A method for analyzing network attacker behavior based on attack graph
A behavior analysis and network attack technology, applied in transmission systems, electrical components, etc., can solve problems such as inability to respond in time to attacks, errors, and the system cannot detect attacks, so as to improve network security defense capabilities, prevent network crimes, and improve defense. The effect of efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] The present invention will be further explained below in conjunction with the embodiments and the accompanying drawings. The following examples are only used to illustrate the present invention, but are not intended to limit the scope of the present invention.
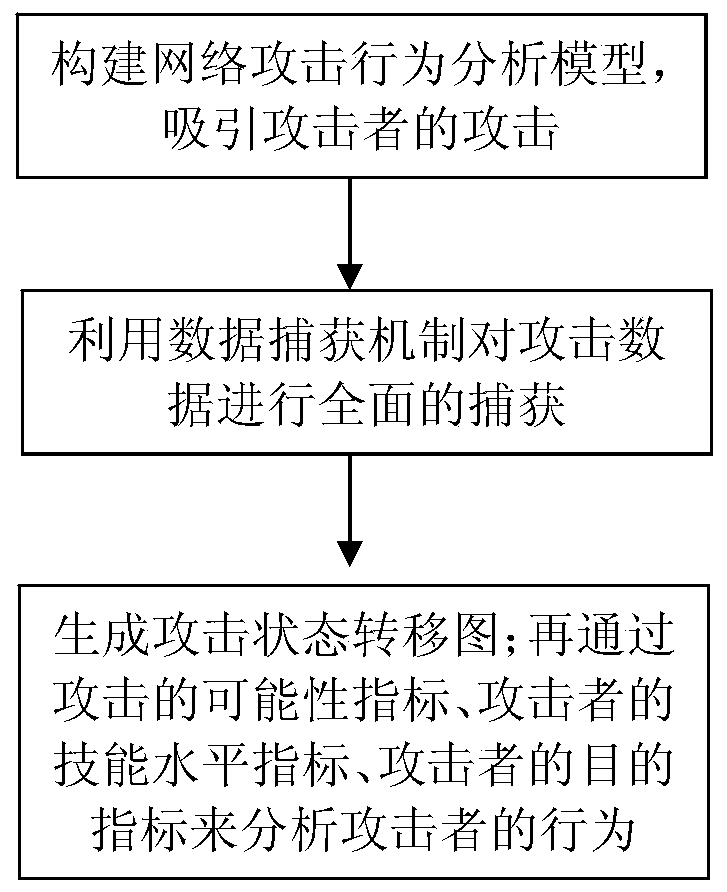
