Method, system and equipment for implementing multicast service effective authentication and key distribution protocol
A technology of key distribution and protocol implementation, which is applied in the field of satellite communication information security, can solve the problems of stealing privacy control, etc., achieve the effects of ensuring security, simplifying the key layering mechanism, and improving the efficiency of key management
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
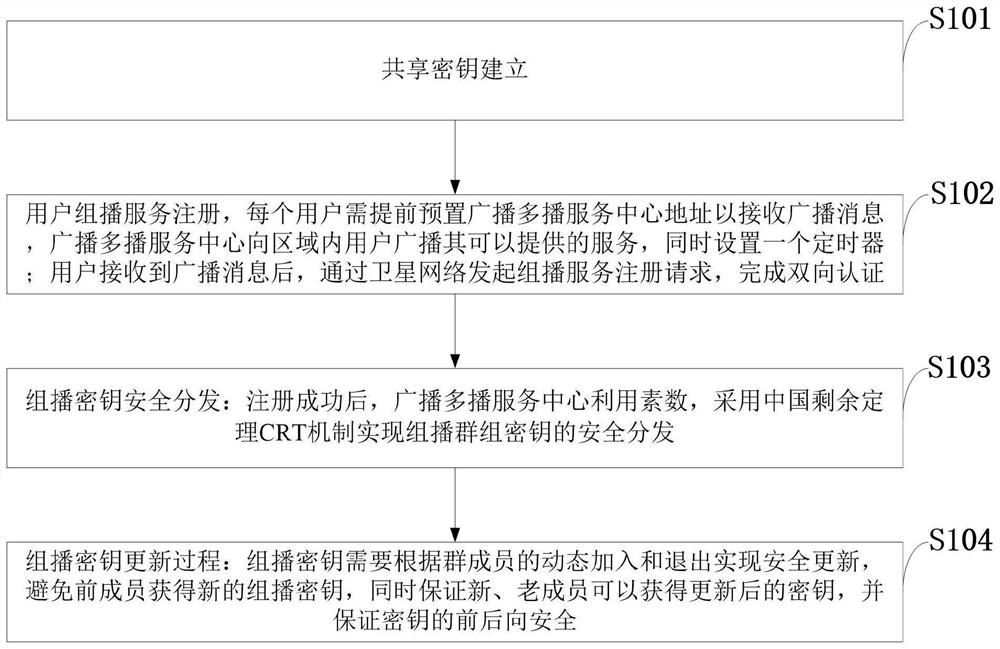
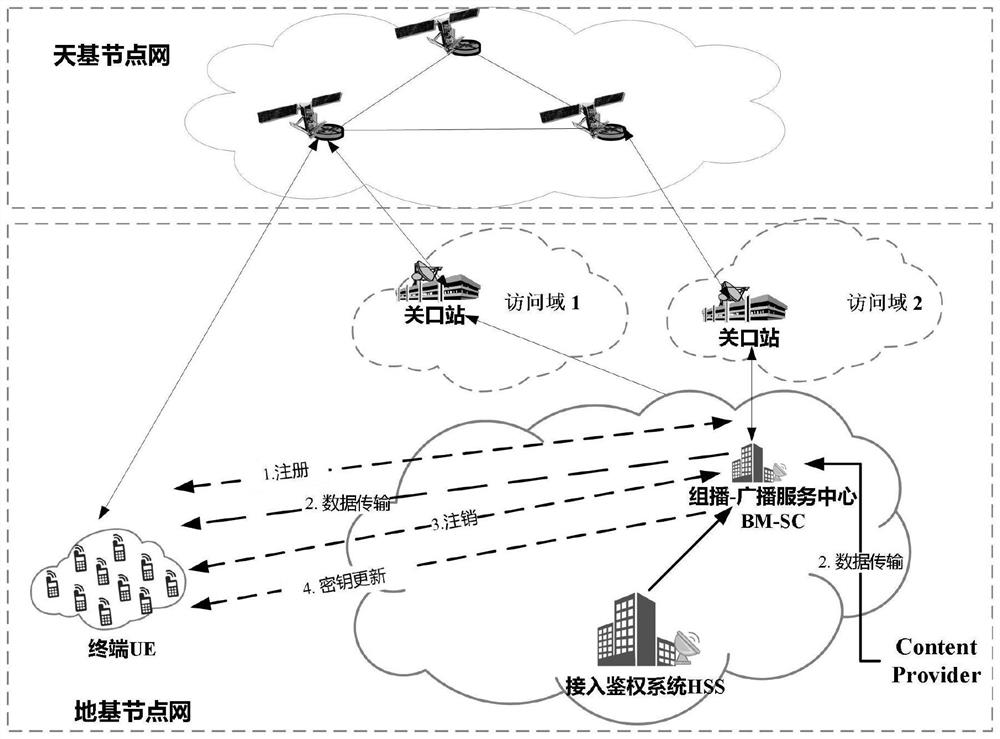
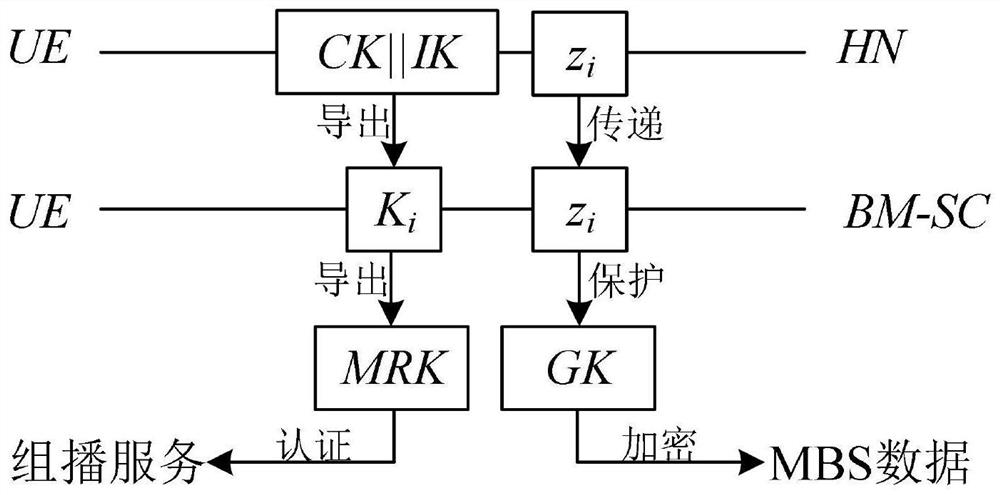
[0078] The embodiment of the present invention describes the establishment process of the shared key of the system. First, the user UE generates a prime number z i , using the home domain network HN public key to encrypt z i Generate {z i} pb , send an access authentication request message to the ground service network SN through the satellite network, which contains the user identity information SUCI i ,{z i} pb And multicast service request flag mbs_req (1bit). Then access the space-ground integrated network based on the 5GAKA mechanism. After the access authentication is successful, the user side saves z i . The home network HN decrypts to obtain z i . At the same time, based on the negotiated shared key, UE and HN respectively derive the shared key K between UE and BM-SC i =KDF(CK||IK,RAND,IMSI,BM-SC ID ) and Temporary ID TID i =h(IMSI,K i ). Among them, KDF() is the key derivation function, h() is the one-way hash function, CK, IK, RAND are the 5GAKA key ne...
Embodiment 2
