Patents
Literature
32results about How to "Improve defense efficiency" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
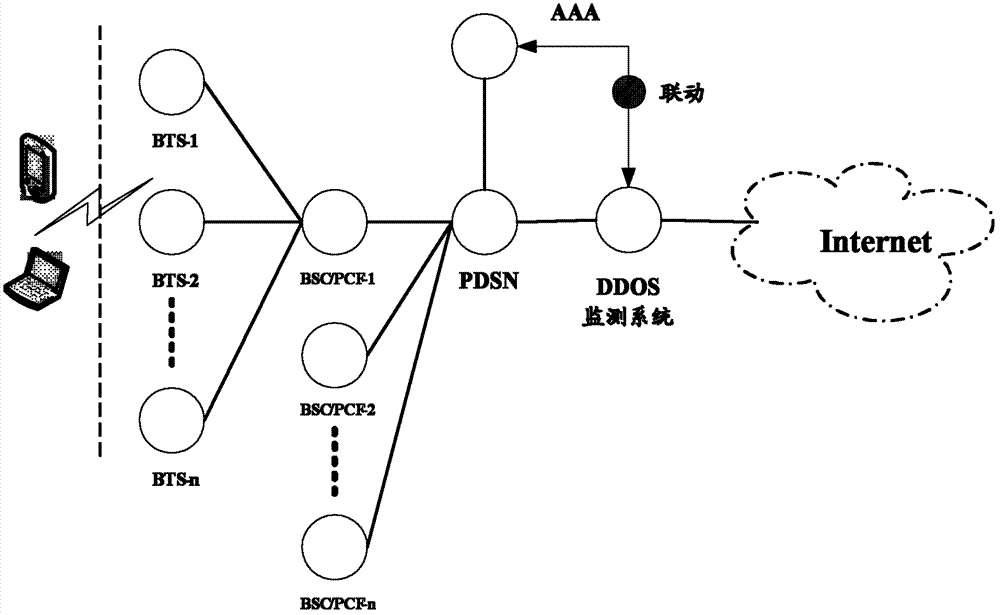
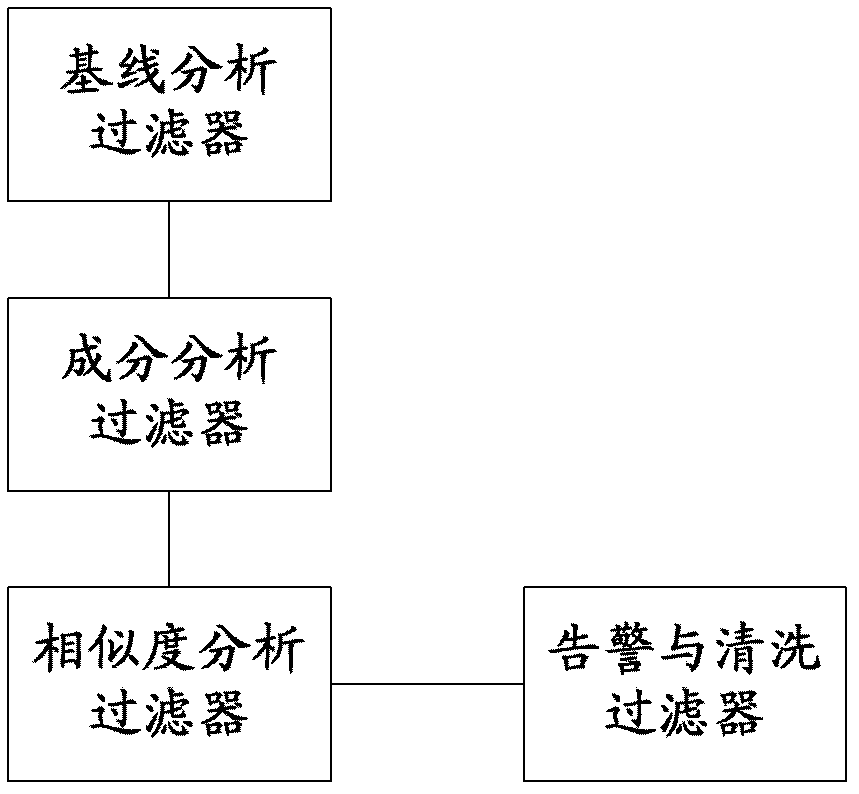
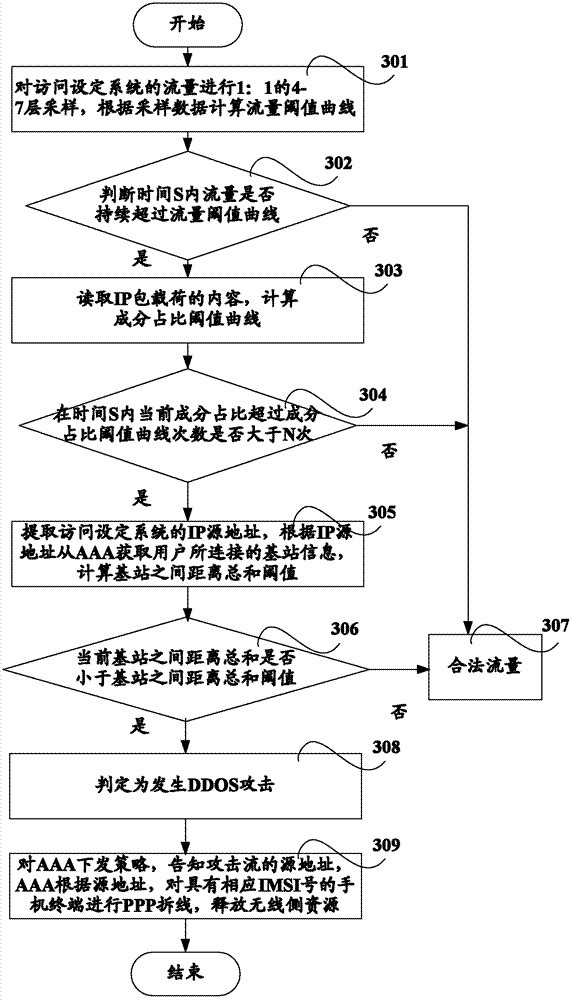
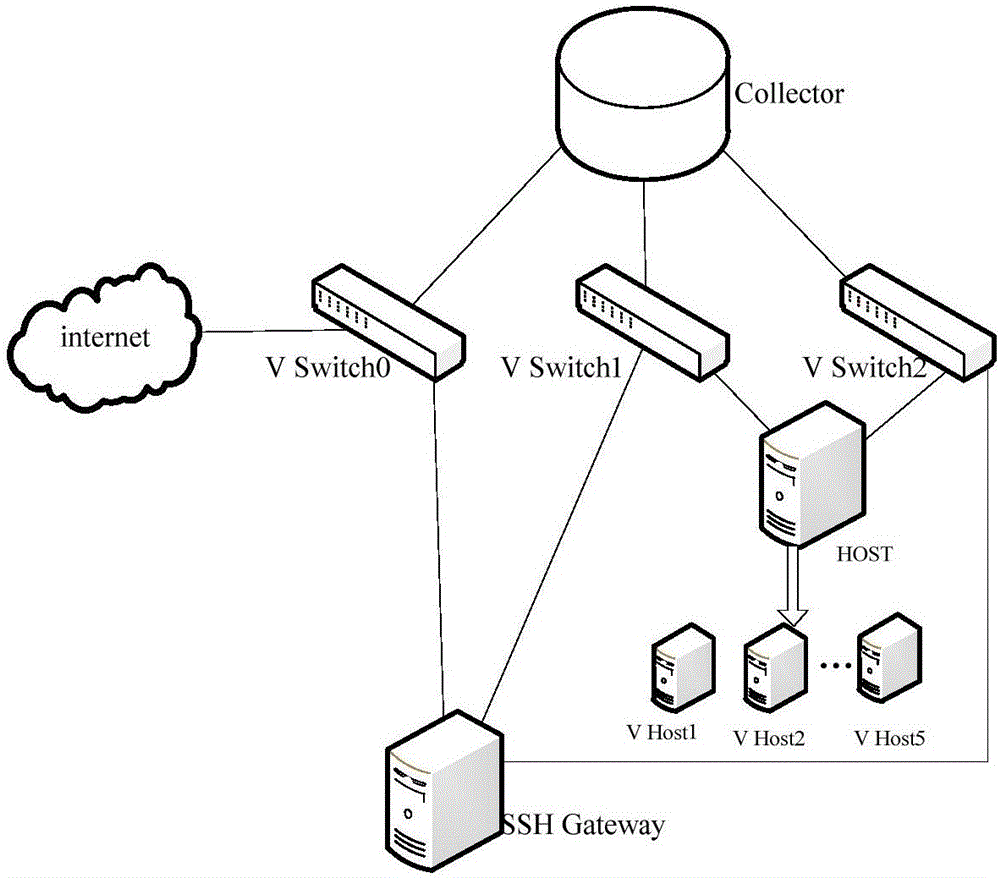
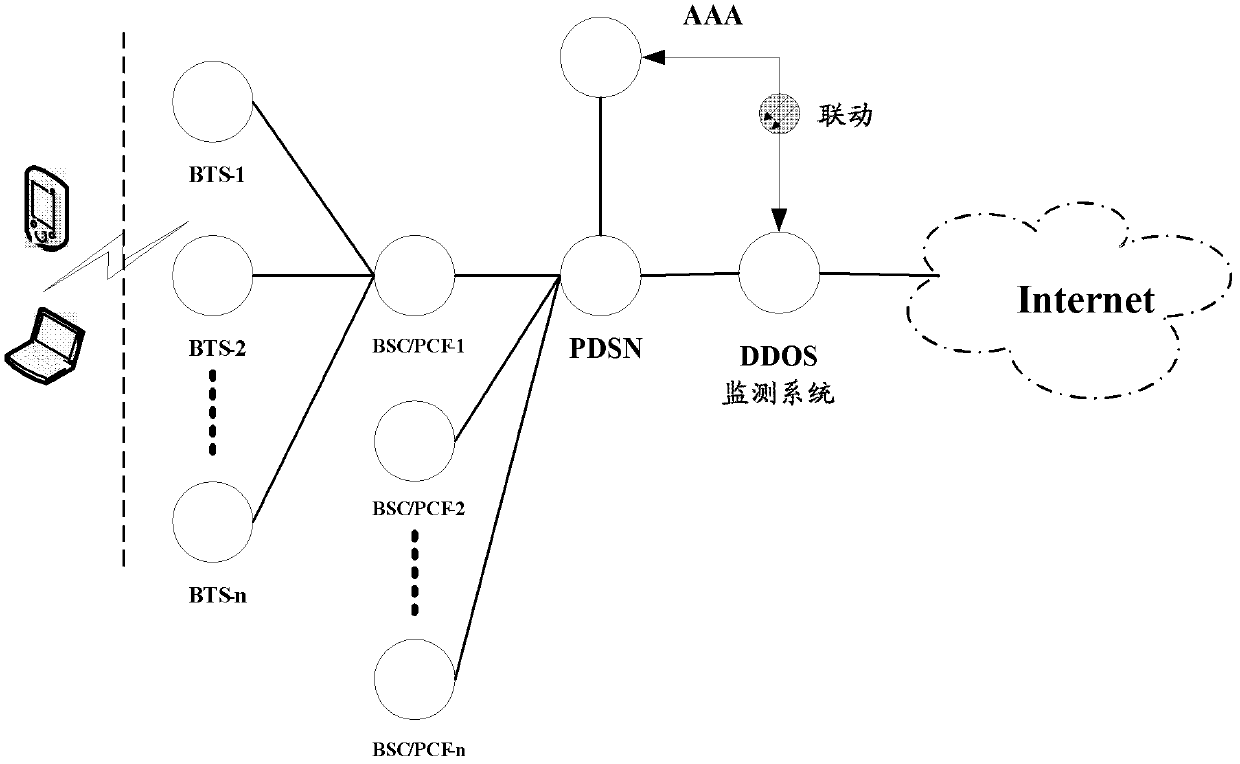
Method and system for monitoring DDOS (distributed denial of service) attacks in small flow
ActiveCN102821081AMake up for the inability to detect low-rate DDoS attacksHigh false positive rateData switching networksSimilarity analysisProtocol Application
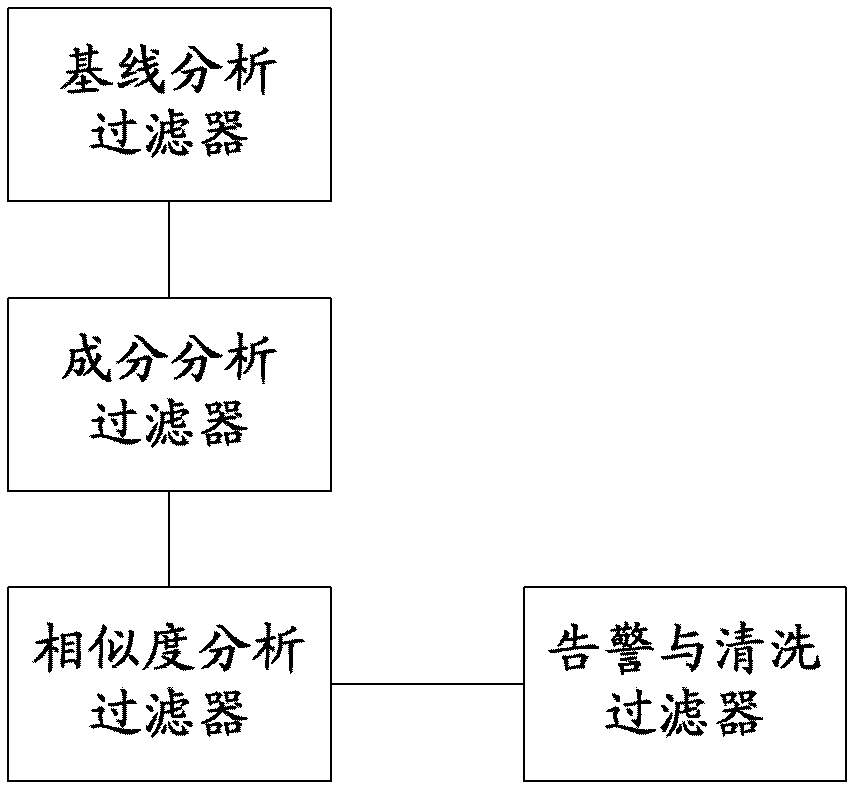
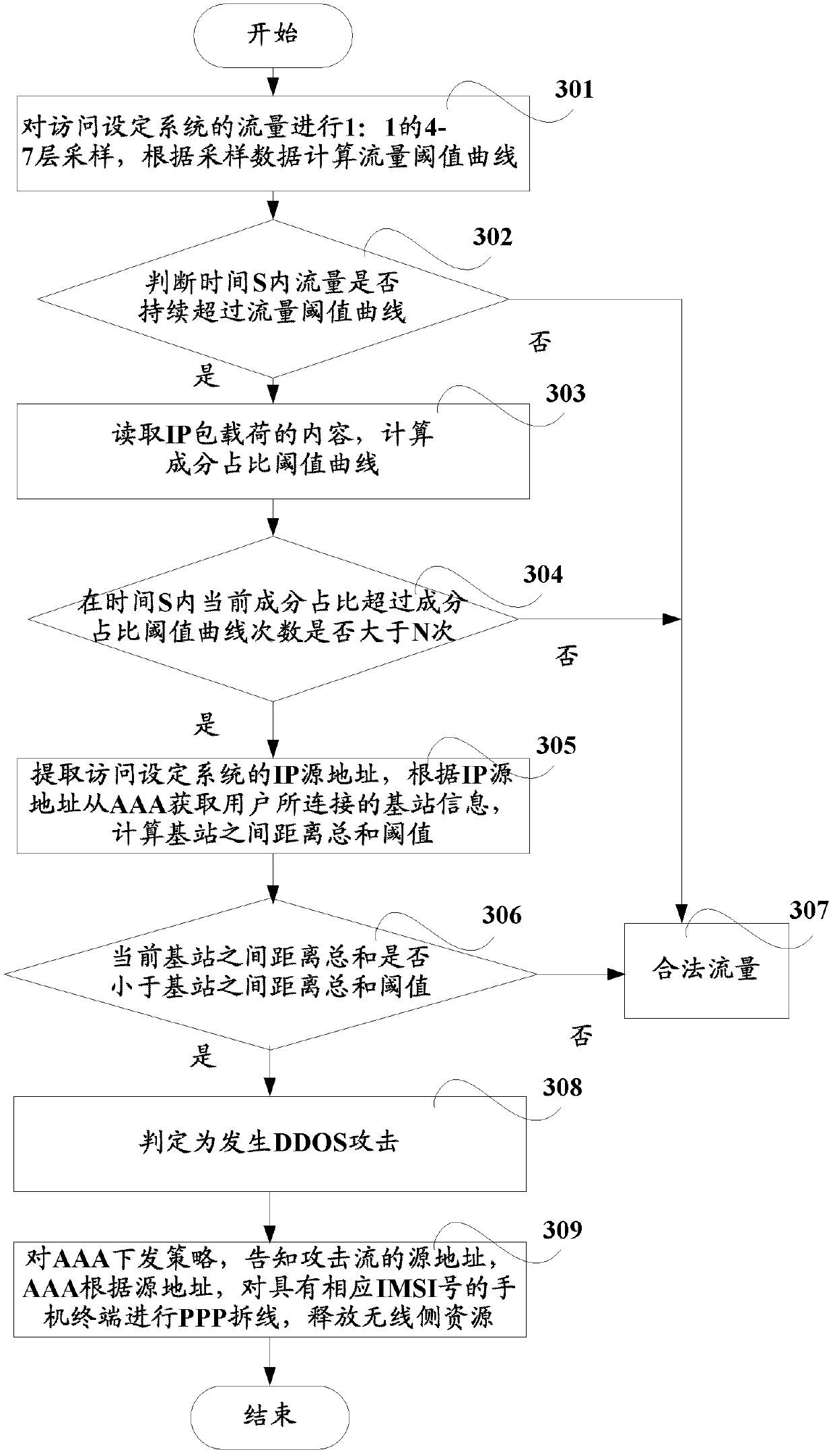
The invention discloses a method and a system for monitoring DDOS (distributed denial of service) attacks in small flow, solves the problems that the existing DDOS attack detection technology is high in cost, complex to implement and high in misjudgment rate, cannot respond to DDOS attacks aiming at an application layer and the like, and provides the monitoring scheme of an integrated DPI (dots per inch) technology. A baseline analysis, component analysis and similarity analysis method is used to establish a normal use model, characteristics are accurately matched to detect the attacks in small flow and the application layer attacks, deployment at one point of an operator network and complete coverage of the operator network are achieved, and detection accuracy is increased.
Owner:CHINA TELECOM CORP LTD
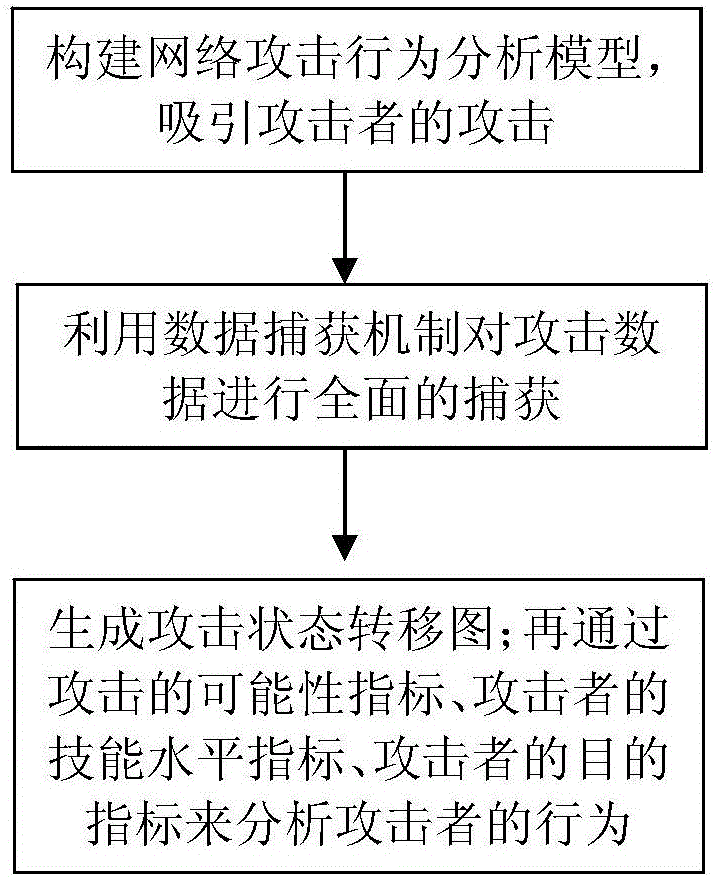
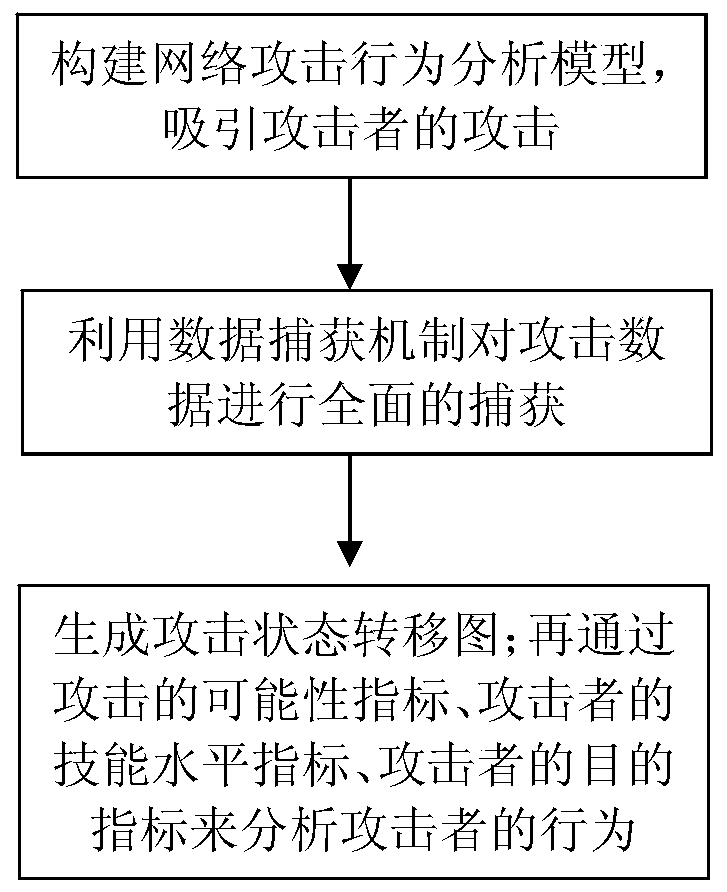
Network attacker behavior analyzing method based on attack graph
The invention discloses a network attacker behavior analyzing method based on an attack graph. The method comprises the steps of establishing a network attacker behavior analyzing model and attracting attacks of attackers; carrying out comprehensive capturing on attack data through a data capturing mechanism; and generating an attack state transfer graph through combination of a finite-state machine and analyzing behaviors of the attackers according to possibility indexes of attack behaviors, skill level indexes of the attackers and destination indexes of the attackers. According to the network attacker behavior analyzing method based on the attack graph provided by the invention, the good foundation can be laid for design of an active defense system, the network attacks can be defended, the attacks can be prevented before the network attacks occur, one part of the attacks are screened, a cybercrime can be effectively prevented, the defense efficiency is improved, and the defense cost is reduced.