[0031] A network attacker behavior analysis method based on attack graph, such as figure 1 shown, including the following steps:
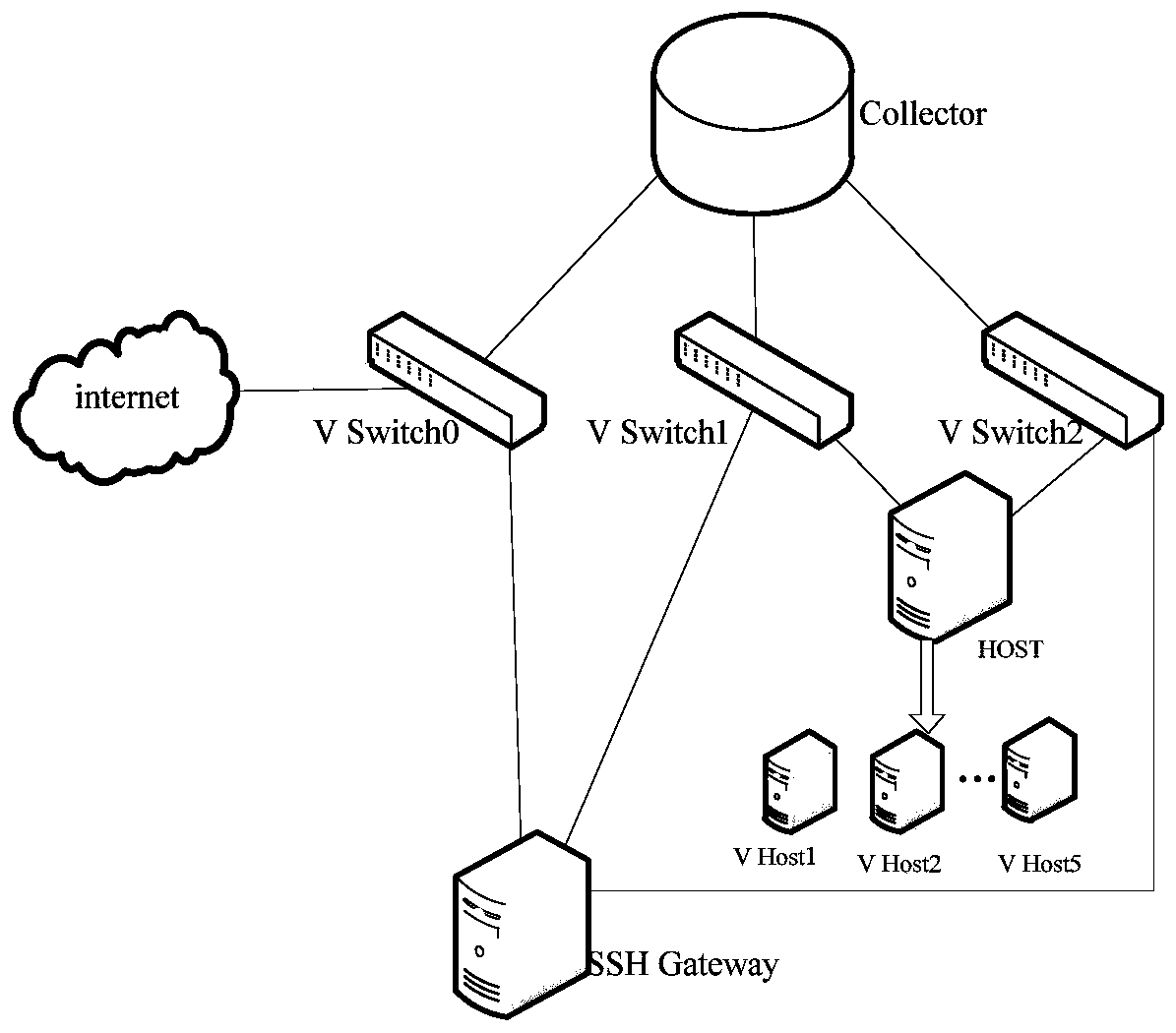
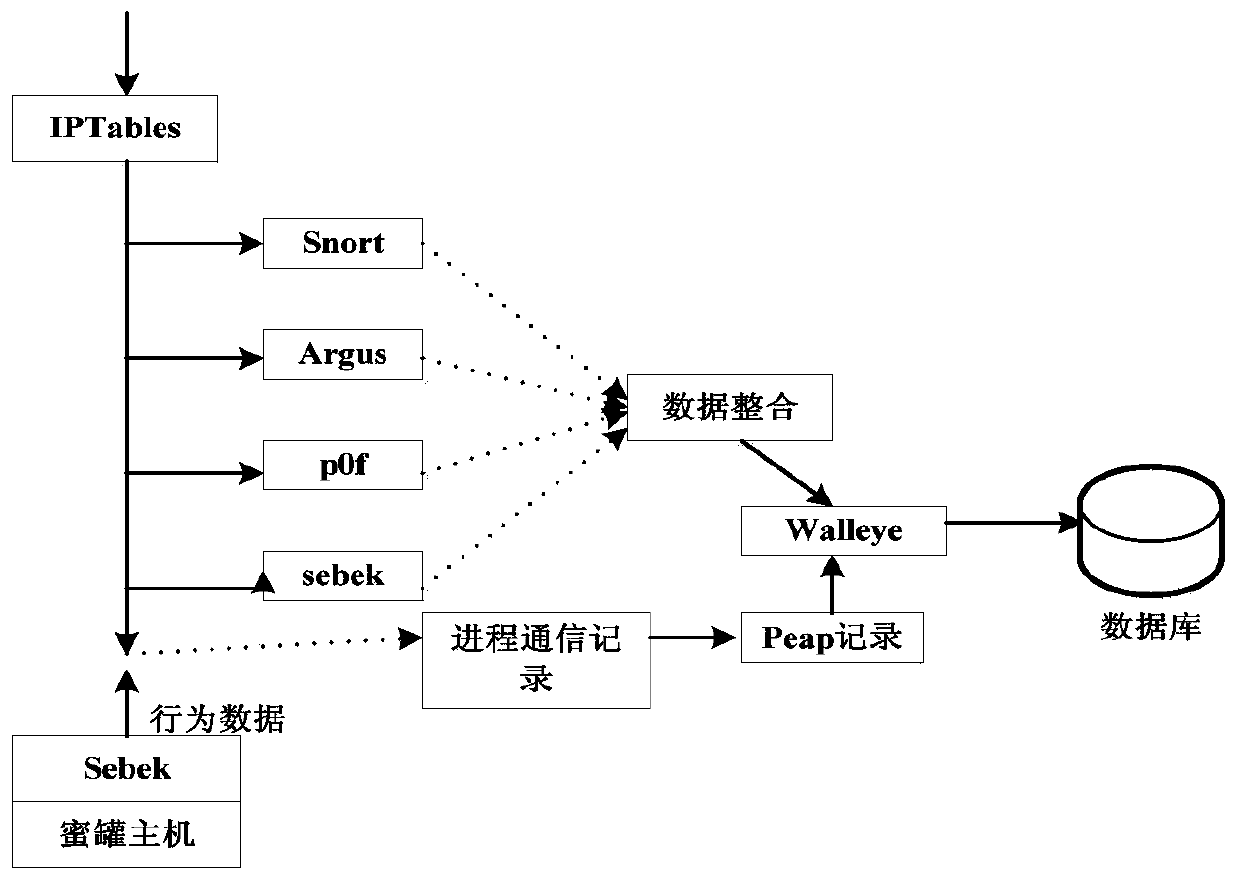
[0032] 1) Build a network attack behavior analysis model to attract attackers' attacks. The network attack behavior analysis model is the honeypot deployment network structure diagram as shown in figure 2 As shown, it is composed of SSH Gateway, Host and Collector, which are divided into three network segments to form a master-slave architecture; the SSH Gateway and host series machines are in the honeypot network segment, and the host series The machine and the controller are in the management network segment, and the SSH gateway and the controller are in the Internet network se...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com