Patents
Literature
36results about How to "Easy to tamper with" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
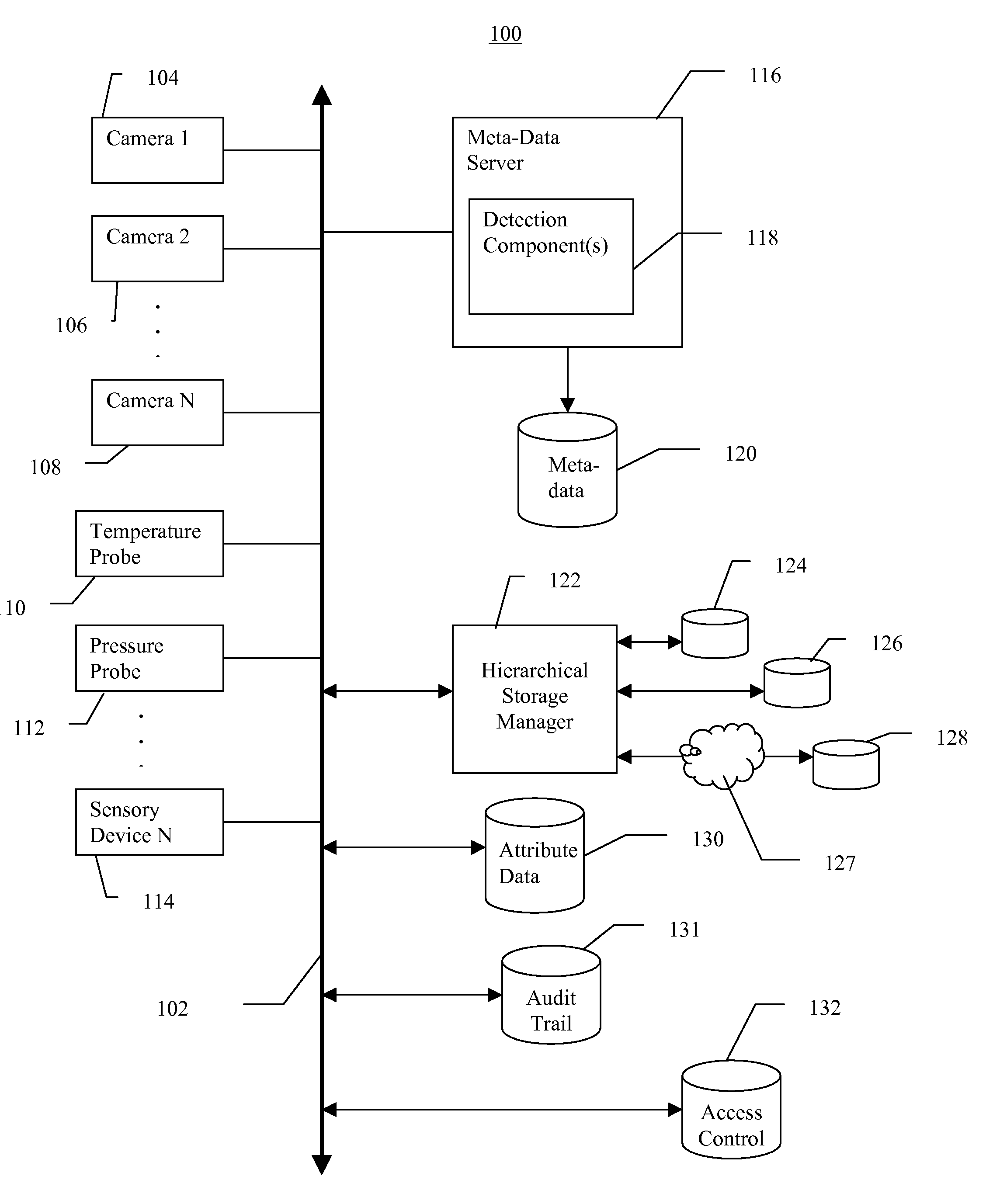
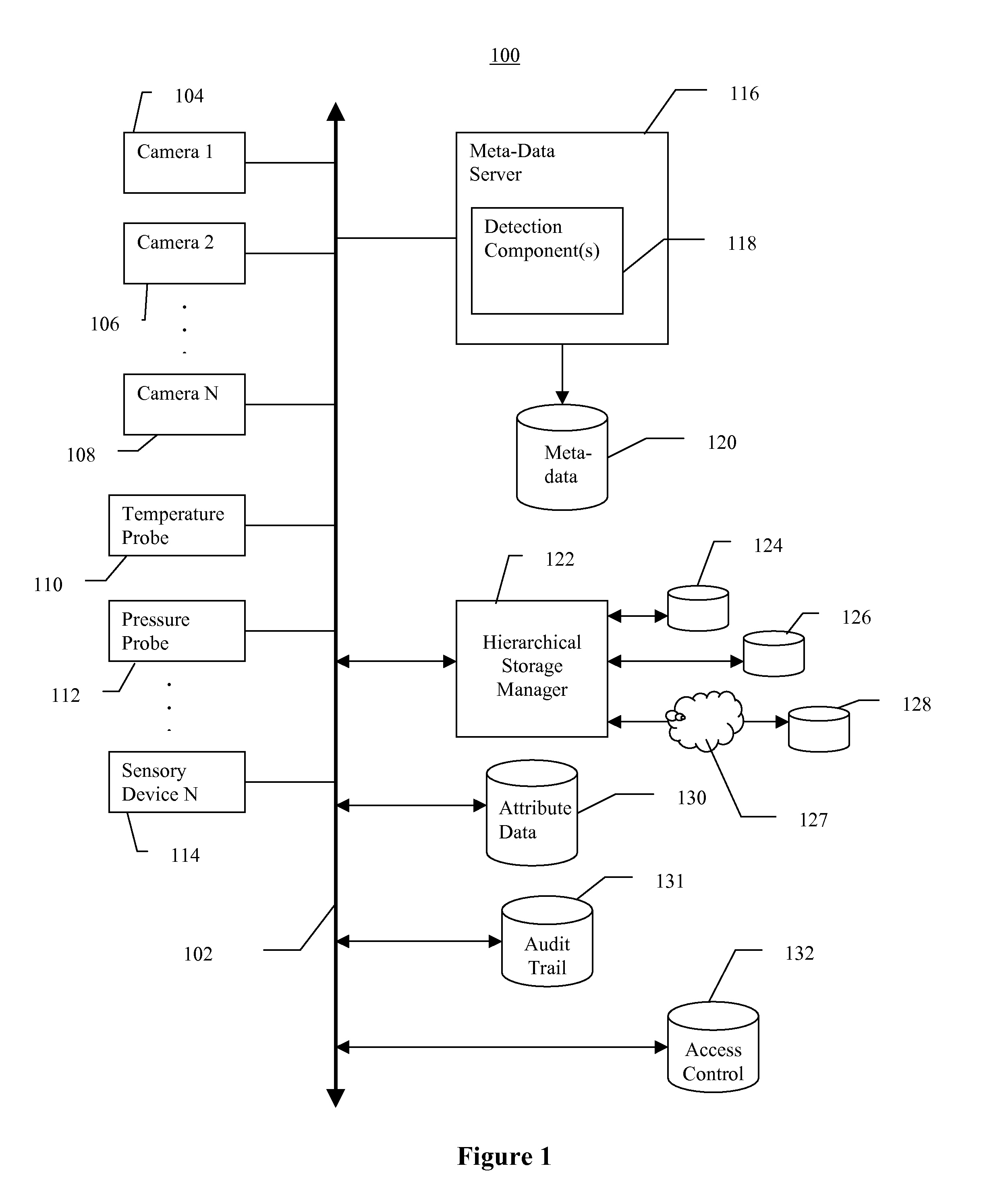
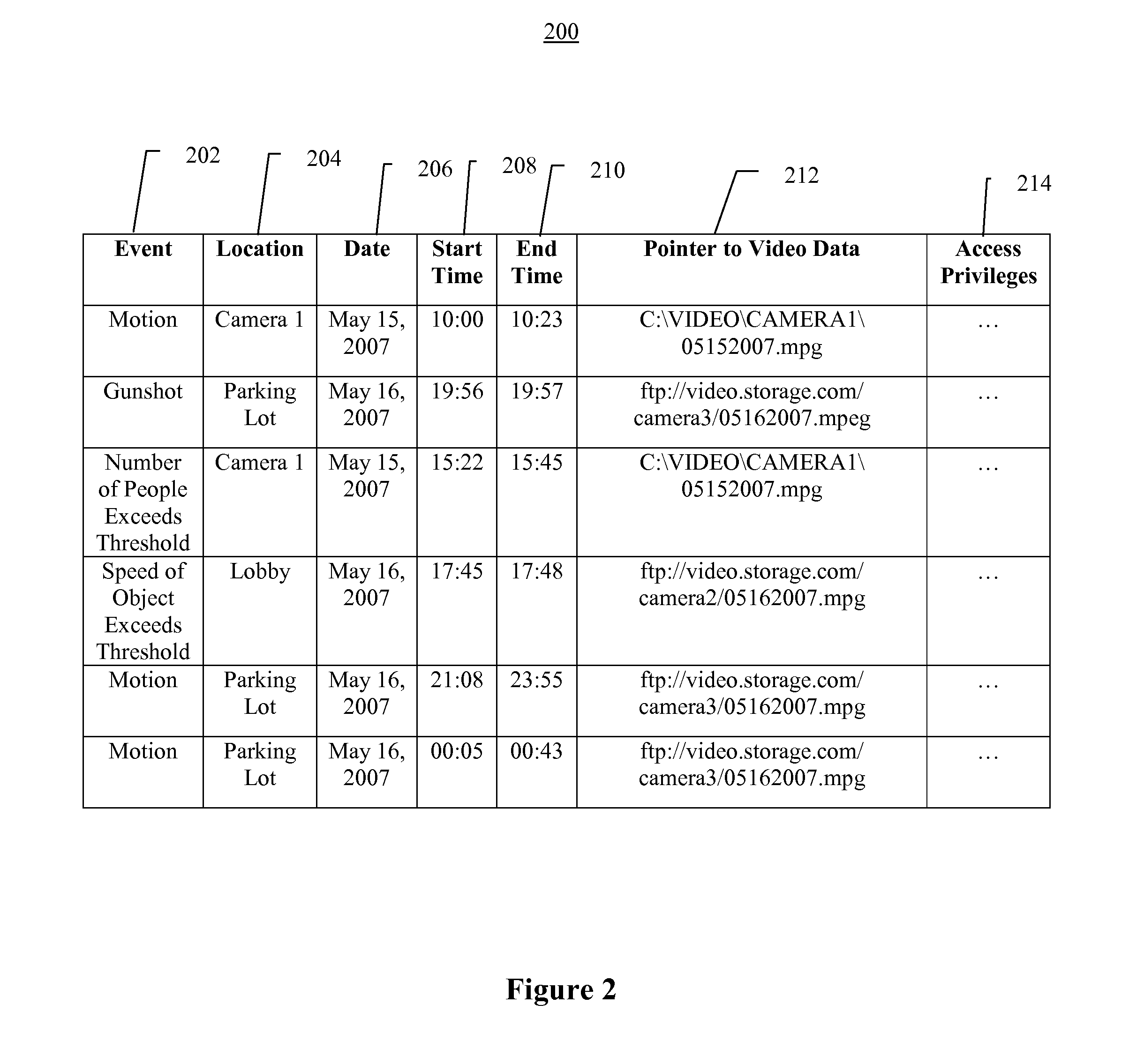
Video data storage, search, and retrieval using meta-data and attribute data in a video surveillance system
InactiveUS20080297599A1Easy to tamper withReduce weightTelevision system detailsRecording carrier detailsVideo monitoringVideo storage
One embodiment is a method of storing video data from a video surveillance system having one or more cameras. Video data is captured from one or more surveillance cameras. Meta-data is automatically generated by performing video analysis on the captured video data from the surveillance cameras. A human operator may manually enter additional meta-data. Attribute data and associated weights, representing information about the relevance of the meta-data, is received. The video data is stored in a hierarchical video storage area; the meta-data, indexed by date and time stamp to the video data, is stored in a meta-data storage area; and the attribute data is stored in an attribute storage area. One or more alerts may be issued based on the past and present meta-data. The video data is secured by encrypting and storing the video data remotely, and audit trails are generated about who and when viewed the video data.
Owner:SECURENET SOLUTIONS GRP
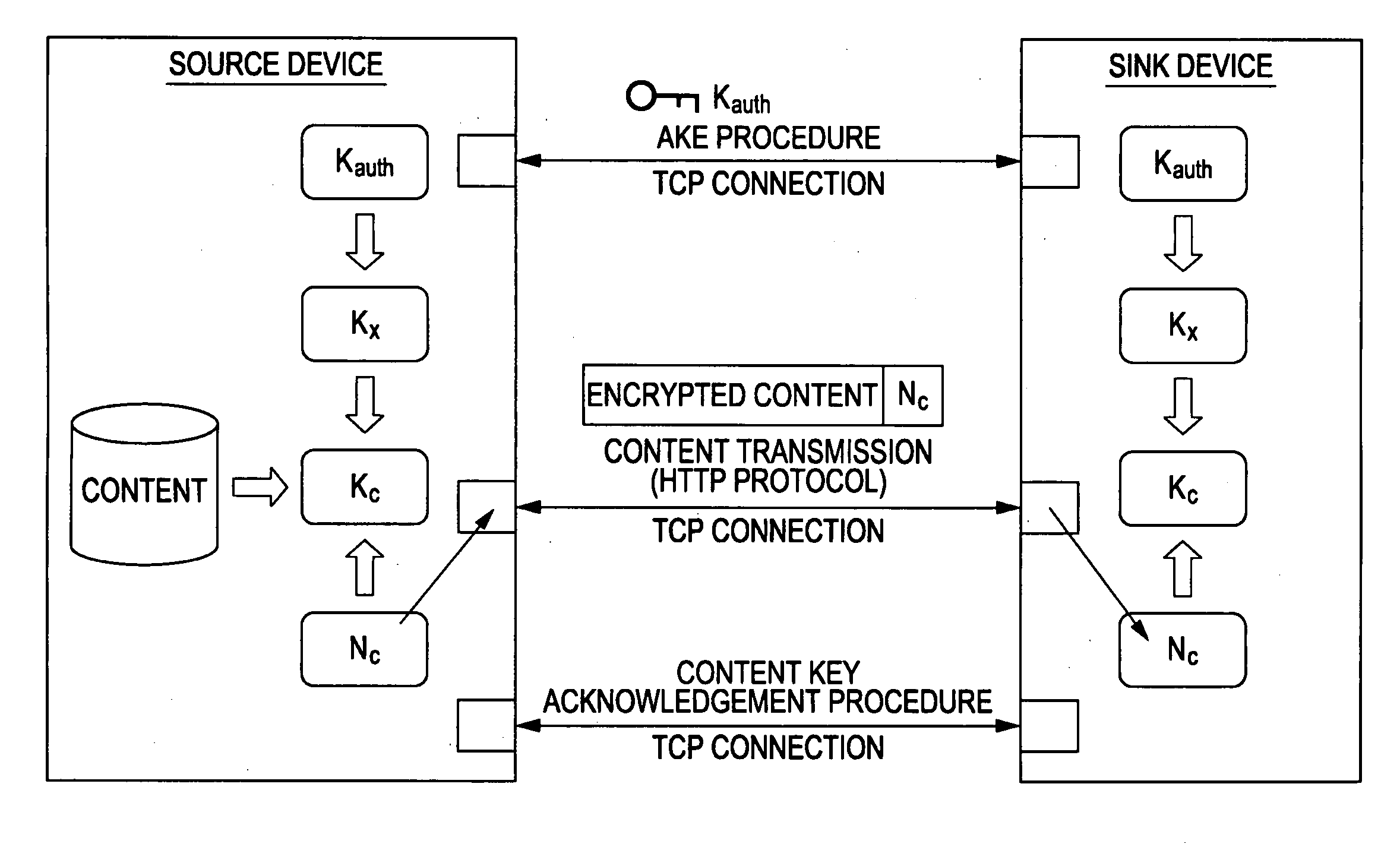
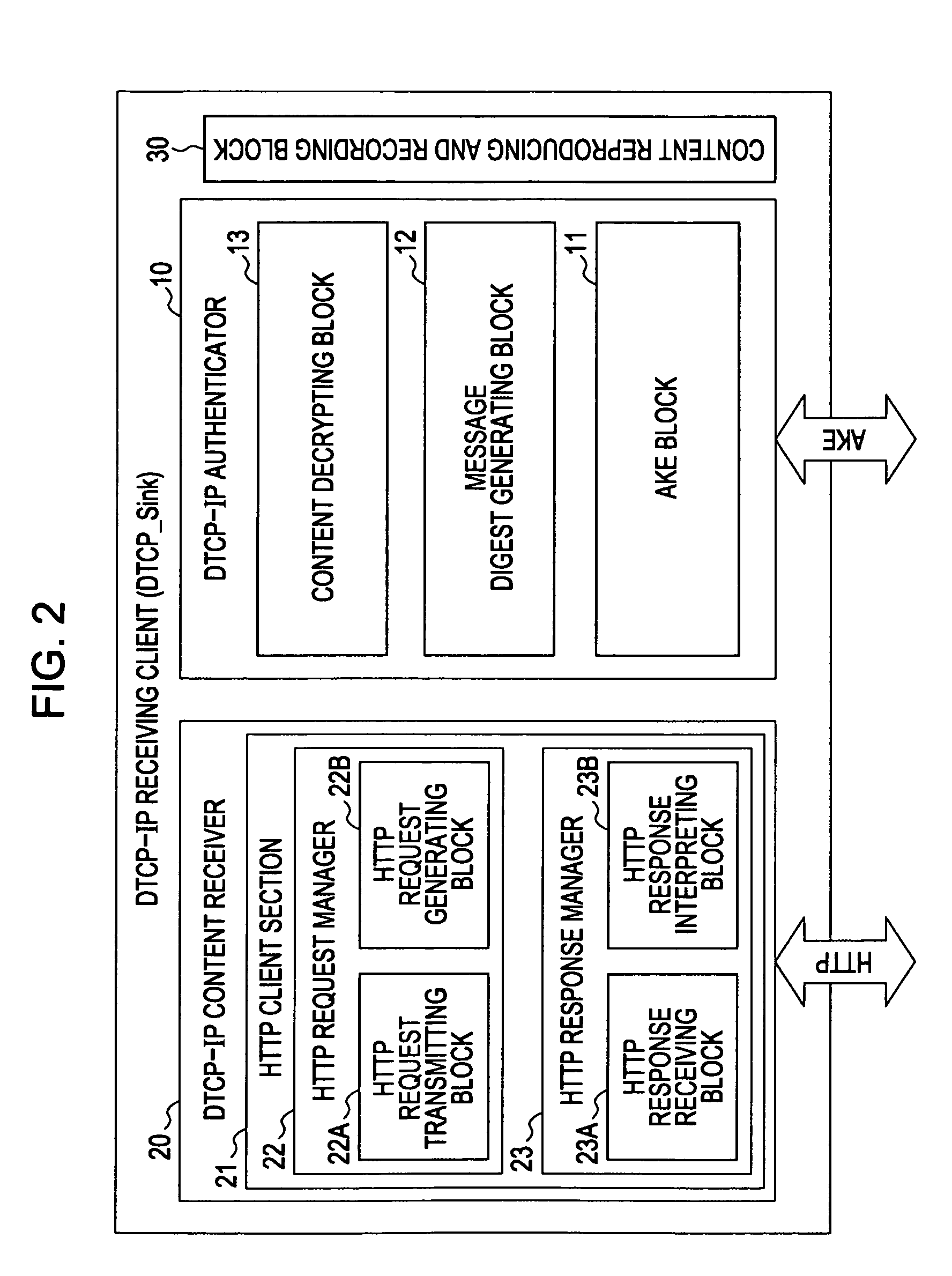
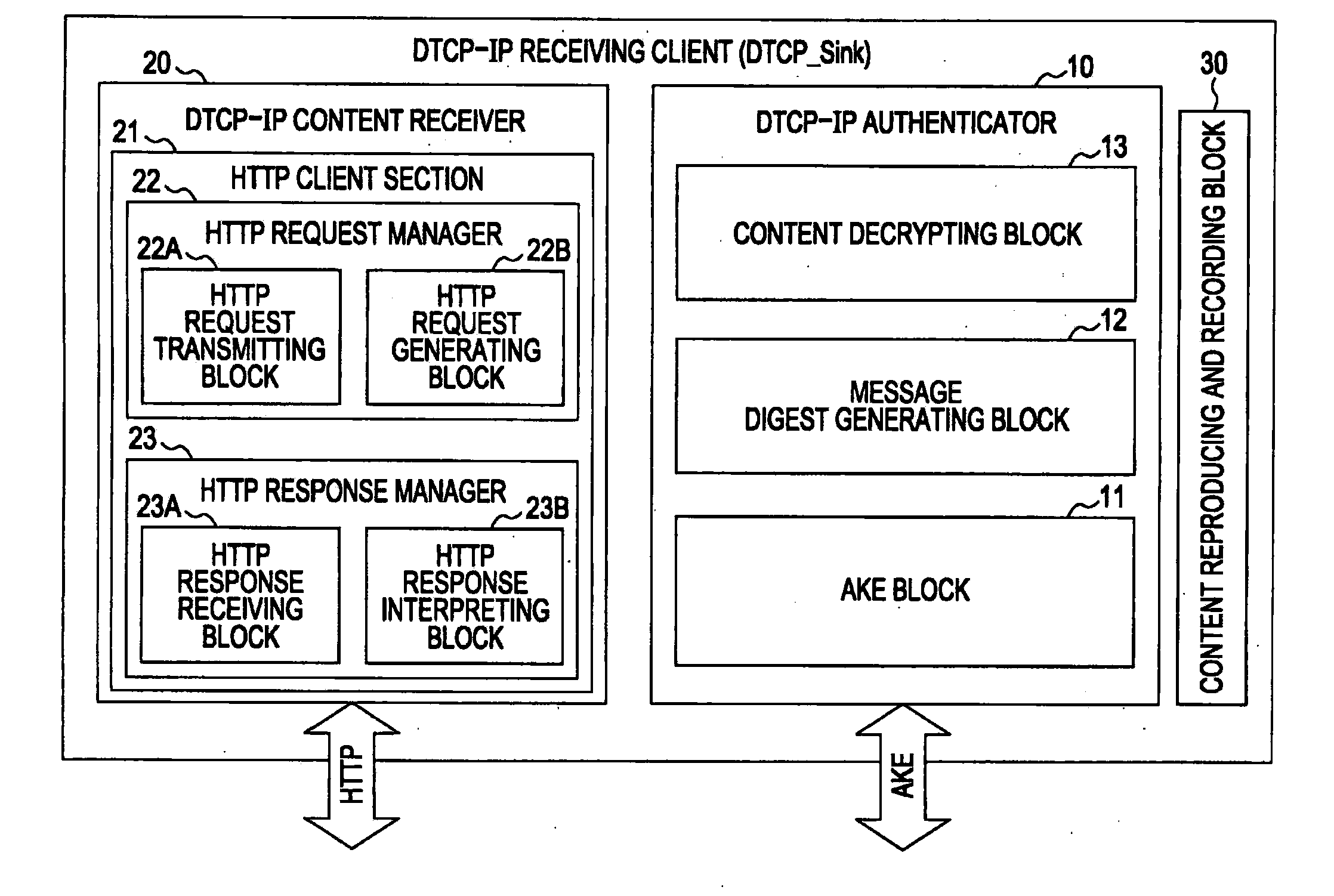
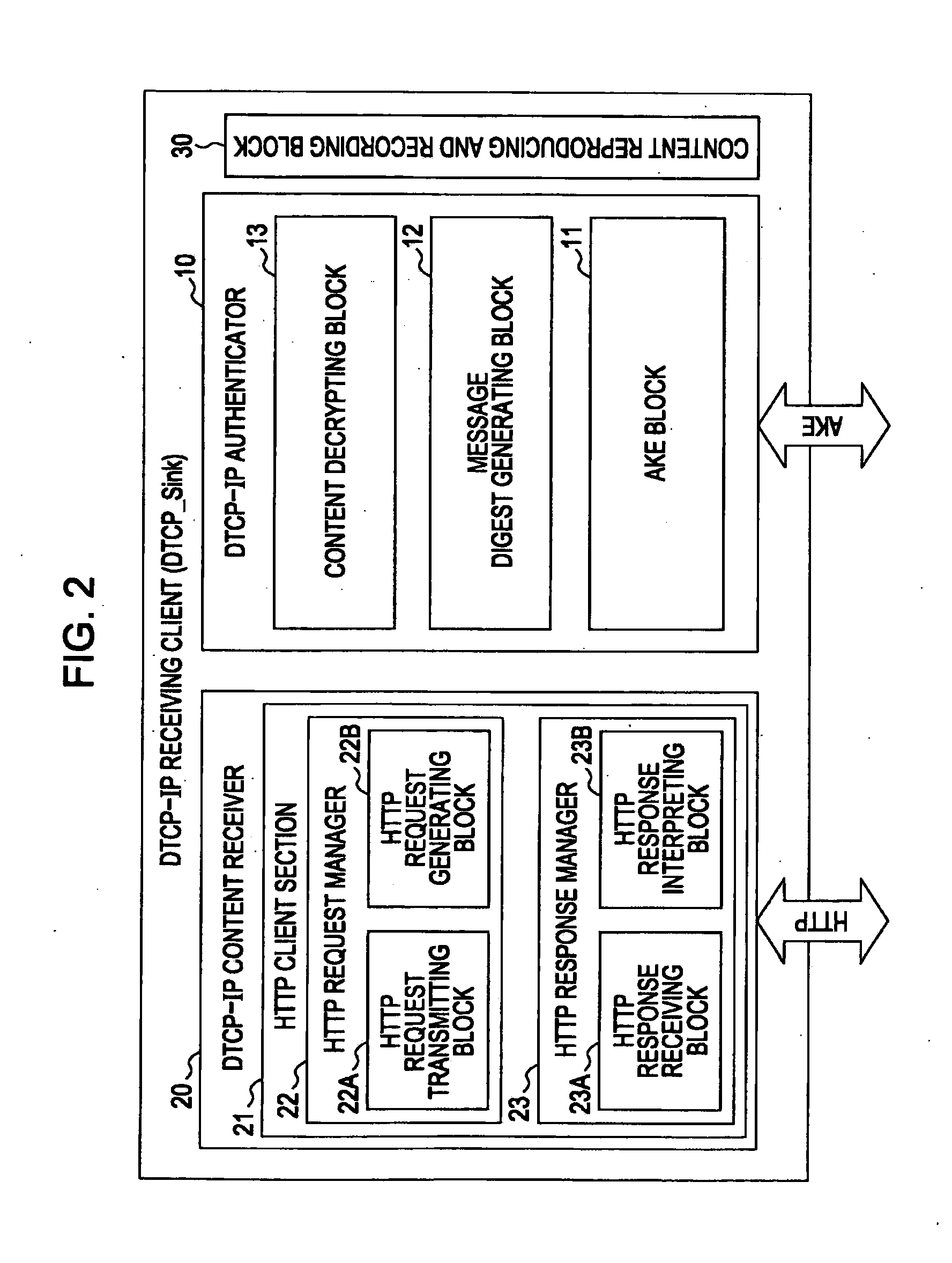
System, apparatus, method and computer program for transferring content
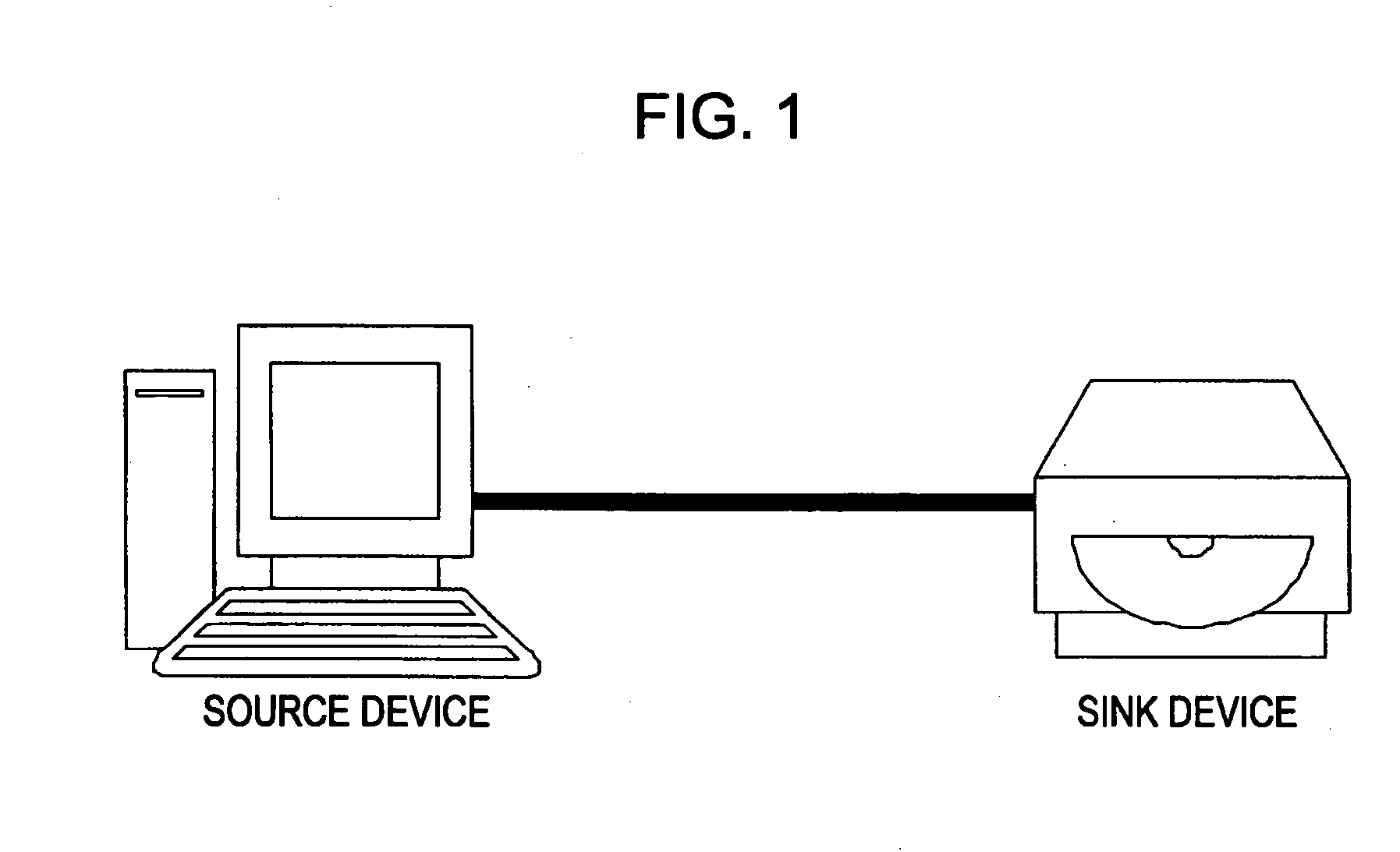
ActiveUS20070162753A1Reduce usageEasy to useData processing applicationsUser identity/authority verificationKey exchangeTransfer system
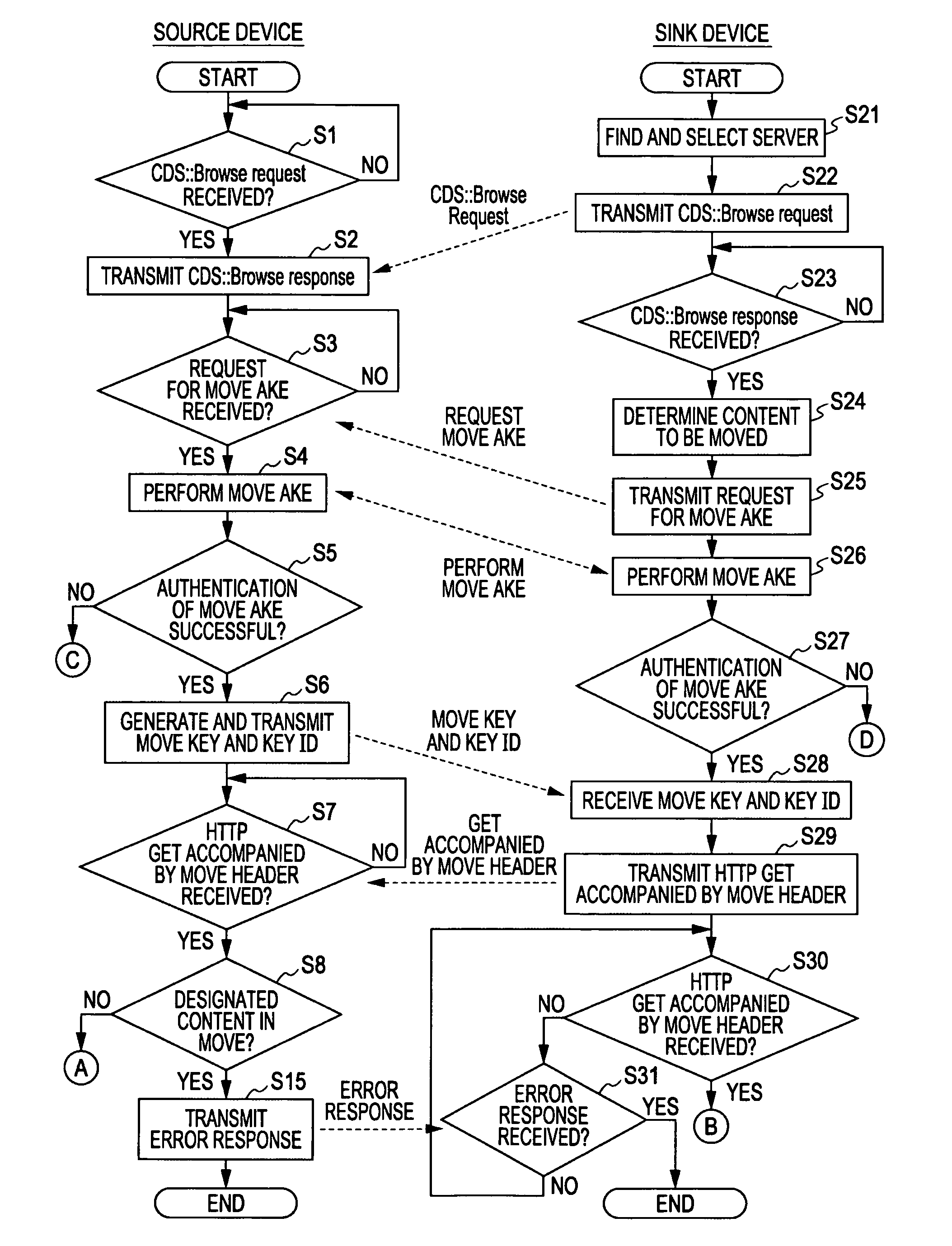
