Method and system for monitoring DDOS (distributed denial of service) attacks in small flow
A monitoring system and small flow technology, applied in transmission systems, digital transmission systems, electrical components, etc., can solve the problems of undetectable low-rate DDoS attacks, high implementation costs, low usability, etc., to prevent denial of service attacks , Make up for the high cost of deployment and improve the effect of security level
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
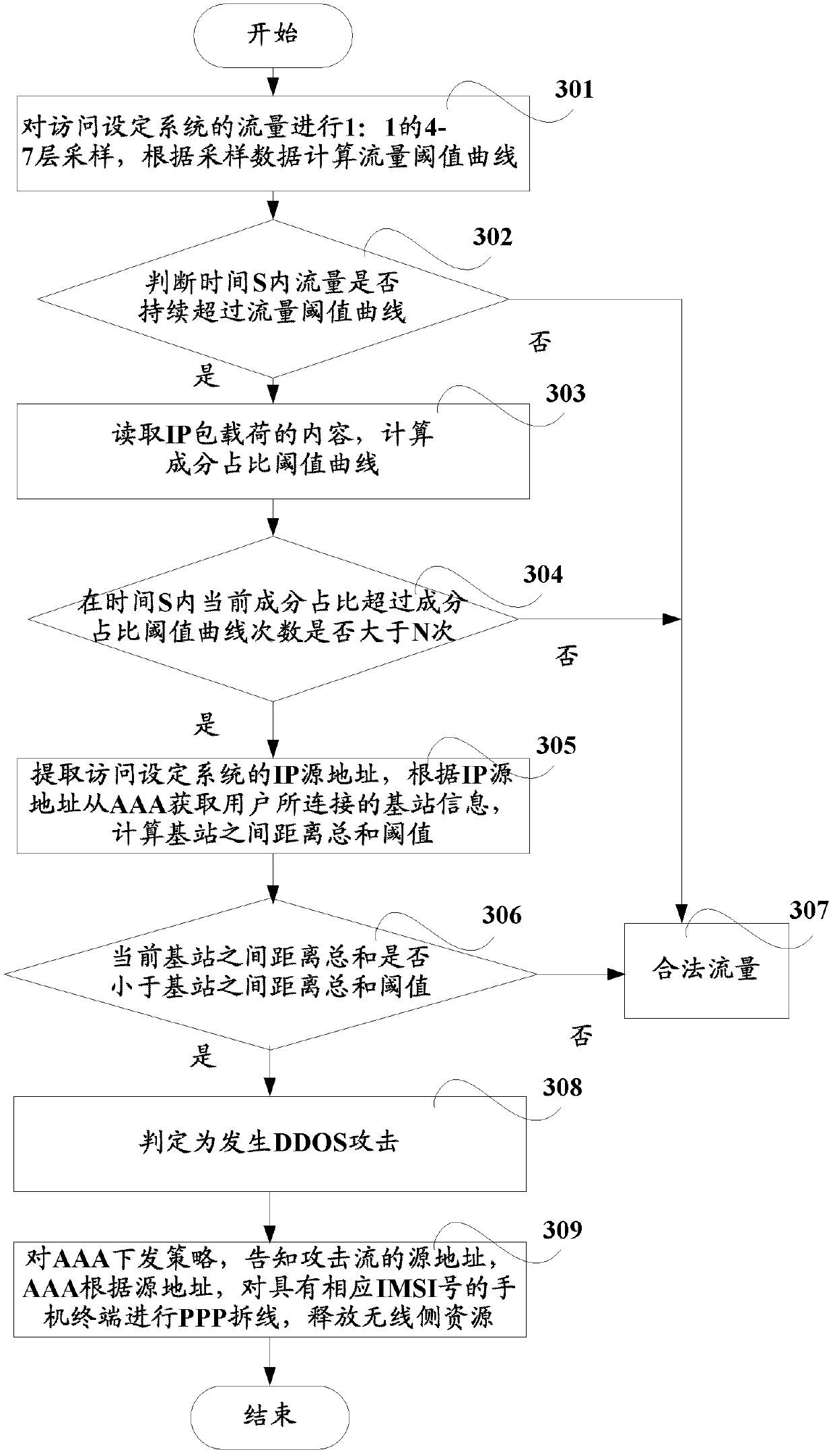
[0029] The present invention performs baseline analysis, component analysis, and traffic similarity analysis, and once a threshold alarm occurs after matching the above three models, it is determined that a DDOS attack has occurred. After a DDOS attack occurs, AAA can also perform PPP disconnection on the mobile terminal with the corresponding IMSI number according to the source address, so as to prevent the attack in a timely and effective manner and release the resources on the wireless side. A detailed description will be given below in conjunction with the accompanying drawings.
