Suspicious threat index active validation method and system based on source-opening information
A verification method and technology of indicators, applied in the field of active verification of suspicious threat indicators, can solve the problems of inability to monitor open intelligence sources, incomplete open intelligence sources, and high cost, and avoid problems with low intelligence coverage, easy implementation, and low cost. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] The present invention will be described in further detail below through specific embodiments and accompanying drawings.
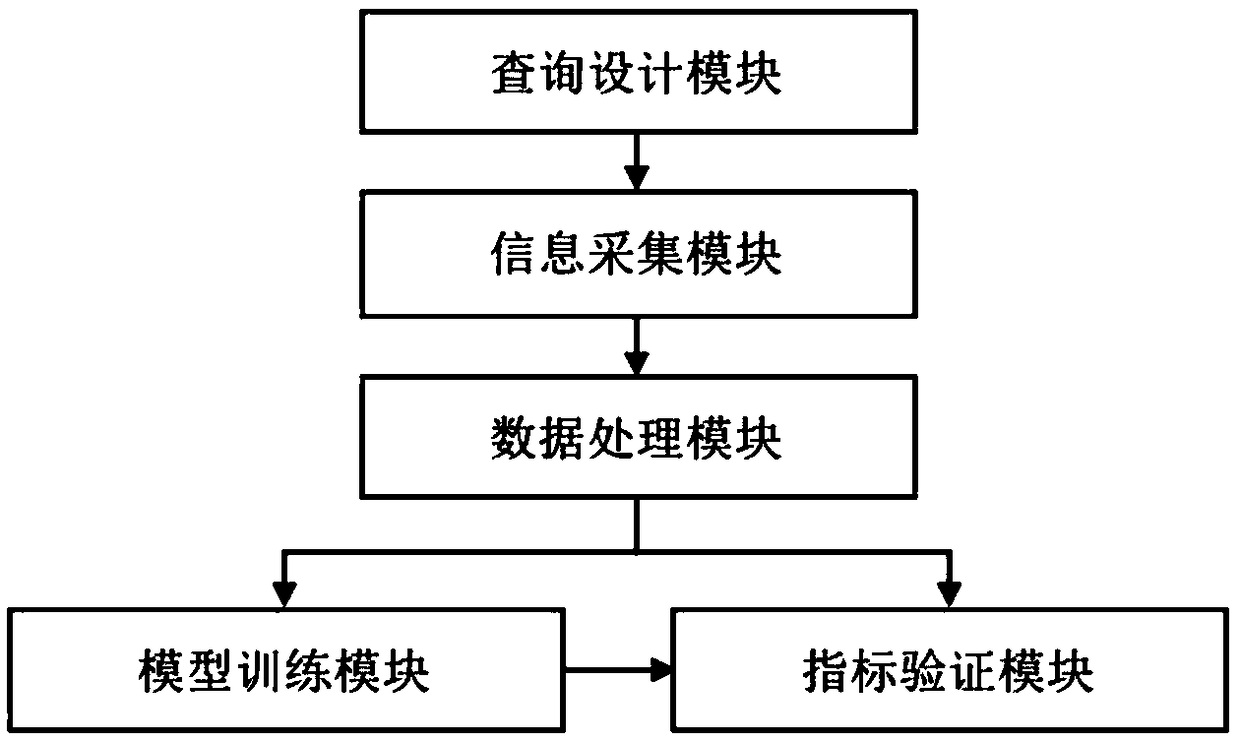
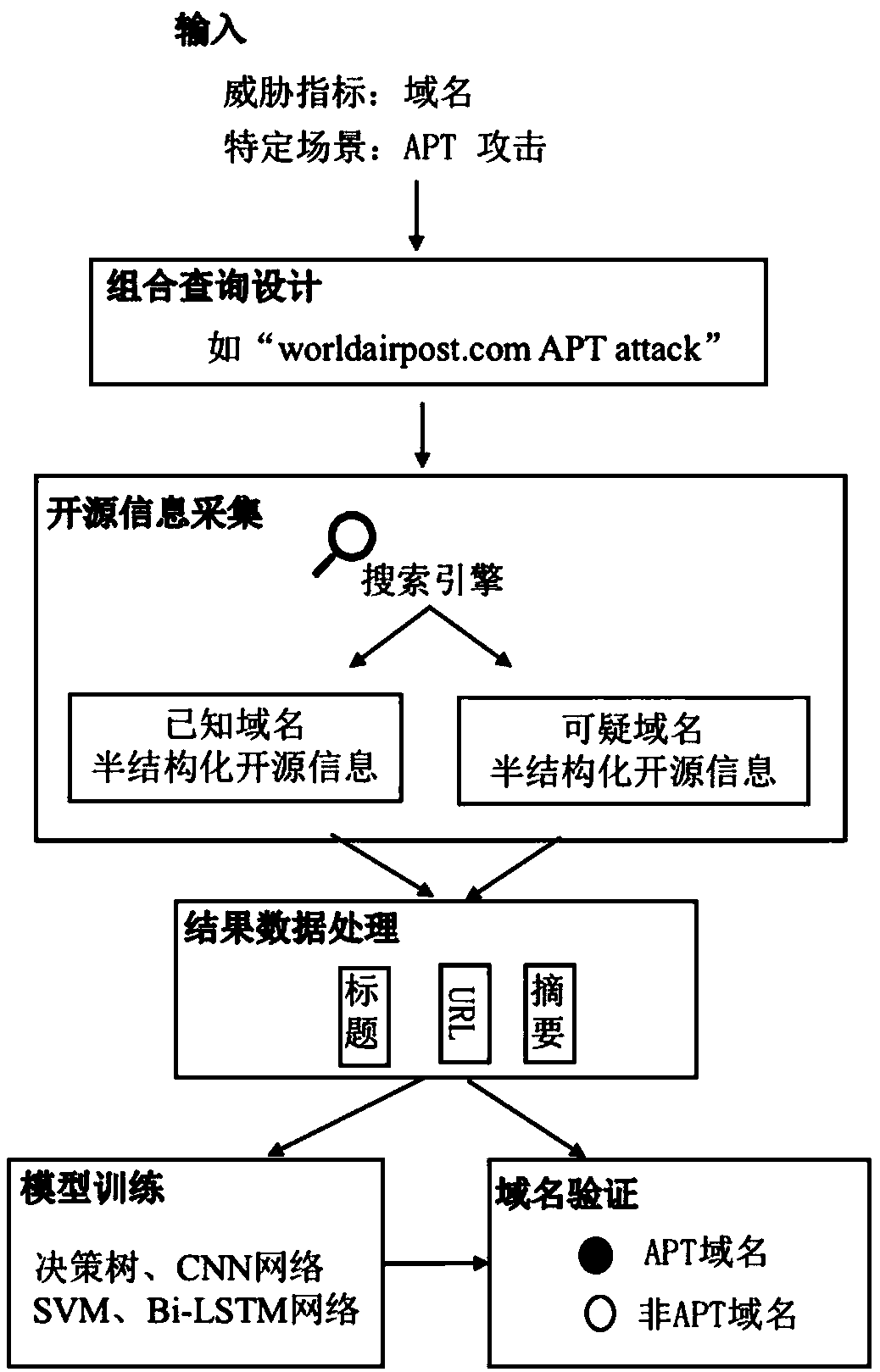
[0039] This embodiment provides an active verification system for suspicious threat indicators based on open source information, such as figure 1 As shown, it includes: query design module, information collection module, data processing module, model training module, and index verification module.
[0040] The query design module is used to design a specific query statement to complete the query combination of suspicious threat indicators and specific scenarios, so as to quickly locate all public information related to suspicious threat indicators on the Internet;
[0041] The information collection module is used to collect and crawl the result information retrieved on the Internet according to specific query statements, so as to provide knowledge basis for the later verification of suspicious threat indicators.
[0042] The data processing module ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com