Data safety defense system and method based on cloud terminal, and cloud terminal safety system
A data security and defense system technology, applied in transmission systems, electrical components, etc., can solve problems such as cloud terminals not operating normally, and achieve the effect of improving defense efficiency and preventing attacks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
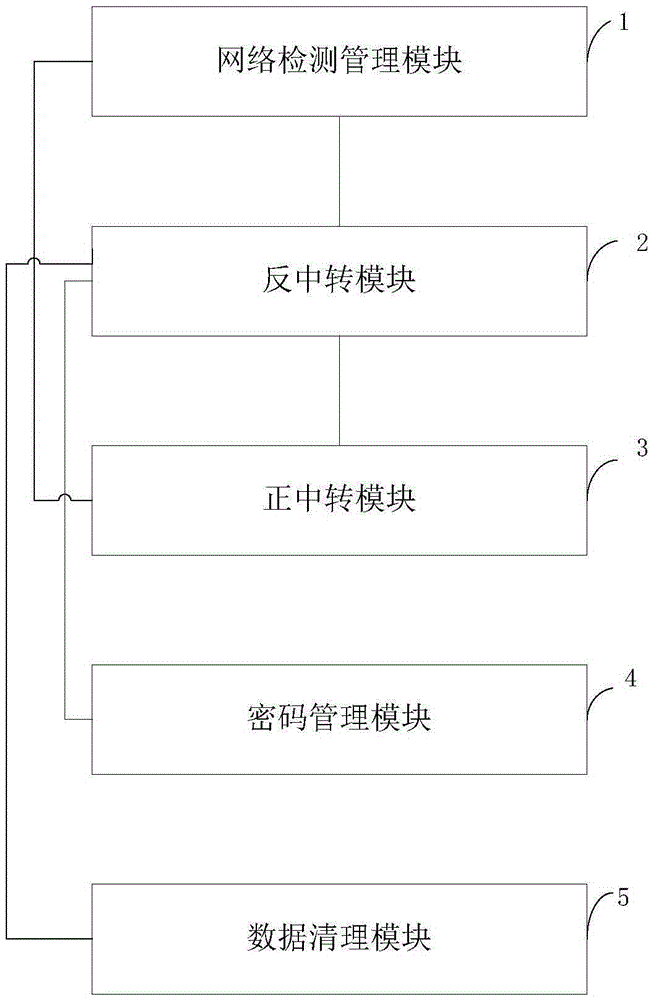
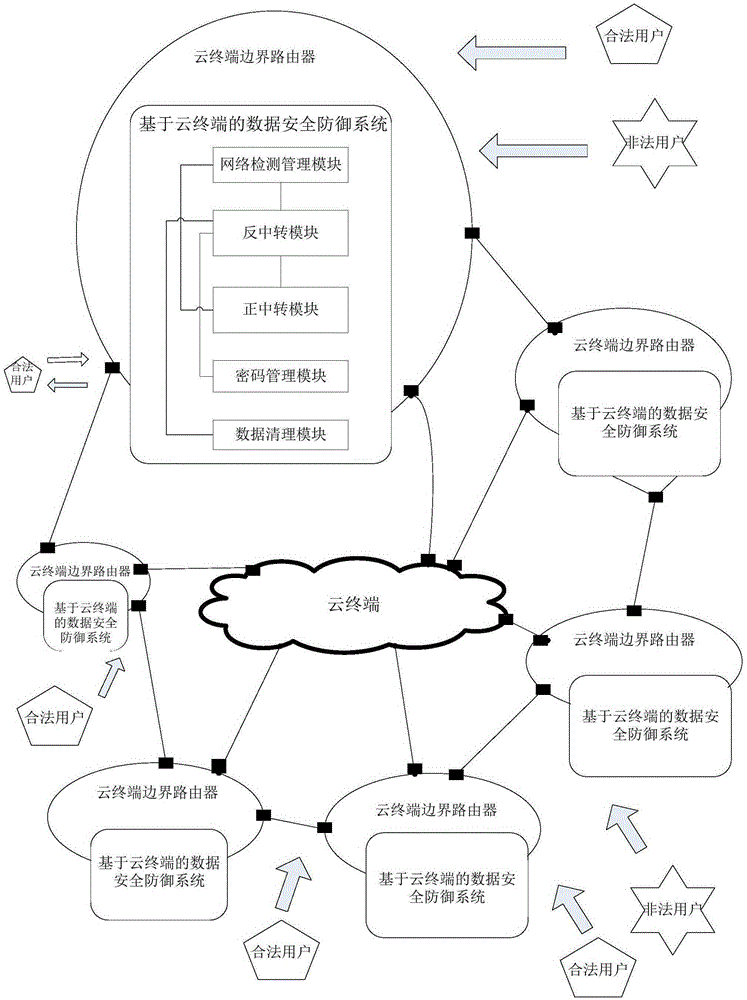
[0046] see figure 1, is a structural diagram of a cloud terminal-based data security defense system of the present invention, the system includes: a network detection management module 1, an anti-transfer module 2, and a forward transfer module 3, the network detection management module 1 and the anti-transfer module Both the module 2 and the forward transfer module 3 are connected, and the reverse transfer module 2 is connected to the forward transfer module 3 .