A content transfer system for transferring content between a source device transmitting the content and a sink device receiving the content, includes a content specifying unit for specifying the content to be transferred between the source device and the sink device, an authentication unit for performing an authentication exchange key process between the source device and the sink device, a content transfer unit for performing a content transfer process by encrypting and transferring the content specified by the content specifying unit from the source device to the sink device using the key exchanged by the authentication unit, and a content transfer finalizing unit for performing a content transfer finalizing process by validating the content at the sink device and invalidating the original content at the source device in response to the end of the content transfer process performed by the content transfer unit, the content thus being moved from the source device to the sink device.
Owner:SONY CORP
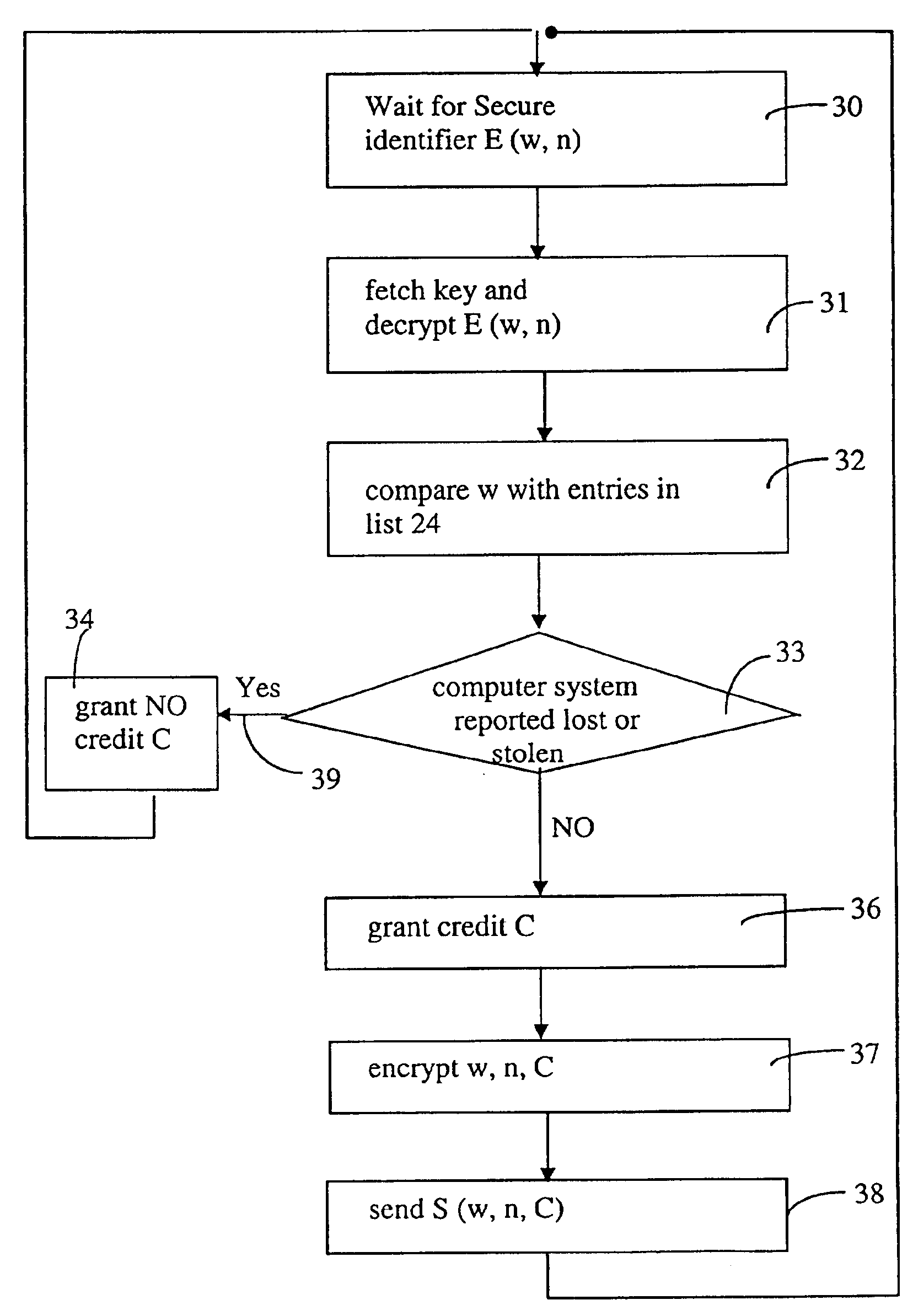
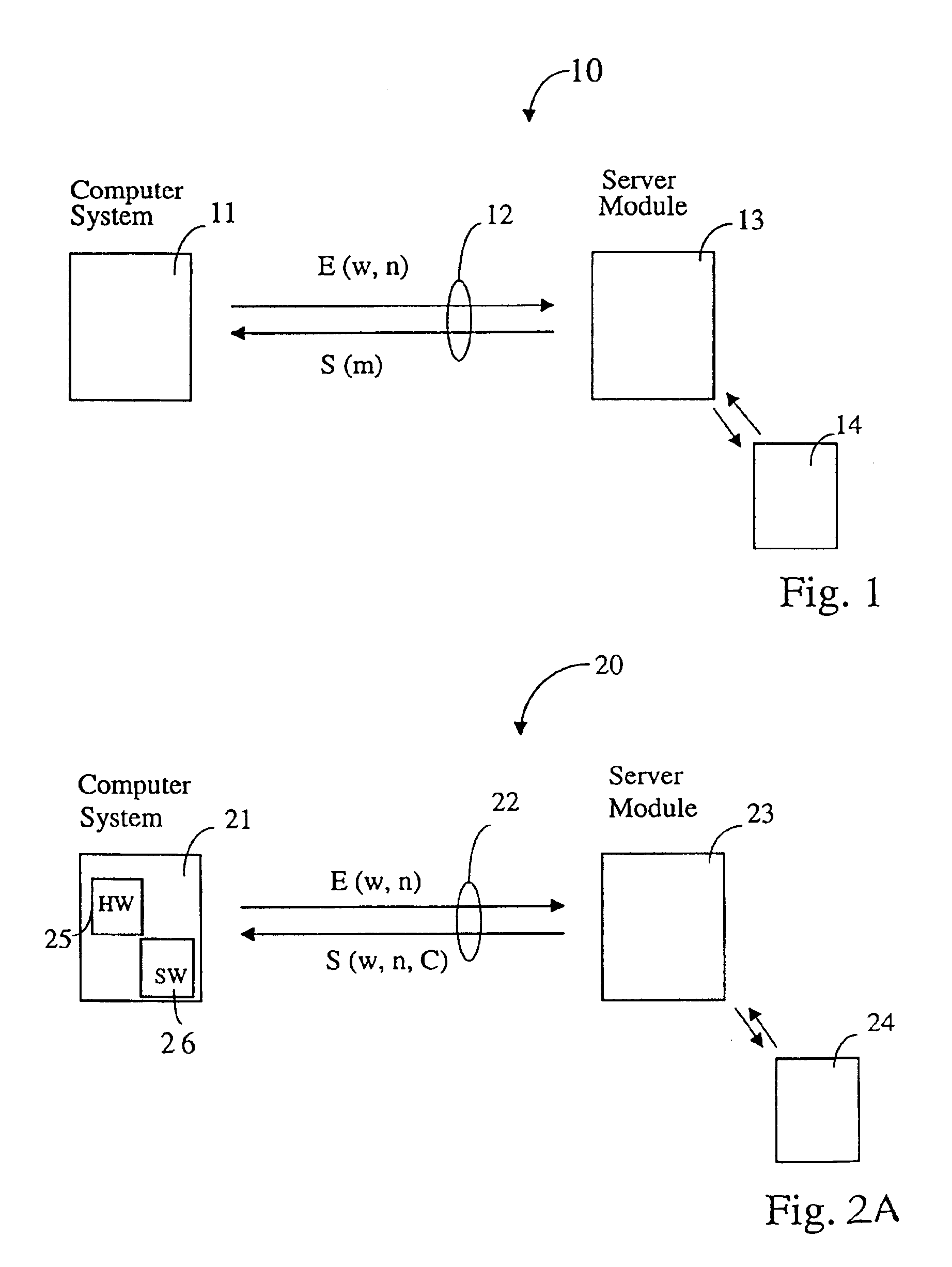
Scheme for blocking the use of lost or stolen network-connectable computer systems
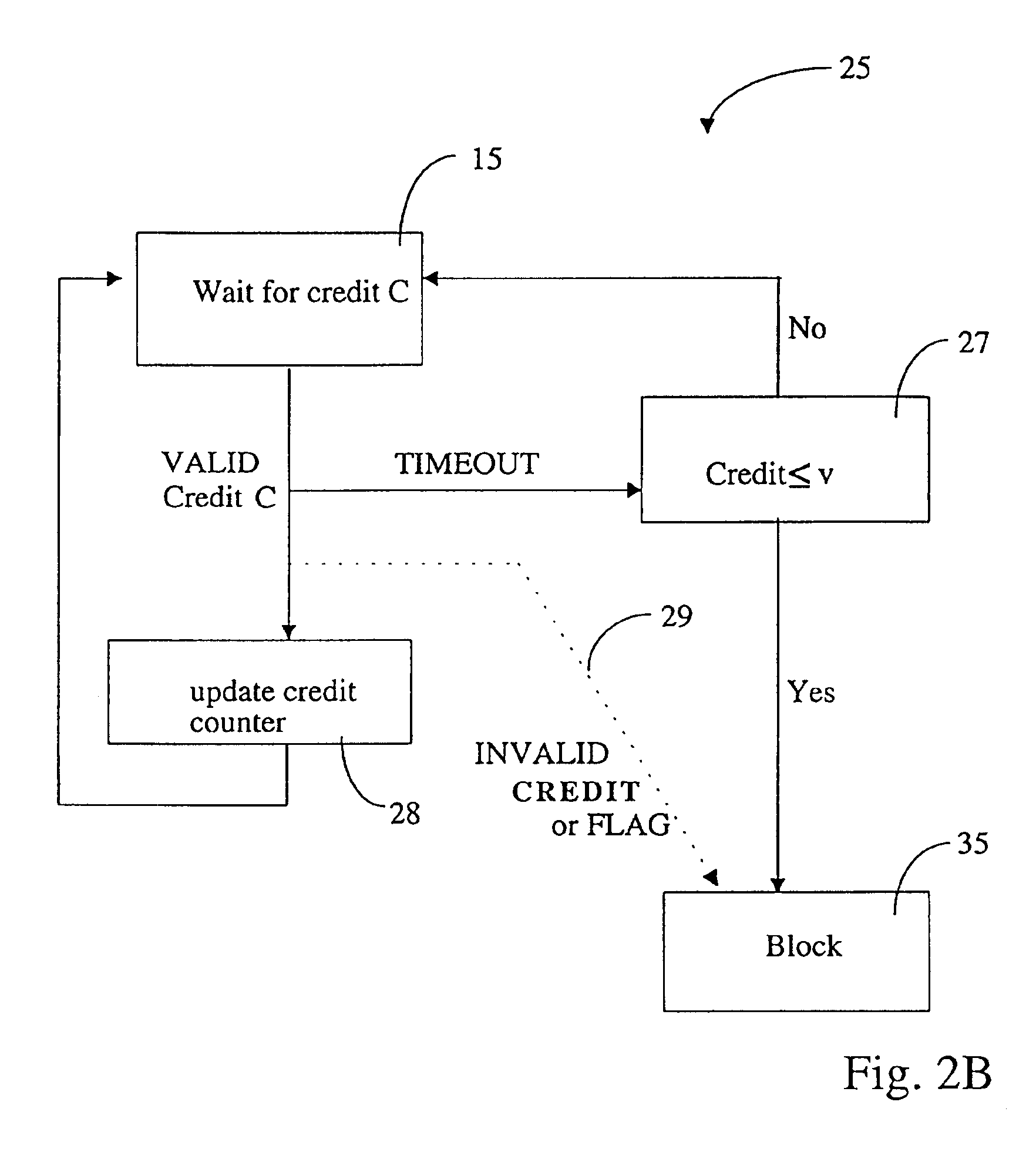
ActiveUS6925562B2Easy to tamper withMaximum flexibilityDigital data processing detailsUser identity/authority verificationCommunication interfaceTrusted hardware
Scheme for switching a computer system (21), which is connectable via a communication interface and a network (22) to a server module (23), into a special mode of operation. The computer system (21) comprises a software component (26) for sending an identifier (w) assigned to the computer system (21) via the communication interface and the network (22) to the server module (23). In response, the software component (26) receives a token (S), issued by the server module (23), whereby the token (S) comprises a credit (C). In addition, the computer system (21) comprises a trusted hardware component (25) storing the identifier (w) and comprising a credit counter (44) with a credit which is automatically exhaustible step-by-step, and which is updateable with the credit (C) received from the server module (23). The computer system (21) has a trigger unit for switching the computer system (21) into the special mode of operation, e.g. a mode where the computer system (21) is of limited use to a user, if the credit of the credit counter is exhausted.
