Node discovering method and system in communication network
A communication network and discovery method technology, applied in the field of node discovery methods and systems, can solve problems that are not suitable for cross-domain, high-speed, large-scale communication networks, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
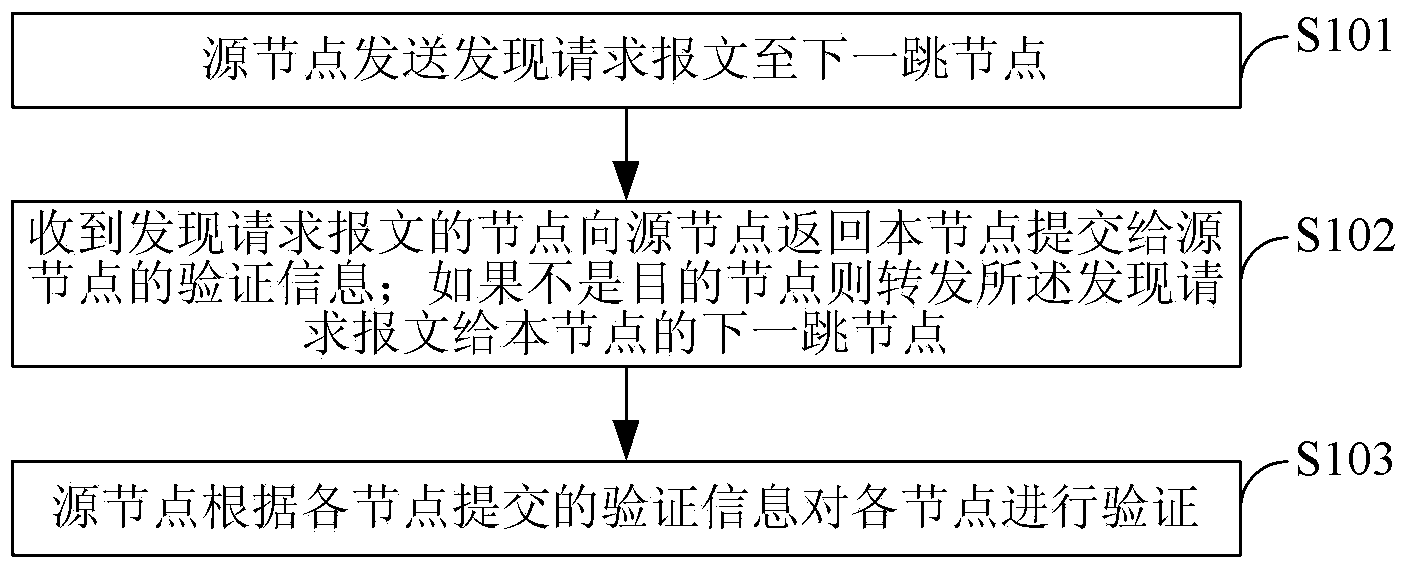
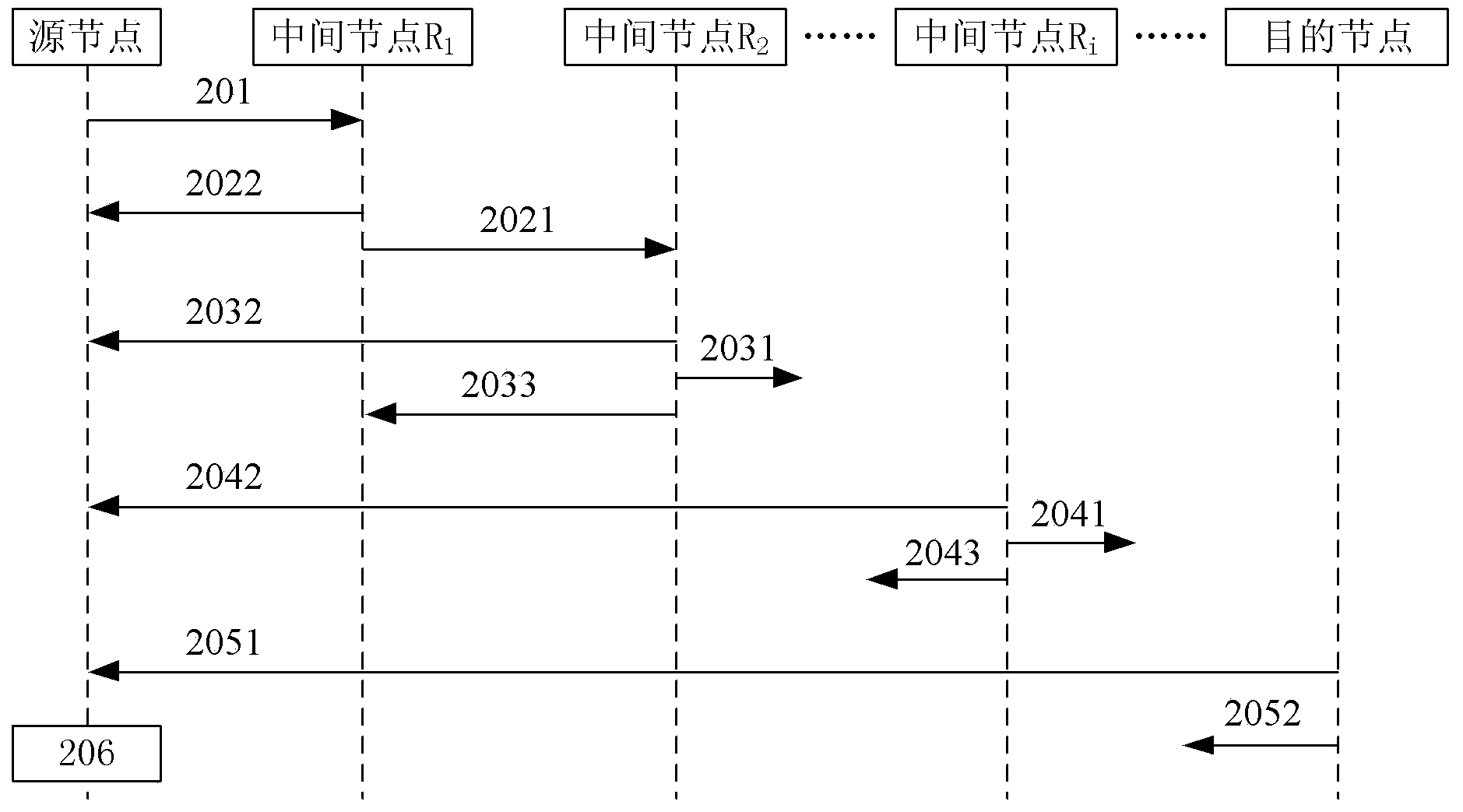
[0059] Embodiment 1. A node discovery method in a communication network, such as figure 1 shown, including:
[0060] S101. The source node sends a discovery request message to the next-hop node, and the discovery request message carries address information of the source node, identity information of the source node, address information of the destination node, and a challenge value generated by the source node;
[0061] S102. The node that receives the discovery request message returns to the source node the verification information submitted by the node to the source node, including: the address information and digital certificate of the node, and the challenge response of the node to the source node value; judging whether the current node is a destination node according to the address information therein, if not the destination node, forwarding the discovery request message to the next hop node of the current node;
[0062] S103. After receiving the verification information...
