RFID two-way authentication method based on Hash function and capable of updating keys synchronously
A synchronous update, two-way authentication technology, applied in the field of radio frequency identification, can solve the problems of limited storage space, computing power and power supply, difficult to apply, etc., to avoid denial of service attacks, prevent tracking, and ensure forward security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0057] The present invention will be further described below in conjunction with the accompanying drawings.
[0058] The protocol of the present invention includes three stages of system initialization, mutual authentication, and key update, and the specific interaction process is as follows:
[0059] 1. RFID system initialization
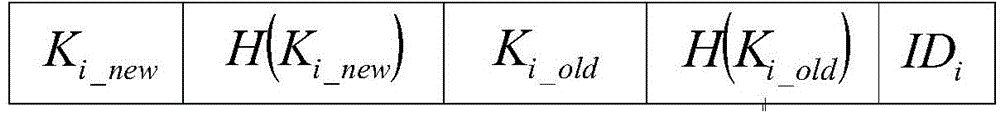
[0060] First initialize the RFID system, and the back-end database stores a record for each tag, such as figure 1 shown. Additionally, tags also store their own IDs i and key K i .
[0061] 2. System certification process
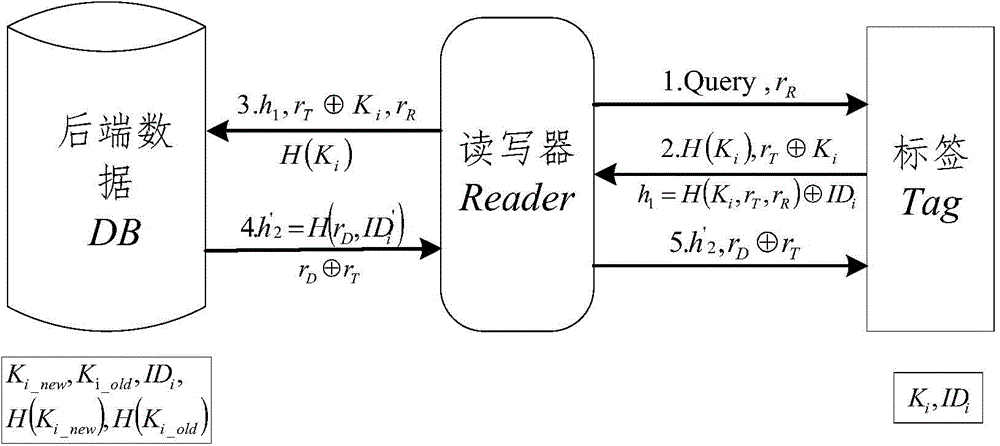
[0062] RFID system security certification process such as figure 2 As shown, the steps are as follows:
[0063] (1) The reader generates a random number r R , and send it to the tag together with the query command Query as an authentication request.
[0064] (2) The authentication of the tag by the reader
[0065] ① (reader → back-end database): the label receives the message {Query,r R}, also generate a random numbe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com