Owner:TREND MICRO INC
Safety network time synchronizing method and device
ActiveCN107395312AImprove securityLow reliabilityTime-division multiplexComputer hardwareMessage authentication code
The invention relates to the field of network safety, in particular to a safety network time synchronizing method and device. The method comprises the following steps: key agreement: acquiring a session key and a message authentication code by a client side through a session key request and a message authentication code request, and establishing mutual trust between the client side and a server; and time synchronization: implementing safety time synchronization by time synchronizing data frame interaction. The client side transmits a client side key request data frame to a server side; after receiving the client side key request data frame, the server replies a server session key responding frame to the client side; after receiving the server session key responding frame, the client side examines frame formats and contents, and acquires a session key; the client side transmits a client side message authentication code request frame to the server; after receiving the client side message authentication code responding frame of the client side, the server computes a message authentication code according to a session key and message contents and replies a server message authentication code responding frame to the client side; and after receiving the server message authentication code responding frame, the client side examines the frame format and content, and acquires the message authentication code.
Owner:电信科学技术第五研究所有限公司
Embedded-type system for ensuring completeness of program and realization method thereof
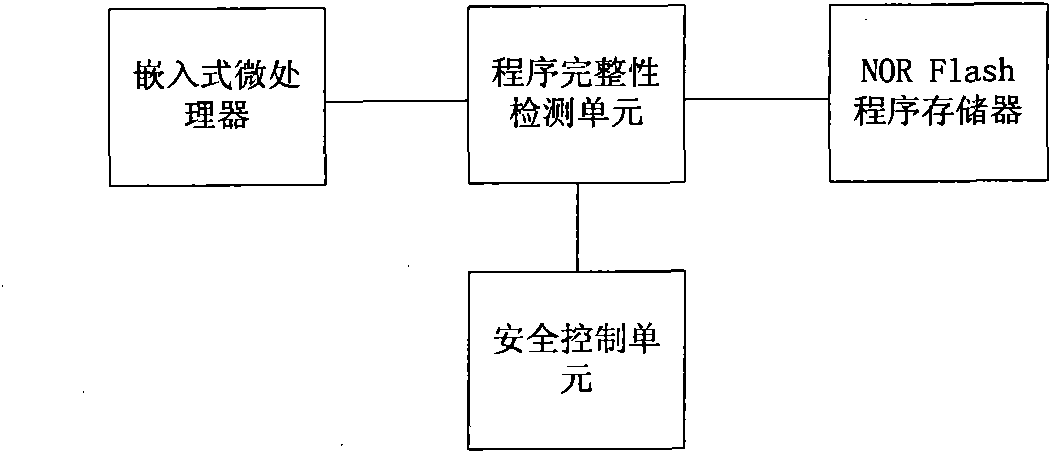
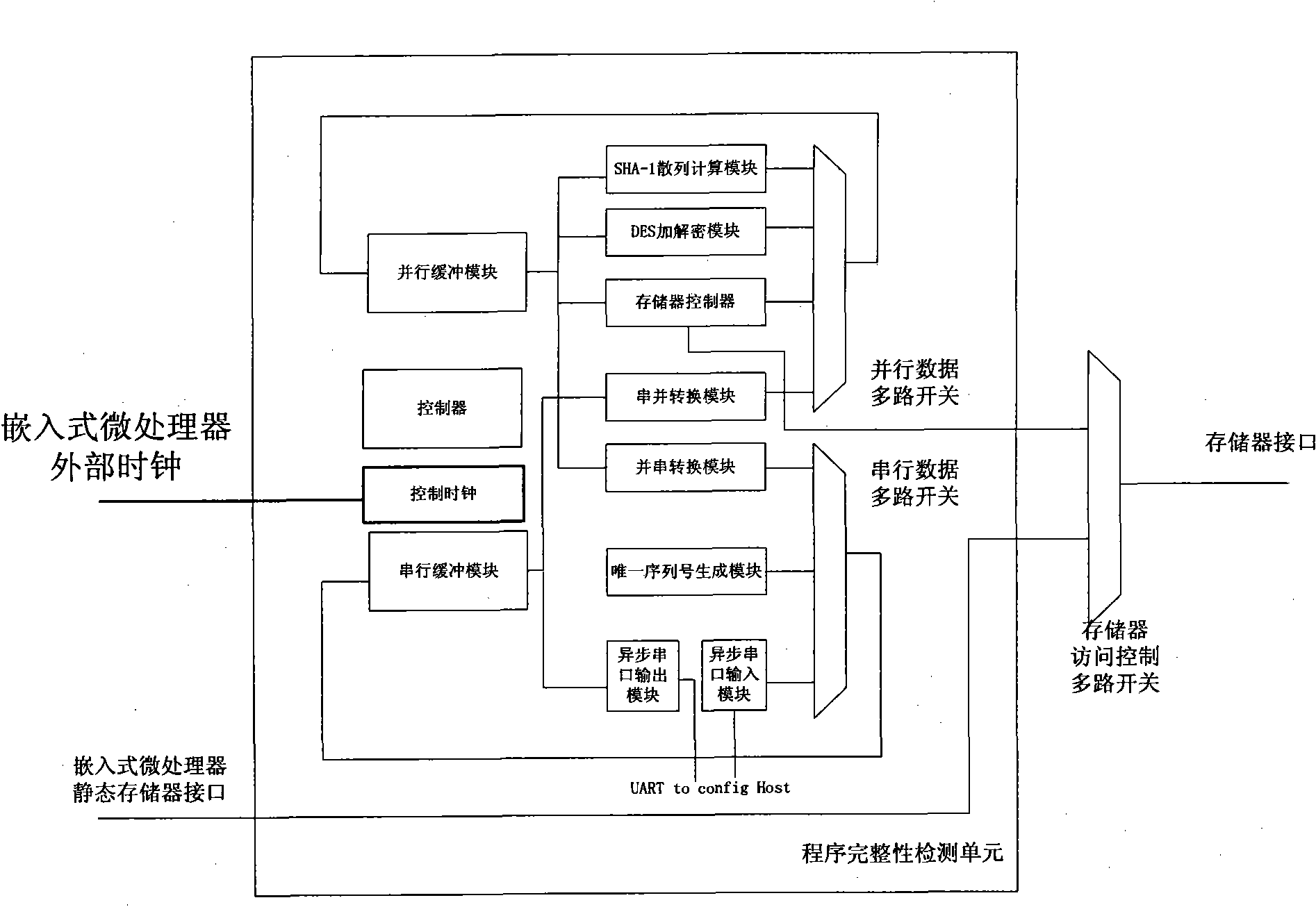
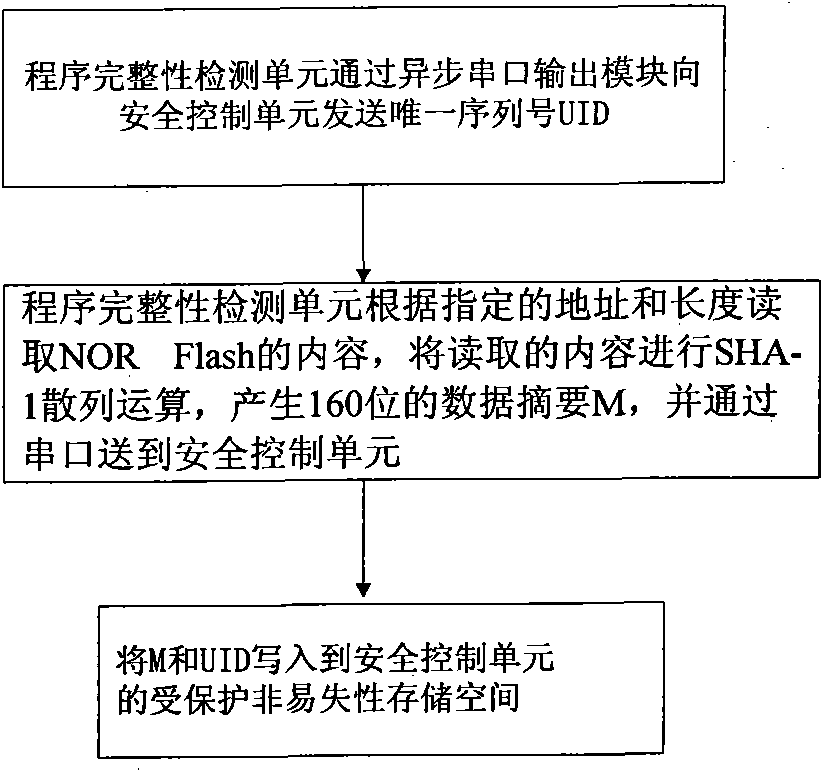
InactiveCN101882189AEasy to tamper withEasy to implementDigital data protectionHash functionRunning time
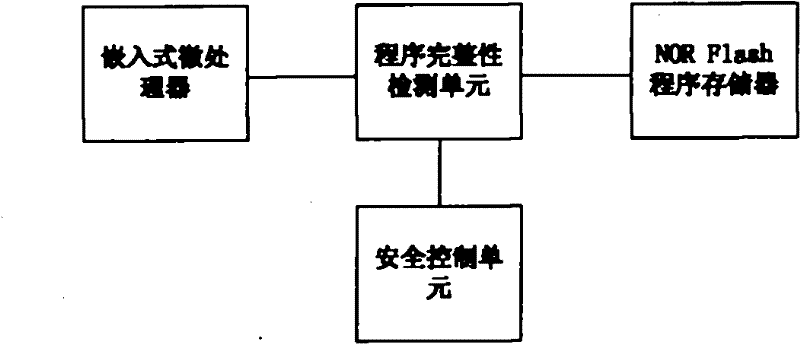
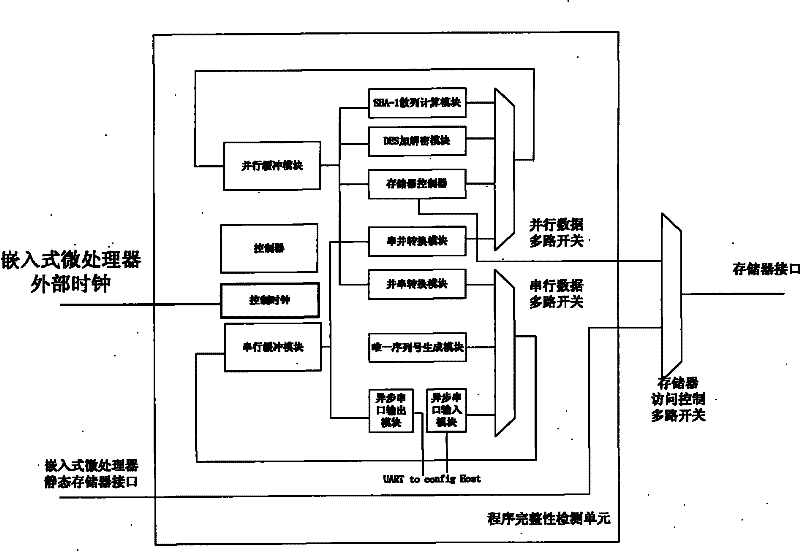
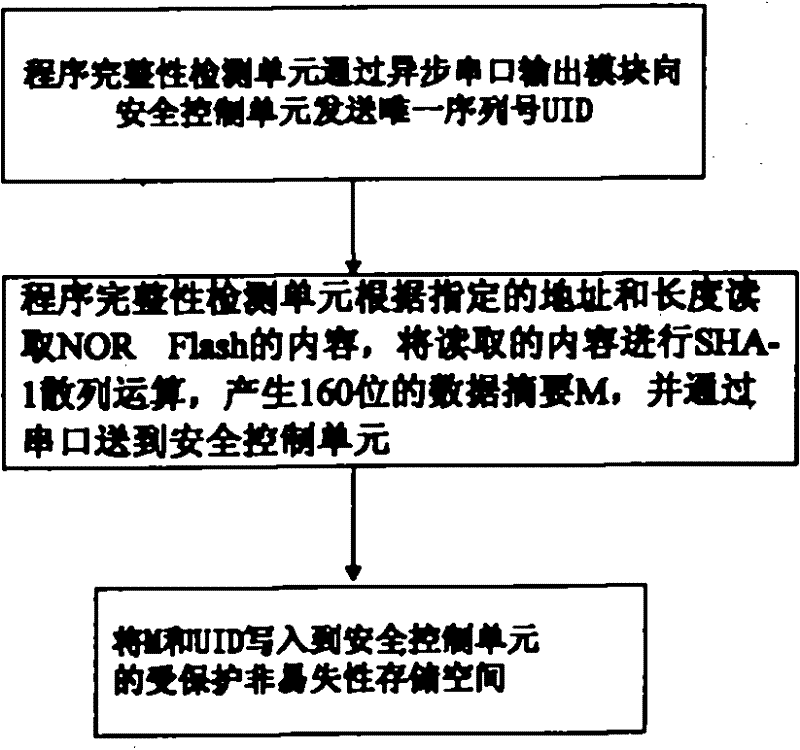
The invention discloses an embedded-type system for ensuring the completeness of a program, which comprises an embedded-type microprocessor, a storage device, a program completeness detection unit and a safety control unit wherein: the program completeness detection unit is used for detecting content of an appointed area of the storage device before the running, utilizing a standard hash function to calculate the hashed value of the area in the appointed area, for encrypting the hashed value and for transmitting the hashed value to the safety control unit; and the safety control unit is used for storing a correct hashed value of the content in the appointed area of the storage device, for comparing the correct hashed value with a running time hashed value which is transmitted by the completeness detection unit, and for judging whether the appointed area is altered. The invention also discloses a realization method of the embedded-type system for ensuring the completeness of the program, which comprises a configuration process and a running time detection process. The embedded-type system solves the safety problem that the code in the conventional system is easy to be altered, has the advantages of universality, low cost, less running expenditure and the like, and is particularly suitable for ensuring the completeness of the most basic trusted root of the embedded-type system.
Owner:SOUTH CHINA UNIV OF TECH
System, apparatus, method and computer program for transferring content
ActiveUS8074290B2Reduce usageEasy to useData processing applicationsDigital data processing detailsKey exchangeTransfer system
Owner:SONY CORP
System, apparatus, method and computer program for transferring content
InactiveUS20120110613A1Reduce usageEasy to useData processing applicationsAnalogue secracy/subscription systemsComputer hardwareComputer program
Apparatus and methods are provided for moving electronic content between devices. In one implementation, an content-transmitting apparatus may include a transmitting unit configured to transmit content to a content-receiving apparatus. The content-transmitting apparatus may also include a determination unit configured to determine, in response to the transmission, whether first key information associated with the content-receiving apparatus corresponds to second key information associated with the content-transmitting apparatus. A receiving unit may be configured to receive a confirmation message from the content-receiving apparatus, and a confirmation unit may be configured to confirm whether the content is usable at the content-receiving apparatus, based on at least the confirmation message.
