Intelligent equipment binding method and device
A smart device and binding technology, applied in electrical components, transmission systems, etc., can solve problems such as smart device legality verification, achieve the effect of preventing false binding requests, enhancing security, and avoiding security risks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
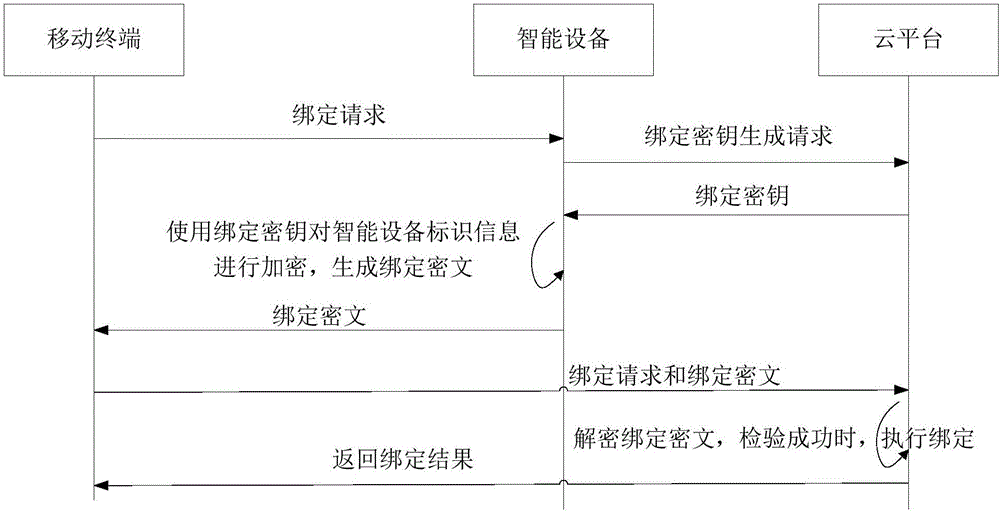
[0046] The smart device binding method with the cloud platform as the execution subject includes:
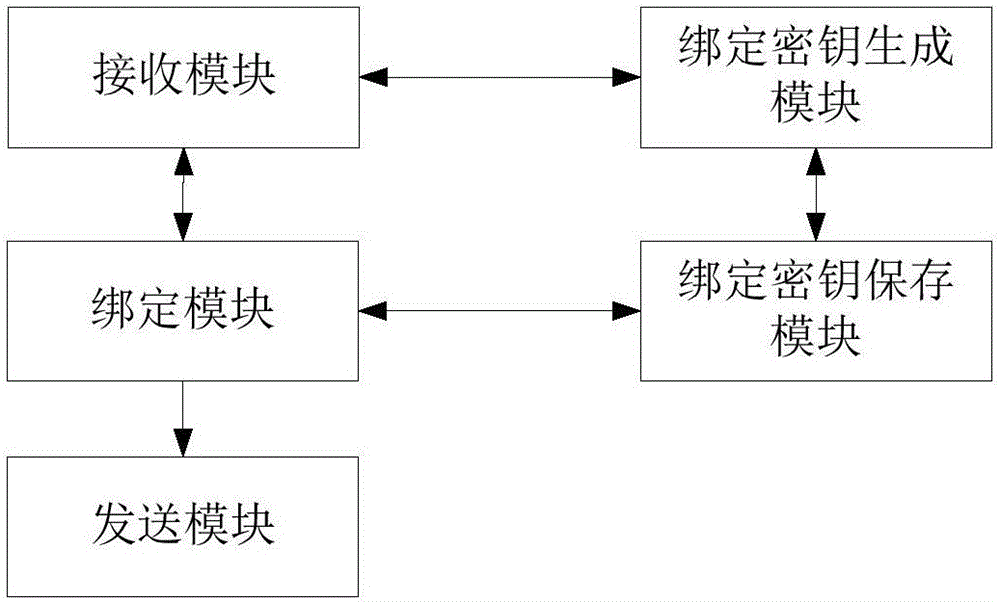
[0047] Step 1: The cloud platform receives a binding key generation request carrying the identification information of the smart device from the smart device, generates a binding key according to the generation request and sends it to the smart device, and generates the binding key carried by the smart device in the request. The corresponding relationship between the identification information and the binding key generated according to the generation request is recorded in the corresponding relationship table;
[0048] Step 2: When the cloud platform receives a binding request carrying the client ID, the smart device ID, and the binding ciphertext from the mobile terminal, it searches the correspondence table for the smart device ID information carried in the binding request For the corresponding binding key, use the binding key to decrypt the binding ciphertext with a preset en...
Embodiment 2
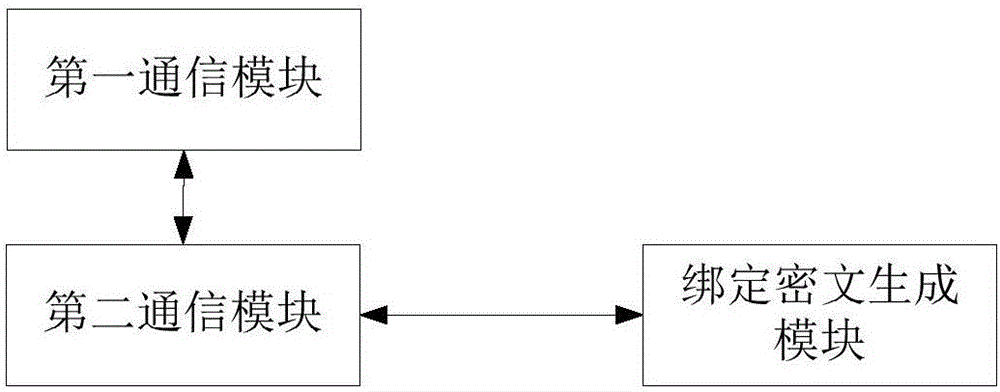
[0066] The smart device binding method with the smart device as the execution subject includes: after the smart device receives the binding request from the mobile terminal, sends a binding key generation request carrying the smart device identification information to the cloud platform, and receives the binding key from the cloud platform Using a preset encryption algorithm to encrypt the identification information of the smart device with the binding key to generate a binding ciphertext, and sending the binding ciphertext to the mobile terminal.
[0067] The smart device identification information includes the unique identification of the smart device, or the smart device identification information includes the unique identification and time stamp of the smart device. The unique identifier of the smart device may be the MAC address of the smart device.
[0068] The method further includes: the smart device sending a binding key update request to the cloud platform. The cond...
Embodiment 3
[0074] The smart device binding method with the mobile terminal as the execution subject includes: the mobile terminal sends a binding request to the smart device, receives a binding ciphertext from the smart terminal, and sends the binding ciphertext carrying the smart device identifier and the binding ciphertext to the cloud platform. The binding request.
[0075] The present invention adds a security control measure for verifying the legitimacy of the smart device when the smart device is bound, and an effective security control mechanism is formed when the smart device is bound. Through the method of binding ciphertext verification, the false smart device identification information submitted by the client will be recognized and rejected by the verification mechanism, and the binding request cannot be completed, so that false binding requests can be prevented and the security risk of unauthorized binding can be avoided. Enhanced security for smart device control and operati...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com