Offline physical isolation authentication method and authentication system thereof
An authentication method and physical isolation technology, applied in the field of offline physical isolation authentication methods and authentication systems, can solve problems such as being hacked, and achieve the effects of convenient use, good promotion, and security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
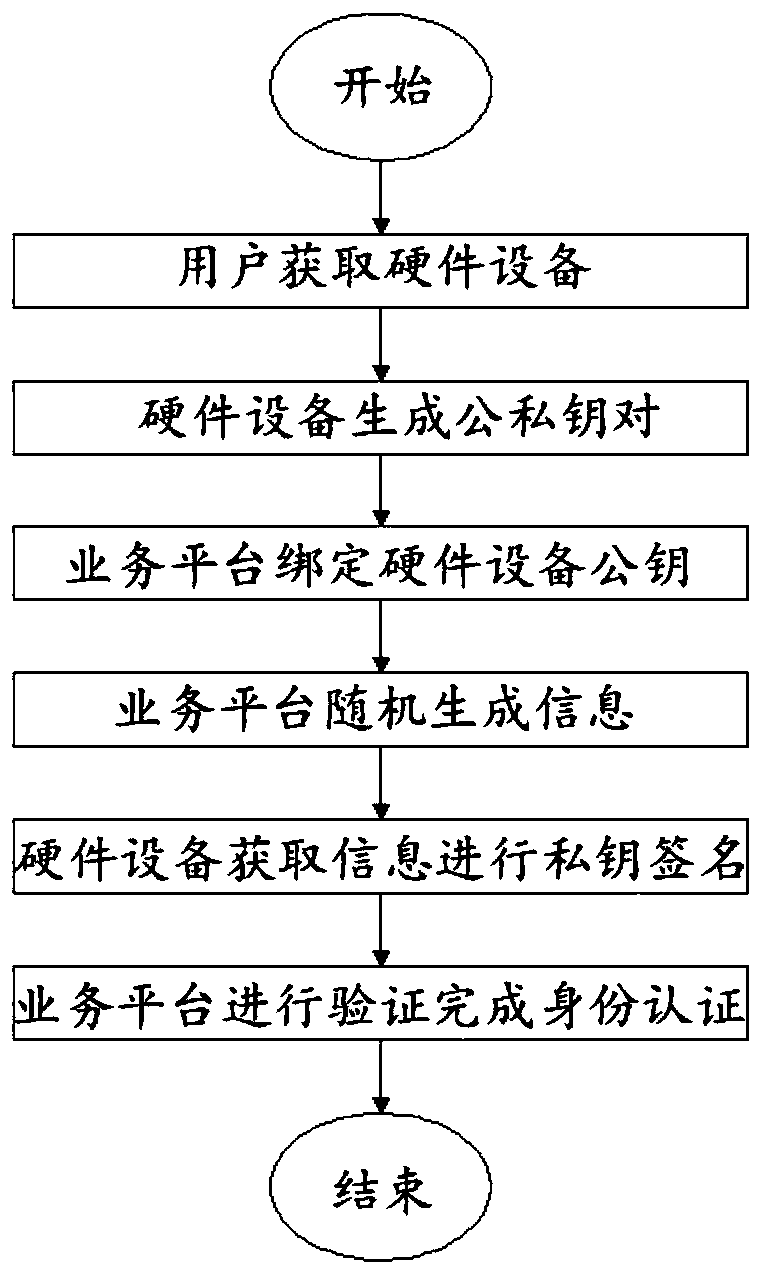
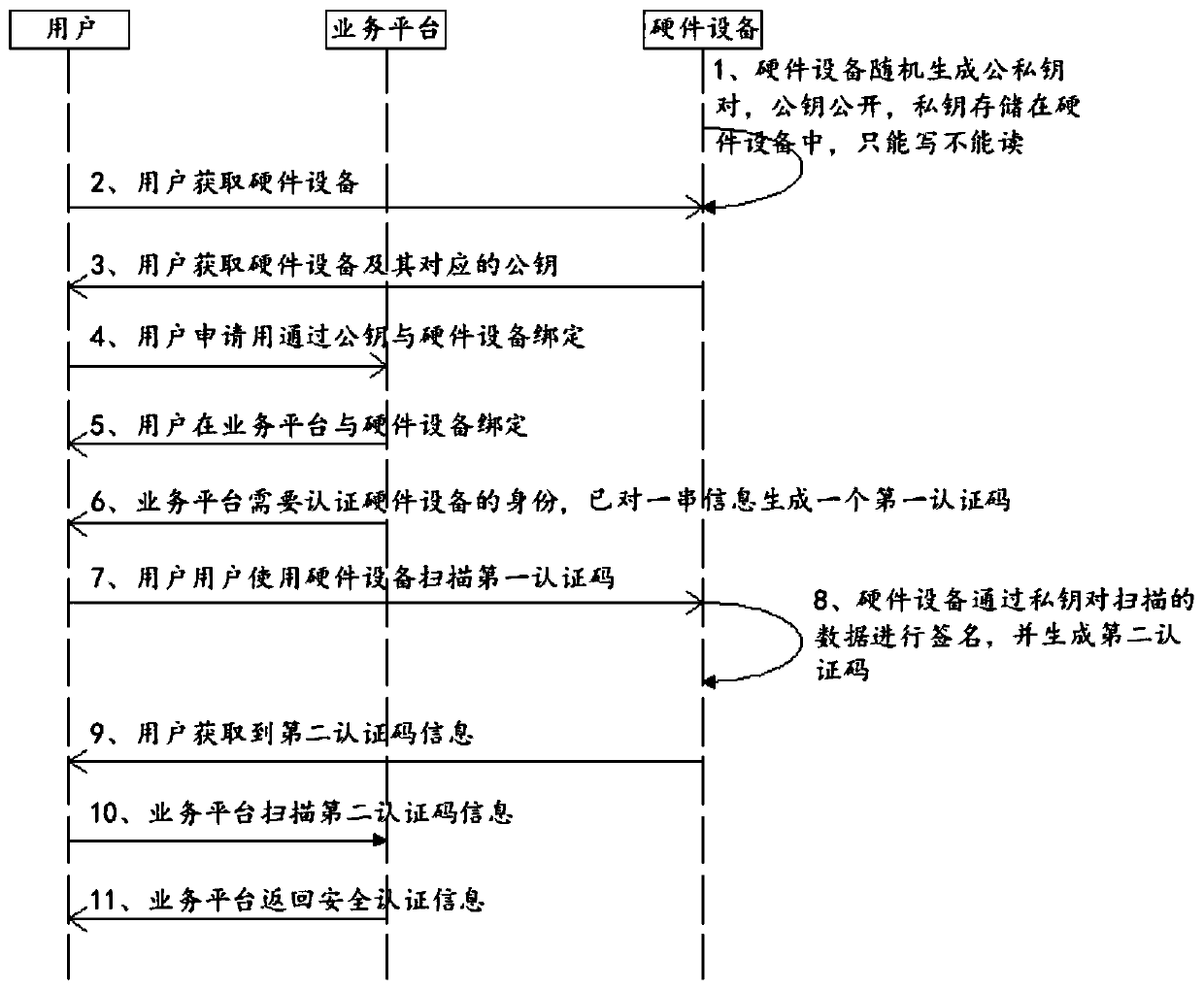
[0026] Such as figure 1 As shown, this embodiment provides an authentication method for offline physical isolation based on digital certificate KPI, including hardware devices and business platforms. The hardware devices can recognize two-dimensional codes and display information, and have certain storage capabilities and computing capabilities. Contains the key generation algorithm. Through the key generation algorithm, a pair of public and private key pairs are generated. The private key is stored in the hardware device as a write-only, and the public key is displayed on the hardware device. After purchasing or obtaining this hardware device, the user can generate a public-private key pair by himself, or use the previous public-private key pair. When identity authentication with the