Owner:SONY CORP
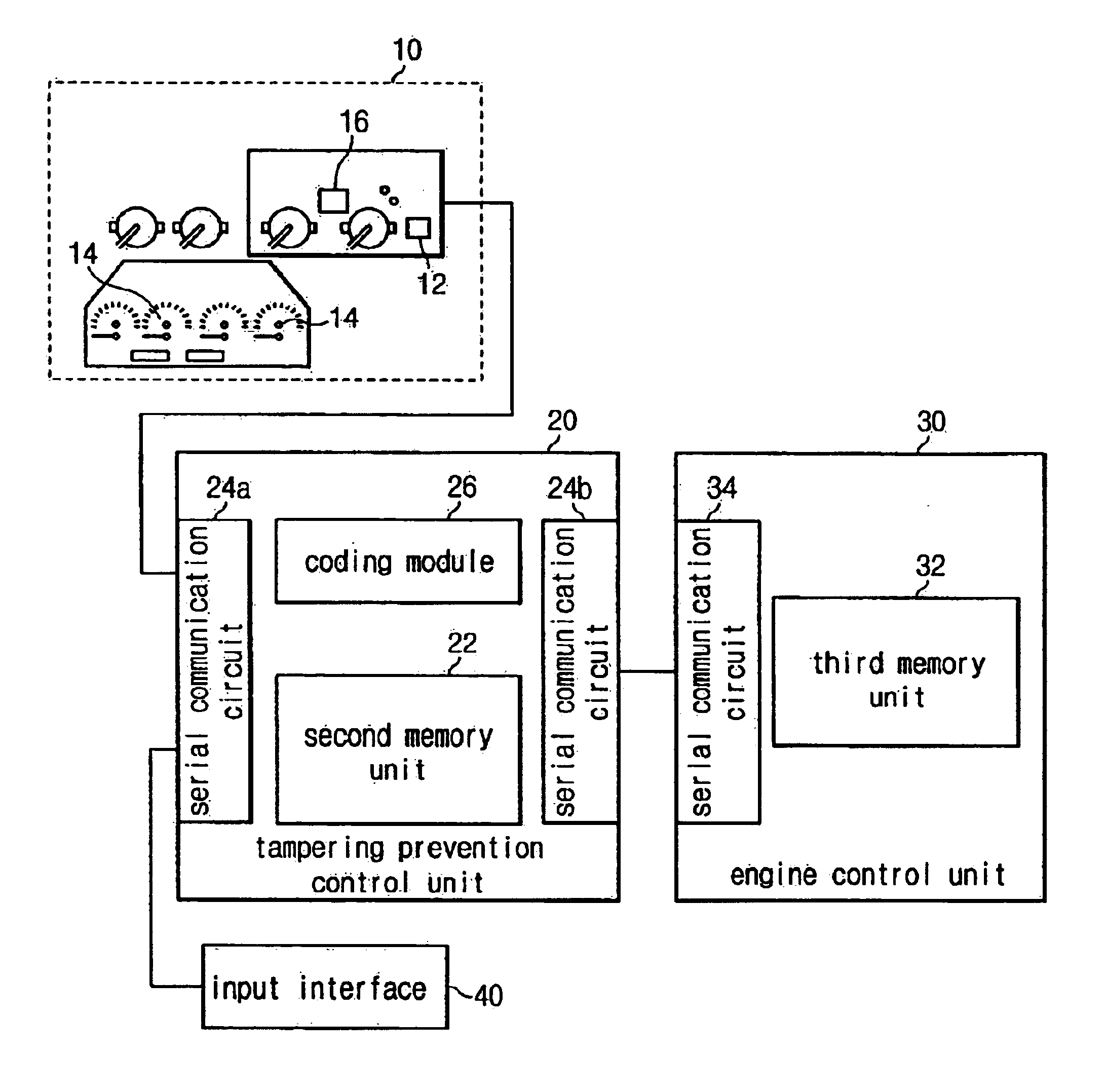
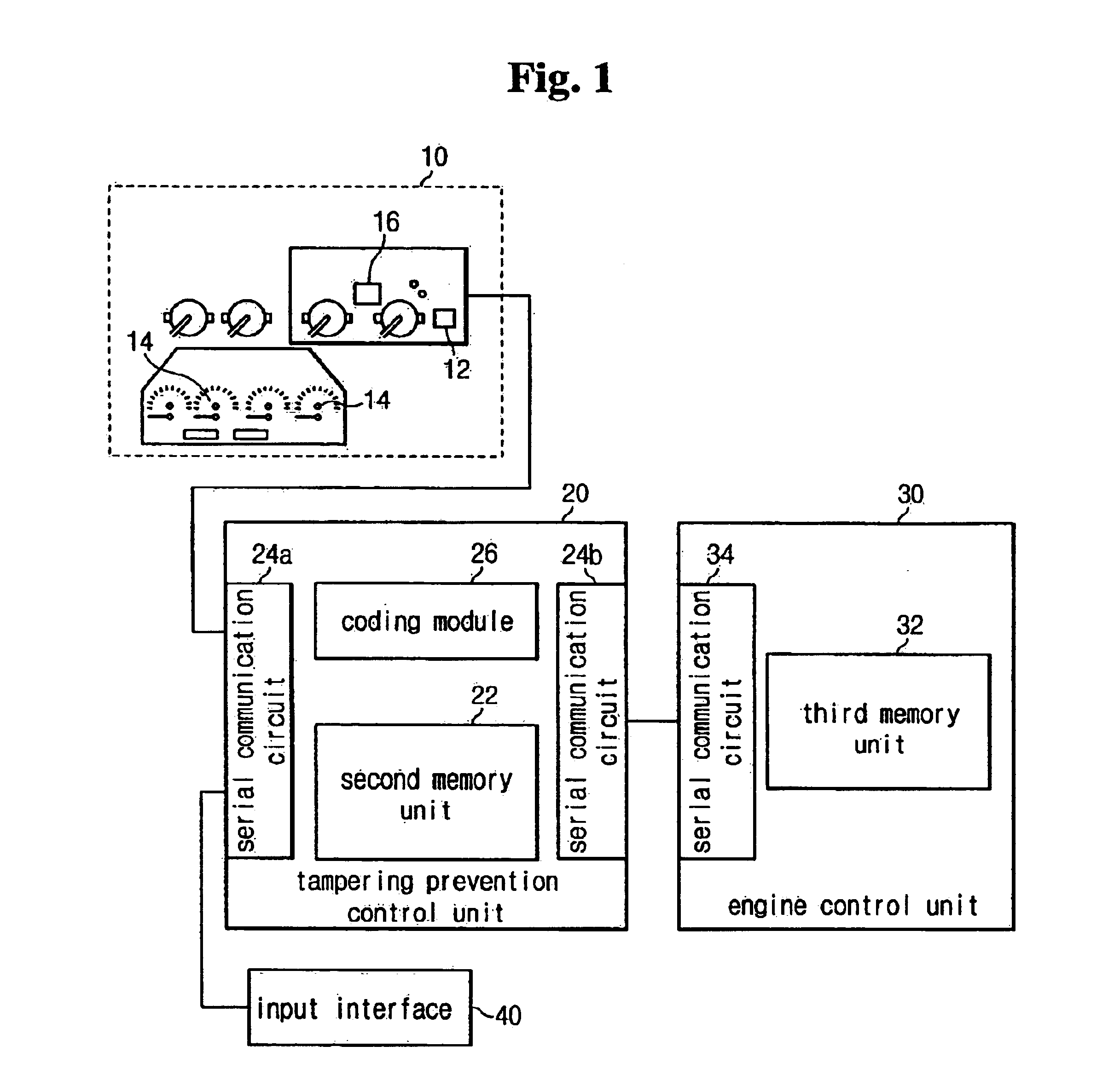
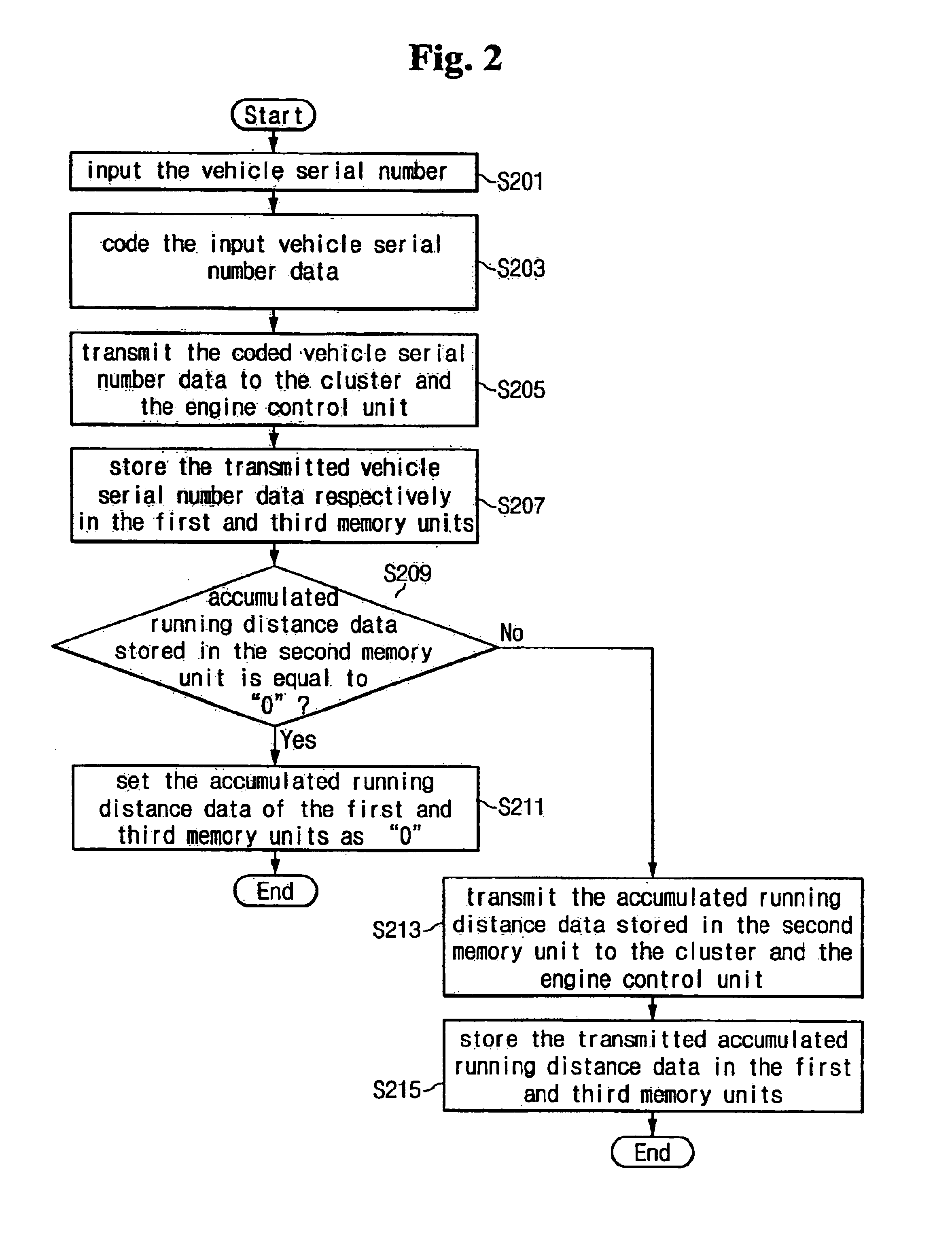
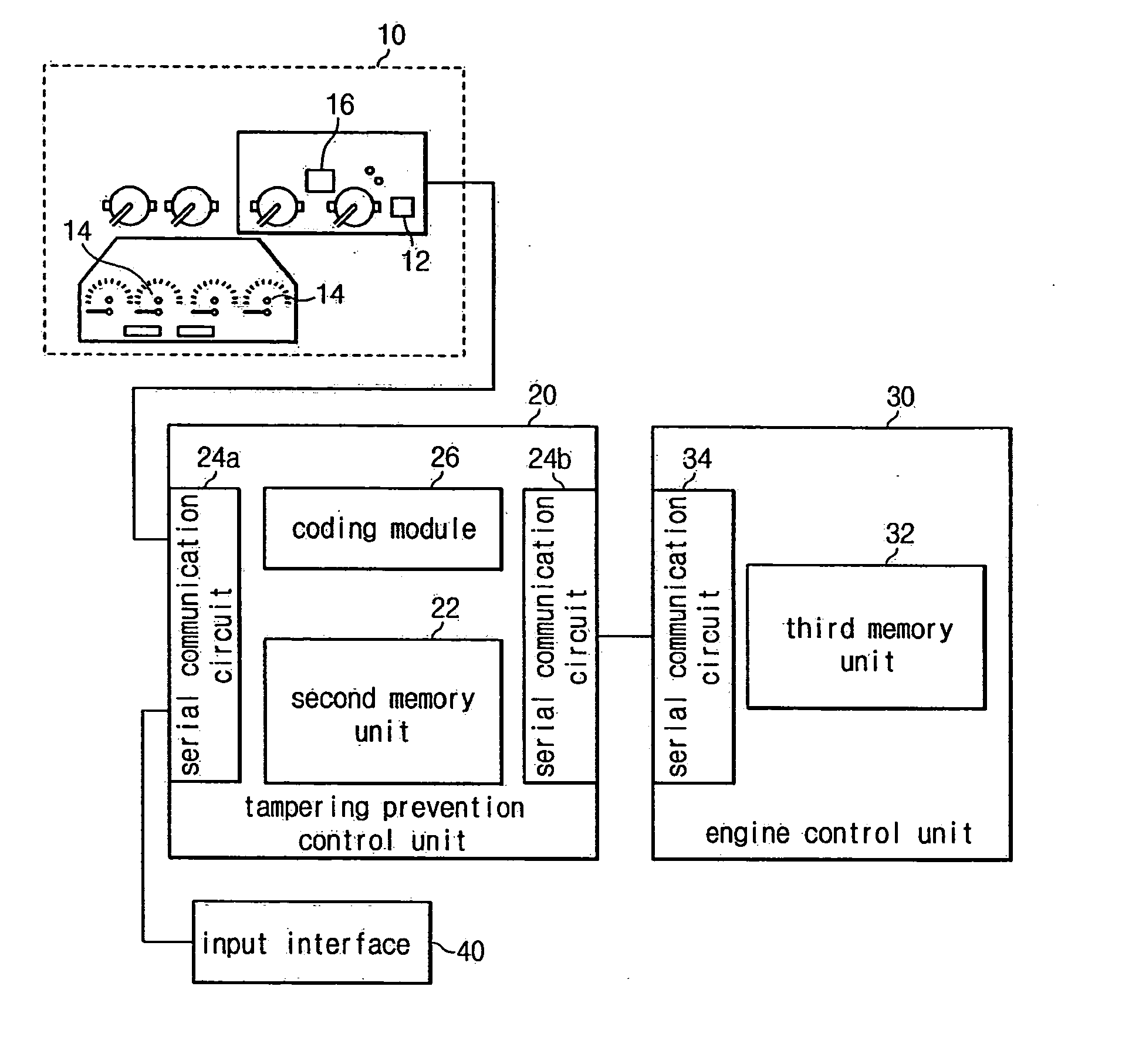
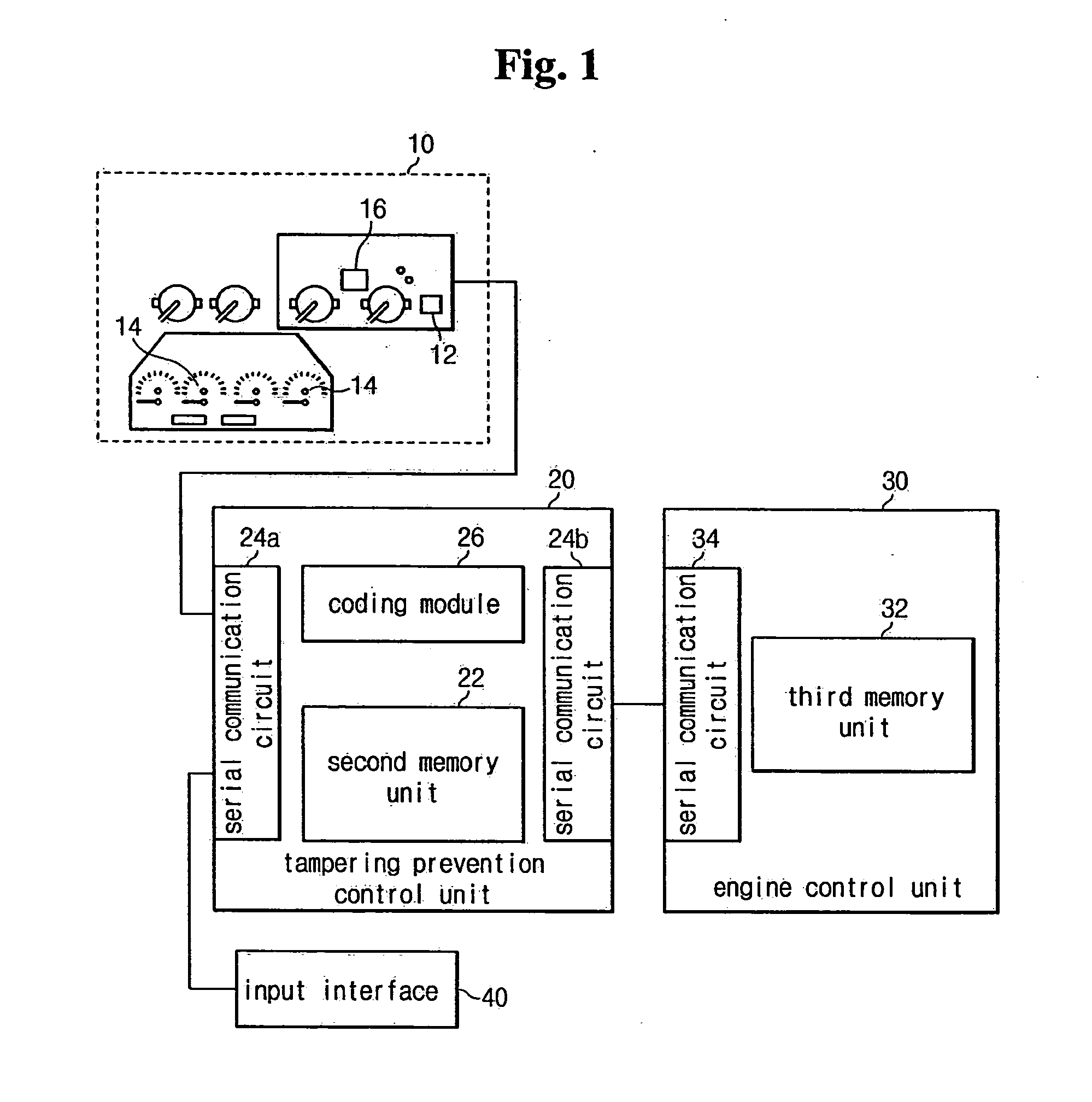
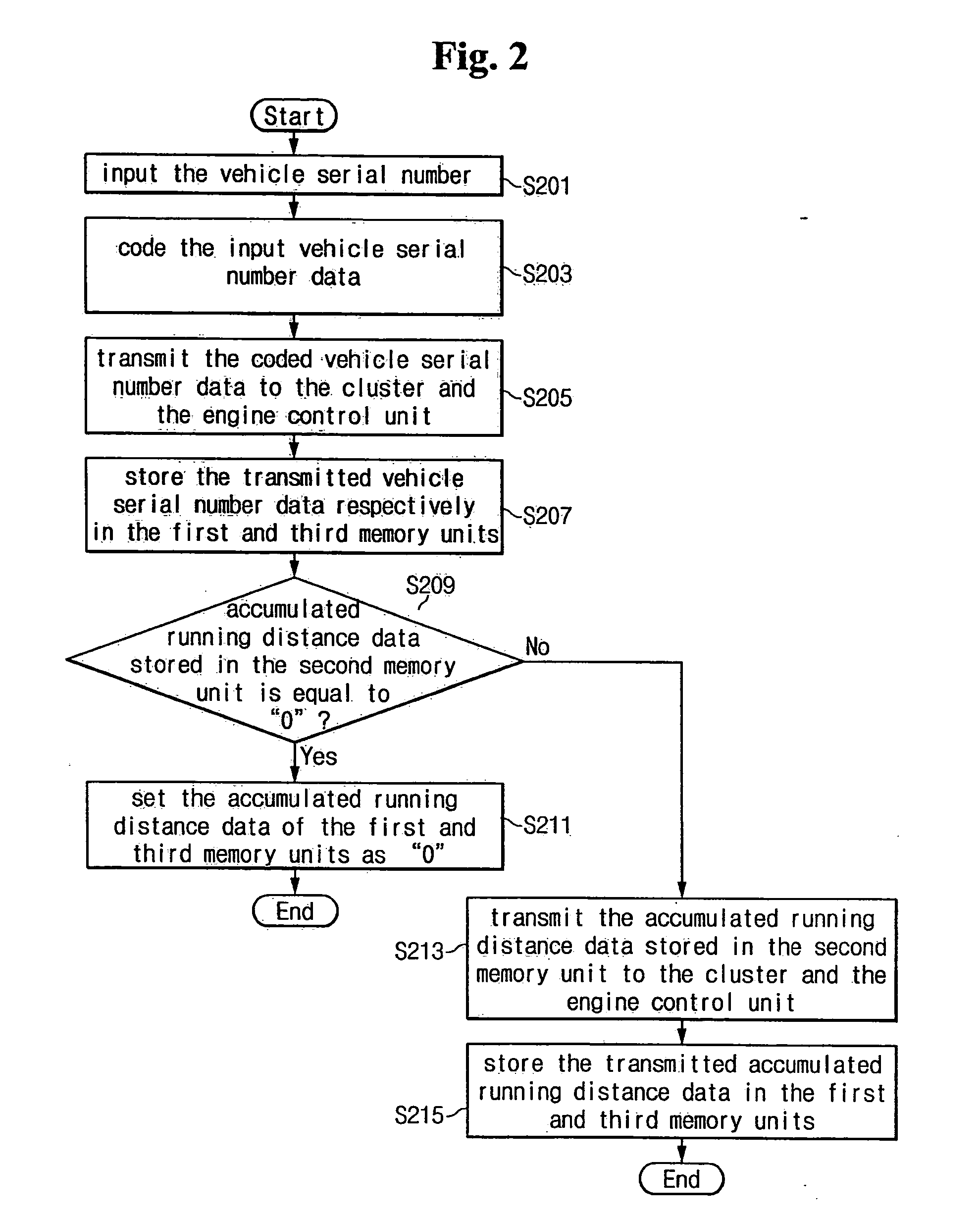
System and a method for preventing tampering with a recorded accumulated running distance of a vehicle
InactiveUS6961671B2Increase credibilityEasy to tamper withRegistering/indicating working of vehiclesFeeler-pin gaugesPrevention controlData storing
A system for preventing tampering with recorded accumulated running distance data is provided which comprises a first memory, a tampering prevention control unit, and a third memory. The tampering prevention control unit is configured to output an error message if the vehicle serial number data stored in the second memory unit is not equal to the vehicle serial number data stored in the first memory unit and in the third memory unit. The tampering prevention control unit is configured to determine whether the accumulated running distance data stored in the second memory unit is equal to the accumulated running distance data stored in the first memory unit, and if not, the tampering prevention control unit stores the accumulated running distance data stored in the second memory unit to the first memory unit.
Owner:HYUNDAI MOTOR CO LTD
System and a method for preventing tampering with a recorded accumulated running distance of a vehicle
InactiveUS20050045713A1Increase credibilityEasy to tamper withTicket-issuing apparatusRegistering/indicating working of vehiclesTamper resistanceMemory cell
A system for preventing tampering with recorded accumulated running distance data is provided which comprises a first memory, a tampering prevention control unit, and a third memory. The tampering prevention control unit is configured to output an error message if the vehicle serial number data stored in the second memory unit is not equal to the vehicle serial number data stored in the first memory unit and in the third memory unit. The tampering prevention control unit is configured to determine whether the accumulated running distance data stored in the second memory unit is equal to the accumulated running distance data stored in the first memory unit, and if not, the tampering prevention control unit stores the accumulated running distance data stored in the second memory unit to the first memory unit.
