Image recognition back door defense method and device based on swarm intelligence, and medium
A technology of image recognition and swarm intelligence, applied in the field of artificial intelligence, can solve problems such as limiting erasure efficiency, exploring and researching the efficiency of backdoor attack defense, and achieve the effect of improving defense efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
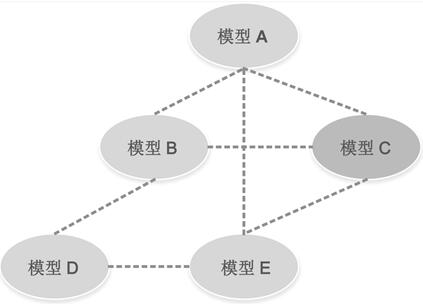
[0036] The invention sets the defense scene as a multi-model distributed cluster environment. Among them, due to the incremental training of multiple models, multiple image recognition models in a cluster are infected by poisoned data produced by malicious attackers. The object of the present invention is to erase the backdoor triggers of the models in the cluster when the distributed clusters of multi-neural network models are respectively implanted with different types of backdoor triggers, while maintaining the image data without the implanted backdoor triggers performance. The connection diagram between the neural network image recognition models of the distributed clusters of the present invention, such as figure 1 shown.
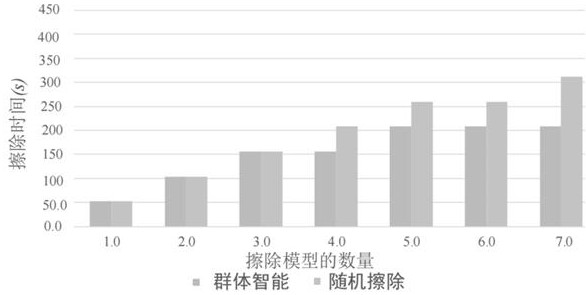
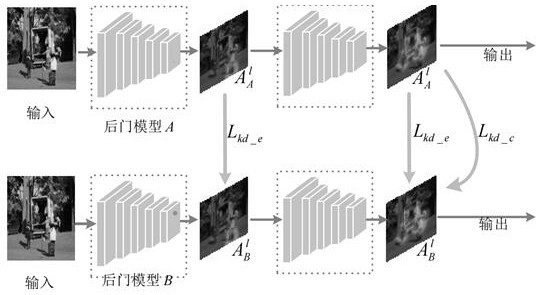
[0037] The invention proposes a swarm intelligence algorithm and a neural distillation strategy to improve the erasure accuracy and efficiency of multiple neural network models in a distributed cluster for backdoor attacks.
[0038] Considering tha...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com