A sip DDoS attack distributed defense system and its load balancing method
A load balancing algorithm and defense system technology, which is applied in the field of VoIP network security and IP communication, can solve the problems of increasing the processing burden of SIP proxy server, the defense system cannot be used for defense, server crashes, etc., and achieve good load balancing characteristics, high message Effect of processing power, high attack detection rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0063] The present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments.
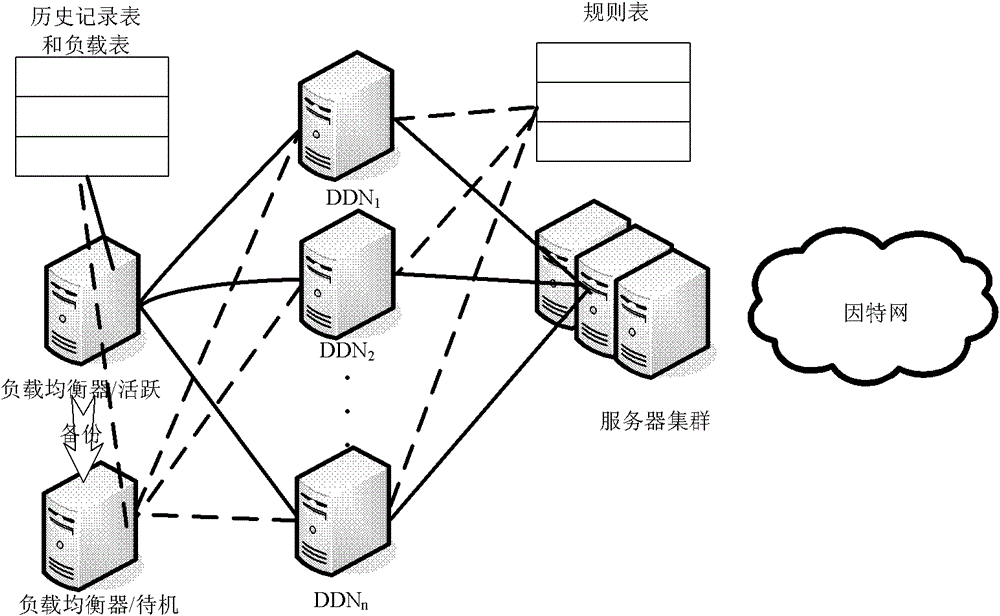
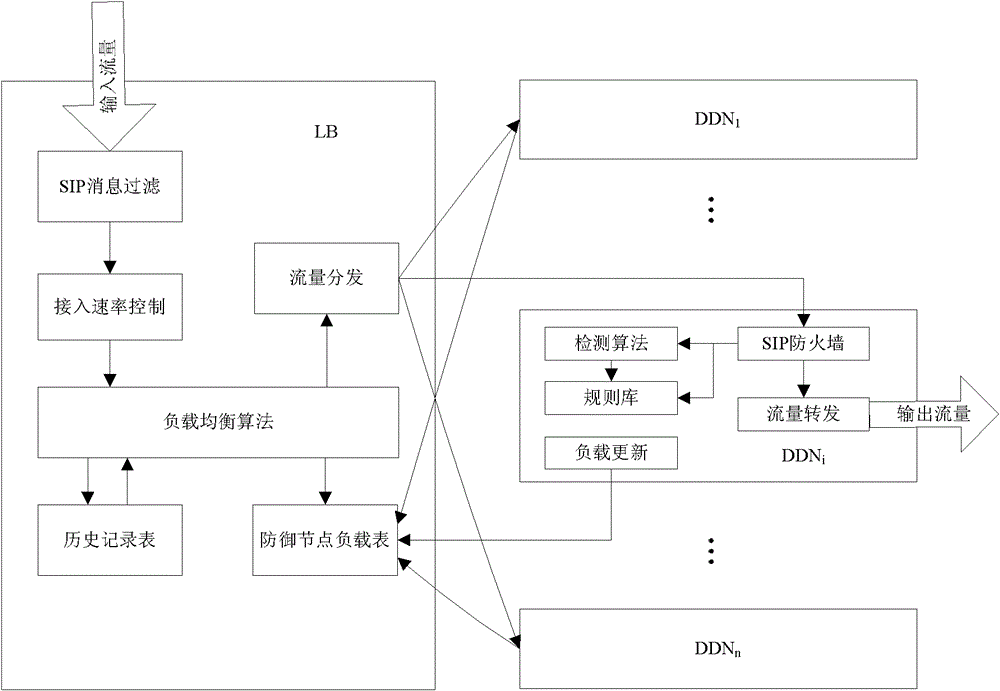
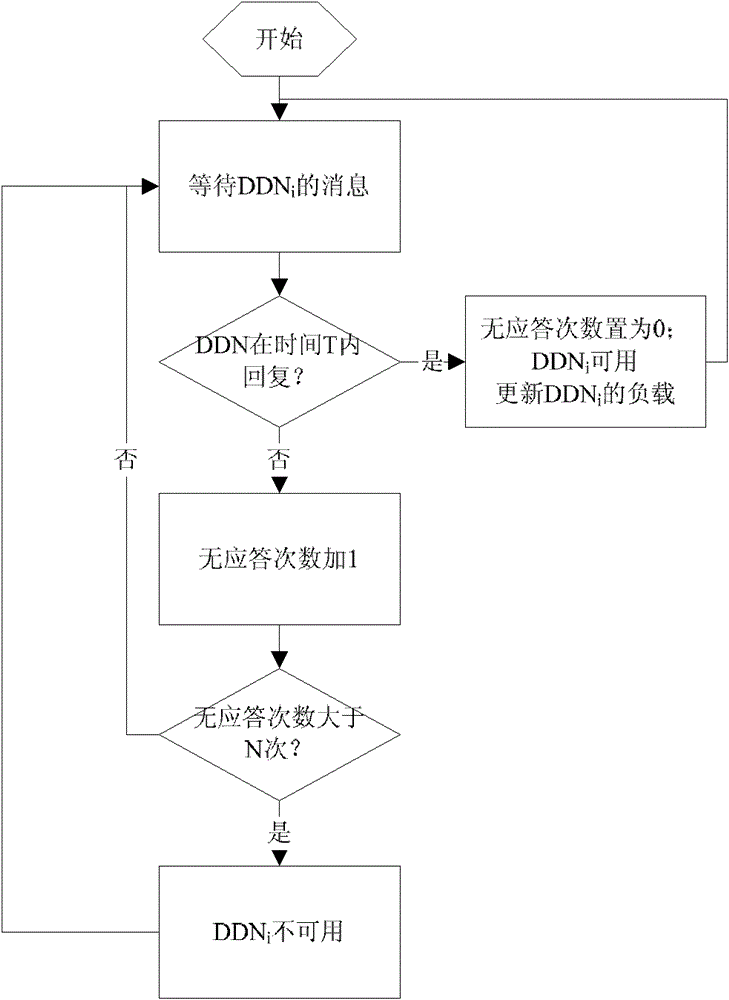
[0064] The SIP DDoS attack distributed defense system of the present invention comprises a load balancer (Load Balacer, LB), is connected with a plurality of defense detection nodes, carries out preliminary processing to network flow and uses load balancing algorithm to distribute to each defense detection node; Defense detection node ( Defending and Detecting Node, DDN), process the SIP messages assigned to it, filter out attack messages, and send normal messages to the server.
[0065] The system of the present invention is an intrusion prevention system for defending against SIP DDoS attacks. This embodiment runs on the front end of the SIP server cluster, processes SIP messages sent to the server, defends against SIP DDoS attacks, and protects the SIP server from the harm of the attack. Such as figure 1 The load balancer in the system sh...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com