[0080] The embodiment of the present invention describes the user multicast service registration process of the system. Each user needs to preset BM-SC address in advance to receive broadcast messages, and BM-SC broadcasts the services it can provide to users in the area through Satellite-RAN, and sets a timer at the same time. After receiving the broadcast message, the user initiates a multicast service registration request through the satellite network.
[0081] (1)UE i generate random number r i , together with the user's temporary identity TID i Initiate a multicast service registration request to Satellite-RAN.
[0082] (2) Assuming that n user requests are received when the timer expires, Satellite-RAN will receive all registration requests 1 ,...,TID n ,r 1 ,...,r n ,uG ID ,sRAN ID >Sent to BM-SC, where uG ID Used to identify user groups, sRAN ID It is the identity of the Satellite-RAN.
[0083] (3) After the BM-SC receives the message, according to the TID o...
Embodiment 3
[0091] The embodiment of the present invention describes the safe distribution process of the user multicast key of the system.
[0092] (1) BM-SC calculates the group key. First, a random number GK is generated as a group key. calculate and Y i ≡X i -1 (modz i ). make calculate Generate a random number GK as the multicast key, and calculate b=a×GK.
[0093] Then, set the group key validity period ET GK , the group key identifies GK ID Increment, calculate MAC GK =h(b,ET GK ,GK ID ,z i ), put b, ET GK 、GK ID and MAC GK Sent to the satellite, the Satellite-RAN multicasts this message to the UE.
[0094] (2) User UE i After receiving the message, verify b, ET GK Integrity of GK, GK≡b(modz i ).
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com