Vulnerability defense method and device
A vulnerability and defense system technology, applied in the field of vulnerability defense methods and devices, can solve the problems of private information acquisition, system paralysis, etc., achieve the effect of protecting private information, system stability, and improving the overall security level
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
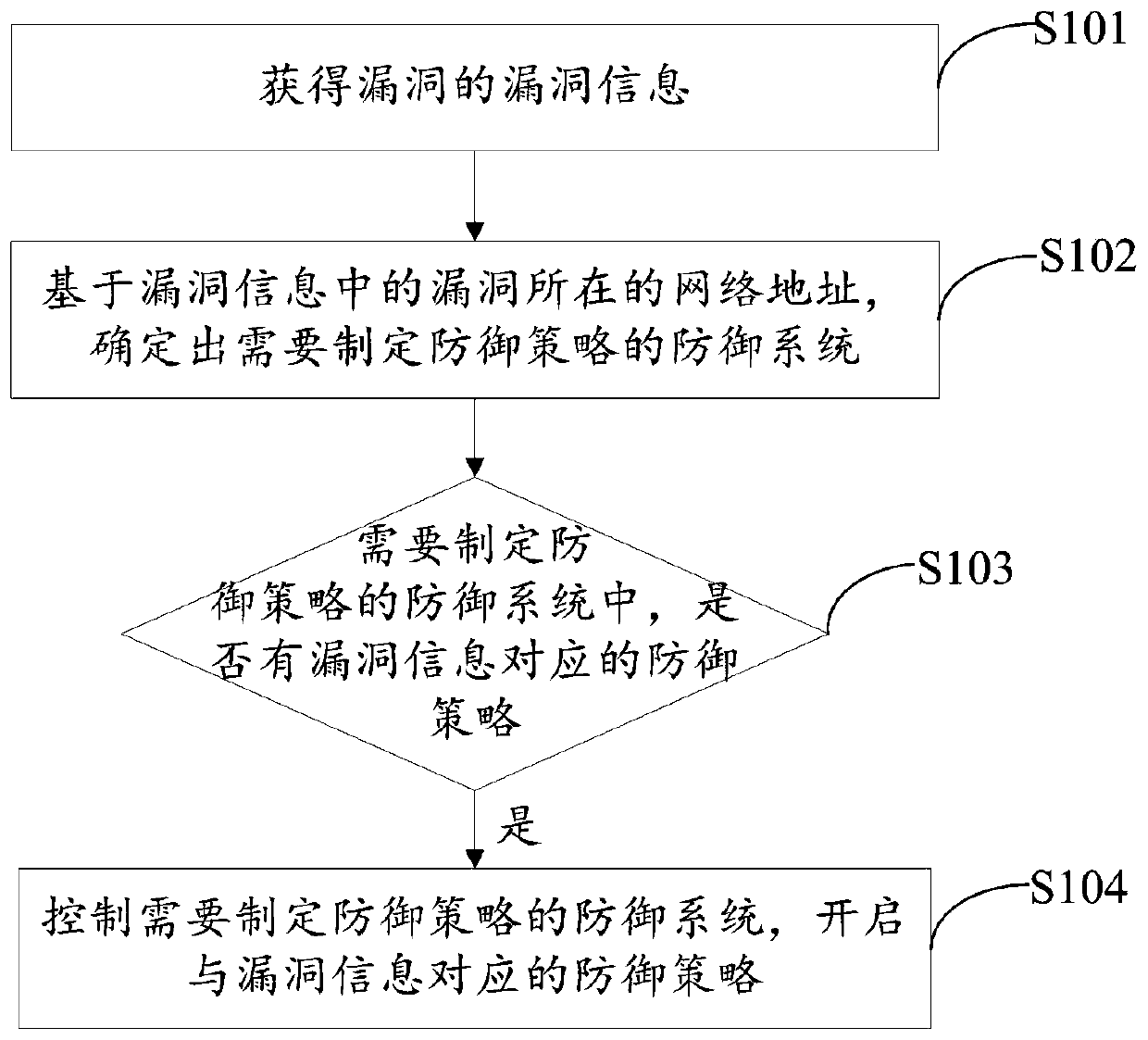
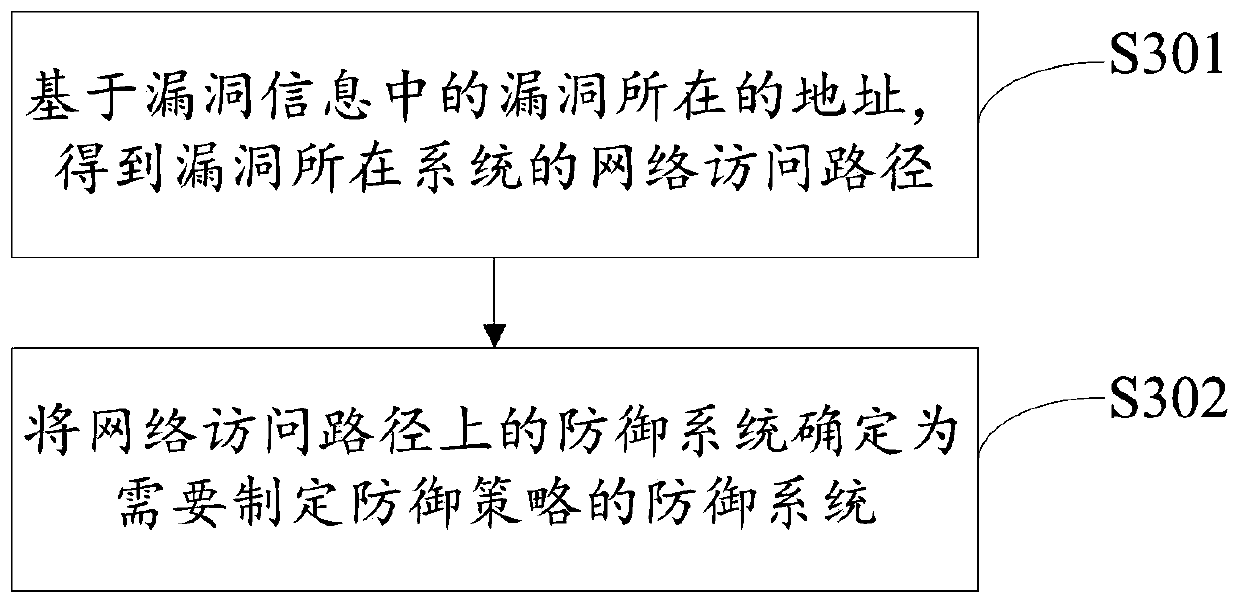
[0075] Optionally, in another embodiment of the present invention, an implementation manner of step S103 includes:
[0076] Obtain the CVE number of the vulnerability.
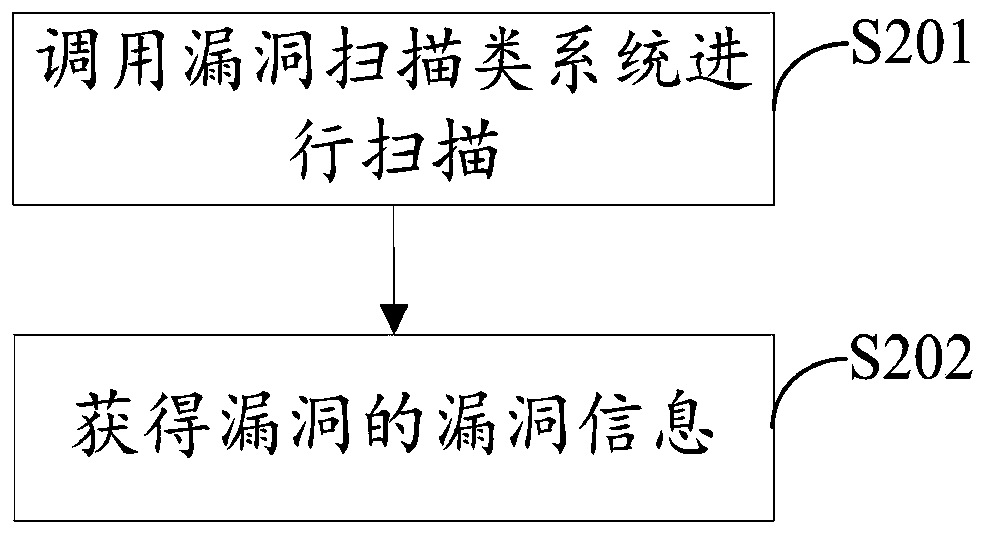
[0077] Specifically, after the vulnerability scanning system scans the vulnerability, the vulnerability information of the vulnerability is extracted to obtain the CVE number of the vulnerability, or the CVE number of the vulnerability can be obtained after the vulnerability scanning system scans the vulnerability.
[0078] Determine whether the CVE number of the defense system that needs to develop a defense strategy is the same as the CVE number of the vulnerability.
[0079] Among them, in each defense system, information such as the CVE number corresponding to the published public vulnerability and the corresponding defense strategy can be stored in advance. The defense strategy is used to defend against the vulnerability and can be used to block the vulnerability.
[0080] Specifically, if the CVE number...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com