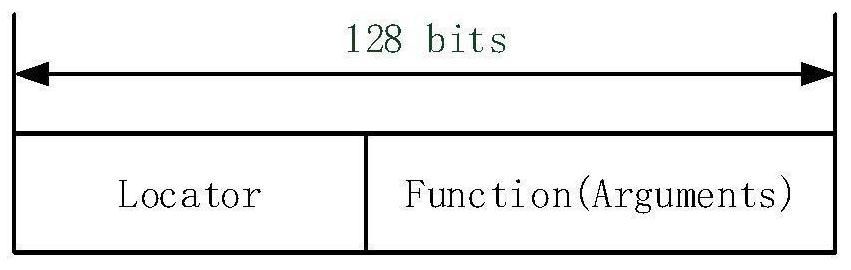
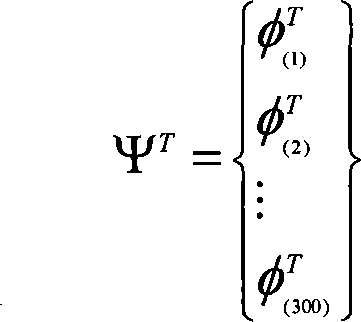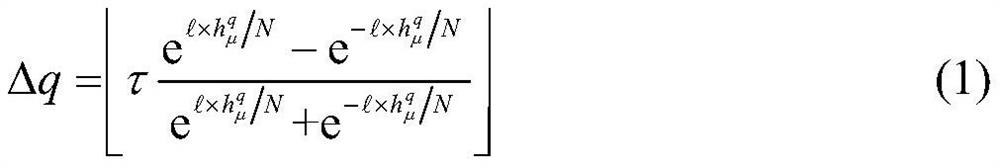Patents
Literature
43results about How to "Widely deployed" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
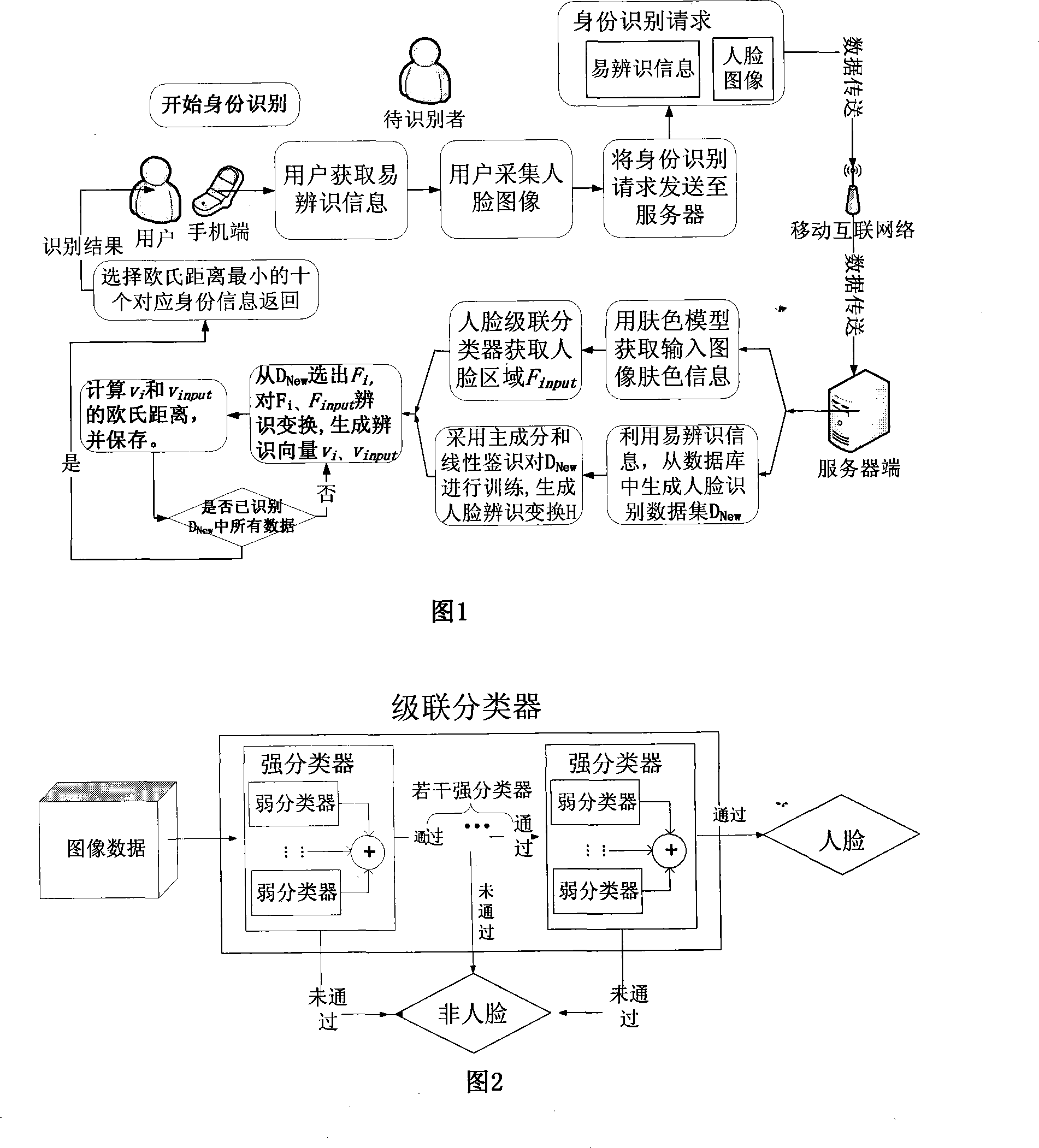
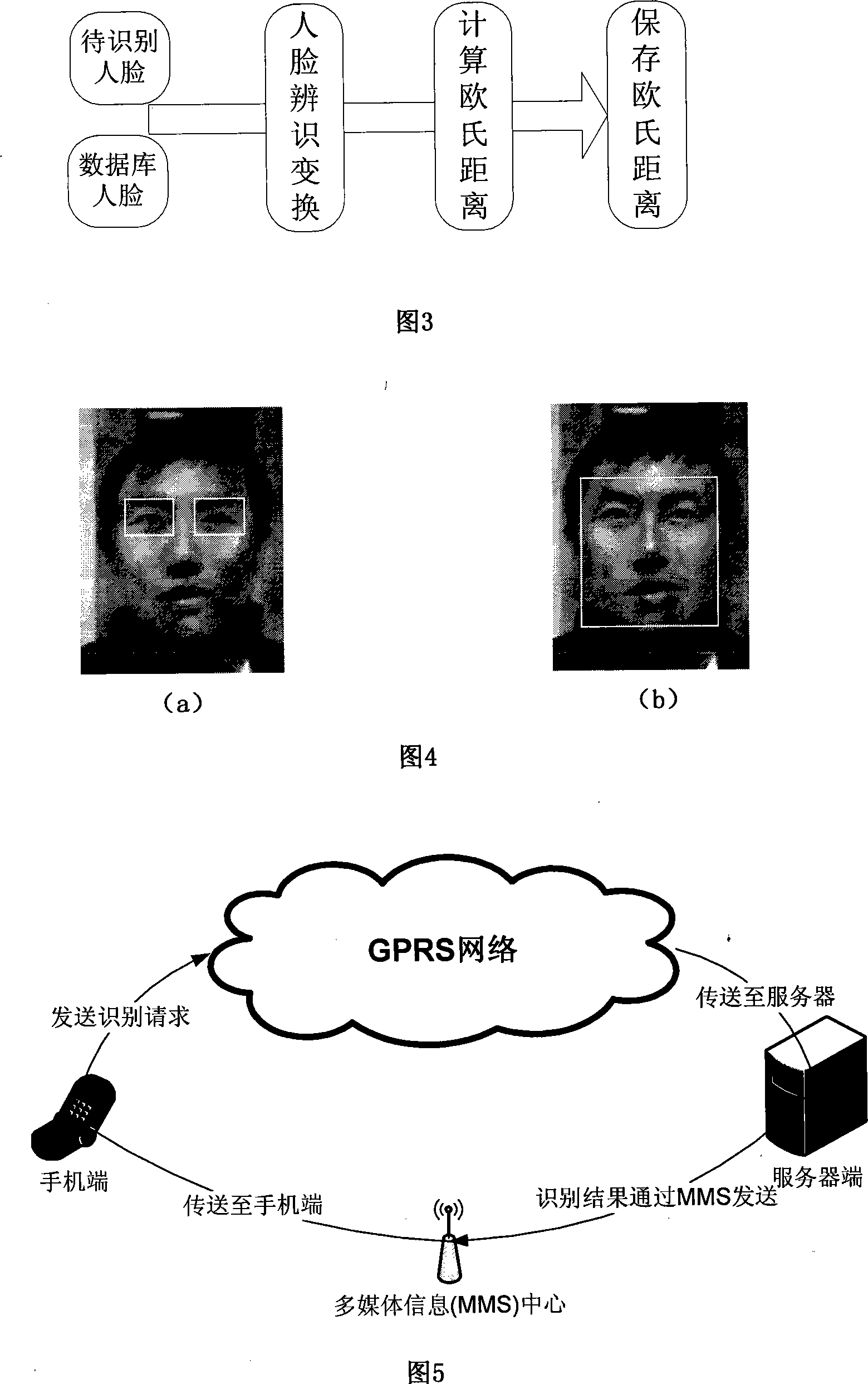
Personal identification method based on mobile phone pick-up head combining with human face recognition technique
InactiveCN101226591ALow costLow priceCharacter and pattern recognitionMobile WebMultimedia information
Disclosed is an identification method based on the combination of cell phone cameras and face recognition technique in the field of wireless network technique and pattern recognition. A mobile network is used to transfer easily cognizable information of to-be-identified persons and face image information collected by the cell phone cameras to a server which combines the data meeting the specifications of sex, age and the like in a data bank to a candidate data set according to the easily cognizable information. The sever identifies the face data in the candidate data set by employing principal component analysis and linear discrimination analysis for training, identifies image-transferred face areas and selects the most similar results, the number of which is set by users, from the identification results to transfer back to cell phones for final judgment by the users. The invention realizes the purposes of largely reducing cost and difficulty and increasing speed and accuracy of identification.
Owner:SHANGHAI JIAO TONG UNIV
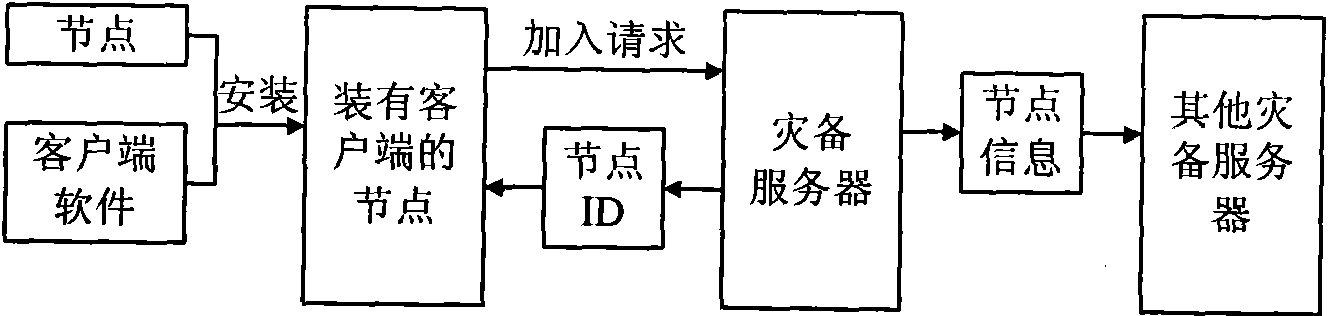
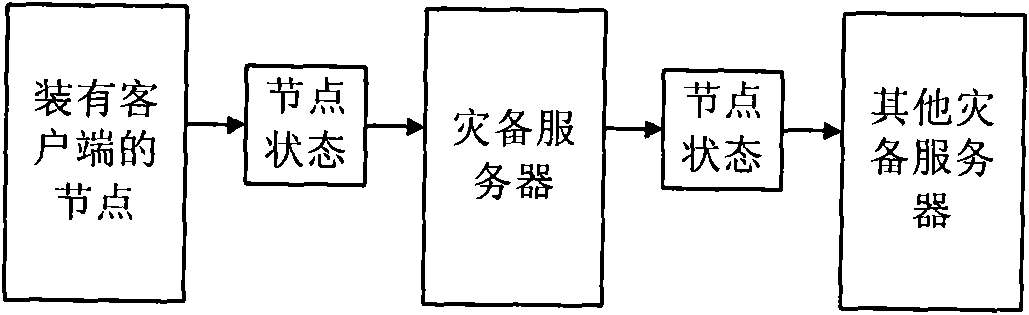
Disaster-tolerant backup method based on P2P
InactiveCN101651710ALow costImprove resource utilizationData switching networksResource utilizationBackup
The invention discloses a disaster-tolerant backup method based on P2P. The method comprises the following steps that a network of a disaster-tolerant backup system to be configured is divided into aplurality of logic regions; each logic region includes at least one disaster-tolerant backup server and a plurality of nodes; the disaster-tolerant backup server allocates one unique identity for eachnode added to the disaster-tolerant backup system and takes charge of saving a node information list and a disaster-tolerant backup data list; each node mutually executes the data backup according tothe node information list and the disaster-tolerant backup data list saved on the disaster-tolerant backup server; and after the disaster happens, the disaster-tolerant backup server recovers data broken by the disaster from the nodes not suffering the disaster according to the two lists. The invention utilizes a P2P technology and fully utilizes the spare resource of each node in the disaster-tolerant backup system to perform disaster-tolerant backup to recover data and services of other nodes so as to reduce the cost of the disaster-tolerant backup system and also improve the resource utilization ratio of the disaster-tolerant backup system.
Owner:BEIJING UNIV OF TECH
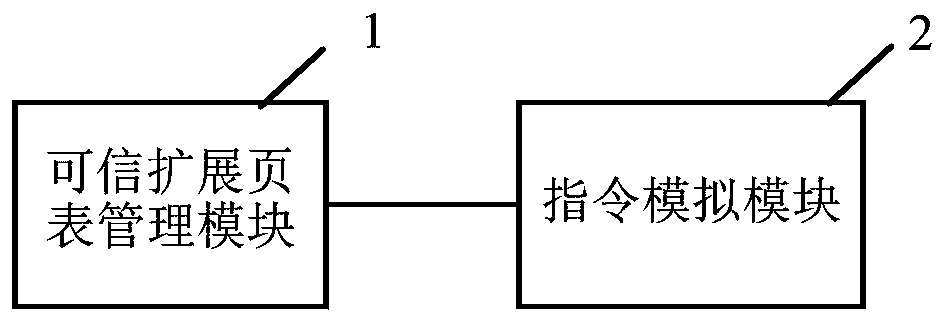
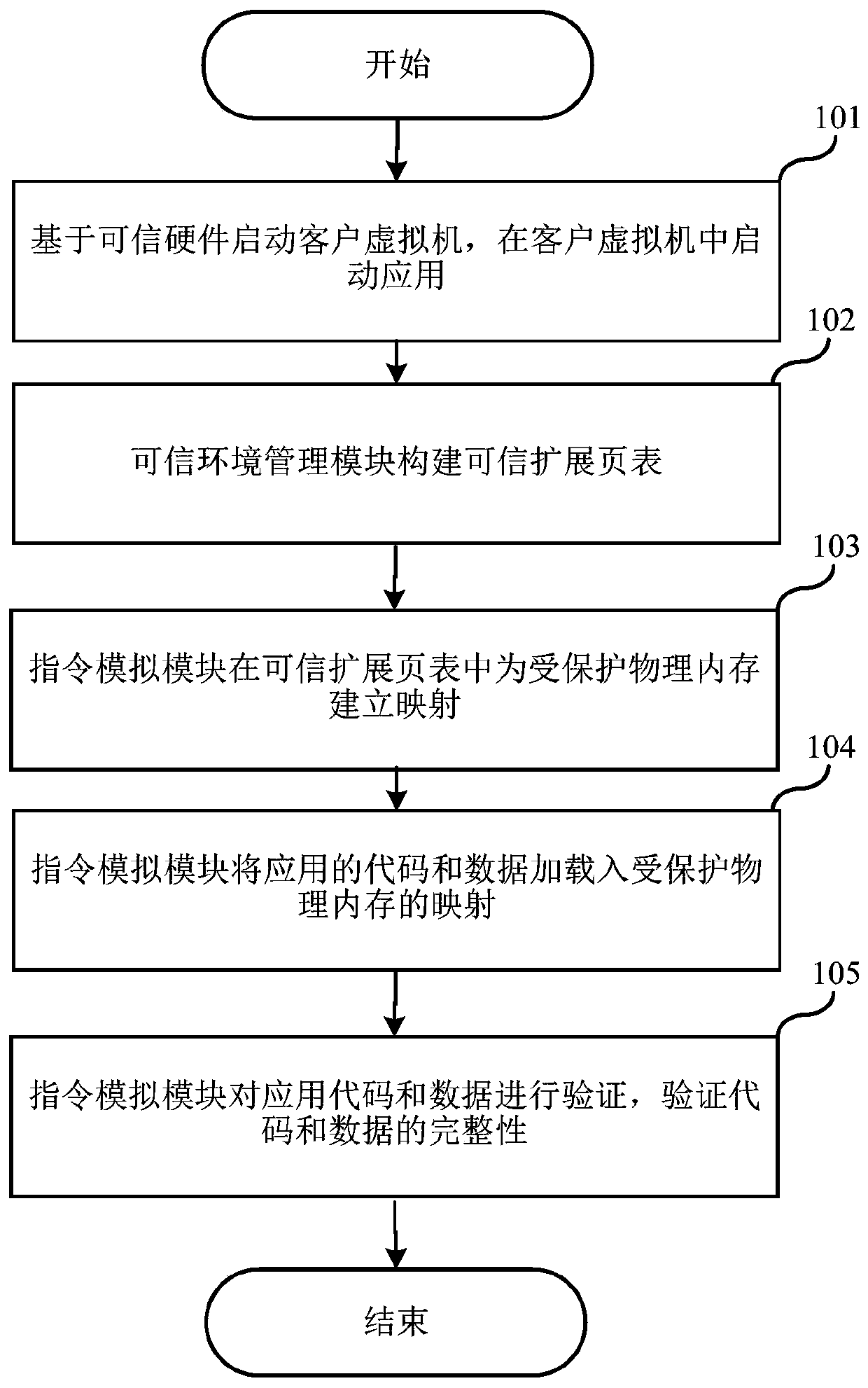
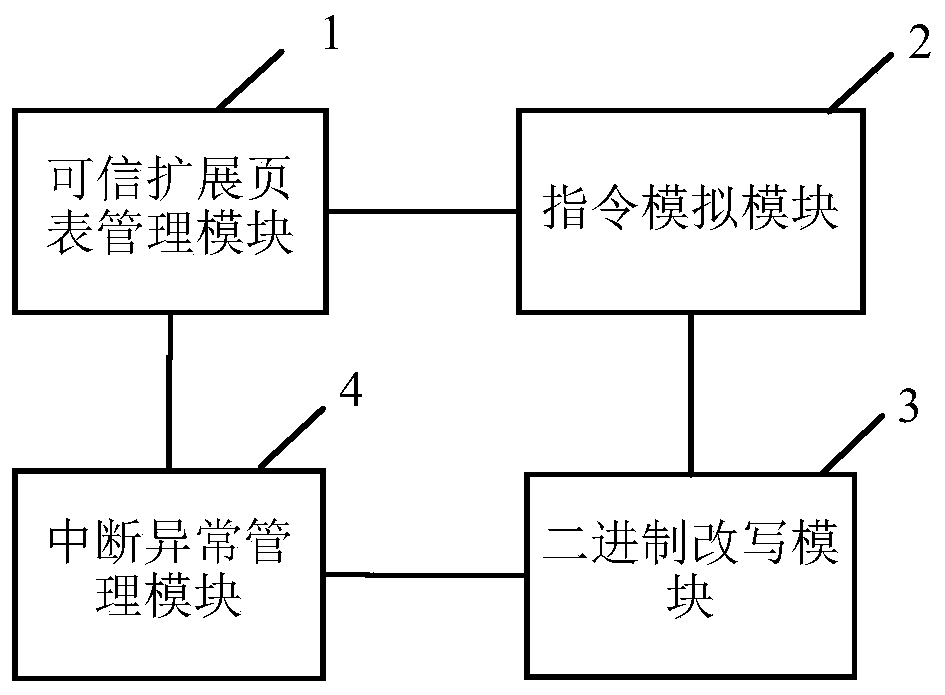
Virtual machine monitor and virtual trusted execution environment construction method
PendingCN110119302AWidely deployedAvoid difficultySoftware simulation/interpretation/emulationEnergy efficient computingTrusted hardwareComputer module
The embodiment of the invention relates to the technical field of software, and discloses a virtual machine monitor and a virtual trusted execution environment construction method. The invention provides a virtual machine monitor which starts a client virtual machine based on trusted hardware and starts an application in the client virtual machine. The virtual machine monitor comprises a trusted extension page table management module and an instruction simulation module, the trusted extension page table management module used for establishing a trusted extension page table when the applicationis started, and the instruction simulation module used for establishing mapping for the protected physical memory in the trusted extension page table, loading codes and data of an application into the protected physical memory, and verifying the integrity of the codes and the data; the instruction simulation module completes the construction of the virtual trusted execution environment when the verification is passed. Therefore, a trusted execution environment is realized without using an SGX technology, the difficulty brought to wide deployment of security applications due to the fact that only a few servers support the SGX technology is avoided, and wide deployment of the security applications is realized.
