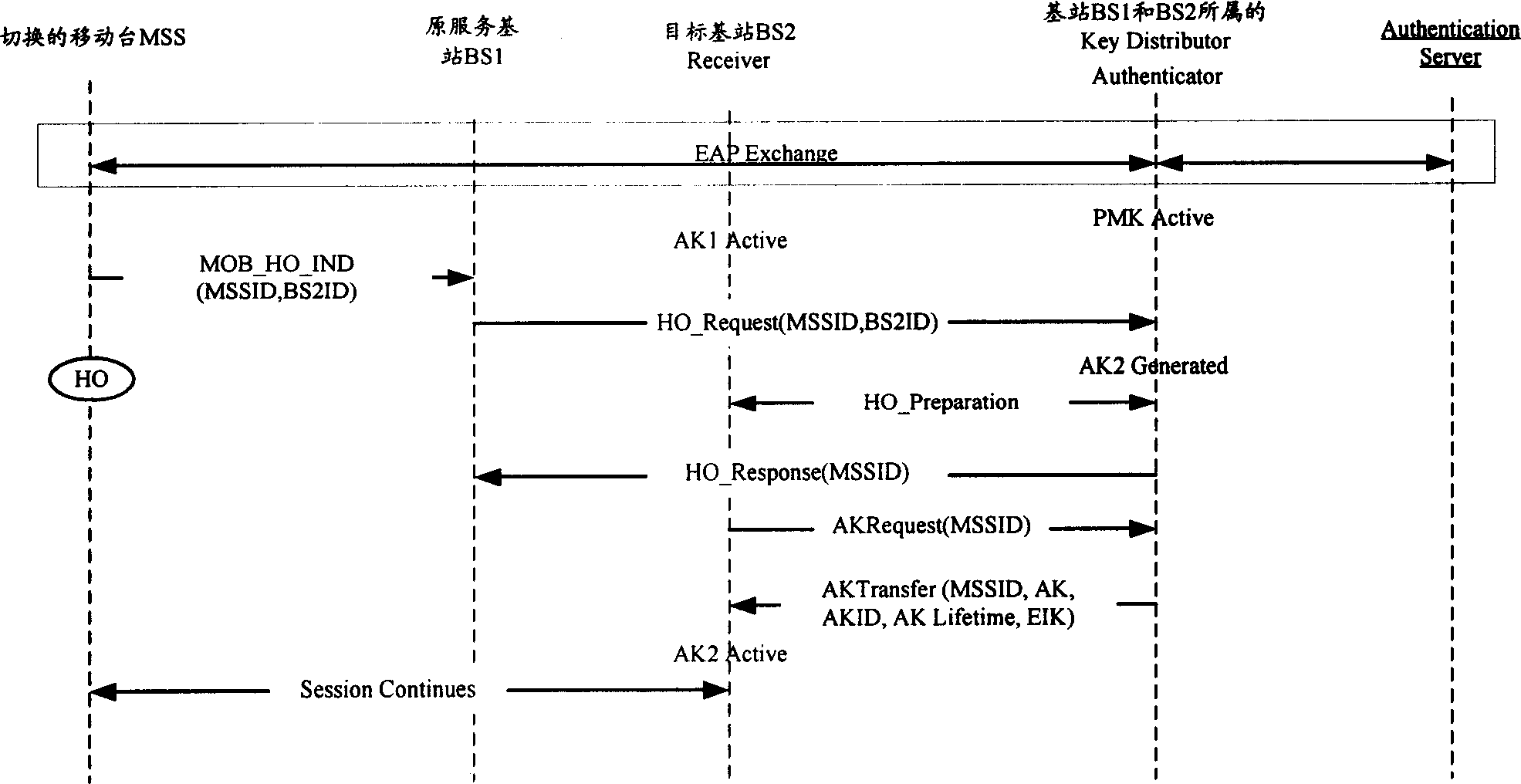
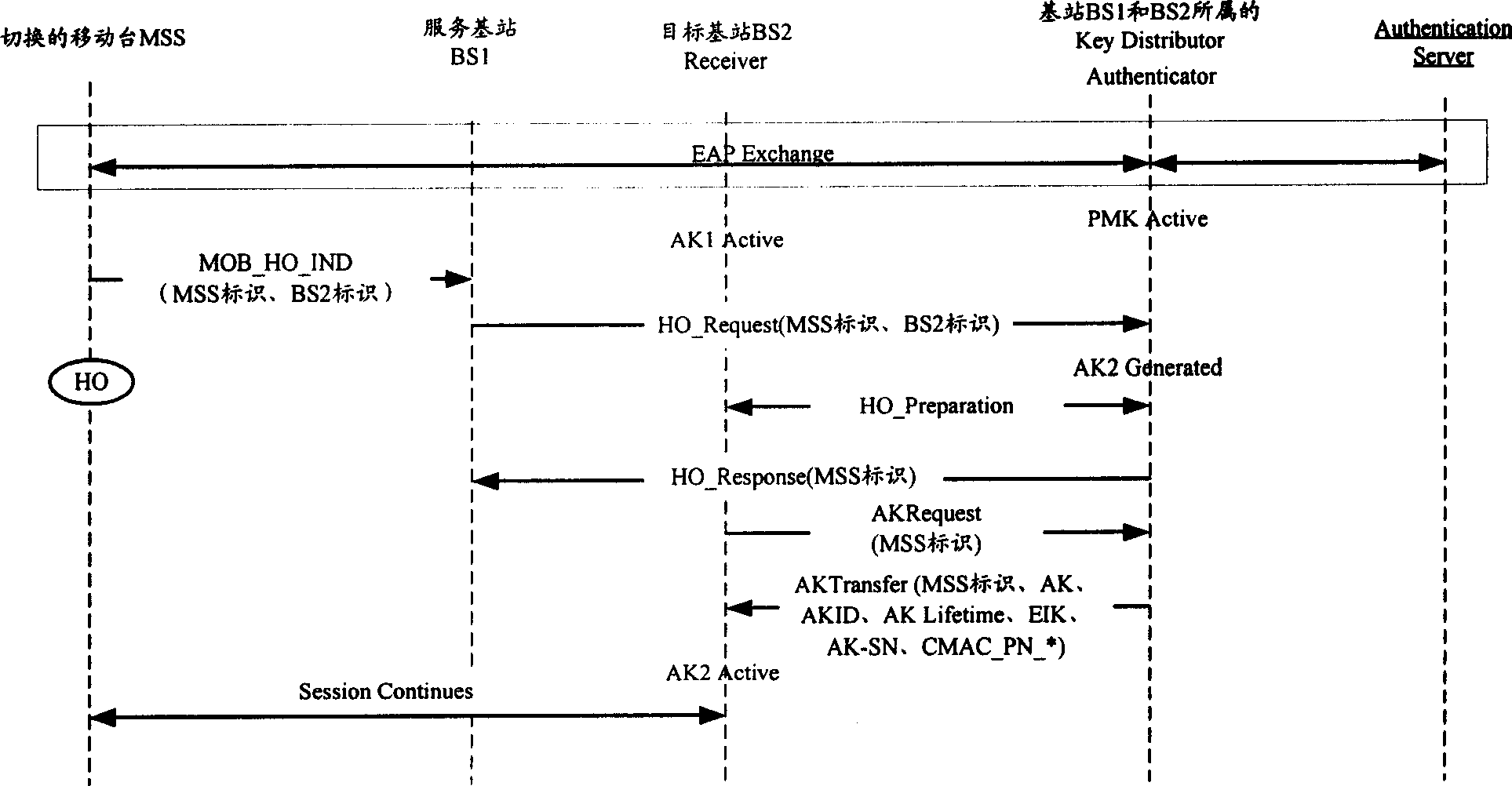
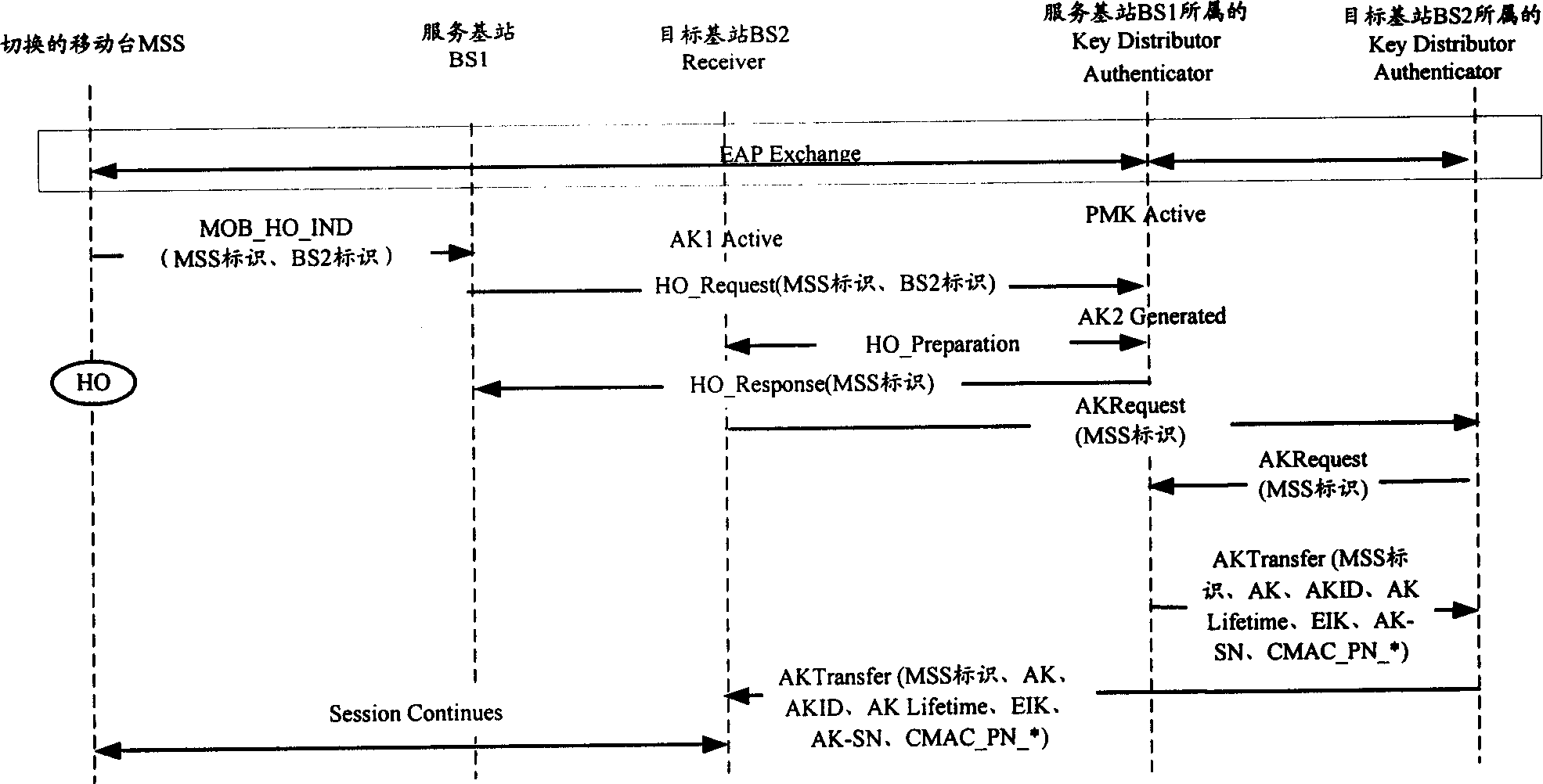
Method for acquring authentication cryptographic key context from object base station
A target base station and authentication key technology, which is applied to the target service base station to obtain the context information of the authentication key, and can solve problems such as serial number information inconsistency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 2
[0085] Such as image 3 As shown, the serving BS1 and the target BS2 belong to different Authenticators / Key Distributors, and the Authenticator / Key Distributor to which the target BS2 belongs does not save the current AK and its context information of the MSS, and the service authenticator / key distributor receives the switching request message Afterwards, the handover preparation message will be exchanged with the target BS2, and the target BS will learn the address information of the service authenticator / key distributor during this process.
[0086] Then BS2 will carry the address information of the serving Authenticator / Key Distributor in the key request message sent to the home target Authenticator / Key Distributor;
[0087] The target Authenticator / Key Distributor sends a key request message to the service Authenticator / Key Distributor according to the address information of the service Authenticator / Key Distributor carried in the key request message of BS2, and the message...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com