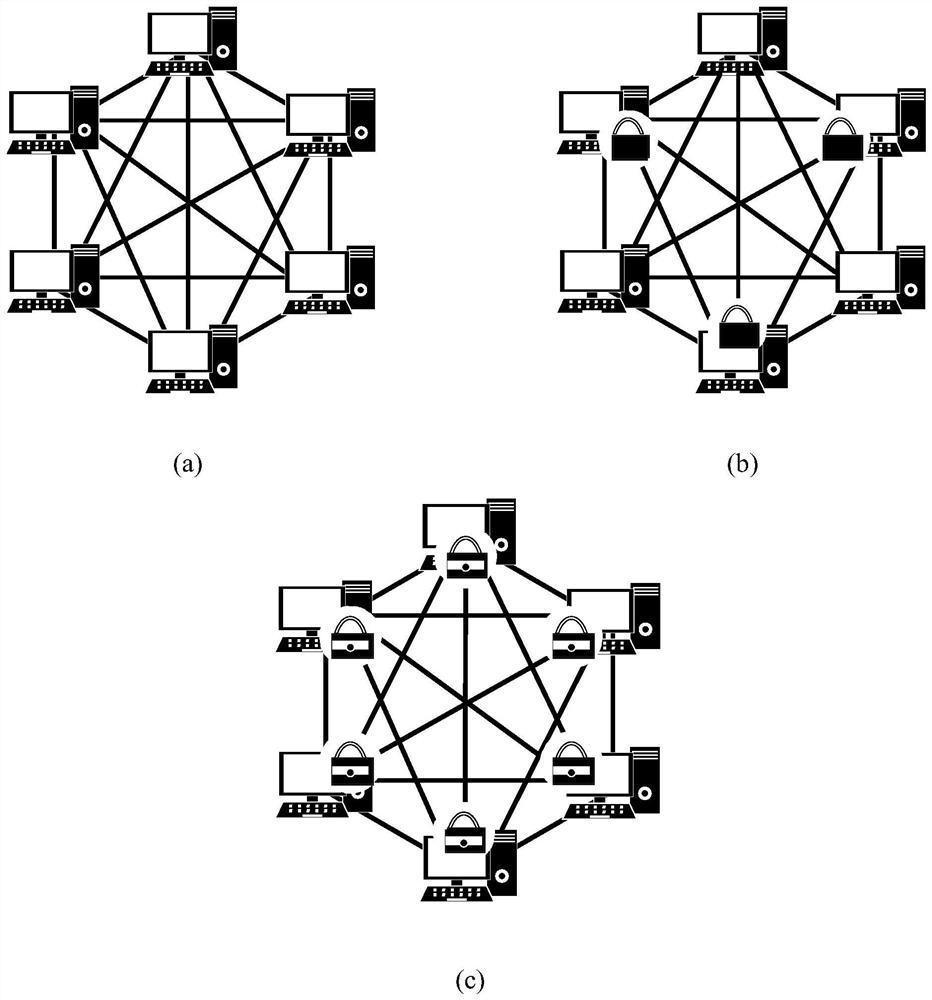
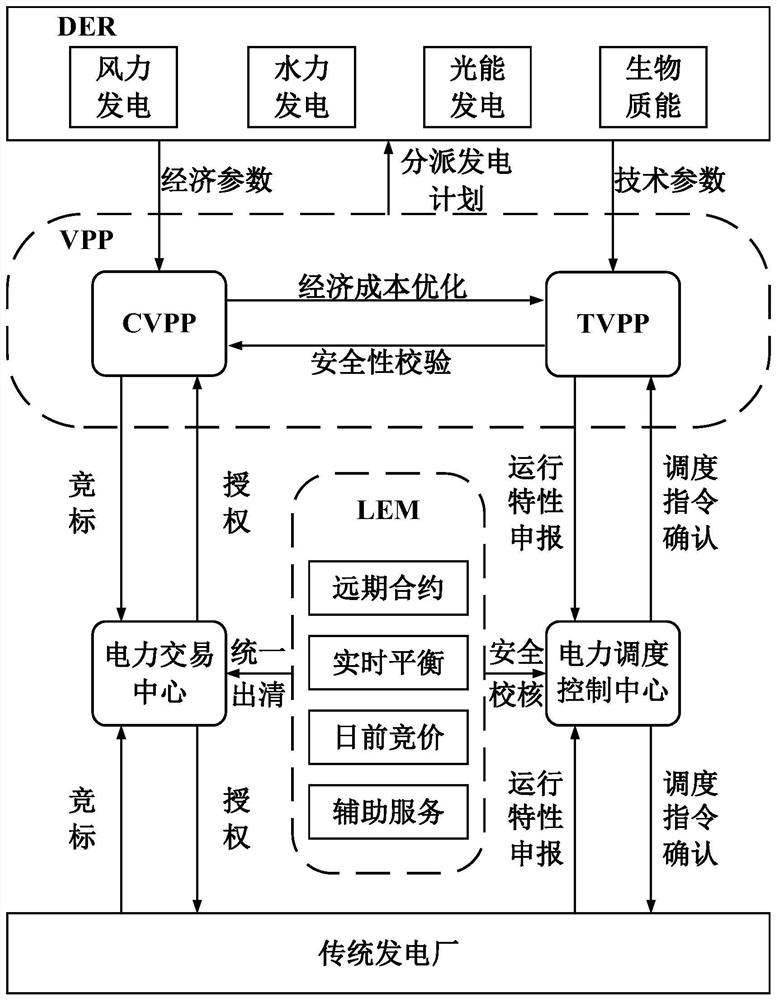
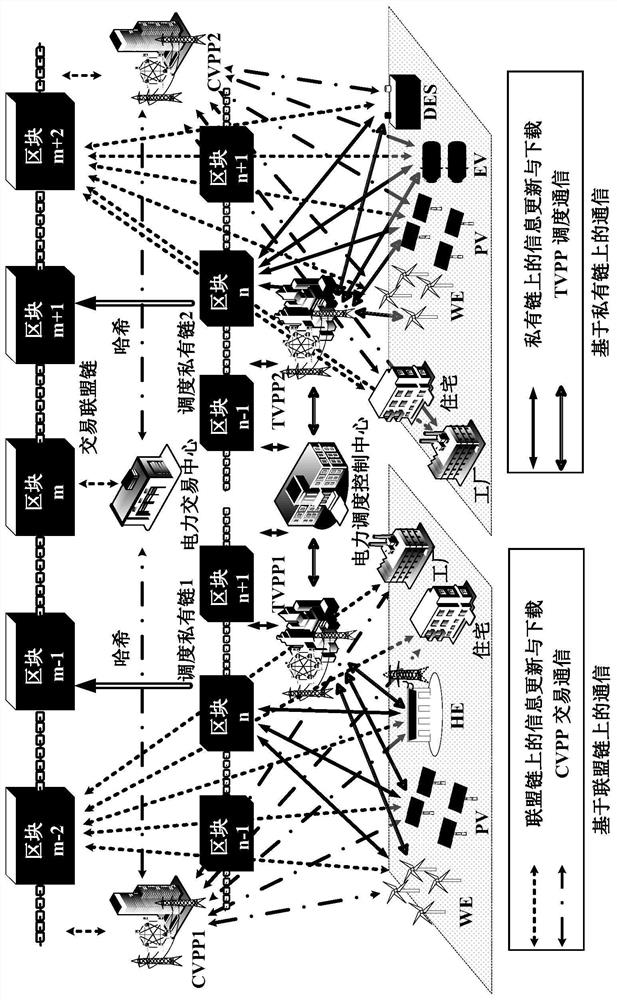
Virtual power plant security scheduling and trading method based on dual blockchain technology
A virtual power plant and transaction method technology, applied in the field of identity-based encryption and proxy re-encryption technology, can solve the problems of less use and analysis of blockchain technology, failure to highlight the functions of blockchain technology, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0131] Embodiment 1: The power generation unit sends production-related information to the virtual power plant for safe scheduling. which is Image 6 The corresponding steps are as follows:
[0132] (1) System settings:
[0133] The verification authority executes the algorithm. Enter system security parameters and the system property set U, and then construct two multiplicative cyclic groups G and G of order p T , p is a prime number. g, g 1 , g 2 , g 3 Both are generators of G, and G and G T Satisfy the bilinear mapping relationship e:G×G→G T . random selection of elements And define three hash functions H 1 :(0,1) * →G,H 2 :G T →G,H 3 : Finally, output system public parameters GP and master key MSK.
[0134] GP=(p,g,g 1 , g 2 , g 3 ,e(g,g) α ,H 1 ,H 2 ,H 3 ), MSK=α (1)
[0135] It should be noted that the system public parameters and master key of IBE have been included in Equation 1, and the specific IBE system public parameters GP IBE and m...
Embodiment 2
[0179] Embodiment 2: The specific realization process of virtual power plant acquiring transaction information and implementing auction. which is Figure 7 The corresponding steps are as follows:
[0180] There are three entities involved in the reputation-based CDA mechanism: buyers, sellers, and auctioneers. In the present invention, power consumption units such as residences and factories represent buyers, power generation units such as photovoltaic power plants and hydroelectric power plants represent sellers, and CVPP assumes the responsibility of auctioneers. At the beginning of the transaction cycle, the power consumption unit and the power generation unit submit the initial and Indicates the transaction information submitted by power unit i for the first time in the kth transaction cycle. Similarly, Indicates the transaction information submitted by power generation unit j for the first time in the kth transaction cycle. The specific content contained in the two...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com