Owner:HANGZHOU SUNYARD DIGITAL SCI
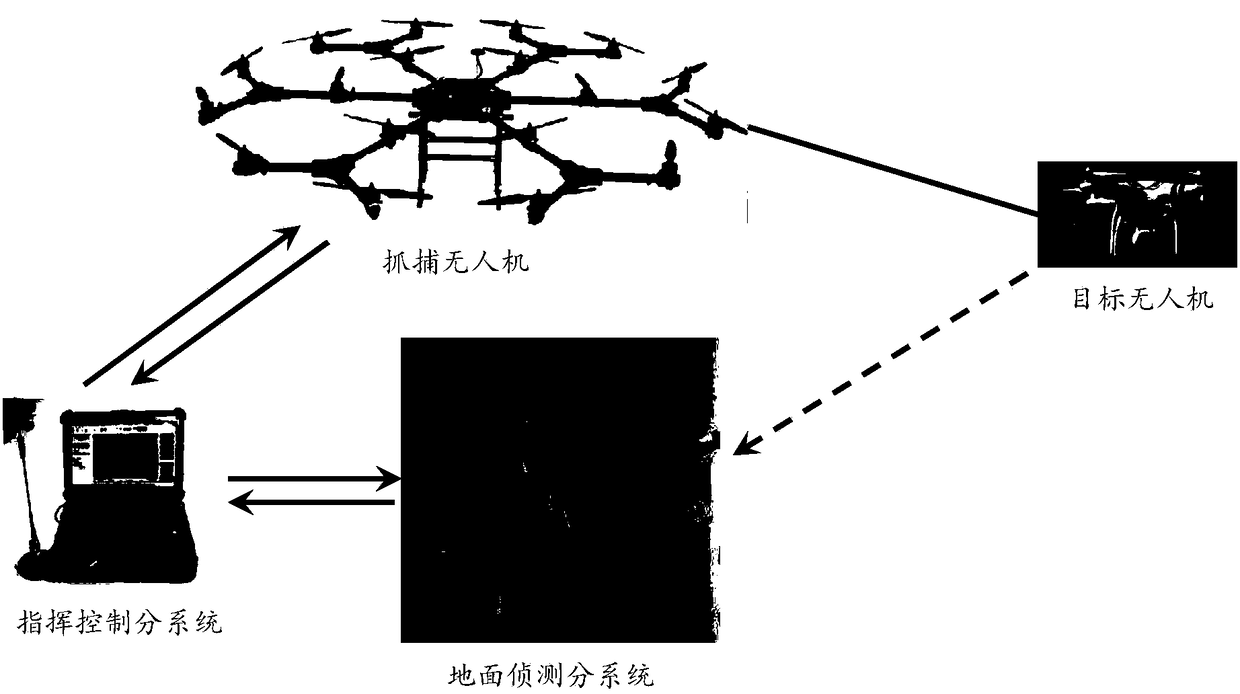
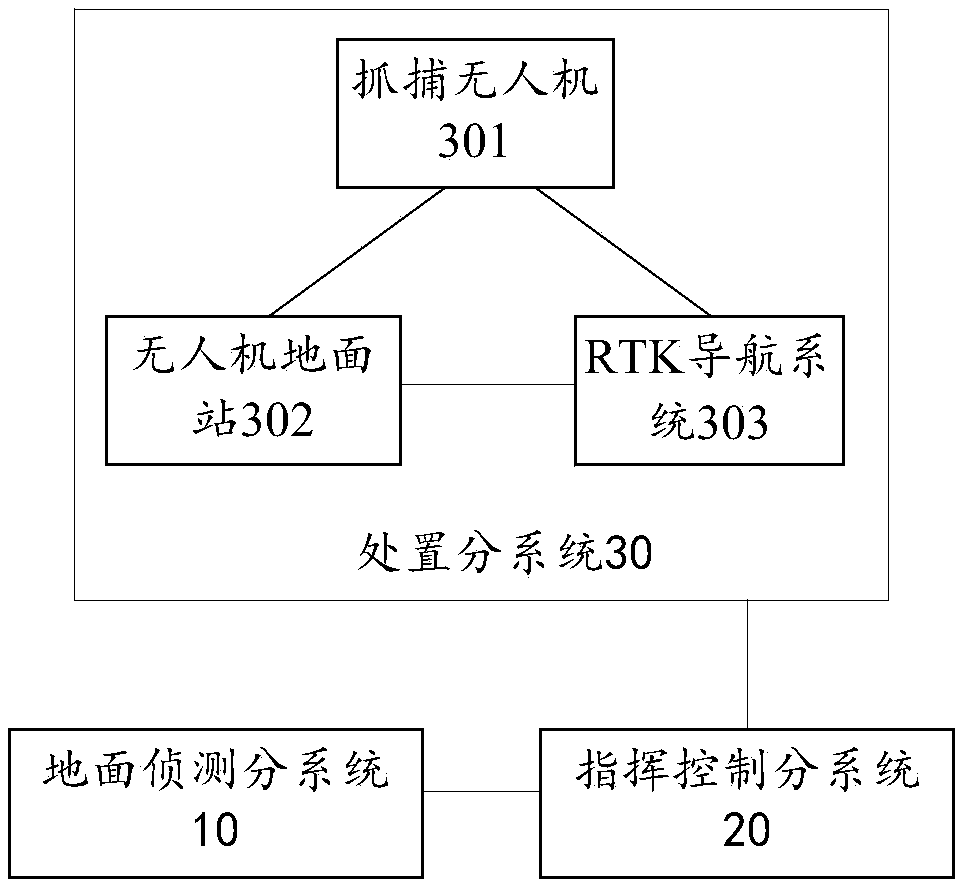
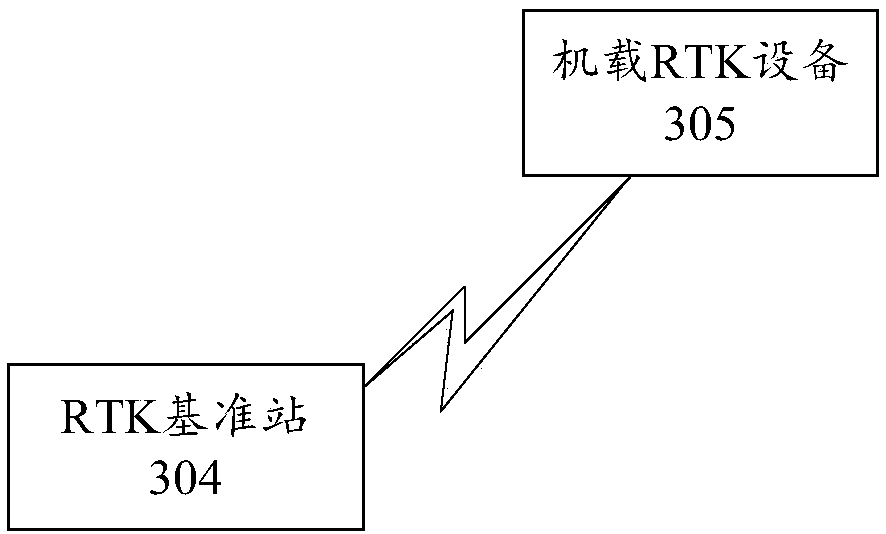
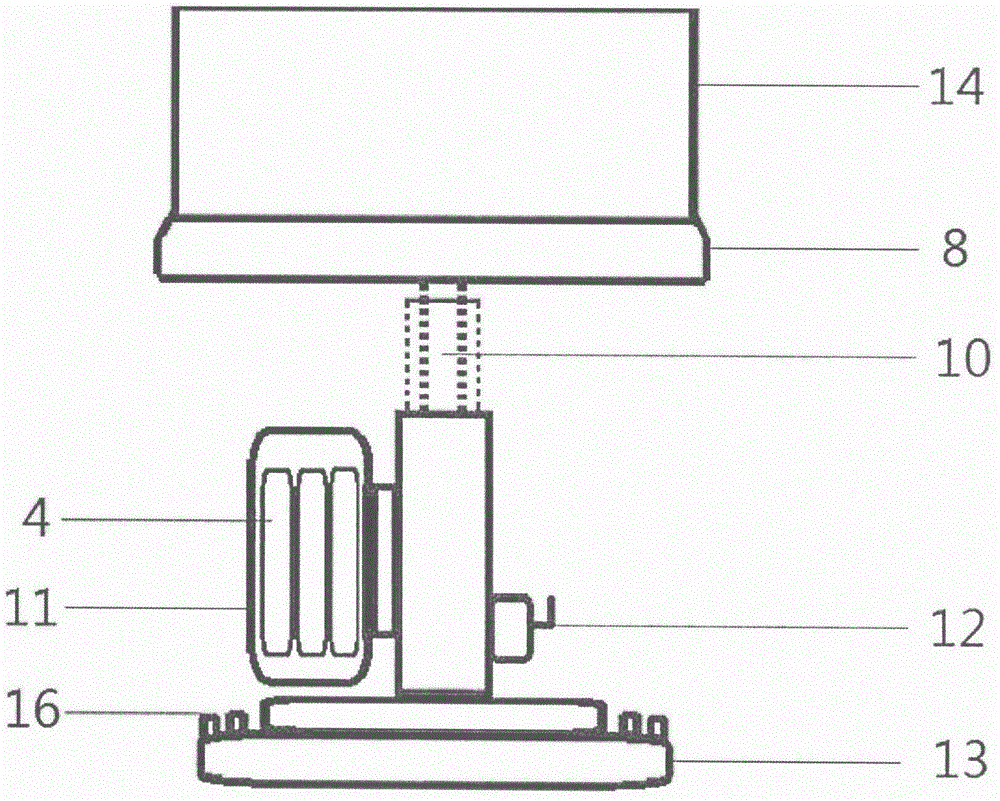
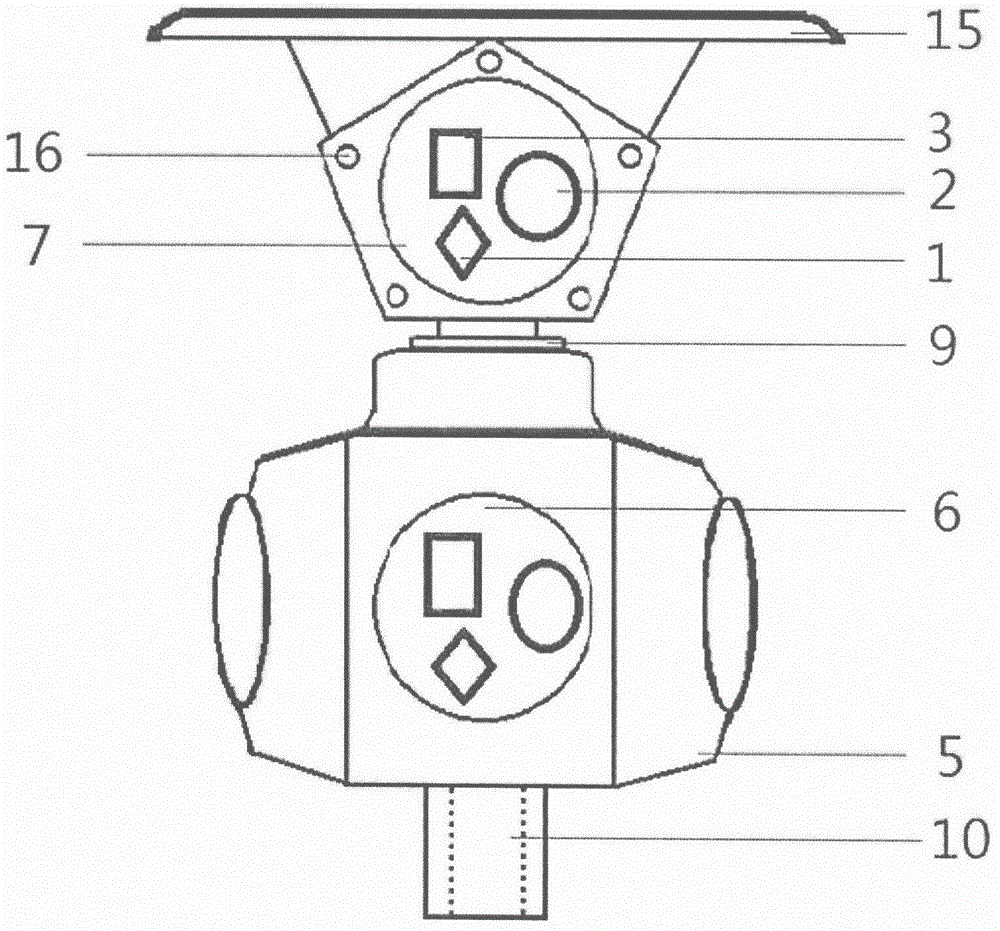
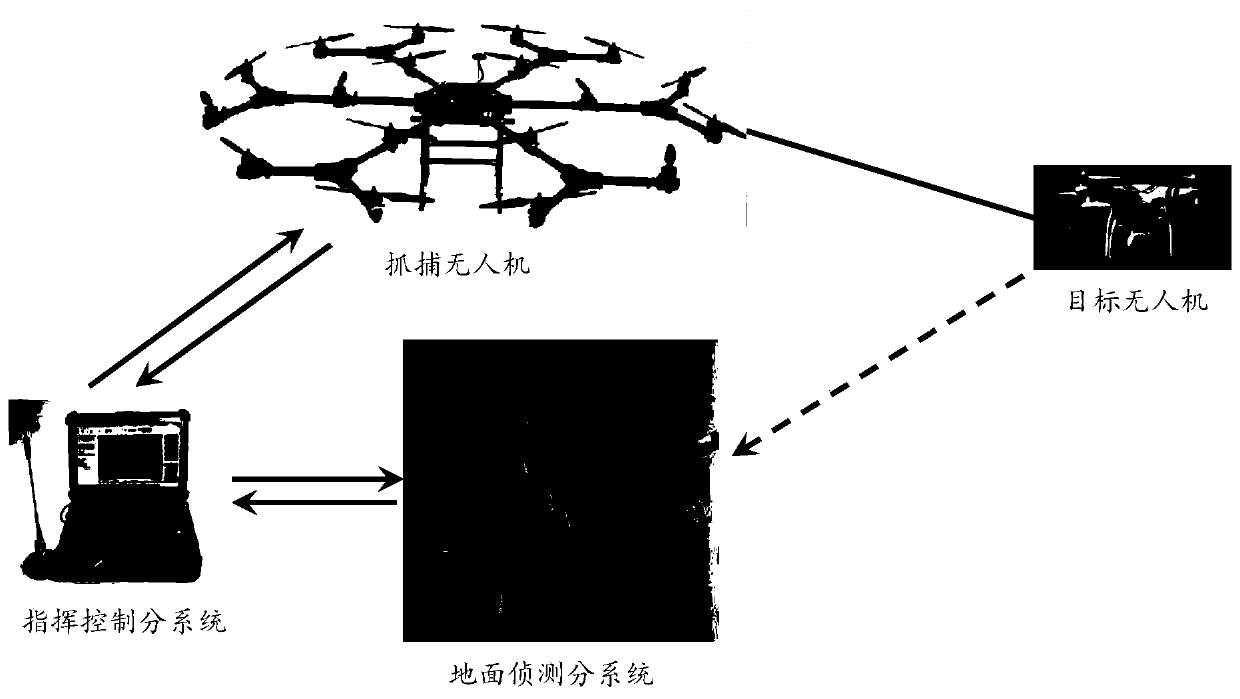
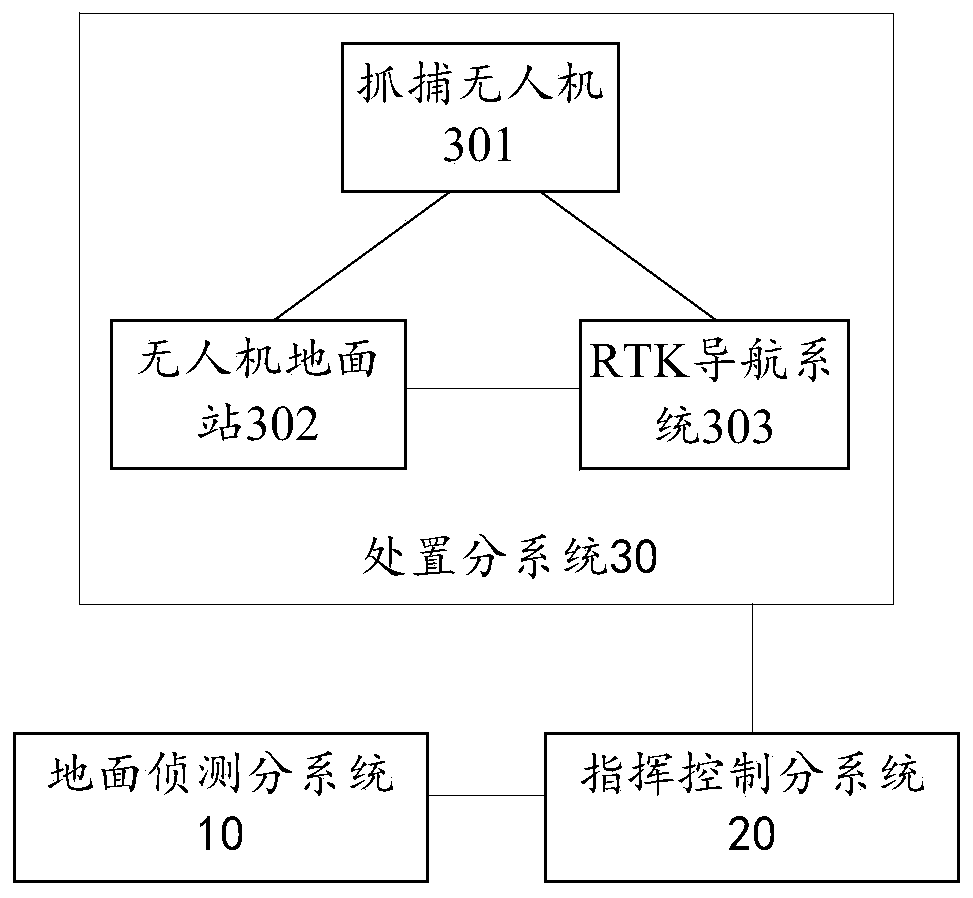
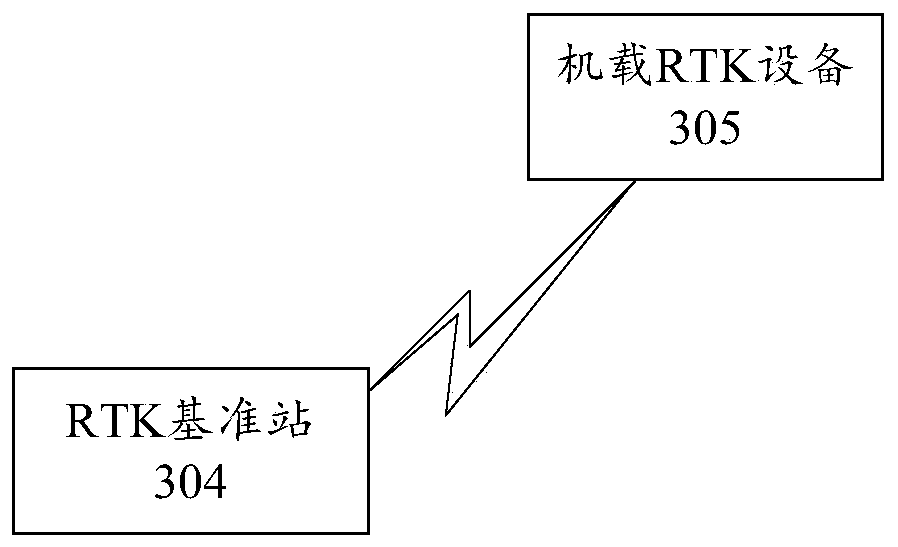
Defensive system and method of unmanned aerial vehicle
ActiveCN108100277AImprove defense efficiencyEasy to catchDefence devicesAircraft componentsCommand and controlUncrewed vehicle
The invention provides a defensive system and method of an unmanned aerial vehicle, and relates to the technical field of unmanned aerial vehicle countering. The defensive system of the unmanned aerial vehicle comprises a ground detection subsystem, a command and control subsystem and a disposition subsystem. The ground detection subsystem is used for detecting and tracking the target unmanned aerial vehicle and sending position information of the target unmanned aerial vehicle to the command and control subsystem; the command and control subsystem is used for receiving the position information and a capturing instruction input by a commander according to the position information and sending the capturing instruction to the disposition subsystem; the disposition subsystem comprises a capturing unmanned aerial vehicle, an unmanned aerial vehicle ground station and an RTK navigation system, and is used for receiving the position information and the capturing instruction, and the capturing unmanned aerial vehicle is guided to capture the target unmanned aerial vehicle through the RTK navigation system. With the defensive system and method of the unmanned aerial vehicle, high-precisionnavigation information can be obtained, the target unmanned aerial vehicle is convenient to capture, and the defensive efficiency of the unmanned aerial vehicle is improved.