Owner:上海隔镜信息科技有限公司
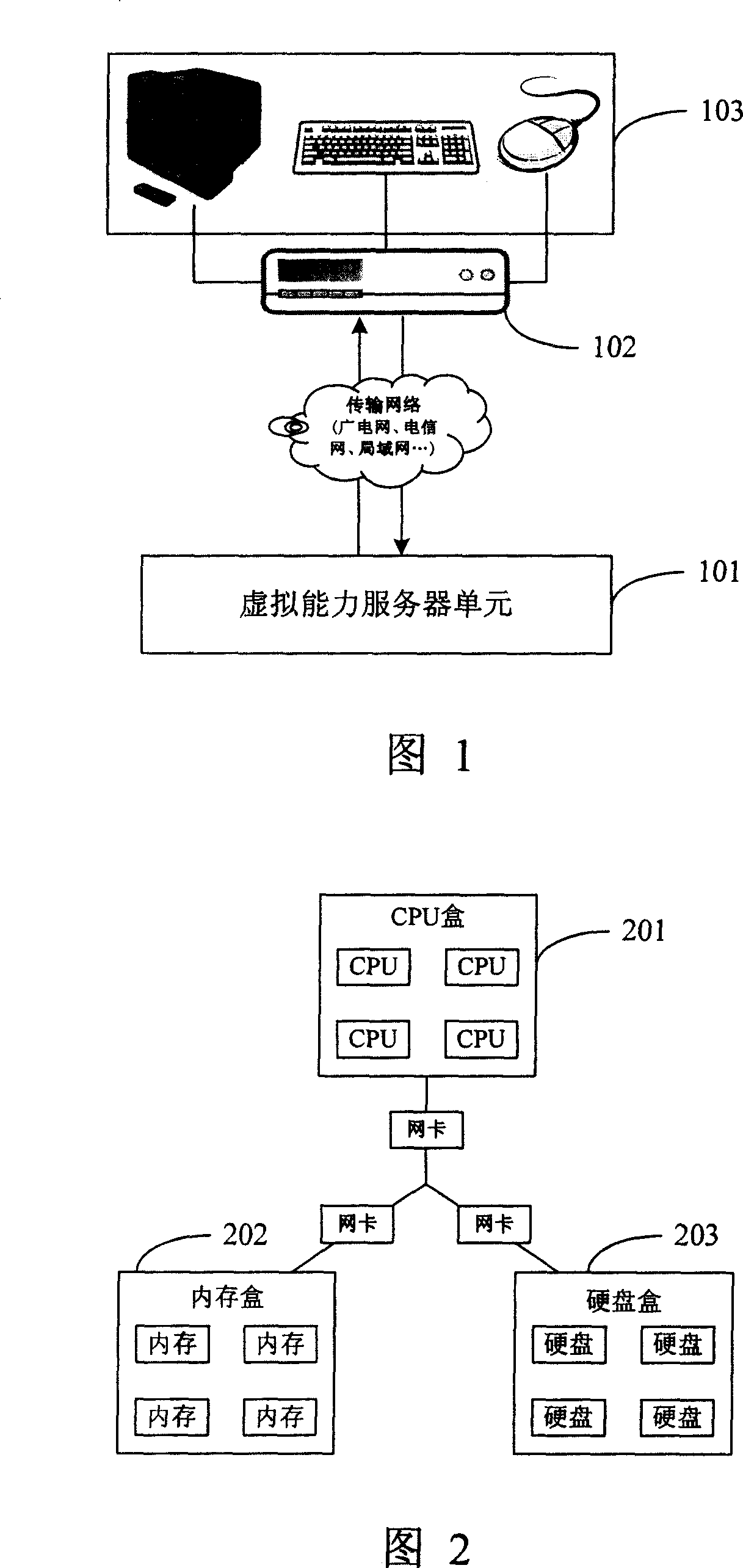
Household informatization system
InactiveCN101083714AImprove overall utilizationImprove performanceTelevision system detailsColor television detailsInformatizationComputer network
This system includes a virtual ability server unit (VAS), a set-top box (SB), a display and control unit (DC). VAS receives the operation and control info (OCI) from SB, converts OCI into the operation instruction, executes the converted instruction i.e. to calculate and distribute the storage resource, finally packs and puts the executed result into SB. SB is used to STP encapsulate the received OCI and transfers them to VAS unit, and converts the information returned from VAS unit into a image signal and sends it to DC. Here, STP stands for the secure transport protocols. DC show the image signal from SB, sends OCI to SB. This invention can greatly raise the utilization rate of resources and the service features offered by digitalization information technique and can reduce effectively the service cost.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
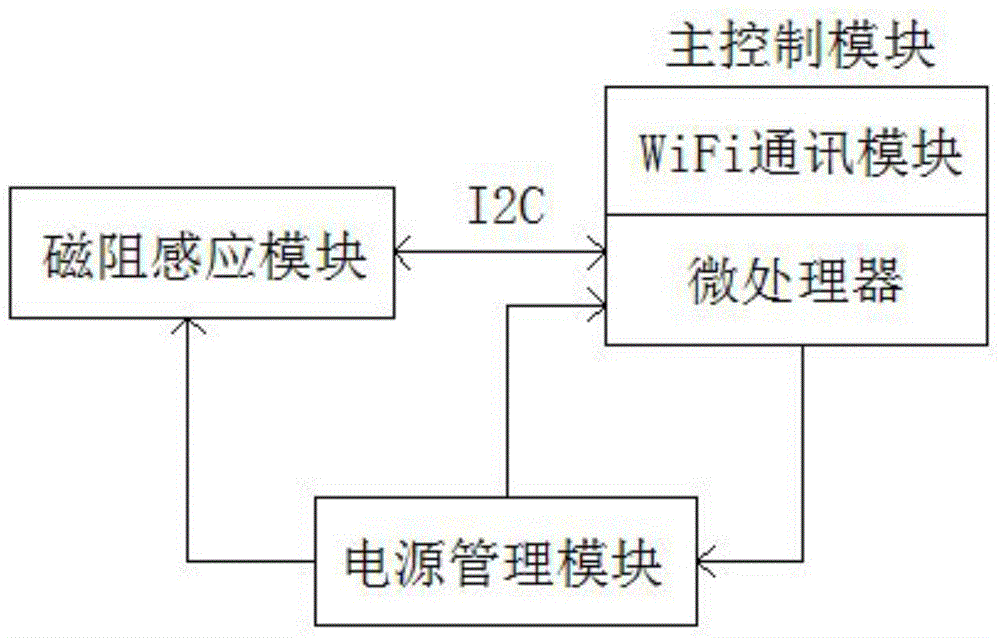
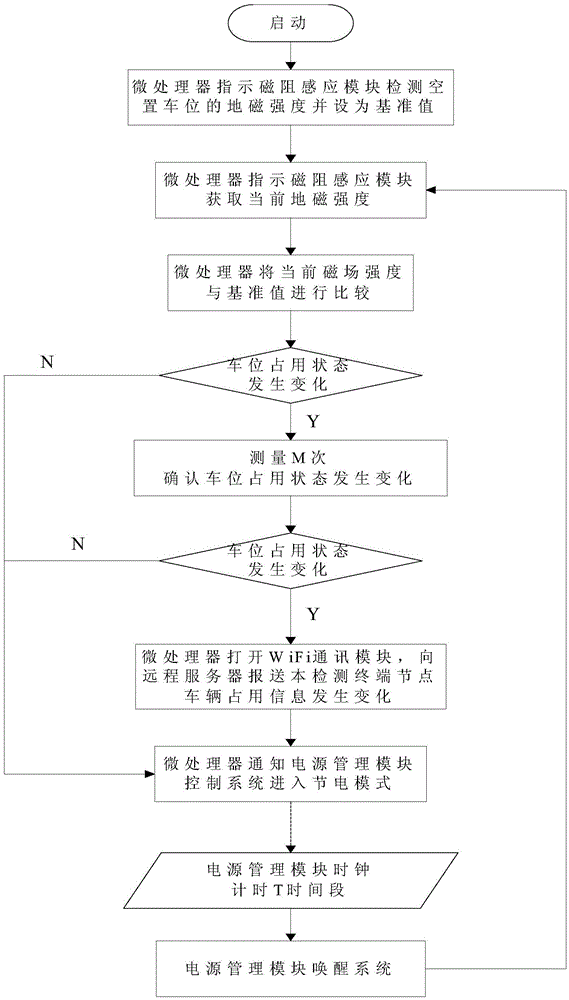
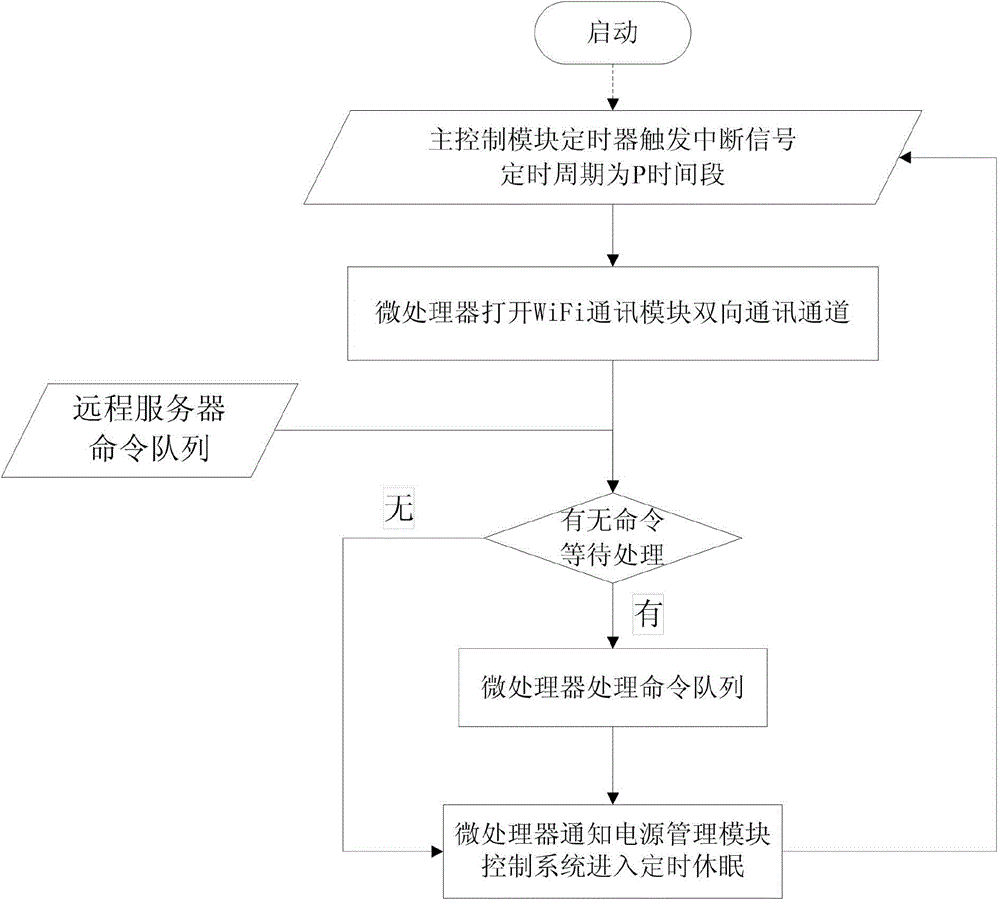
Geomagnetic parking space detector and geomagnetic parking space detection method
InactiveCN104637312AReduce power consumptionMature technologyIndication of parksing free spacesWireless transmissionParking space
The invention relates to a geomagnetic parking space detector and a geomagnetic parking space detection method and belongs to the technical field of vehicle detection. The detector consists of a magnetic resistance sensing module, a main control module and a power management module, wherein the main control module comprises a microprocessor and a WiFi (Wireless Fidelity) communication module; the magnetic resistance sensing module is in two-way connection with the microprocessor; the microprocessor processes data output by the magnetic resistance sensing module and configures relevant parameters of the magnetic resistance sensing module; the power management module is connected with the magnetic resistance sensing module and the main control module and provides working voltage for the magnetic resistance sensing module and the main control module; the microprocessor is connected with the power management module and manages the use effectiveness of a power supply. According to the geomagnetic parking space detector and the geomagnetic parking space detection method, WiFi wireless transmission is adopted, and the geomagnetic parking space detector is simple in networking, high in capacity expansion, low in implementation cost and low in using cost.
Owner:NANJING YIFENGYI INFORMATION TECH
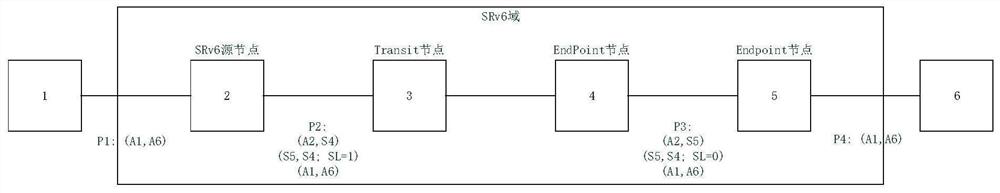
Bidirectional forwarding detection method and system in SRv6 network
ActiveCN113381933ASolve the problem of excessive packet lossWidely deployedData switching networksPathPingPacket loss
The invention discloses a bidirectional forwarding detection method in an SRv6 network, which comprises the following steps that a host node obtains a Segment List [0..N] in an SRH of a BFD message, adds a source address of the message into a first position of the Segment List [0..N], removes an address field belonging to the node from the Segment List [0..N], carries out reverse operation on the corrected Segment List [0..N] to obtain a Reversed Segment List [0..N], packages the SRH by using the Reversed segment List [0..N], sends a response message of the BFD to the source node, and achieves that a reverse path and a forward path of the dynamic BFD or SBFD are consistent. The method provided by the invention solves the problems of failure of service main and standby protection switching and overlong service packet loss time caused by inconsistency of a dynamic BFD / S-BFD reverse path and a dynamic BFD / S-BFD fault detection, and improves the competitiveness of equipment. The invention also provides a corresponding bidirectional forwarding detection system in the SRv6 network.
Owner:FENGHUO COMM SCI & TECH CO LTD
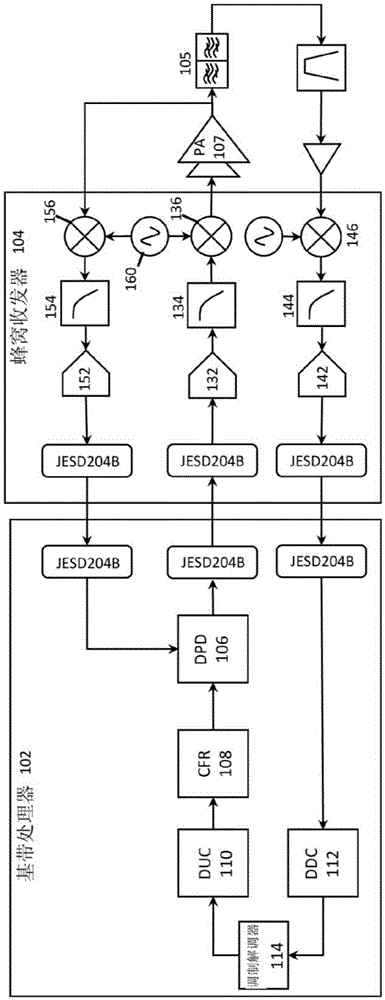
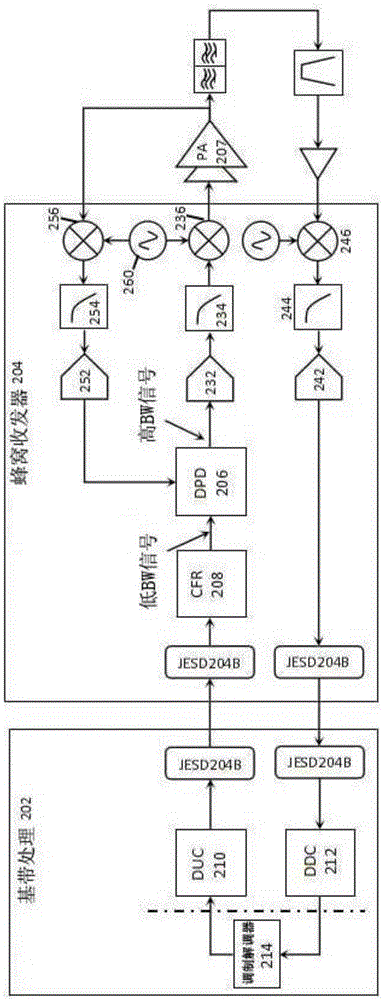
Highly integrated radio frequency transceiver
ActiveCN105812015ALow costWidely deployedSpatial transmit diversityNegative-feedback-circuit arrangementsTransceiverEngineering
The present invention relates to a highly integrated radio frequency transceiver. For small cells, transceivers demand high performance while maintaining system efficiency. The present disclosure describes a highly integrated cellular transceiver that offers such features by providing one or more digital functions on-chip, onto the same die in the cellular transceiver. Effectively, the scope and boundary of the cellular transceiver is expanded to move beyond the data converters of the transceiver to include a variety of digital functions, thus integrating more of the signal chain in the cellular transceiver. Integration can greatly reduce complexity for the baseband processing, lower the cost of the overall transceiver system, reduce power consumption, and at the same time, benefit from improvements on the digital functions through integration.