Owner:HYUNDAI MOTOR CO LTD
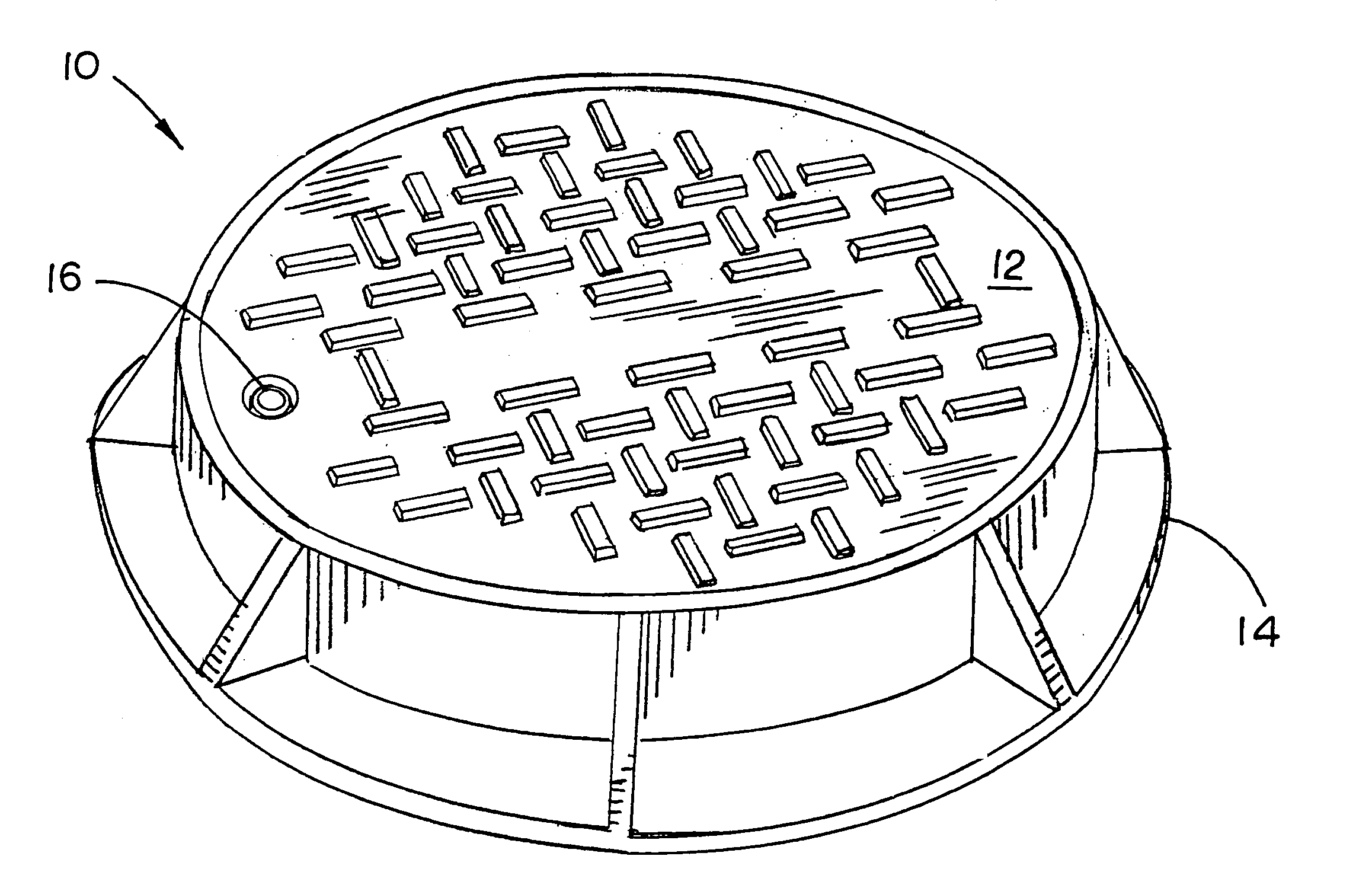
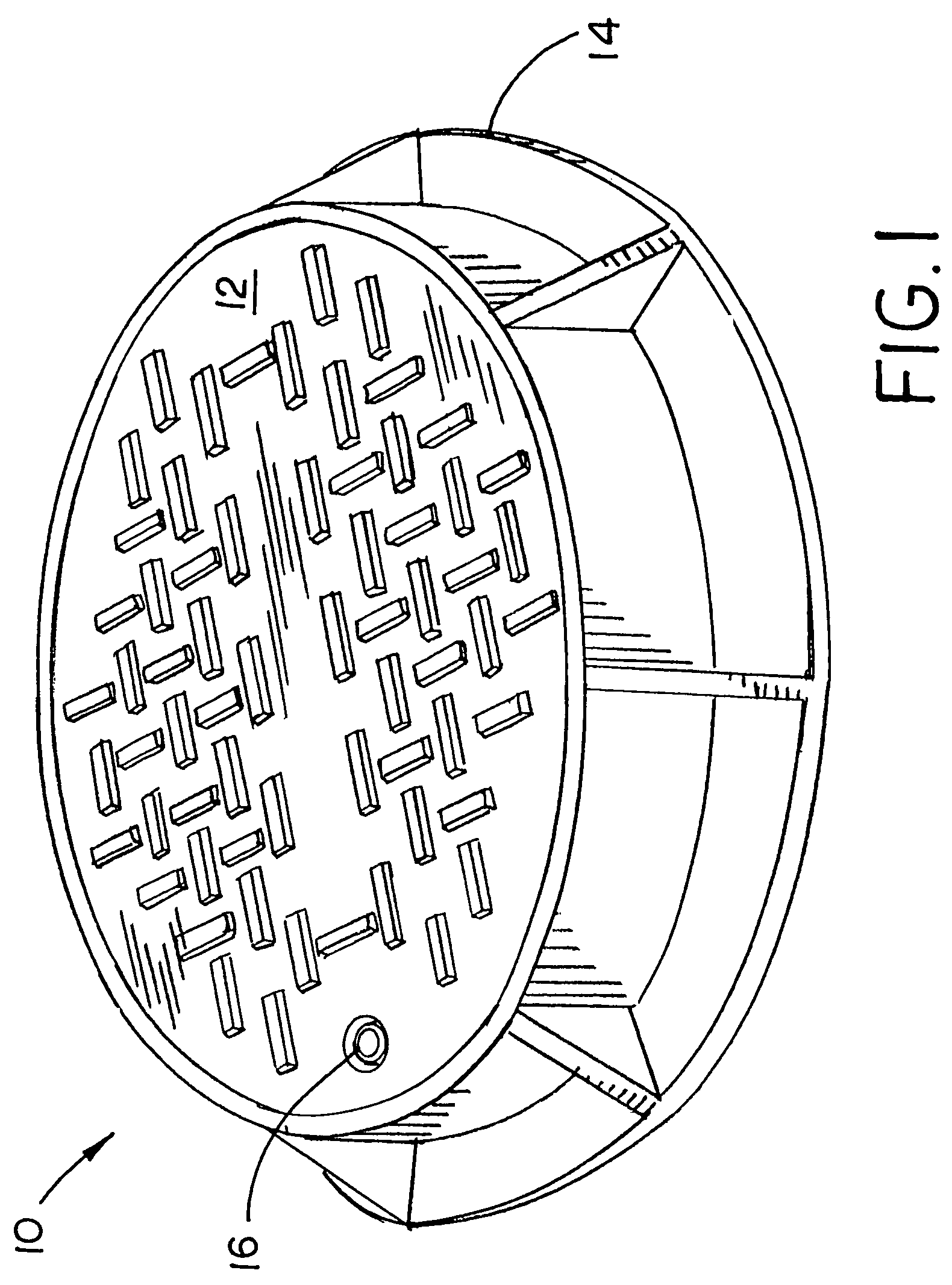
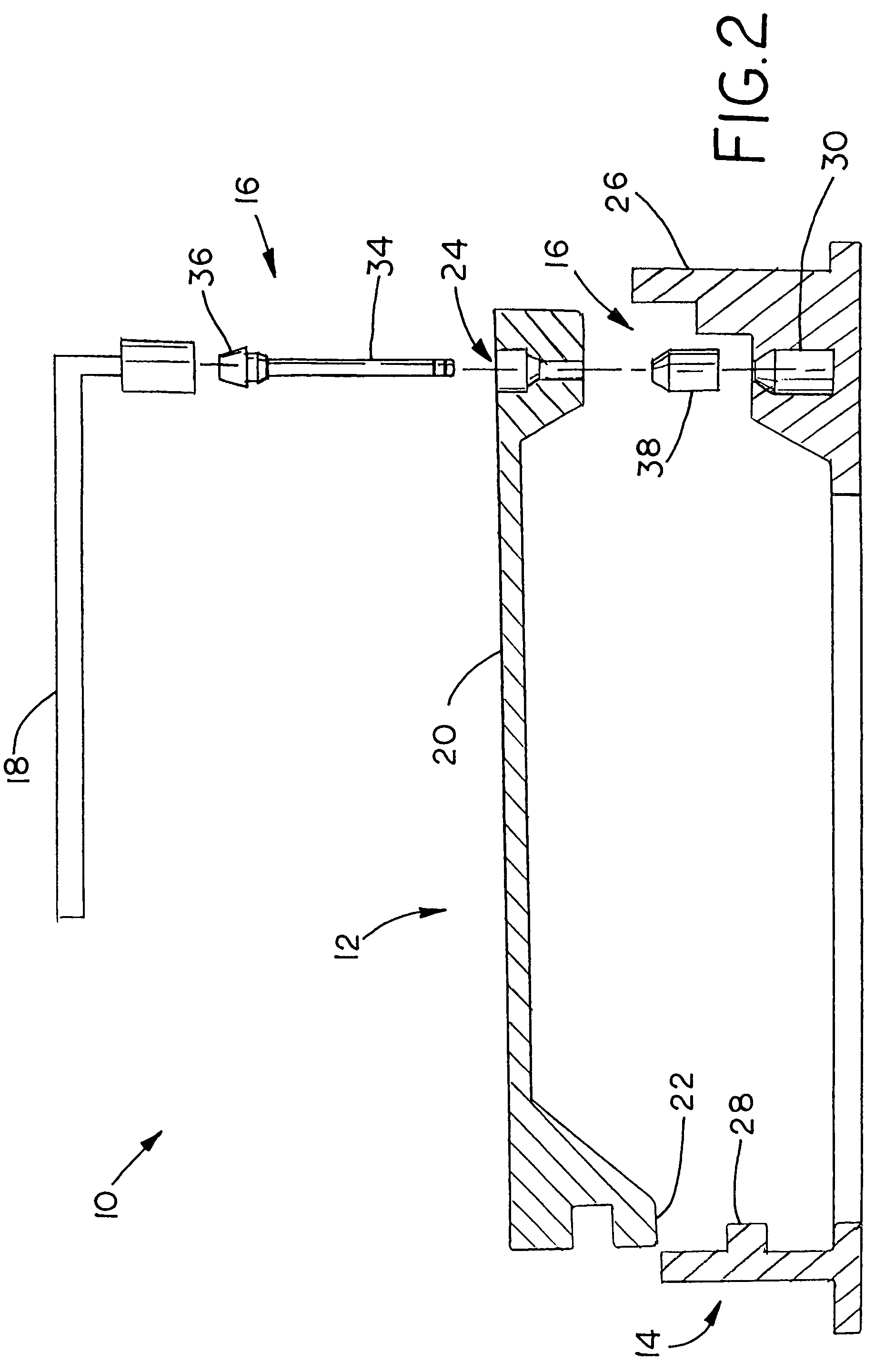
Lockable manhole cover
A manhole system including a cover, a frame receiving the cover and at least one security device securing the cover to the frame.
Owner:MEYERS WILLIAM G
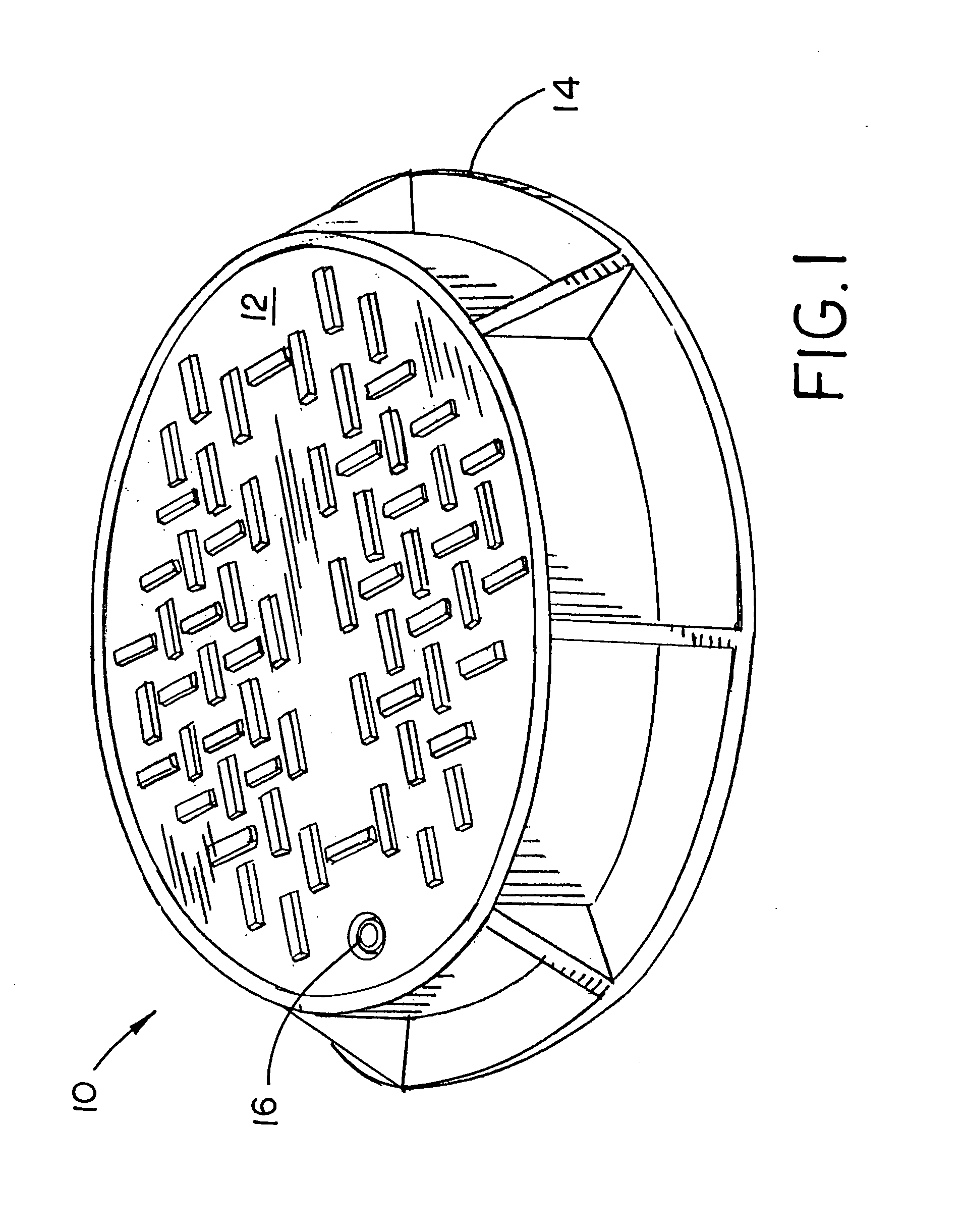
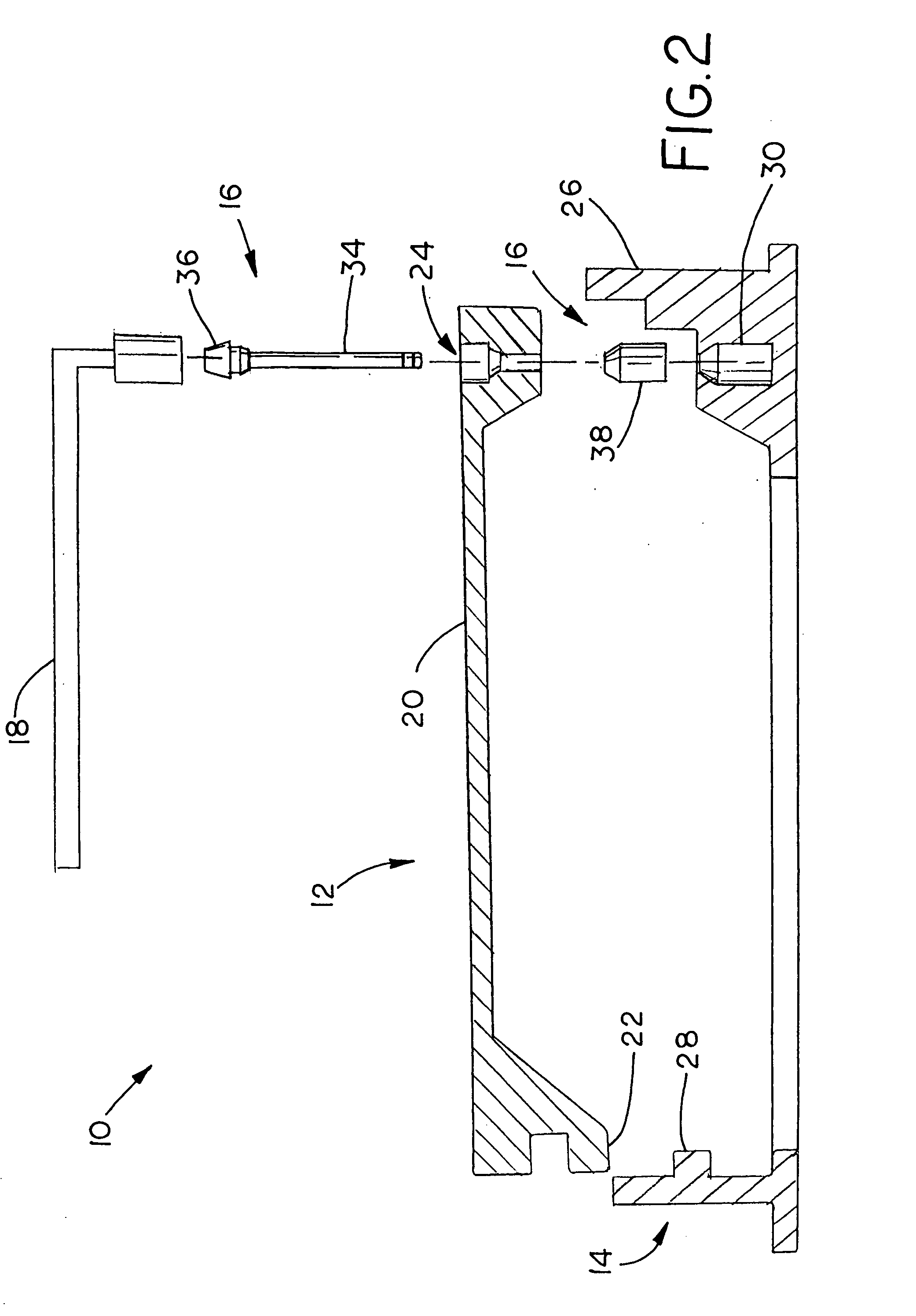
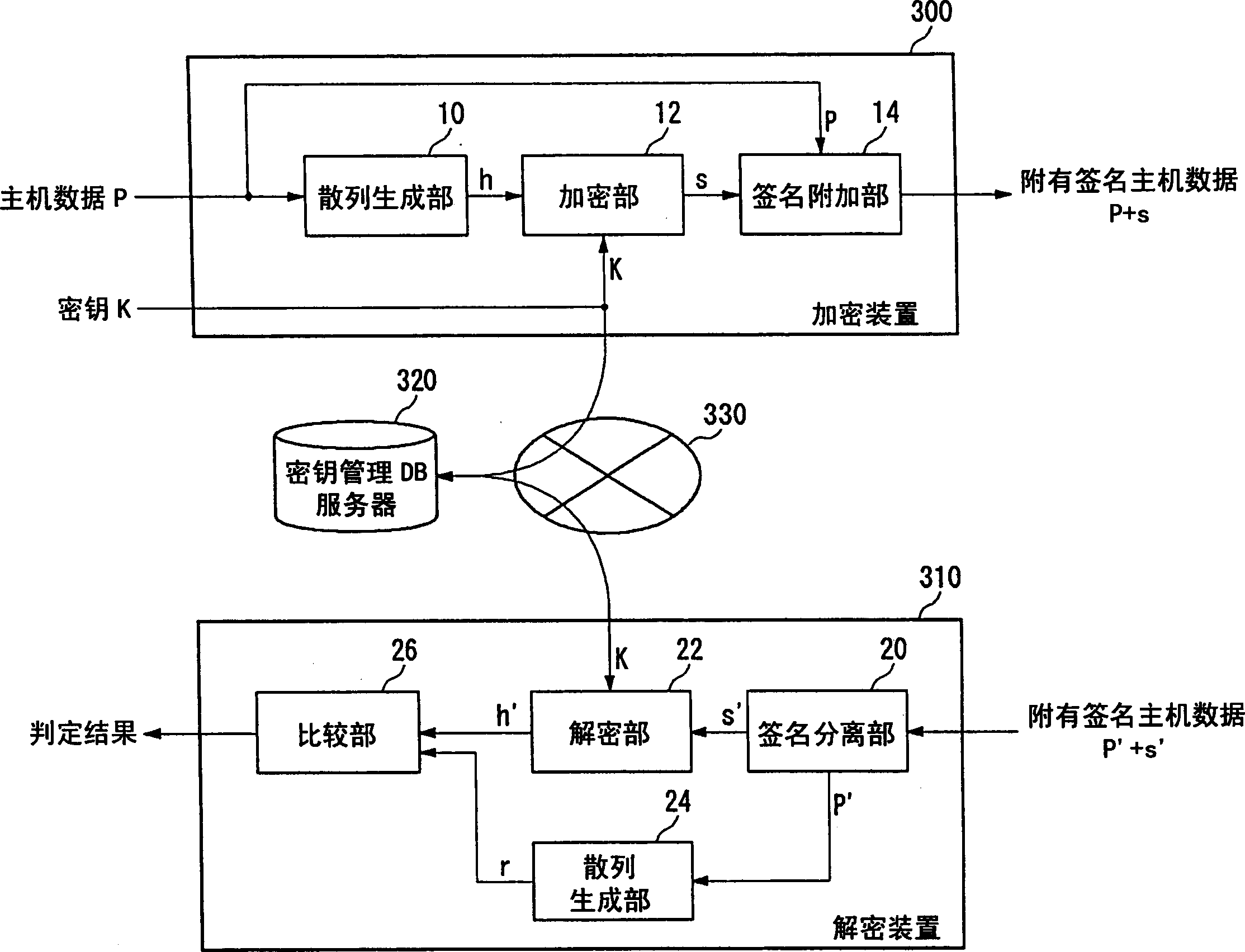
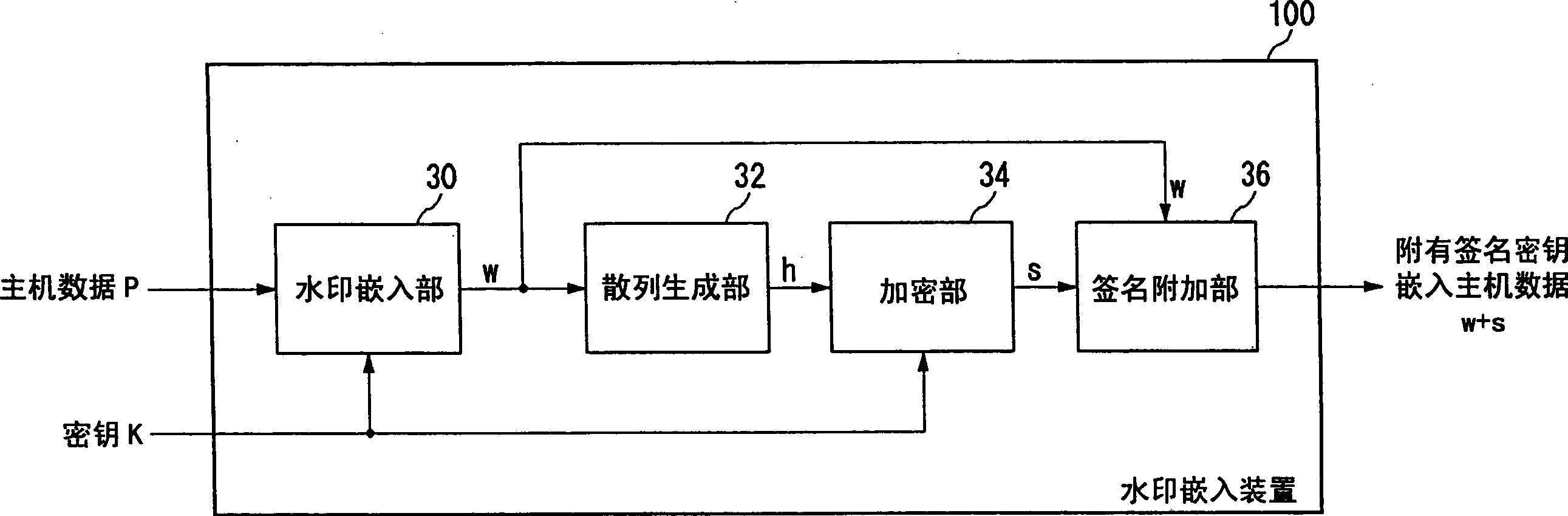
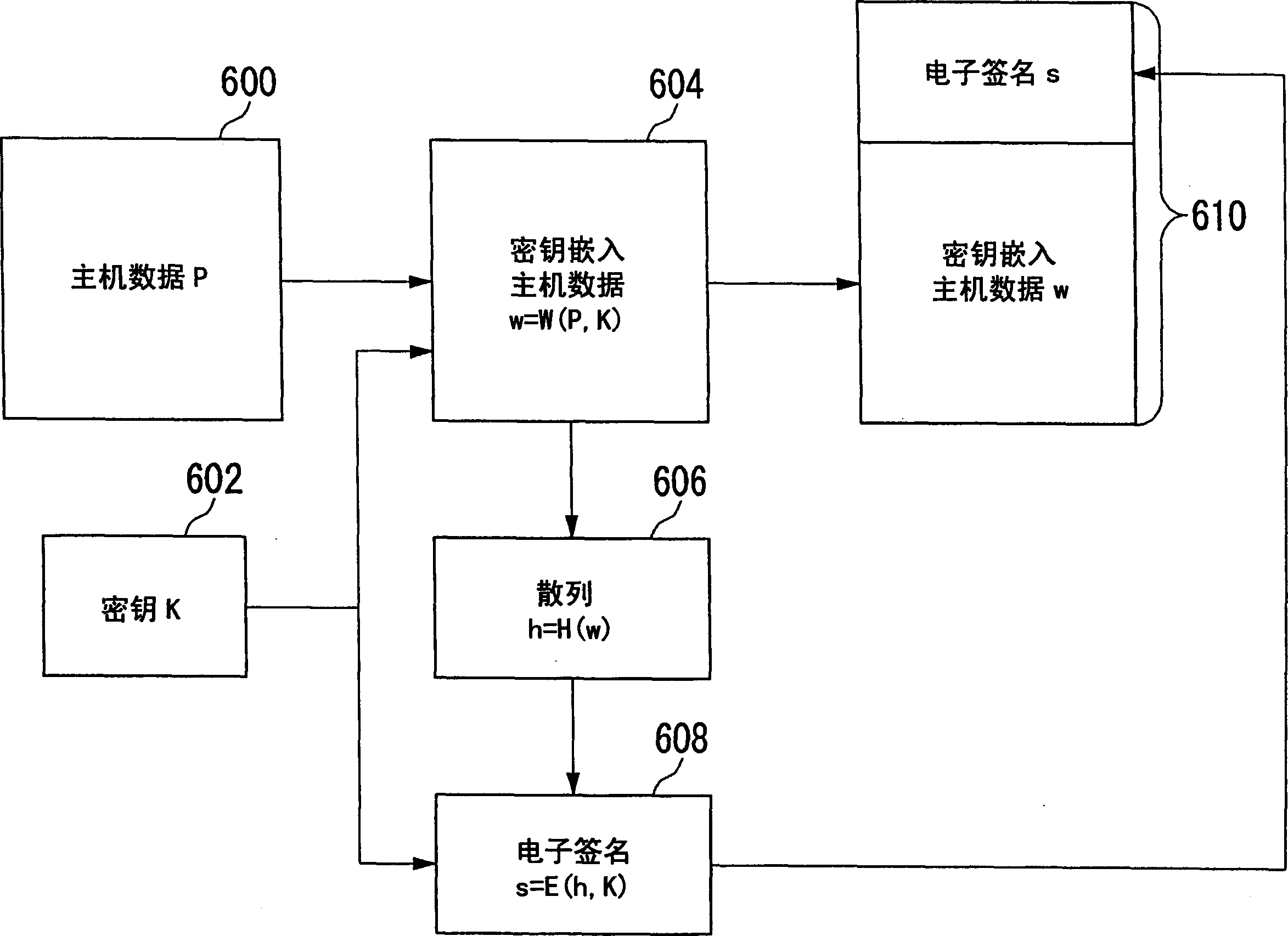
Electronic watermark embedded device and method and electronic watermark pick up device and method
InactiveCN1658555AEasy to tamper withKey distribution for secure communicationUser identity/authority verificationComputer securityWatermark embedding
A watermark embedder embeds a cryptographic key as a digital watermark into input host data and thereby generates key-embedded host data, and then provides it to a hash generator and a signature attacher. A hash generator generates a hash by putting the key-embedded host data into a one-way function, and provides the hash to an encryptor. The encryptor encrypts hash generated by the hash generator with the cryptographic key and thereby generates a digital signature. The signature attacher attaches the digital signature generated by the encryptor to the key-embedded host data generated by the watermark embedder, and outputs the signature-attached key-embedded host data.