Owner:北京华力创通科技股份有限公司 +1
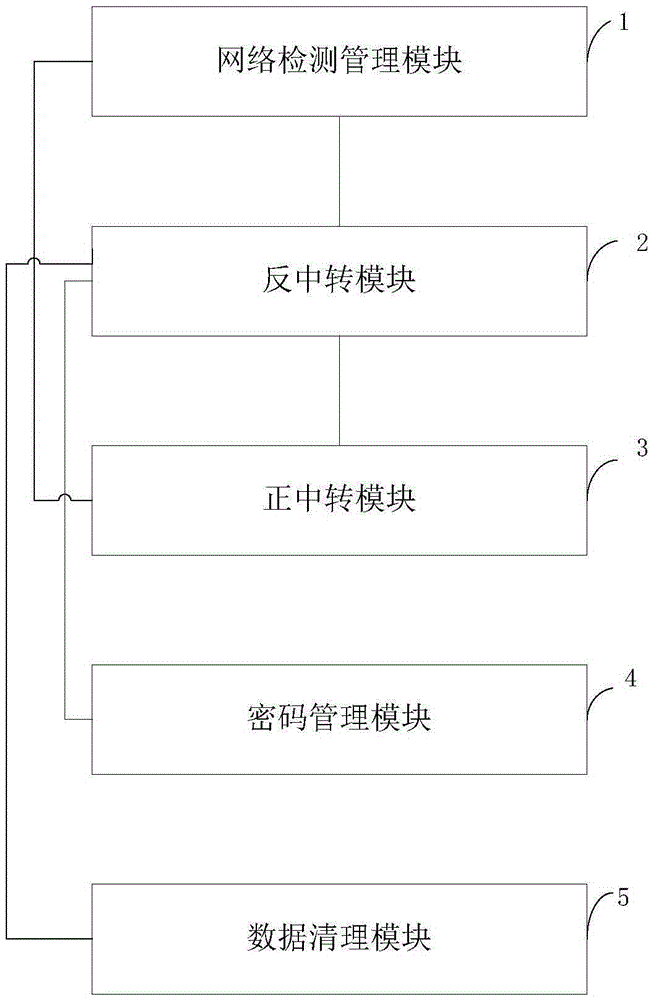
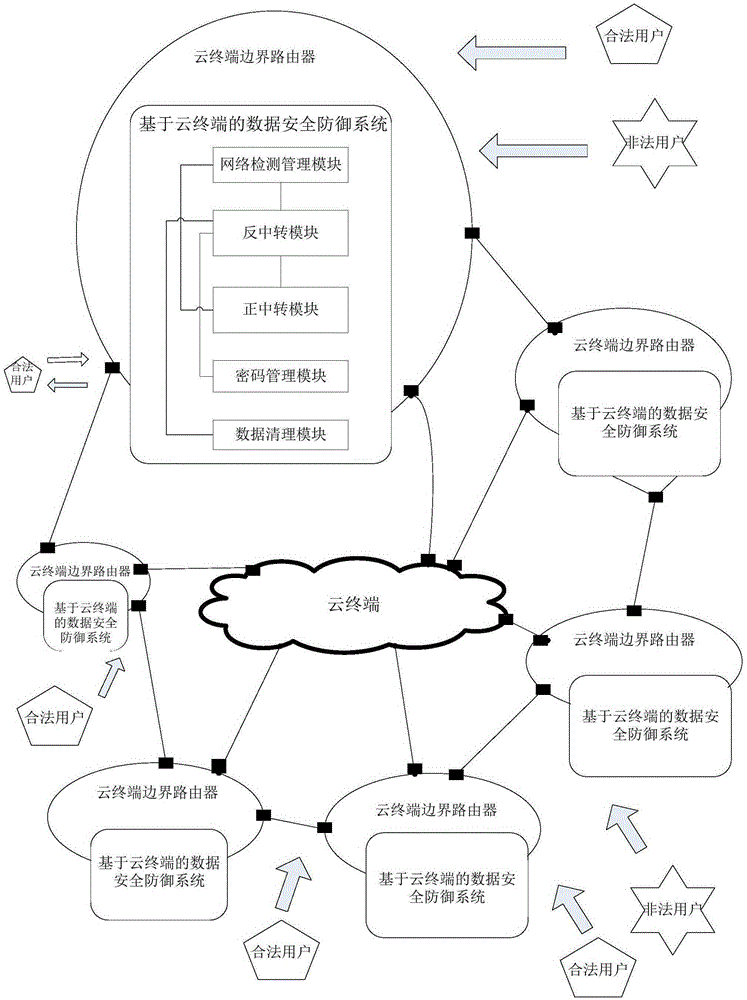
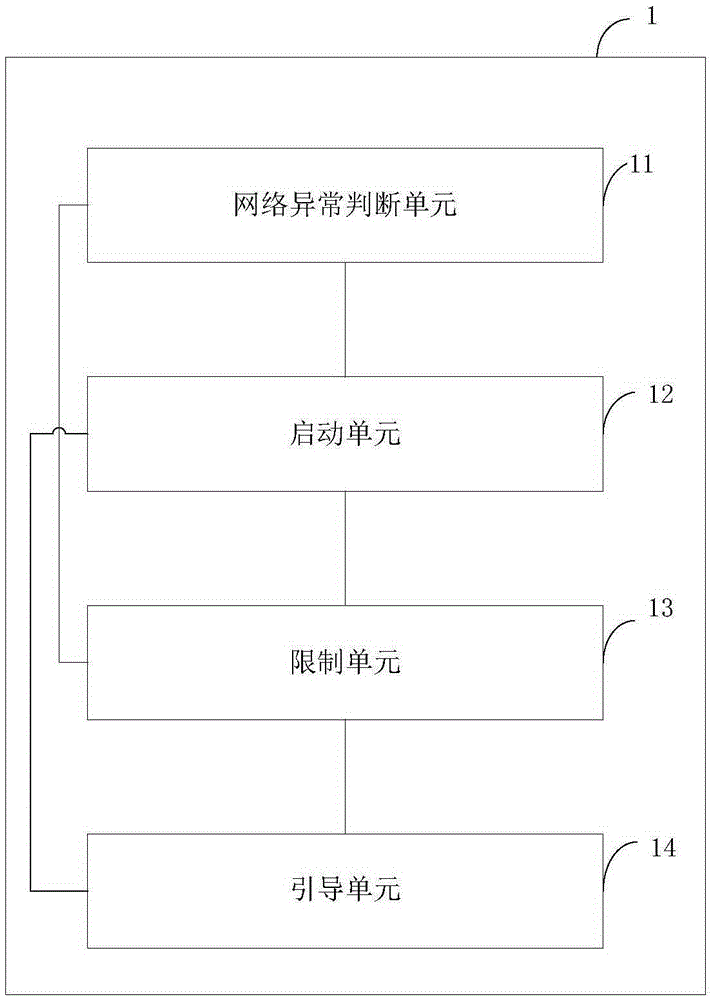
Data safety defense system and method based on cloud terminal, and cloud terminal safety system
ActiveCN105429975AReal-time monitoring of network statusAvoid attackTransmissionNetwork packetComputer module
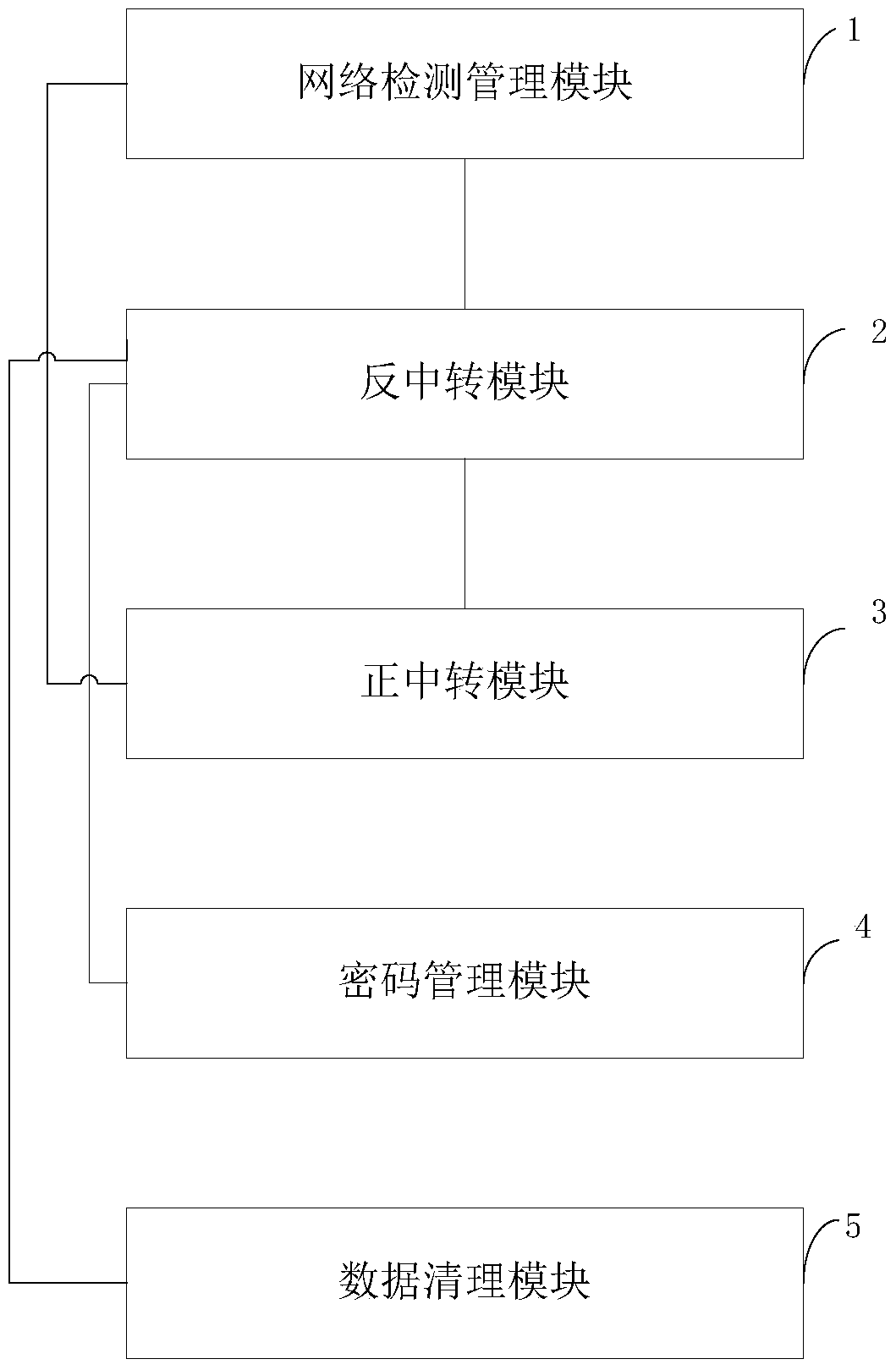
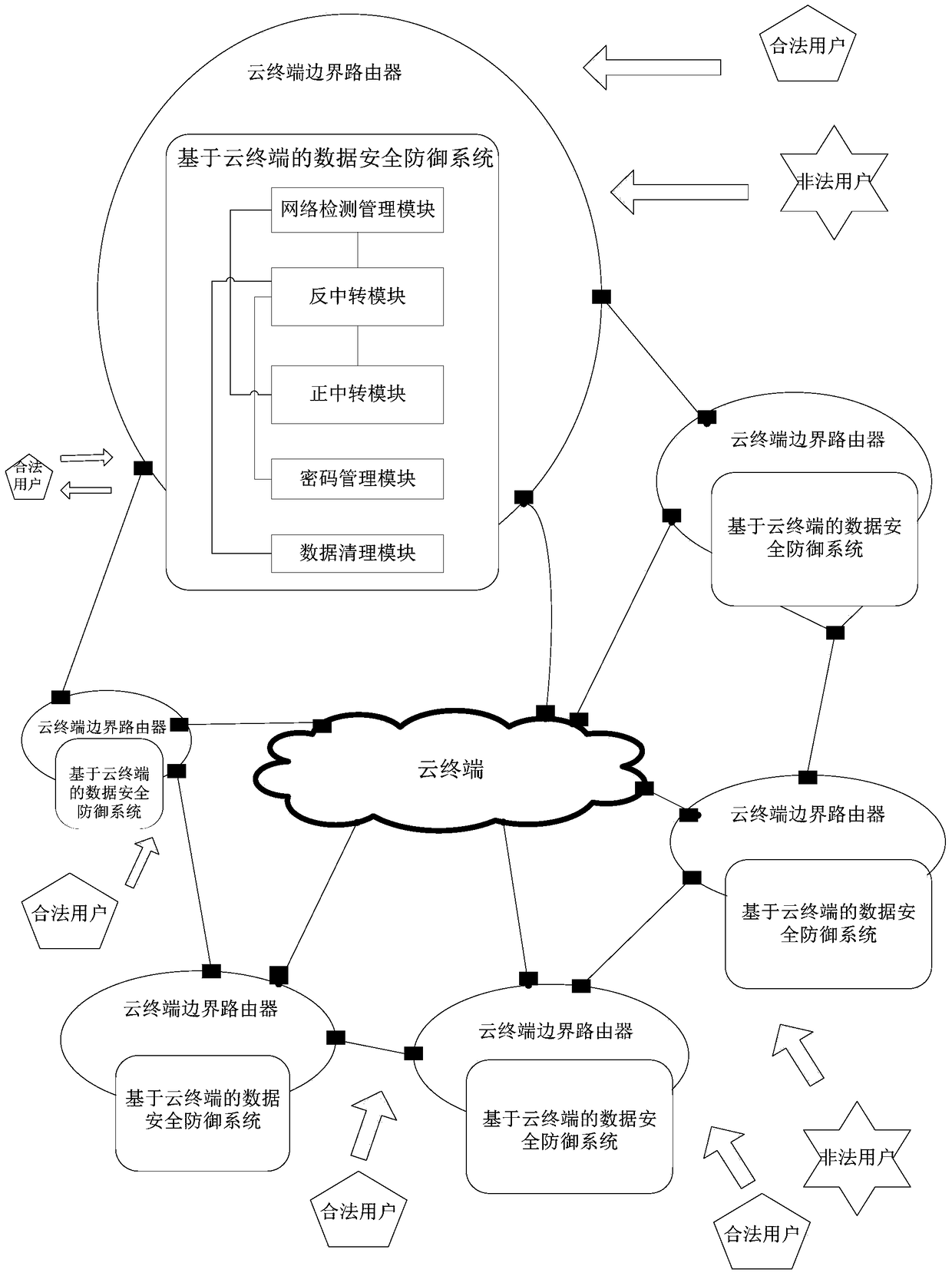
The present invention provides a data safety defense system and method based on a cloud terminal, and a cloud terminal safety system. The data safety defense system comprises a network monitoring management module which is used for monitoring the network condition of the cloud terminal, limiting the access of the cloud terminal, starting a negative-transfer module, and guiding a current access data packet to the negative-transfer module, the negative-transfer module which is used for intercepting the current access data packet, sending the legitimate access data packet in the intercepted current access data packet to a positive-transfer module, and the positive-transfer module which is used for receiving and storing the legitimate access data packet. Since the network condition of the cloud terminal is monitored in real time, when the cloud terminal is attacked, the access data packet is timely intercepted, the operation of a router is controlled, and the unlawful attack to the cloud terminal is effectively prevented.
Owner:SHANGHAI TAIYU INFORMATION TECH
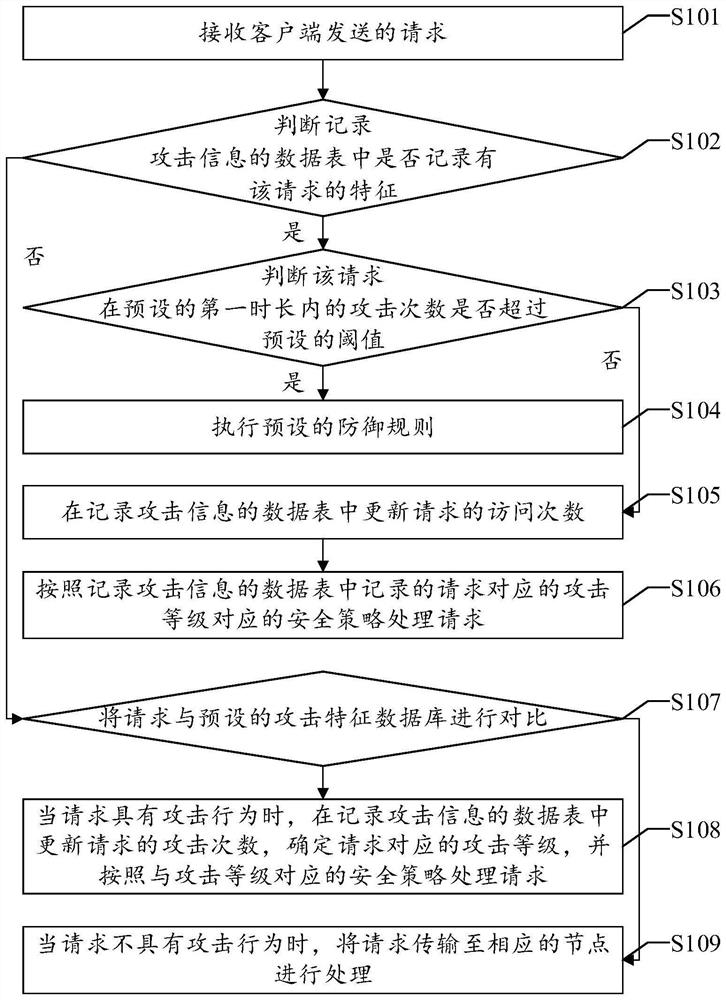
Web intelligent defense method, device and equipment, and readable storage medium
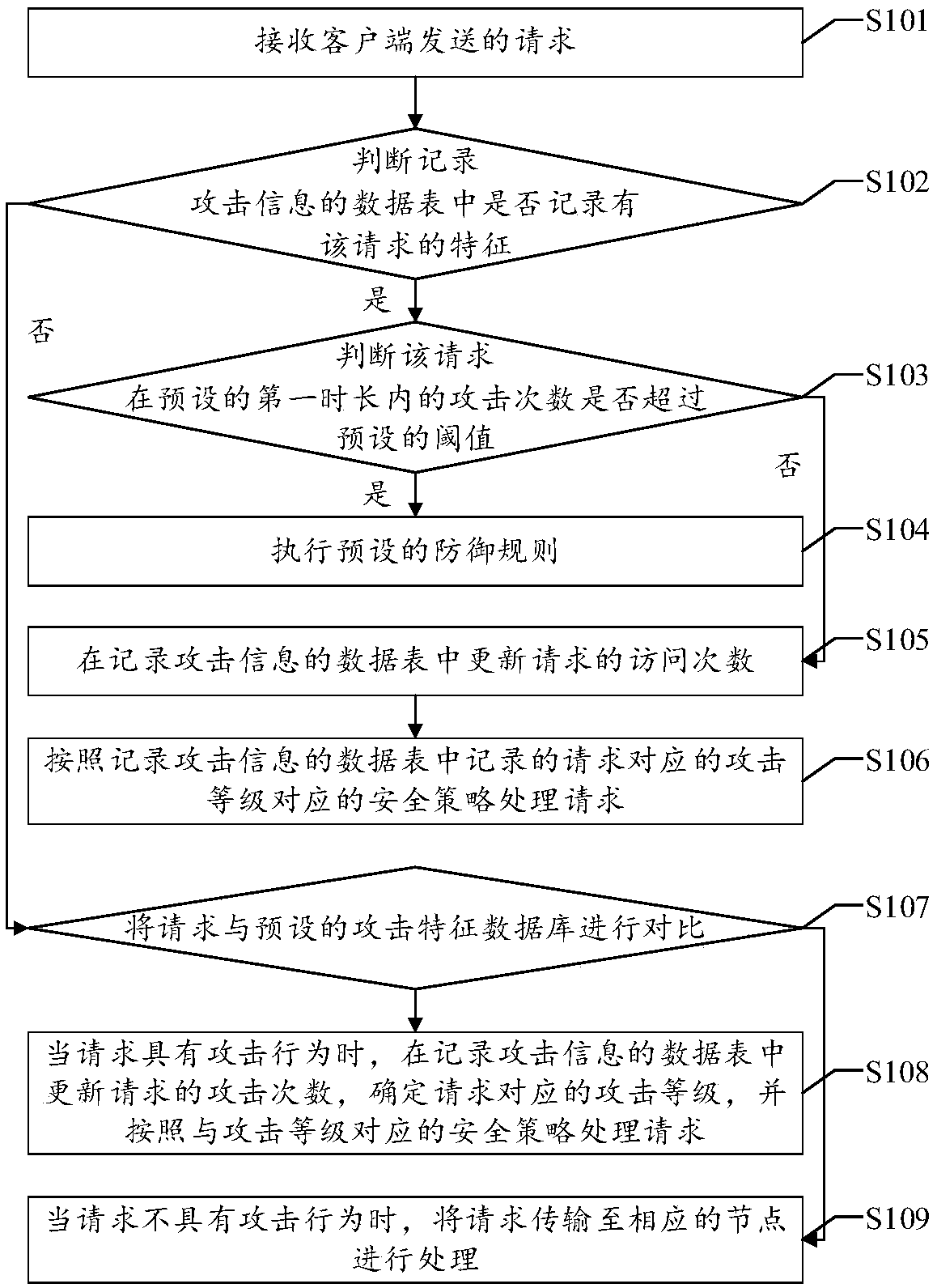
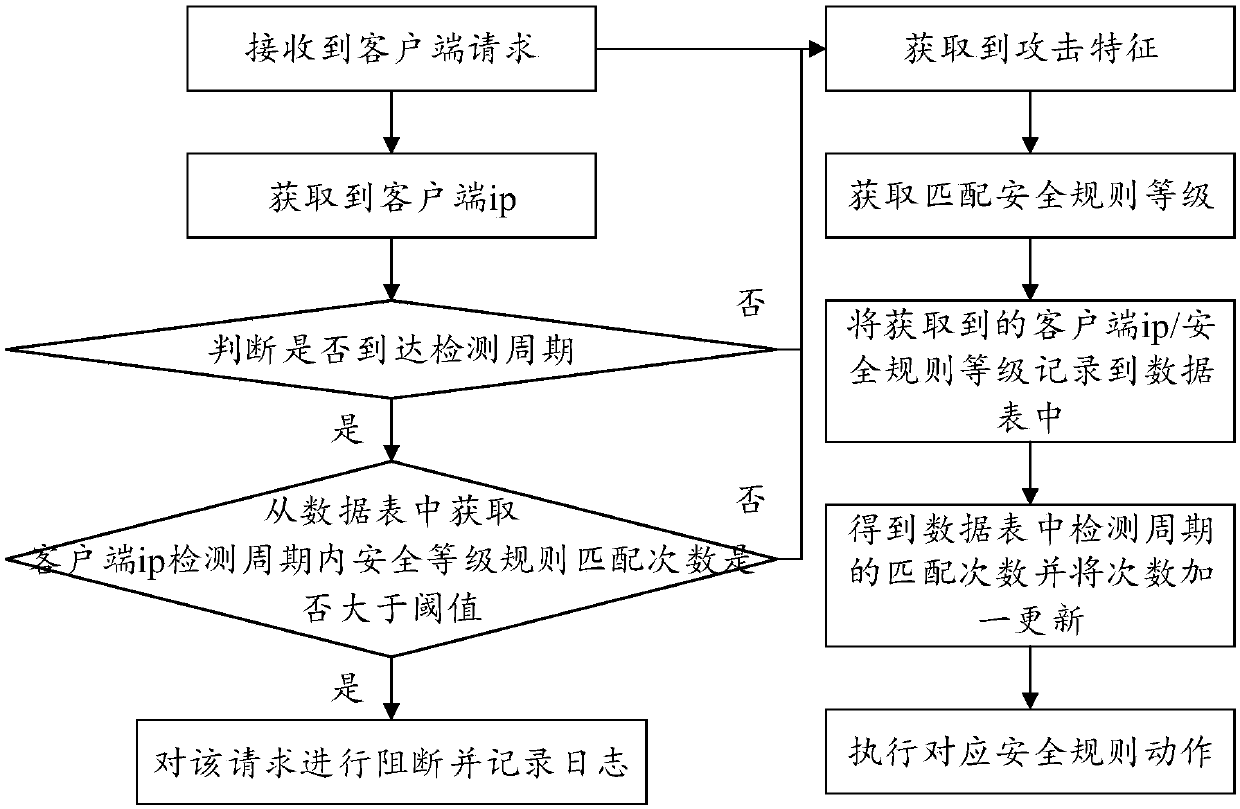
The invention discloses a web intelligent defense method, which comprises the steps of: determining whether features of a request are recorded in a data sheet in which attack information is recorded when receiving the request sent by a client; if so, determining whether a number of attacks of the request within preset first duration exceeds a preset threshold; and executing a preset defense rule when the number of attacks of the request within the preset first duration exceeds the preset threshold. The web intelligent defense method avoids the process of comparing each request with an attack feature library repeatedly, thereby reducing workload, improving the defense efficiency, and correspondingly improving the normal service quality in the network and the performance of the entire network. Correspondingly, a web intelligent defense device, web intelligent defense equipment and a readable storage medium disclosed by the invention further have the above technical effects.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
User demand-oriented security function service network system and implementation method thereof
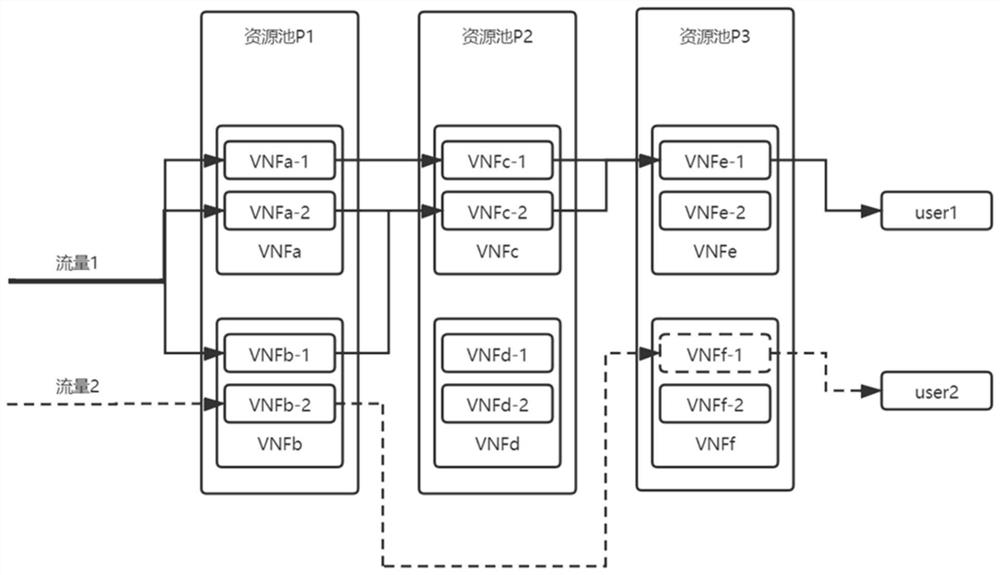
ActiveCN112822192AImprove defense efficiencyImprove securityNetworks interconnectionResource poolStatistical analysis
The invention discloses a user demand-oriented security function service network system and an implementation method thereof, and the method comprises the steps: carrying out the statistical analysis of resources in a cluster to obtain global information; establishing a plurality of virtual network function resource pools in a cloud environment, and processing a virtual network function Pod; selecting a corresponding virtual network function resource pool, and generating a security policy ordered set; selecting a virtual network function Pod in the corresponding virtual network function resource pool, and dynamically adjusting the security policy ordered set to generate a deployment policy; transmitting the deployment strategy to an SDN controller of the cloud environment; issuing a corresponding flow table by the SDN controller according to the security policy ordered set; and forwarding data flow from the outside of the cloud environment and among the nodes of the service function network according to the flow table. The security is improved, the network defense efficiency is improved, and the method can be widely applied to the technical field of network security.
