A WMN anonymous access authentication system and method based on proxy ring signature
An access authentication and ring signature technology, applied in wireless communications, electrical components, security devices, etc., can solve the problems of high computational overhead, reduced applicability, and no consideration of user anonymity, so as to reduce authentication delay and ensure communication security. , the effect of preventing privacy leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] The specific implementation manners of the present invention will be described in detail below in conjunction with the accompanying drawings.
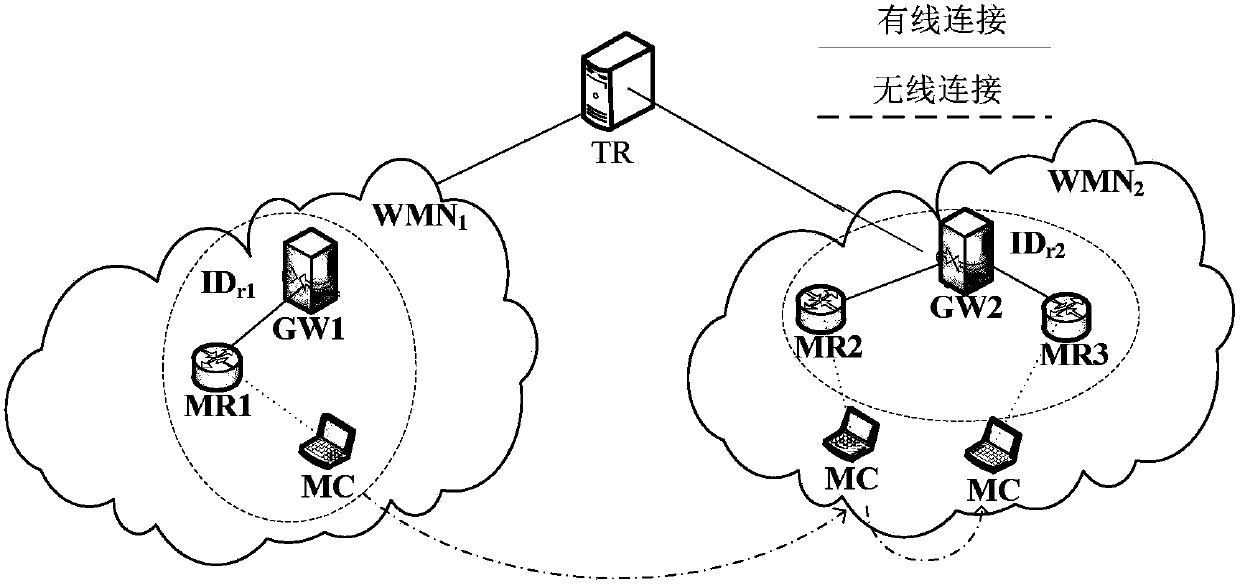
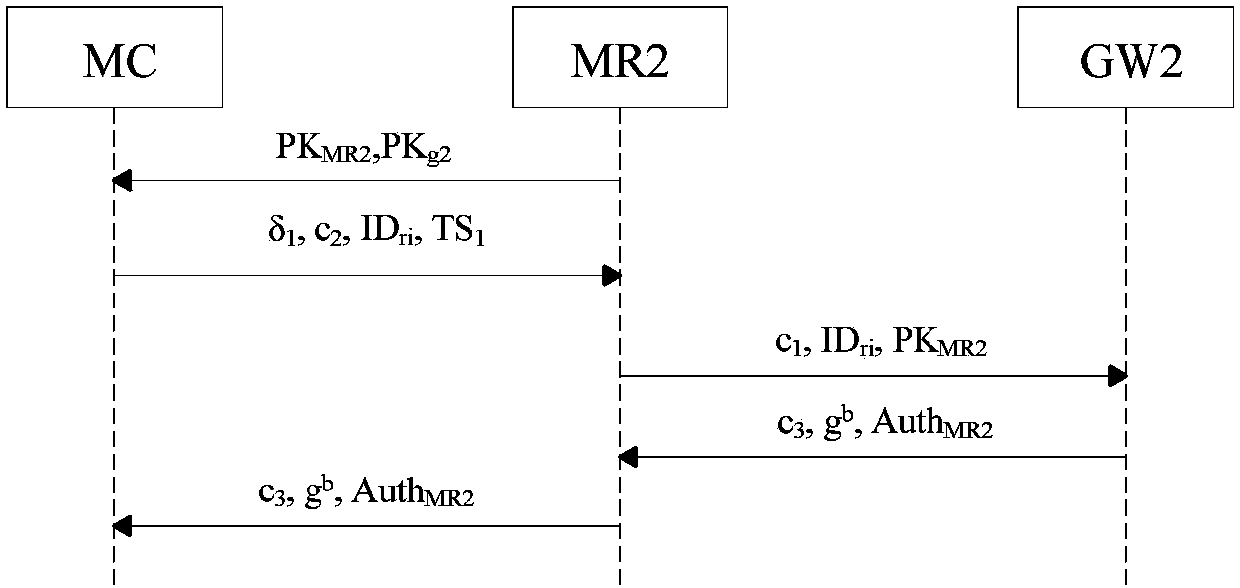
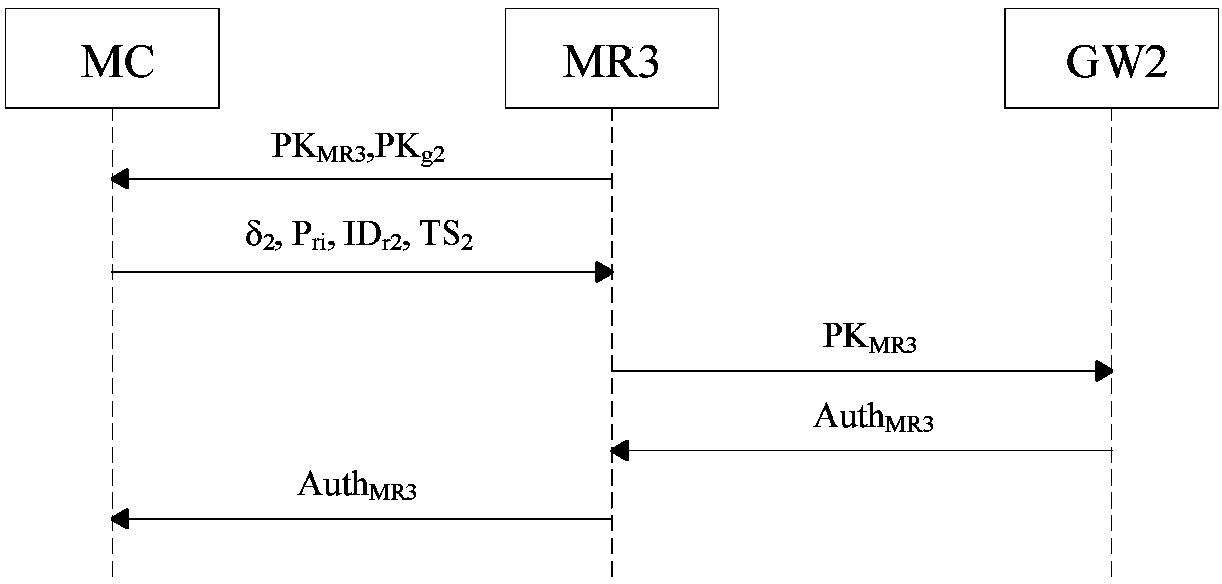
[0038] This embodiment is to apply the WMN anonymous access authentication system and method based on the proxy ring signature to the wireless MESH network access authentication link. In the specific implementation process, the proxy ring signature scheme is adopted to realize anonymous access authentication of users and fully protect the privacy of users. At the same time, a certificateless signature scheme is adopted to realize efficient switch authentication of users.
[0039] Such as figure 1 As shown, the WMN anonymous access authentication system based on proxy ring signature includes a trust center TR, two gateways (GW1 and GW2), multiple MESH routers and mobile clients, a gateway (Gateway, GW), and several underlying A Mesh Router (Mesh Route, MR) and several mobile client nodes (Mesh Client, MC) form a proxy ring signe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com