Owner:SANYO ELECTRIC CO LTD
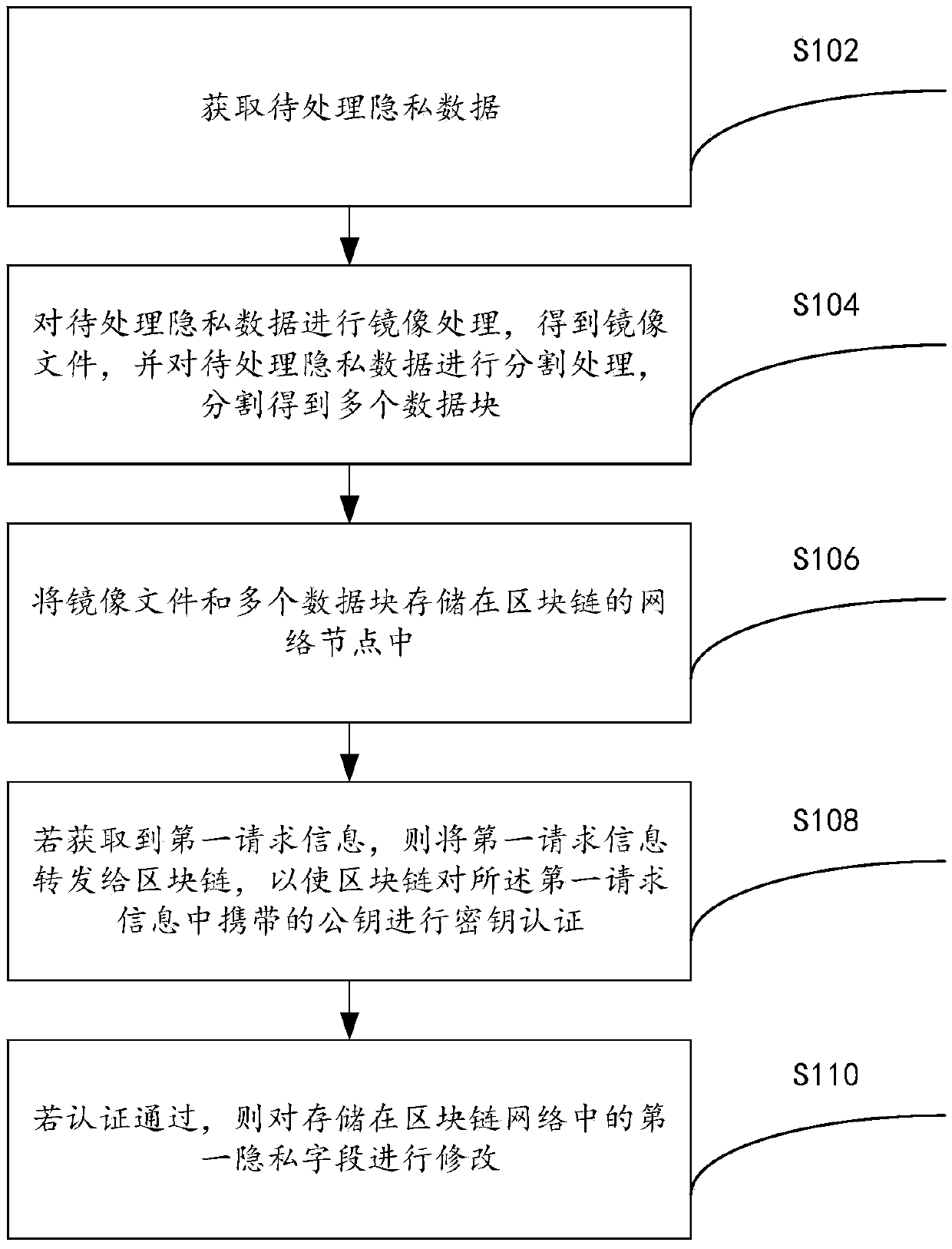
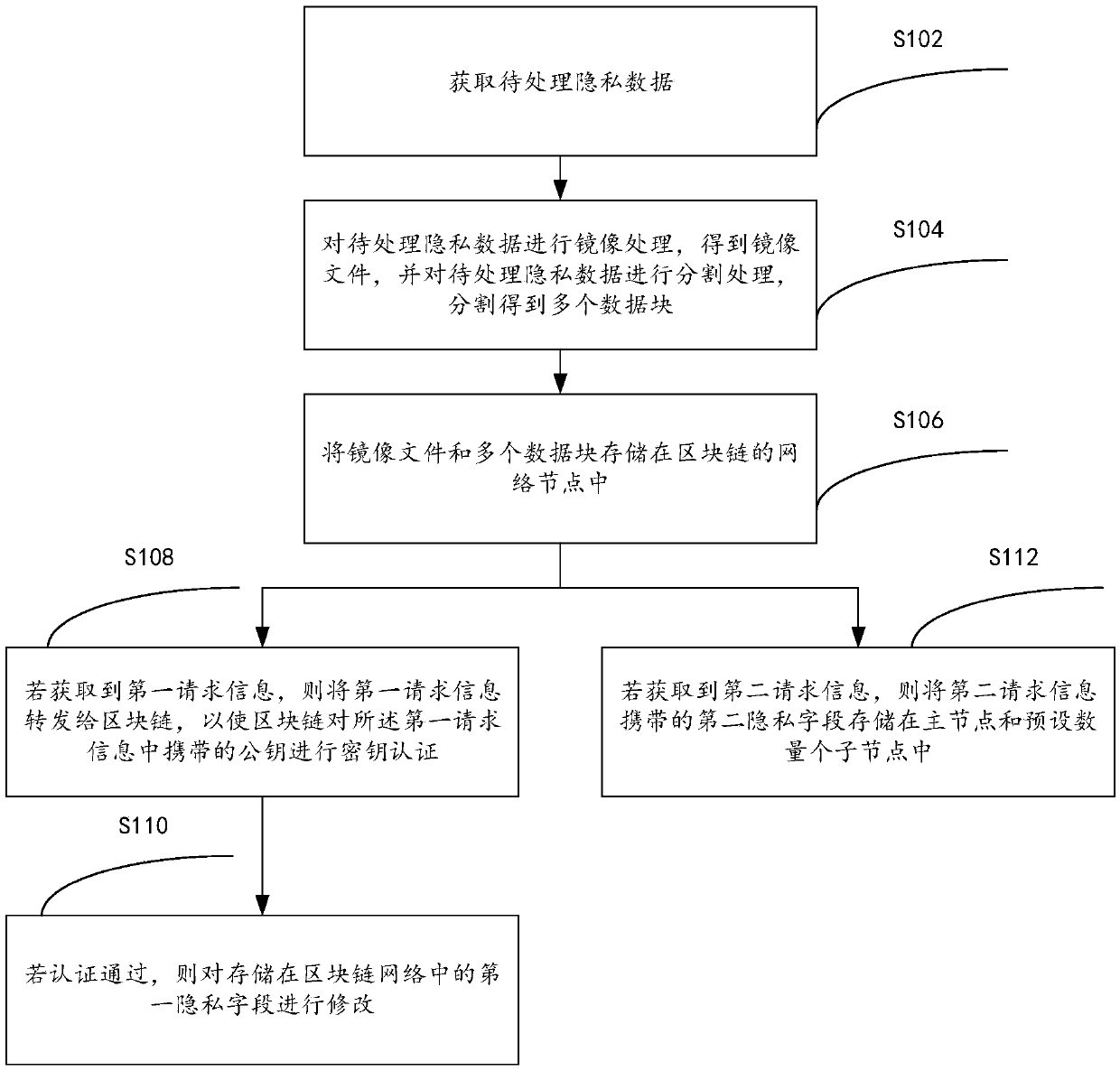
A privacy information tamper-proofing method and system based on a block chain technology
ActiveCN109684878APrevent tamperingEasy to tamper withDigital data protectionChain networkBlockchain
The invention provides a privacy information tamper-proofing method and system based on a blockchain technology, and relates to the technical field of data security, and the method comprises the steps: obtaining to-be-processed privacy data; Performing mirror image processing on the to-be-processed privacy data to obtain a mirror image file; Carrying out segmentation processing on the to-be-processed private data to obtain a plurality of data blocks; Storing the mirror image file and the plurality of data blocks in a network node of a block chain, each network node being provided with a key pair; If the first request information is obtained, the first request information is forwarded to a block chain, so that the block chain carries out key authentication on a public key carried in the first request information, and the first request information is request information for modifying a first privacy field in the to-be-processed privacy data; And if the authentication is passed, modifyingthe first privacy field stored in the block chain network, thereby solving the technical problem that the privacy data is easily tampered in the prior art.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
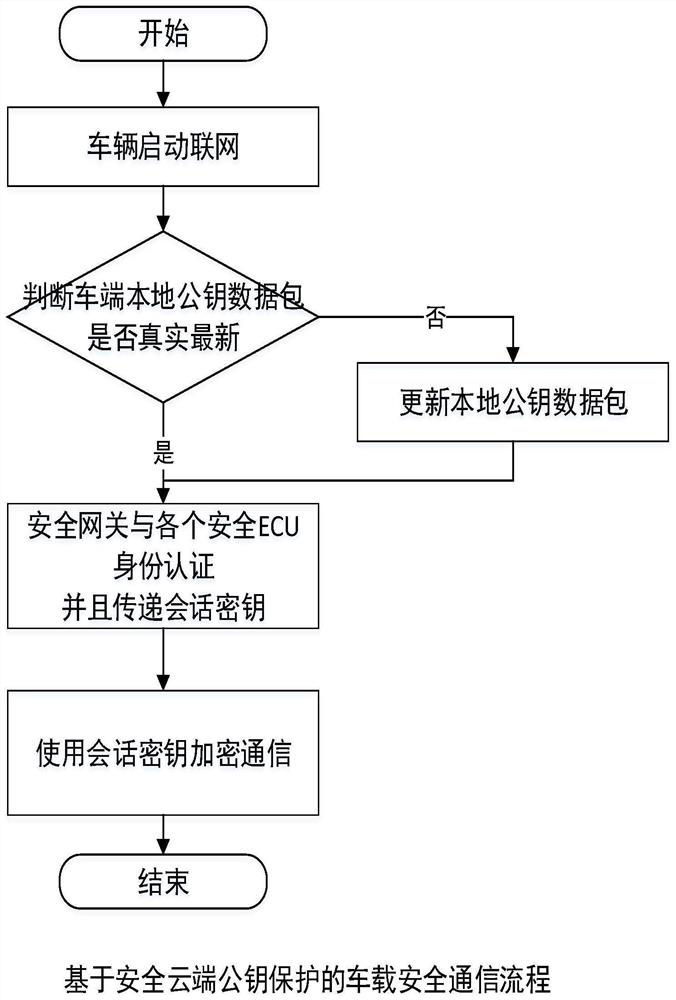
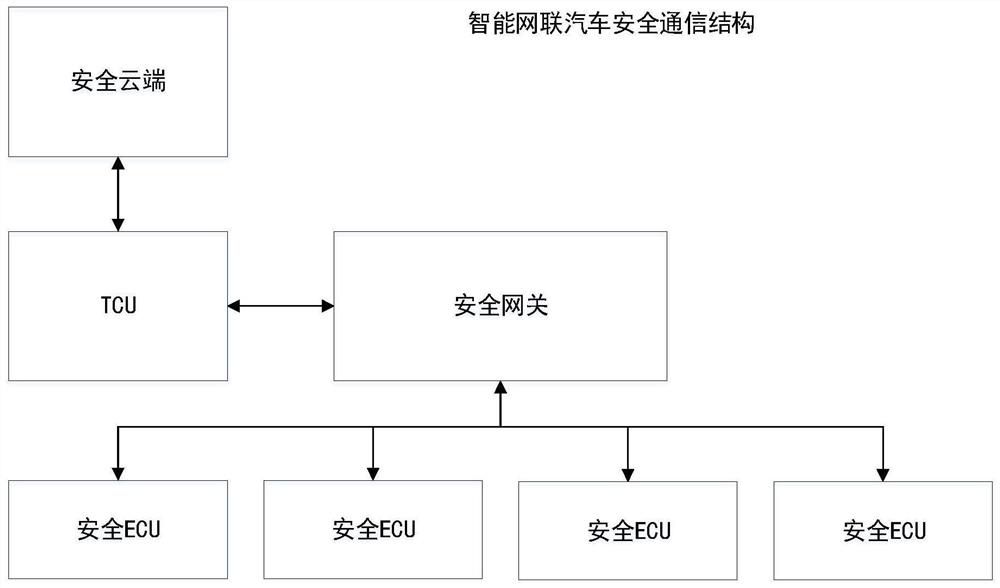
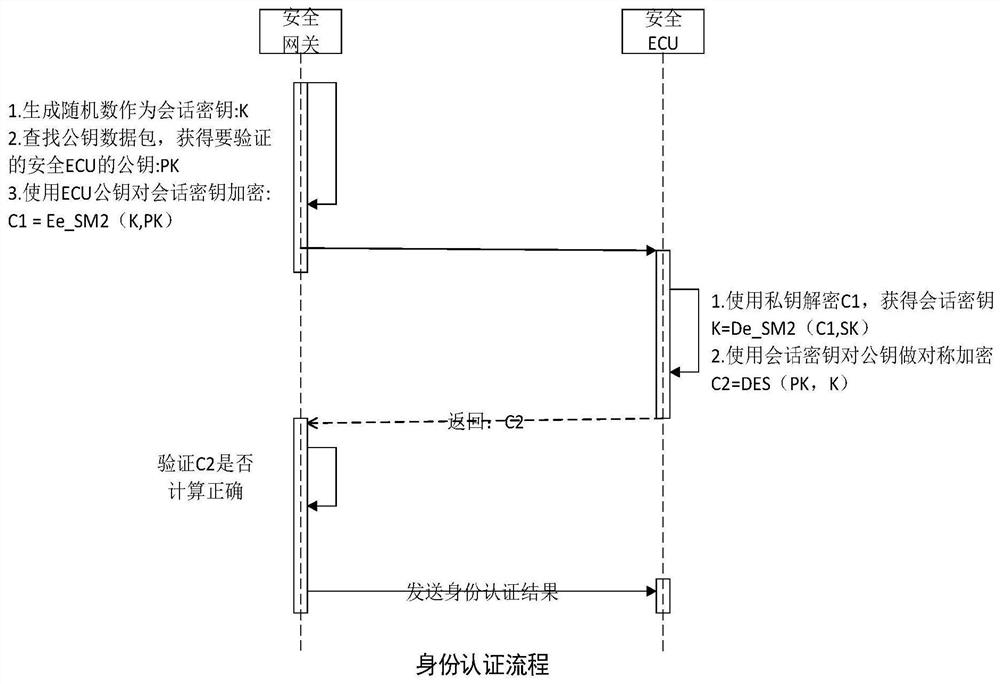
Vehicle-mounted safety communication method, system and device based on safety cloud public key protection
PendingCN113411294AMonitor Security StatusGuarantee authenticityKey distribution for secure communicationUser identity/authority verificationCommunications securityKey (cryptography)
The invention provides a vehicle-mounted security communication method, system and device based on security cloud public key protection. The intelligent networked automobile vehicle-mounted network communication comprises communication between a security cloud and a security TCU, communication between the security TCU and a security gateway, and communication between the security gateway and a security ECU, wherein the TCU is Telematics Control Unit; the security cloud and the security TCU communicate through a security wireless network communication technology, and bidirectional identity authenticity authentication is carried out between the security cloud and the TCU; and the security TCU and the security gateway are communicated by adopting a vehicle-mounted Ethernet security communication technology. The vehicle-mounted safety communication method, system and device based on the safety cloud public key protection have the beneficial effects that a whole set of safe, efficient and enforceable solution for network connection vehicle-mounted safety communication is provided, and the method comprises a public key data management and updating method based on the cloud safety protection; the invention discloses a challenge-response identity authentication method based on a public key cryptography technology, and a message encryption method based on a one-time session key.
Owner:CATARC TIANJIN AUTOMOTIVE ENG RES INST CO LTD
Lockable manhole cover
A manhole system including a cover, a frame receiving the cover and at least one security device securing the cover to the frame.