Owner:SUN YAT SEN UNIV
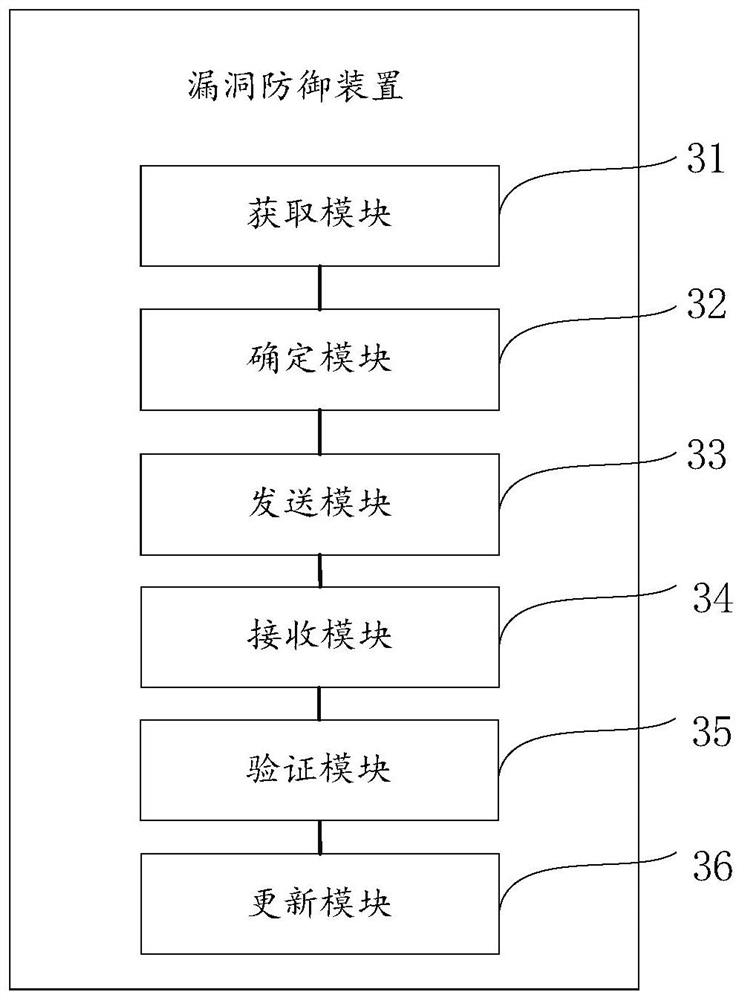
Vulnerability defense method and device
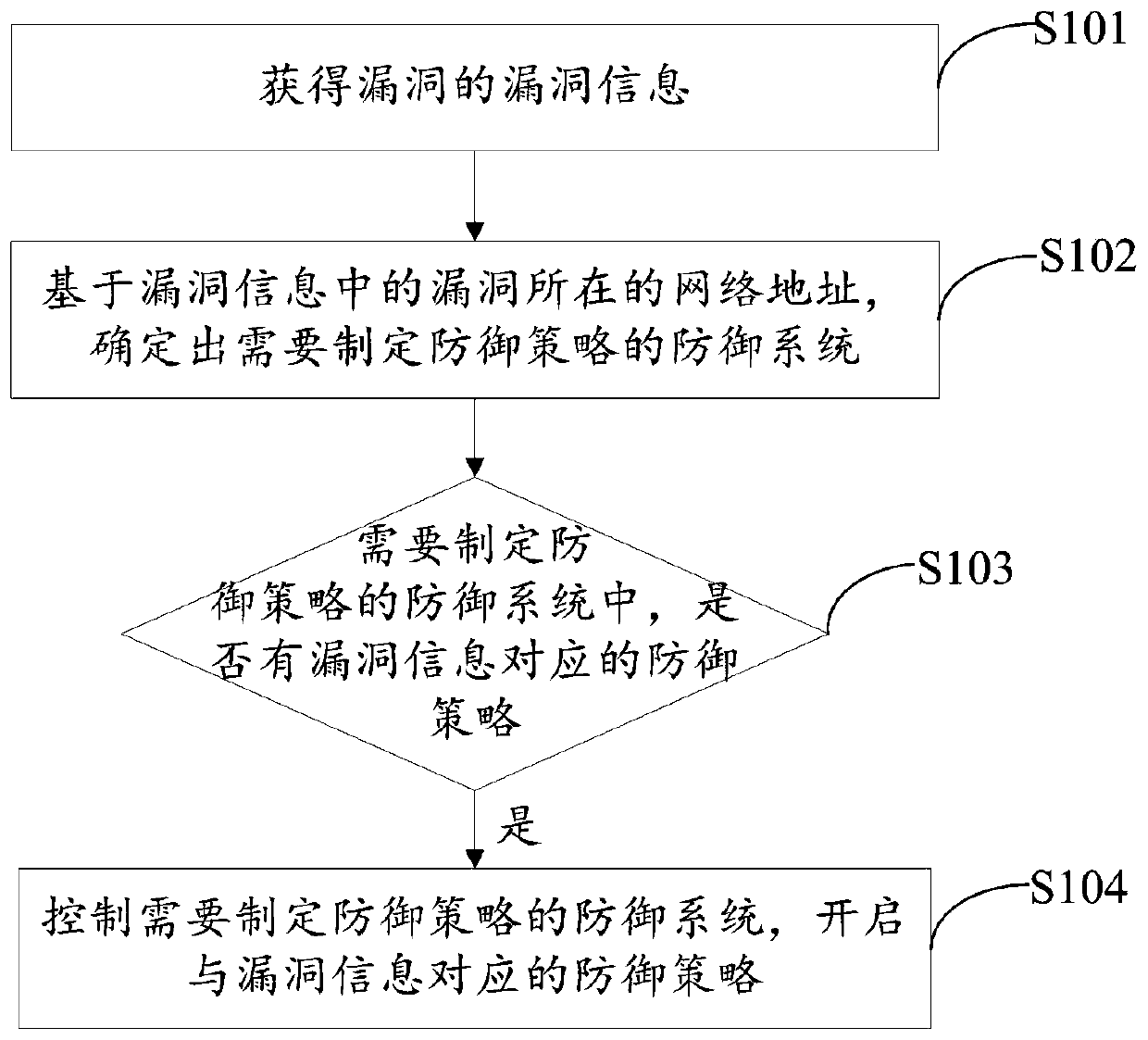
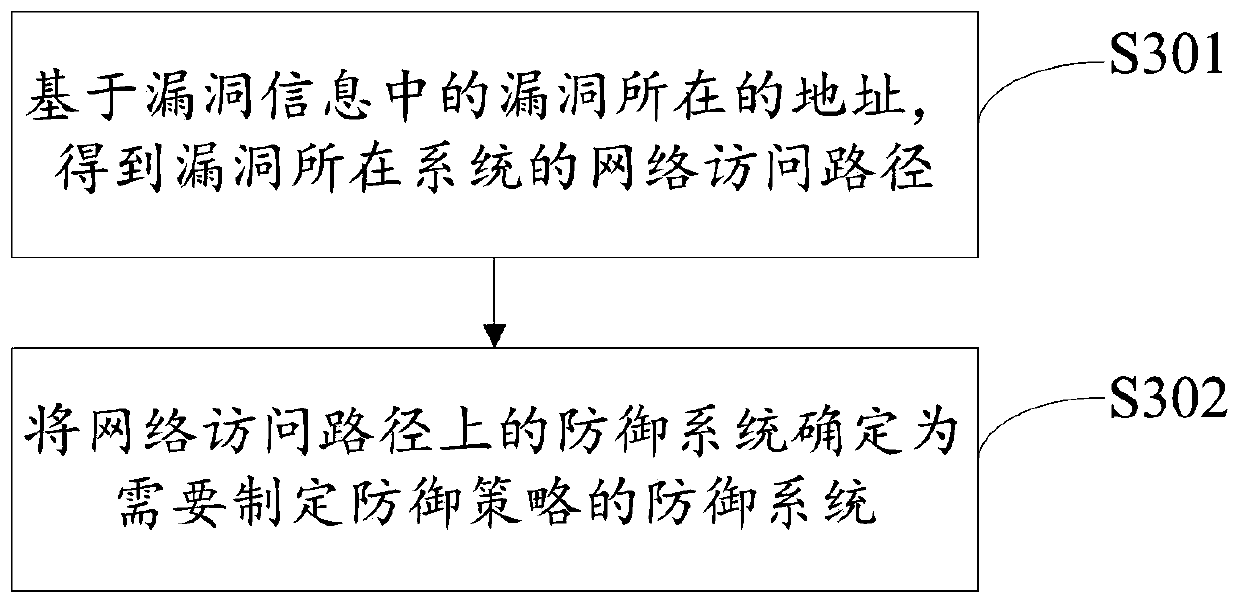
InactiveCN109818984AImprove defense efficiencyImprove securityTransmissionNetwork addressingNetwork address
The invention provides a vulnerability defense method and apparatus. The method comprises the steps of obtaining vulnerability information of a vulnerability; wherein the vulnerability information atleast comprises a network address where a vulnerability is located; based on the network address where the vulnerability in the vulnerability information is located, determining a defense system needing to formulate a defense strategy; Judging whether a defense strategy corresponding to the vulnerability information exists in the defense system needing to formulate the defense strategy or not; wherein the defense strategy is used for defending vulnerabilities; If it is judged that the defense strategy needs to be formulated in the defense system; a defense strategy corresponding to the vulnerability information exists; if yes, controlling a defense system needing to formulate a defense strategy; starting a defense strategy corresponding to the vulnerability information, Therefore, the scanning system and the defense system are accurately linked according to the vulnerabilities found in the enterprise, and when the obtained vulnerabilities are within the dangerous time, a defense strategy is executed on the vulnerabilities in time through the defense system, so that the system and information security is protected within the dangerous time, and the stable operation of the information system is ensured.
Owner:吉林亿联银行股份有限公司
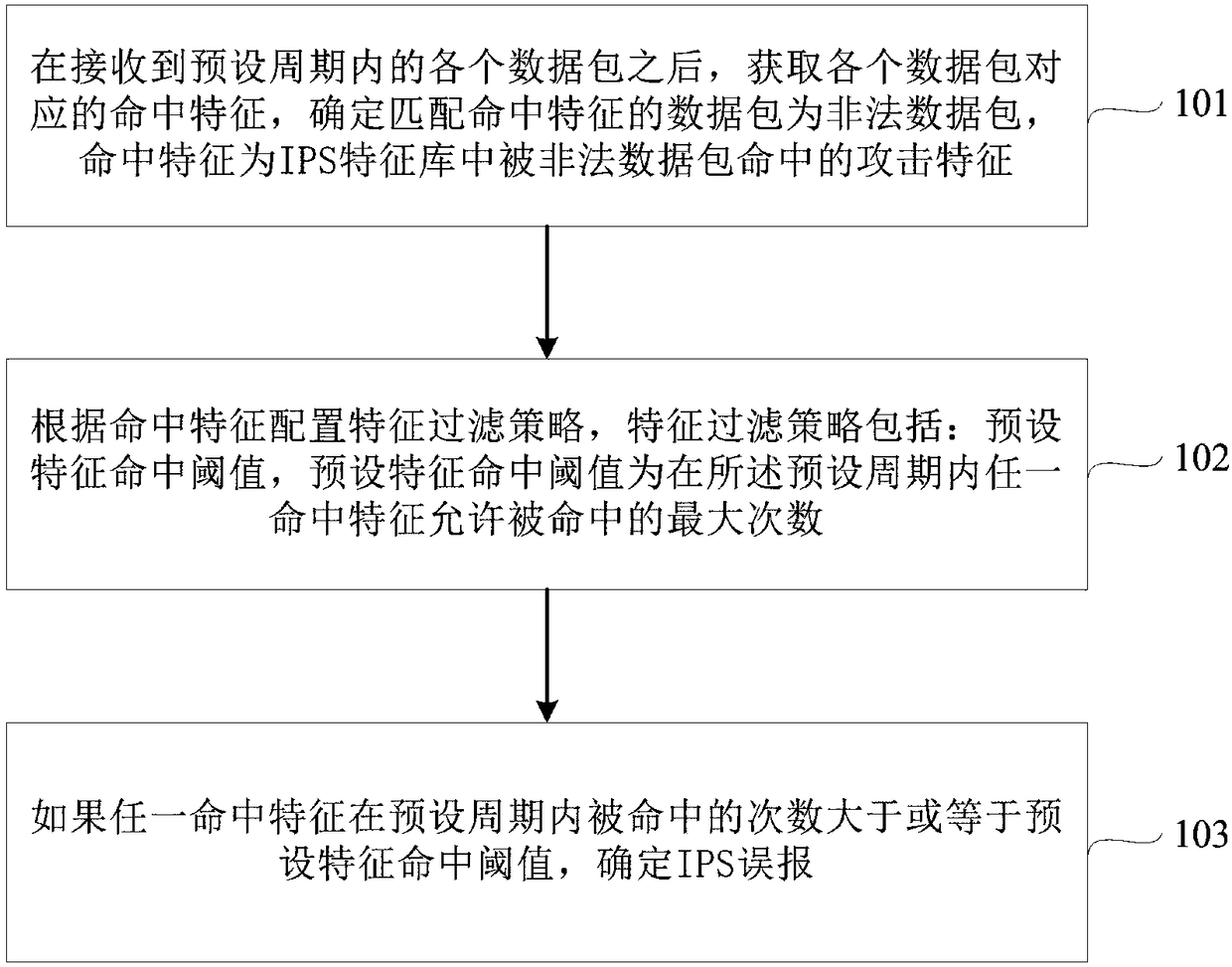
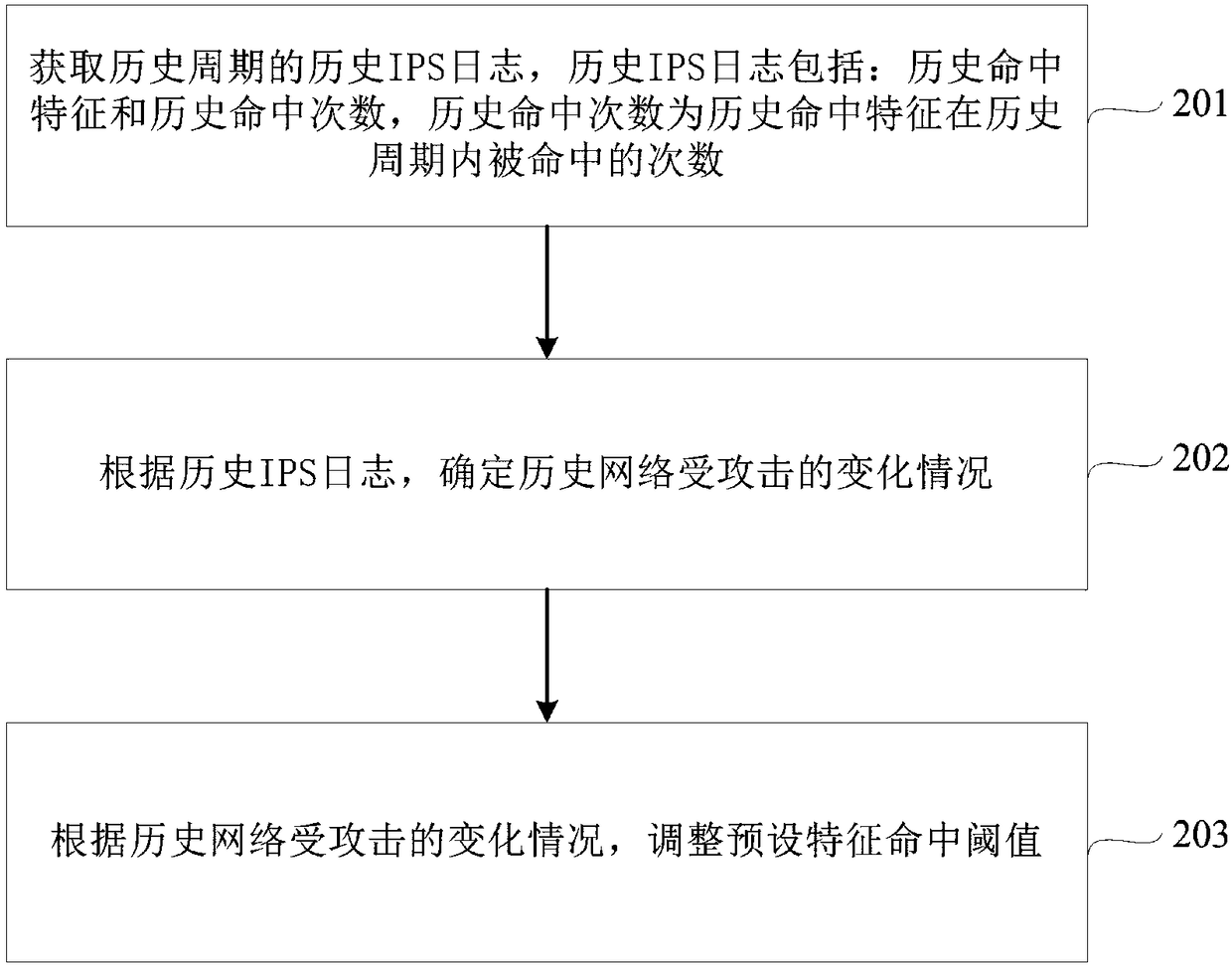
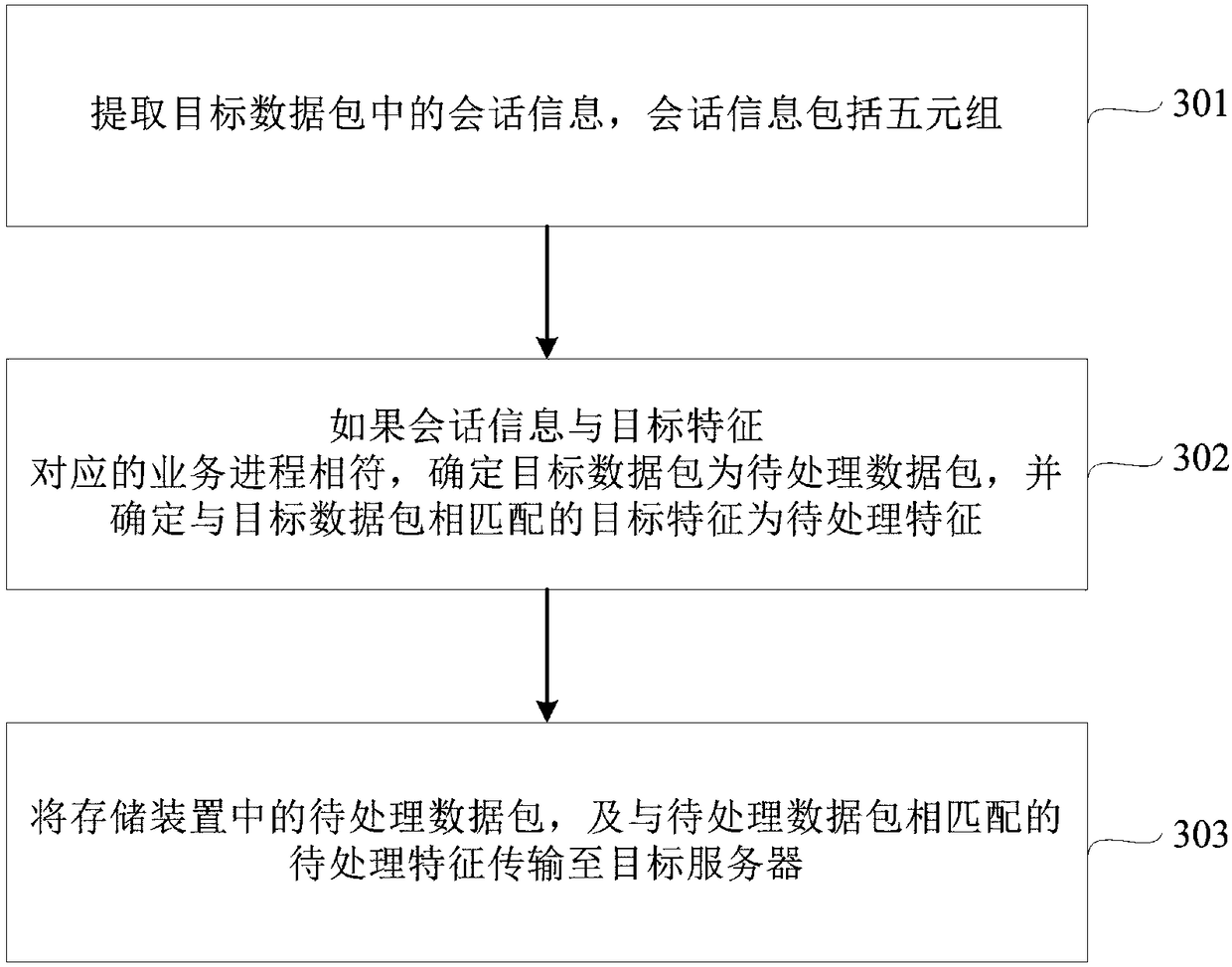
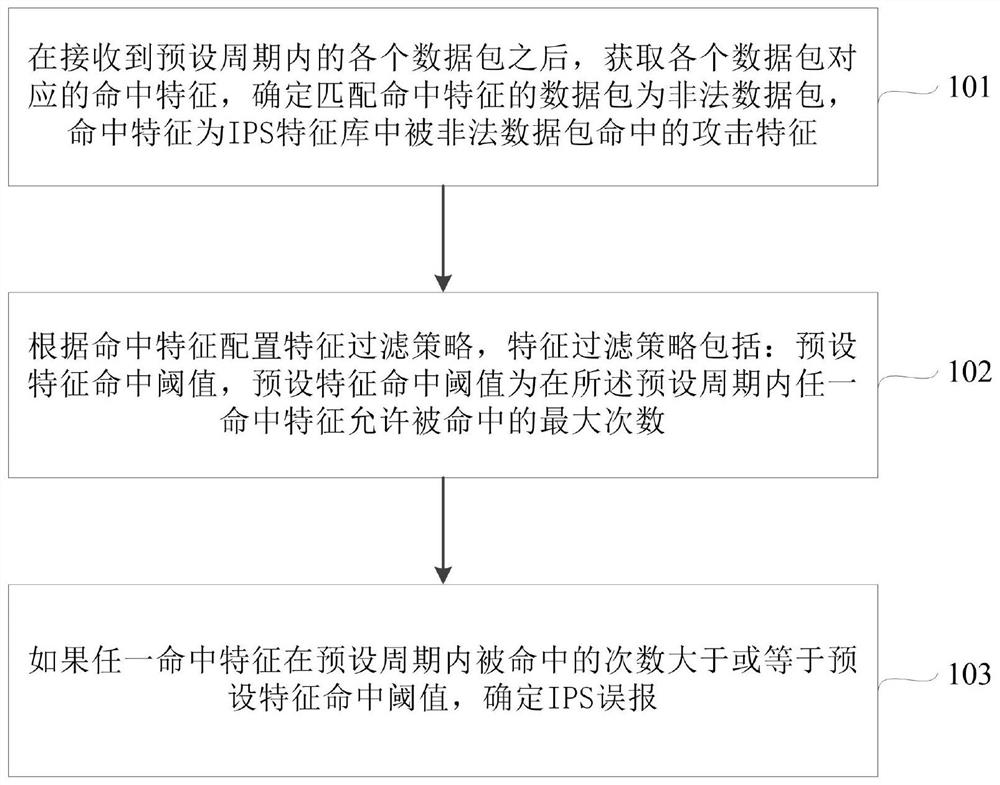
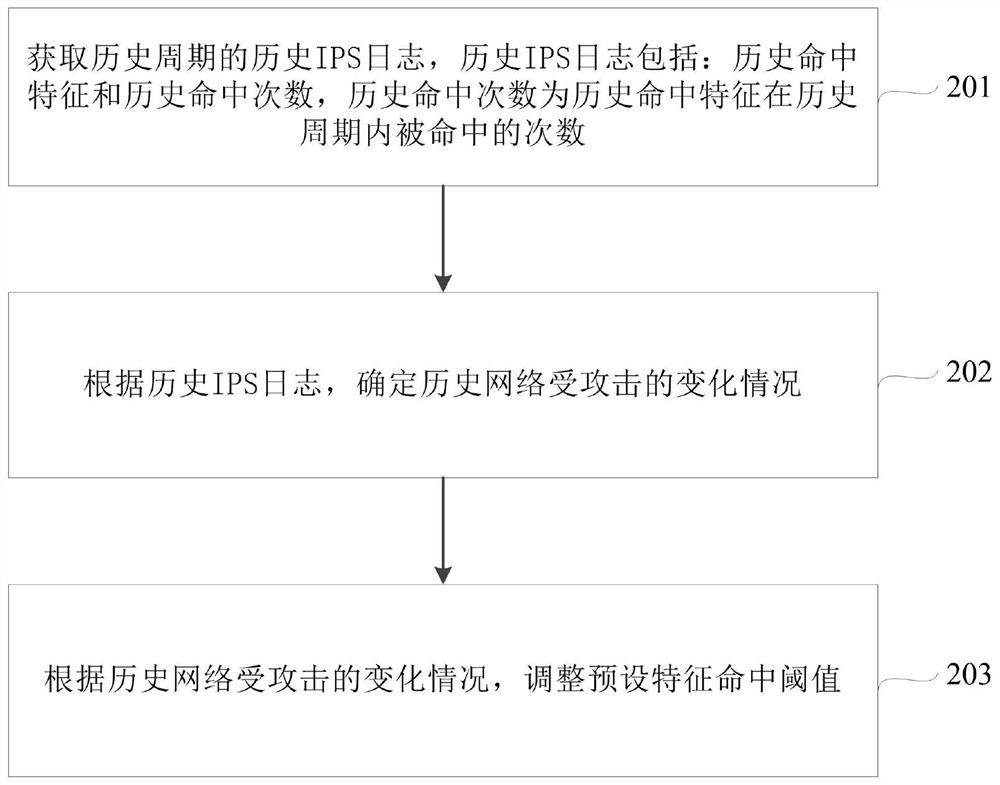
Intrusion prevention system (IPS) false positive detection method and device
ActiveCN109413021AImprove defense efficiencyFilter in timeTransmissionIntrusion prevention systemAttack signature
Embodiments of the invention disclose an intrusion prevention system (IPS) false positive detection method and device. The method comprises steps of after all data packets in a preset period are received, acquiring a hit characteristic corresponding to each data packet, and determining the data packet matched with the hit characteristic as an illegal data packet, wherein the hit characteristic isan attack characteristic hit by the illegal data packet in an IPS characteristic bank; configuring a characteristic filter policy according to the hit characteristic, wherein the characteristic filterpolicy comprises a preset characteristic hit threshold, and the preset characteristic hit threshold represents a maximum that any hit characteristic is allowed to hit in the preset period; and if thehit times of any hit characteristic in the preset period is greater than or equal to the preset characteristic hit threshold, determining IPS false positive. Through adoption of the method and device, IPS false positive can be detected timely, impact of IPS false positive on normal network businesses is reduced, and IPS prevention efficiency is improved.