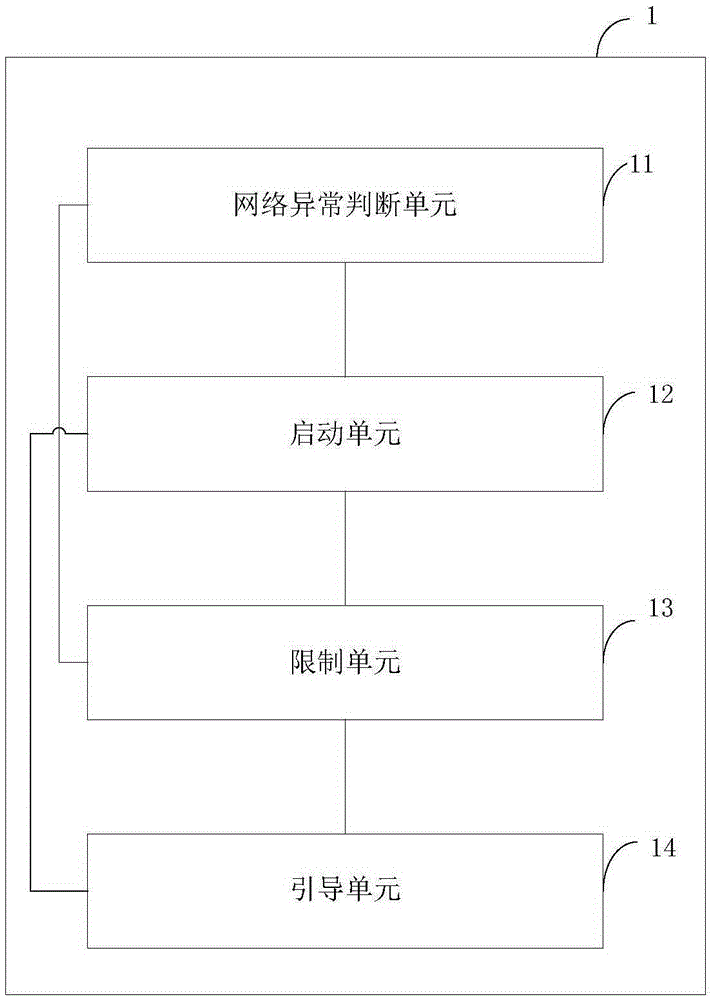
[0047] The network monitoring and management module 1 is used to monitor the network status of the cloud terminal in real time. When it is monitored that the cloud terminal is under attack, restrict the client's access to the cloud terminal, start the anti-transfer module, and guide the current access data packet to the anti-transit module 2;
[0048] The anti-transfer module 2 is used to intercept the current access data packet, and send the legal access data packet in the intercepted current access data packet to...
Embodiment 2
[0090] Based on the above embodiments, the present invention also provides a security defense method based on cloud terminals, such as Figure 6 As shown, it is a flowchart of a cloud terminal-based security defense method of the present invention, wherein the method includes steps:
[0091] Step S1, real-time monitoring of the network status of the cloud terminal;
[0092] Step S2, when it is monitored that the cloud terminal is under attack, restricting access to the cloud terminal;
[0093] Step S3, intercepting the current access data packet;
[0094] Step S4, storing legal access data packets in the intercepted current data packets, the current access data packets including legal access data packets and illegal access data packets.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com