Owner:ANALOG DEVICES INT UNLTD
Self-adapted method for detecting the clock resetting based on the mode recognition
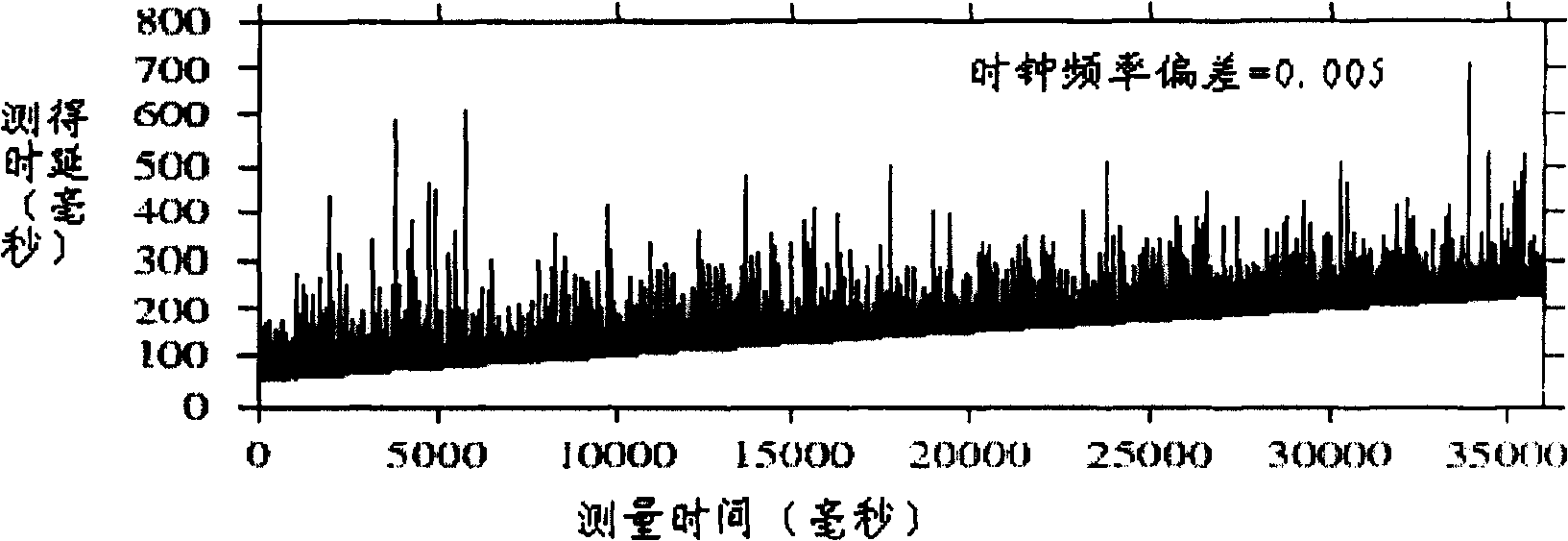
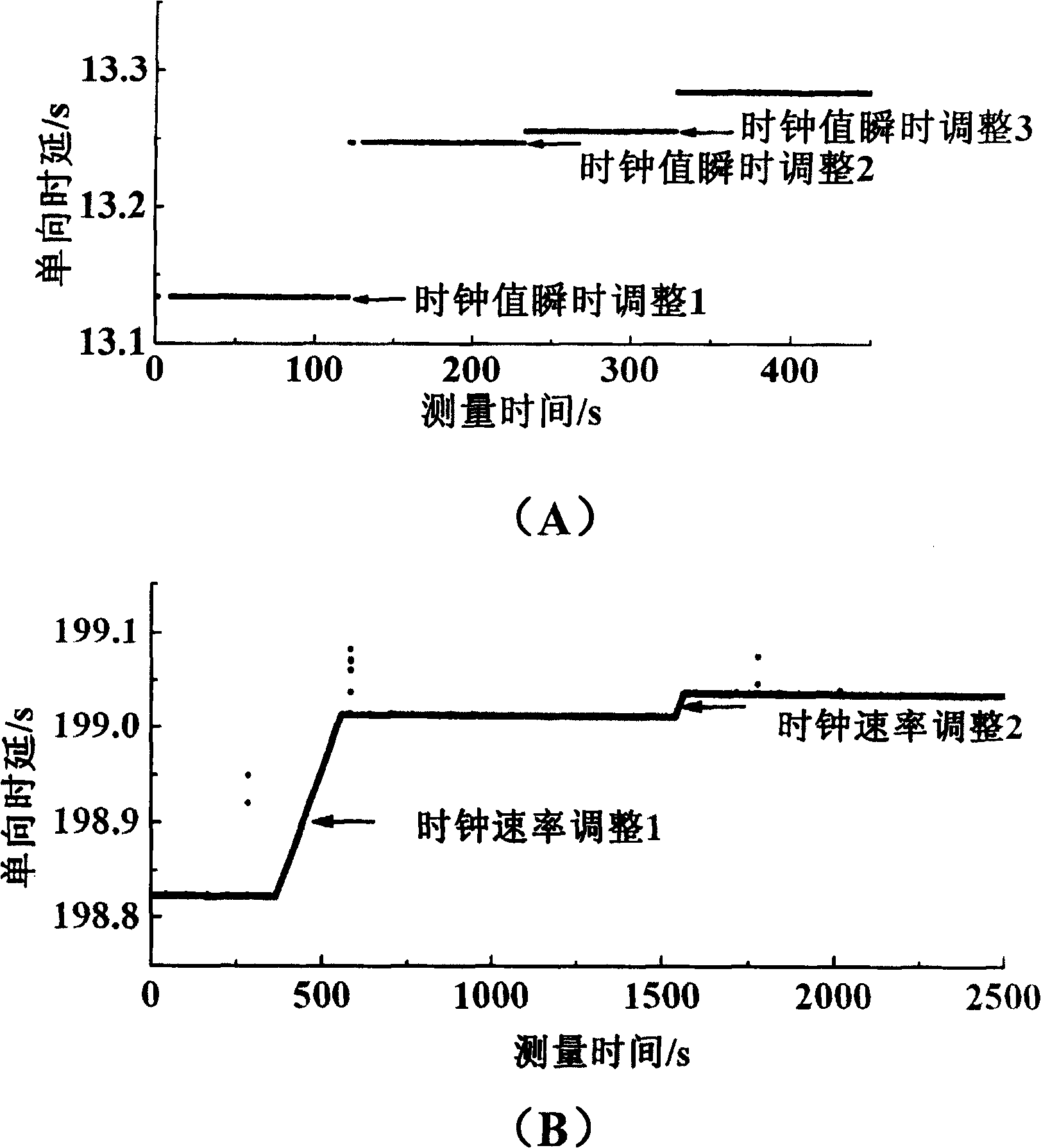
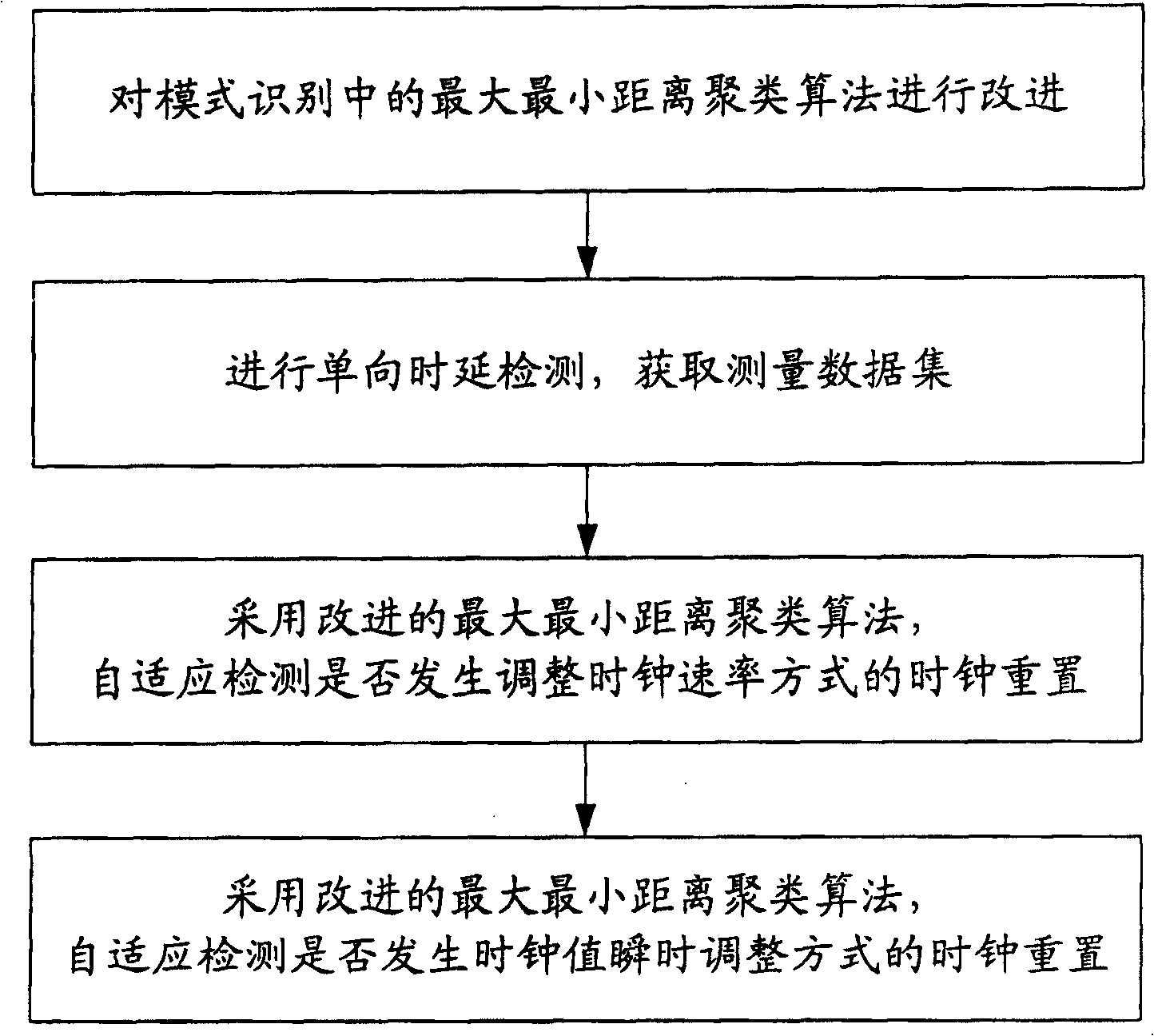
InactiveCN101035038AReduce limitationsImprove accuracyError detection/prevention using signal quality detectorData switching networksCluster algorithmData set
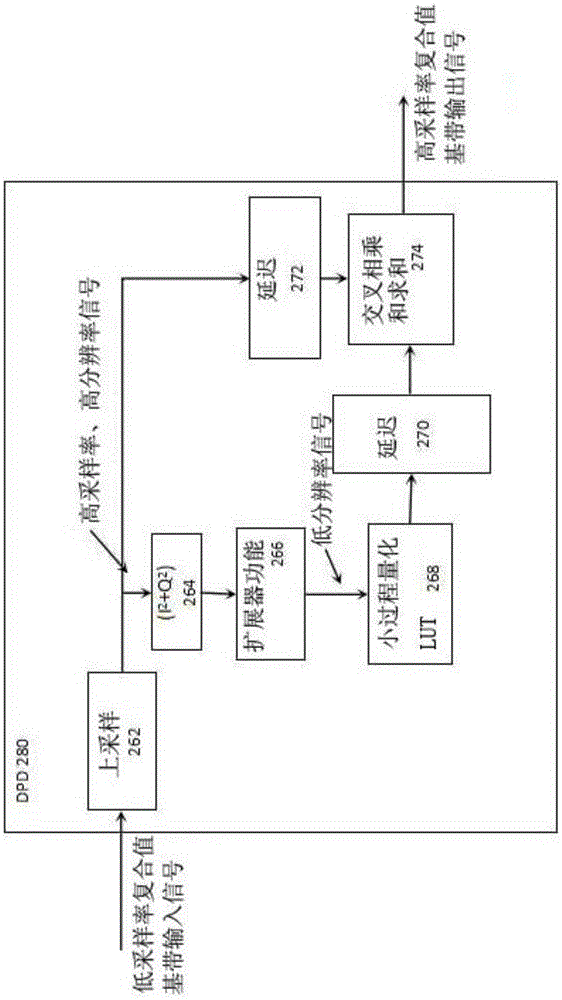
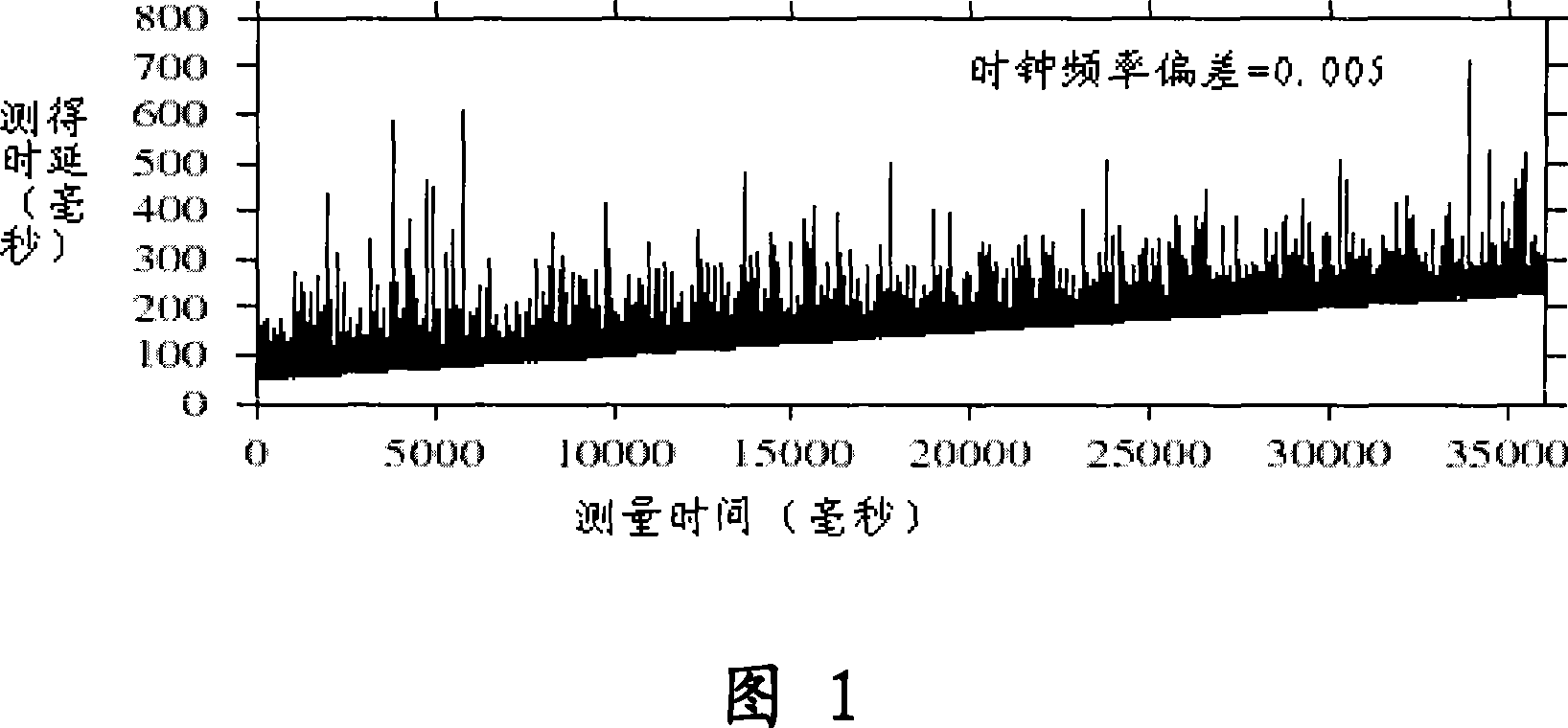
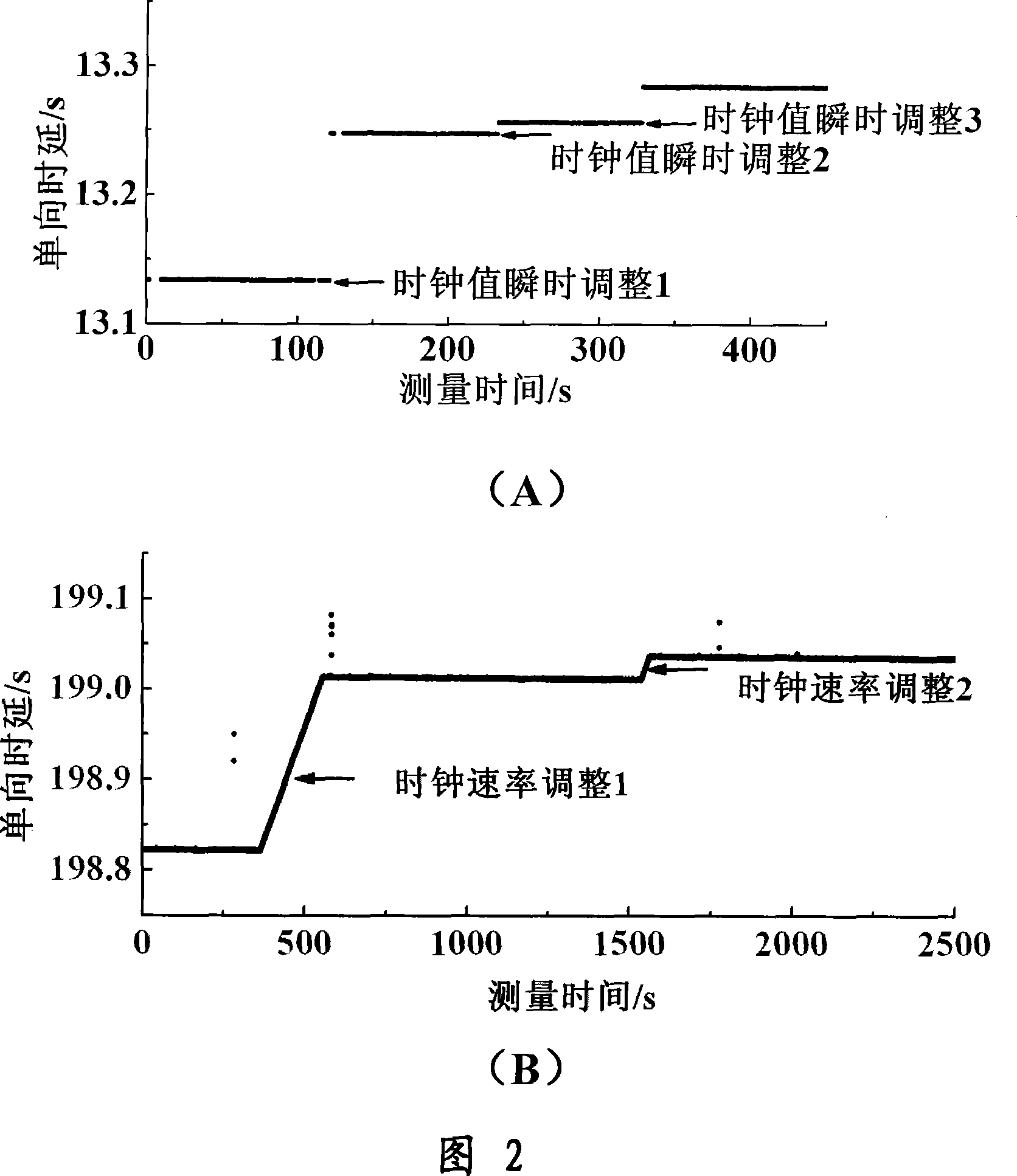
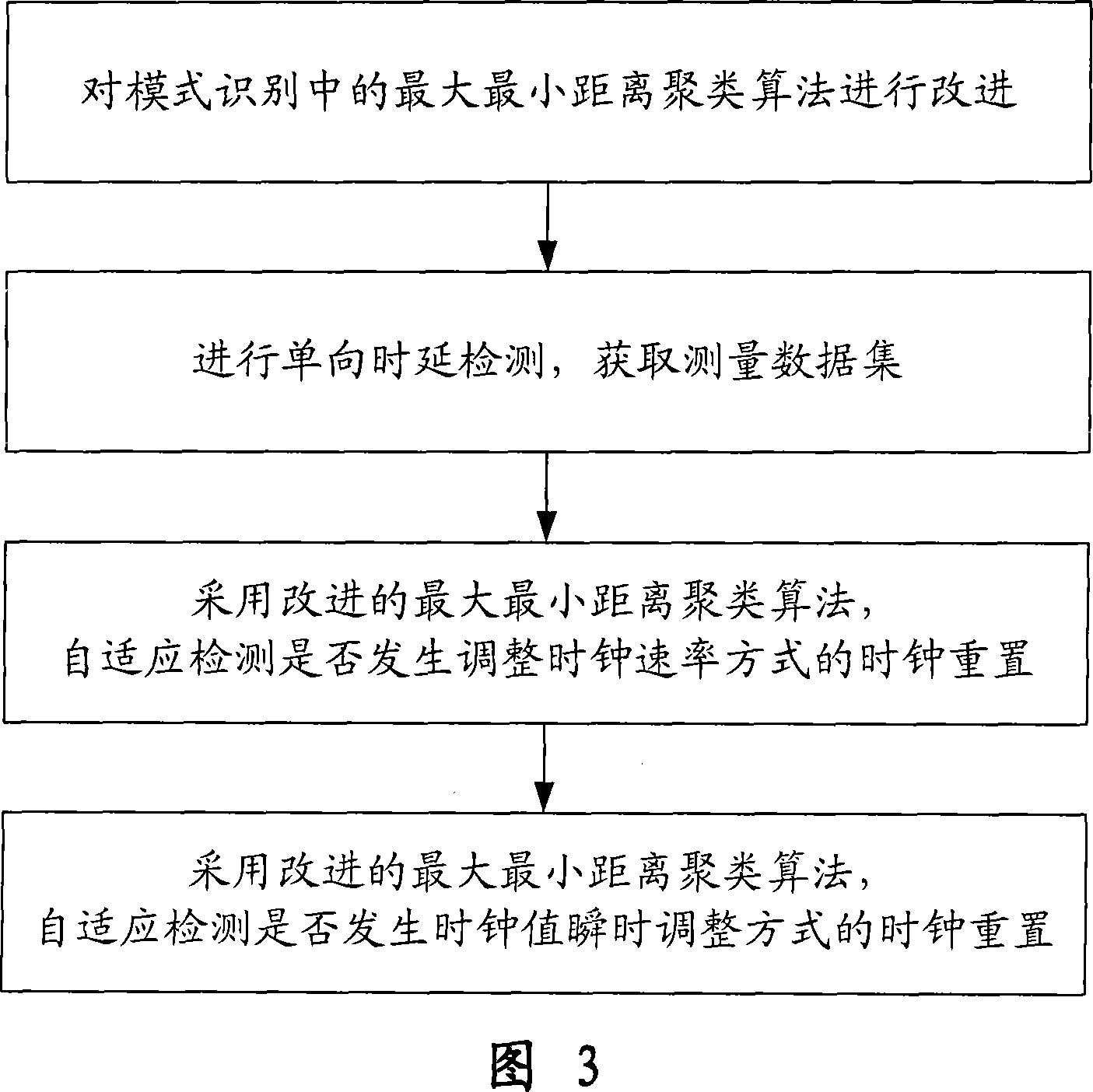
A clock reset detection method based on Adaptive Pattern Recognition, the use of pattern recognition in the improvement of the largest minimum distance clustering algorithm on a one-way delay the processing of data clustering, respectively test for the adaptive re-adjustment methods and the clock rate adjustment means instantaneous value of two different types of time bell replacement, but also to determine the frequency of the clock reset. The main features of the present invention is smaller limitations: the only path forward for a one-way delay measurements to obtain the positive path of one-way delay the measurement data set, we can also use this method to complete adaptive detection and judgment of the two clock reset the type and frequency.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Measurement method and apparatus
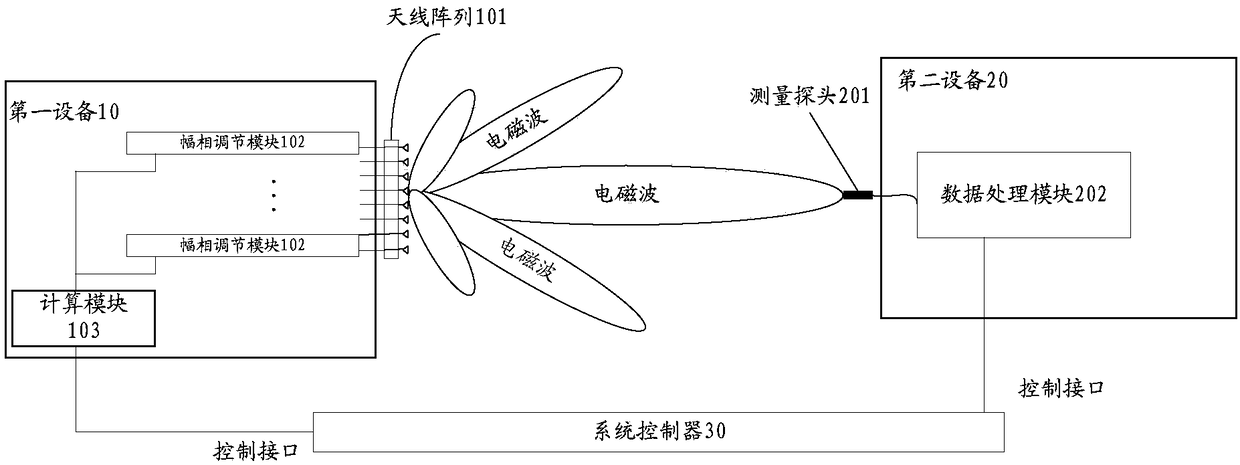
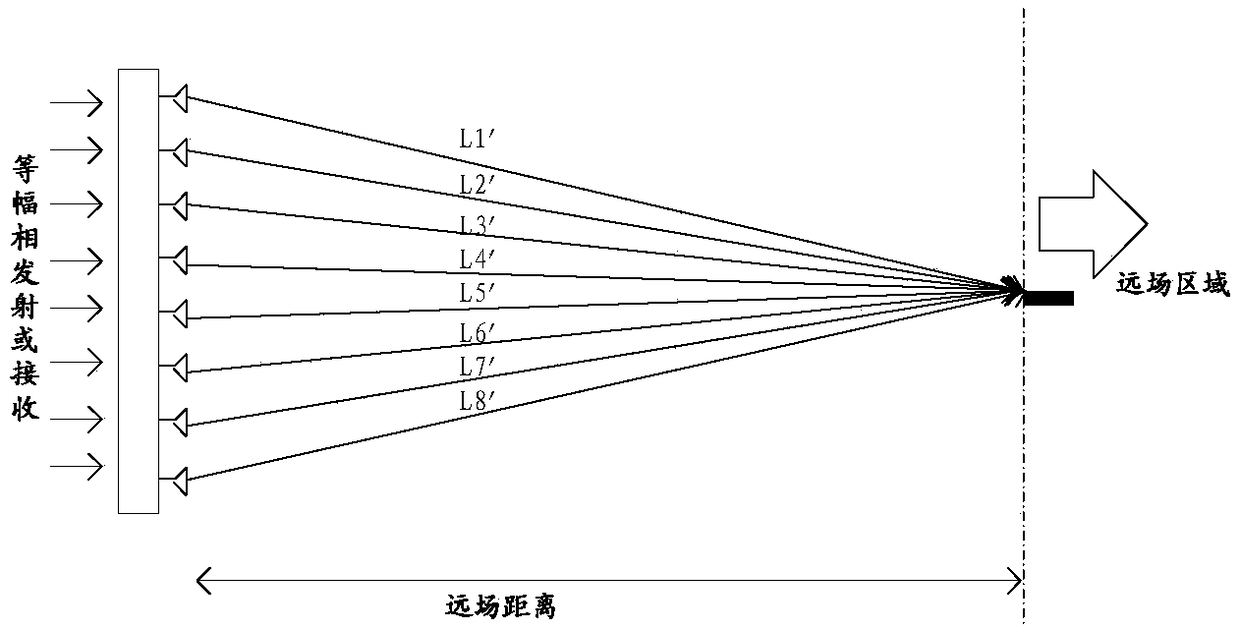
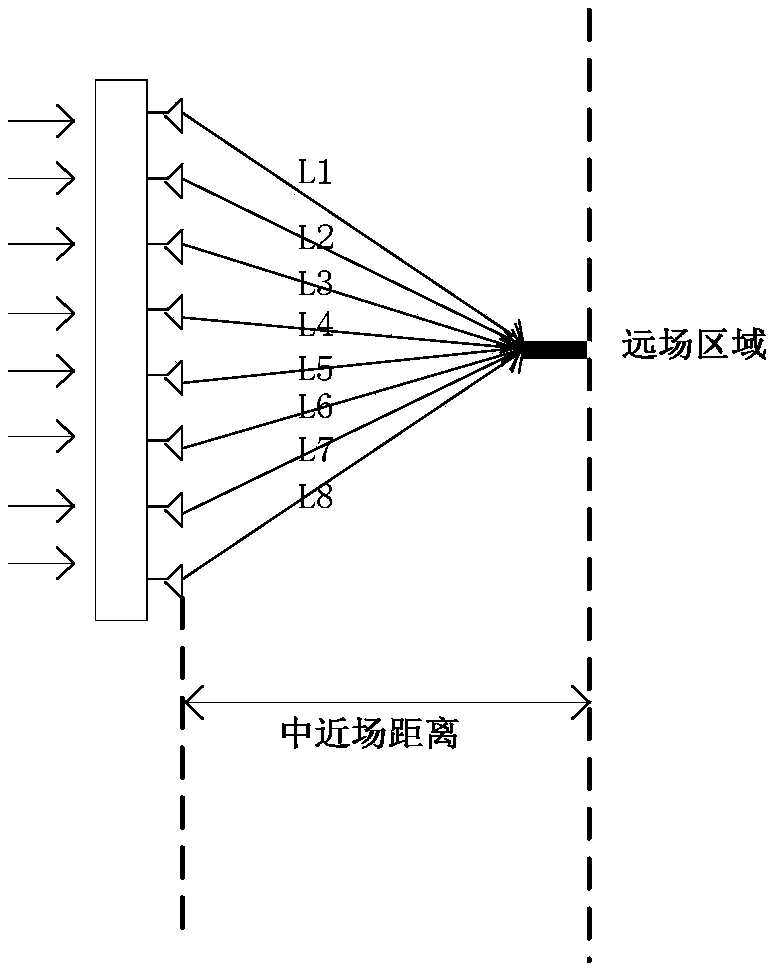
ActiveCN108963459AWidely deployedImprove accuracyTransmitters monitoringAntenna arraysPhase compensationMeasurement cost
The embodiments of the present invention disclose a measurement method and apparatus and belong to the communication field. According to the measurement method and apparatus adopted, a small-size measurement system can be utilized to realize an equivalent far-field measurement effect in a short distance, measurement costs can be decreased, and the wide deployment of the measurement system can be benefitted. The method includes the following steps that: the compensation values of all antenna groups except a target antenna group in an antenna array are determined according to the characteristicparameters of the antenna groups and the characteristic parameters of the target antenna group, wherein the compensation values include phase compensation values and amplitude compensation values; electromagnetic waves emitted by each antenna unit of the antenna groups are adjusted according to the compensation values of the antenna groups, so that phases and amplitudes by which the electromagnetic waves emitted by each antenna unit in the antenna array arrive at measurement probes can be identical, wherein the electromagnetic waves are used to measure the air interface beam parameters of a first device, and a distance between the measurement probes of the first device and a second device is smaller than a far field boundary distance.
Owner:HUAWEI TECH CO LTD
Environmental-friendly street lamp with dust removing function
InactiveCN103486529ARealize self-extractionWidely deployedOutdoor lightingWith built-in powerDust controlEnvironmental engineering
The invention discloses an environmental-friendly street lamp with a dust removing function. The environmental-friendly street lamp comprises a hollow lamp pole main body, a static dust deposition device and a power generation device, wherein the power generation device comprises an impeller arranged on the lamp pole main body and a power generator driven by the impeller and used for storing generated electric energy in a storage battery; the static dust deposition device comprises a static blade arranged on the inner wall of the upper end of the lamp pole main body, the static blade is insulated form the lamp pole main body and powered by the storage battery; an air inlet door dust clearing door is arranged at the lower end of the lamp pole main body. An existing street lamp pole is reconstructed or replaced, no new land is occupied, and the street lamps can be uniformly and widely distributed; by using the effect of sucking air by a chimney, the street lamp can be used for realizing self air suction, saving energy resources, and removing dust by using the electric energy generated by airflow energy, thereby being safe, environmental-friendly and energy-saving.