Owner:武汉思普崚技术有限公司
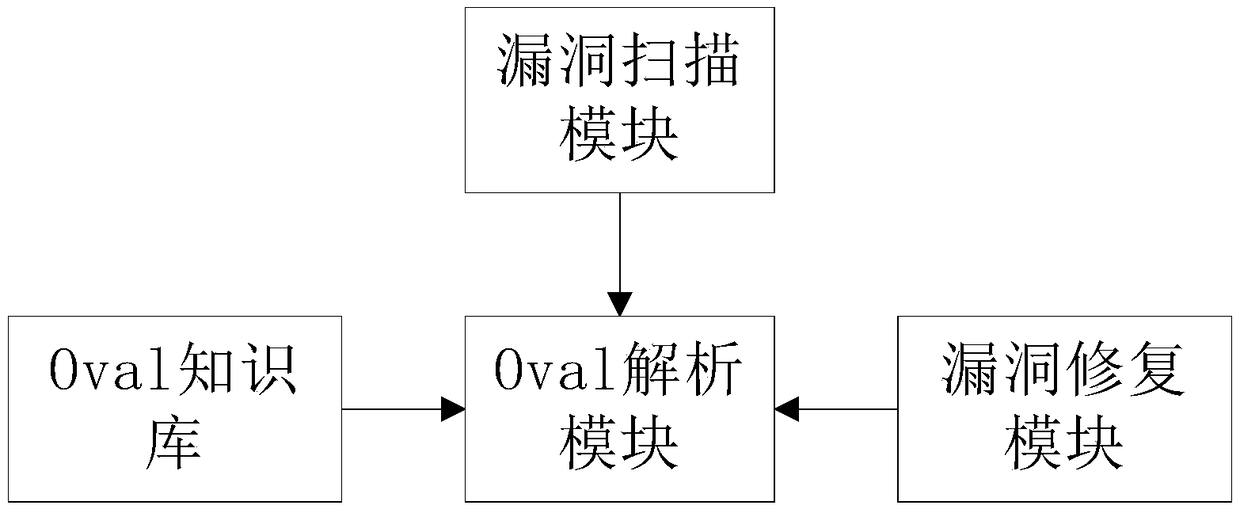
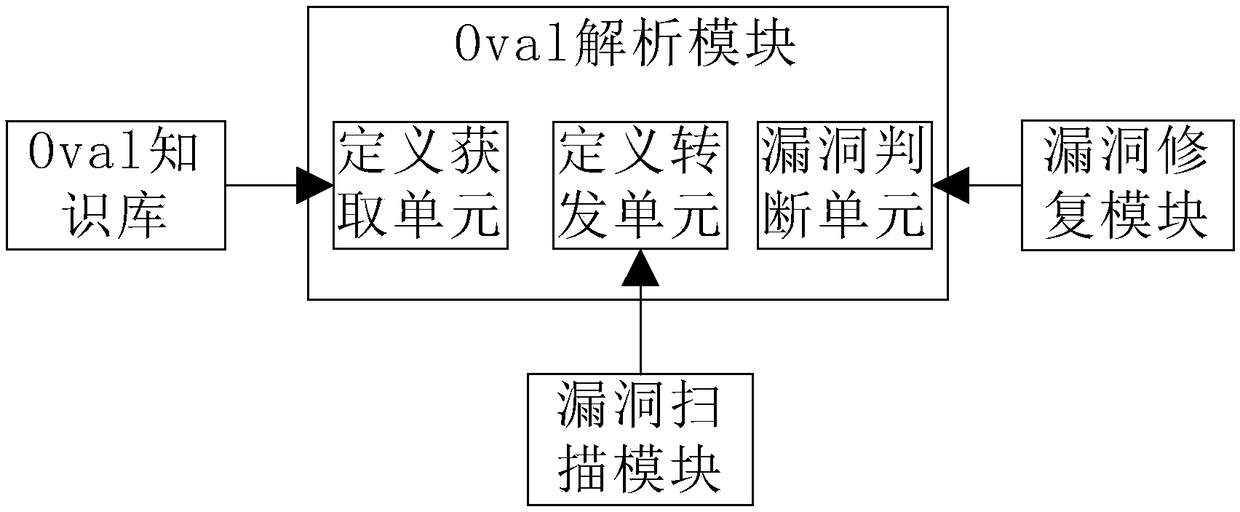
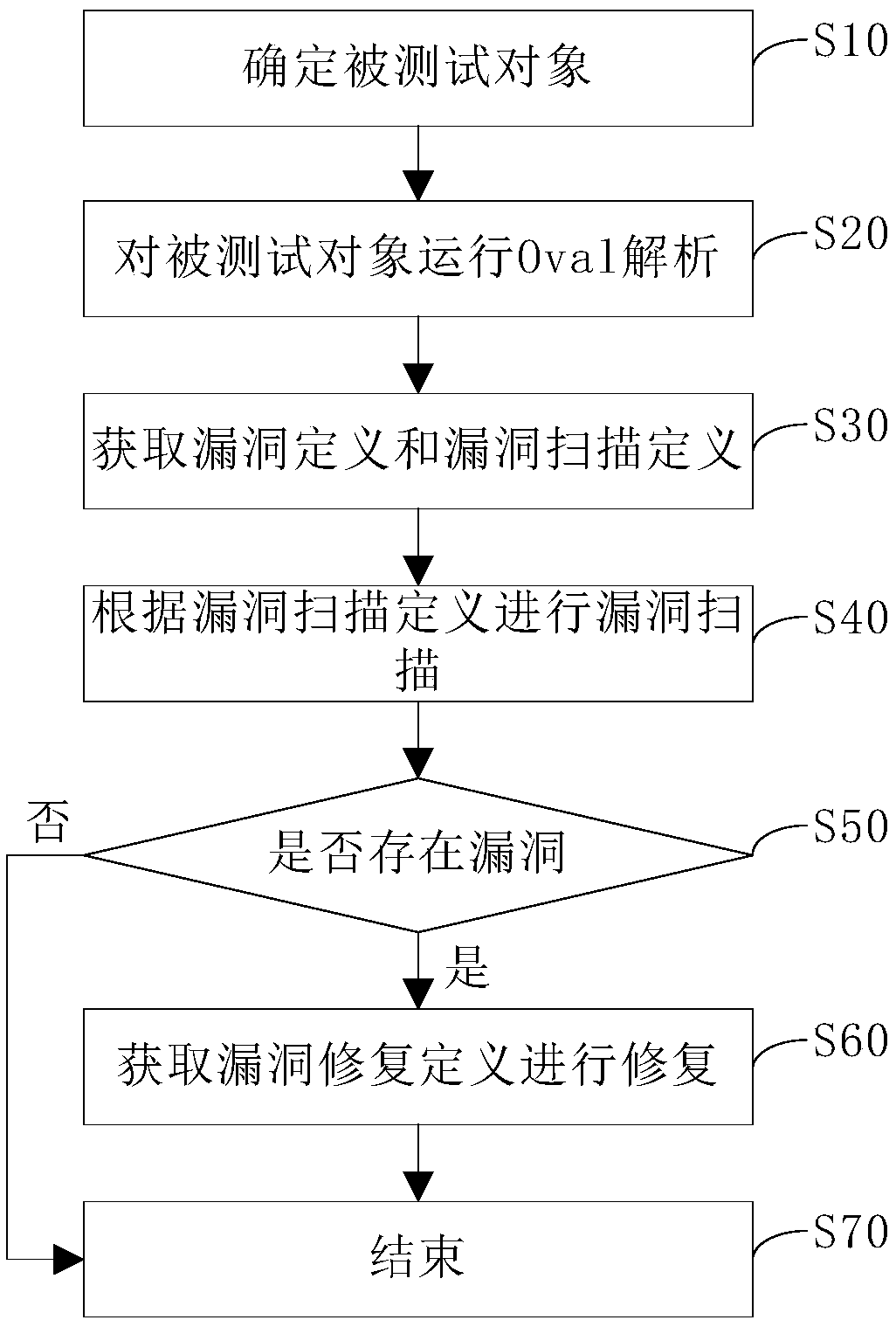
A vulnerability scanning repair system and method based on Oval
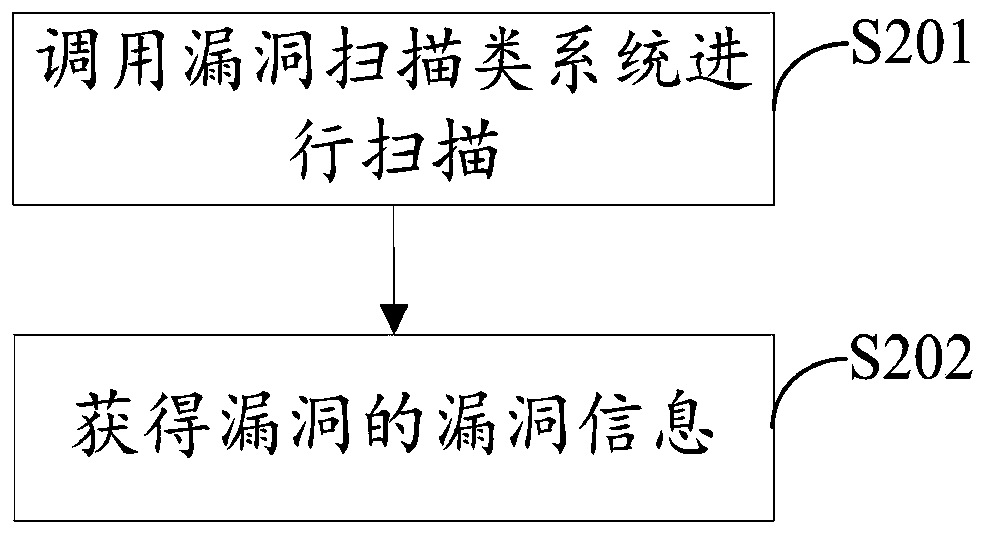
InactiveCN109002720AImprove defense efficiencyPlatform integrity maintainanceTest objectVulnerability scanning
The embodiment of the invention discloses a vulnerability scanning and repairing system and method based on Oval, and the system includes an Oval knowledge base, an Oval parsing module, a vulnerability scanning module, and a vulnerability repairing module. The Oval knowledge base, the vulnerability scanning module and the vulnerability repairing module are connected to the a vulnerability parsingmodule, wherein, the Oval knowledge base is used for storing vulnerability definition, vulnerability scanning definition and vulnerability repairing definition; the vulnerability scanning module is used to scan the vulnerability of the tested object. The vulnerability repair module is used to repair the scanned vulnerabilities. The vulnerability parsing module is used to send vulnerability definitions and vulnerability scanning definitions to the vulnerability scanning module and to send vulnerability repair definitions to the vulnerability repair module according to the vulnerability. The invention can pre-repair the leak in an active state before the leak occurs, and the leak prevention efficiency is improved.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
A method for analyzing network attacker behavior based on attack graph
The invention discloses a network attacker behavior analyzing method based on an attack graph. The method comprises the steps of establishing a network attacker behavior analyzing model and attracting attacks of attackers; carrying out comprehensive capturing on attack data through a data capturing mechanism; and generating an attack state transfer graph through combination of a finite-state machine and analyzing behaviors of the attackers according to possibility indexes of attack behaviors, skill level indexes of the attackers and destination indexes of the attackers. According to the network attacker behavior analyzing method based on the attack graph provided by the invention, the good foundation can be laid for design of an active defense system, the network attacks can be defended, the attacks can be prevented before the network attacks occur, one part of the attacks are screened, a cybercrime can be effectively prevented, the defense efficiency is improved, and the defense cost is reduced.
Owner:HANGZHOU SUNYARD DIGITAL SCI
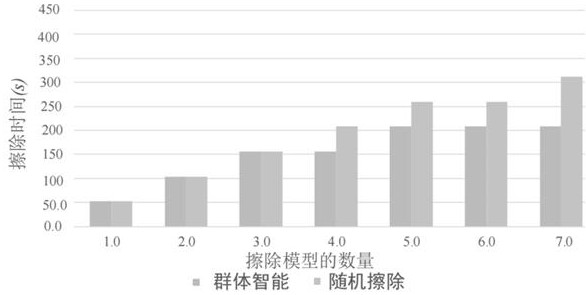
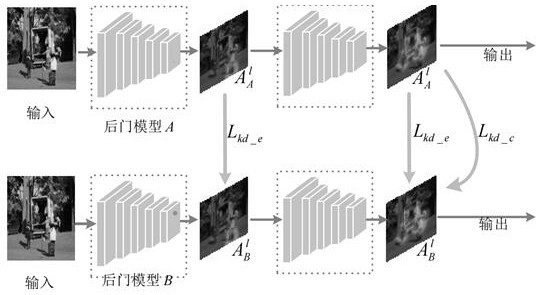
Image recognition back door defense method and device based on swarm intelligence, and medium
PendingCN114048474AImprove defense efficiencyNormal image recognition taskPlatform integrity maintainanceNeural architecturesAlgorithmEngineering
The invention discloses an image recognition backdoor defense method and device based on swarm intelligence, and a medium. The method comprises the following steps: selecting neural network models with dense connection as seed neural network models based on the incidence relation of a plurality of neural network image recognition models in a distributed cluster and according to the ranking of connection density; aiming at every two seed neural network models, performing distillation operation on the two seed neural network models by utilizing attention distillation representation, and extracting an attention activation graph Al which is invalid to the back door attack of the seed neural network models; and measuring the Euclidean distance and the cosine distance of activation attention maps Al of the two seed neural network models by designing a robust distillation loss function L, allowing the seed neural network models to calculate gradient values based on the L and to carry out back propagation, and updating the parameters of the seed neural network models. The performance and efficiency of an image recognition back door defense algorithm based on swarm intelligent under the image recognition back door defense task reach a current optimal level.
Owner:CENT SOUTH UNIV
Laser communication suppression and friend or foe identification comprehensive system for military vehicles
InactiveCN106679508AAvoid omissionsStrengthen offensive forceArmoured vehiclesCommunication jammingStandby powerEngineering
The invention discloses a laser communication suppression and friend or foe identification comprehensive system for military vehicles. The laser communication suppression and friend or foe identification comprehensive system for the military vehicles comprises a laser communication module, a laser detection suppression disturbing module, a laser friend or foe identification module, a reserve power supply set, a main equipment bin, a fixed laser lens set, a circular-viewing laser lens, a platform, a rotary disc, a lifting sleeve, an external equipment bin, a mechanical lifting handle, a fixing seat, an uncovered protective box, a protective top cap and bolts. The laser communication suppression and friend or foe identification comprehensive system for the military vehicles is characterized in that the laser communication module, the laser detection suppression disturbing module and the laser friend or foe identification module are integrated in the main equipment bin. The laser communication suppression and friend or foe identification comprehensive system for the military vehicles has the beneficial effects that a plurality sets of active-passive attack-defense modules are arranged on the top ends of the military vehicles, wherein each active-passive attack-defense module combines the laser communication module, the laser detection suppression disturbing module and the laser friend or foe identification module into a whole, so that the military vehicles utilize the advantages of high measuring precision, quick conveying, high security and quick energy collecting weaponization of lasers in the battles, the survival rate of the military vehicles in the battlefields is increased.
Owner:NANJING LINGYA AUTOMOBILE TECH RES INST
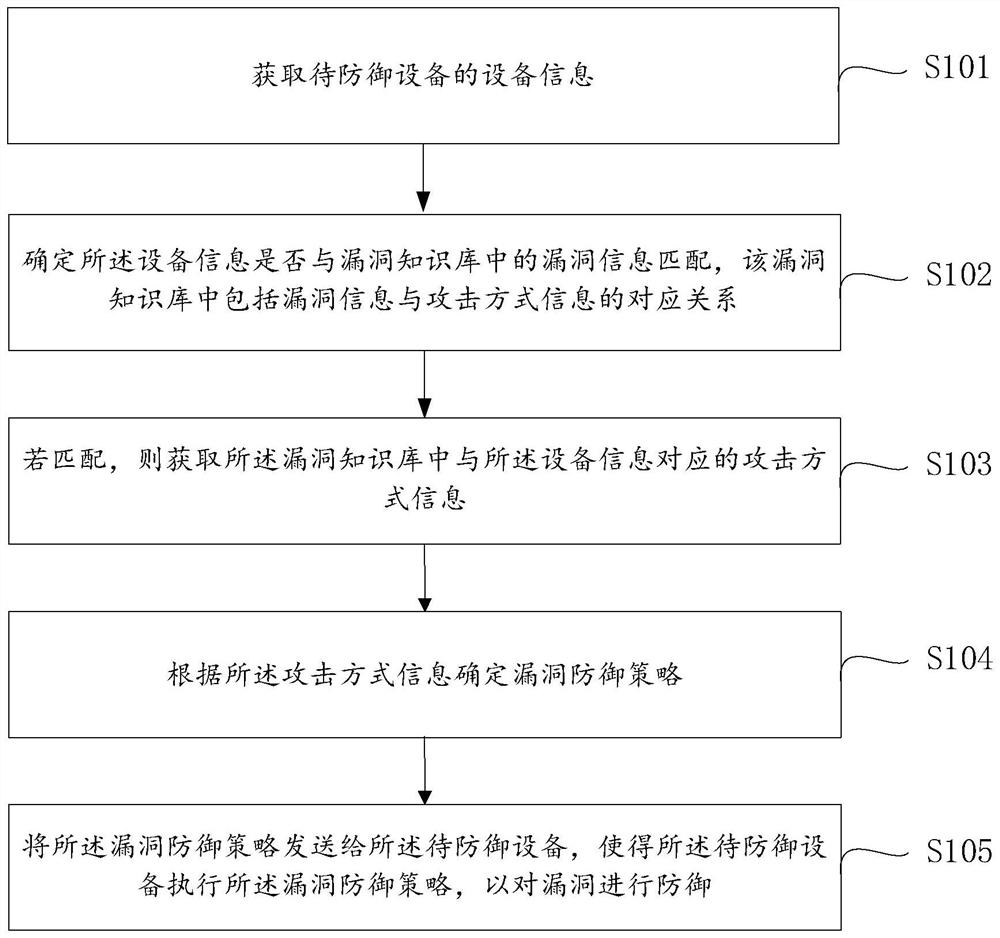
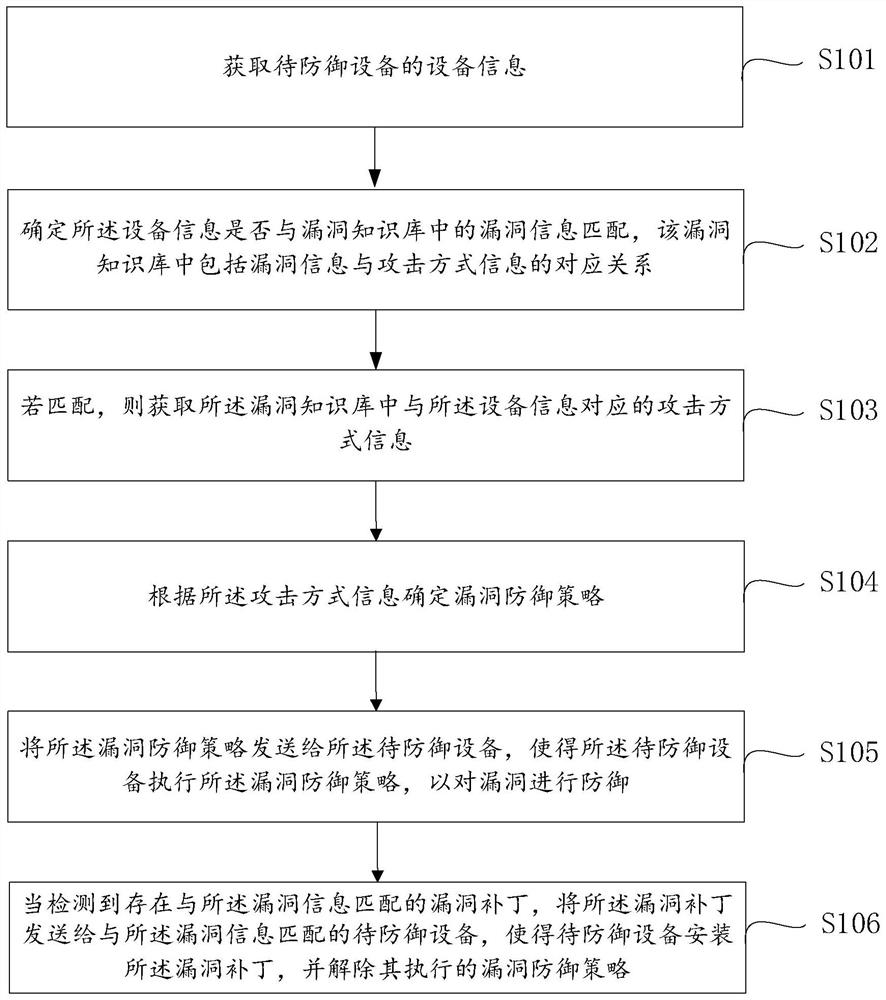
Vulnerability defense method and device and computer equipment
PendingCN114282225AImprove defense efficiencyImprove securityPlatform integrity maintainanceAttackReliability engineering
The invention provides a vulnerability defense method and device and computer equipment, relates to the technical field of network security, and is used for improving the vulnerability defense efficiency. The method mainly comprises the following steps: acquiring equipment information of to-be-defended equipment; determining whether the equipment information is matched with vulnerability information in a vulnerability knowledge base, wherein the vulnerability knowledge base comprises a corresponding relationship between the vulnerability information and attack mode information; if yes, acquiring attack mode information corresponding to the equipment information in the vulnerability knowledge base; determining a vulnerability defense strategy according to the attack mode information; and sending the vulnerability defense strategy to the to-be-defended device, so that the to-be-defended device executes the vulnerability defense strategy to defend vulnerabilities.
