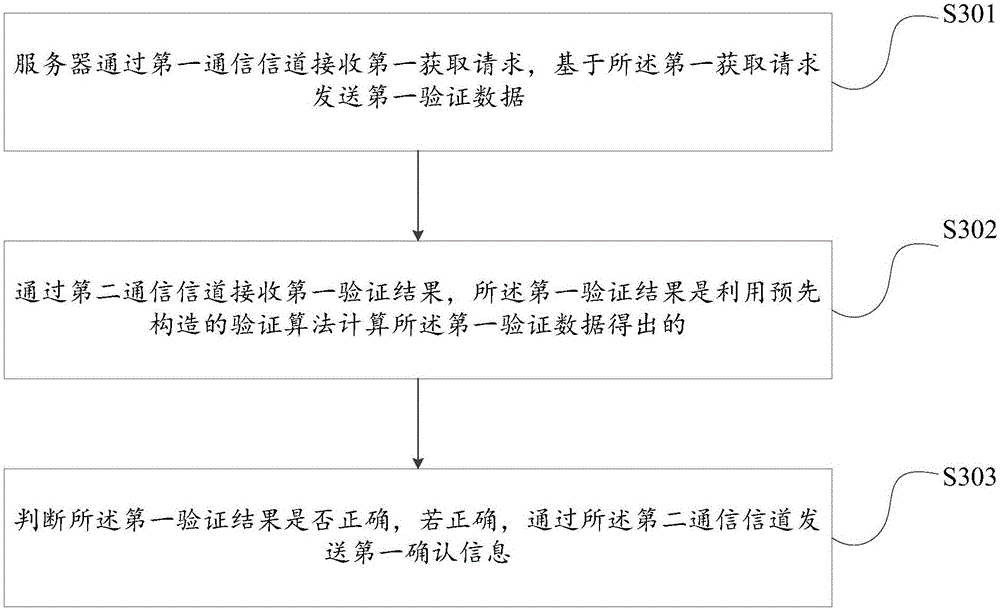
[0083] This embodiment provides a verification method, which is applied on the server side, see image 3 , the method includes:
[0084] S301. The server receives a first acquisition request through a first communication channel, and sends first verification data based on the first acquisition request.
[0085] In this step, when verifying the legitimacy of the client, the client needs to send a first acquisition request to the server through the first communication channel to obtain verification data; wherein, the first communication channel may be based on the HTTP protocol, or Based on the TCP protocol, or the communication channel established based on the UDT protocol, or other protocols that can communicate between the client and the server, etc.
[0086] When the server receives the first acquisition request through the first communication channel, the server sends the first verification data to the client based on the first acquisition request. Wherein, the first veri...
Embodiment 3
[0107] This embodiment also provides a verification method, which is applied on the client side, such as Figure 4 As shown, the method includes:
[0108] S401. The client sends a first acquisition request through a first communication channel, so that the server can return first verification data based on the first acquisition request.
[0109] In this step, when verifying the legitimacy of the client, the client needs to send a first acquisition request to the server through the first communication channel to obtain verification data; wherein, the first communication channel may be based on the HTTP protocol, or Based on the TCP protocol, or the communication channel established based on the UDT protocol, or other protocols that can communicate between the client and the server, etc.
[0110] After the server receives the first acquisition request, it will send the first verification data to the client through the first communication channel based on the first acquisition r...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com