Service denial detection method for large data platform
A big data platform, denial of service technology, applied in the field of big data security, can solve the problems of denial of service attacks, cluster security hardening guidance is not effective, and achieve the effect of preventing denial of service attacks, preventing malicious damage, and simple deployment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
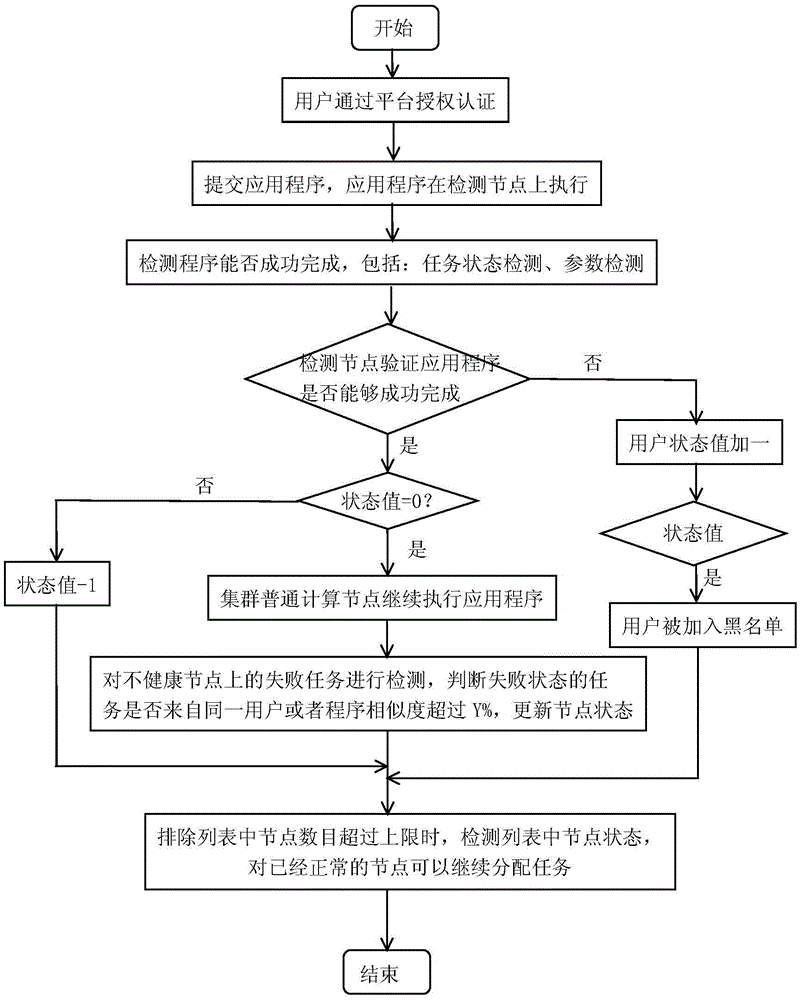
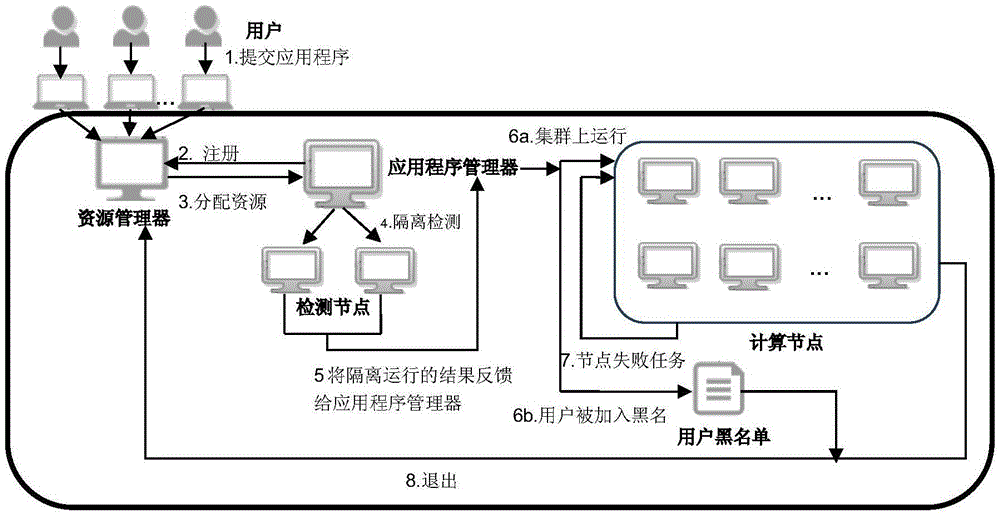
[0041] Take Hadoop YARN as an example.
[0042] 1) In the actual situation, the administrator divides the cluster, divides 5% of the nodes (more than 10) as detection nodes, and 95% of the nodes as ordinary computing nodes, and configures the user's default submission queue as the queue where the detection nodes are located , all user applications are first submitted to the detection node to run.
[0043] 2) The MapReduce program submitted by the user can be detected in two ways:
[0044] ①Map task status detection, adding a log scanning engine engine on the detection node to track the running status of the task. If there is a problem, such as throwing an exception or failing to complete successfully, the task status is read from the log as failed, and subsequent resources are no longer available. distribute.
[0045] ② Parameter detection, to detect the parameters of the MapReduce program that can be set by the user, for example, to detect the program timeout time, the defa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com