Owner:BEIJING ANTIY NETWORK SAFETY TECH CO LTD
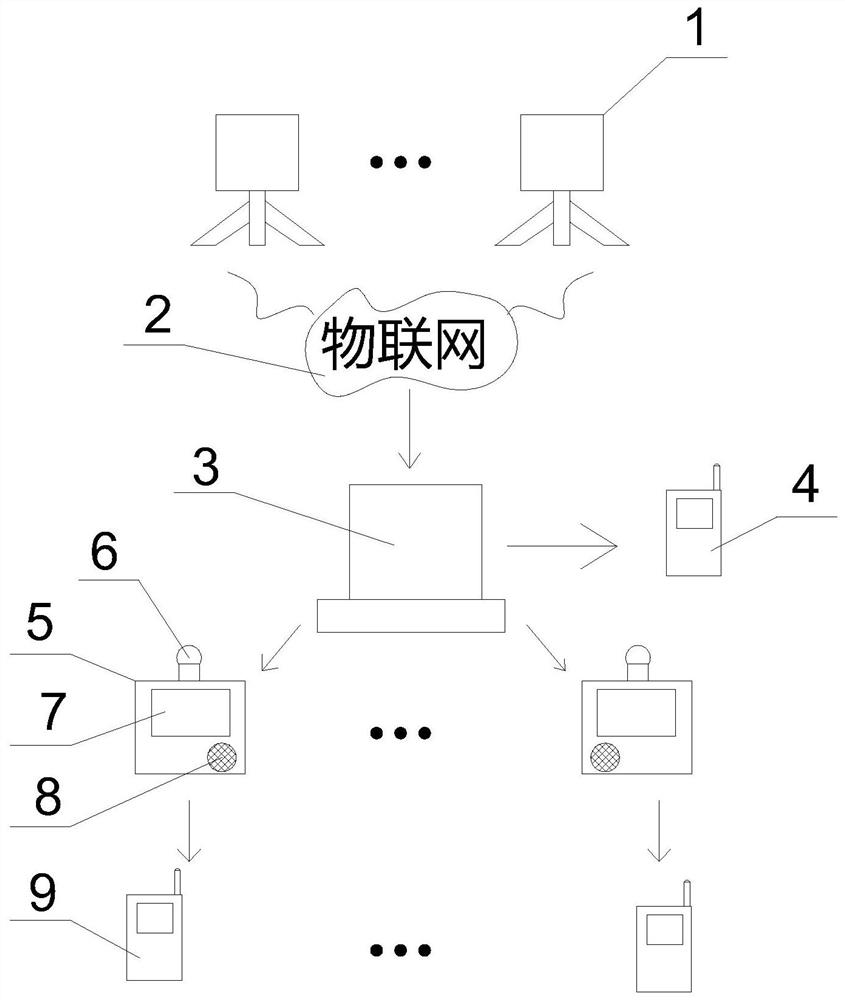
Weather forecast and early warning service system
InactiveCN112068223AAchieve defenseImprove protectionWeather condition predictionElectric transmission signalling systemsMonitoring siteThe Internet
The invention relates to the field of climate monitoring and early warning, in particular to a weather forecast and early warning service system, which comprises a weather monitoring point, an internet of things, a weather monitoring center and a forecast and early warning service point, wherein the weather monitoring point is connected with the weather monitoring center through the internet of things. The weather monitoring center is connected with a mobile device I and the forecast and early warning service point through the communication network. The system effectively solves the problems that the emergency processing efficiency is low and the life and property loss is increased due to the fact that the natural disaster forecasting and early warning service for sudden and turning weather changes is not in time, can effectively prevent and early warn, improves the emergency processing efficiency, and is high in practicability. Life and property loss caused by the situation is avoidedor reduced to the maximum extent, life and property safety is protected, and healthy and orderly development of social economy in our district is promoted.
Owner:西安市阎良区气象局
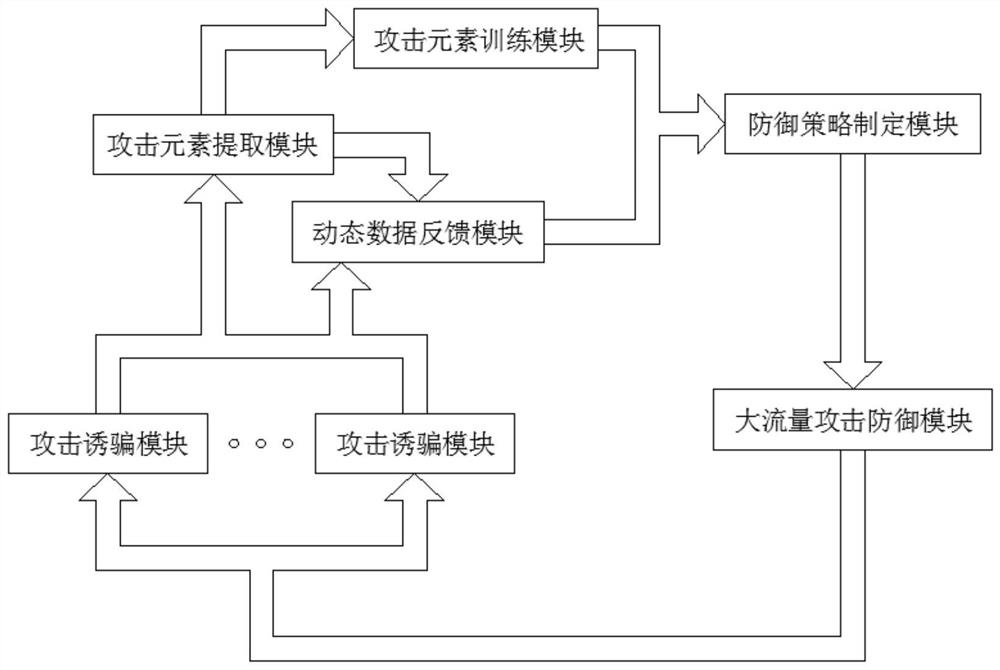
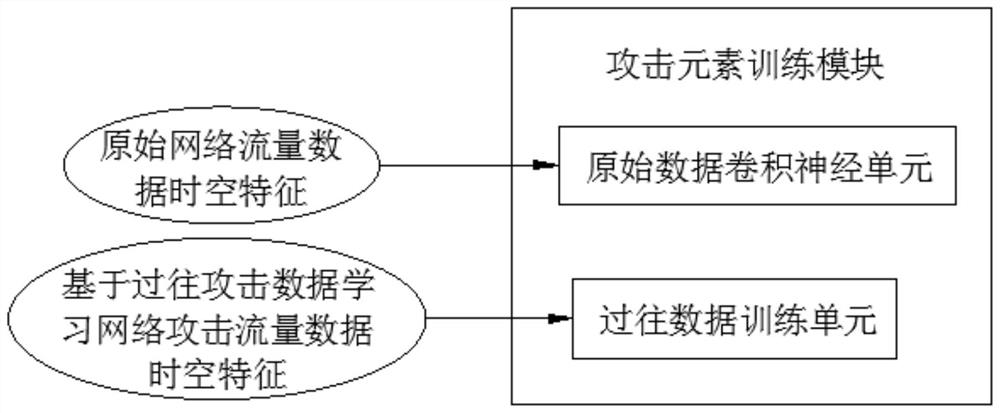
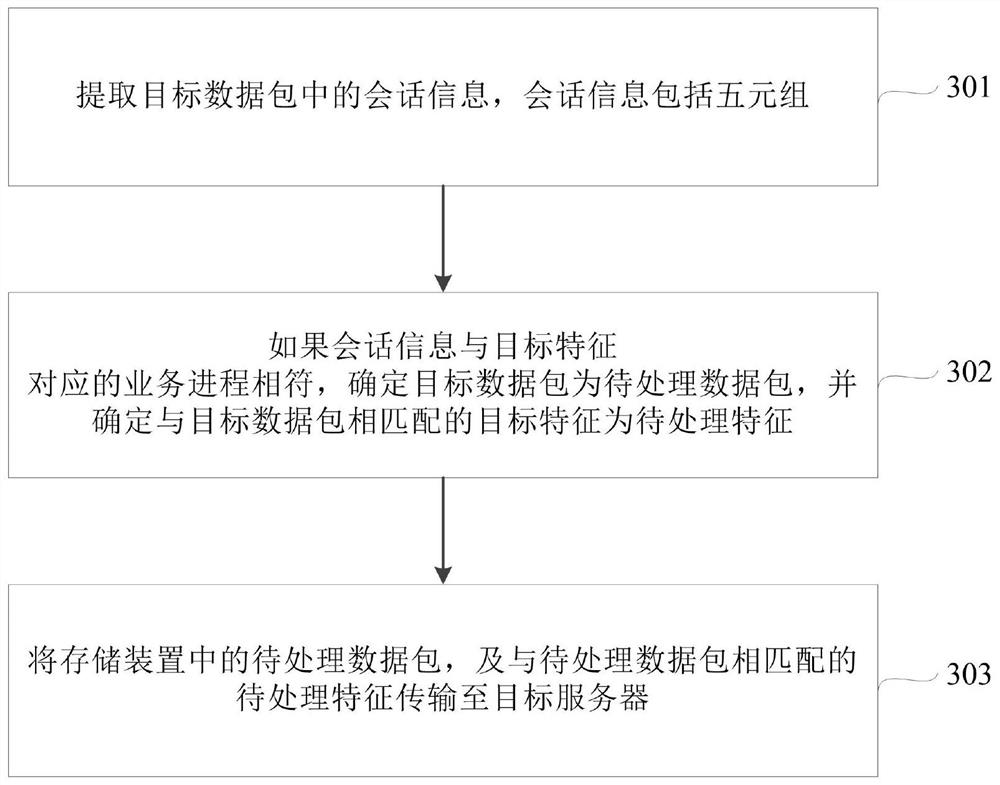
Dynamic defense system for resisting large-flow attacks in honey farm system
ActiveCN113489694AFlexible controlReal-time monitoring of attack dataTransmissionReliability engineeringSystems engineering
The invention discloses a dynamic defense system for resisting large-flow attacks in a honey farm system. The system comprises an attack decoy module arranged at a subnet gateway, an attack element extraction module arranged at the center of a honey farm and in communication connection with the attack decoy module, an attack element training module arranged at the center of the honey farm and connected with the attack element extraction module, a defense strategy making module arranged in the center of the honey farm and connected with the attack element extraction module and the attack element training module, a dynamic data feedback module arranged in the center of the honey farm and connected with the attack decoy module and the defense strategy making module, and a large-flow attack defense module arranged in the center of the honey farm and is connected with the defense strategy making module and the attack decoy module. According to the dynamic defense system for resisting the large-flow attack in the honey farm system, the network security defense performance and security of the honey farm system in response to the large-flow attack are effectively improved.
Owner:浙江德迅网络安全技术有限公司
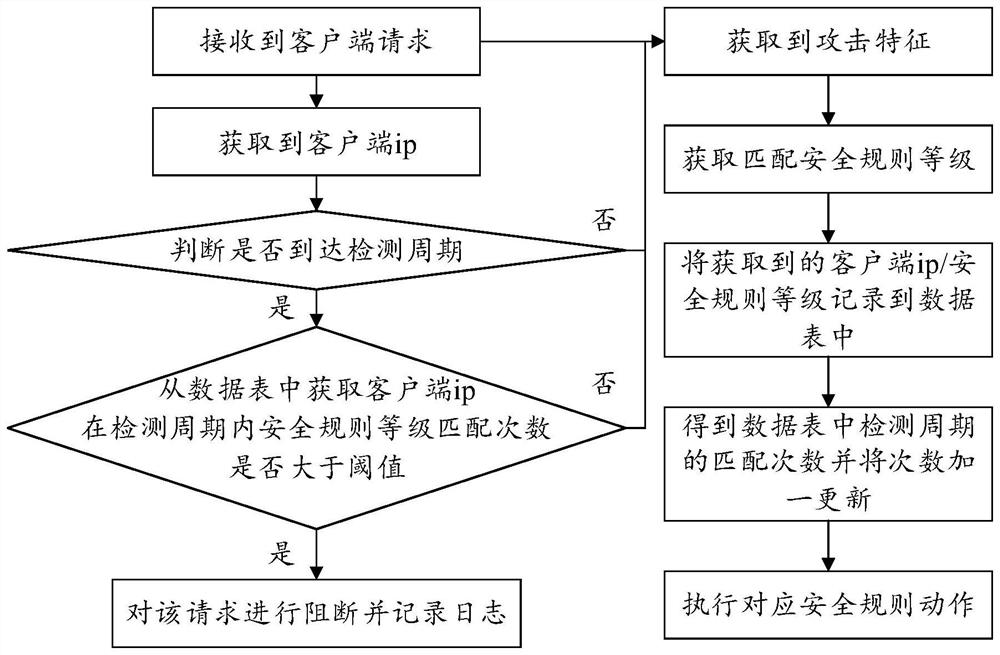
A detection method and device for ips false alarm
The embodiment of the present application discloses a method and device for detecting IPS false alarms, wherein the method includes: after receiving each data packet within a preset period, obtaining the hit feature corresponding to each data packet, and determining the matching The data packets with the above hit characteristics are illegal data packets, and the hit characteristics are the attack characteristics hit by illegal data packets in the IPS signature database; configure the feature filtering strategy according to the hit characteristics, and the feature filtering strategies include: preset feature hit threshold, preset feature hit The threshold is the maximum number of times that any hit feature is allowed to be hit within a preset period; if any hit feature is hit for a number greater than or equal to the preset feature hit threshold within the preset period, it is determined that the IPS is false positive. By adopting the foregoing method or device, IPS false positives can be detected in time, the influence of IPS false positives on normal network services can be reduced, and the defense efficiency of IPS can be improved.
Owner:武汉思普崚技术有限公司
A cloud terminal-based data security defense system, method, and cloud terminal security system
ActiveCN105429975BReal-time monitoring of network statusAvoid attackTransmissionNetwork packetComputer module
Owner:SHANGHAI TAIYU INFORMATION TECH
Virus defense optimization method and device, storage medium and computer equipment
PendingCN112580036AAchieve the purpose of defenseImprove defense efficiencyPlatform integrity maintainanceReliability engineeringComputer engineering
The invention discloses a virus defense optimization method and device, a storage medium and computer equipment, relates to the technical field of network security, and mainly aims to solve the problem that a targeted searching and killing tool is written only after virus features are stored in a virus library in existing computer virus defense, the defense requirement of the novel computer viruscannot be quickly met, and the defense of the computer system fails. The method comprises the steps of judging whether feature information in a target file is matched with defense feature informationin a preset defense feature library or not, and determining the defense feature information in the preset defense feature library according to expected searching and killing and / or repairing of suspicious files under different defense scenes; and if the feature information is matched with the defense feature information, calling a defense operation bound with the defense feature information, and executing the defense operation. The invention is mainly used for optimizing virus defense.
Owner:QI AN XIN SECURITY TECH ZHUHAI CO LTD +1
Vulnerability defense method and system
PendingCN113051583AReduce security risksImprove defense efficiencyPlatform integrity maintainanceAttackNetwork model
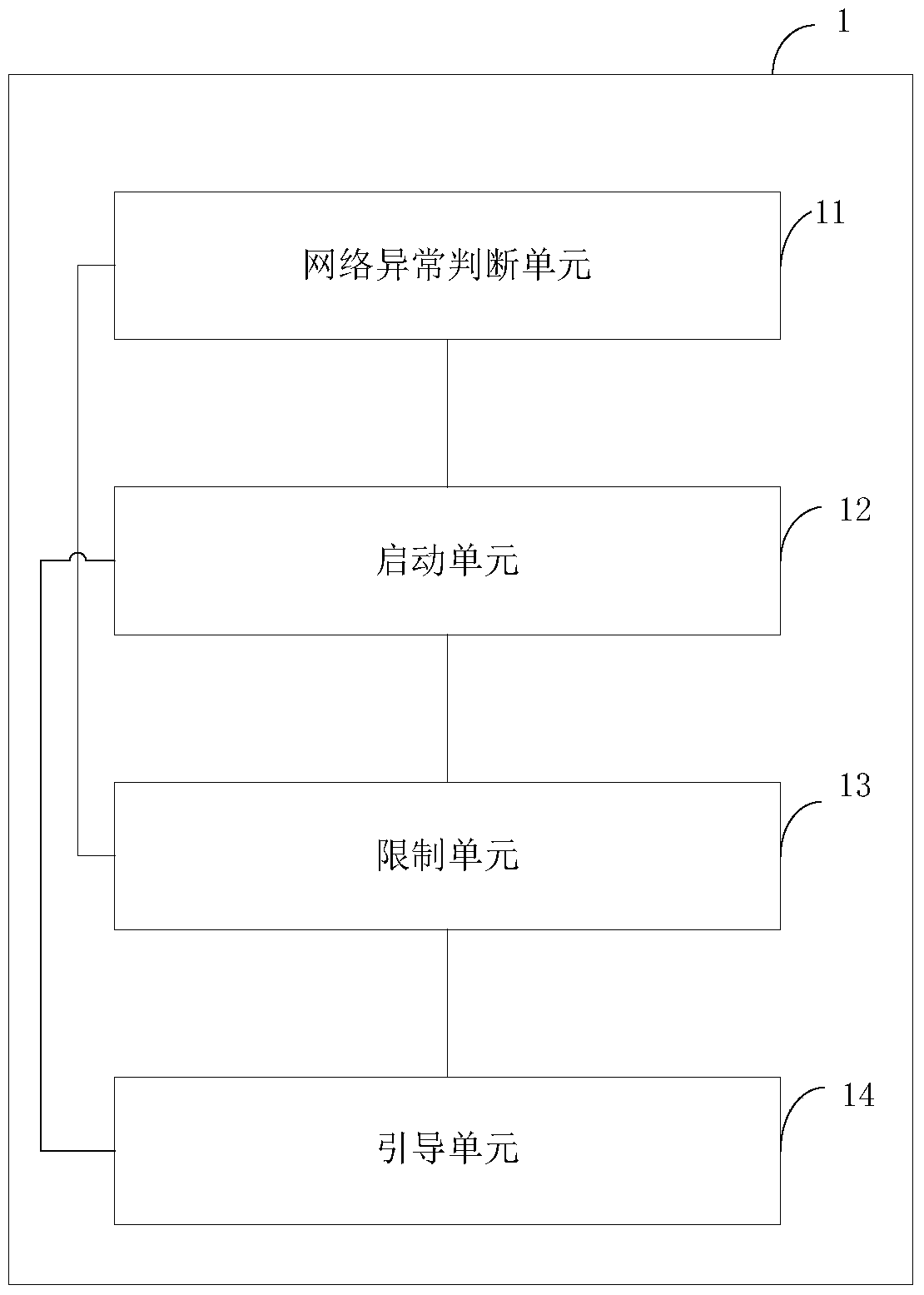
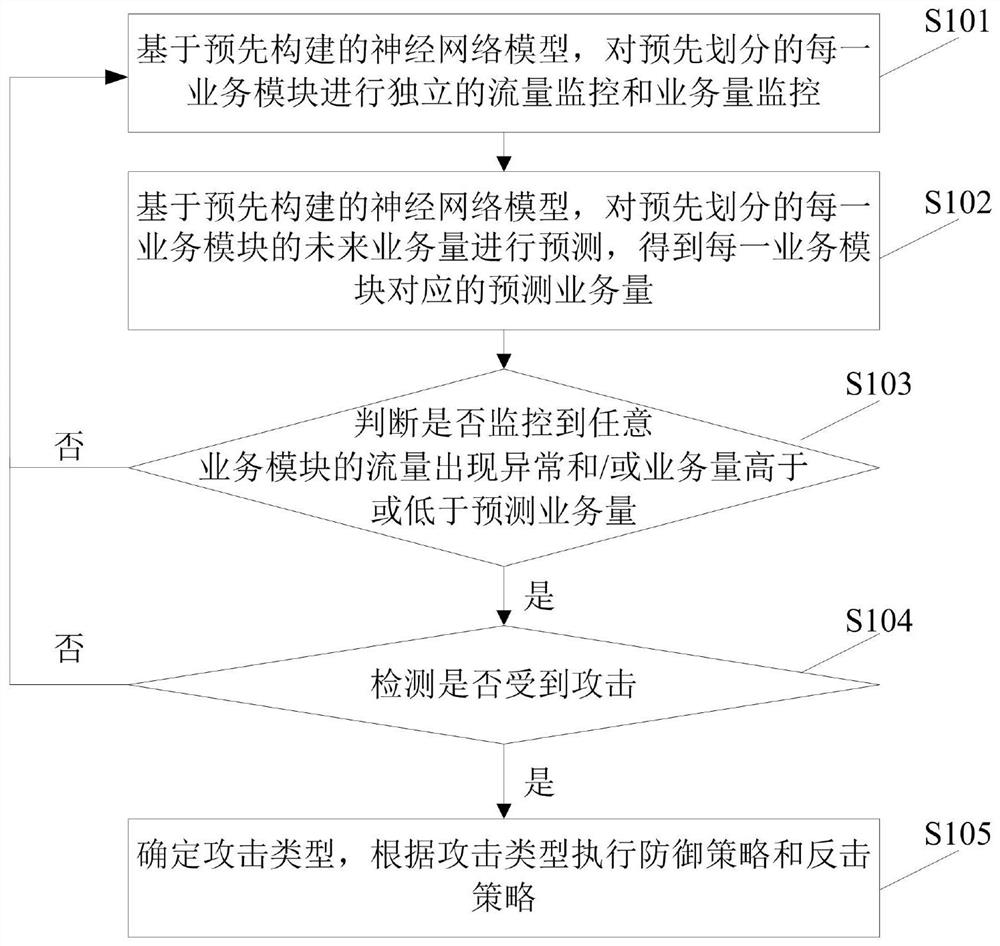
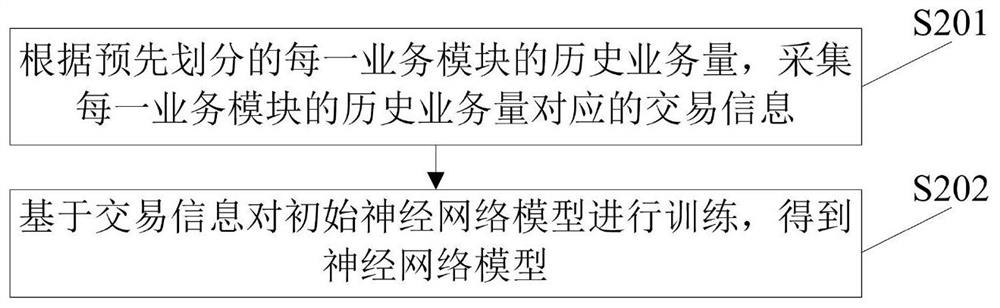
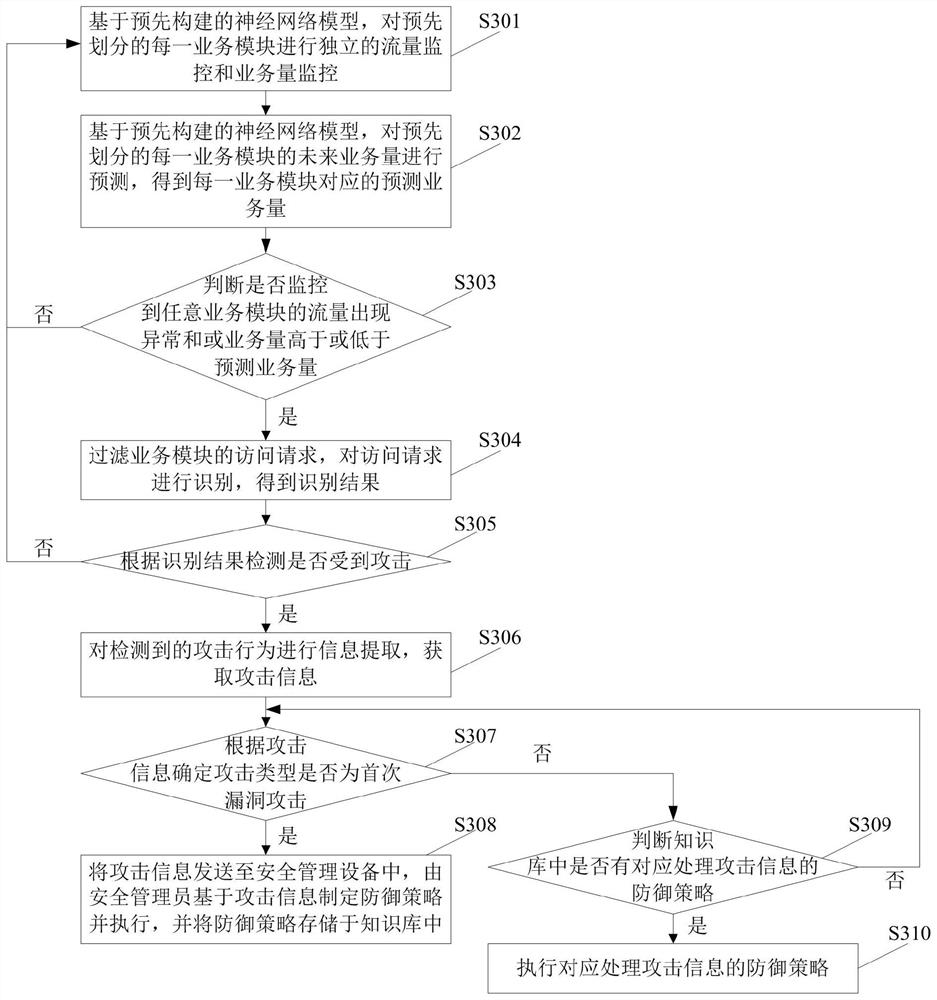
The invention provides a vulnerability defense method and system, and the method comprises the steps: carrying out the independent flow monitoring and business volume monitoring of each pre-divided business module based on a pre-constructed neural network model, predicting the future business volume of each business module, and obtaining the predicted business volume corresponding to each business module; when monitoring that the traffic of any business module is abnormal and / or the business volume is higher or lower than the predicted business volume, detecting whether the business module is attacked; and if the attack is detected, determining an attack type, and executing a defense strategy and a counterattack strategy according to the attack type. According to the scheme, the business modules are divided, the neural network model obtained through pre-training is used for carrying out independent flow monitoring and business volume monitoring on each business module, when any business module is attacked, attacks are defended in time, so that the security risk is reduced, and the attacks are defended in a targeted mode according to the attack types. The defense efficiency is improved, and the overall safety level is improved.
