Improved anonymous authentication method based on conditional privacy protection
An anonymous authentication and privacy protection technology, which is applied in the direction of services, electrical components, and vehicle parts based on specific environments, and can solve the problems of long calculation time for anonymous certificates and signature authentication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
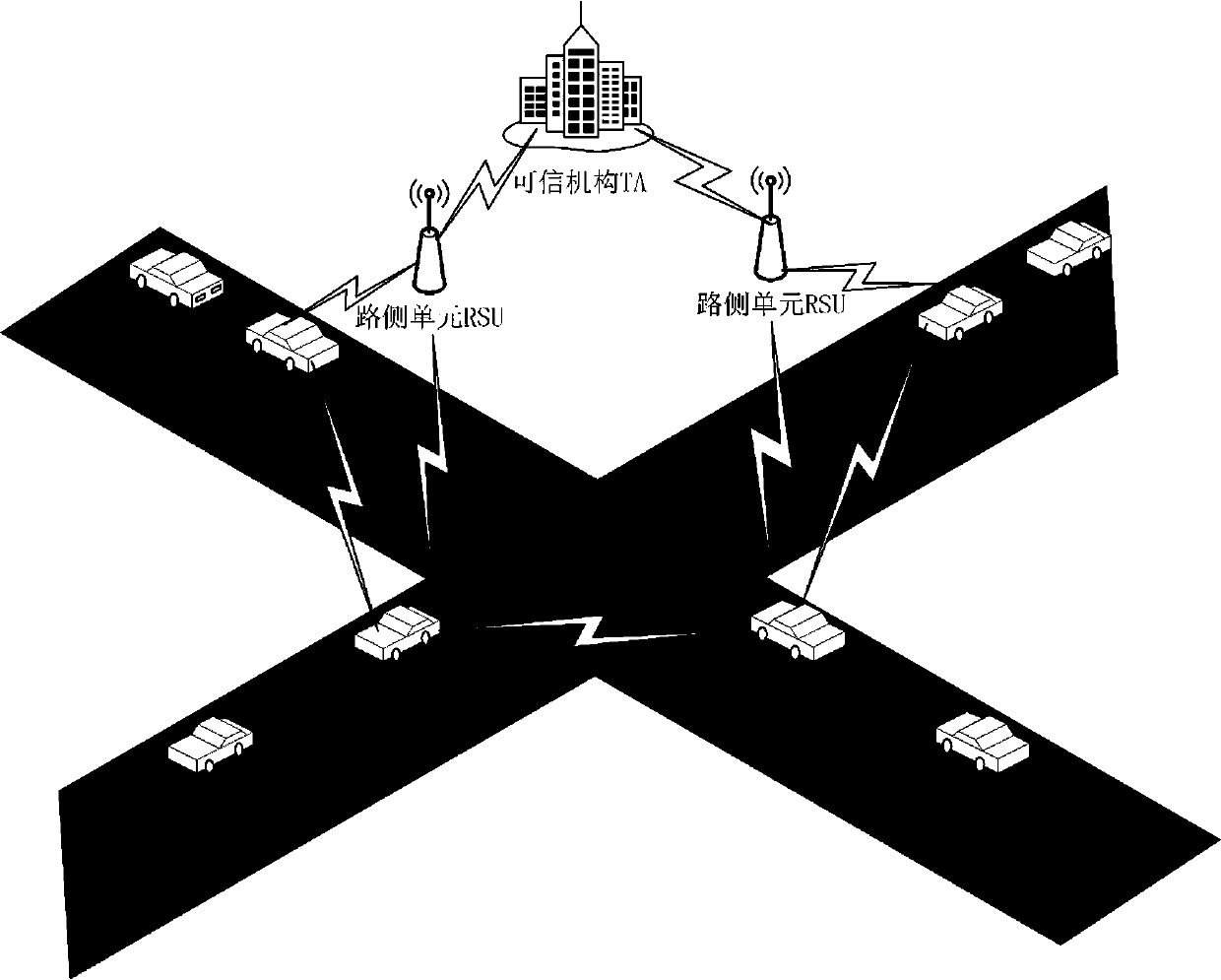
[0054] This example is carried out under certain system assumptions, the specific system model such as figure 1 As shown,