Owner:MEYERS WILLIAM G
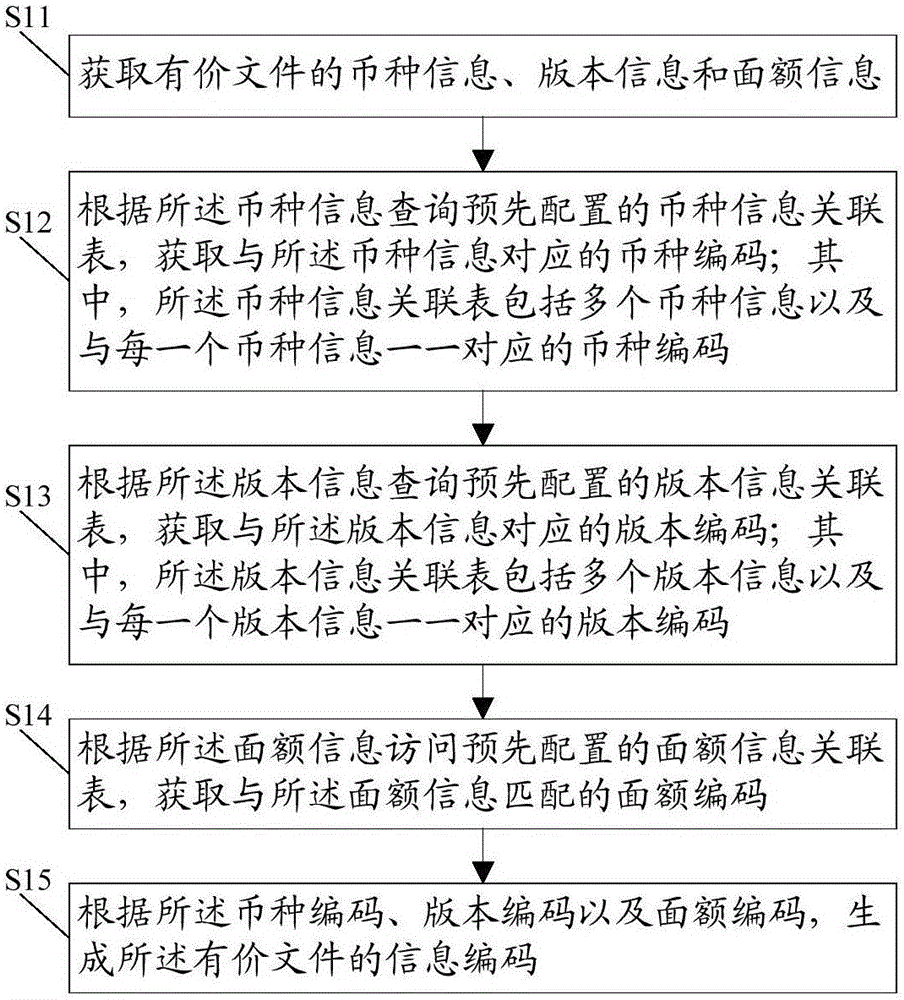
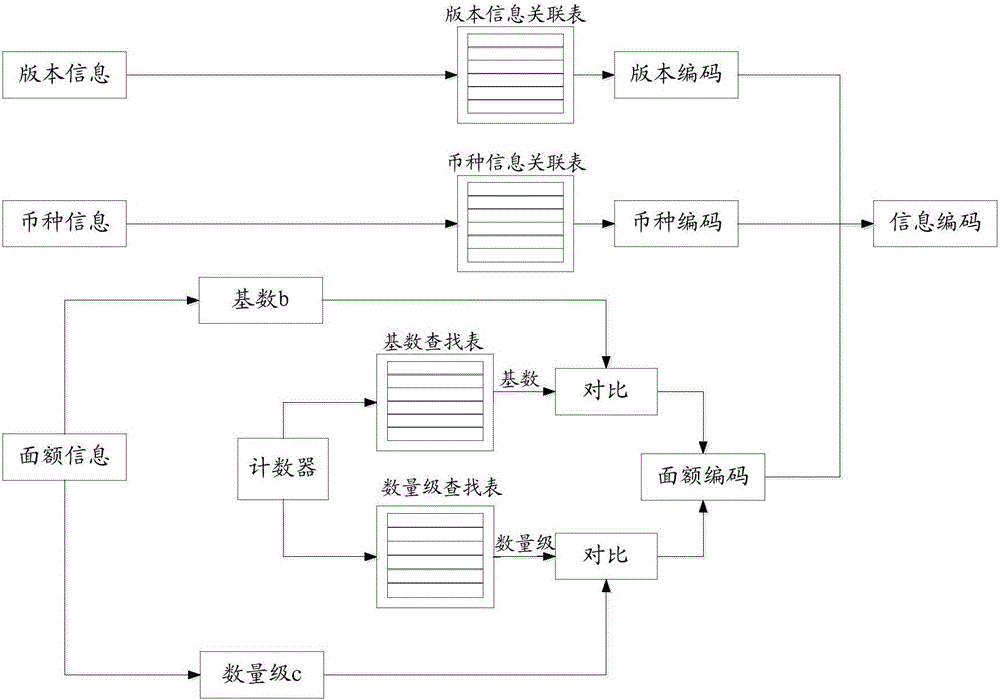
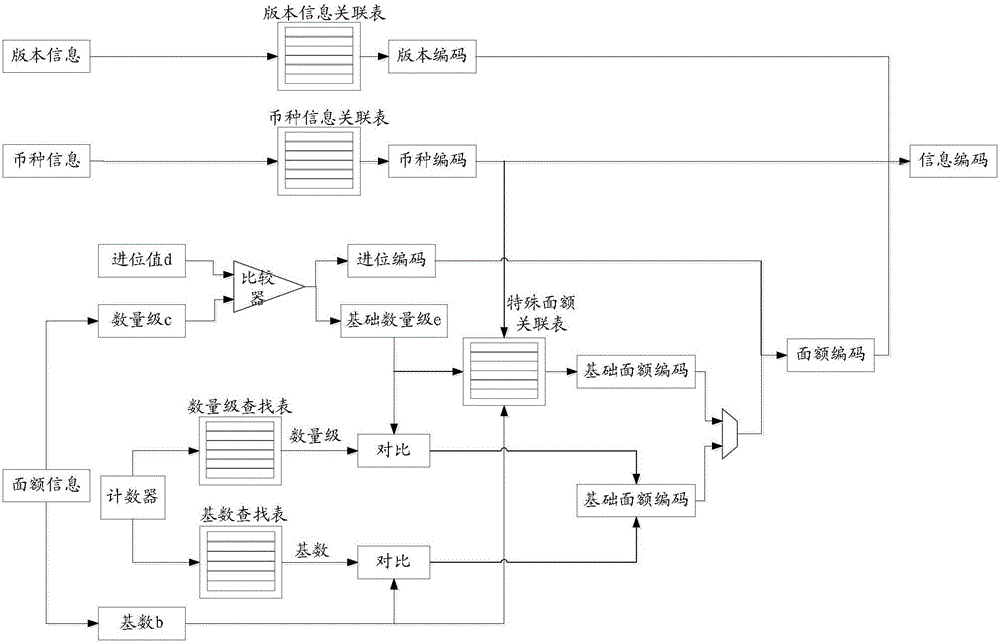
Valuable document information coding/decoding method and device, processing system and financial self-service equipment
ActiveCN106056758AEasy to tamper withComplete banking machinesCoin/currency accepting devicesDecoding methodsInformation access
The invention discloses a valuable document information coding method, which comprises the following steps: obtaining currency information, version information and denomination information of a valuable document; searching a pre-configured currency information association table according to the currency information and obtaining currency codes corresponding to the currency information; searching a pre-configured version information association table according to the version information and obtaining version codes corresponding to the version information; searching a pre-configured denomination information association table according to the denomination information, and obtaining denomination codes corresponding to the denomination information; and generating information codes of the valuable document according to the currency codes, the version codes and the denomination codes. The invention also provides a decoding method, a coding device, a decoding device, a processing system and financial self-service equipment. The method can realize coding of new-version and new-denomination valuable documents; and each code table is stored in hardware in the form of code data, so that the data cannot be modified by man and the risk of data tampering does not exist.
Owner:GRG BAKING EQUIP CO LTD
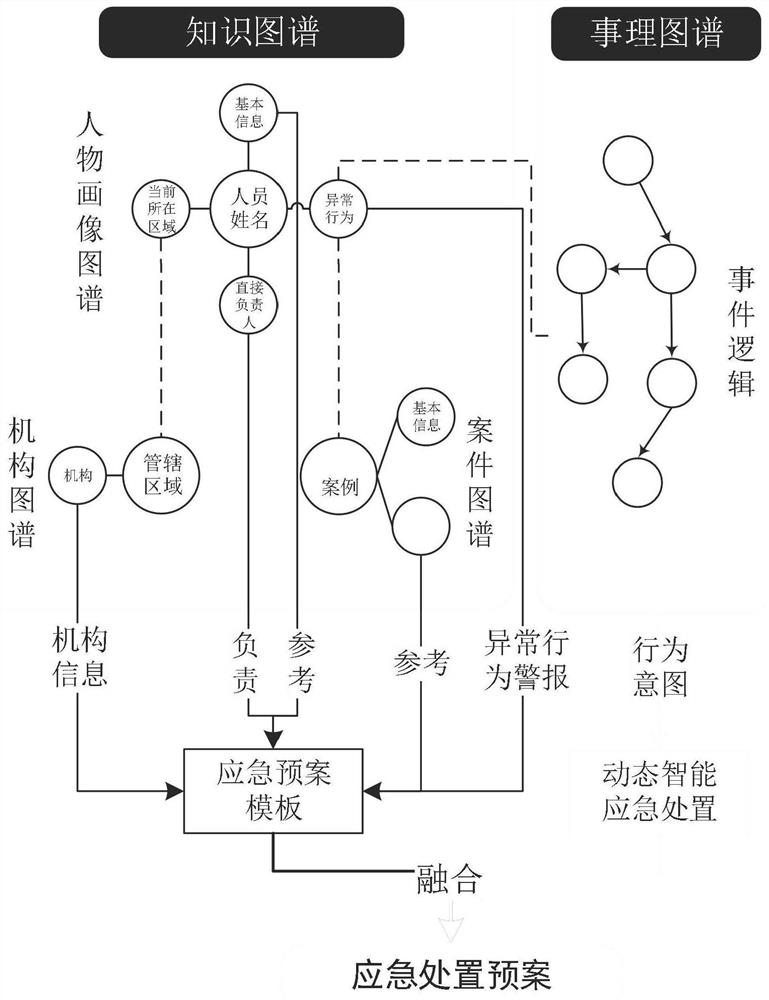
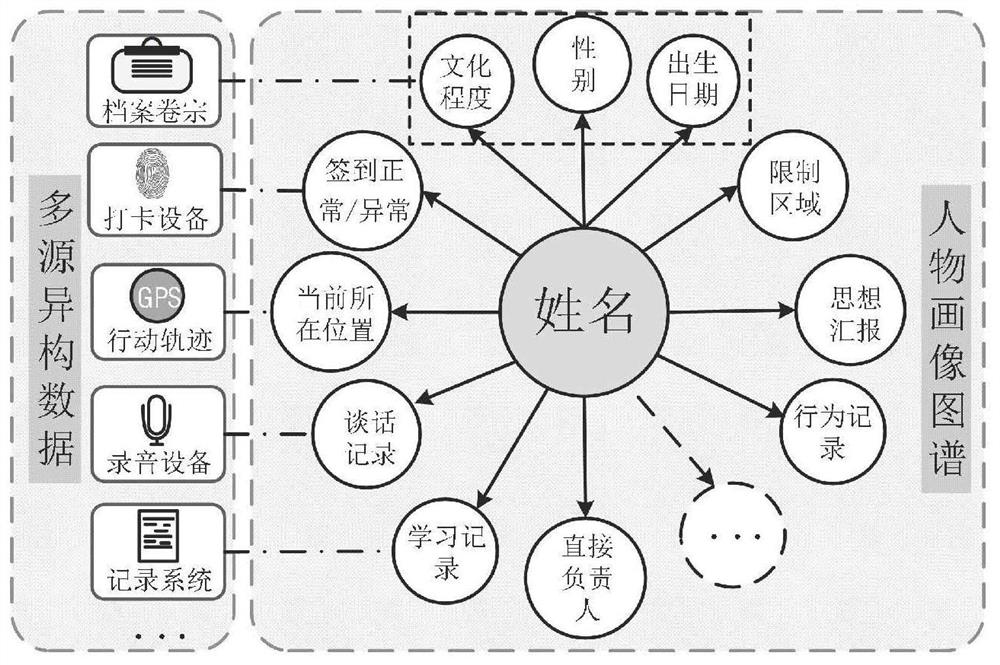
Emergency disposal plan method and system
PendingCN113407726AEasy to loseEasy to tamper withData processing applicationsSpecial data processing applicationsEmergency planFeature data
The invention relates to the technical field of verification, in particular to an emergency disposal plan method and system. The method comprises the following steps: according to intelligent equipment, obtaining data such as basic information and historical behavior tracks of centralized management personnel, extracting feature data from multiple dimensions such as a time sequence, space and a personnel relation network, establishing a personnel behavior feature library, and constructing a figure portrait map; then establishing an institution map to form an institution linkage network in a jurisdiction area so as to realize supervision; and providing a historical reference for the generation of an emergency plan. According to the invention, education reconstruction work quality and supervision quality are improved, personnel management cost is saved, and technical support is provided for emergency disposal of personnel.
Owner:中科嘉速(北京)信息技术有限公司 +1
Embedded-type system for ensuring completeness of program and realization method thereof
InactiveCN101882189BEasy to tamper withEasy to implementDigital data protectionHash functionRunning time
The invention discloses an embedded-type system for ensuring the completeness of a program, which comprises an embedded-type microprocessor, a storage device, a program completeness detection unit and a safety control unit wherein: the program completeness detection unit is used for detecting content of an appointed area of the storage device before the running, utilizing a standard hash functionto calculate the hashed value of the area in the appointed area, for encrypting the hashed value and for transmitting the hashed value to the safety control unit; and the safety control unit is used for storing a correct hashed value of the content in the appointed area of the storage device, for comparing the correct hashed value with a running time hashed value which is transmitted by the completeness detection unit, and for judging whether the appointed area is altered. The invention also discloses a realization method of the embedded-type system for ensuring the completeness of the program, which comprises a configuration process and a running time detection process. The embedded-type system solves the safety problem that the code in the conventional system is easy to be altered, has the advantages of universality, low cost, less running expenditure and the like, and is particularly suitable for ensuring the completeness of the most basic trusted root of the embedded-type system.
Owner:SOUTH CHINA UNIV OF TECH
Tag writing and reading method for semiconductor product
InactiveUS20060191991A1Easy to identifyEasy to tamper withRecord carriers used with machinesSpecial data processing applicationsCode conversionWorld Wide Web
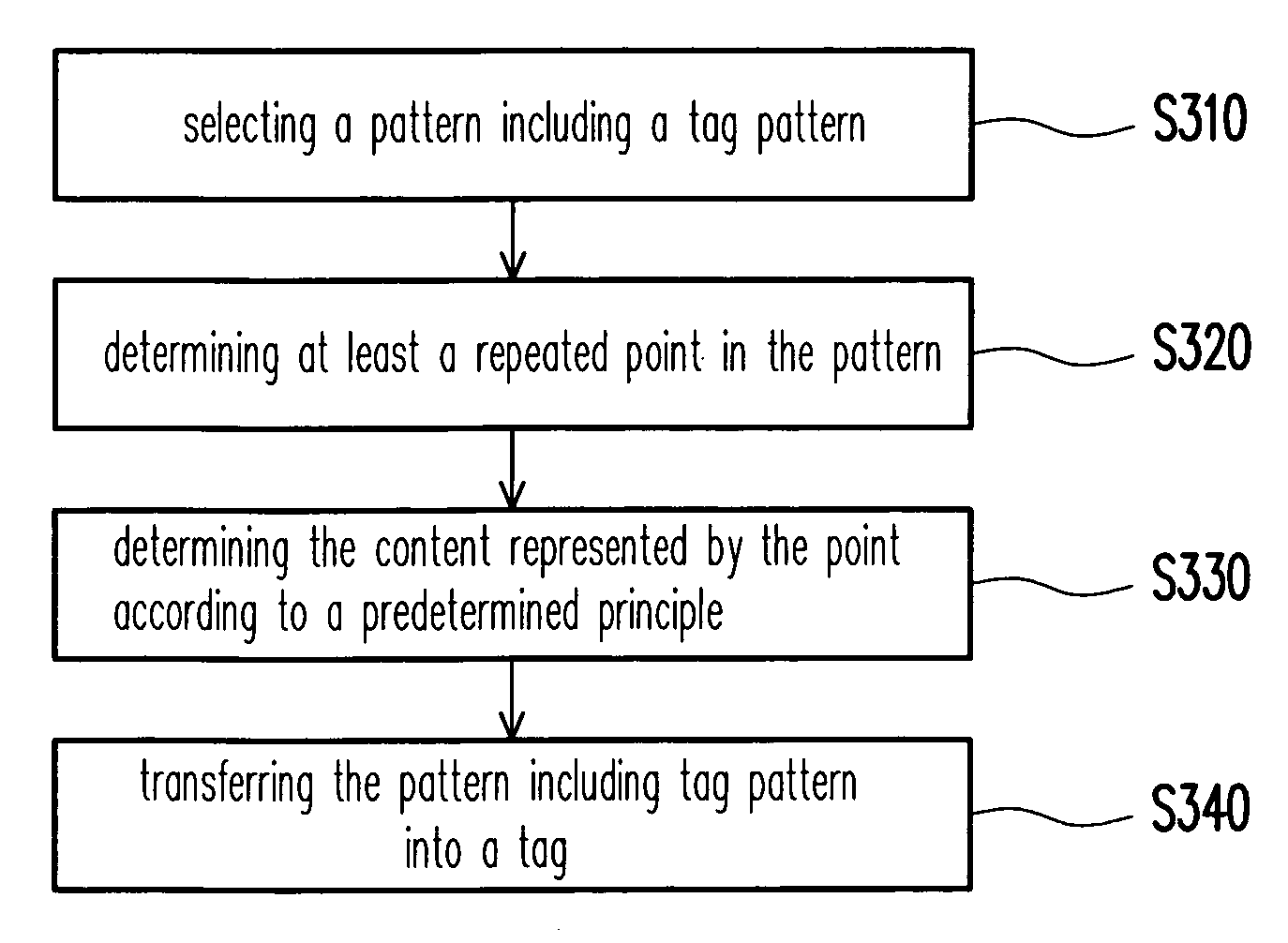
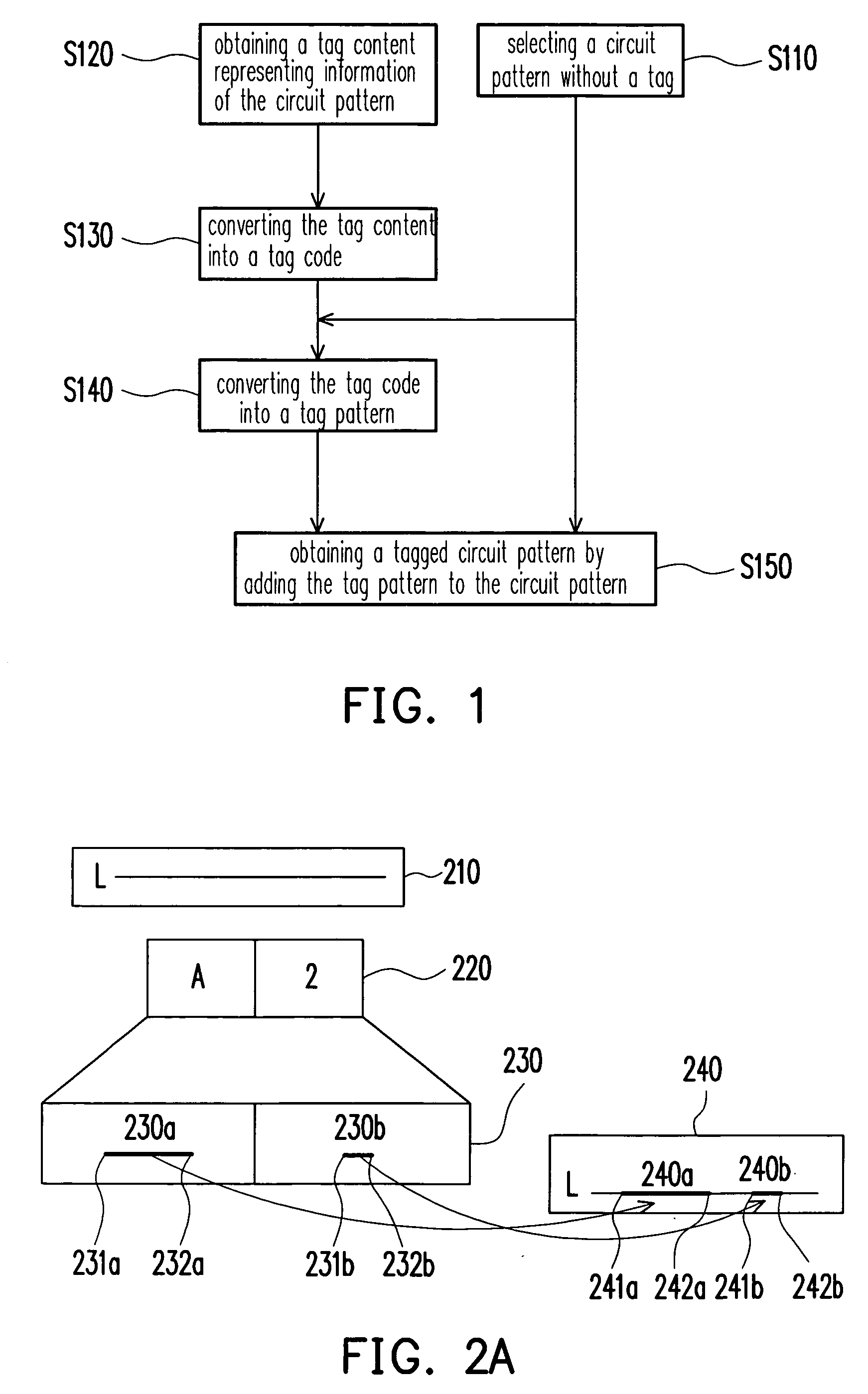
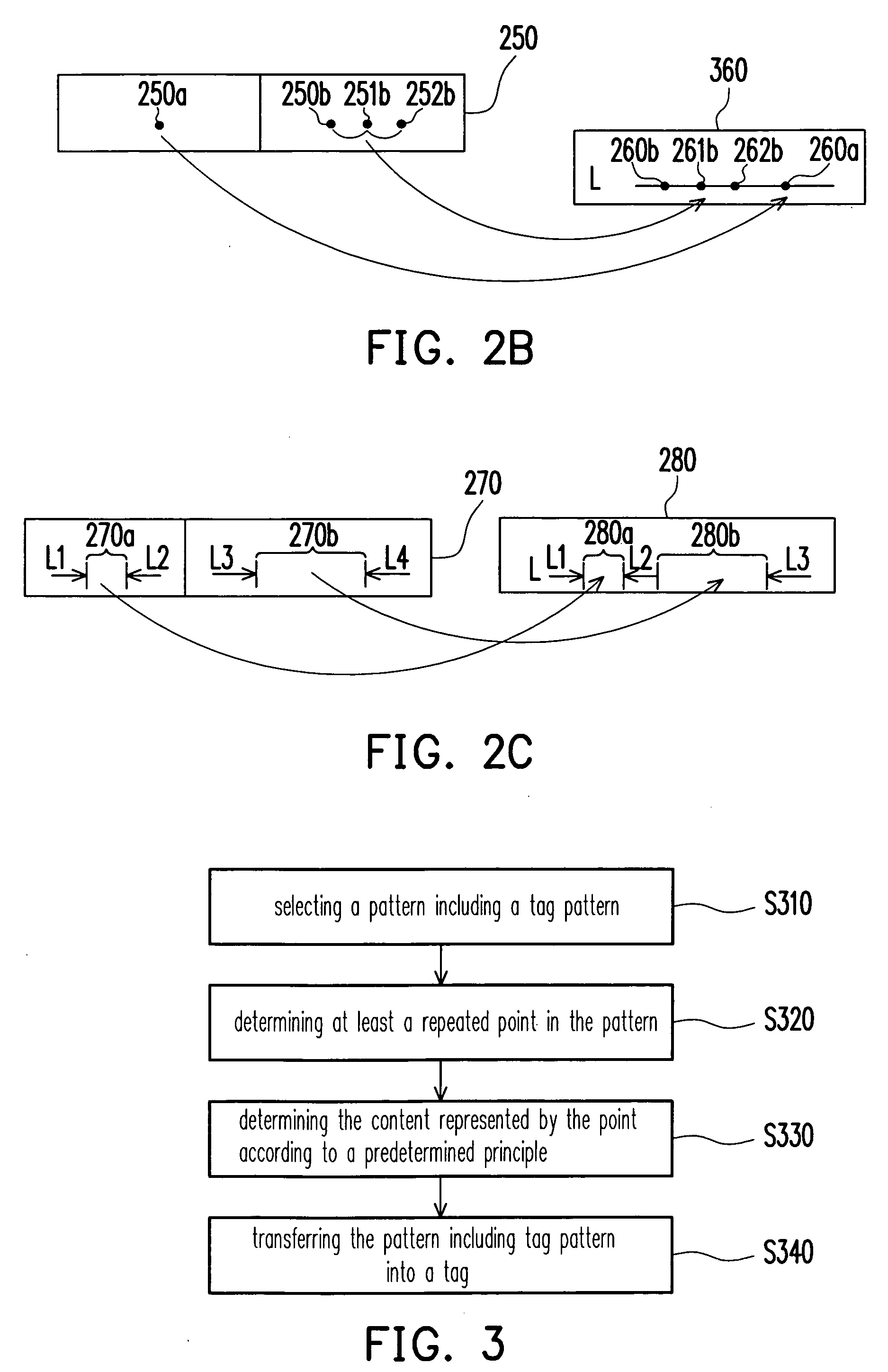
A tag writing and reading method suitable for a semiconductor product are provided. In the tag writing method, a code representing a tag is provided, and then the code is converted into a tag pattern that is then combined with a portion of the pattern of the pattern. Next, the pattern is combined with the tag pattern and used as the design content of the semiconductor product. In addition, a length of line segment, a number of points or interval(s) between a plurality of line segments may be adopted for representing the code of the tag. In addition, the tag code may include a patent number.