Owner:BANK OF CHINA
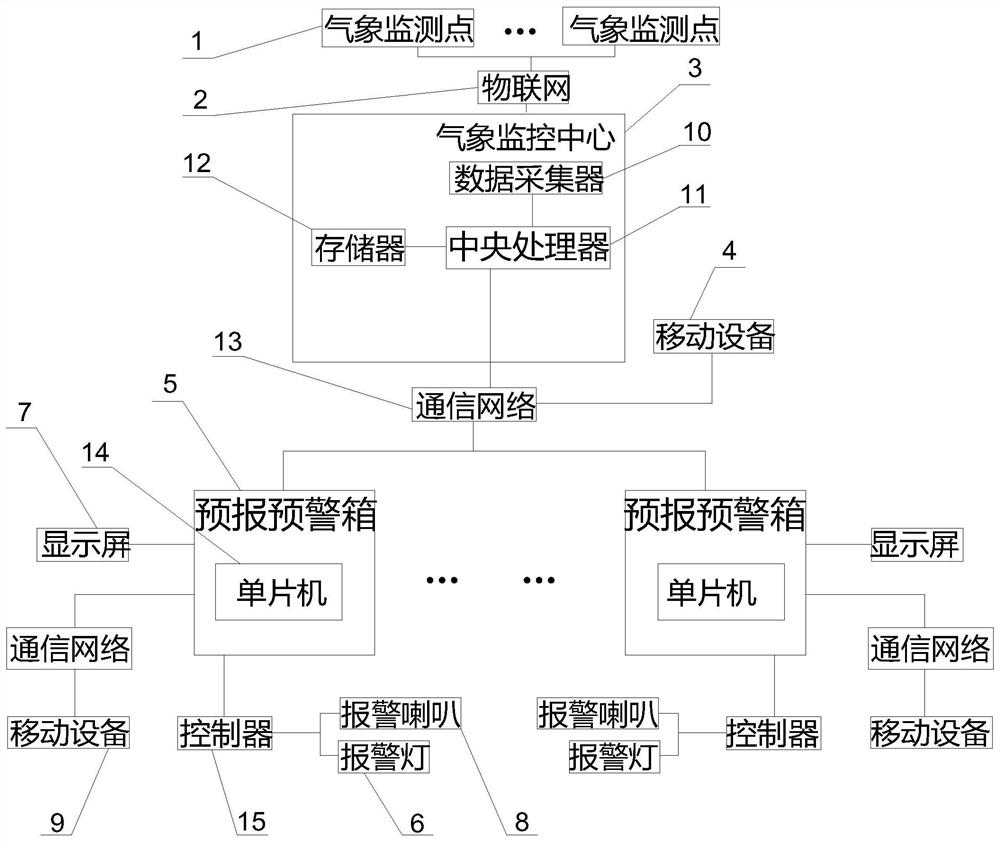
An urban waterlogging warning device and method based on precipitation forecast
ActiveCN112578479BImprove defense efficiencyHuman health protectionRainfall/precipitation gaugesData acquisitionEngineering
Owner:北京风云气象科技发展有限公司
A defense method against rop attack
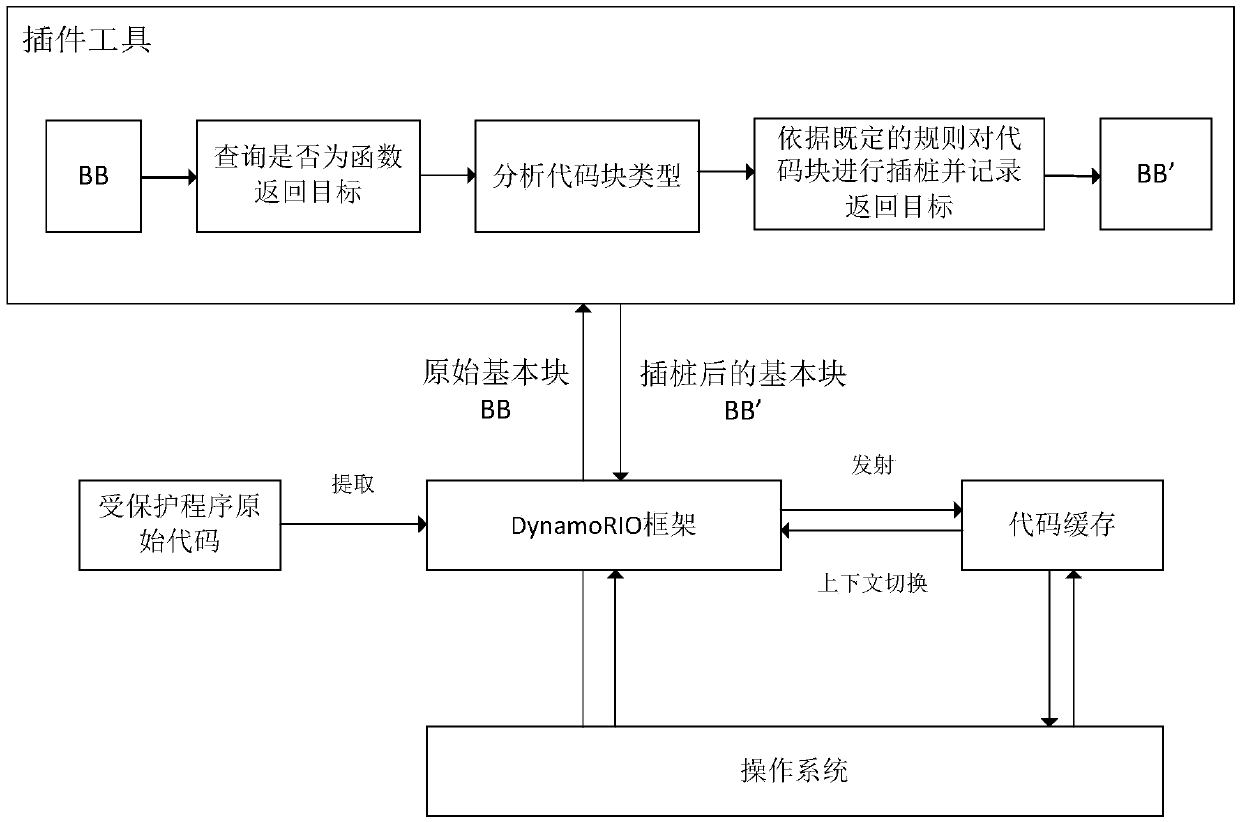
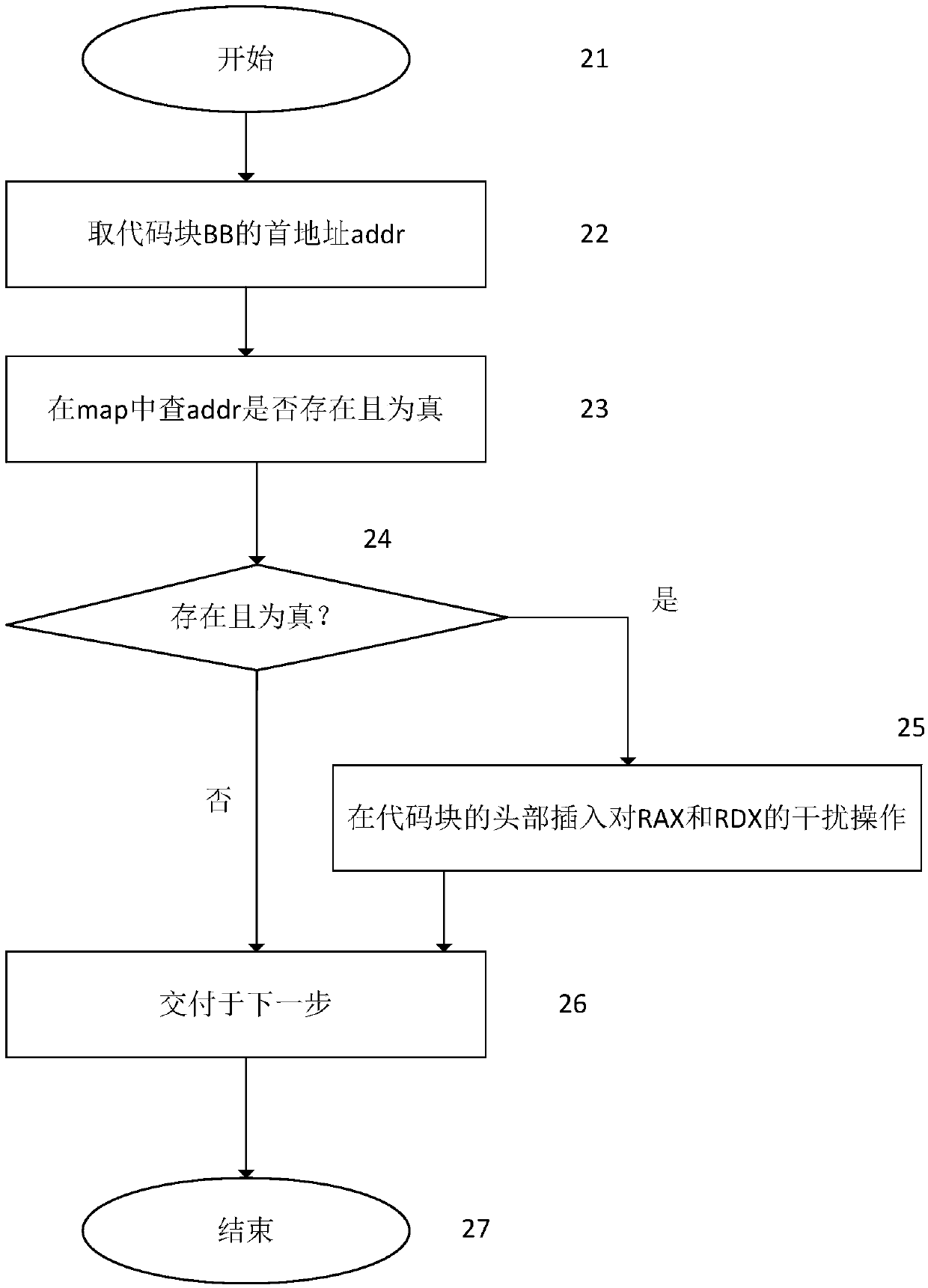
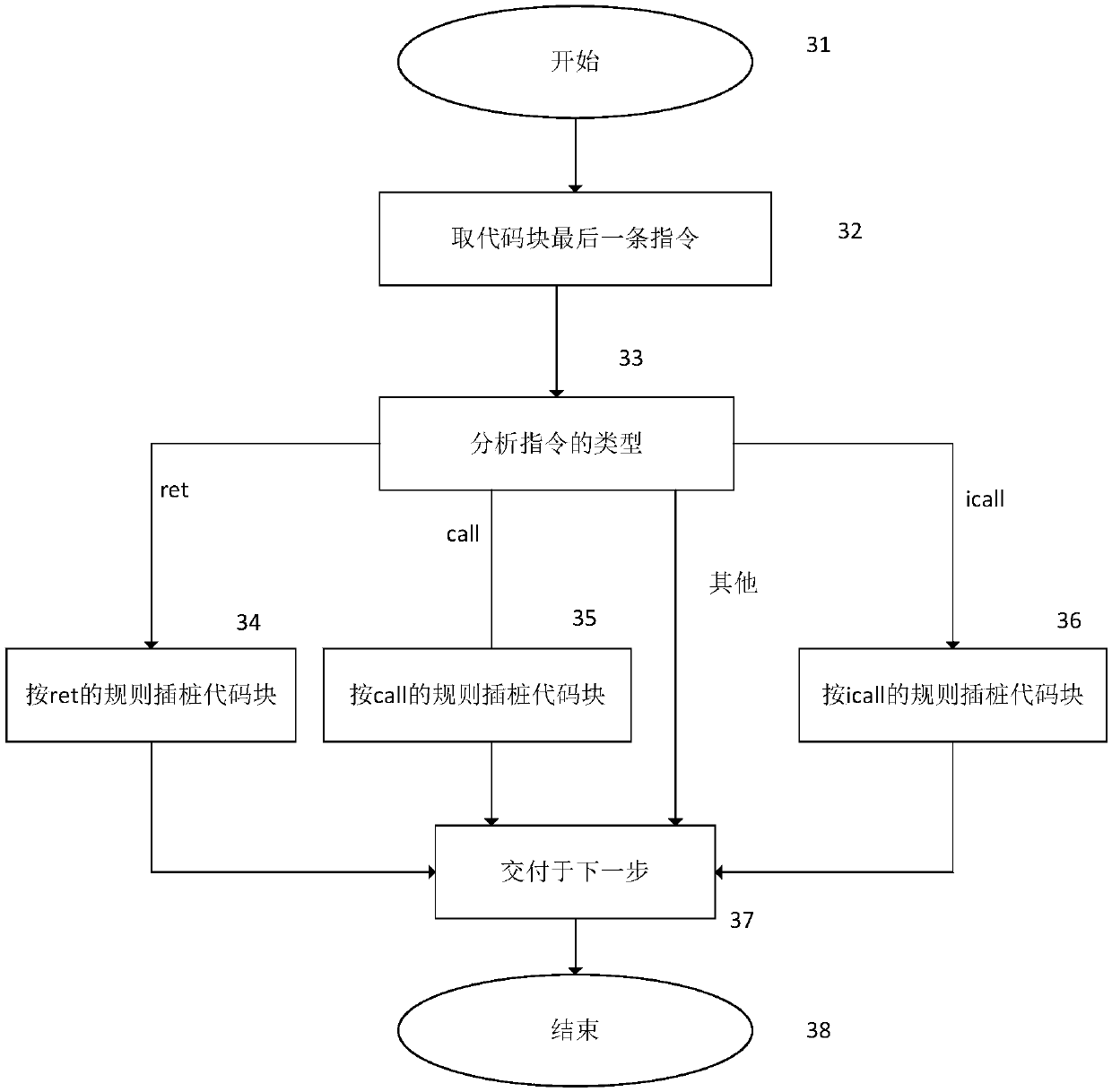
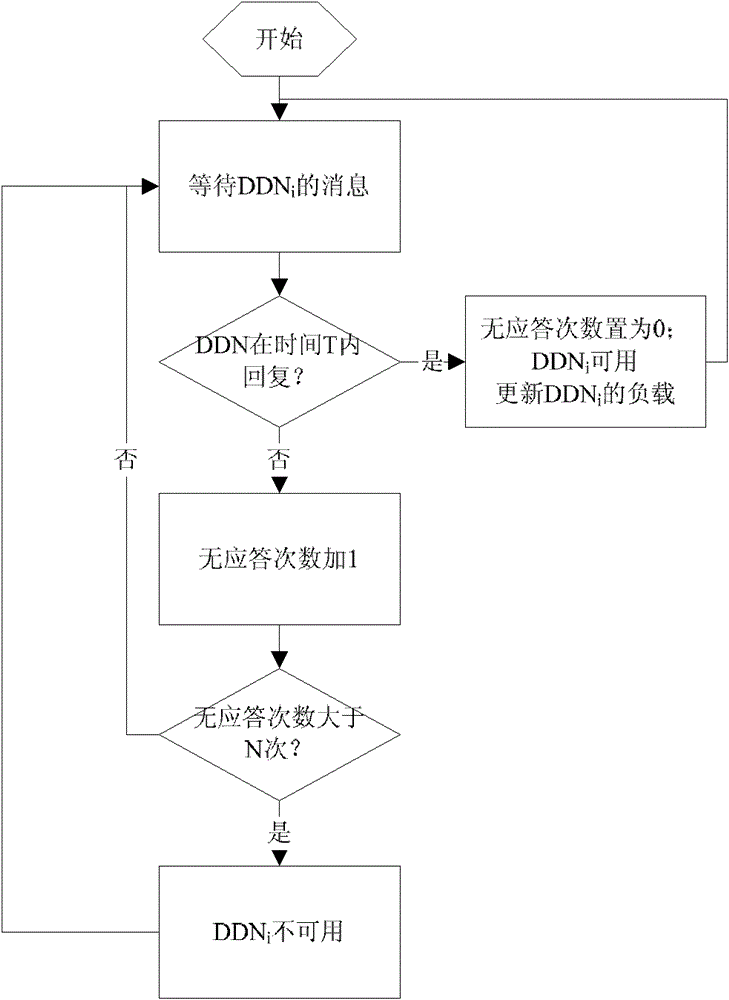
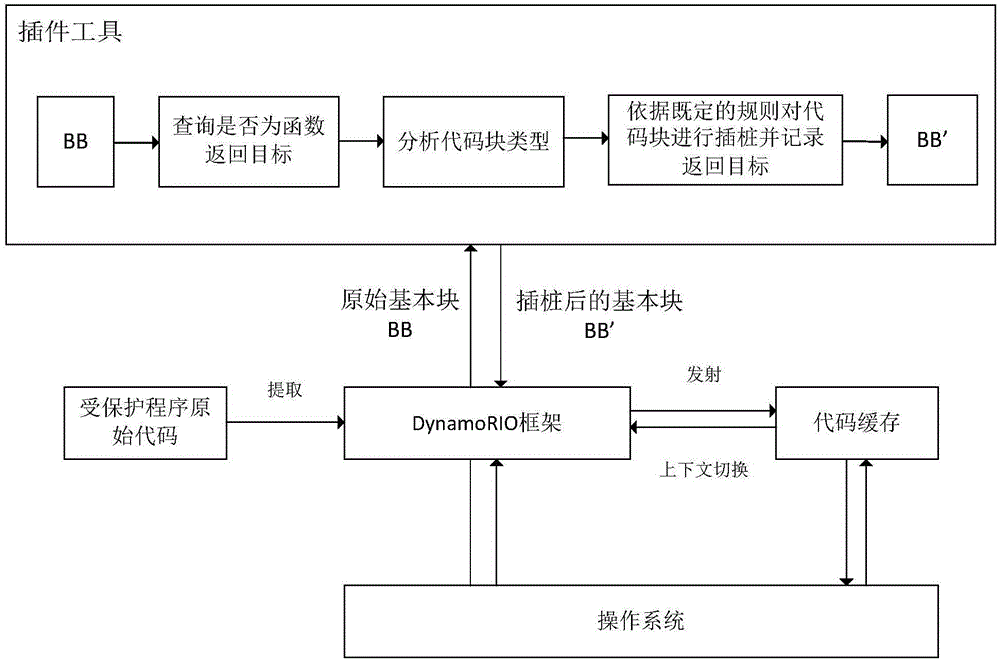
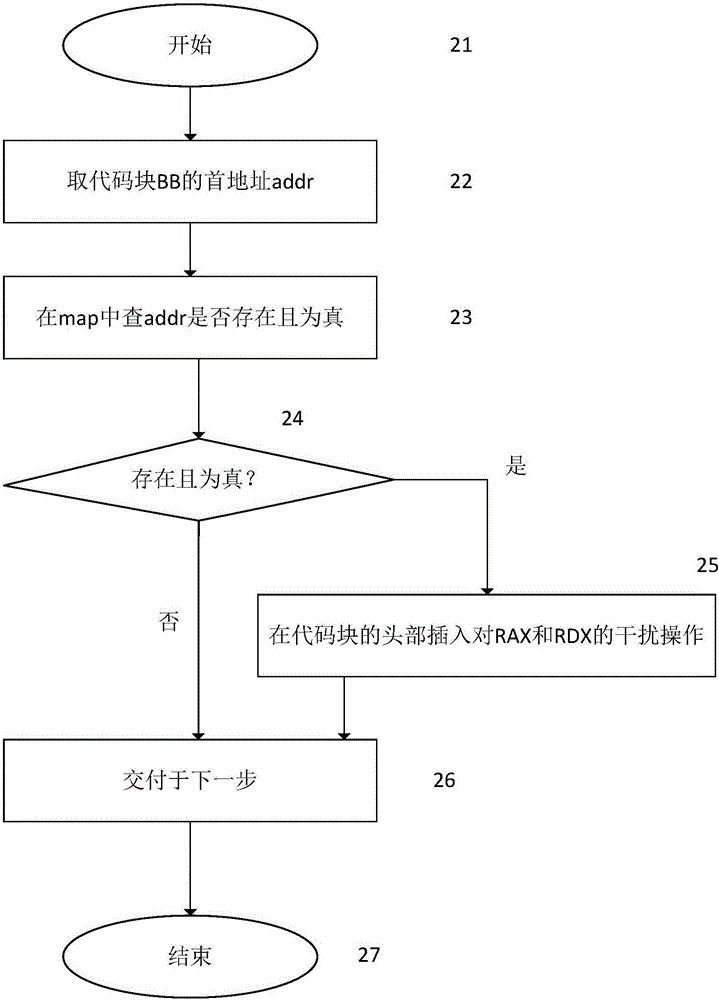
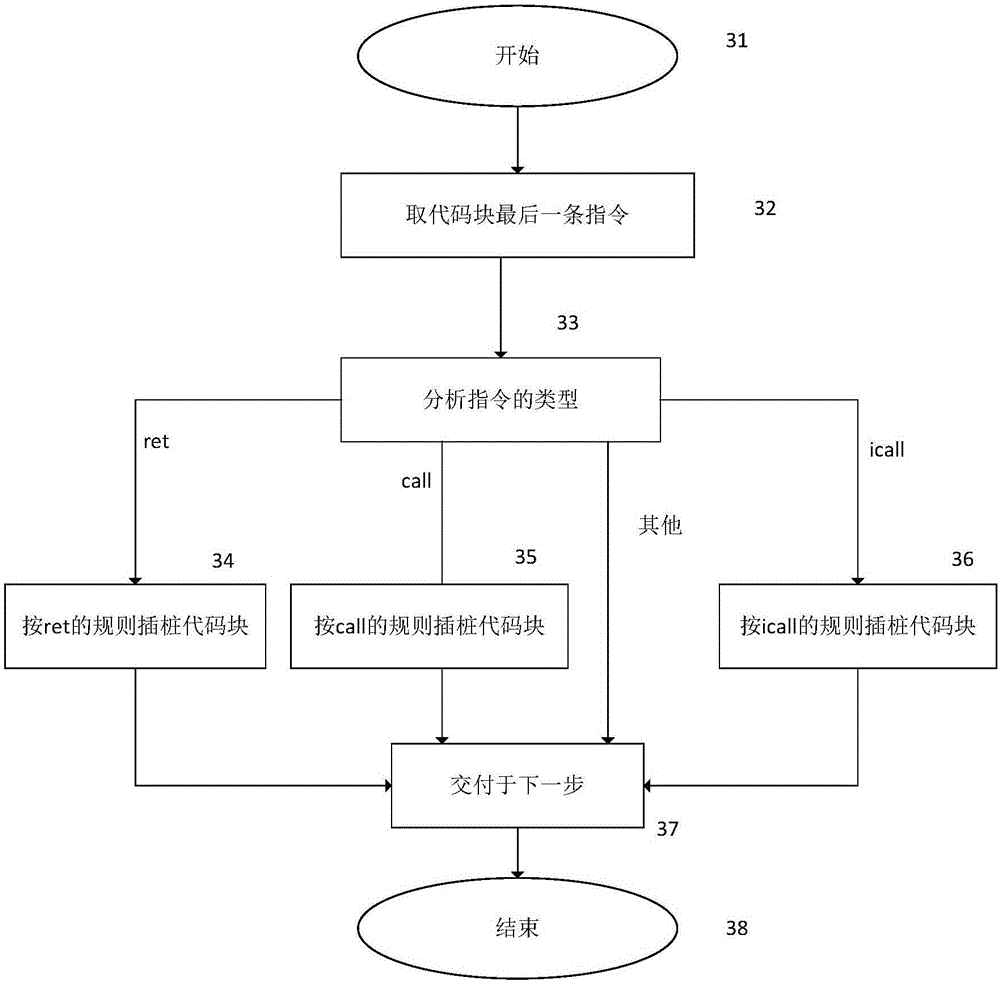
ActiveCN106372501BImprove defense efficiencyPlatform integrity maintainanceComputer hardwareDynamic instrumentation
The invention provides an ROP attack-oriented defense method. The method comprises the following steps of: receiving a basic block sent by a dynamic instrumentation frame, wherein the basic block is extracted by the dynamic instrumentation frame from original codes of protected programs; judging whether the basic block is a return target of a function, and carrying out instrumentation processing on the basic block when the basic block is the return target of the function; analyzing the type of the basic block which undergoes the instrumentation processing and carrying out instrumentation processing on the basic block again according to the analysis result so as to obtain an instrumented basic block; and sending the instrumented basic block to the dynamic instrumentation frame. The ROP attack-oriented defense method provided by the invention does not need to repeatedly carry out complicated storage and recovery operations during the operation, so that the defense efficiency is improved.
