An identity-based authentication method for space-based networks
An authentication method and network technology, applied in the field of space network security communication, can solve the problems of high network transmission delay, high cost, inapplicability, etc., and achieve the effects of reducing interaction, ensuring security, and reducing size
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
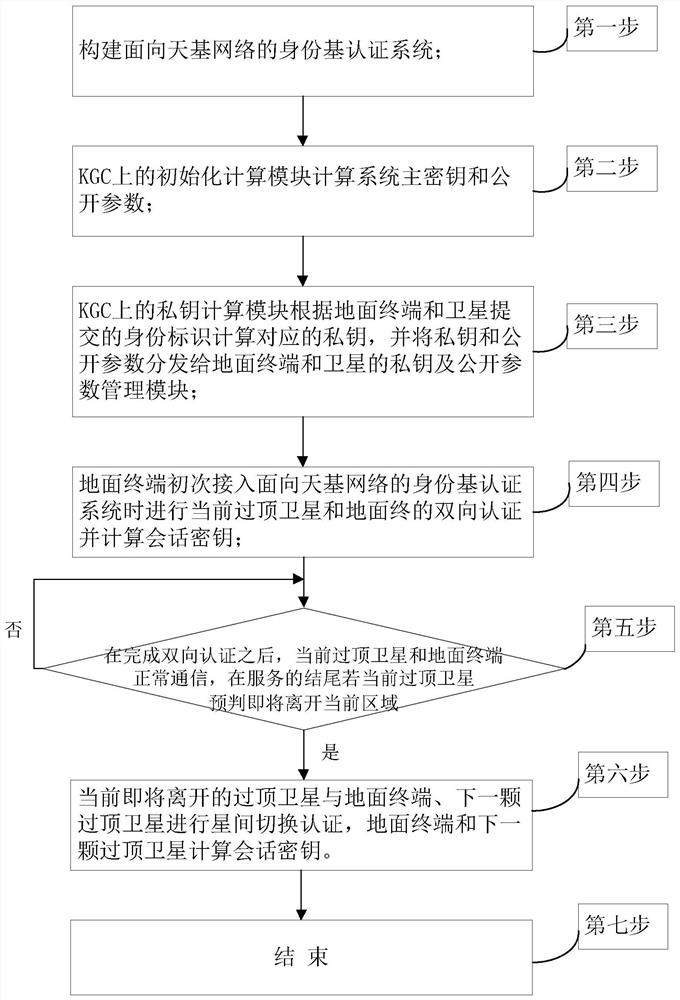
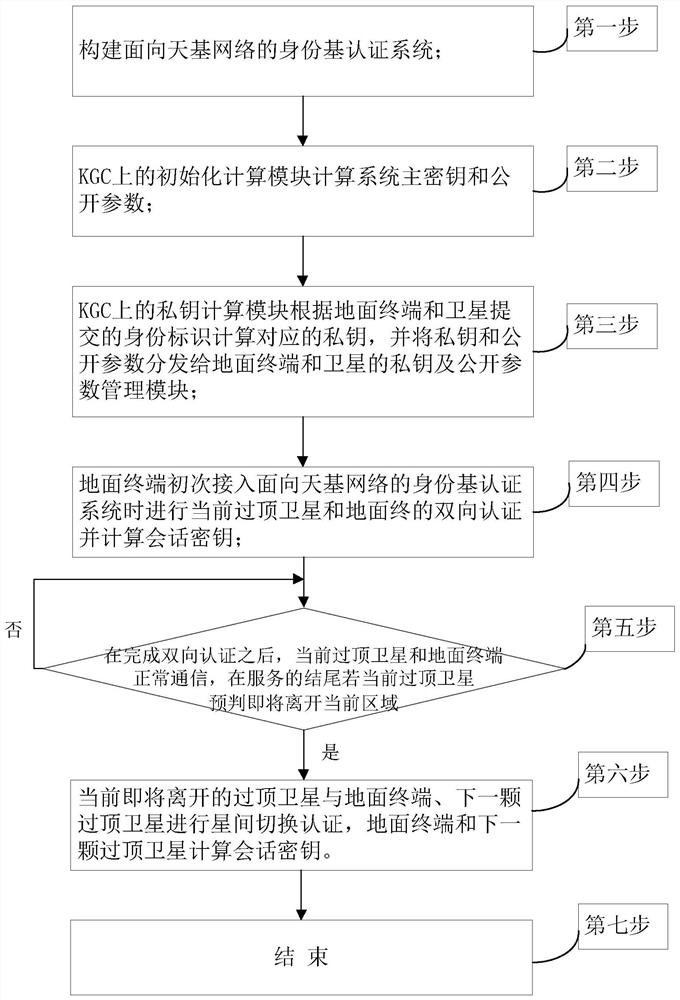
[0109] figure 1 It is an overall flowchart of the present invention; the present invention comprises the following steps:
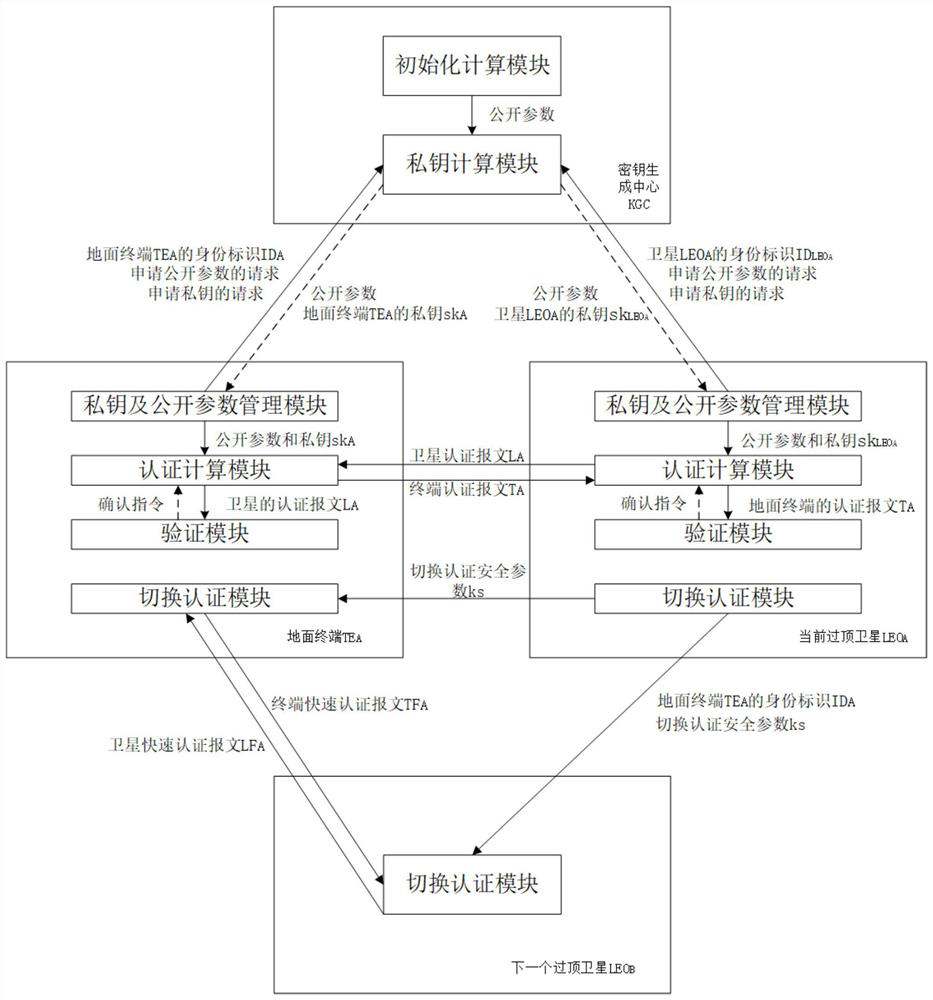
[0110] The first step is to build an identity-based authentication system for space-based networks. like figure 2 As shown, the identity-based authentication system for space-based networks consists of three types of network entities: ground terminals (denoted as TE), key generation centers (denoted as KGC), and low-orbit satellites (denoted as LEO). The KGC is connected to multiple TEs and LEOs through wireless links.
[0111] Before mutual authentication between TE and LEO, KGC uses an identity-based signature scheme with message recovery proposed by Kyung-Ah Shim (see Shim K-A. Basis: A Practical Multi-User Broadcast Authentication Scheme for Wireless Sensor Networks[J] .IEEE Information Forensics and Security Transactions.2017,PP:1-1.The English literature index is Shim K-A.BASIS:APractical Multi-User Broadcast Authentication Scheme in Wireless Se...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com