Owner:NANJING XIPU CEMENT ENG GROUP
Optical signal-to-noise ratio monitoring device and optical signal-to-noise ratio monitoring method
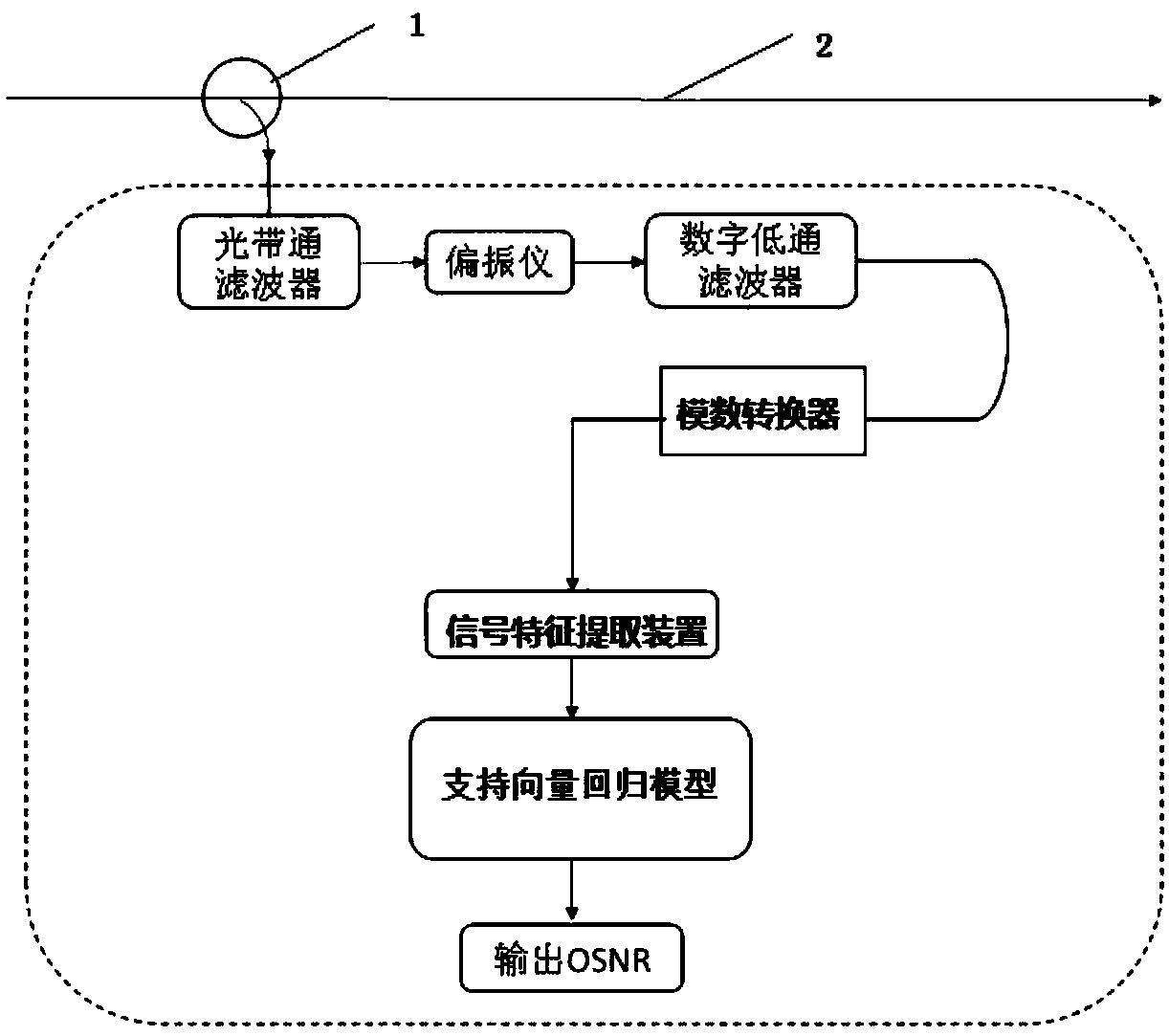
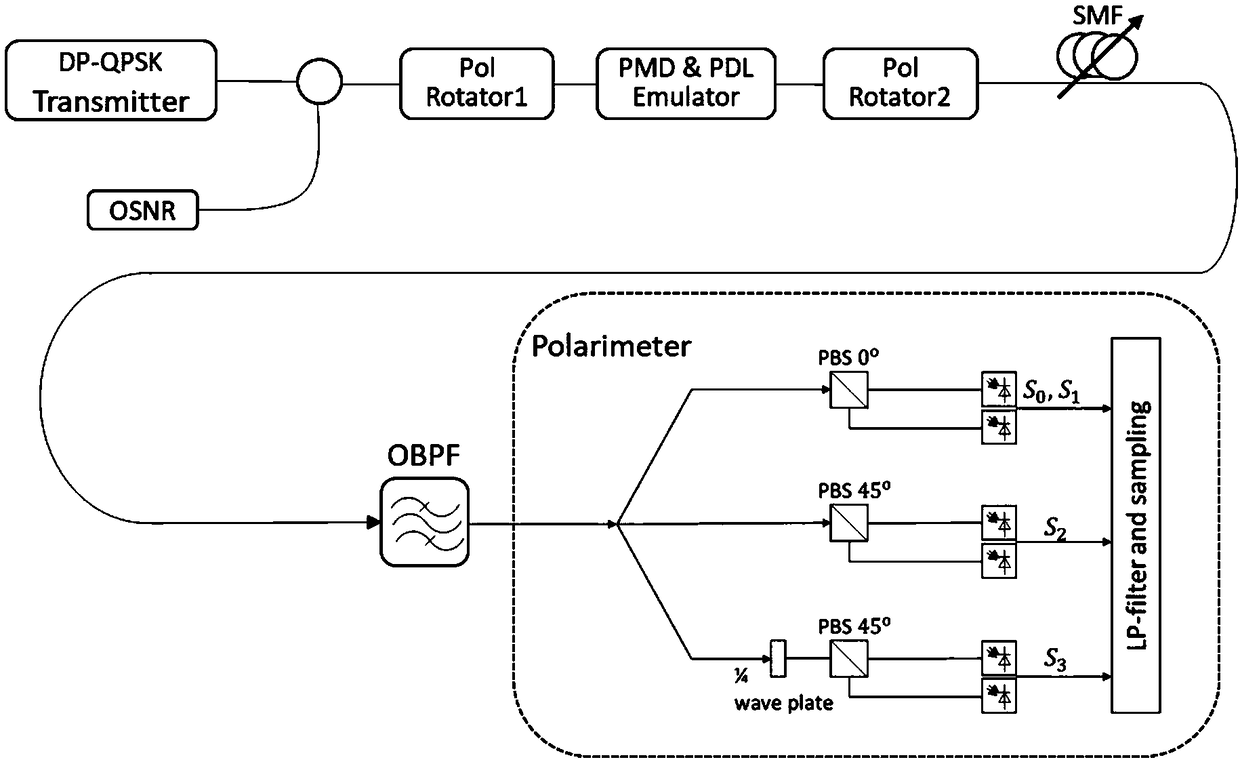
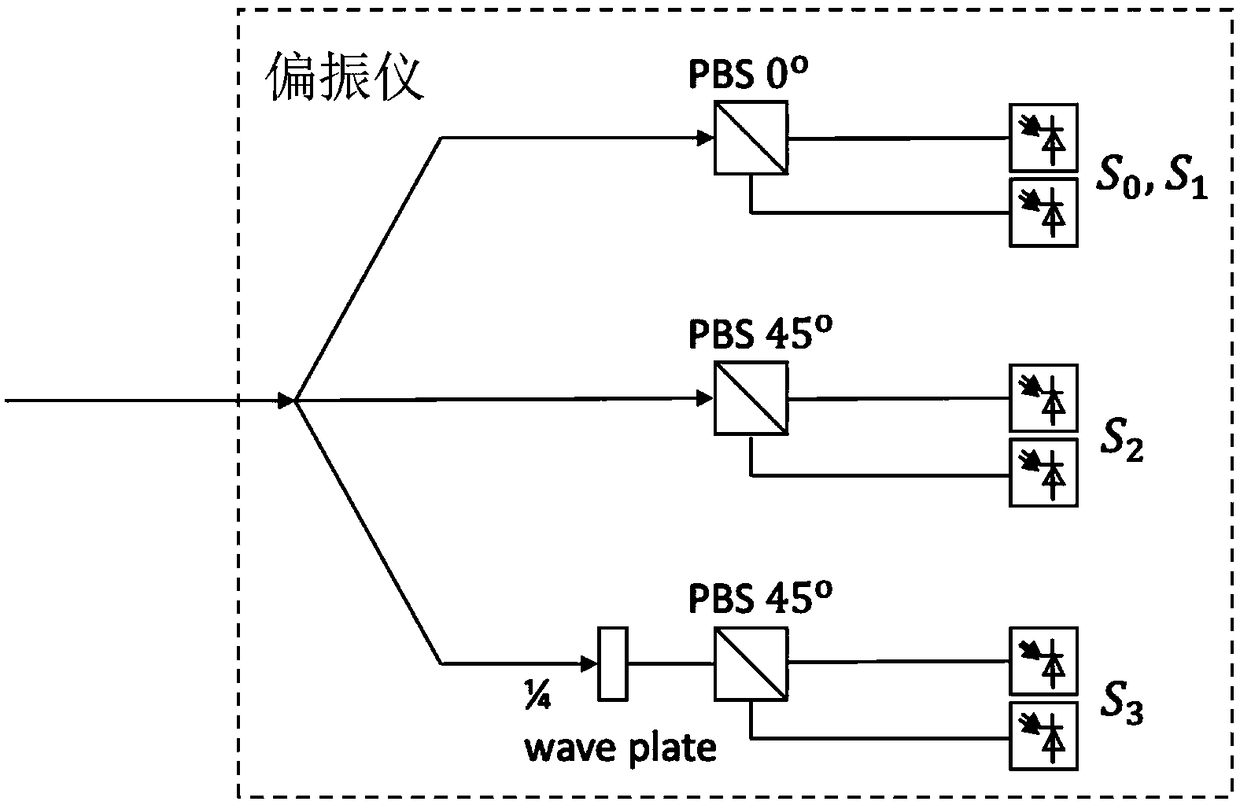
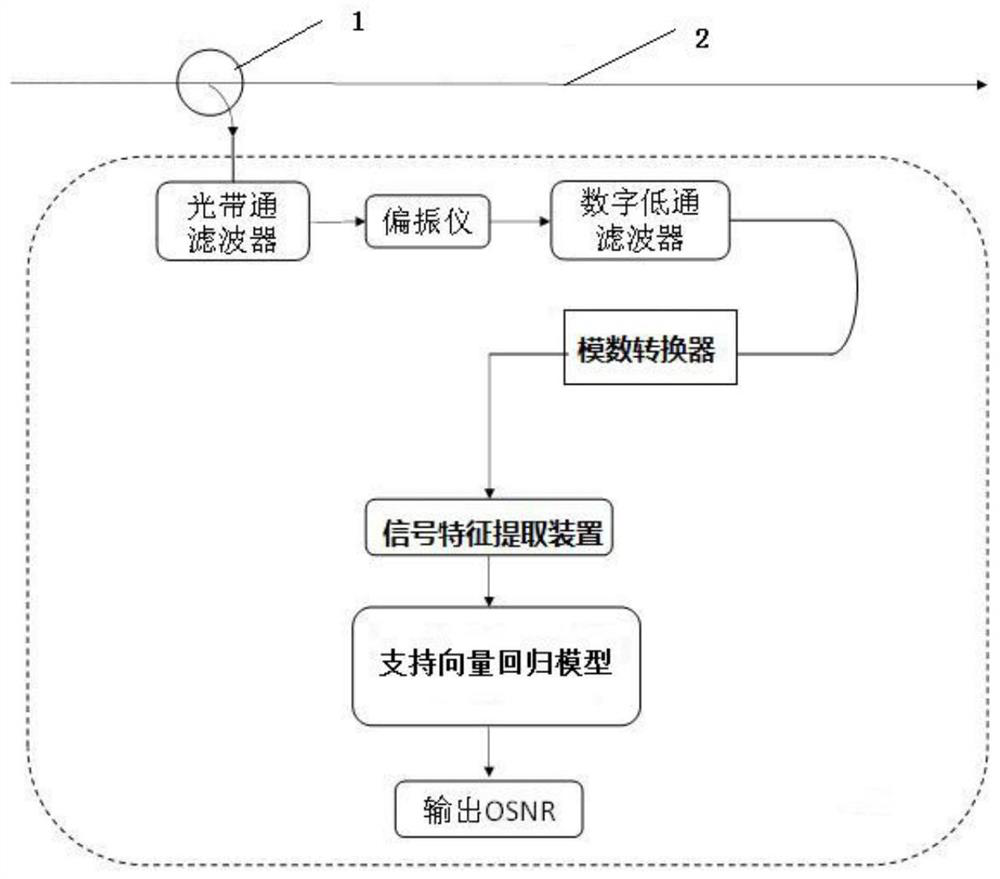
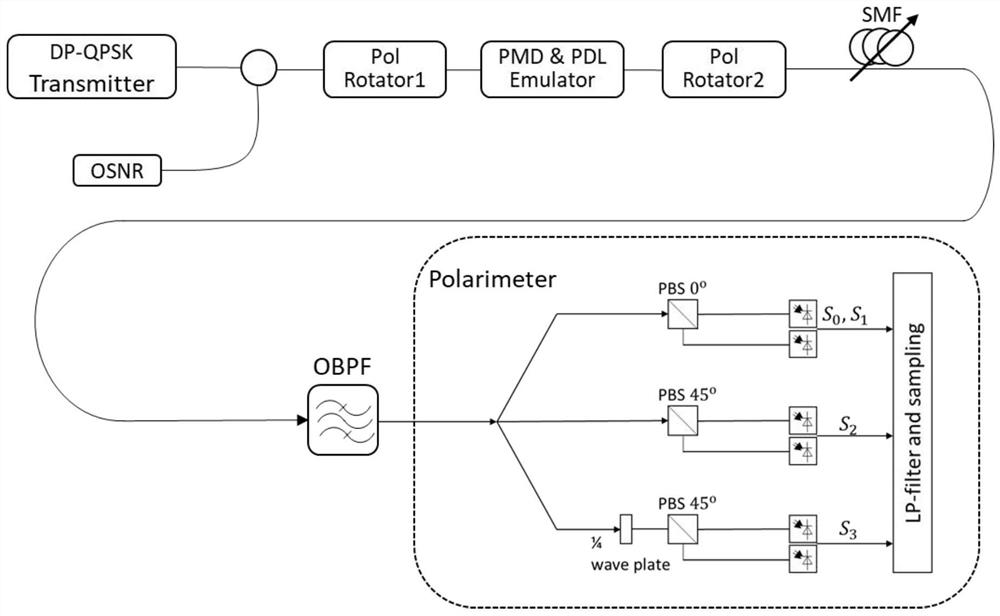
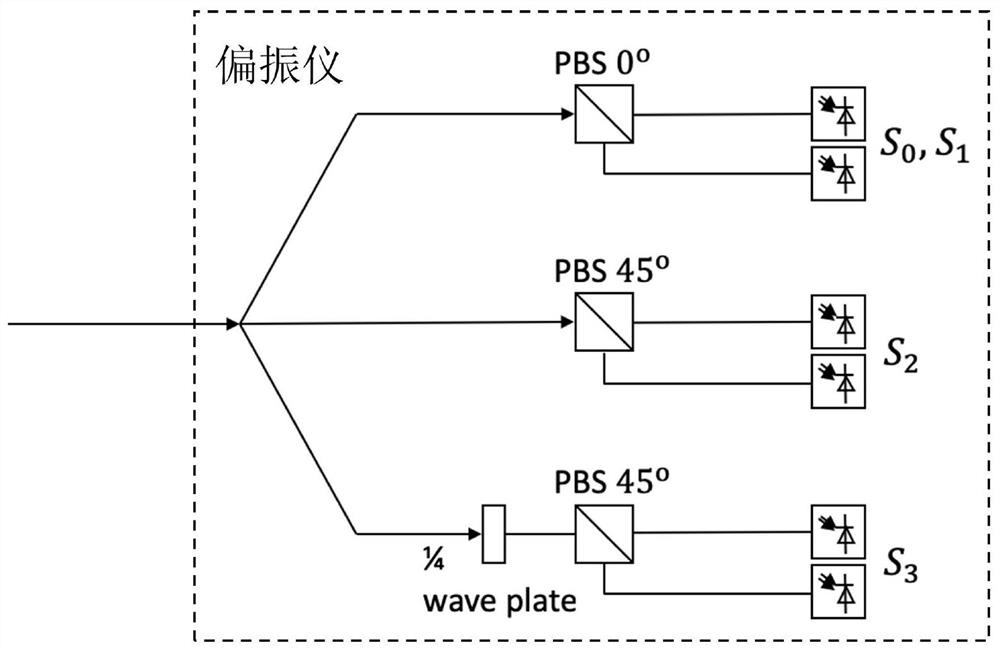
ActiveCN109474336ASimple structureLow costCharacter and pattern recognitionElectromagnetic transmissionEngineeringSupport vector regression machine
The invention discloses an optical signal-to-noise ratio monitoring device and an optical signal-to-noise ratio monitoring method. The optical signal-to-noise ratio monitoring device comprises a signal acquisition device for acquiring a Stokes parameter of a to-be-monitored signal, a signal feature extraction device for extracting signal-to-noise ratio and polarization damage in the Stokes parameter, and a support vector regression model obtained by training with an optical signal feature parameter and an optical signal-to-noise ratio value corresponding to the optical signal feature parameter. The optical signal-to-noise ratio monitoring device realizes optical signal-to-noise ratio monitoring through acquiring the Stokes parameter and extracting the signal-to-noise ratio and the polarization damage based on a support vector regression machine, is simple in structure and low-cost, can be widely deployed at each node in a network and can provide information basis for resource allocation and dynamic routing in an optical network.
Owner:UNIV OF SCI & TECH BEIJING
Brain signal identity recognition method based on multi-layer perceptron
InactiveCN110348430AImprove test accuracyImprove accuracyBiometric pattern recognitionNeural architecturesPattern recognitionIdentity recognition
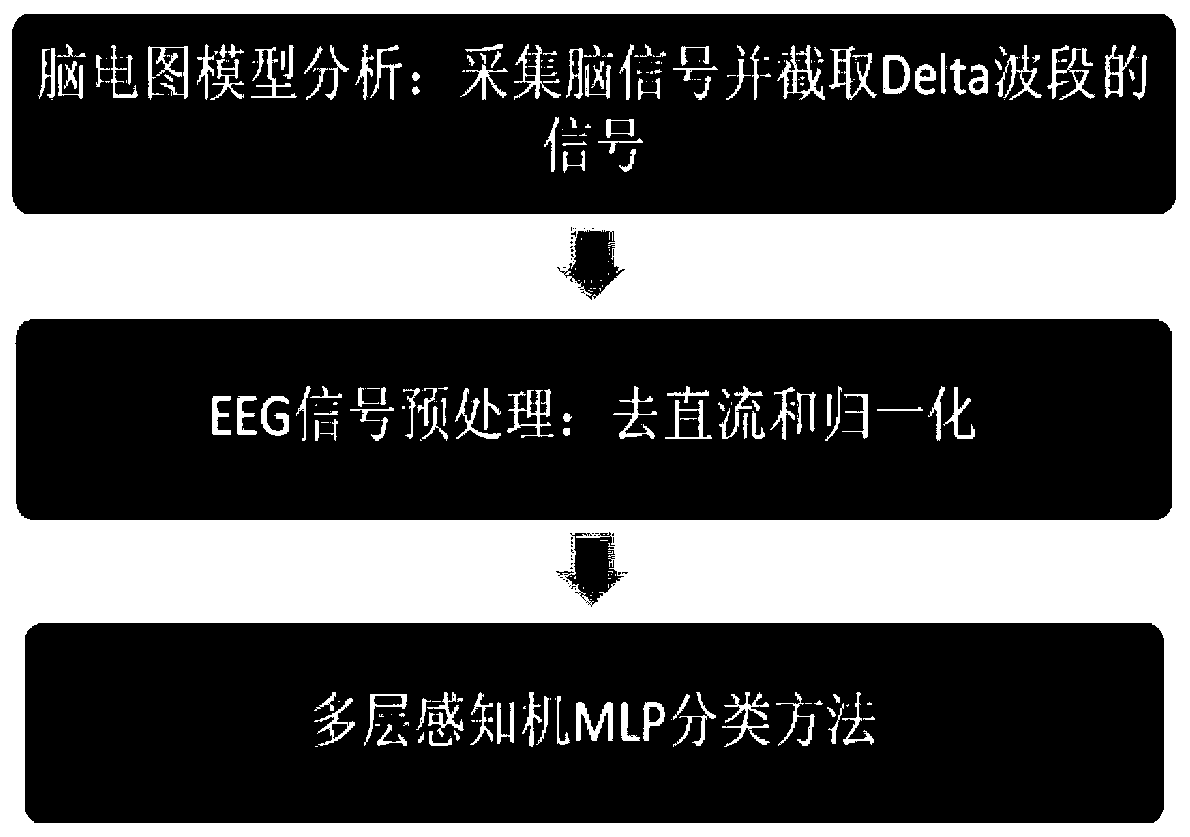
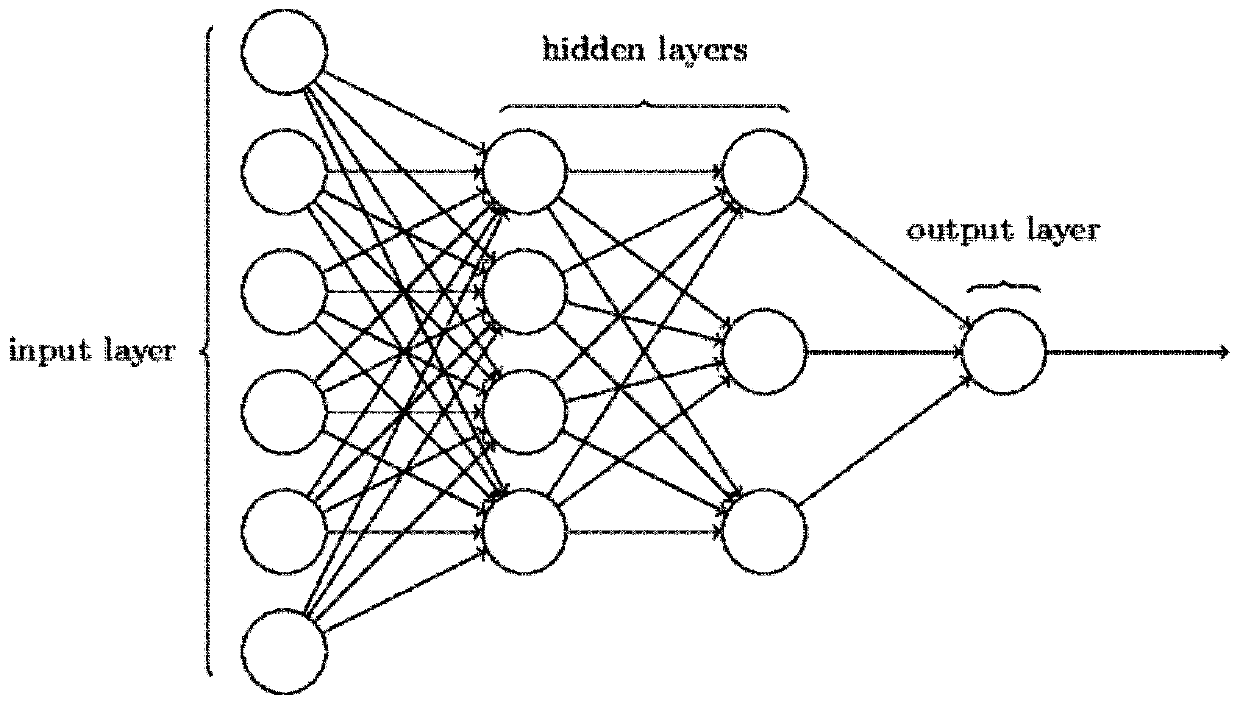
The invention discloses a brain signal identity recognition method based on a multilayer perceptron, and the method comprises the following steps: S1, collecting EEG samples of all brain regions, carrying out the individual difference analysis of the waveforms of the EEG samples, and extracting Delta waveband signals in the EEG samples; and S2, preprocessing the EEG sample from which the Delta waveband signal is extracted, removing DC offset, and normalizing the sample signal; and S3, inputting the EGG sample into a structure based on a multi-layer perceptron for individual classification. Thebrain signals of different individuals are classified by adopting a multi-layer perceptron method, so that the classification precision and accuracy can be effectively improved.
Owner:NANJING UNIV OF POSTS & TELECOMM
Dual-architecture mode method for implementing application
InactiveCN109413181AReduce development costsEasy to deploy and maintainSoftware designTransmissionClient-sideBusiness logic
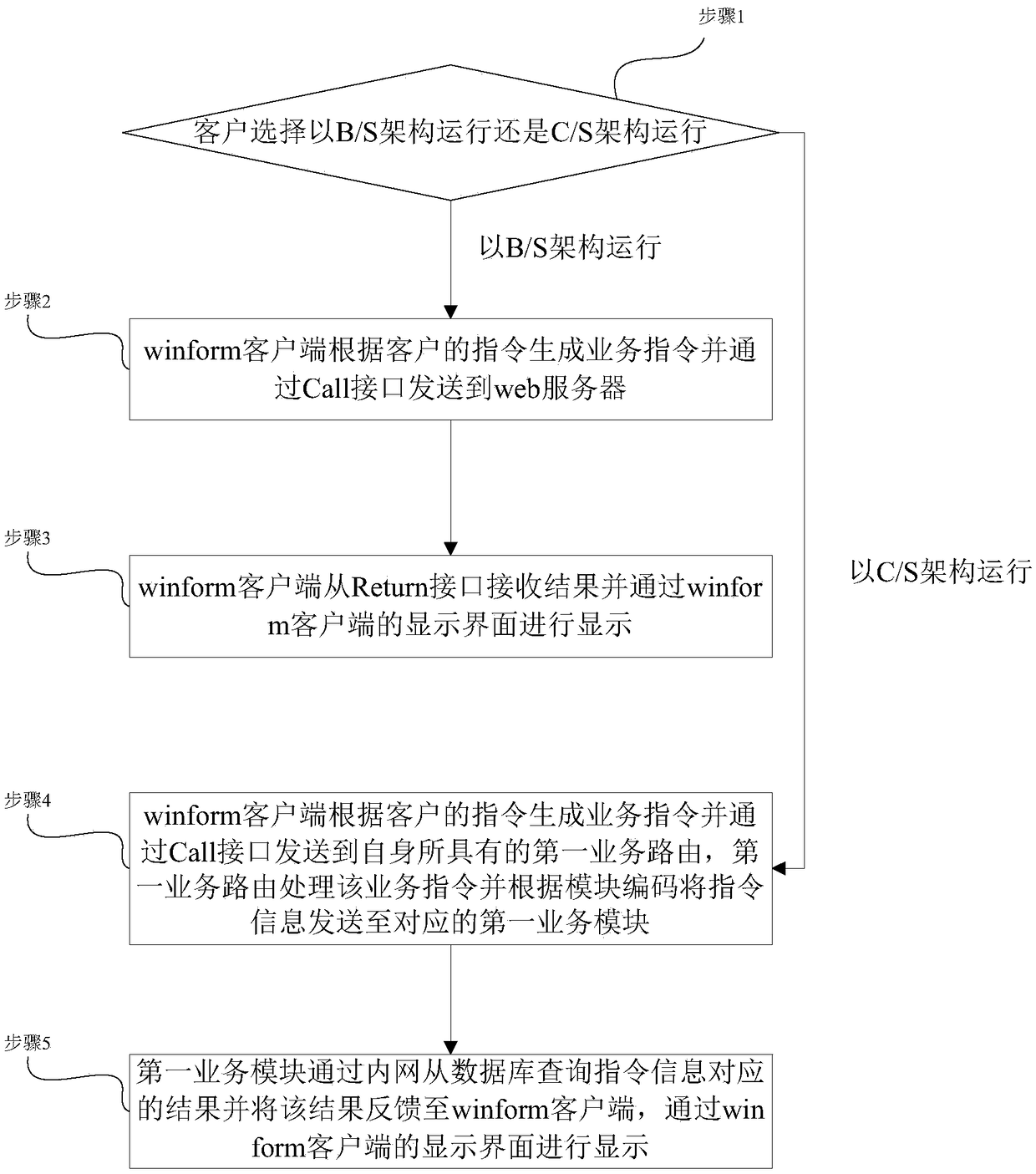
The invention belongs to the field of communication, and particularly relates to a dual-architecture mode method for implementing an application. The method relates to a winform client, a web server and a databse, and a first service router and a plurality of first service modules are arranged in the winform client; a second service router and a plurality of second service modules are arranged inthe web server; when a client selects to operate with a B / S architecture, the winform client sends a service instruction to the web server and receives a feedback result of the web server; and when the client selects to operate with a C / S architecture, the winform client allocates the service instruction to the corresponding first service module by the first service router and acquires a feedbackresult from the database by the first service module. The method combines the advantages of two architectures, and two architectures are simultaneously used in one program, so that the client can select to execute the B / S architecture or the C / S architecture according to different scene networks and select a corresponding service logic by the service router to implement a service.