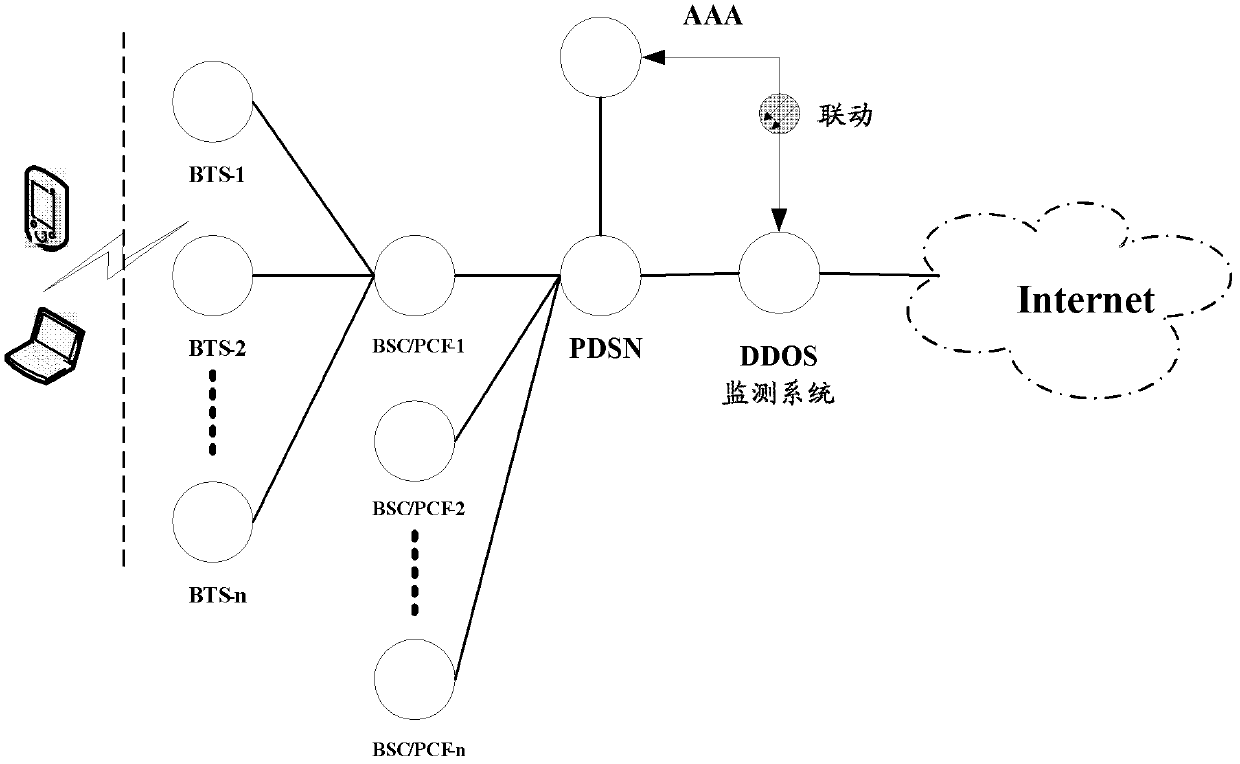
[0030] figure 1 It is a schematic structural diagram of a system for monitoring small traffic DDOS attacks in the present invention, and the DDOS monitoring system is deployed at the egress of a metropolitan area network.
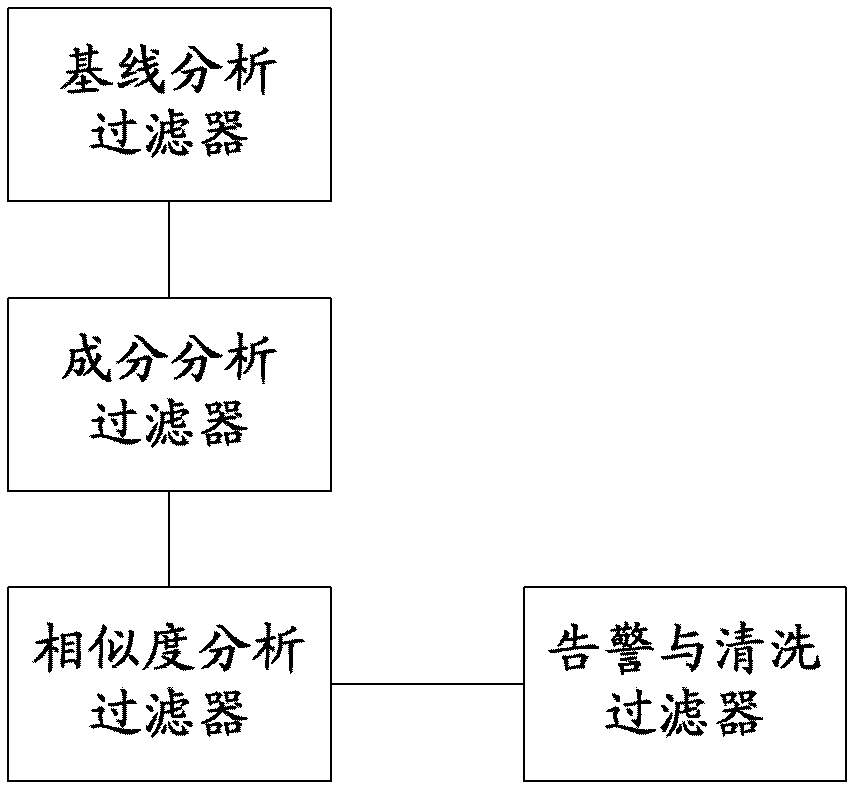
[0031] The specific structure of the system is as follows figure 2 Shown, including baseline analysis filter, component analysis filter and similarity analysis filter. in:...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com