Method for realizing safety model of access authentication in mobile internet
A mobile Internet and security model technology, applied in the security field of the mobile Internet, can solve the problem of large data transmission volume, achieve the effects of small authentication delay, load balance, and prevent denial of service attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
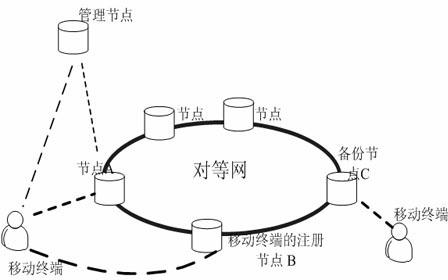
[0030] 1. System structure:
[0031] The entire authentication scheme is for the user terminal to quickly access the mobile Internet and realize the two-way authentication of the user and the network node. The authentication process includes user access to the network, user authentication network service node, service node authentication user node, session key generation and other parts. Due to the need to realize information exchange between two different platforms, two sets of TCP-based socket transmissions are established. One group of sockets is used to realize the information transmission between the user terminal and the management node, and the other group of sockets is used to realize the authentication service between the user terminal and the authentication server. All other functional modules are implemented separately on the two platforms.
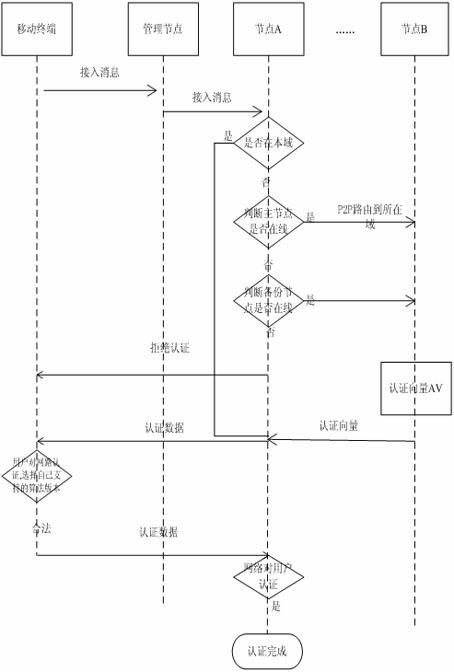
[0032] 2. Method flow
[0033] 2.1 Introduction to Authentication Scenarios
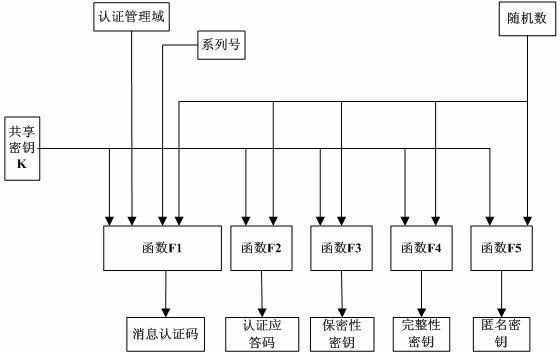
[0034] In order to facilitate the descr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com