Electronic document safe sharing system and method thereof
An electronic file and sharing system technology, applied in the field of information security, to achieve the effect of high efficiency, authenticity, flexible and convenient use
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
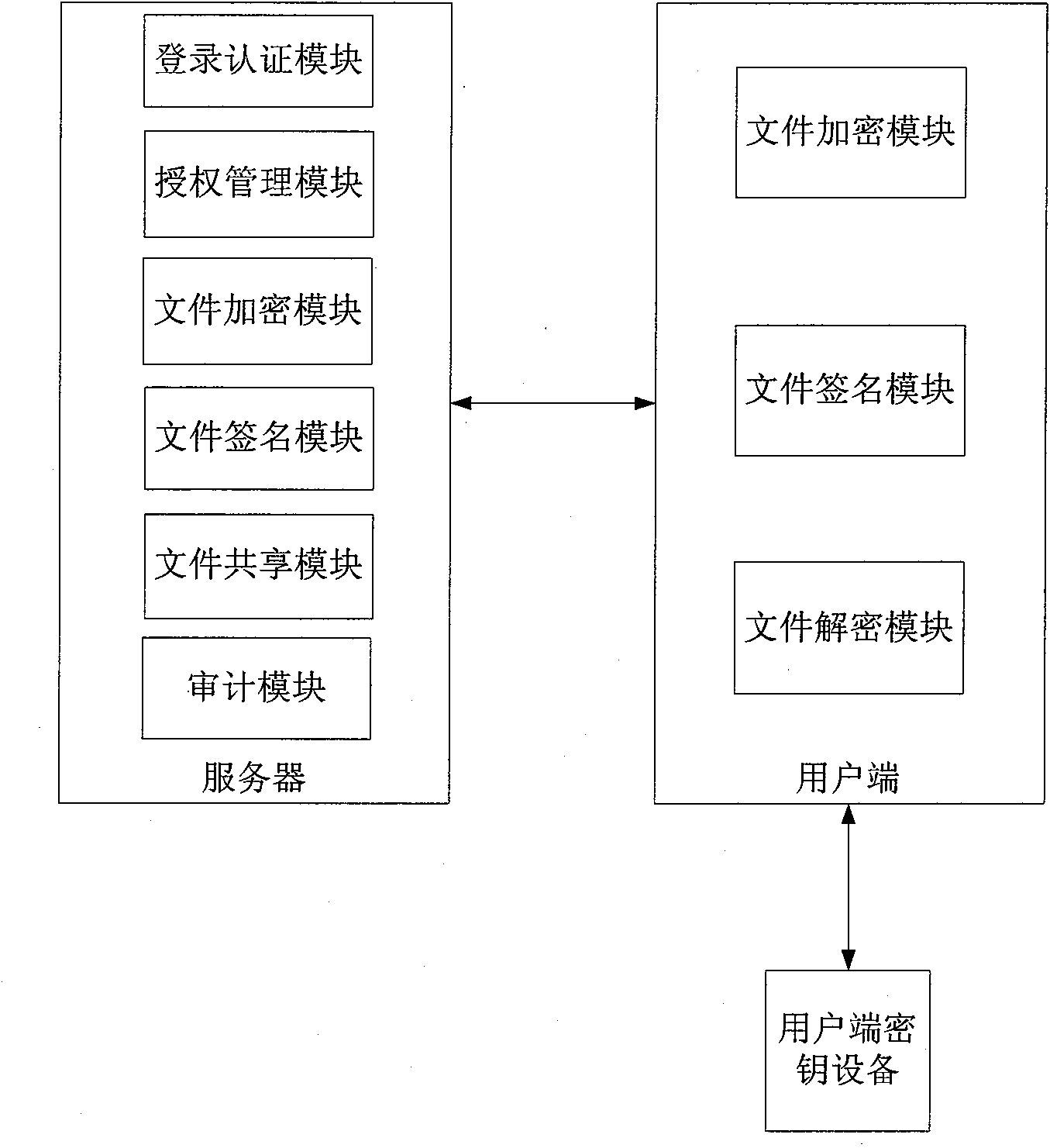
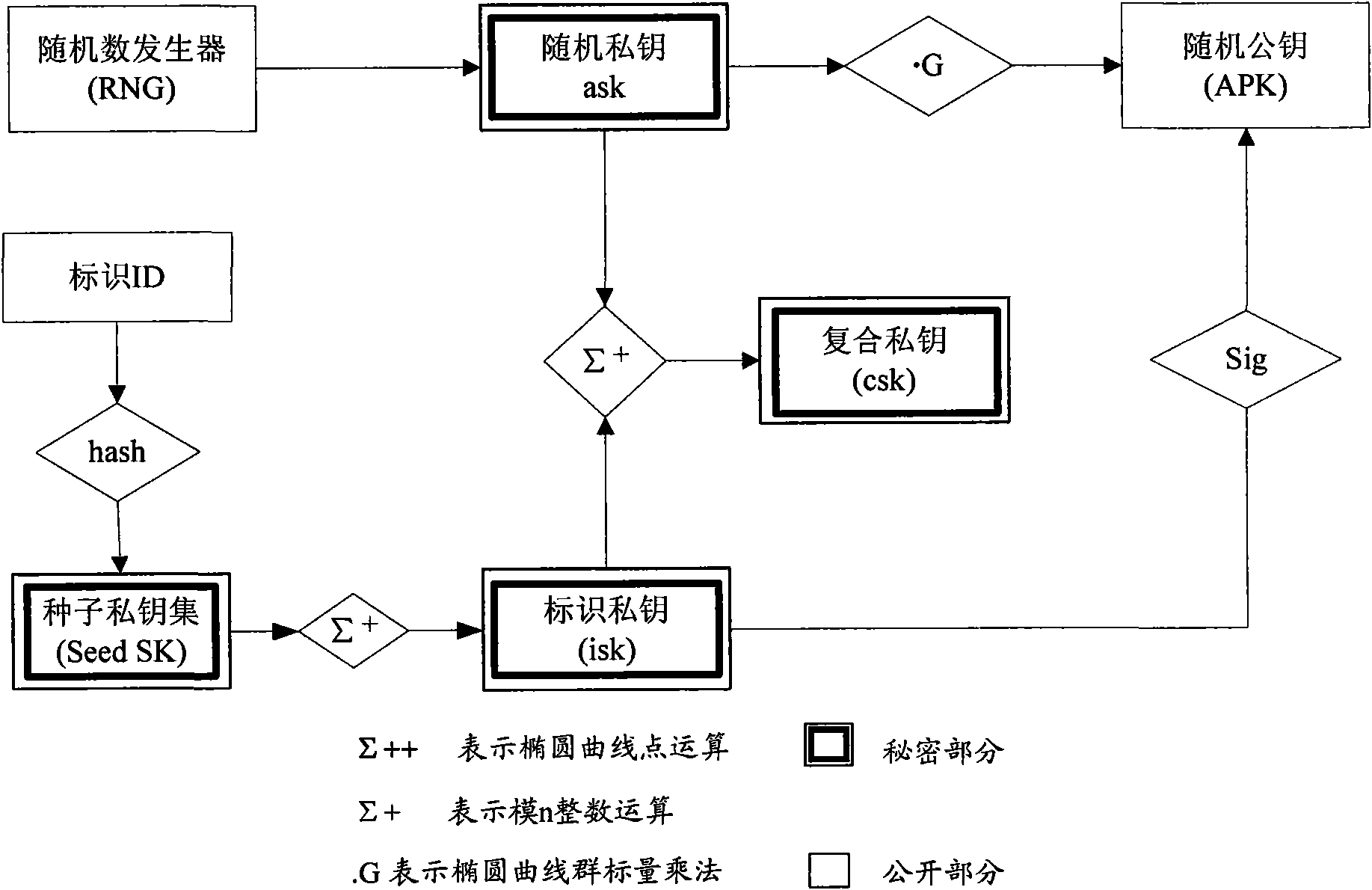
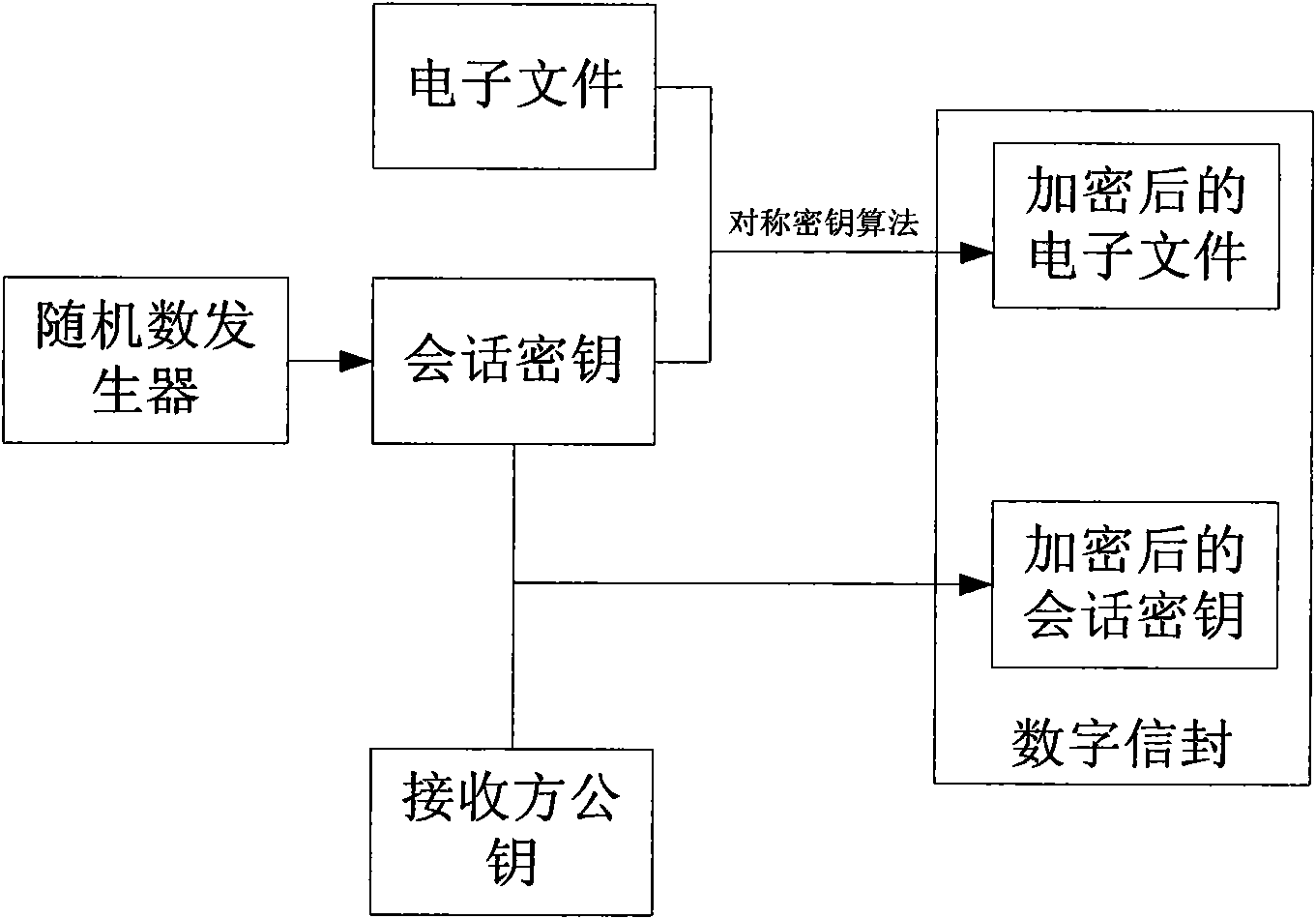
[0046] Combined Public Key Algorithm (Combined Pubic Key, CPK) is an identity-based public key algorithm, and its key management center generates corresponding private key calculation parameters (private key calculation base) and public key calculation parameters (public key calculation base); According to the identification provided by the first user, use the private key calculation parameters to calculate the private key of the first user, and provide the generated private key to the first user; and publish the public key calculation parameters so that the second user After the identification of the first user is obtained, the public key of the first user may be calculated by using the public key calculation parameters according to the identification of the first user.
[0047] On the basis of proposing the CPK algorithm, a CPK chip is also provided. The CPK chip has a CPK algorithm functional unit and a verification protocol unit, which are specifically implemented in the ap...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com