Remote protocol authentication method based on biological features
A biometric, remote authentication technology, applied in the field of information security, can solve problems such as being unable to resist denial of service attacks, unable to protect user anonymity, and unable to provide performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0042] The present invention will be further described in detail with reference to the accompanying drawings and embodiments.
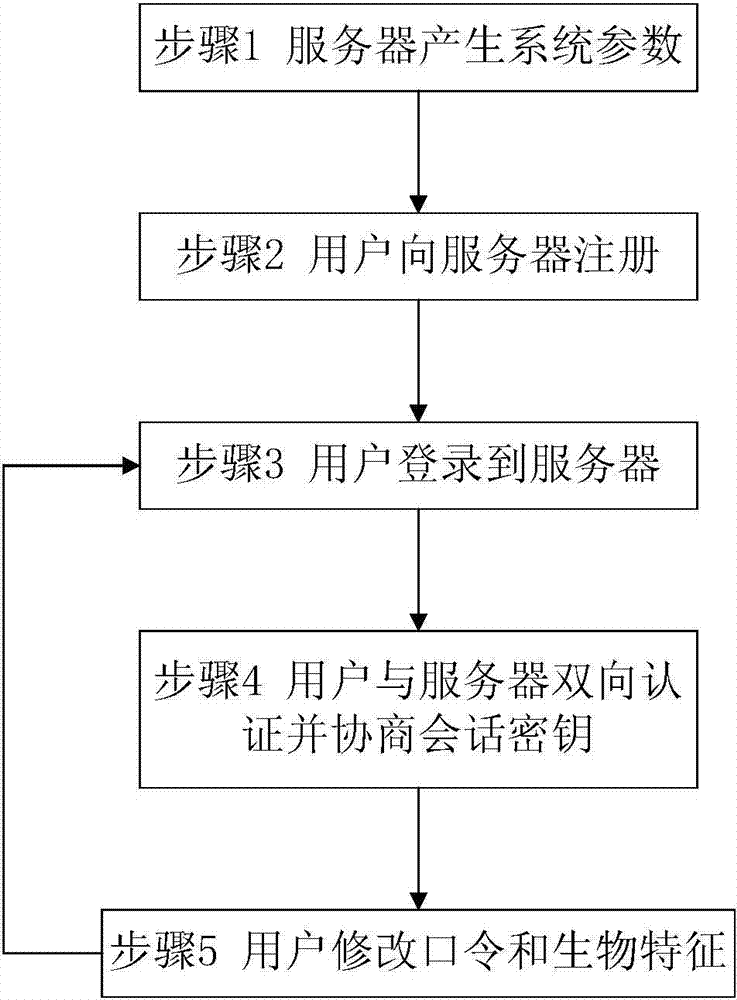
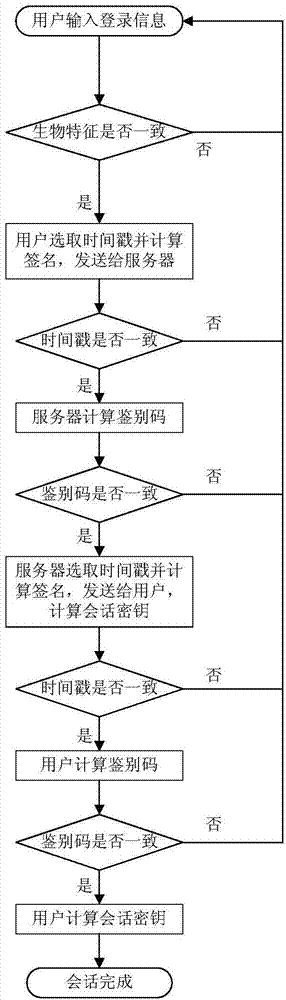
[0043] This protocol uses an efficient elliptic curve cryptosystem algorithm, through a reasonable design of the protocol process, based on multiple factors such as biometric features, passwords and smart cards, it has strong security performance and fast calculation speed, and can be specifically applied in telemedicine and other systems, such as figure 1 The specific operation shown is as follows:
[0044] (1) System initialization
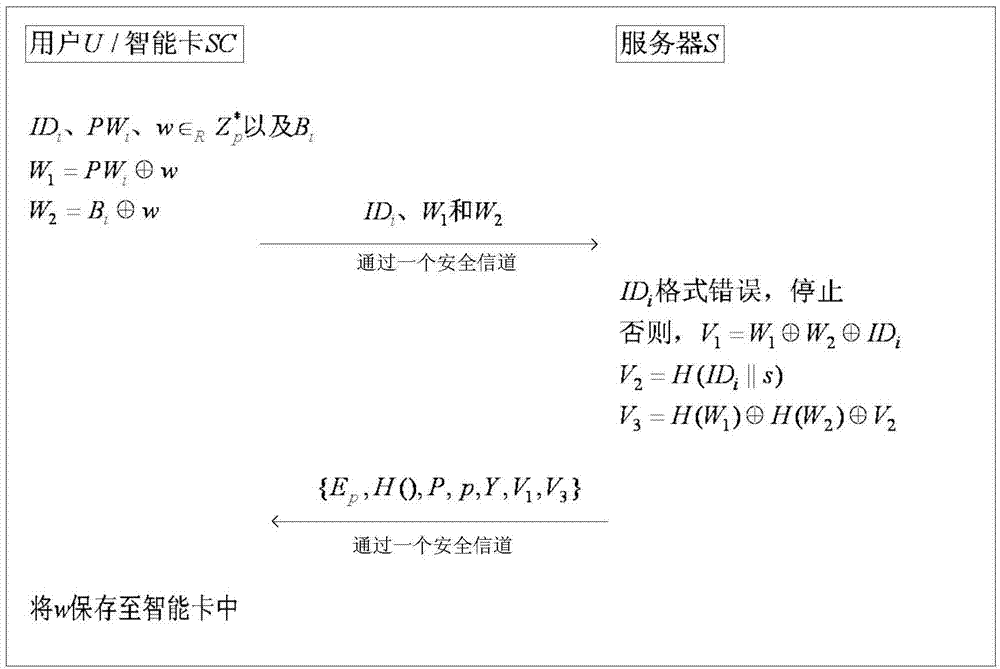
[0045] Server S will generate system parameters through the following steps.
[0046] (1) S selects the elliptic curve E:y 2 ≡x 3 +ax+b(modp),E p (a, b) is the nth-order point addition group of the elliptic curve E, and P is its generator, that is, n·P=O.
[0047] (2) S selection As your own private key and save it, calculate Y=s·P as the public key, and then choose a one-way hash function H ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com