Electronic contract signing method and device, terminal device and storage medium
An electronic contract and pre-storage technology, applied in the field of terminal equipment and computer-readable storage medium, device, and electronic contract signing method, can solve the problem of low security of real-name authentication, and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0067] The electronic contract signing method provided by the embodiment of the present application can be realized through a mobile terminal or WEB, that is, the user can realize the electronic contract signing through the WEB method, or can realize the electronic contract signing through a mobile terminal, and the mobile terminal can include but not limited to a mobile phone, Tablets, PDAs and other mobile devices with cameras.
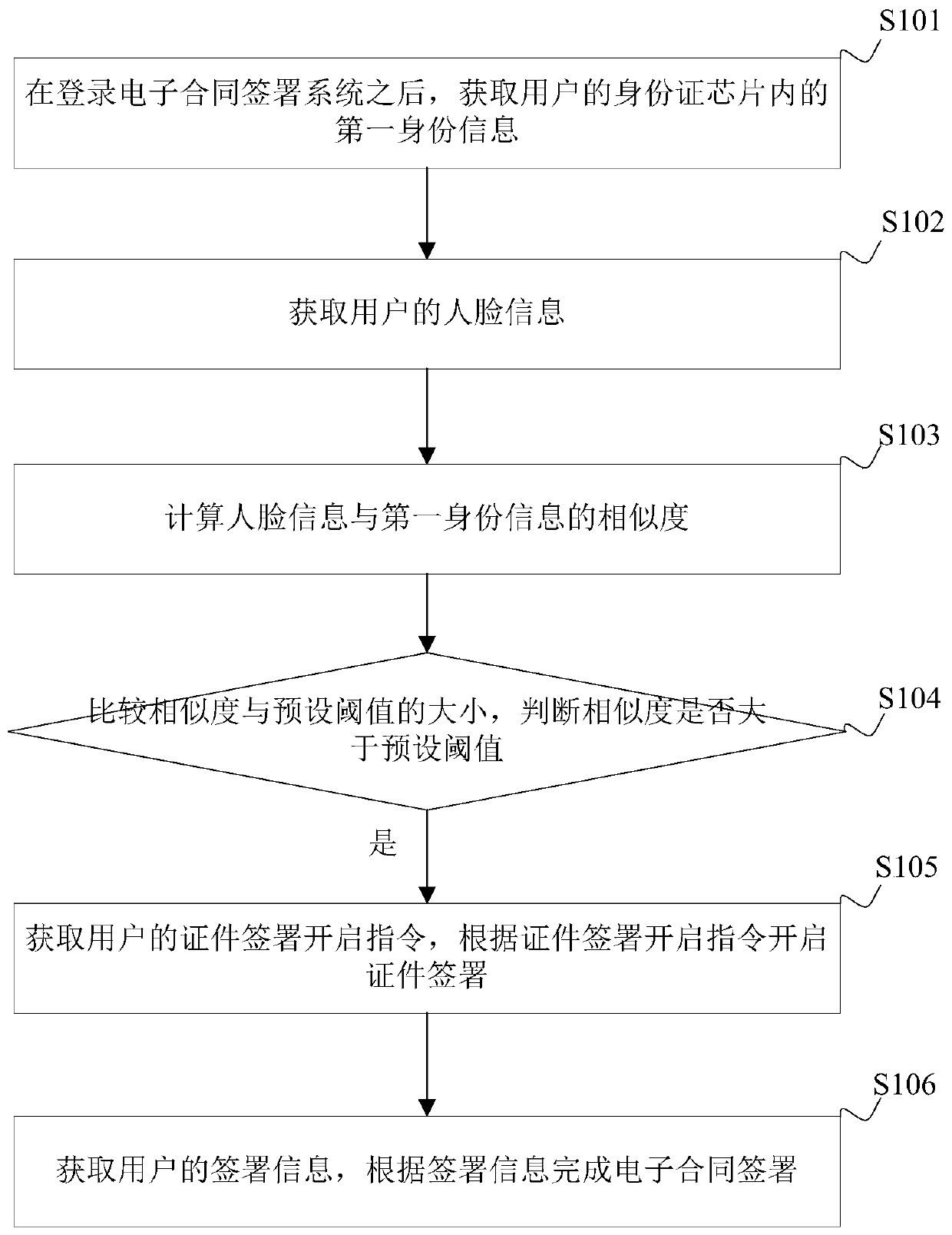
[0068] See figure 1 , which is a schematic flow diagram of a method for signing an electronic contract provided in the embodiment of the present application, the method may include the following steps:
[0069] Step S101. After logging into the electronic contract signing system, obtain the first identity information in the user's ID card chip.