Owner:广州中元软件有限公司
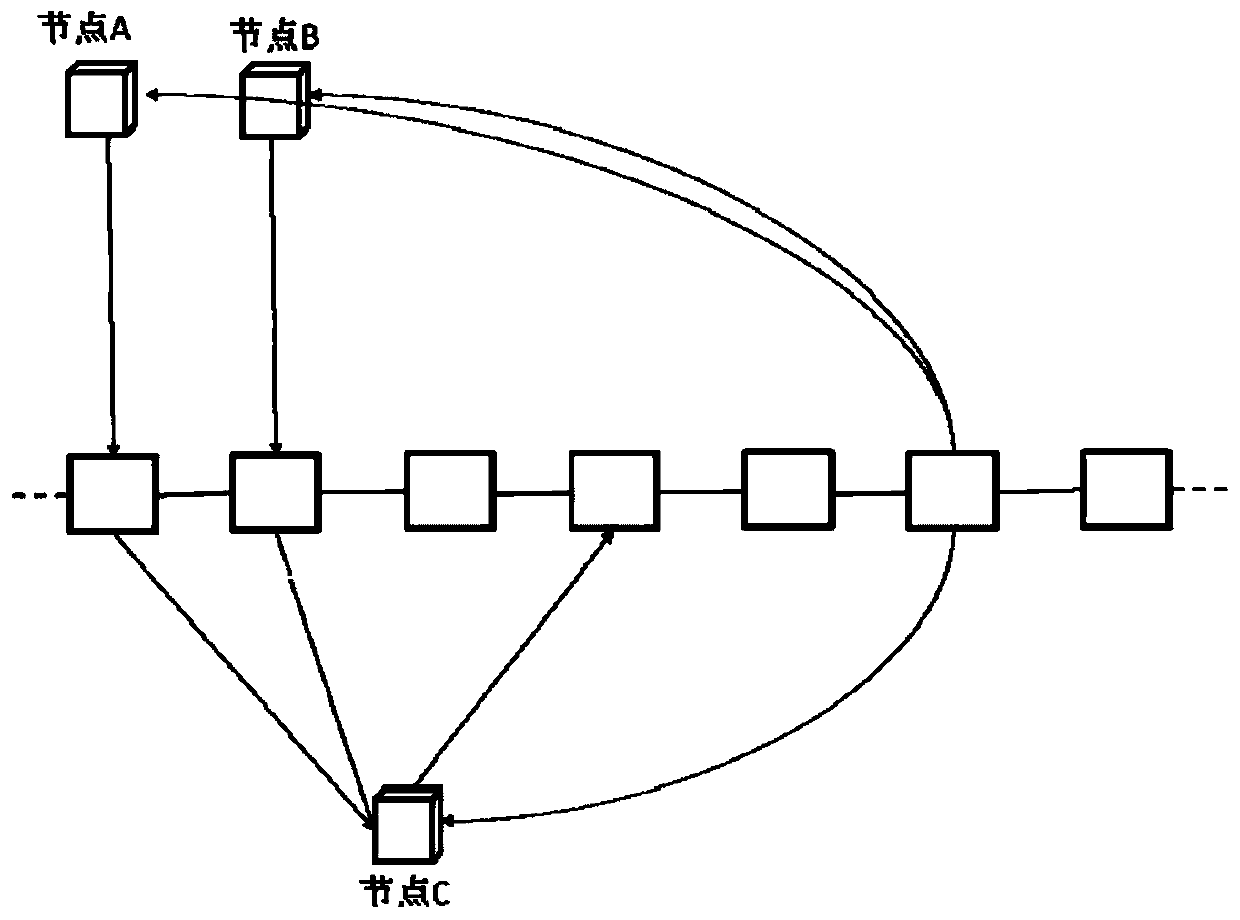
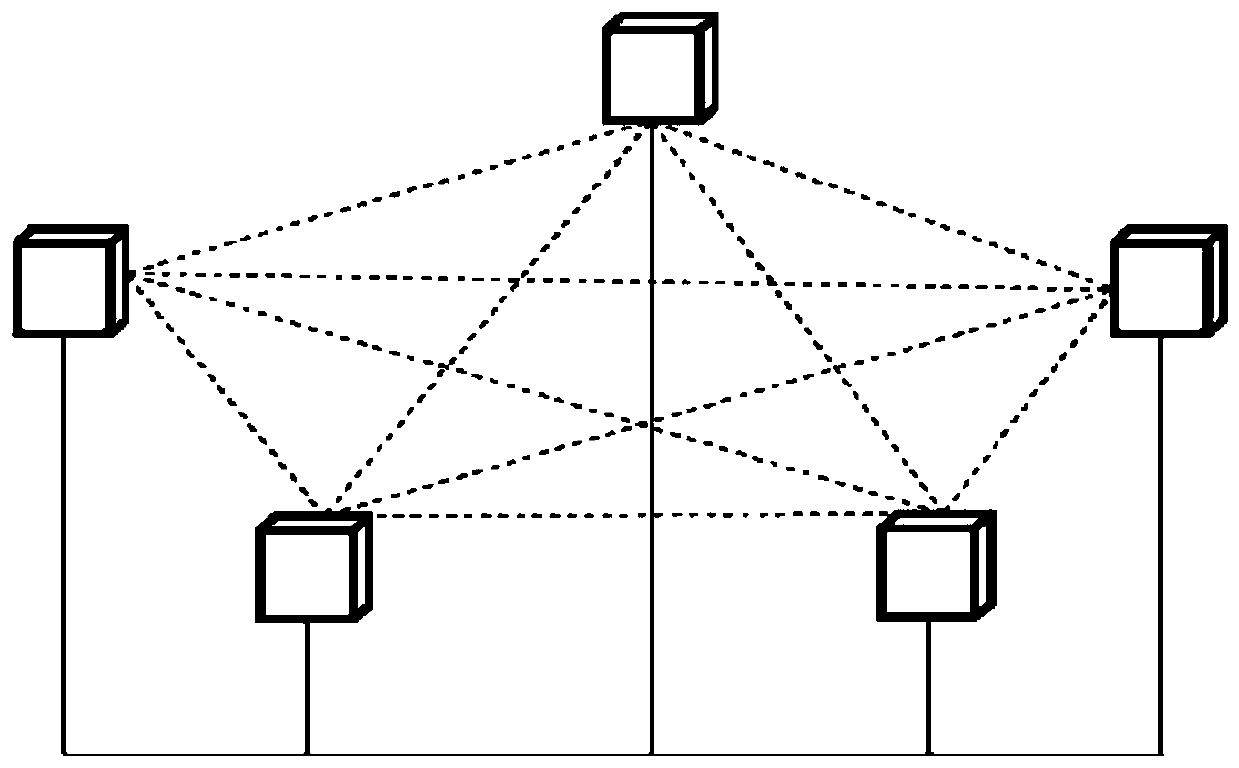
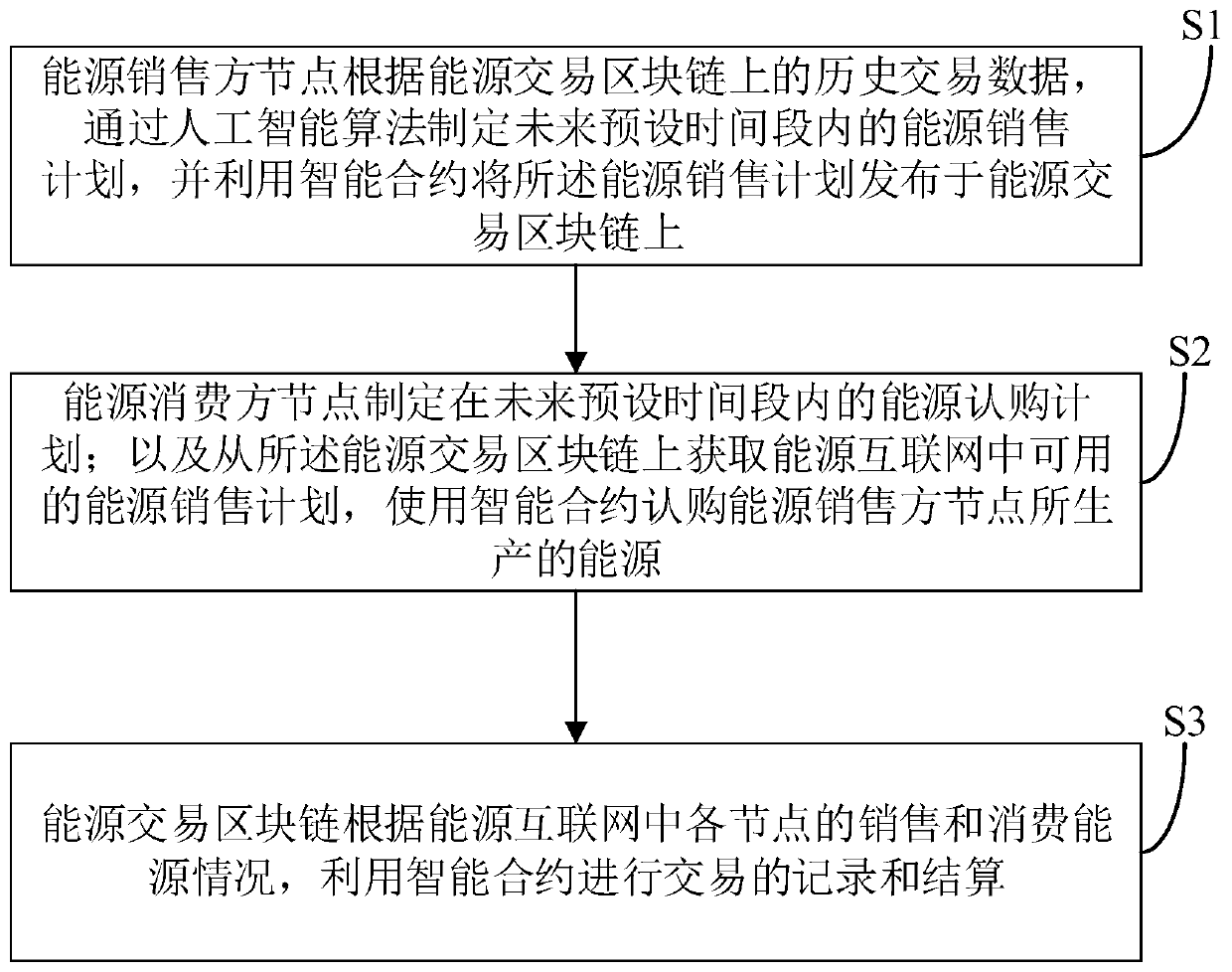
Energy transaction system and method based on block chain
PendingCN110956466ARealize distributed decentralizationWidely deployedPayment protocolsComputer networkEngineering
The embodiment of the invention discloses an energy transaction system and method based on a block chain. The energy transaction system comprises an energy Internet and an energy transaction block chain, wherein energy seller nodes are used for making an energy sales plan and publishing the energy sales plan on the energy transaction block chain; the energy transaction block chain is used for broadcasting the energy sales and subscription plan to all nodes, and performing transaction recording and settlement according to the sales and energy consumption conditions of each node; and energy consumer nodes are used for making an energy subscription plan, obtaining an available energy sales plan and subscribing the energy produced by the energy seller node. According to the embodiment of the invention, the distributed decentralization, trust removal, traceability, tampering difficulty, transparency, high reliability of the system and the characteristics of automation, batch execution and parallel processing of the transaction process of the energy transaction platform are realized by utilizing the characteristics of the blockchain, artificial intelligence, the Internet of Things and the intelligent contract, and the wide deployment of the energy transaction platform between nodes is facilitated.
Owner:国家电网有限公司大数据中心
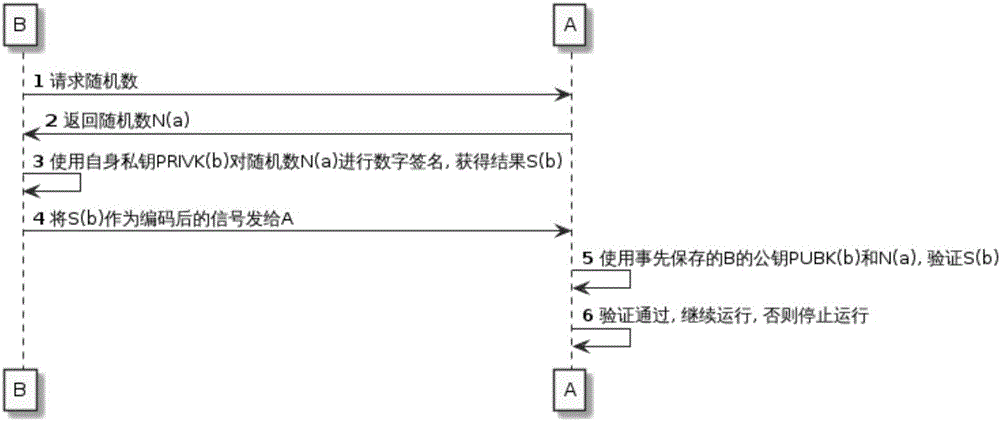
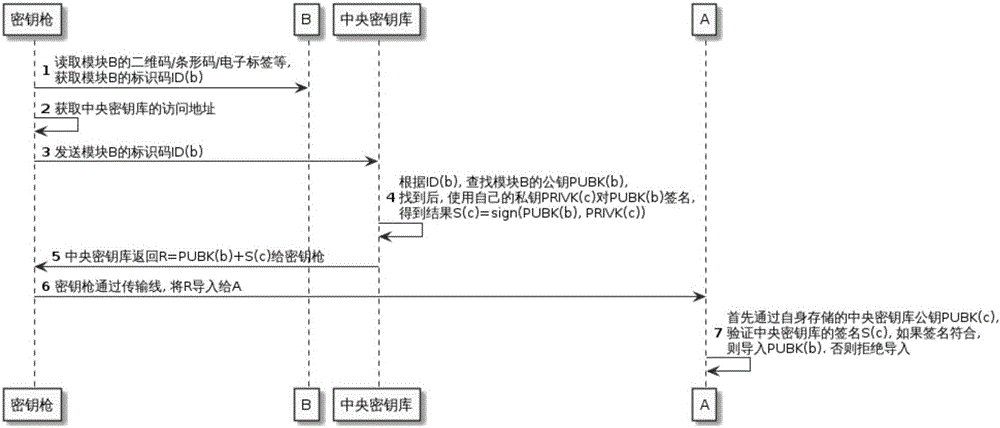
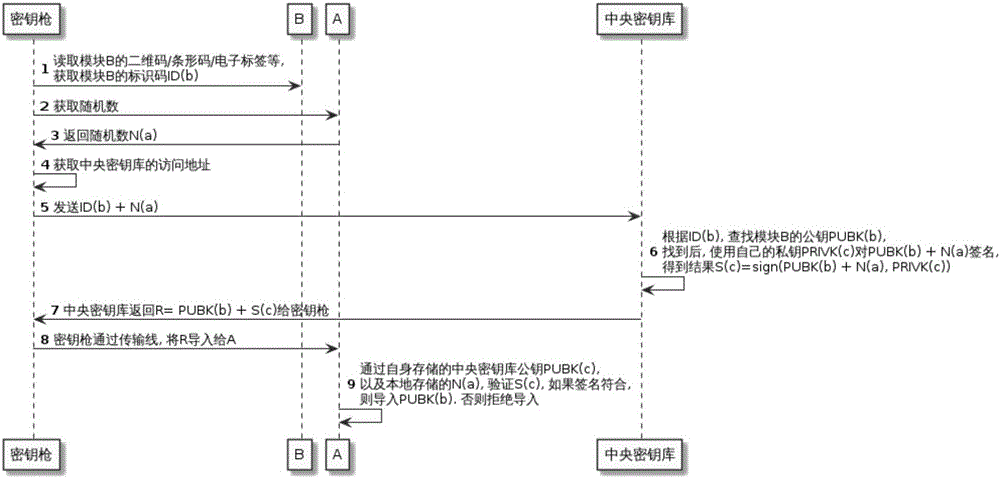
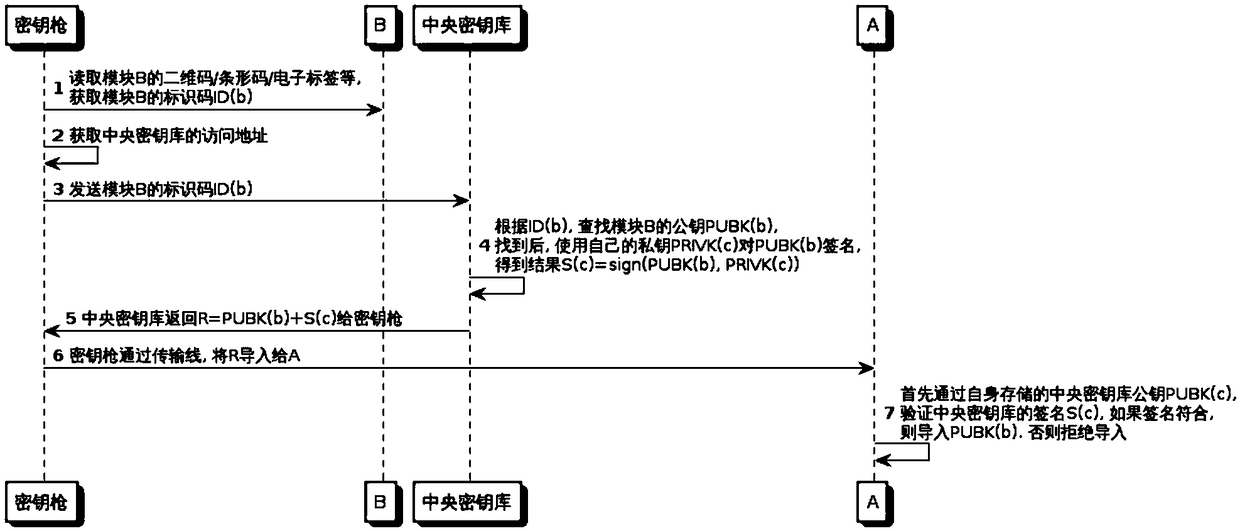
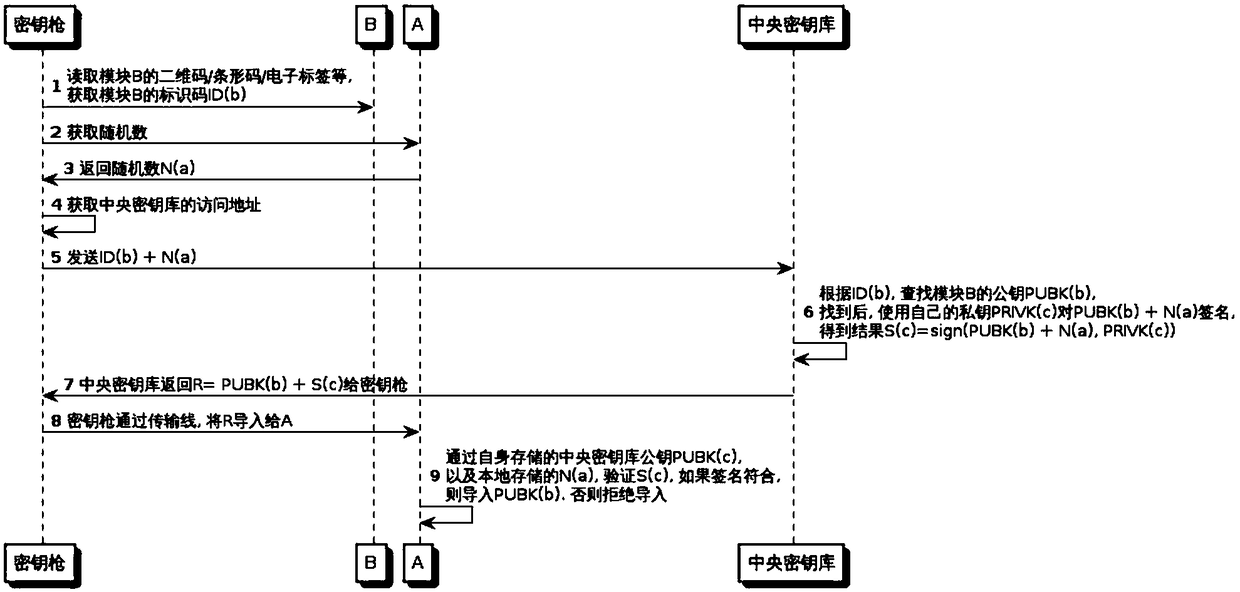
Offline key injection system and method
ActiveCN105959112ARealize mutual recognitionReliable importKey distribution for secure communicationComputer moduleData content
The invention discloses an offline key injection system. The offline key injection system comprises a key injection gun and a central key store; the key injection gun comprises an identification code reader, a display module, a keyboard module, a connection transmission module and a network communication module; and public and private keys of central distributors and public keys of managed equipment or modules are stored in the central key store. The invention further discloses an offline key injection method. Due to the method, reliable import of the public keys of the equipment in a non-reliable environment can be ensured. In the whole process, the key gun is only used as a carrier for interacting data with the central key store; the key gun itself does not participate in generation and modification of data contents; therefore, equipment maintenance / replacement place and personal requirements are greatly simplified.
Owner:江苏先安科技有限公司
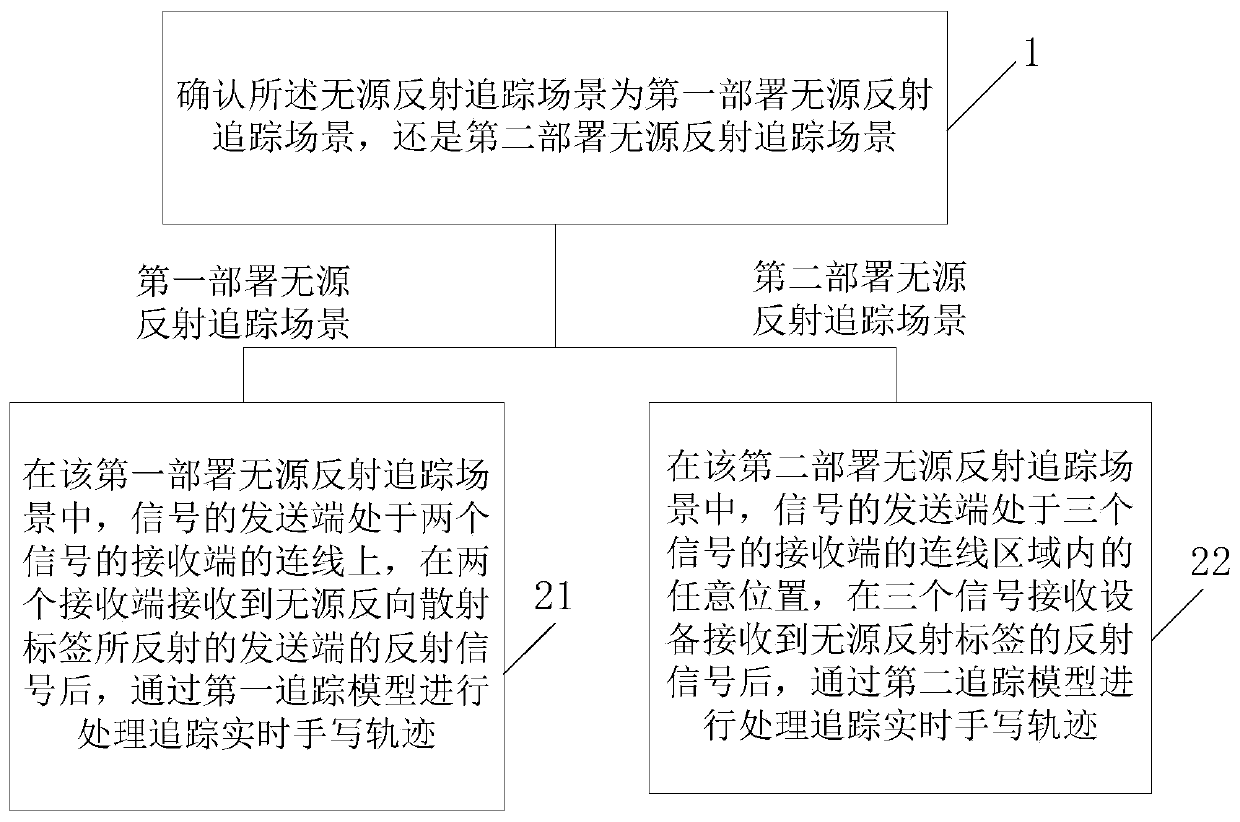
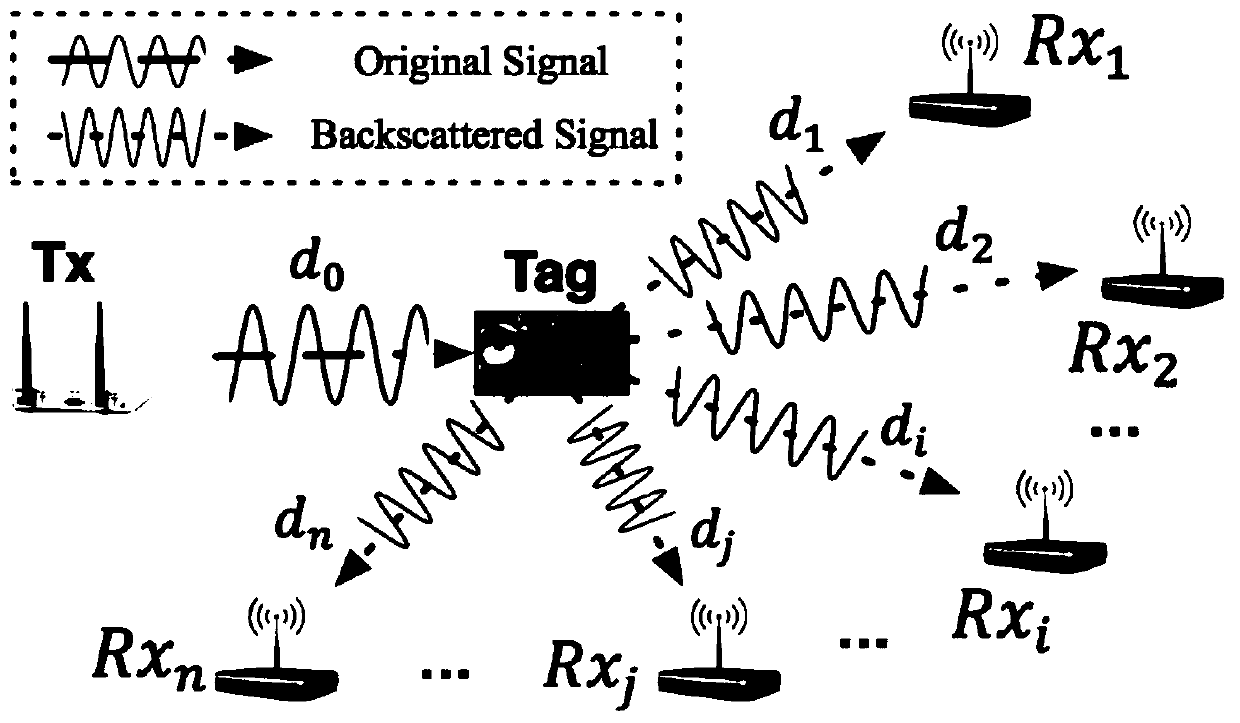
High-precision real-time handwritten trajectory tracking method based on passive reflected signals
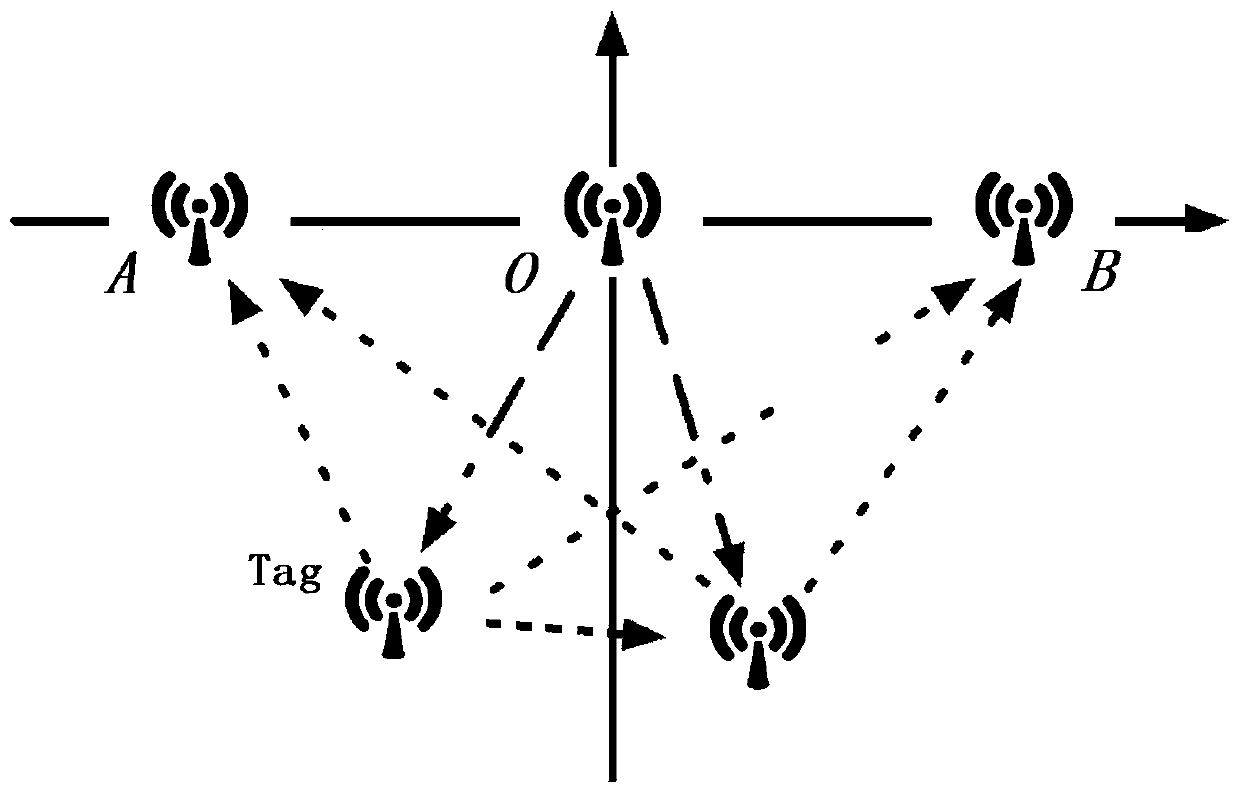
ActiveCN110133584AIncrease sampling rateWidely deployedPosition fixationHigh level techniquesTracking modelReal-time computing
The invention discloses a high-precision real-time handwritten trajectory tracking method based on passive reflected signals, which is used for a first deployment passive reflection tracking scene including a passive backscatter tag, a signal transmitting end and two signal receiving ends and a second deployment passive reflection tracking scene including a passive backscatter tag, a signal transmitting end and three signal receiving ends; the method comprises the following steps: step a, confirming that the passive reflection tracking scene is the first deployment passive reflection trackingscene or the second deployment passive reflection tracking scene; if being the first deployment passive reflection tracking scene, performing a step b; if being the second deployment passive reflection tracking scene, performing a step c; step b, processing to track the real-time handwritten trajectory through a first tracking model; and step c, processing to track the real-time handwritten trajectory through a second tracking model. According to the tracking method, millimeter-level high-precision trajectory tracking can be realized with low cost and a simple system.