Owner:NANJING UNIV
Drone defense systems and methods
ActiveCN108100277BImprove defense efficiencyEasy to catchDefence devicesAircraft componentsCommand and controlSimulation
The invention provides a defensive system and method of an unmanned aerial vehicle, and relates to the technical field of unmanned aerial vehicle countering. The defensive system of the unmanned aerial vehicle comprises a ground detection subsystem, a command and control subsystem and a disposition subsystem. The ground detection subsystem is used for detecting and tracking the target unmanned aerial vehicle and sending position information of the target unmanned aerial vehicle to the command and control subsystem; the command and control subsystem is used for receiving the position information and a capturing instruction input by a commander according to the position information and sending the capturing instruction to the disposition subsystem; the disposition subsystem comprises a capturing unmanned aerial vehicle, an unmanned aerial vehicle ground station and an RTK navigation system, and is used for receiving the position information and the capturing instruction, and the capturing unmanned aerial vehicle is guided to capture the target unmanned aerial vehicle through the RTK navigation system. With the defensive system and method of the unmanned aerial vehicle, high-precisionnavigation information can be obtained, the target unmanned aerial vehicle is convenient to capture, and the defensive efficiency of the unmanned aerial vehicle is improved.
Owner:北京华力创通科技股份有限公司 +1
A web intelligent defense method, device, equipment and readable storage medium
ActiveCN109561090BImprove service qualityImprove performanceSecuring communicationQuality of serviceDatasheet
The invention discloses a web intelligent defense method, which includes: when receiving a request sent by a client, judging whether the request feature is recorded in a data table recording attack information; if so, judging that the request is within a preset first duration Whether the number of attacks within the preset first duration exceeds the preset threshold; when the number of attacks within the preset first duration of the request exceeds the preset threshold, the preset defense rule is executed. Among them, this method avoids the process of repeatedly comparing each request with the attack signature database, thereby reducing the workload, improving the defense efficiency, and correspondingly improving the normal service quality in the network and the performance of the entire network. Correspondingly, a web intelligent defense device, equipment, and readable storage medium disclosed in the present invention also have the above-mentioned technical effects.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
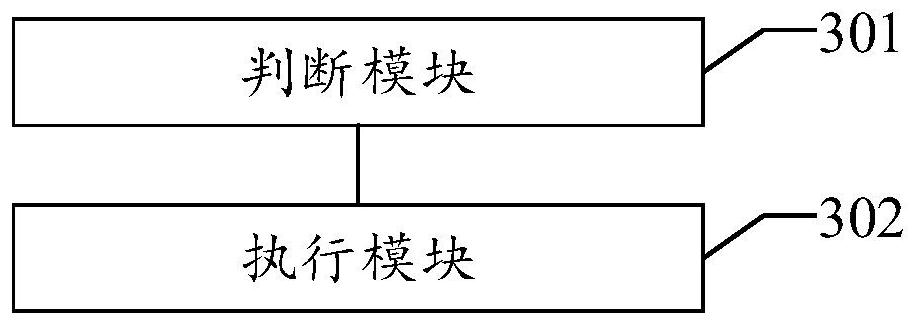
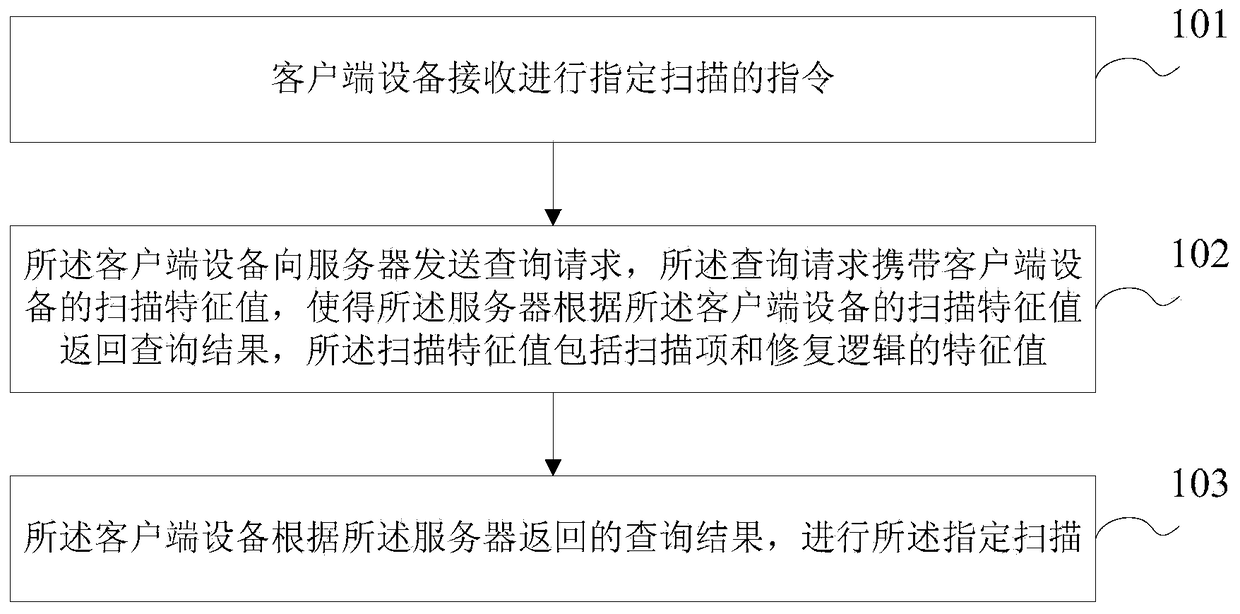
File Scanning Methods, Client Devices, and Servers
Owner:TENCENT TECH (SHENZHEN) CO LTD
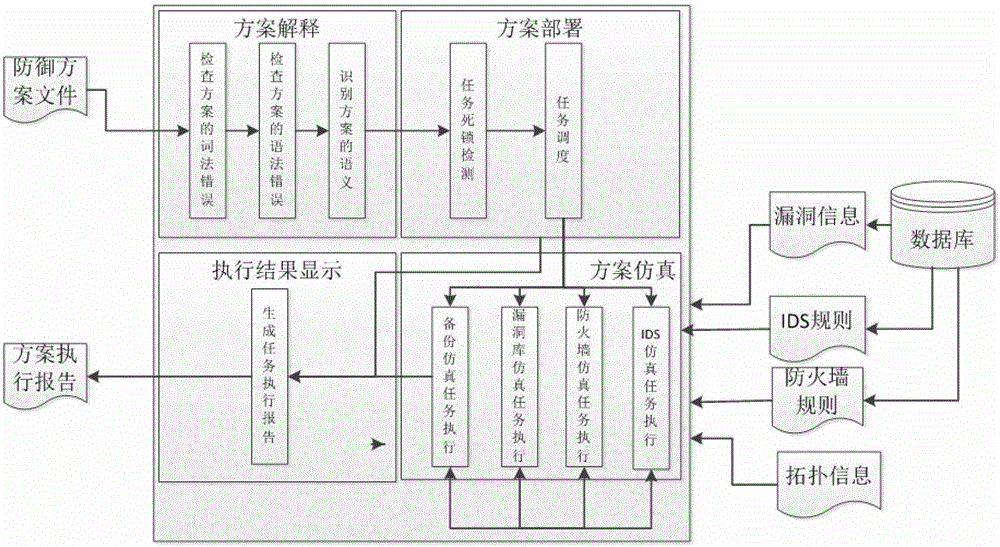
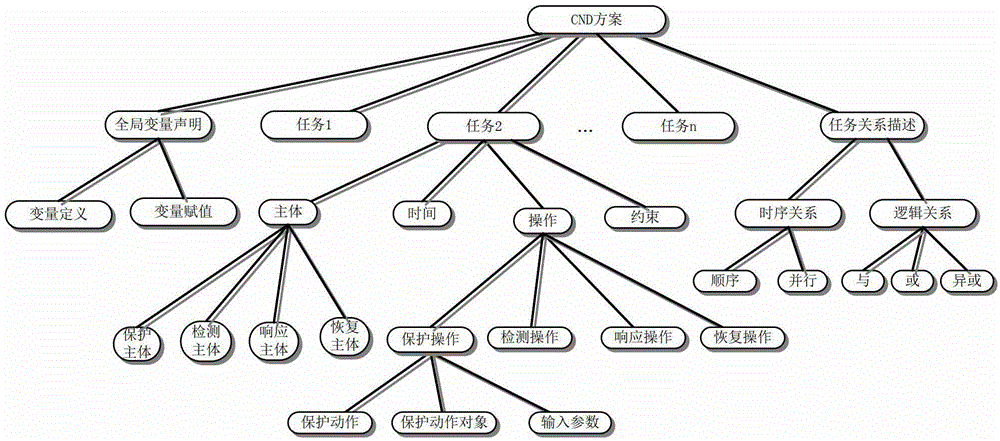
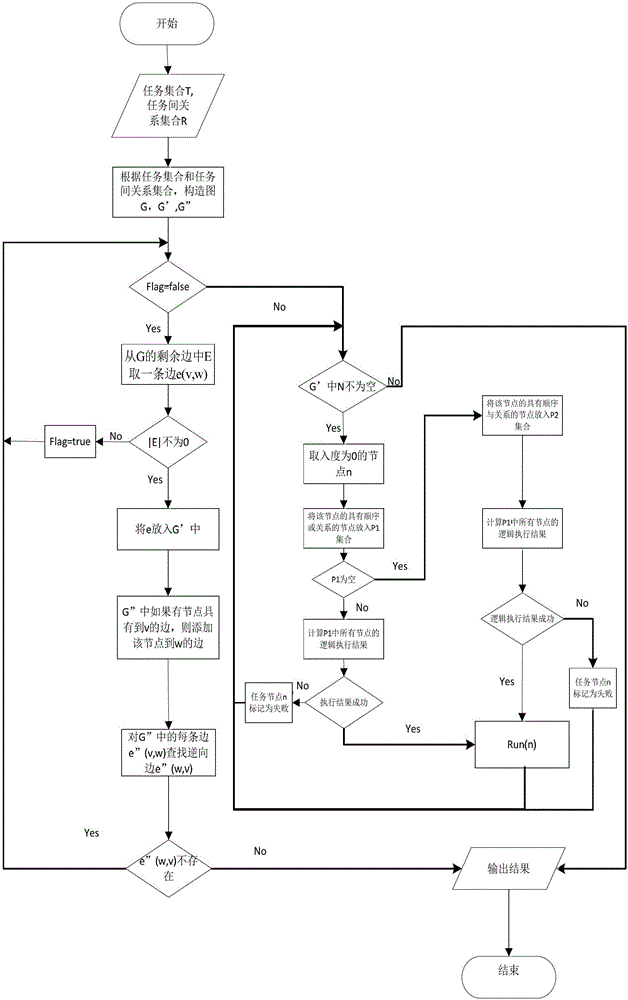
Computer Network Defense Scheme Simulation Execution System
InactiveCN103092680BImprove defense efficiencyTask of preventing conflictSoftware simulation/interpretation/emulationExtended Backus–Naur FormDeadlock
A computer network defense scheme simulation execution system comprises the steps of (1) designing and achieving a formalized computer network defense scheme description language (CNDSDL) with context-free grammar, providing an extended backus naur form (EBNF), designing a language interpreter based on the CNDSDL; (2) proposing a scheme arrangement method based on the CNDSDL, wherein the method comprises a deadlock detection and scheduling algorithm for tasks in a defense scheme, guaranteeing correctness of the defense scheme; and (3) achieving simulation of the defense scheme in a GT net simulation platform, wherein the simulation comprises simulation of an identification section (IDS), a firewall, backups, recovering and linkage tasks among the IDS, a bug library and the firewall.
Owner:BEIHANG UNIV
Method and system for monitoring DDOS (distributed denial of service) attacks in small flow
ActiveCN102821081BHigh false positive rateRealize security protectionData switching networksSimilarity analysisProtocol Application
The invention discloses a method and a system for monitoring DDOS (distributed denial of service) attacks in small flow, solves the problems that the existing DDOS attack detection technology is high in cost, complex to implement and high in misjudgment rate, cannot respond to DDOS attacks aiming at an application layer and the like, and provides the monitoring scheme of an integrated DPI (dots per inch) technology. A baseline analysis, component analysis and similarity analysis method is used to establish a normal use model, characteristics are accurately matched to detect the attacks in small flow and the application layer attacks, deployment at one point of an operator network and complete coverage of the operator network are achieved, and detection accuracy is increased.
Owner:CHINA TELECOM CORP LTD
A sip DDoS attack distributed defense system and its load balancing method
ActiveCN103166926BHigh message processing capacityImprove scalabilityTransmissionDistributed structureStructure of Management Information
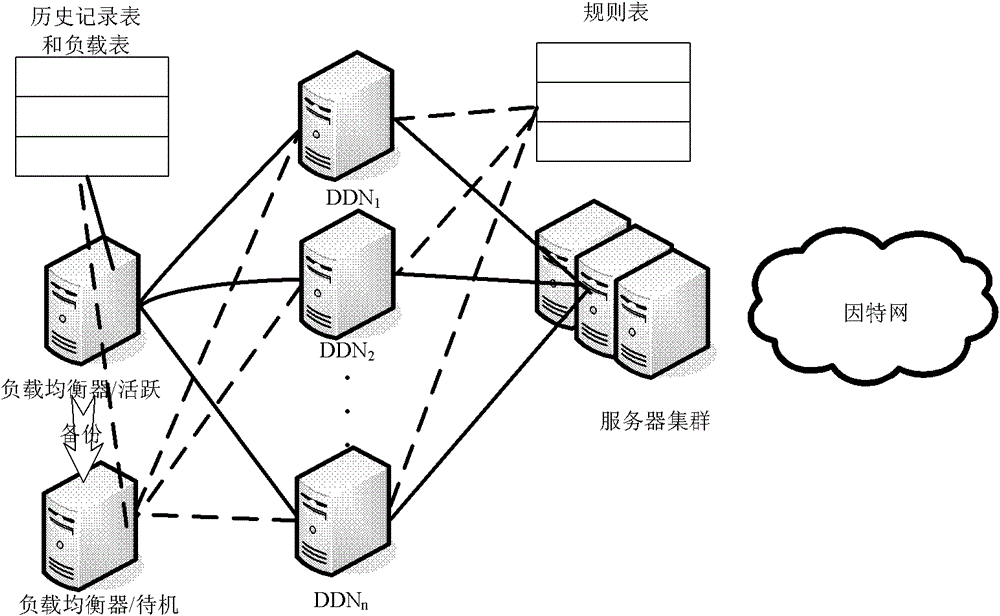
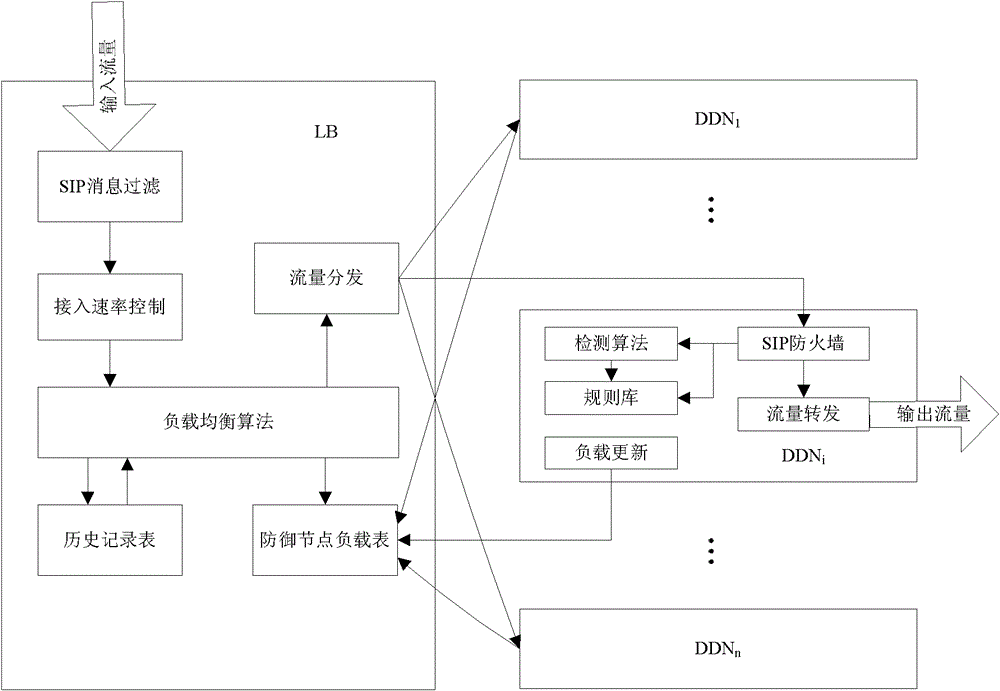
The invention relates to the fields of VoIP network security and IP communication, in particular to a SIP DDoS attack distributed defense system and a load balancing method thereof. The invention includes a defense detection node connected with a load balancer for notifying load information to the load balancer in real time and sharing a rule base; a load balancer connected with multiple defense detection nodes for distributing SIP messages to each defense The detection node updates the defense node load table according to the load information sent by the defense detection node. The invention adopts a distributed structure with high message processing capability and good scalability; based on the detection algorithm load balancing method, it has a high attack detection rate and a low false alarm rate; using a load distribution algorithm, each node It has good load balancing characteristics.
Owner:中国科学院沈阳计算技术研究所有限公司
ROP attack-oriented defense method
ActiveCN106372501AImprove defense efficiencyPlatform integrity maintainanceDynamic instrumentationDROWN attack
The invention provides an ROP attack-oriented defense method. The method comprises the following steps of: receiving a basic block sent by a dynamic instrumentation frame, wherein the basic block is extracted by the dynamic instrumentation frame from original codes of protected programs; judging whether the basic block is a return target of a function, and carrying out instrumentation processing on the basic block when the basic block is the return target of the function; analyzing the type of the basic block which undergoes the instrumentation processing and carrying out instrumentation processing on the basic block again according to the analysis result so as to obtain an instrumented basic block; and sending the instrumented basic block to the dynamic instrumentation frame. The ROP attack-oriented defense method provided by the invention does not need to repeatedly carry out complicated storage and recovery operations during the operation, so that the defense efficiency is improved.
Owner:NANJING UNIV
Method and device for identifying network access source based on network address
ActiveCN106921628BImprove defense efficiencyEffective defenseTransmissionNetwork addressingEngineering
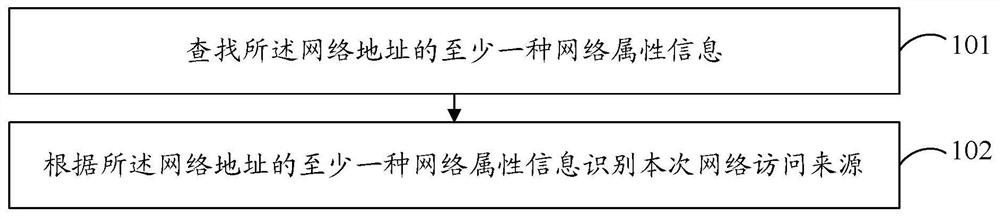
An embodiment of the present application provides a method for identifying a network access source based on a network address. The method includes: searching for at least one type of network attribute information of the network address; and identifying the source of this network access according to the at least one type of network attribute information of the network address. According to the embodiment of the present application, the real network access source can be identified, so that effective defense can be performed, and the defense efficiency against malicious network attacks is improved.
Owner:ALIBABA GRP HLDG LTD
Virus recognition method and device, storage medium and computer equipment
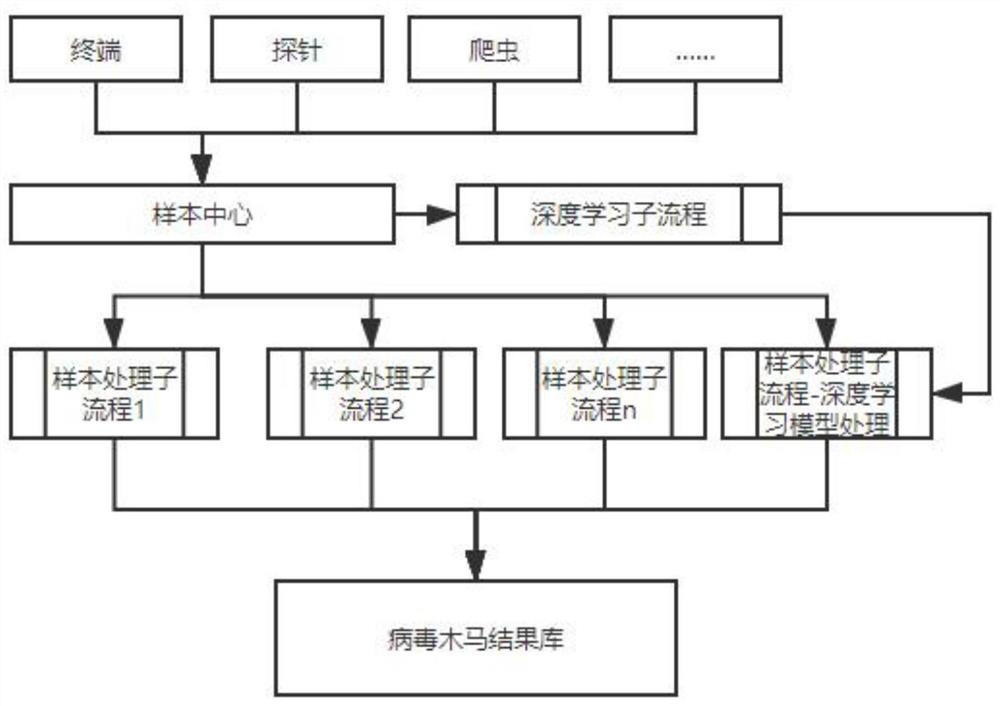
InactiveCN112579878AAchieve advanceImprove defense efficiencyDigital data information retrievalCharacter and pattern recognitionFeature extractionEngineering
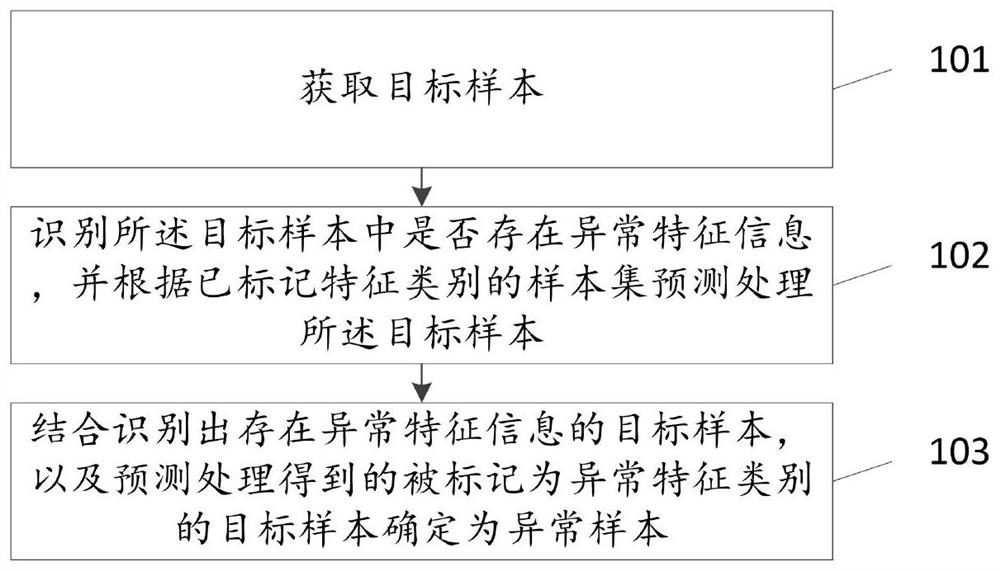
The invention discloses a virus recognition method and device, a storage medium and computer equipment, relates to the technical field of network security, and mainly aims to solve the problem that when a network security tool recognizes computer viruses, corresponding feature extraction, detection and other operations are performed on suspicious virus Trojans after the suspicious virus Trojans are found. The method comprises of obtaining a target sample; identifying whether abnormal feature information exists in the target sample or not, and predicting and processing the target sample according to the sample set marked with the feature category; and determining the target sample marked as the abnormal feature category as an abnormal sample in combination with the target sample with the abnormal feature information and the target sample obtained by prediction processing. The invention is mainly used in the identification of viruses.
Owner:QI AN XIN SECURITY TECH ZHUHAI CO LTD +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com