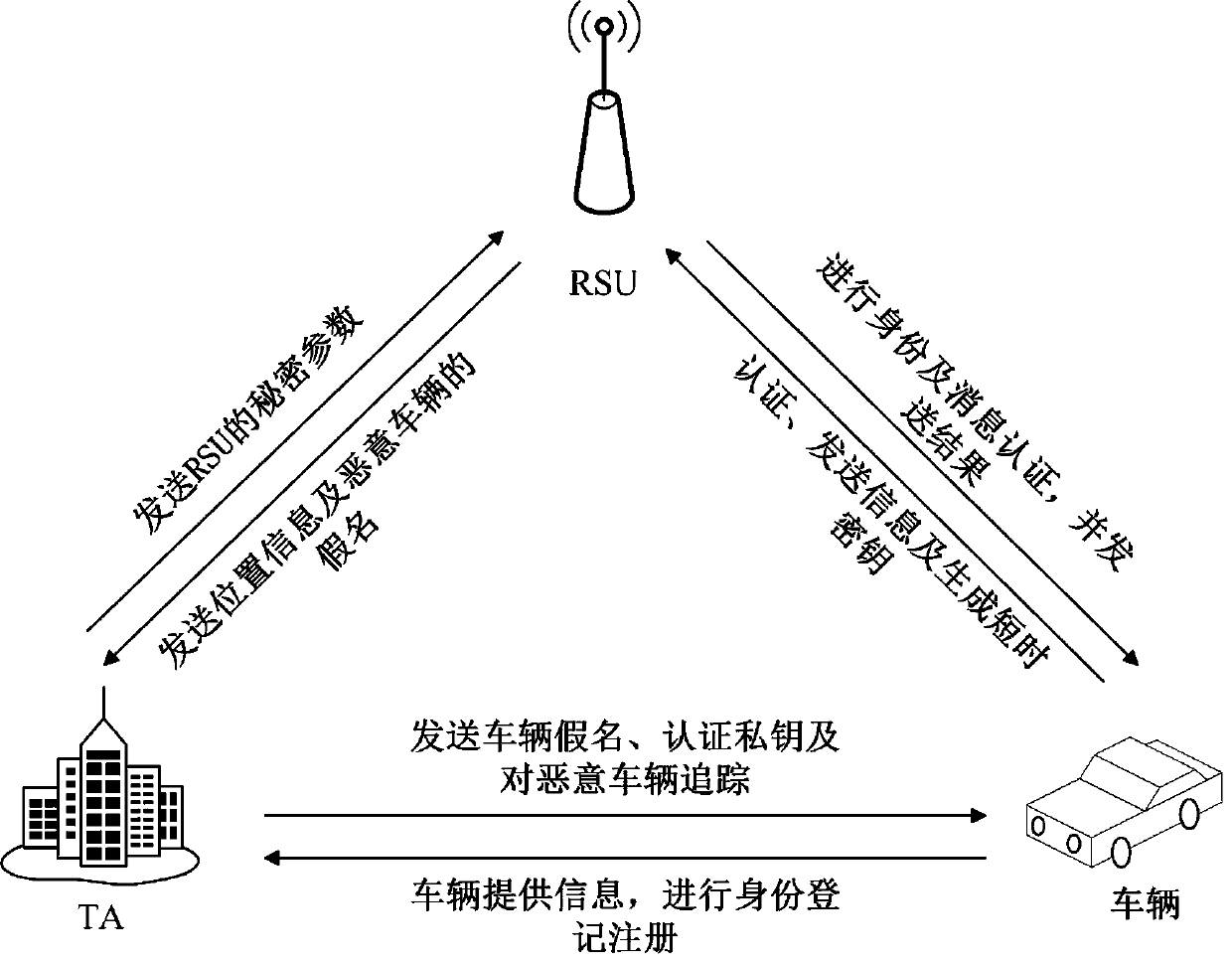
[0055] Such as figure 2 As shown, an improved anonymous authentication method based on conditional privacy protection using this system model includes the following steps:
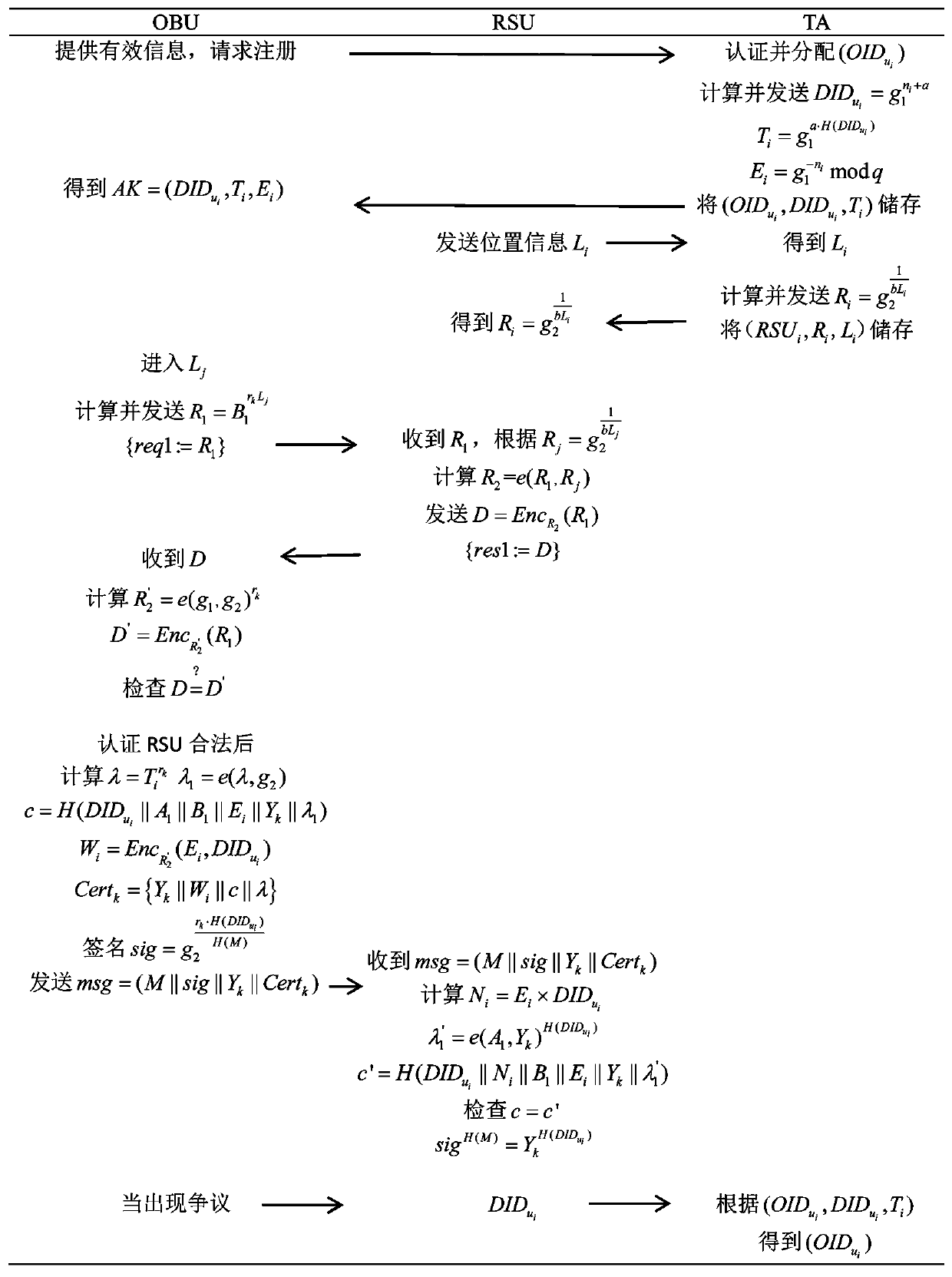
[0056] 1) System initialization, the process is as follows:
[0057] (1) Choose three cyclic groups G 1 ,G 2 ,G T , Their orders are all large prime numbers q, starting from G 2 To G 1 , Generate a homomorphic mapping ψ:G 2 →G 1 , And satisfy ψ(g 2 )=g 1 , Where g 1 And g 2 Respectively G 1 And G 2 Generator of, so we get a bilinear mapping e:G 1 ×G 2 →G T ;
[0058] (2) According to the parameters in step (1) (G 1 ,G 2 ,G T ,e,q,g 1 ,g 2 ), the trusted agency TA generates other system parameters, and TA selects two random numbers As the private key of the system, and calculate As the public key of the system;
[0059] (3) TA chooses a one-way hash function H: And a secure symmetric encrypt...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com