Owner:UNIV OF SCI & TECH OF CHINA
GGSN capacity overload emergency safeguard method based on IP address pool
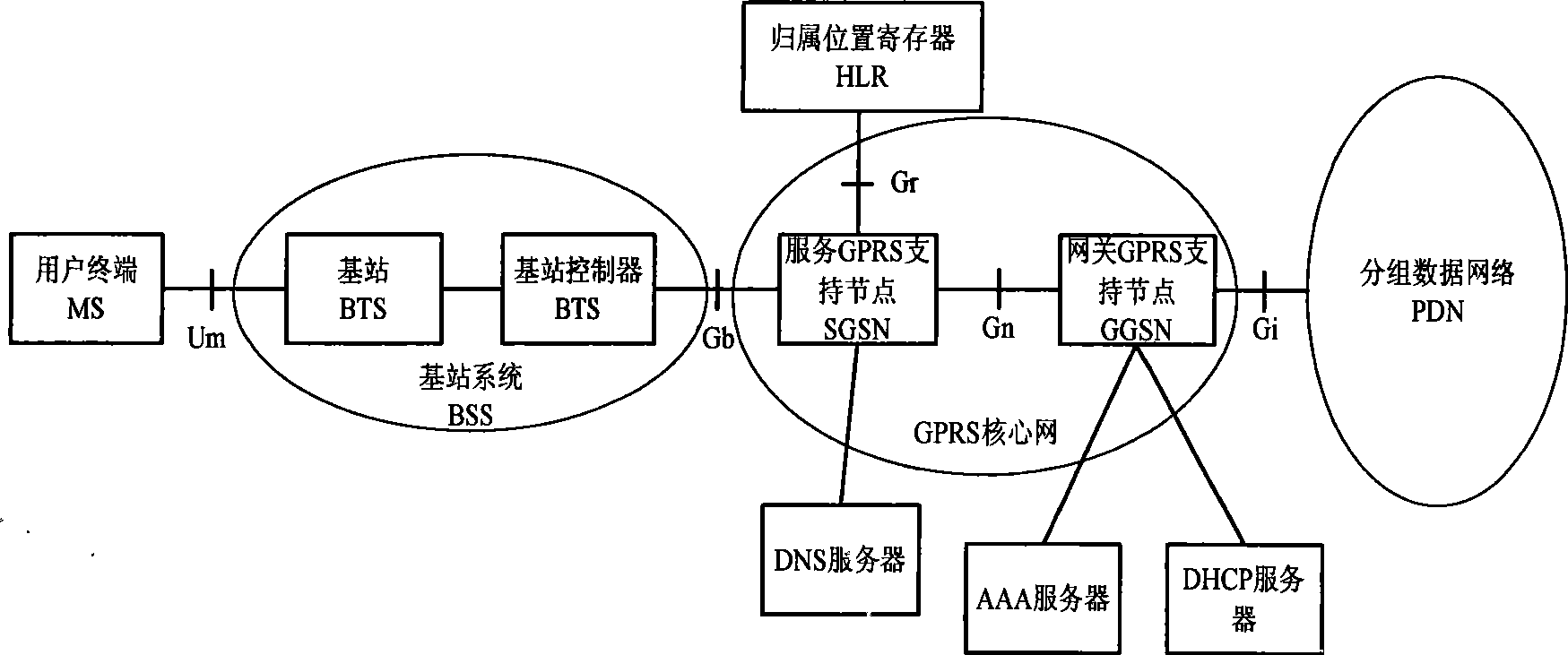
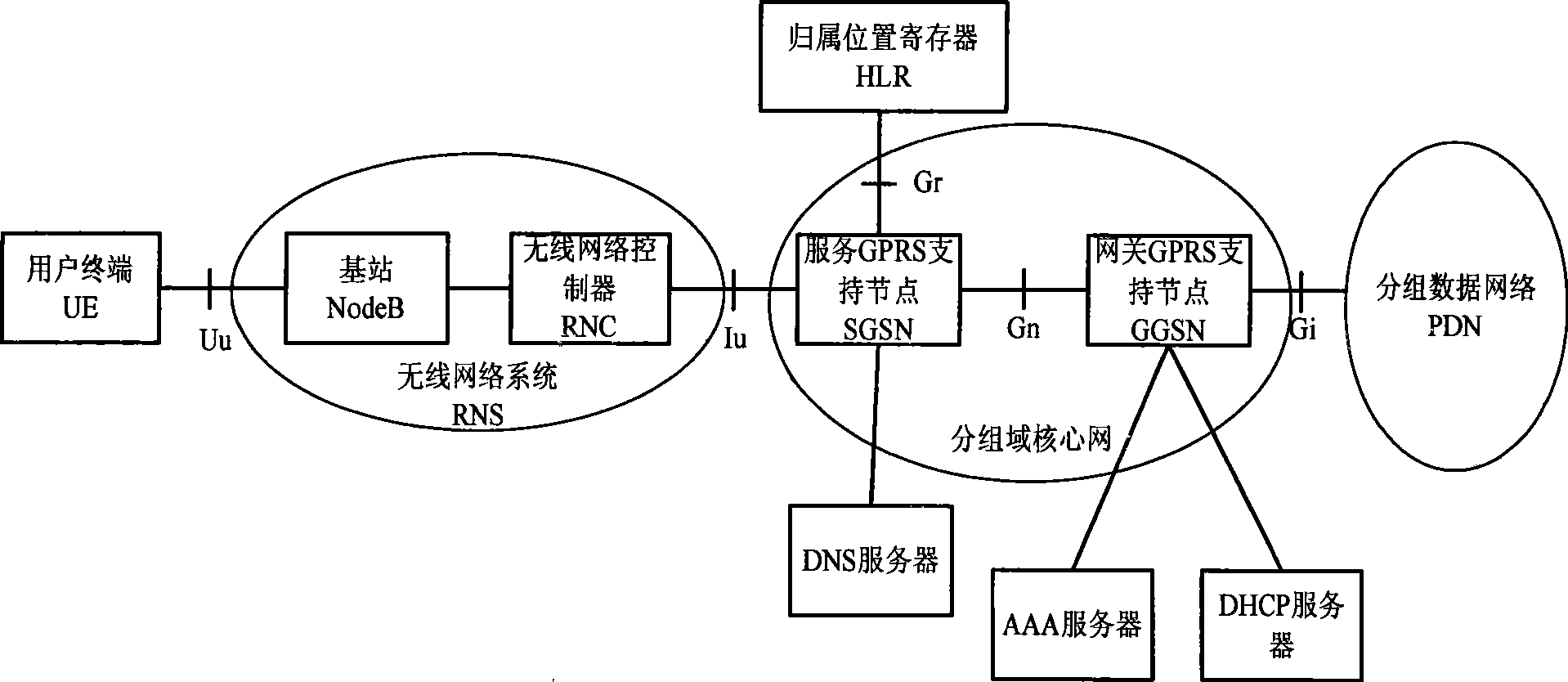
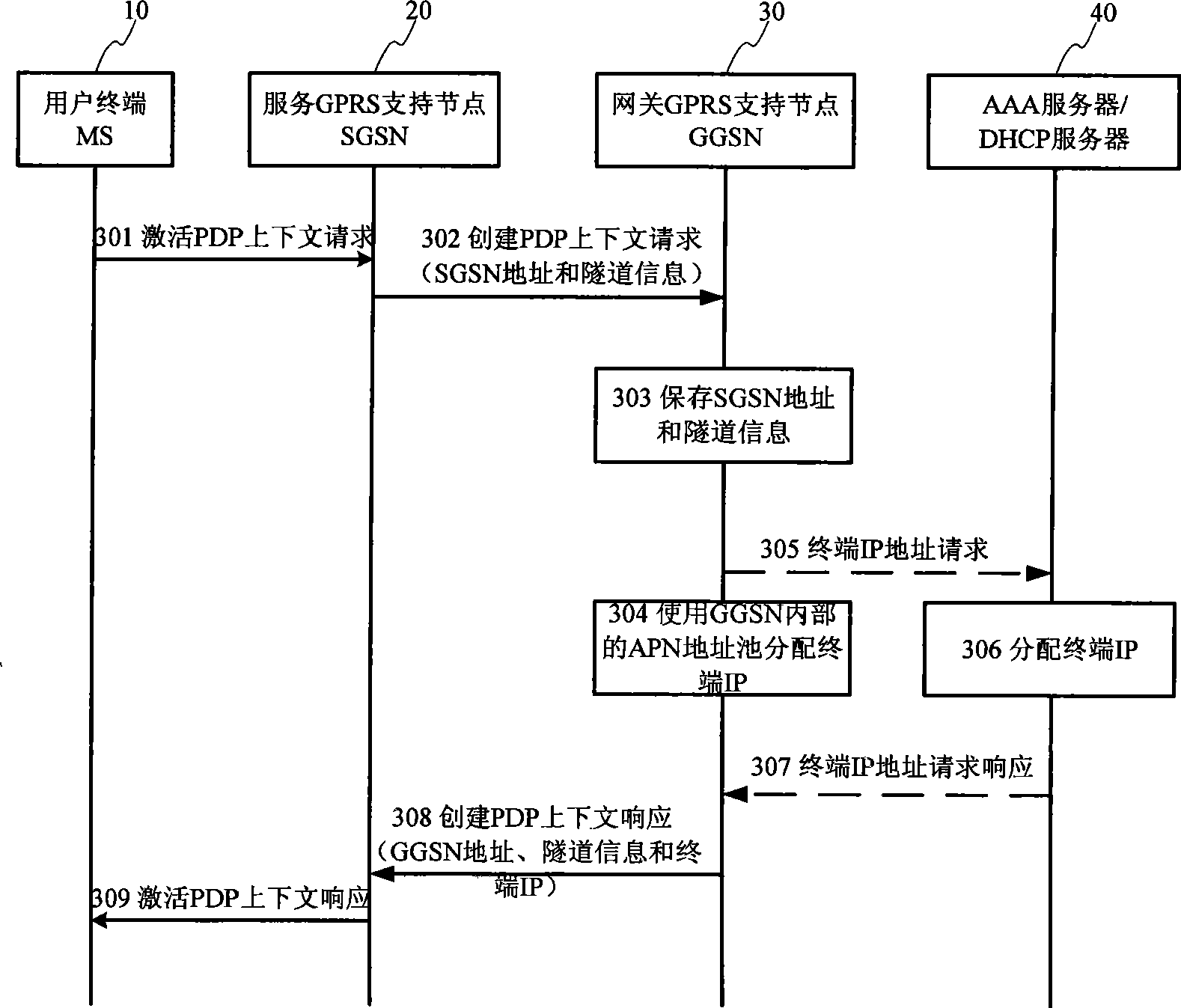
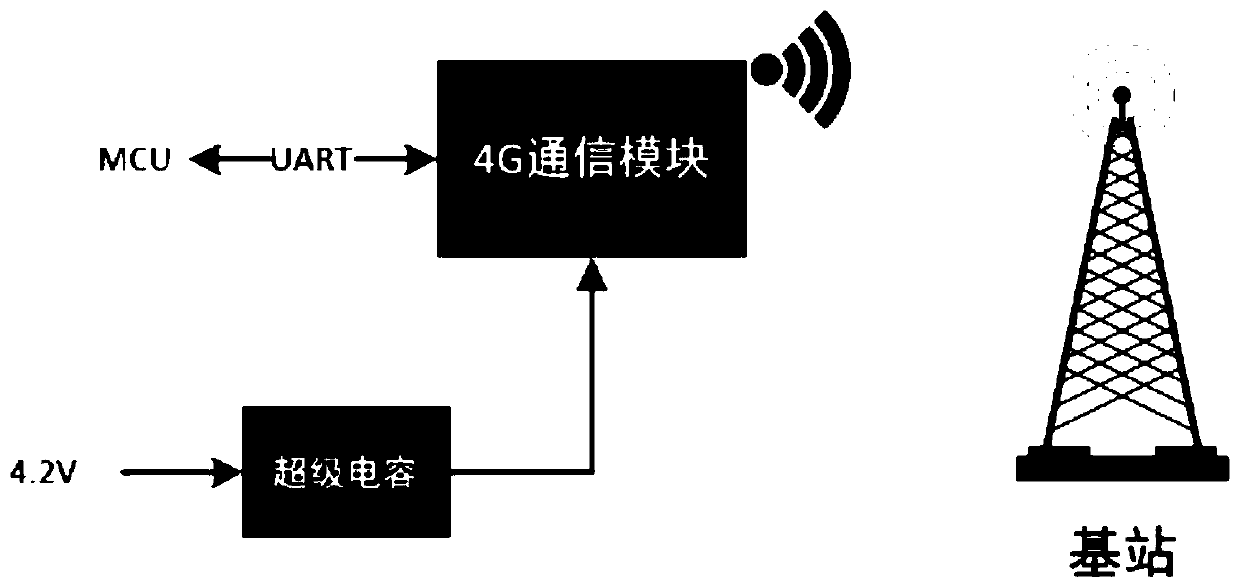
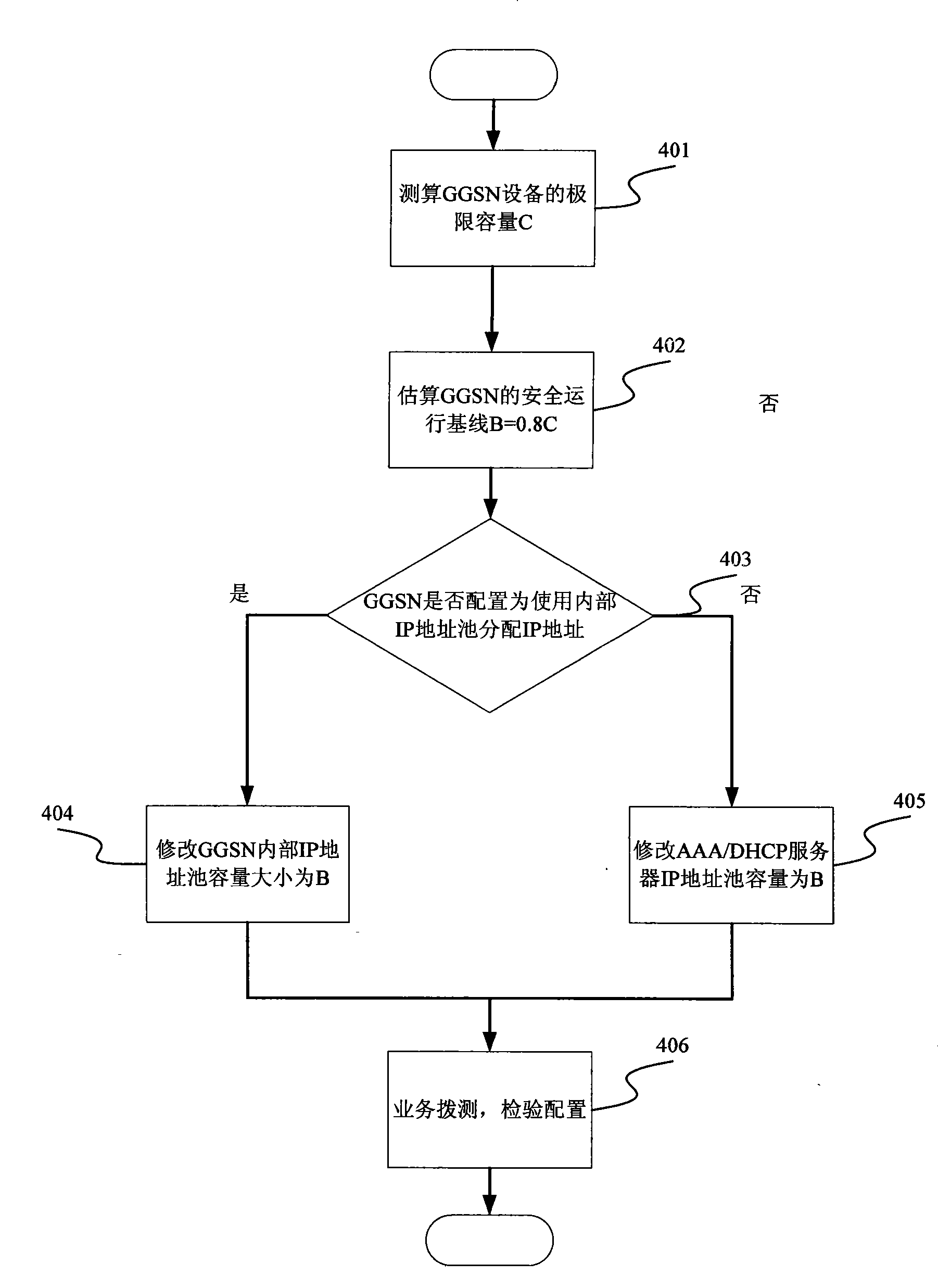
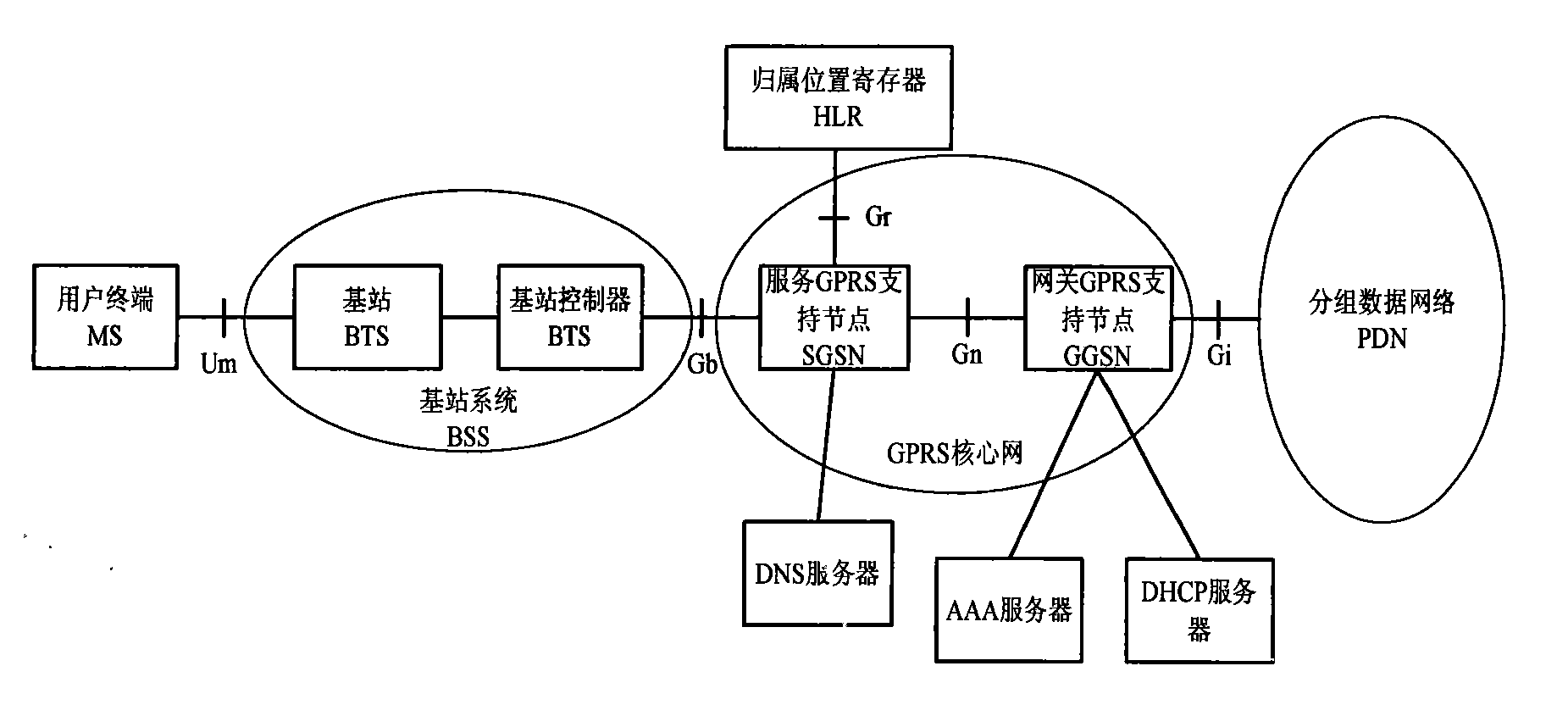
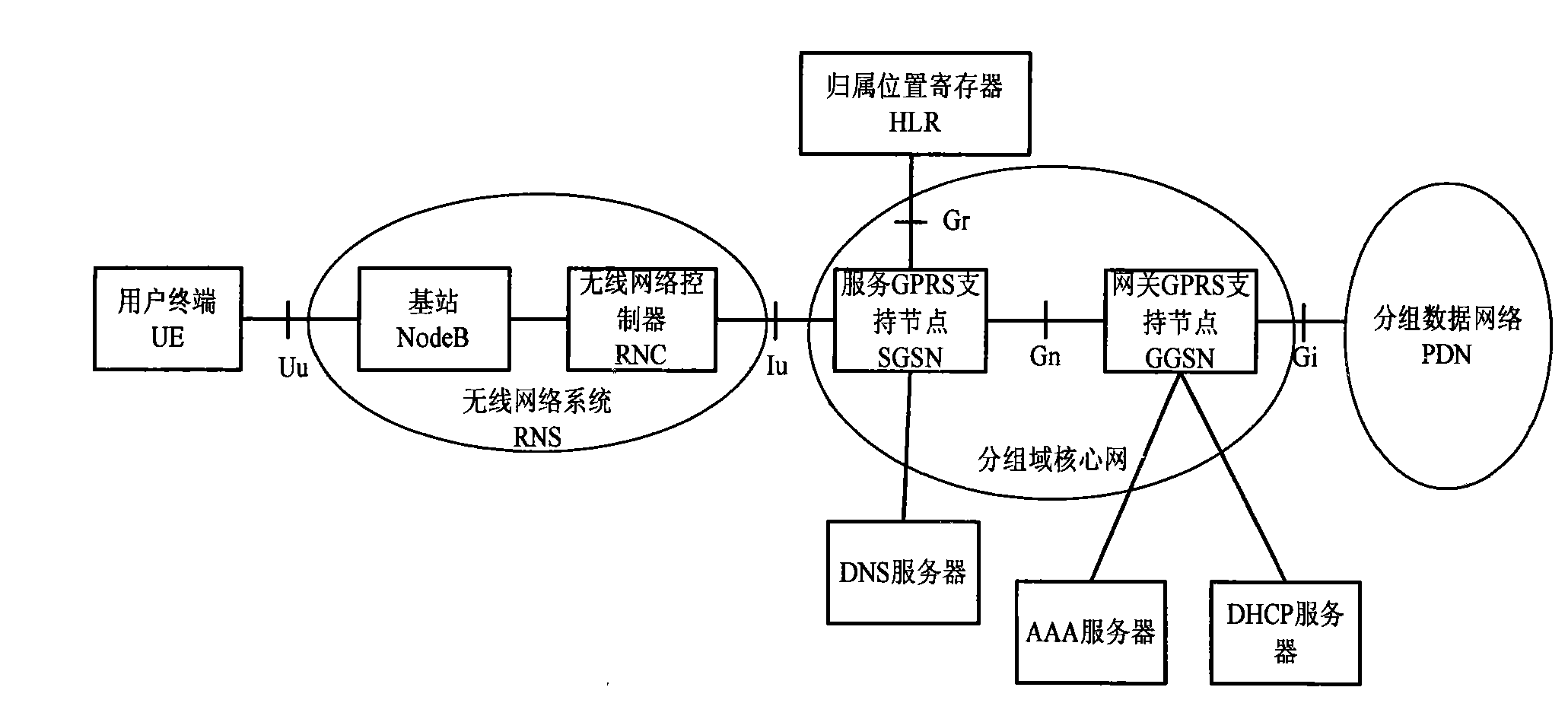
ActiveCN101426182AGuaranteed service qualityWidely deployedNetwork traffic/resource managementMessaging/mailboxes/announcementsQuality of serviceIp address
The present invention provides a method for guaranteeing GGSN capability at a condition that the load of network operation capacity is high. The method comprises the following steps: measuring a safety operation capacity of GGSN device, the safety operation capacity is a maximum capacity limit which can be obtained by the GGSN device; setting a safety threshold as a base line of the GGSN device based on the safety operation capacity; restricting the capacity of an IP address pool in the safety threshold to guarantee that the number of PDP text subscriber in the GGSN device is in the base line of safety operation; and executing full-service testing after the configuration operation to guarantee the rightness of data modification. The method according to the invention actively restricts the capacity of GGSN access through adjusting the magnitude of capacity of IP address pool at the condition that the load of network operation capacity is high. The method according to the invention guarantees that the device can work normally at the condition of high load and guarantees the service quality of access subscriber.