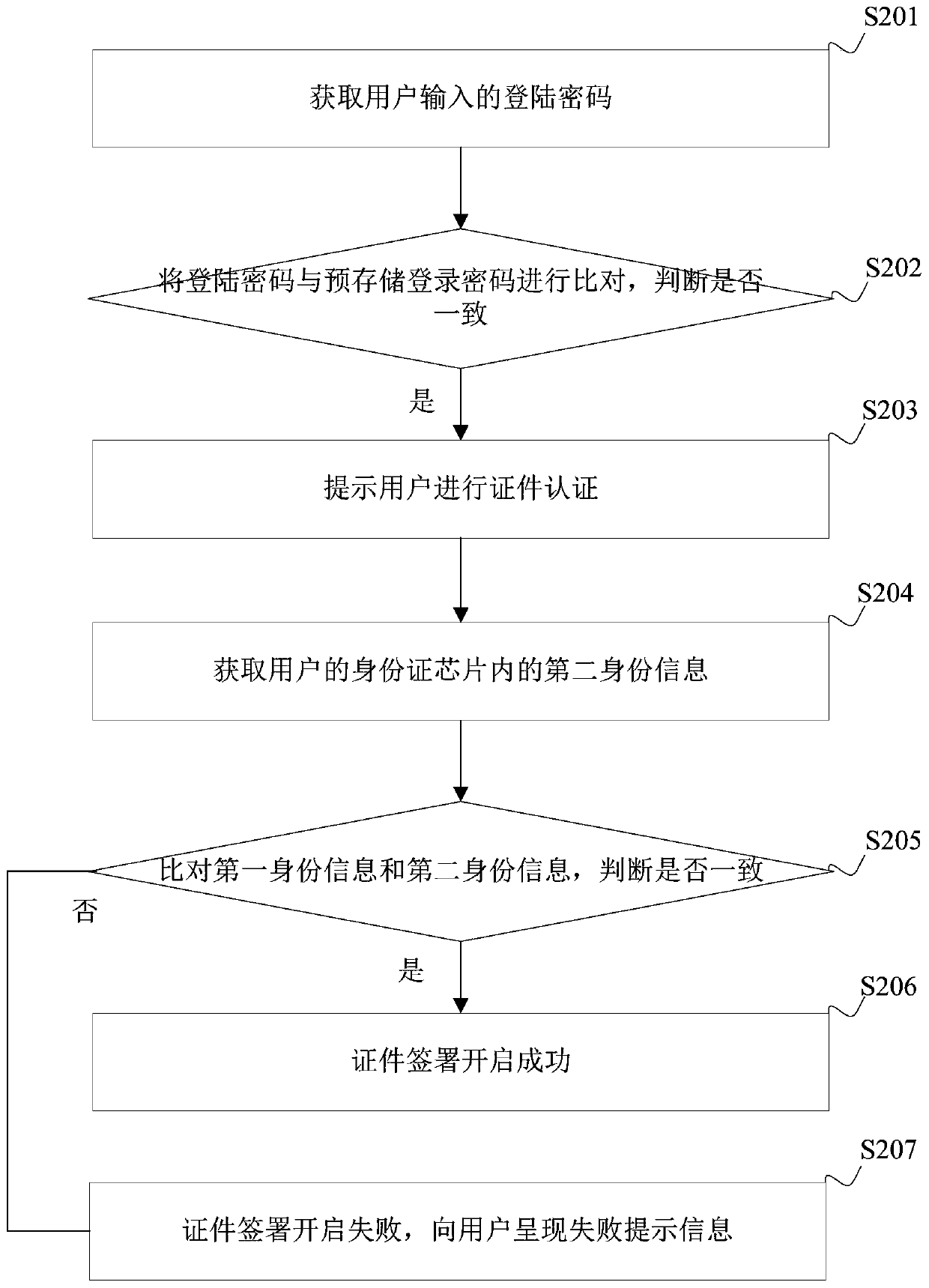
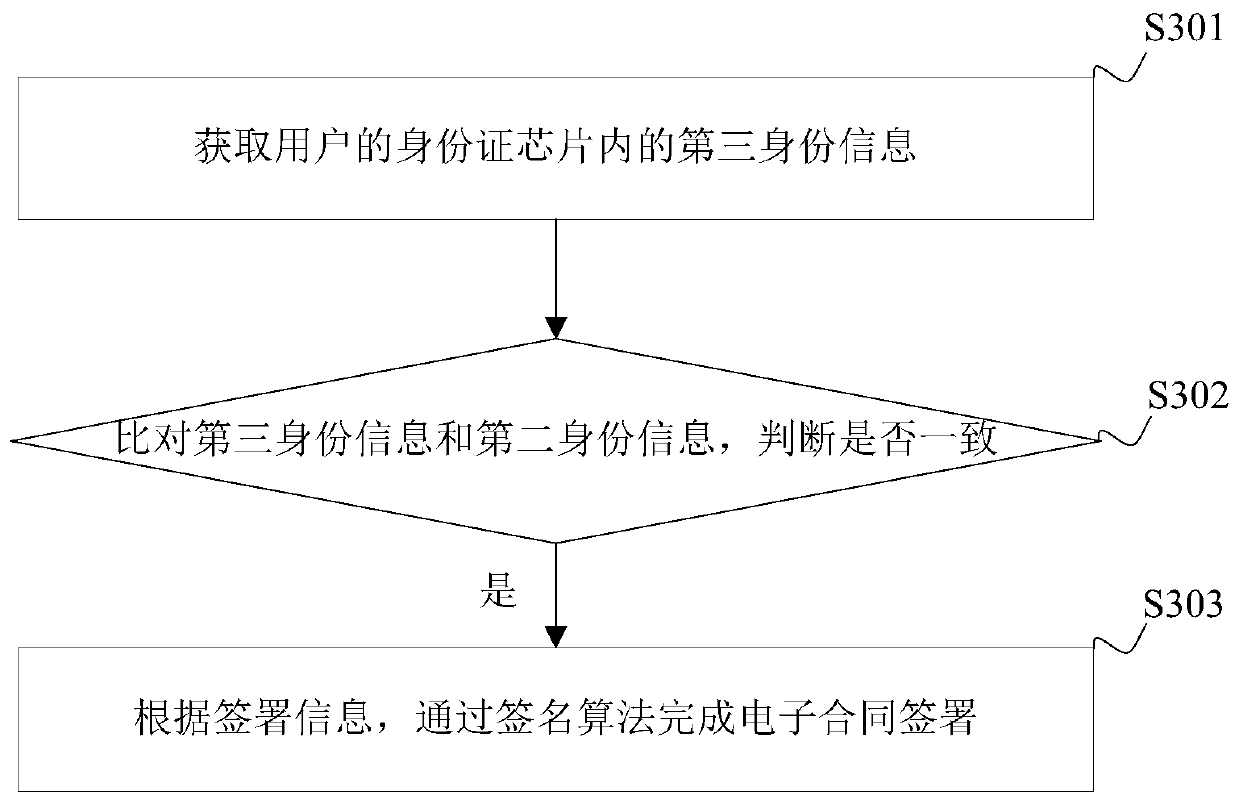
[0070] Specifically, after the user logs in to the electronic contract signing system through the user account, the user performs real-name authentication of the certificate, and the system prompts the use...
Embodiment 2
[0116] See Figure 4 , which is a schematic structural block diagram of an electronic contract signing device provided in the embodiment of the present application, the device may include:
[0117] The first obtaining module 41 is used to obtain the first identity information in the ID card chip of the user after logging into the electronic contract signing system;
[0118] The second obtaining module 42 is used to obtain the face information of the user;
[0119] Calculation module 43, for calculating the similarity between face information and the first identity information;
[0120] Comparison module 44, used to compare the size of the similarity with the preset threshold;
[0121] The authentication module 45 is used for when the similarity is greater than the preset threshold, then the real-name authentication is successful;
[0122] The opening module 46 is used to obtain the user's certificate signature opening instruction, and open the certificate signature accordin...
Embodiment 3
[0143] Figure 5 It is a schematic diagram of a terminal device provided by an embodiment of the present application. Such as Figure 5 As shown, the terminal device 5 of this embodiment includes: a processor 50 , a memory 51 , and a computer program 52 stored in the memory 51 and operable on the processor 50 . When the processor 50 executes the computer program 52, it implements the steps in the above-mentioned embodiments of the electronic contract signing method, for example figure 1 Steps S101 to S106 are shown. Alternatively, when the processor 50 executes the computer program 52, it realizes the functions of the modules or units in the above-mentioned device embodiments, for example Figure 4 The functions of modules 41 to 47 are shown.
[0144] Exemplarily, the computer program 52 can be divided into one or more modules or units, and the one or more modules or units are stored in the memory 51 and executed by the processor 50 to complete this application. The one ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com