System and method for user authentification using non-language words
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
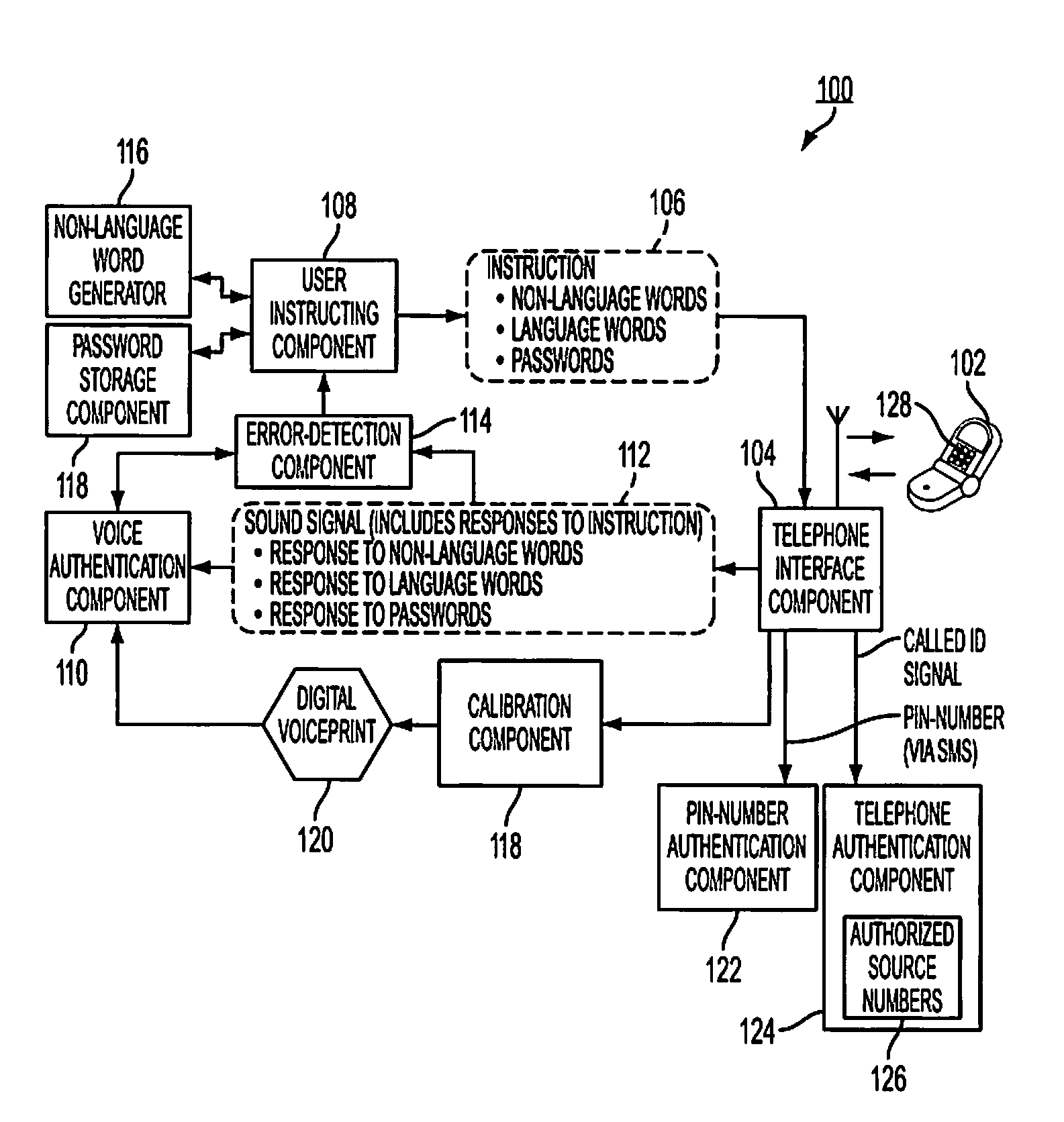
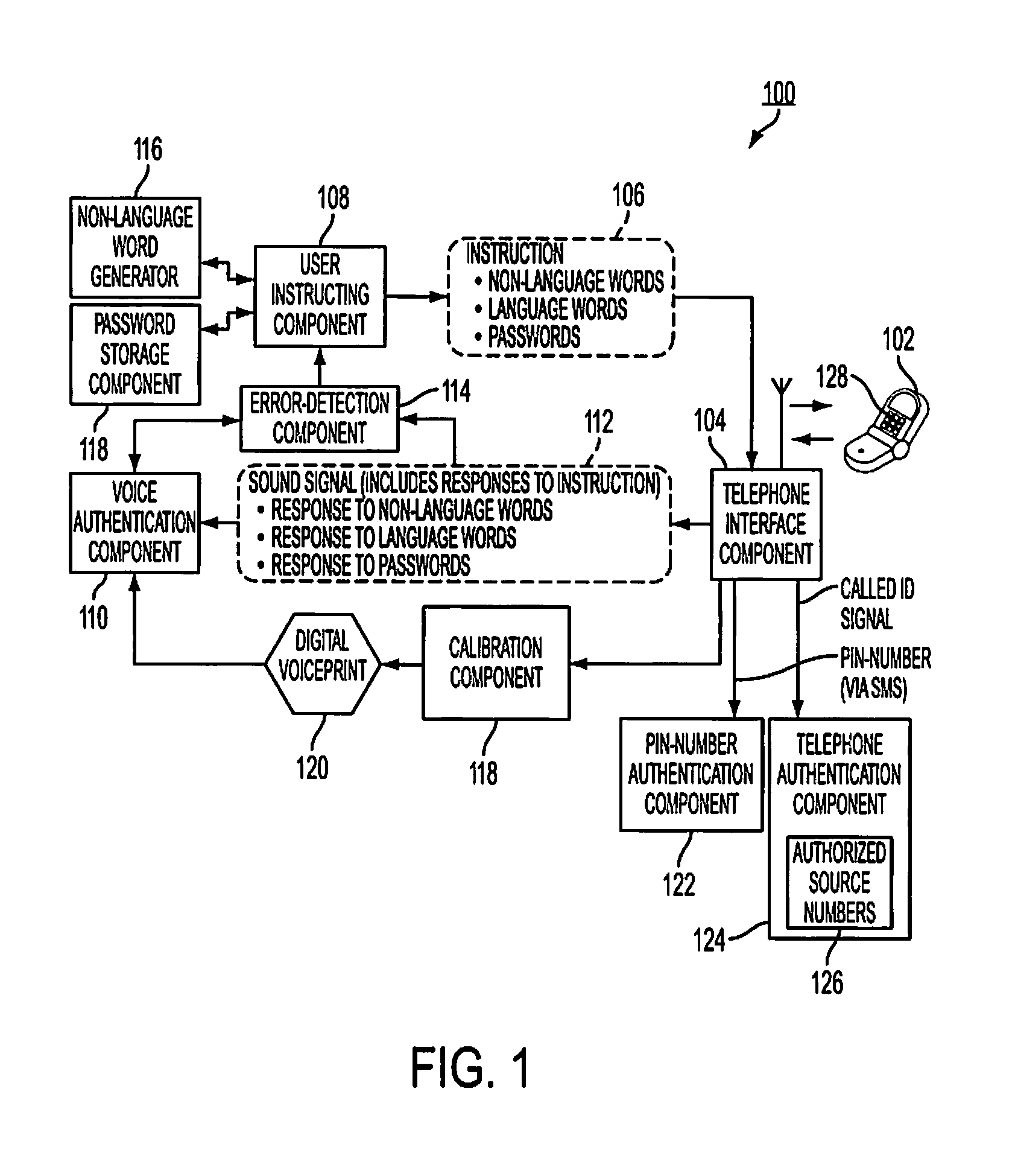
[0026]Referring to the drawings, FIG. 1 is a block diagram of a system 100 for user authentication using non-language words in accordance with the present disclosure. System 100 may be implemented, wholly or partially, in hardware, software, software in execution, firmware, microcode, CPLDs, PALs, FPLGs, hardware description language, bytecode, a virtual machine, emulation, on one or more processors and the like. For example, system 100 may be implemented by one or more x86-processor based computers (not shown).
[0027]System 100 can authenticate a user (not shown) using a user's voice. Specifically, system 100 can authenticate a user's voice using cell phone 102. A person's voice is somewhat specific to that person in the same way a fingerprint or a person's iris is specific to a person. This quality makes a person's voice well suited for authentication. Cell phone 102 operatively communicates with telephone interface component 104. Cell phone 102 may be considered part of or separat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com