Owner:CHINA MOBILE GRP GUANGDONG CO LTD
Method and system for target detection using MIMO radar
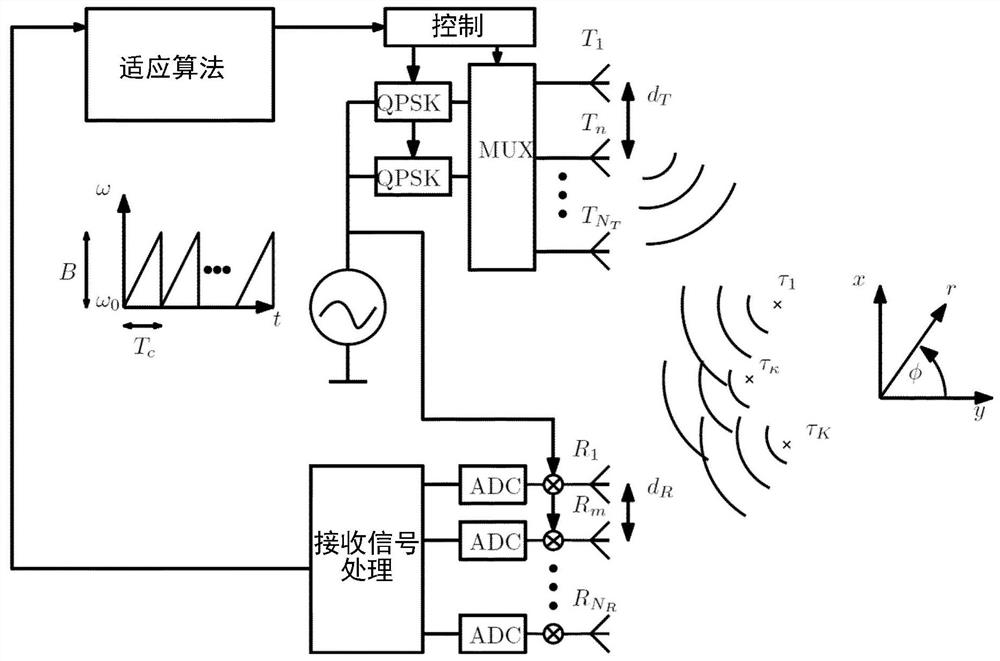
PendingCN111971580AWidely deployedImprove comfortRadio wave reradiation/reflectionSignal processing circuitsLinear arrays
A method of sensing a target in a target detection system is provided. The method comprises processing circuitry, a multiplexer coupled to the processing circuitry and to a plurality NT of transmit antennas forming a sparse transmit uniform linear array, ULA, the multiplexer being configured to generate multiplexed and phase modulated transmit signals based on signals from a local oscillator, theprocessing circuitry being further coupled for receiving signals via a plurality of receive antennas forming a dense receive ULA. The method comprises transmitting the plurality of transmit signals via the transmit antennas so as to form a general radiation pattern corresponding to a block circulant probing signal matrix and receiving via the receive antennas receive signals resulting from backscattering of the plurality of transmit signals transmitted towards K targets. The method further comprises processing the received reflection signals to determine the presence, range and / or angular position of a target within a field of view of the transmit antennas. A corresponding target detection system and a vehicle incorporating the target detection system are also disclosed.
Owner:IEE INT ELECTRONICS & ENG SA +1
Method for realizing safety on-chip intelligent members
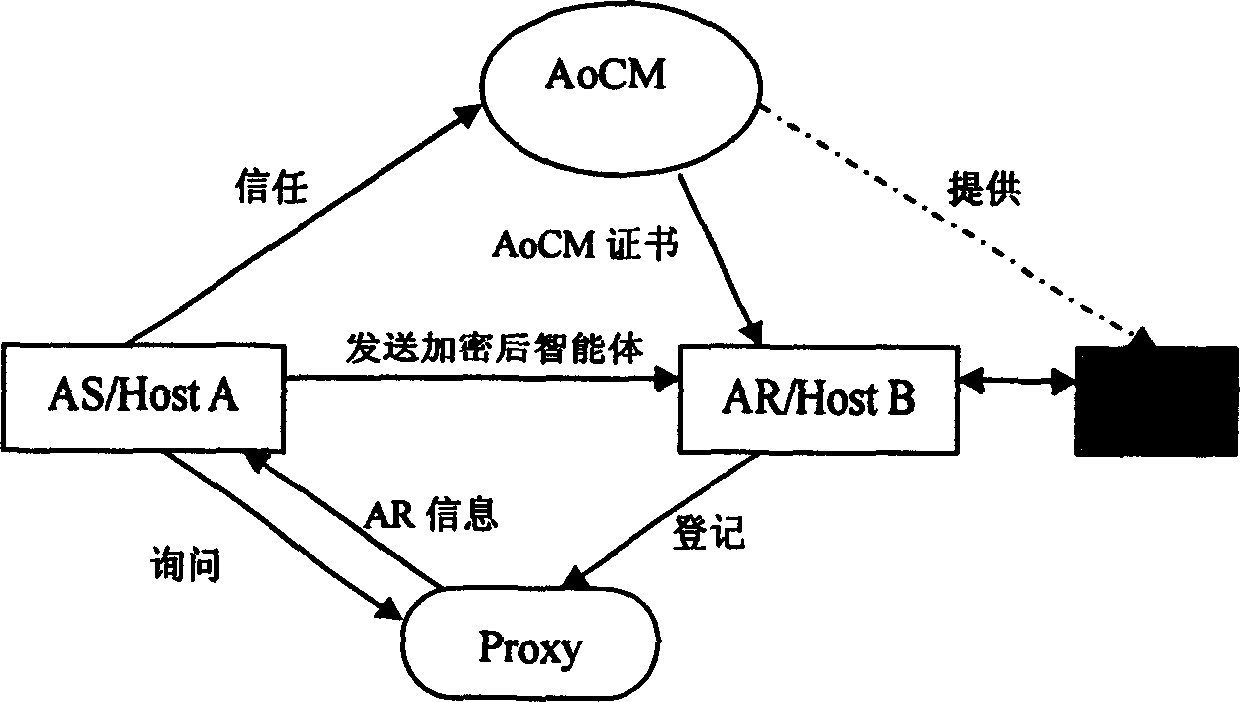
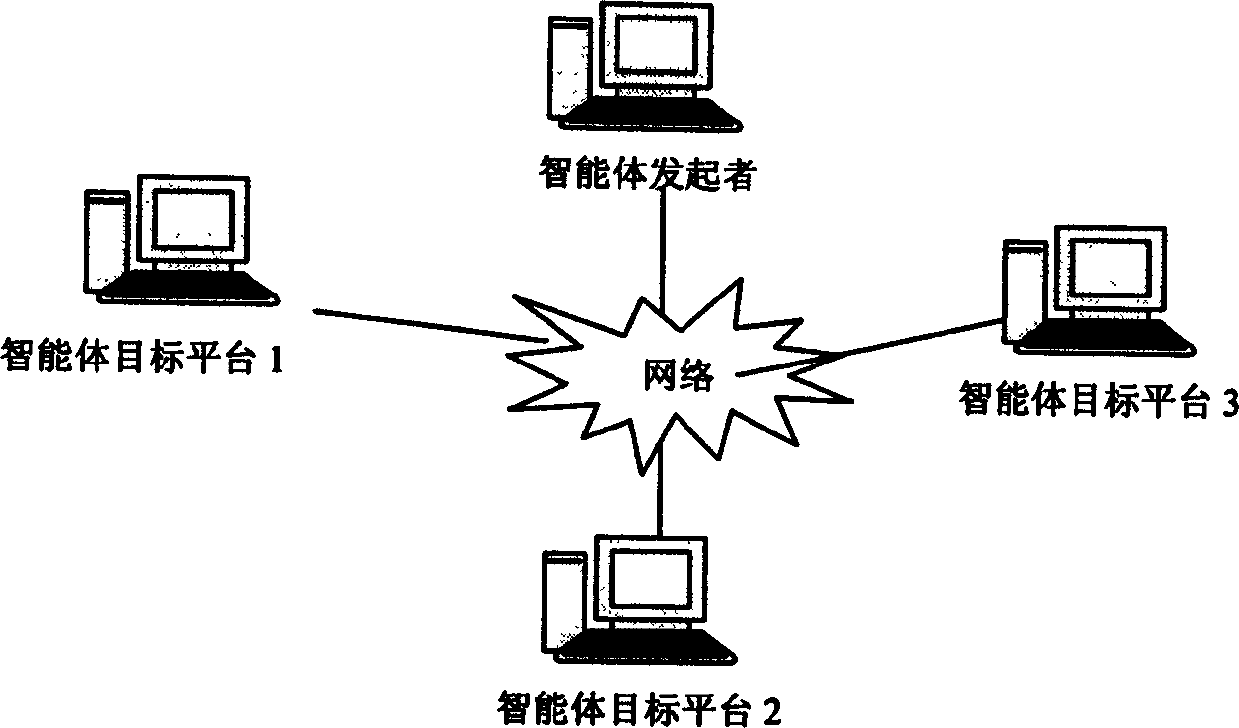
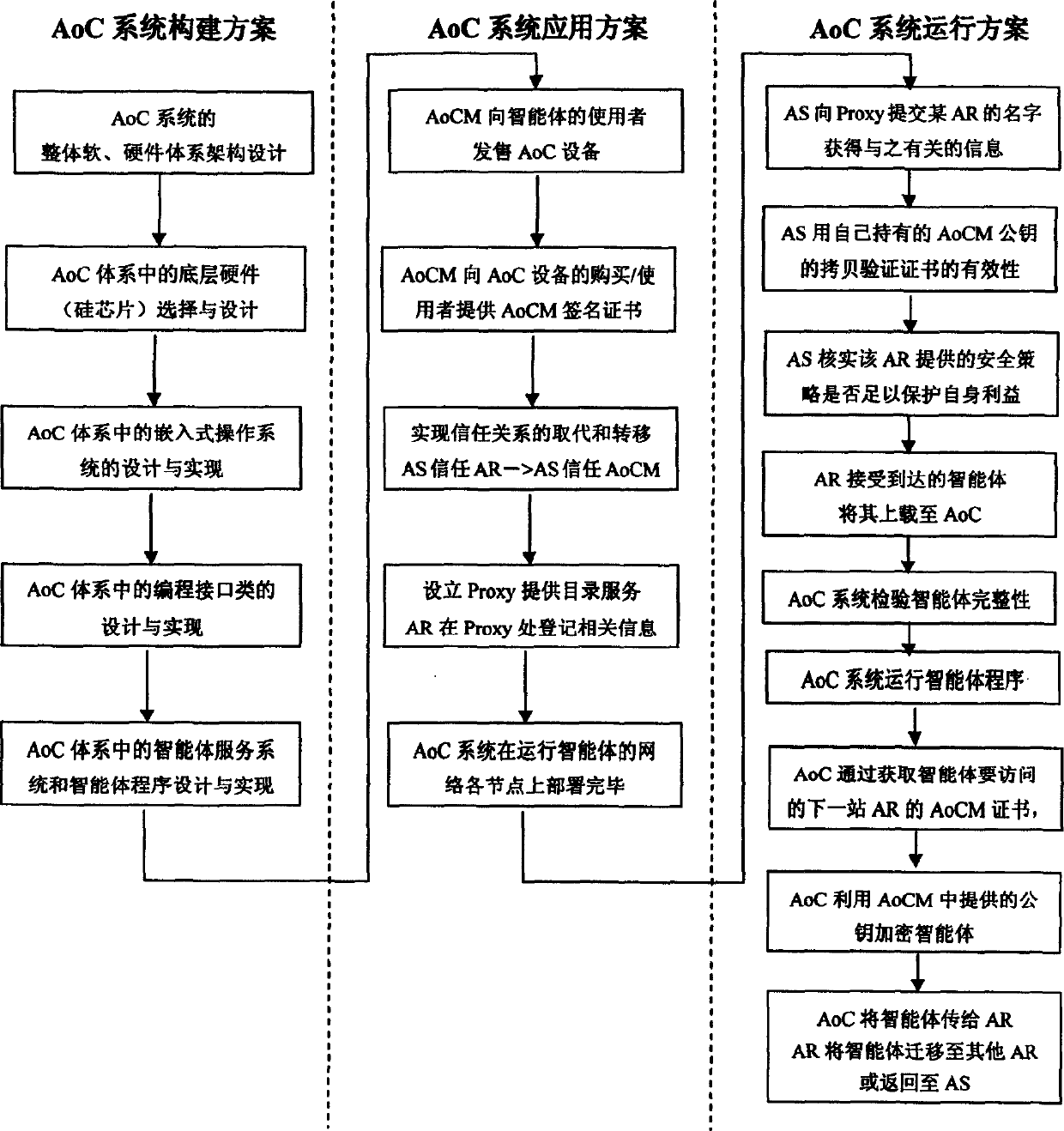
InactiveCN1655523AOperating limitWill not pose a safety hazardDigital data processing detailsData switching networksComputer scienceWeb environment
This invention relates to safe upper intelligent scheme used in open network, which adopts integration chip as hardware base to providing safe executive environment to realize the application system technique scheme in the network. The scheme adopts integration chip as intelligent bottom hardware executive environment and the scheme comprises three parts: AoC system forming scheme, AoC system application scheme and AoC system running scheme.
Owner:NANJING UNIV OF POSTS & TELECOMM
Single-phase multi-channel low-voltage user-side power outage monitoring device
PendingCN110672959APower outage status monitoringReport in timeParticular environment based servicesElectrical testingEngineeringReliability engineering
The invention relates to a single-phase multi-channel low-voltage user-side power outage monitoring device. The single-phase multi-channel low-voltage user-side power outage monitoring device comprises a measurement module, a power module and a communication module. The measurement module is used for monitoring a power outage state of a multi-channel single-phase power supply. The communication module is used for reporting power outage information monitored by the measurement module, and the power module provides the power for the measurement module and the communication module. The single-phase multi-channel low-voltage user-side power outage monitoring device can perform monitoring on up to 15 single-phase power supplies at the same time, and can still maintain normal work and discriminate and report the power outage state in the event of power outage.
Owner:BEIJING KEDONG ELECTRIC POWER CONTROL SYST +2
GGSN capacity overload emergency safeguard method based on IP address pool
ActiveCN101426182BGuaranteed service qualityWidely deployedNetwork traffic/resource managementMessaging/mailboxes/announcementsQuality of serviceIp address
Owner:CHINA MOBILE GRP GUANGDONG CO LTD
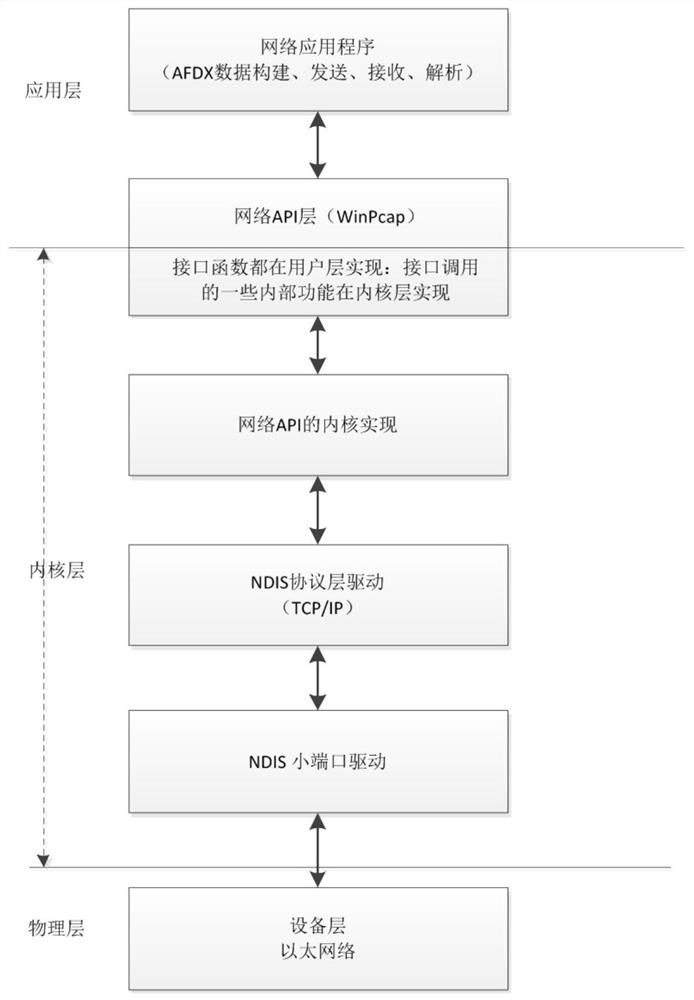
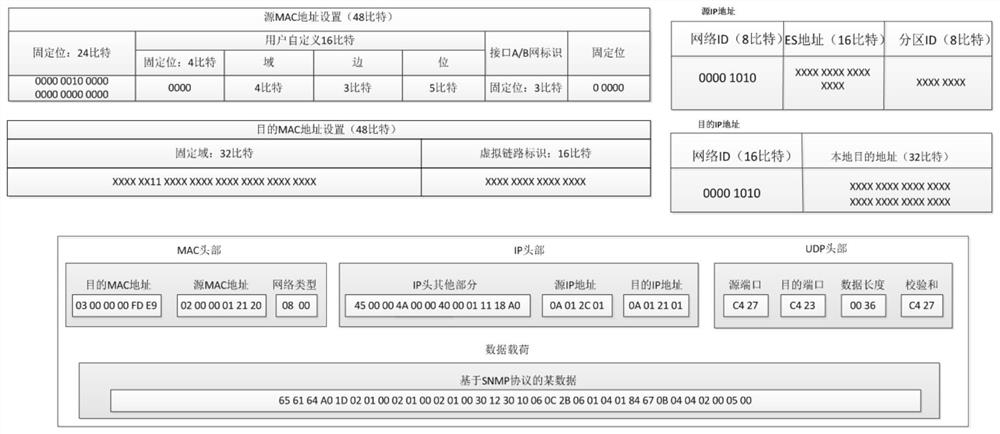
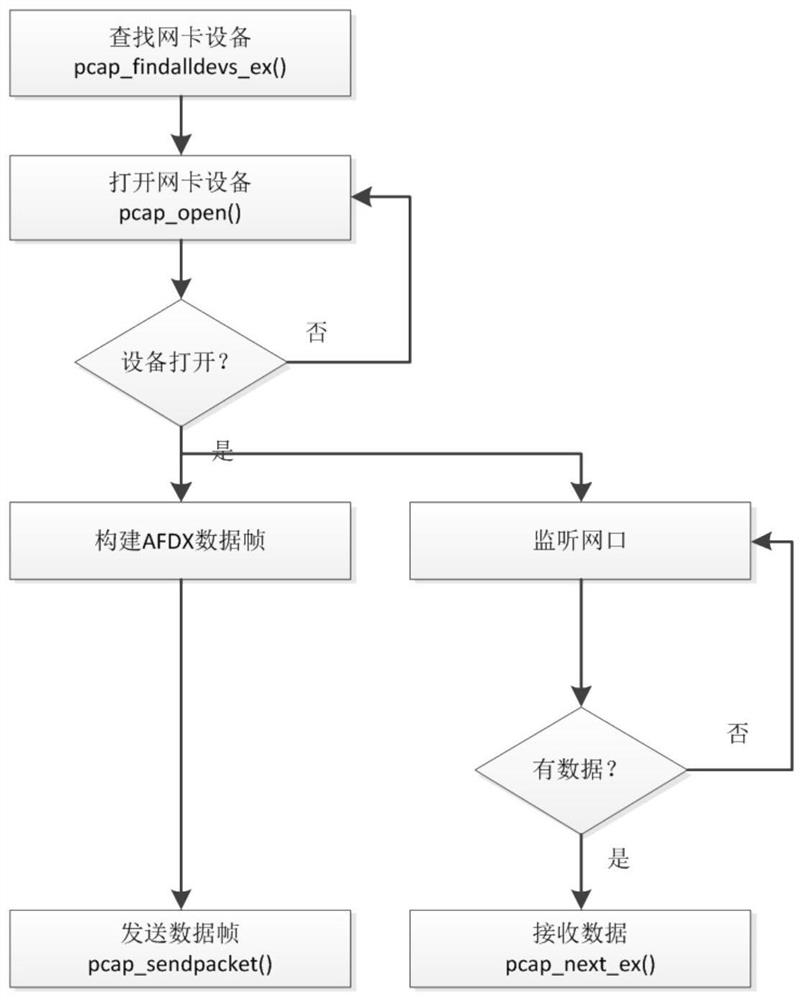
AFDX protocol stack construction method based on WinPcap
The invention discloses an AFDX protocol stack construction method based on WinPcap, the construction, sending, receiving and analysis of AFDX data frames are completed in an application layer, and the method is characterized in that when the AFDX data frames are sent and received, firstly, a WinPcap library function pcap_finaldeves _ex() is used for searching for network card equipment of targetequipment; the selected network card is opened through pcap_opens(), and parameters such as effective reservation length and reading time of the captured data packet at the same time are set; and on the basis that the network card is successfully opened, the pcap_sendpacket()is subjected to calling to send the AFDX data frame, and the pcap_next_ex()is subjected to calling to receive the AFDX dataframe. According to the invention, the data frame in the network card is captured by using a common commercial computer WinPcap, and the data frame conforming to the AFDX protocol can be sent on the basis of not using an AFDX board card.
