Method and device for preventing denial of service (DoS) attacks
A denial of service attack and purpose technology, which is applied in the network field where the identity mark and the location mark are separated, can solve problems such as excessive load of network equipment and failure to work normally, and achieve the effect of preventing denial of service attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
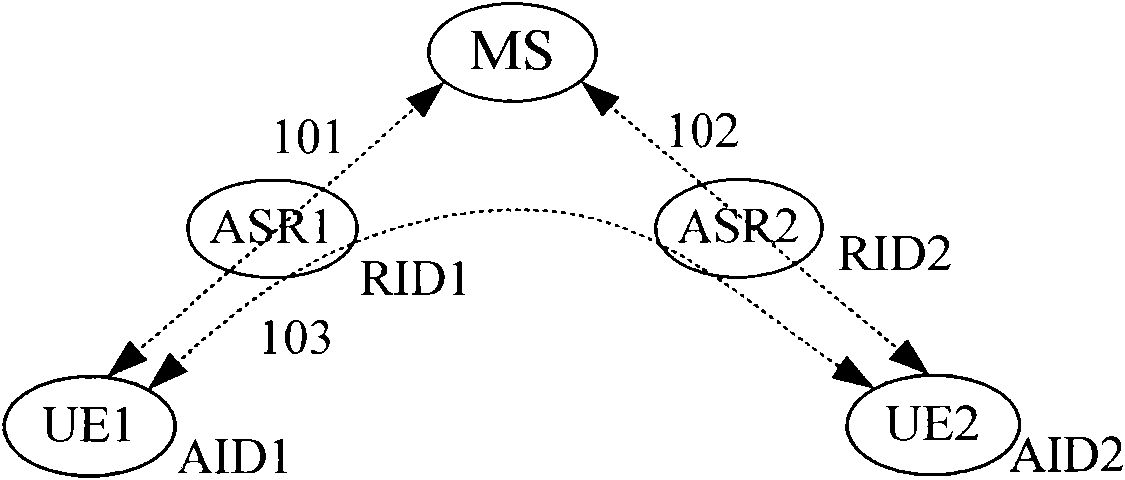
[0064] Figure 5 Shown is another network architecture that realizes the separation of identity identifiers and location identifiers. In this architecture, the network is divided into an access network and a backbone network. The access network is located at the edge of the backbone network and is responsible for the access of all terminals. The backbone network is responsible for the routing and forwarding of data packets between terminals accessed through the access network. There is no overlap between the access network and the backbone network in topology.
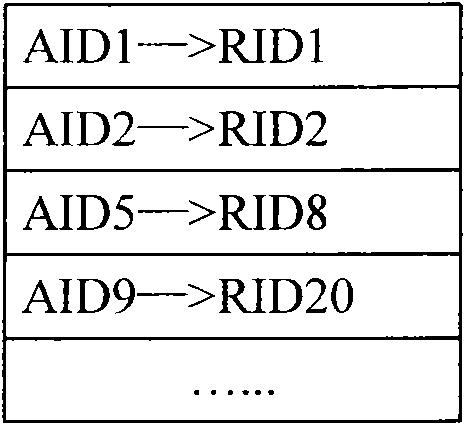
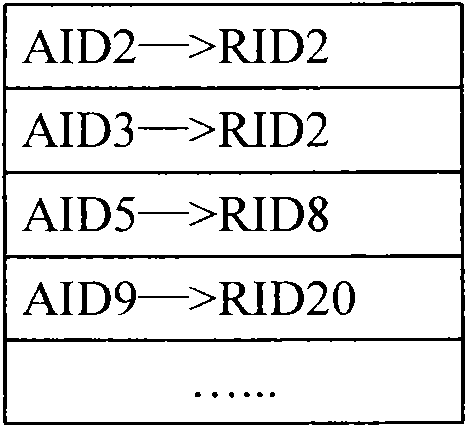
[0065] There are two types of identifiers in the network of this architecture: Access Identifier (AID: Access Identifier) and Routing Identifier (RID: RoutingIdentifier). Among them, AID is the user identity identification of the terminal, which is used to identify the identity of the terminal user (also referred to as the user for short). The network uniquely assigns an AID to each terminal user. Change; RID is a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com