business platform is required, the user's information and the public key corresponding to the hardware device are first bound on the business platform, that is, the public key can represent the u...
Embodiment 2
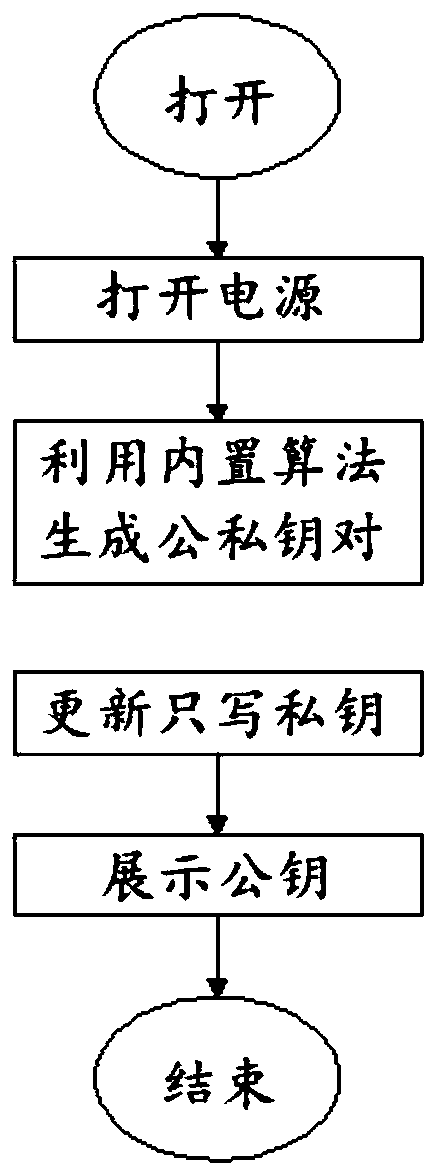
[0045] Such as Figure 5 As shown, this embodiment is an authentication system that implements the offline physical isolation authentication method of Embodiment 1, specifically including hardware devices and business platforms, and the authentication system also includes:
[0046] A processor, a memory, a display screen and a first camera on the hardware device side, wherein the processor is used to generate a public key and a private key, the memory is used to store the private key, and the display screen is used to display the The public key and the second authentication code signed by the private key, the first camera is used to scan the first authentication code; specifically, it also includes a portable battery and a device switch for switching the device;
[0047]The second camera on the service platform side is used to scan the second authentication code signed by the private key.
[0048] When the user needs to be authenticated, turn on the power of the hardware devi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com