Offline key injection system and method
A key and injection gun technology, applied in transmission systems, digital transmission systems, and key distribution, can solve problems such as mutual authentication between devices and modules
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
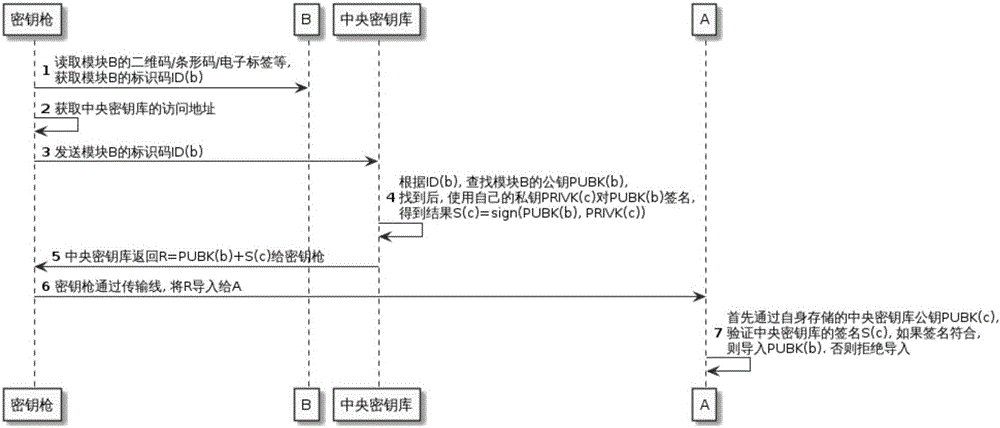
[0119] Example 1, the offline import process is the same as figure 2 As shown, it specifically includes the following steps:
[0120] Step 1, the key injection gun obtains the identification code ID(b) of module B;
[0121] Step 2, the key injection gun obtains the access address of the central key store;
[0122] Step 3, the key injection gun sends ID(b) to the central key store;
[0123] Step 4: The central key store searches for the public key PUBK(b) of module B according to the ID(b), and uses its own private key PRIVK(c) to sign PUBK(b), and obtains the result S(c)=sign (PUBK(b), PRIVK(c));
[0124] Step 5, the central key store returns R=PUBK(b)+S(c) to the key injection gun;
[0125] Step 6, the key injection gun imports R to device A;
[0126] Step 7. Device A verifies the signature S(c) of the central key store, and if the signature matches, imports PUBK(b); otherwise, refuses to import.
Embodiment 2
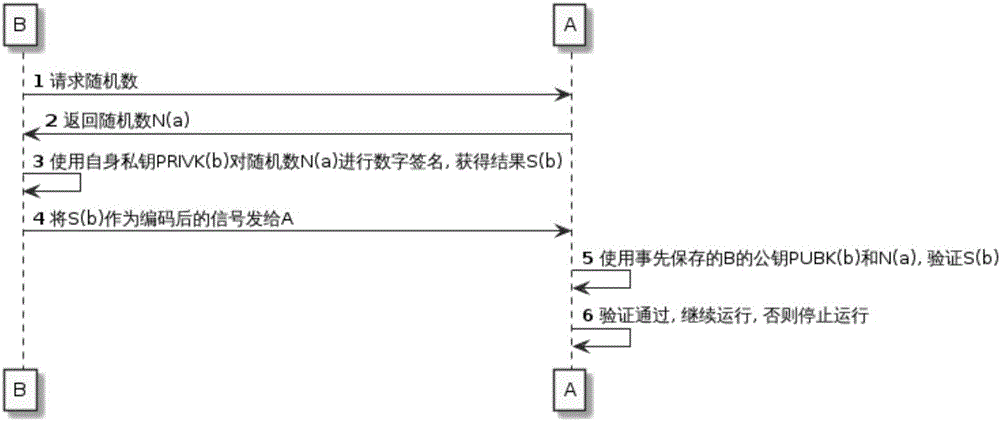
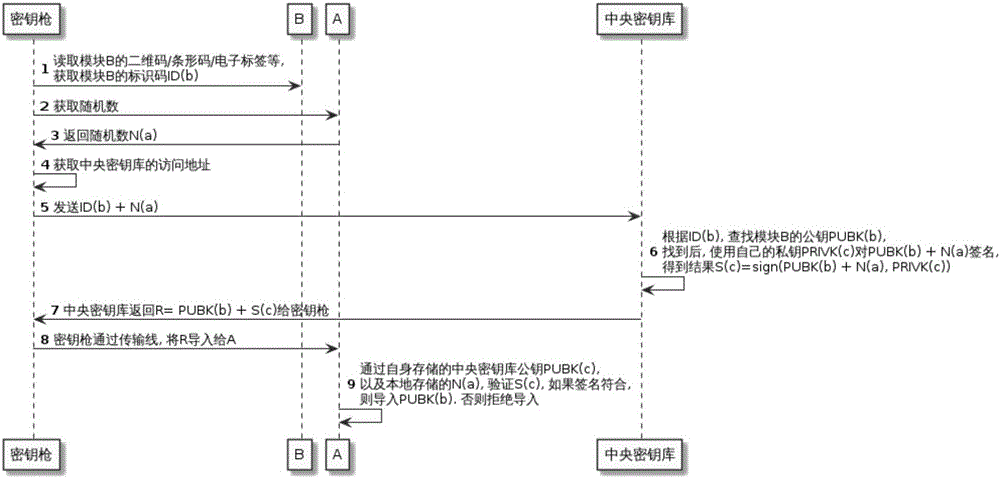
[0127] Example 2, such as image 3 As shown, the process of obtaining random numbers from device A can also be added in Embodiment 1 to enhance the anti-retransmission capability of the entire system. The second process is as follows image 3 .
Embodiment 3
[0128] Example 3, such as Figure 4 As shown, it is also possible to add the device A public key + private key signature information in Embodiment 2, so as to realize the management of the device key pairing situation (device X and module Y have been paired) by the central key storehouse.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com