Embodiment 2
[0138] Embodiment 2, a node discovery system in a communication network, comprising:
[0139] A plurality of nodes, including at least a source node and a destination node for node discovery;
[0140] Each node includes:
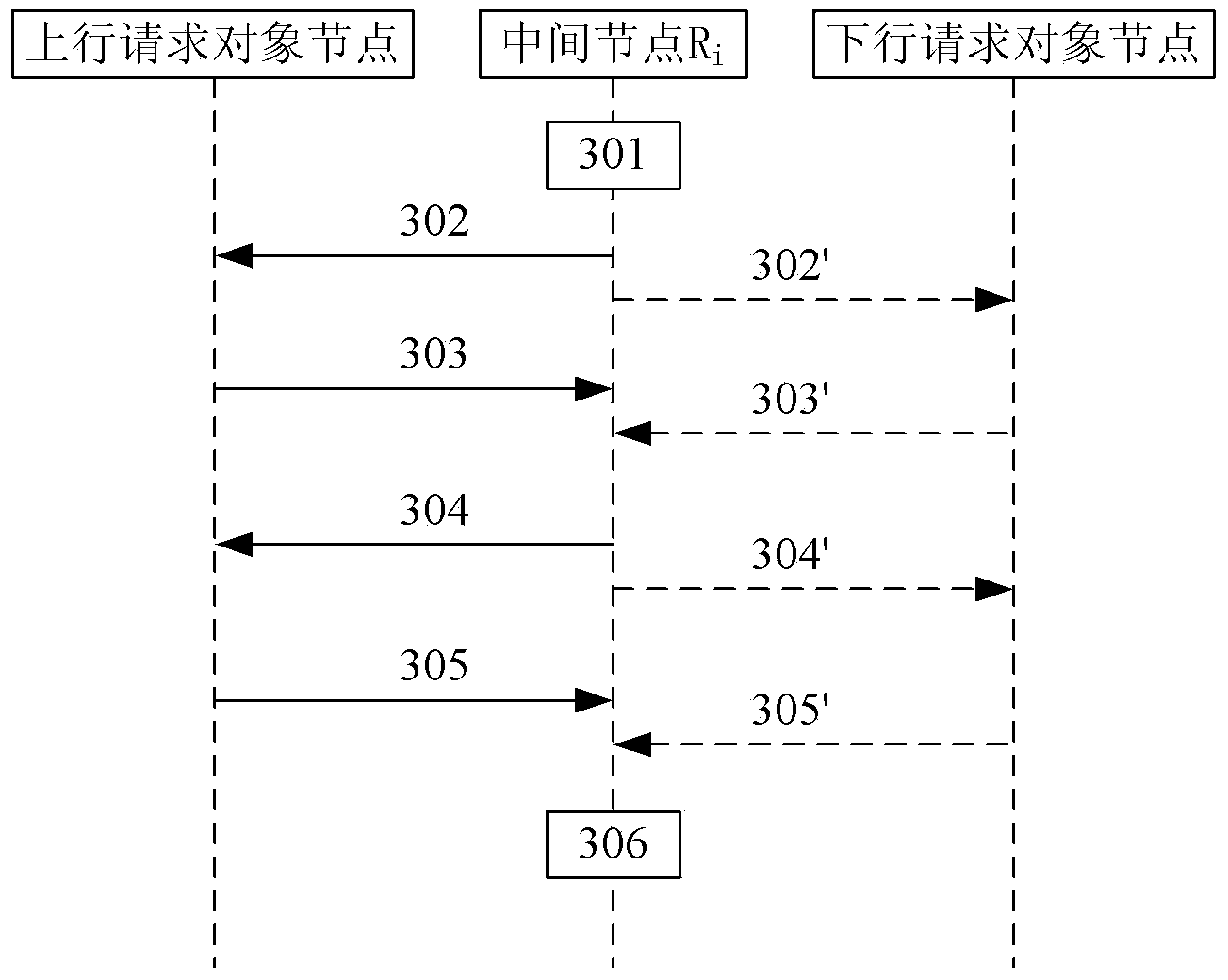
[0141] The request sending module is used to send a discovery request message to the next hop node when the current node is used as the source node, and the discovery request message carries the address information of the source node, the identity information of the source node, and the address of the destination node Information and the challenge value generated by the source node;
[0142] The request response module is used to return to the source node the verification information submitted by the node to the source node after receiving the discovery request message, including: the address information and digital certificate of the node, and the verification information of the node for the source node. challenge response value;
[0143] The request for...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com