System and realization method for trusted authentication of user login in operating system
A technology of operating system and implementation method, which is applied in the field of computer security, can solve problems such as insecurity, and achieve the effects of secure two-way authentication, reasonable design, and convenient use
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
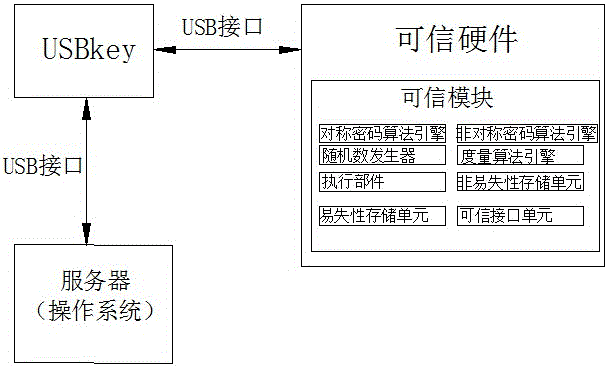
[0035] as attached figure 1 As shown, the operating system user login trusted authentication system of the present invention, its structure includes USBkey and trusted hardware, the USBkey is connected to the trusted hardware through the USB interface, and the USBkey is used to connect to the server through the USB interface to complete the two-way communication between the operating system and the user Authentication; trusted hardware is used to store user identity information and private information related to keys. The trusted hardware includes a trusted module, and the trusted module includes a symmetric cryptographic algorithm engine, an asymmetric cryptographic algorithm engine, a random number generator, a measurement algorithm engine, an execution unit, a non-volatile storage unit, a volatile storage unit, and a trusted interface unit.
Embodiment 2
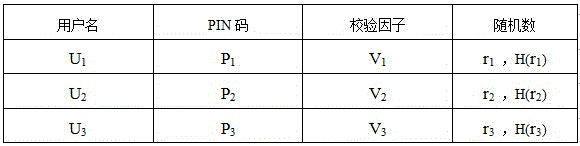
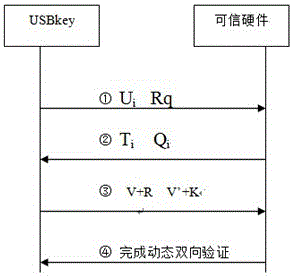
[0037] as attached figure 2 and 3 As shown, the implementation method of the operating system user login trusted authentication of the present invention, the implementation method is to store the user's identity information and related key information in the trusted hardware, the trusted hardware is connected to the USB key through the USB interface, and the USB key is connected to the USB key through the USB interface. The interface is plugged into the server, and the dynamic password technology is used to realize the two-way authentication between the user and the operating system.
[0038] The process of two-way authentication between the user and the operating system includes the following steps:
[0039](1) When the user logs in to the server operating system, plug the USB key into the server through the USB interface;
[0040] (2) The user enters the PIN code to start the two-way authentication process between the trusted hardware and the USBkey;
[0041] (3) The ope...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com