Owner:CHINESE AERONAUTICAL RADIO ELECTRONICS RES INST
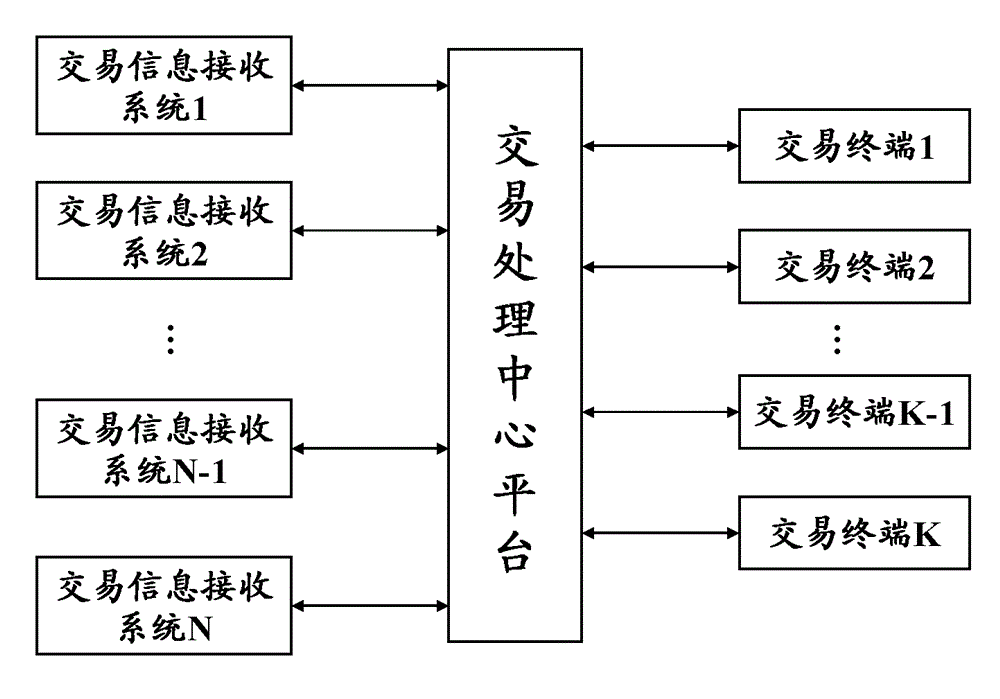
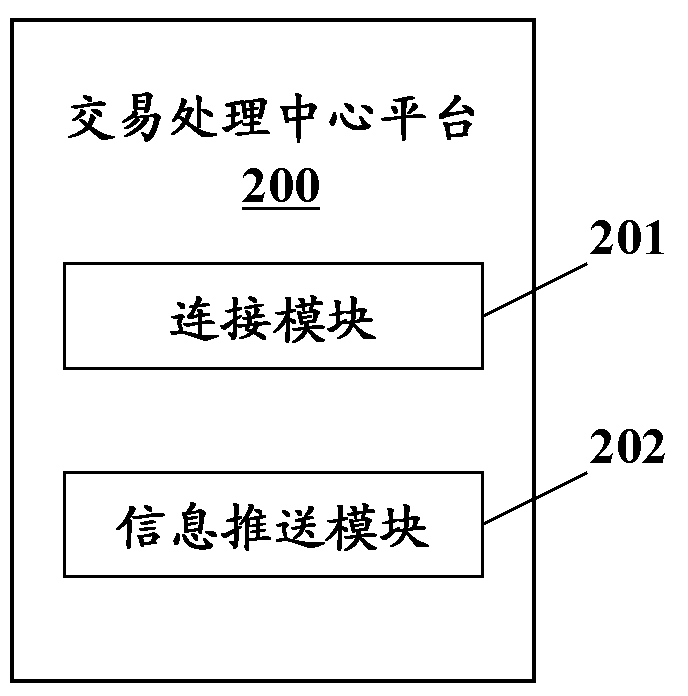
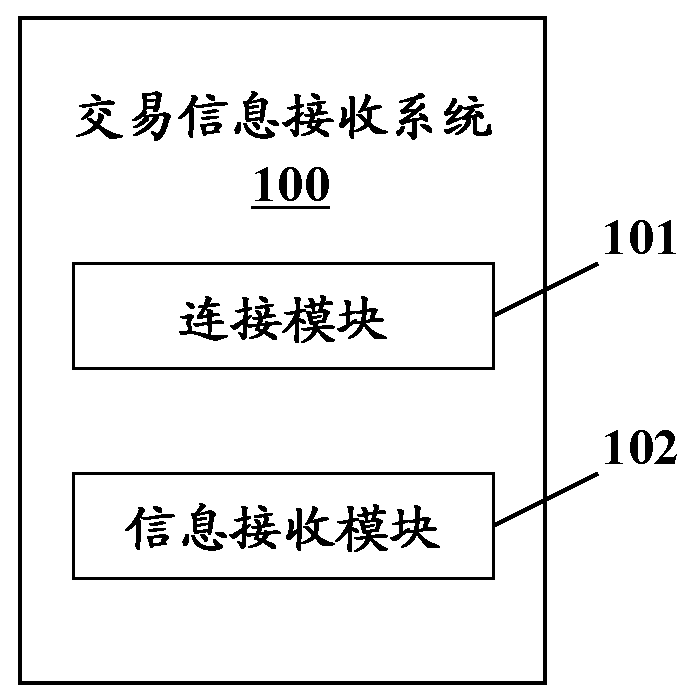
Transaction information receiving system and transaction processing center platform
InactiveCN104978654AFast and effective real-time acquisitionSimple structureProtocol authorisationComputer networkFinancial transaction
The invention provides a transaction information receiving system, which comprises a connection module and an information receiving module, wherein the connection module is configured to initiate a connection request to a transaction processing center platform so as to establish dedicated communication connection with the transaction processing center platform; the information receiving module is configured to send a transaction asking request to the transaction processing center platform and receive a message which is a pushed to the receiving system and is associated with the transaction via the transaction processing center platform while the transaction terminal is acquired through the dedicated communication connection. In addition, the invention also provides the transaction processing center platform. The transaction processing center platform comprises the connection module and an information pushing module, wherein the connection module is configured to respond to the connection request from the transaction information receiving system to establish the dedicated communication connection with the transaction information receiving system; and the information pushing module is configured to respond to an asking request from the transaction information receiving system so as to push the message associated with the traction to the transaction information receiving system through the dedicated communication connection while the transaction terminal is acquired
Owner:UNIONPAY INT CO LTD
Personnel detection counting method based on deep learning
ActiveCN112381021AOvercoming the problem of insufficient deep feature extractionImprove recognition accuracyCharacter and pattern recognitionNeural architecturesVideo monitoringEngineering
The invention discloses a personnel detection counting method based on deep learning, and the method comprises the steps: 1, carrying out periodic collection of a video monitoring image, and detectingpersonnel based on a FiarMot algorithm; 2, extracting a region of interest of detection personnel and calculating an intersection ratio of the region of interest to a monitoring region; and 3, constructing an adaptive scale LSTM neural network, fusing a full connection layer and wavelet transform features, performing classification by using an SCN classifier, and evaluating and automatically adjusting a network scale according to an entropy loss value of a detection result. The network scale can be automatically adjusted according to the entropy loss value evaluation of the detection result,so that the self-optimization adjustment and reconstruction of the video personnel detection model can be realized, the video personnel detection rate of a specified area in different environments isimproved, and the actual requirements of accuracy and rapidness are met.
Owner:安徽一视科技有限公司
Self-adapted method for detecting the clock resetting based on the mode recognition
InactiveCN100450047CReduce limitationsImprove accuracyError detection/prevention using signal quality detectorData switching networksCluster algorithmData set
Owner:BEIJING UNIV OF POSTS & TELECOMM
A method to accelerate the first distribution of packets on the NFV platform
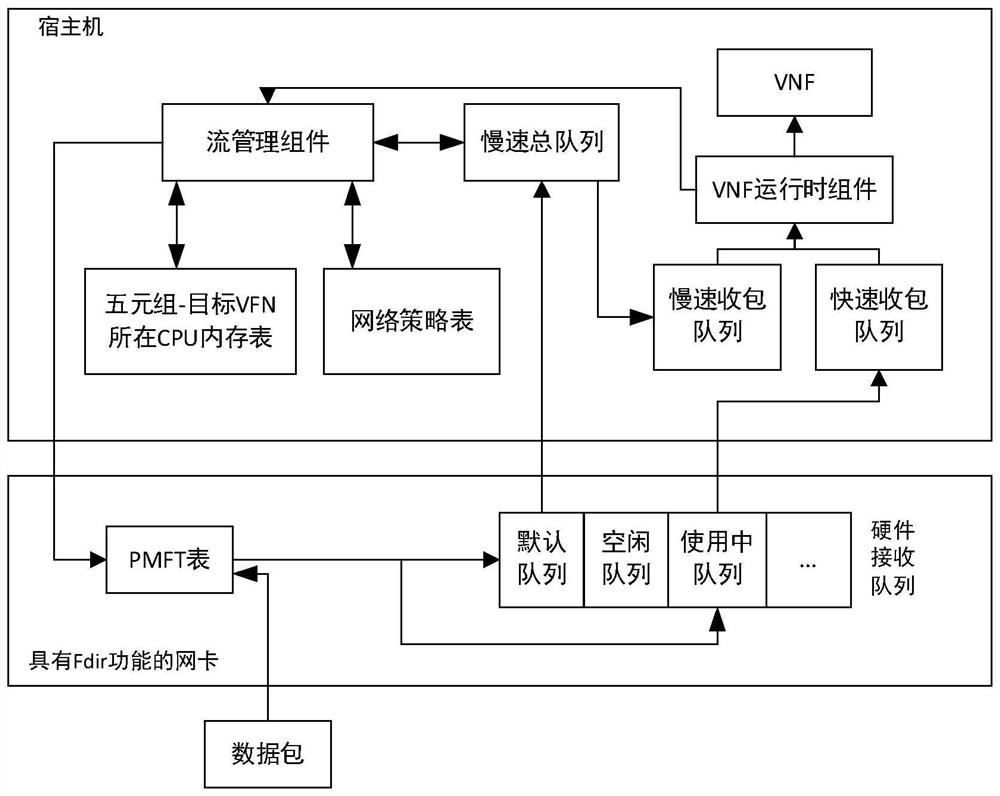
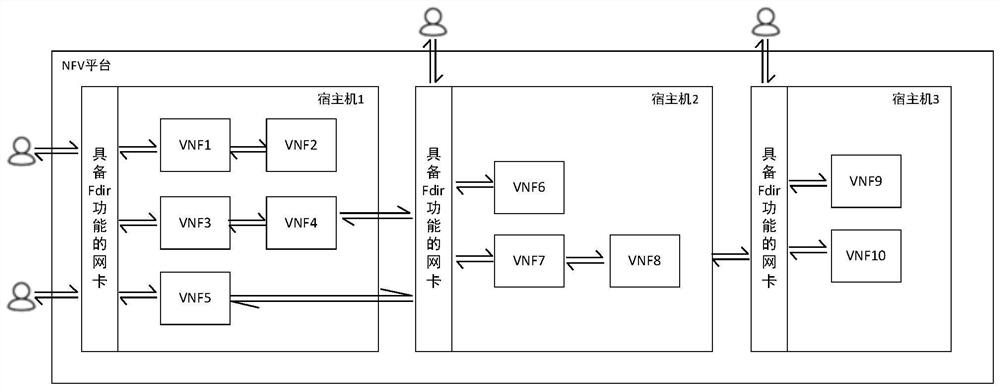
ActiveCN111611051BSave resourcesElimination of internuclear copyingInterprogram communicationTransmissionData packEngineering
The invention discloses a method for accelerating the first distribution of data packets by using the FDir function of the network card on the NFV platform, and using the FDir function to cache the mapping relationship between the quintuple of the active flow and the hardware receiving queue bound to the target VNF into PMFT table, and then the network card can directly send the data packet to the target VNF without CPU intervention; due to the capacity limitation of the PMFT table, for inactive flows, it is not cached to the PMFT table, Instead, the CPU is used in combination with the network policy to calculate the target VNF and then complete the distribution; the activity of each network flow can also be counted through a user-defined algorithm, and the PMFT table is periodically updated to maximize the acceleration benefit. The present invention can save the CPU resources of the host computer without introducing special hardware, and further enhance the overall performance of the NFV platform framework.
Owner:SHANGHAI JIAO TONG UNIV
A Ubiquitous Object Plug and Play Unified Access System and Third-Party Access Method
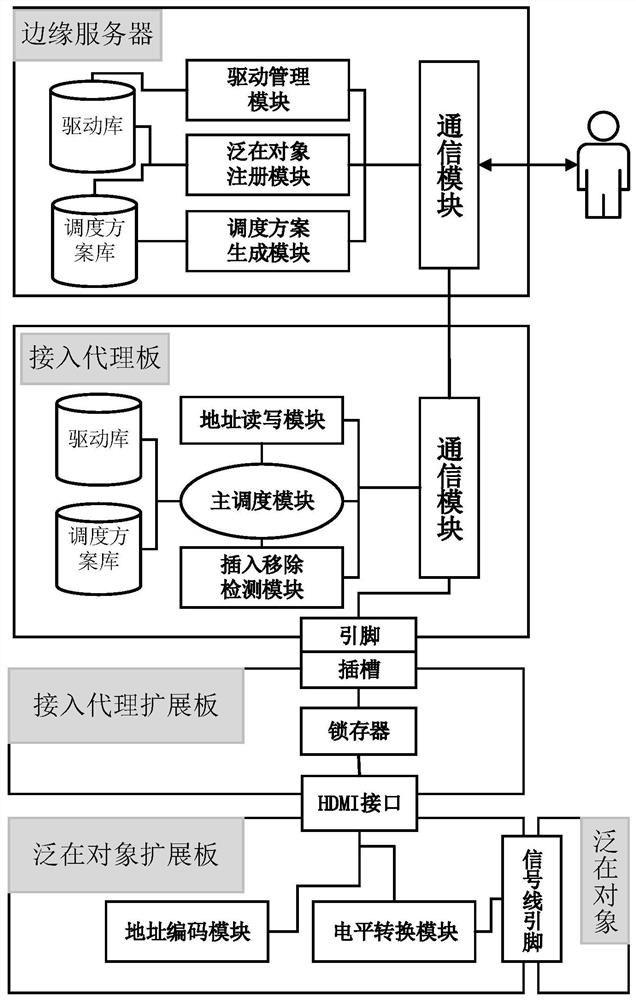
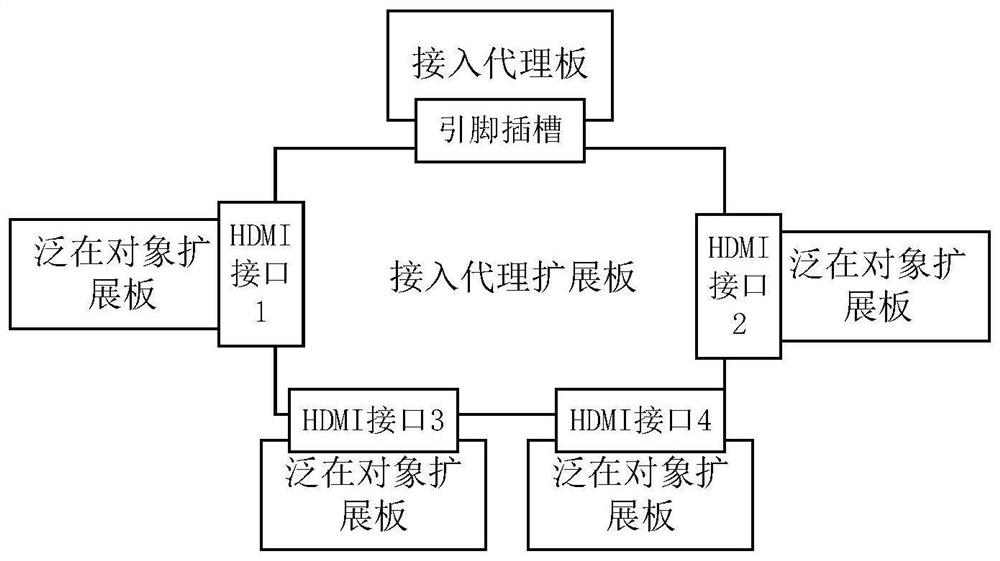
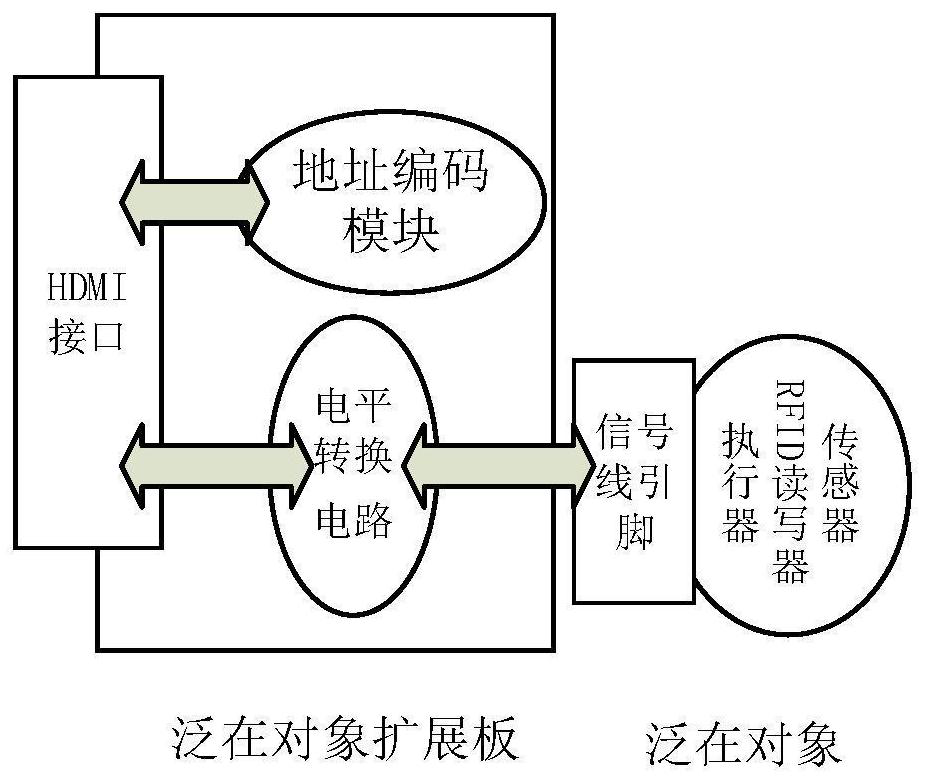
ActiveCN110554644BSimplify workNo need for repeated developmentProgramme controlComputer controlThird partyCode module
The invention discloses a ubiquitous object plug-and-play unified access system and a third-party access method. The system includes a ubiquitous object expansion board, an access proxy board, an access proxy expansion board and an edge server; The hardware circuit of the object expansion board is composed of an address encoding module, a level conversion module and an HDMI interface; the hardware circuit of the access agent board is realized by an MCU with network access function and supports multiple bus interconnection protocols; the edge server includes ubiquitous object Metabase, driver library, scheduling solution library, ubiquitous object registration module, driver management module, scheduling solution management module and communication module. The invention is used to simplify the MCU-based development workload of third-party developers and reduce the difficulty of use by common users.
Owner:SOUTH CHINA UNIV OF TECH
Method for starting a combustion system
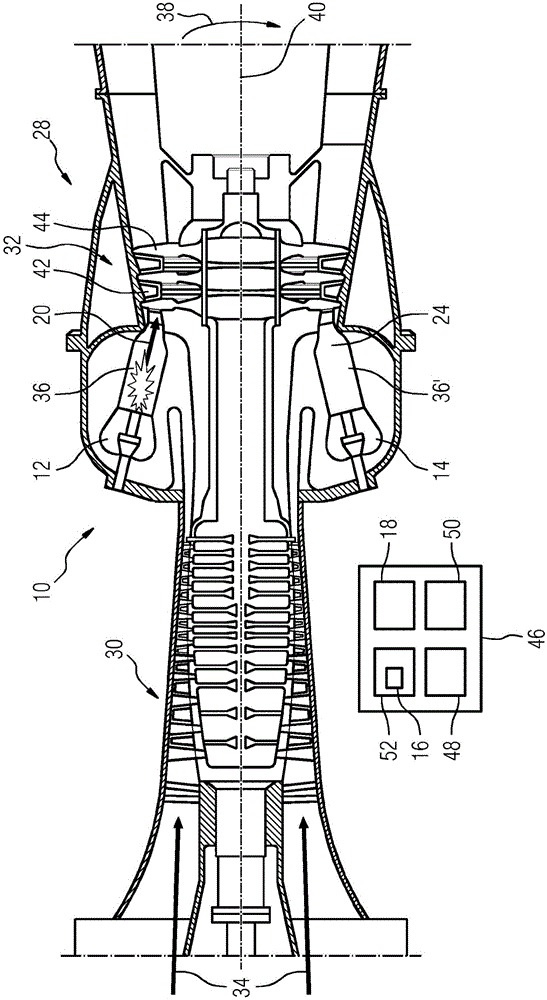
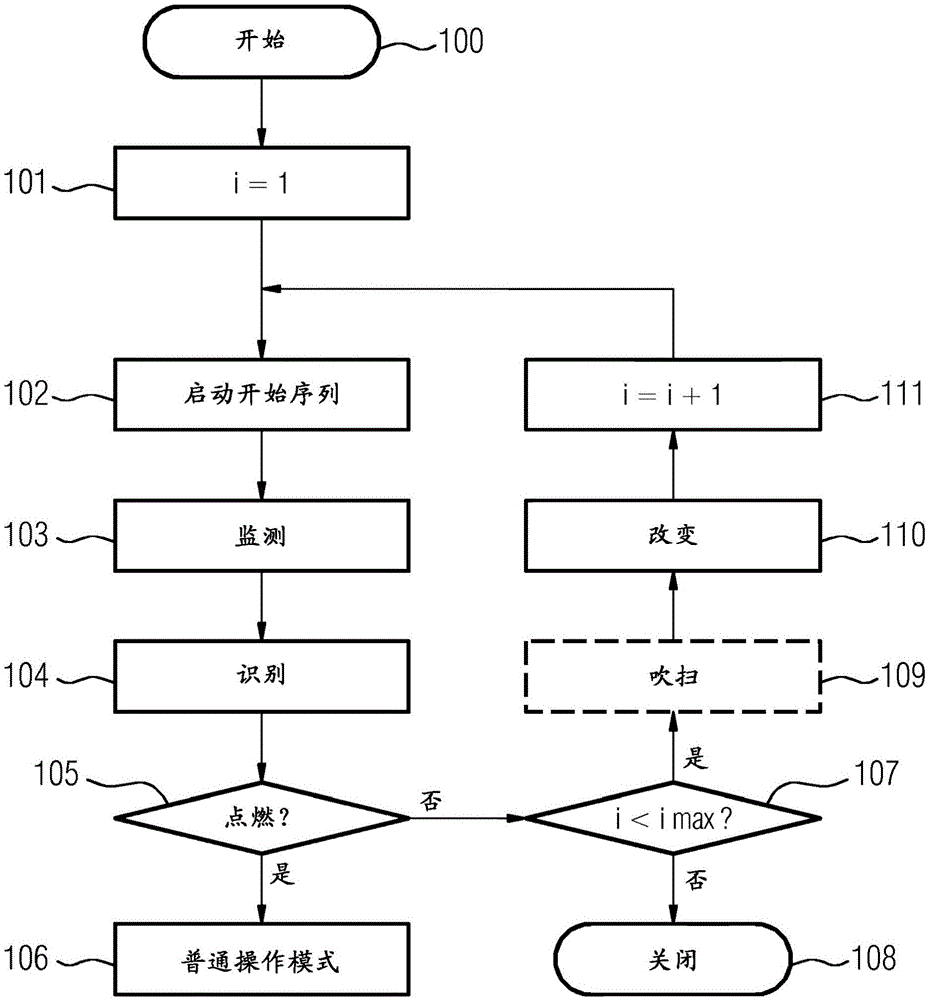
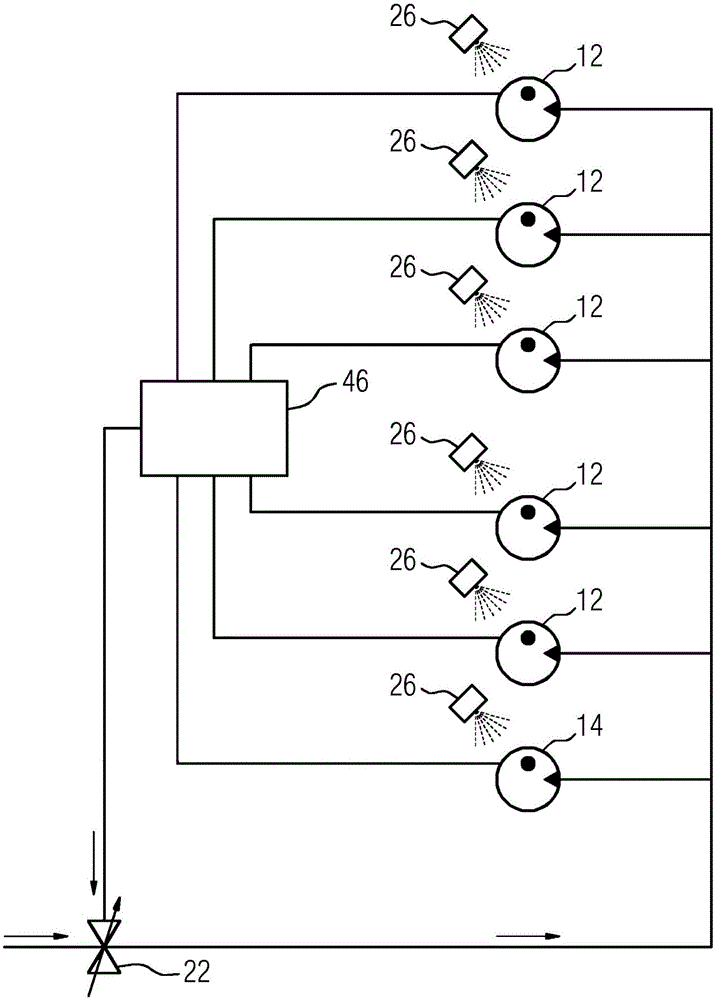
InactiveCN105074136AReliable and long-lasting operationWidely deployedEngine fuctionsTurbine/propulsion engine ignitionCombustion systemSensor system
The present invention relates to a method for starting (100) a combustion system (10, 10a), comprising a first ignition device (12) and an at least second ignition device (14), a processing unit (16) and a sensor system (18). To obtain a reliable ignition the method comprises as a starting sequence at least the following steps: monitoring (103) during a working condition of the combustion system (10, 10a) an operational state of the first and the at least second ignition device (12, 14) by the sensor system (18); identifying (104) a predefined state of the first and / or the at least second ignition device (12, 14) by the processing unit (16); and as a further step: in case of an identification of the predefined state changing (110) in at least one parameter of at least one of the ignition devices (12, 14) by the processing unit (16). The invention further relates to a combustion system (10, 10a) equipped to be operable with said method as well as to a flow engine (28) with such a combustion system (10, 10a).
Owner:SIEMENS AG
An optical signal-to-noise ratio monitoring device and monitoring method
ActiveCN109474336BWidely deployedSimple structureCharacter and pattern recognitionElectromagnetic transmissionEngineeringSupport vector regression machine
The invention discloses an optical signal-to-noise ratio monitoring device and a monitoring method. The device includes a signal acquisition device for obtaining Stokes parameters of a signal to be measured, and a signal-to-noise ratio and a signal-to-noise ratio for extracting Stokes parameters. A device for extracting signal features of polarization damage, and a support vector regression model obtained by training optical signal feature parameters and corresponding optical signal-to-noise ratio values. The device achieves optical signal-to-noise ratio monitoring based on the acquisition of Stokes parameters, the extraction of signal-to-noise ratio and polarization damage based on the support vector regression machine. It has a simple structure and low cost, and can be widely deployed in various nodes in the network. Provide information basis for resource allocation and dynamic routing in the optical network.
Owner:UNIV OF SCI & TECH BEIJING
An offline key injection system and method
ActiveCN105959112BRealize mutual recognitionReliable importKey distribution for secure communicationSoftware engineeringNetwork communication
The invention discloses an offline key injection system. The offline key injection system comprises a key injection gun and a central key store; the key injection gun comprises an identification code reader, a display module, a keyboard module, a connection transmission module and a network communication module; and public and private keys of central distributors and public keys of managed equipment or modules are stored in the central key store. The invention further discloses an offline key injection method. Due to the method, reliable import of the public keys of the equipment in a non-reliable environment can be ensured. In the whole process, the key gun is only used as a carrier for interacting data with the central key store; the key gun itself does not participate in generation and modification of data contents; therefore, equipment maintenance / replacement place and personal requirements are greatly simplified.
Owner:江苏先安科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com