Handover Authentication Method with Privacy Preservation in LTE/Lte‑A Networks
A privacy protection and switching authentication technology, which is applied in the field of switching authentication of bilinear pairing operation, can solve the problems of leakage, identity and location, etc. switching effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
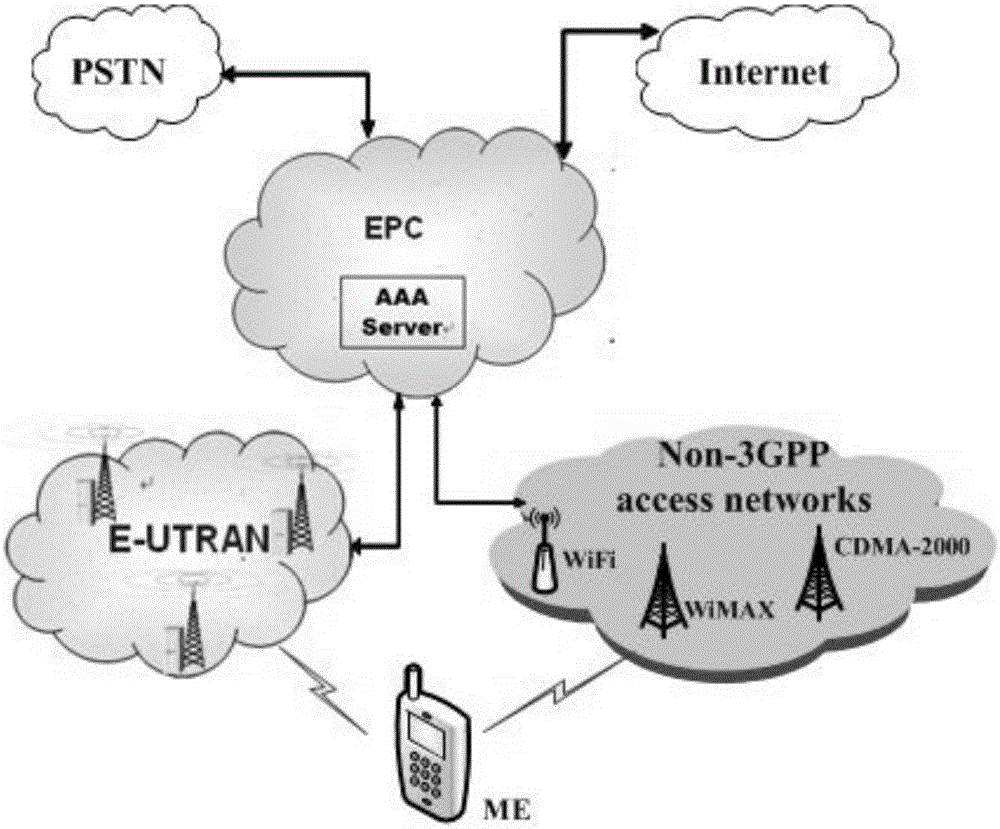
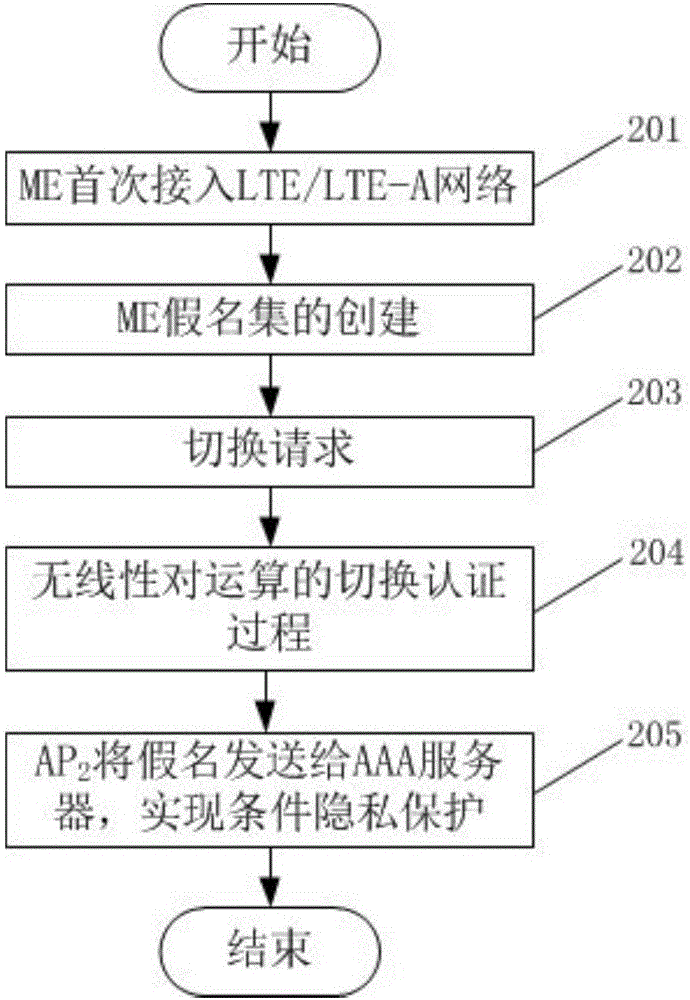
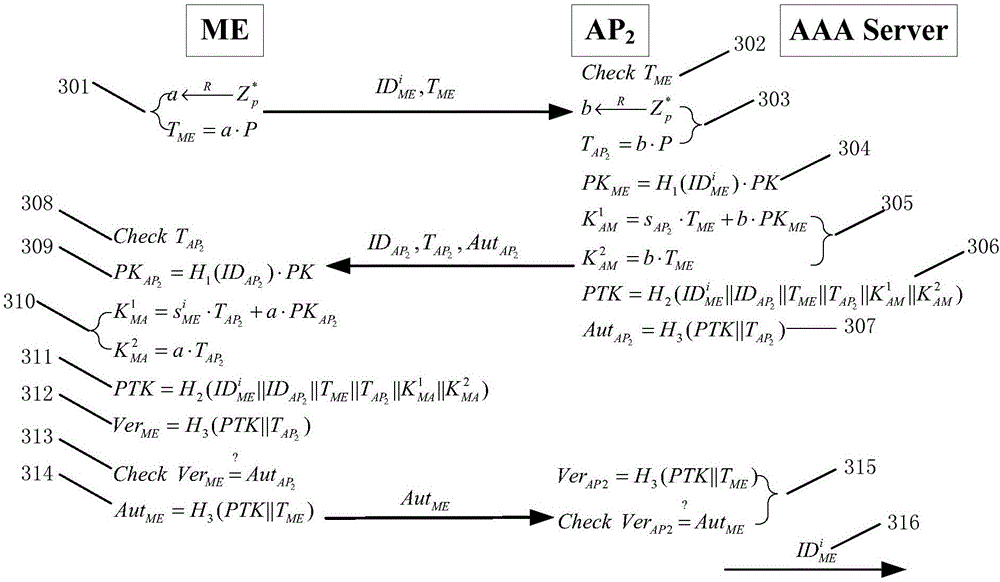
[0026] In the handover authentication method with privacy protection in the LTE / LTE-A network of the present invention, the ME accesses the LTE / LTE-A network for the first time, and after successfully completing the access authentication with the AAA server, the AAA server generates a pseudonym set for the ME; When ME needs to switch to a new AP due to mobility, it only needs to select a pseudonym from the pseudonym set for identity authentication without providing the real identity of ME, so as to avoid the leakage of user identity and location privacy and achieve anonymity and untraceability. In the handover authentication process, the method negotiates keys based on the Diffie-Hellman key exchange algorithm, completes the mutual authentication process through hash function value verification, does not use bilinear pairing operations, and reduces authentication delay.
[0027] The present invention specifically includes two parts: the system initialization stage and the hand...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com