Warning association method and device
An attacker and behavior technology, applied in the field of data security, can solve problems such as being unfavorable to discover the attacker's attack intention
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0076] In order to make the technical problems, technical solutions and advantages to be solved by the present invention clearer, the following will describe in detail with reference to specific embodiments and accompanying drawings.
[0077] The embodiment of the present invention provides an alarm association method and device, which solves the problem that WAF alarms only focus on a single attack behavior, and cannot combine multiple scattered but logically related fine-grained attack behaviors into a coarse-grained attack process, thereby It is not conducive to discovering the real attack intention of the attacker.
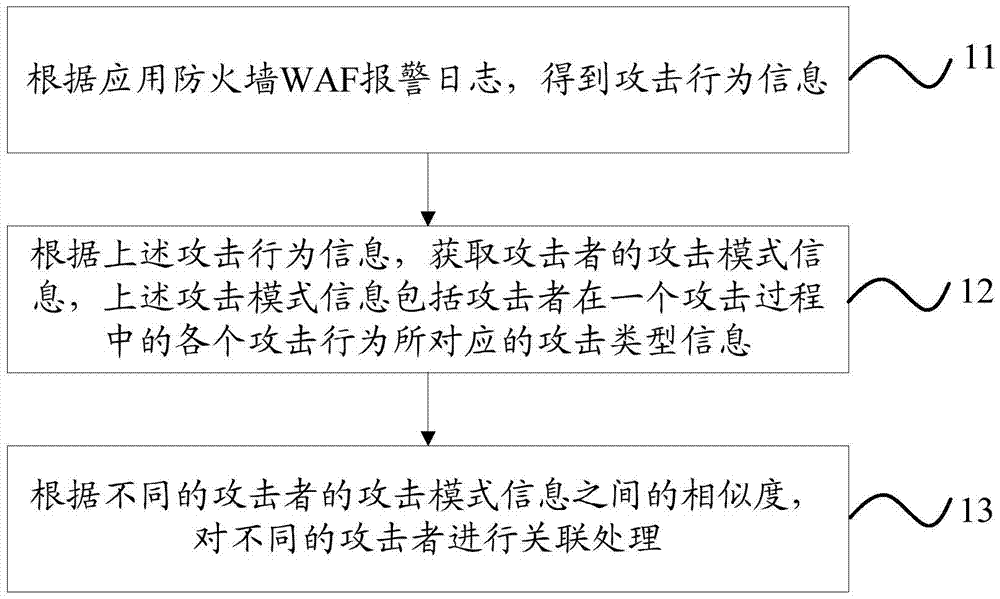
[0078] Such as figure 1 As shown, the alarm correlation method in the embodiment of the present invention includes:
[0079] Step 11: According to the application firewall WAF alarm log, get the attack behavior information.
[0080] Here, the attack behavior information may specifically include: domain name information of the attacked, attack time informatio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com