Remote identity authentication method and system and remote account opening method and system
An identity authentication and ID card technology, applied in user identity/authority verification, transmission system, digital data authentication, etc., can solve problems such as user inconvenience, and achieve the effect of improving user experience and convenience for users
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
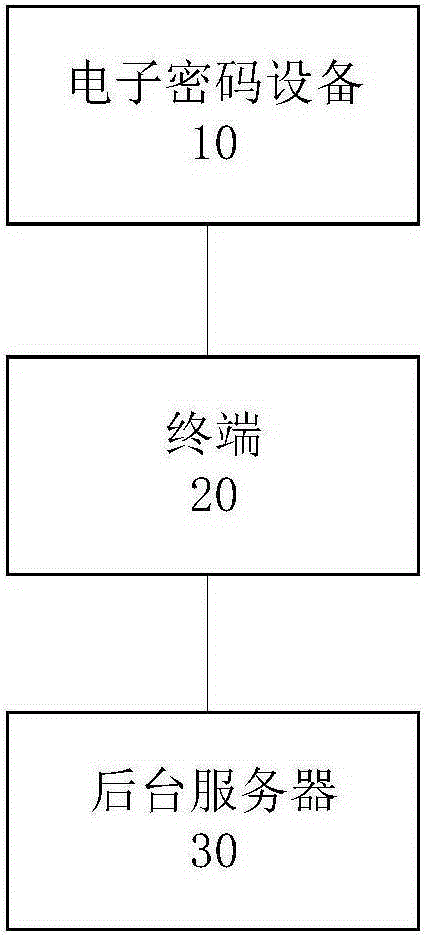
[0058] figure 1 A schematic diagram of the architecture of the remote identity authentication system is provided for this embodiment, such as figure 1 As shown, the system mainly includes: an electronic encryption device 10 , a terminal 20 and a background server 30 .
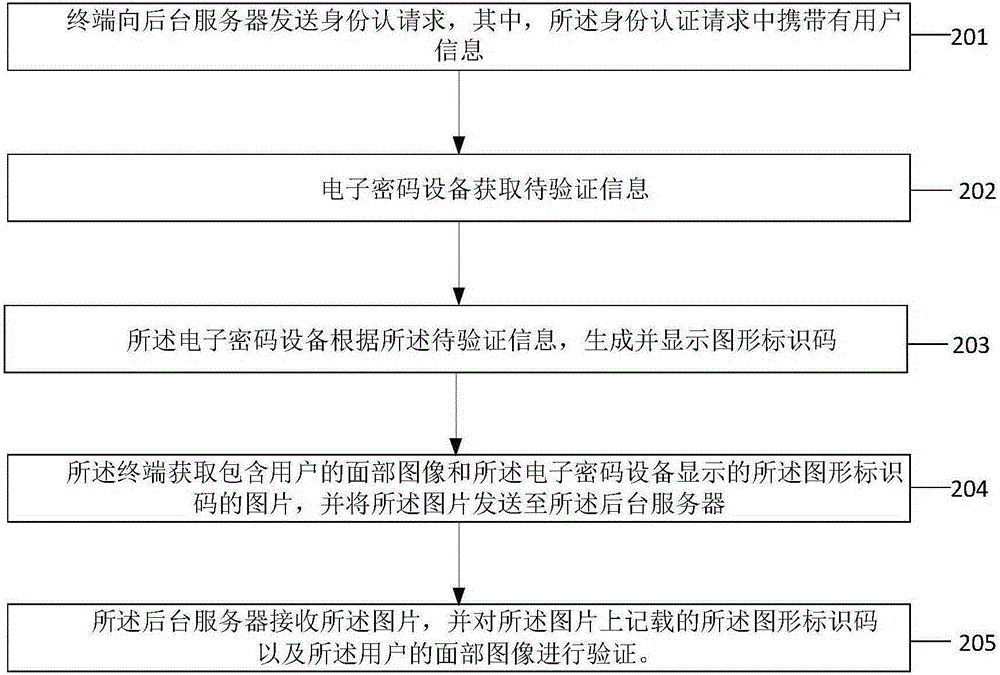
[0059] In this embodiment, the terminal 20 first sends an identity authentication request to the background server 30, and then the electronic cryptographic device 10 obtains the information to be verified, and generates and displays a graphic identification code according to the information to be verified. The user takes a photo with the electronic cryptographic device 10, and the terminal 20 acquires a picture including the user's facial image and the graphic identification code displayed by the electronic encryption device 10, and sends the picture to the background server 30 for verification.
[0060] Therefore, in this embodiment, the terminal 20 is configured to send an identity authentication request to...
Embodiment 2
[0107] figure 1 Provide a schematic structural diagram of a remote identity authentication system for the present invention, figure 1 The system embodiment shown includes: an electronic encryption device 10 , a terminal 20 and a background server 30 .
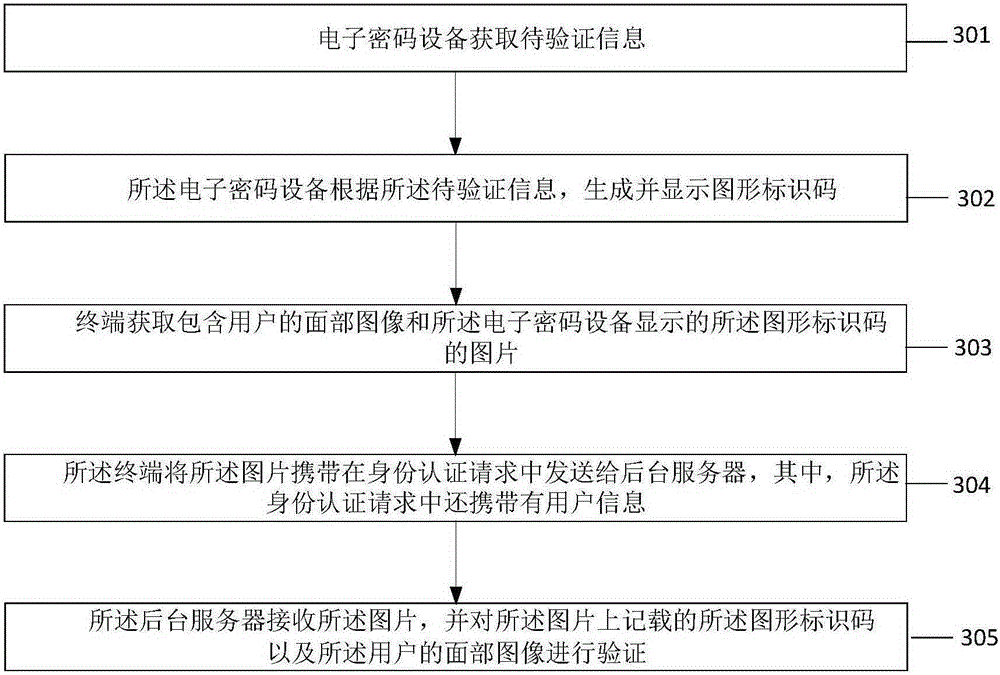
[0108] In this embodiment, the electronic encryption device 10 obtains the information to be verified, and generates and displays a graphic identification code according to the information to be verified. The user takes a photo with the electronic encryption device 10, and the terminal 20 obtains the facial image containing the user and the electronic encryption device 10 displays The picture of the graphic identification code is carried in the identity authentication request and sent to the background server 30 for verification.
[0109] The difference from Embodiment 1 is that in this embodiment, before the terminal 20 sends an identity authentication request to the background server 30, the electronic encryption device 10 g...
Embodiment 3
[0124] This embodiment provides a remote account opening system. The remote identity authentication system in Embodiment 1 or Embodiment 2 above is used to authenticate the user's identity. After the user's identity authentication is passed, the background server 30 performs remote account opening. It can enable users to remotely open accounts anytime and anywhere, which is convenient for users and improves user experience.
[0125] It should be noted that after the identity authentication is passed, the background server 30 may automatically open an account remotely, or the staff may control the background server 30 to open an account remotely.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com