Owner:UNITED MICROELECTRONICS CORP
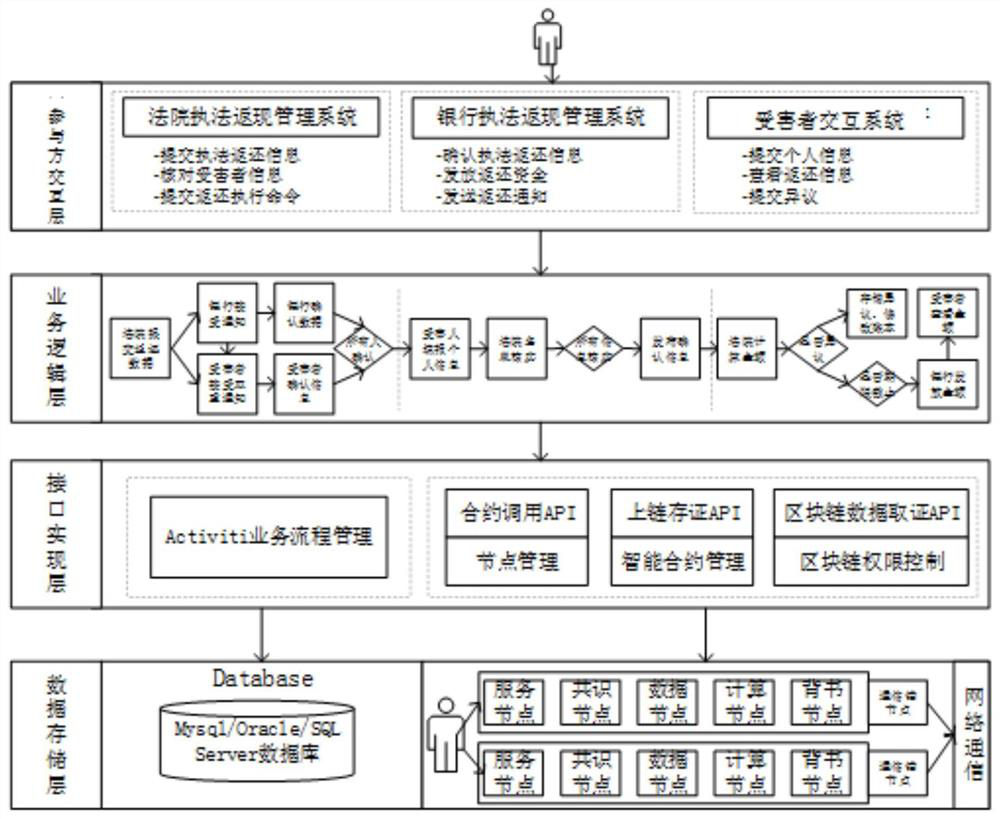
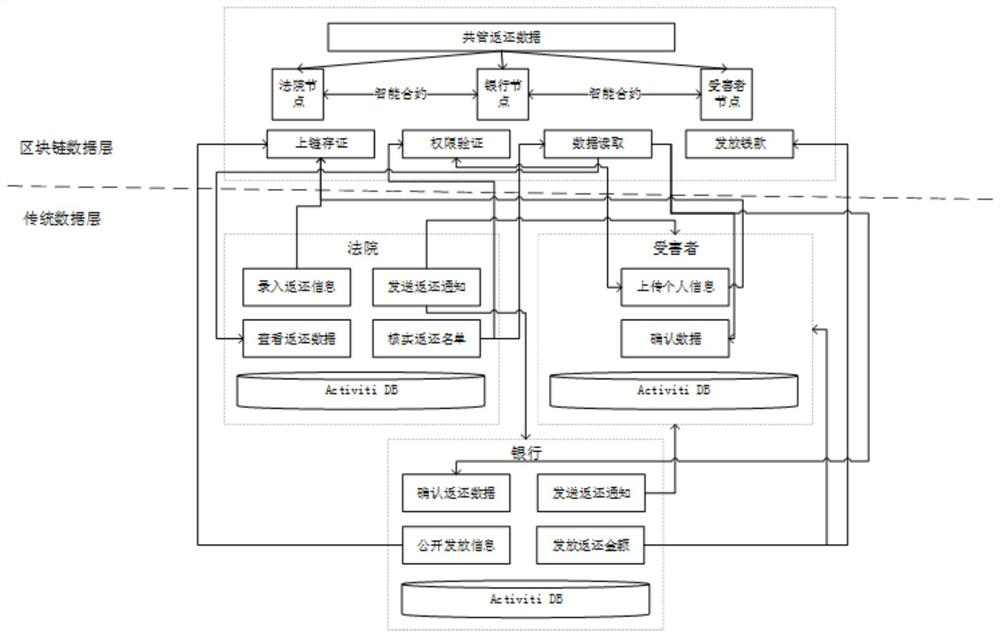
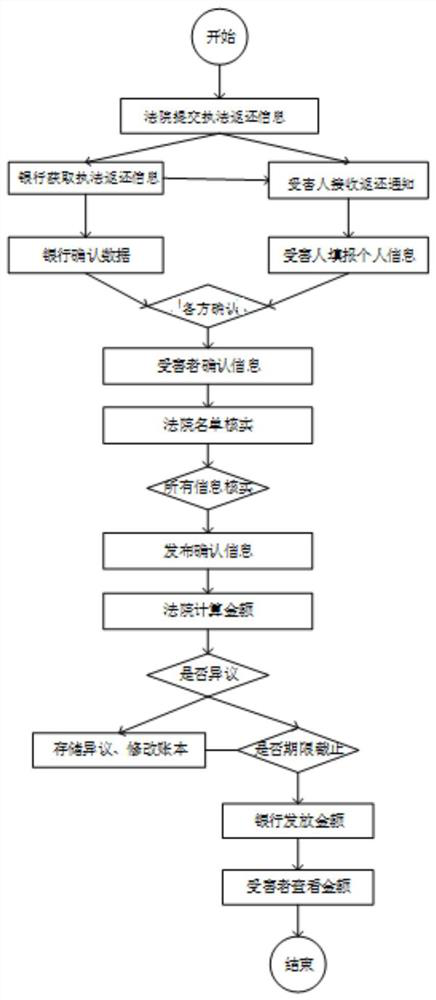
Law enforcement return system and method based on smart contract and workflow architecture
PendingCN112100635AEnsure safetyImprove trustDigital data protectionOffice automationSmart contractData store
The invention provides a law enforcement return system and method based on a smart contract and workflow architecture, and the system comprises a data storage layer which comprises a business information database and a blockchain system; an interface implementation layer, which comprises a workflow management module and a block link interface platform; a business logic layer, which is used for receiving and processing information submitted by courts, banks and victims based on business rules defined by the workflow management module so as to form law enforcement return workflow, and interacting with the blockchain system through the blockchain interface platform so as to realize data chaining, authority verification, data reading and fund return in the operation process of the law enforcement return workflow; and a participant interaction layer, which is used for providing information input, query and display for the user and comprises a court law enforcement cash-back management system, a bank law enforcement cash-back management system and a victim interaction system.
Owner:BOYA ZHENGLIAN (BEIJING) TECH CO LTD +2
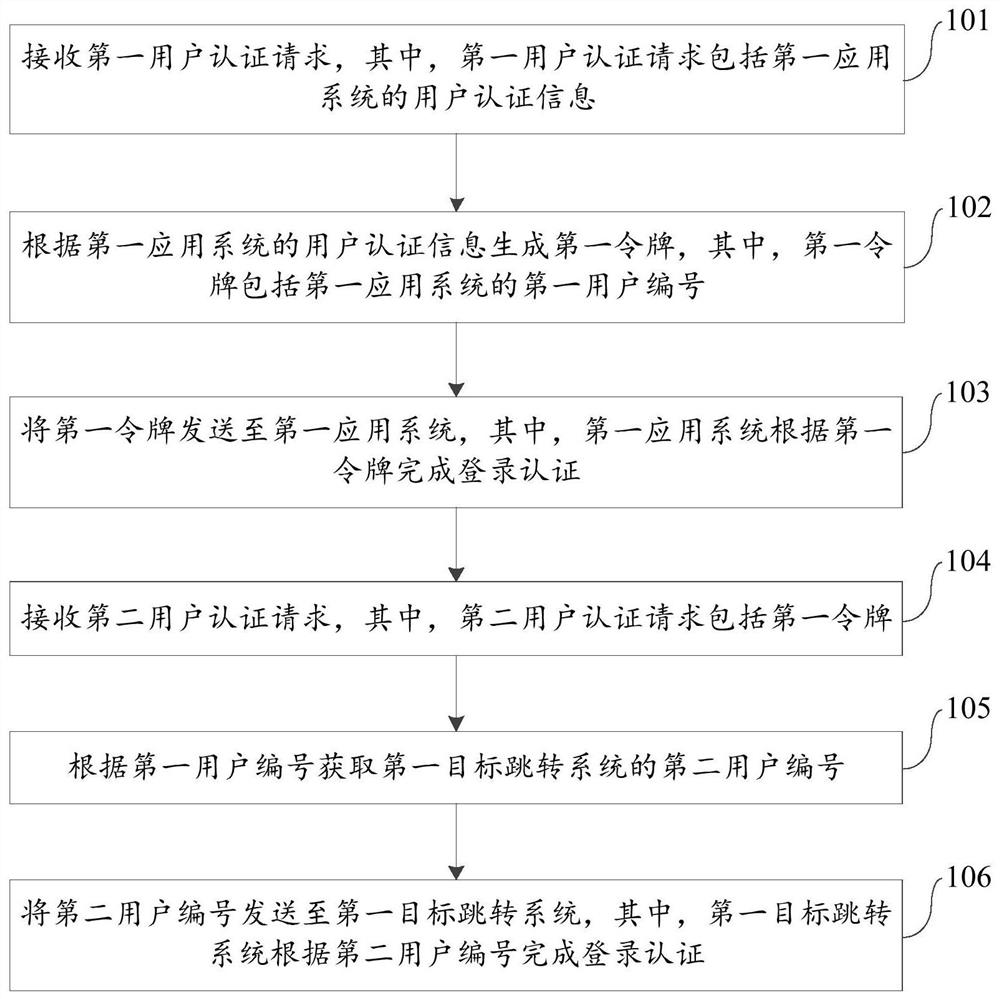
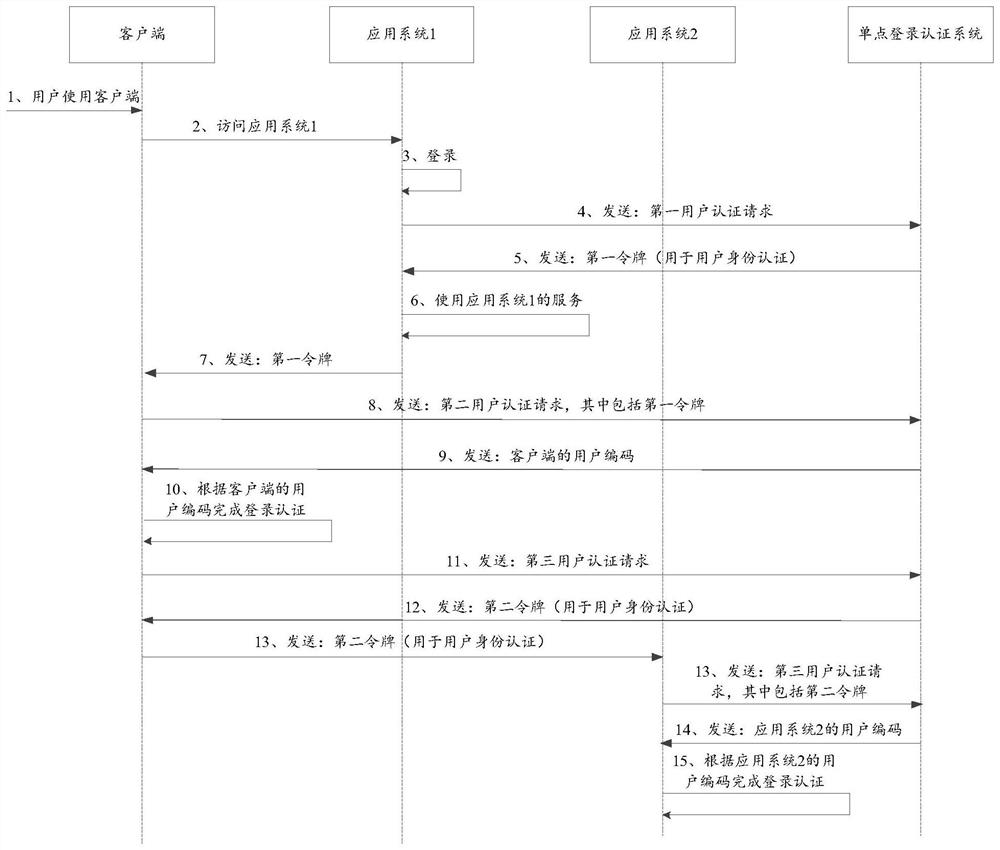
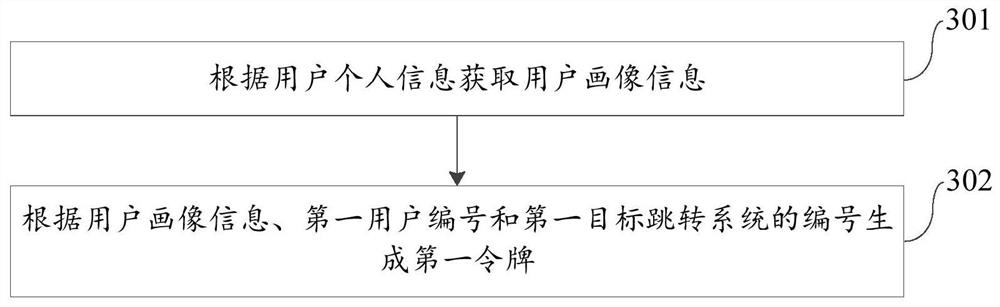
Single sign-on method and device, electronic equipment and storage medium
PendingCN114218550ASolve writing cookies (data stored on the user's local terminal)Work around the limitation of having to share the same client systemDigital data protectionDigital data authenticationTheoretical computer scienceEngineering
The invention provides a single sign-on method and device, electronic equipment and a storage medium, and belongs to the technical field of artificial intelligence recognition and classification. The method comprises the steps that a first user authentication request is received, and the first user authentication request comprises user authentication information of a first application system; a first token is generated according to the user authentication information of the first application system, and the first token comprises a first user number of the first application system; sending the first token to the first application system; receiving a second user authentication request, wherein the second user authentication request comprises the first token; acquiring a second user number of the first target jump system according to the first user number; the second user number is sent to the first target jump system, and the first target jump system completes login authentication according to the second user number. Therefore, the cross-domain single sign-on function can be realized, all application systems do not need to use the same user system, and meanwhile, the security and credibility of identity authentication can be effectively ensured.
Owner:CHINA CONSTRUCTION BANK
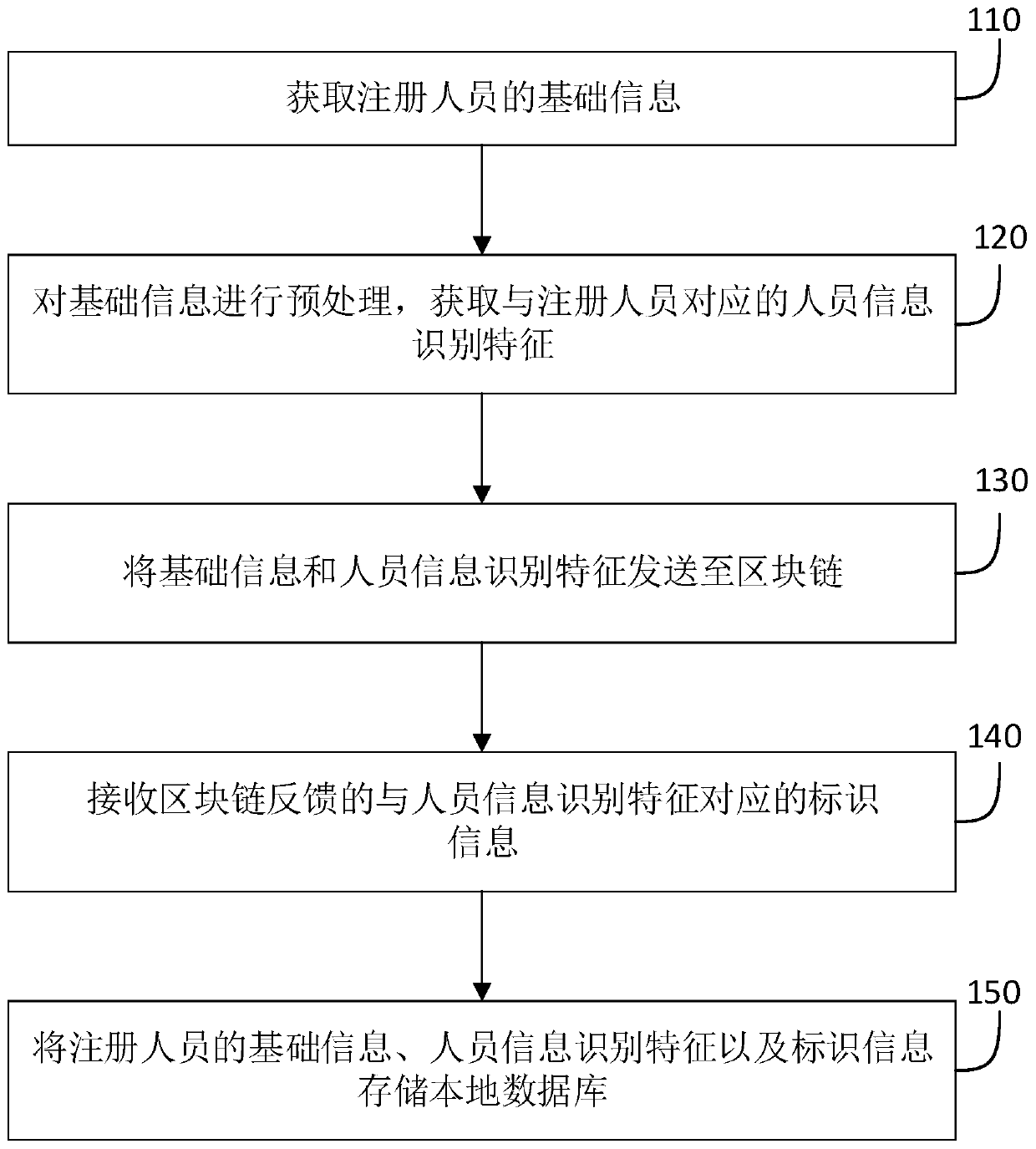
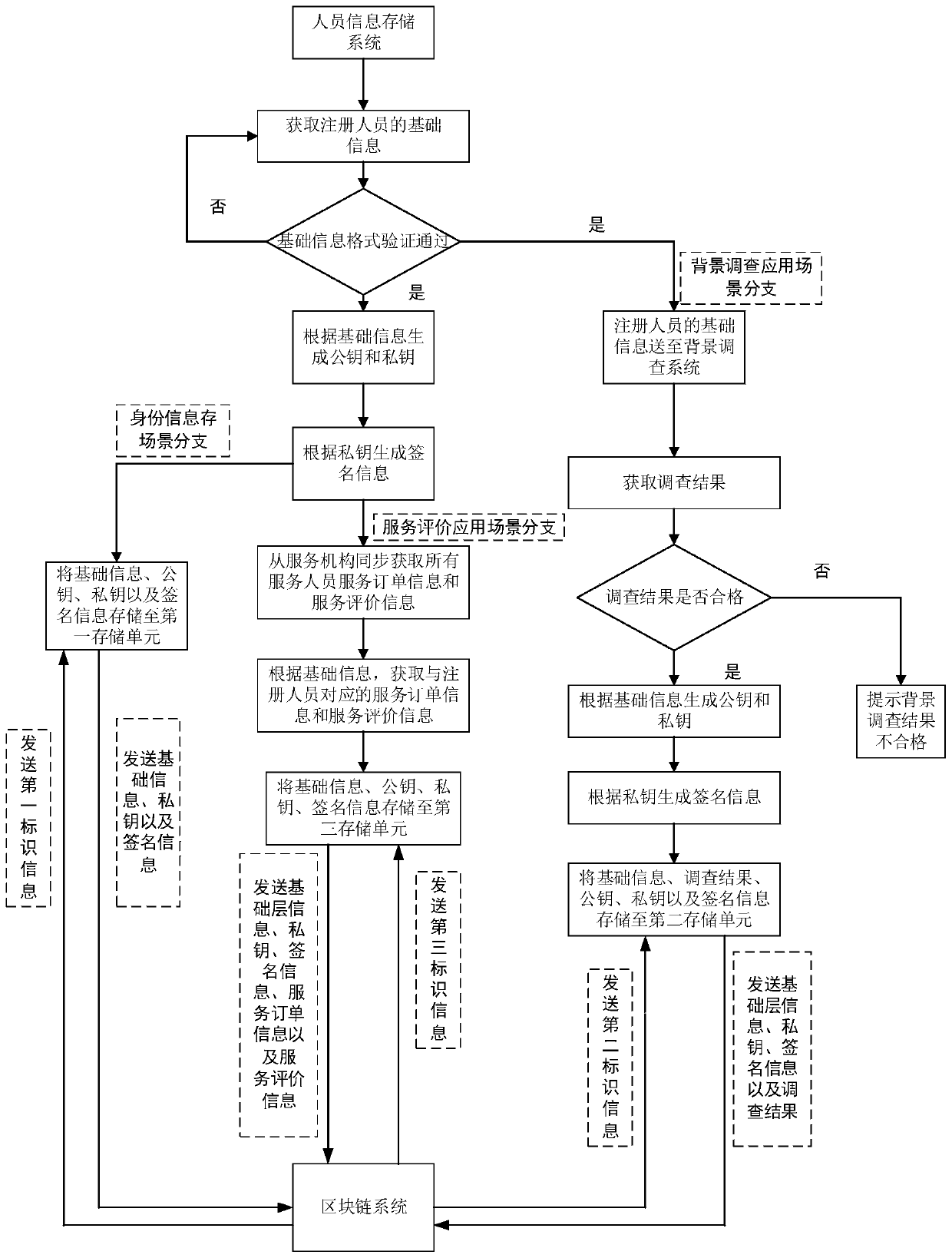
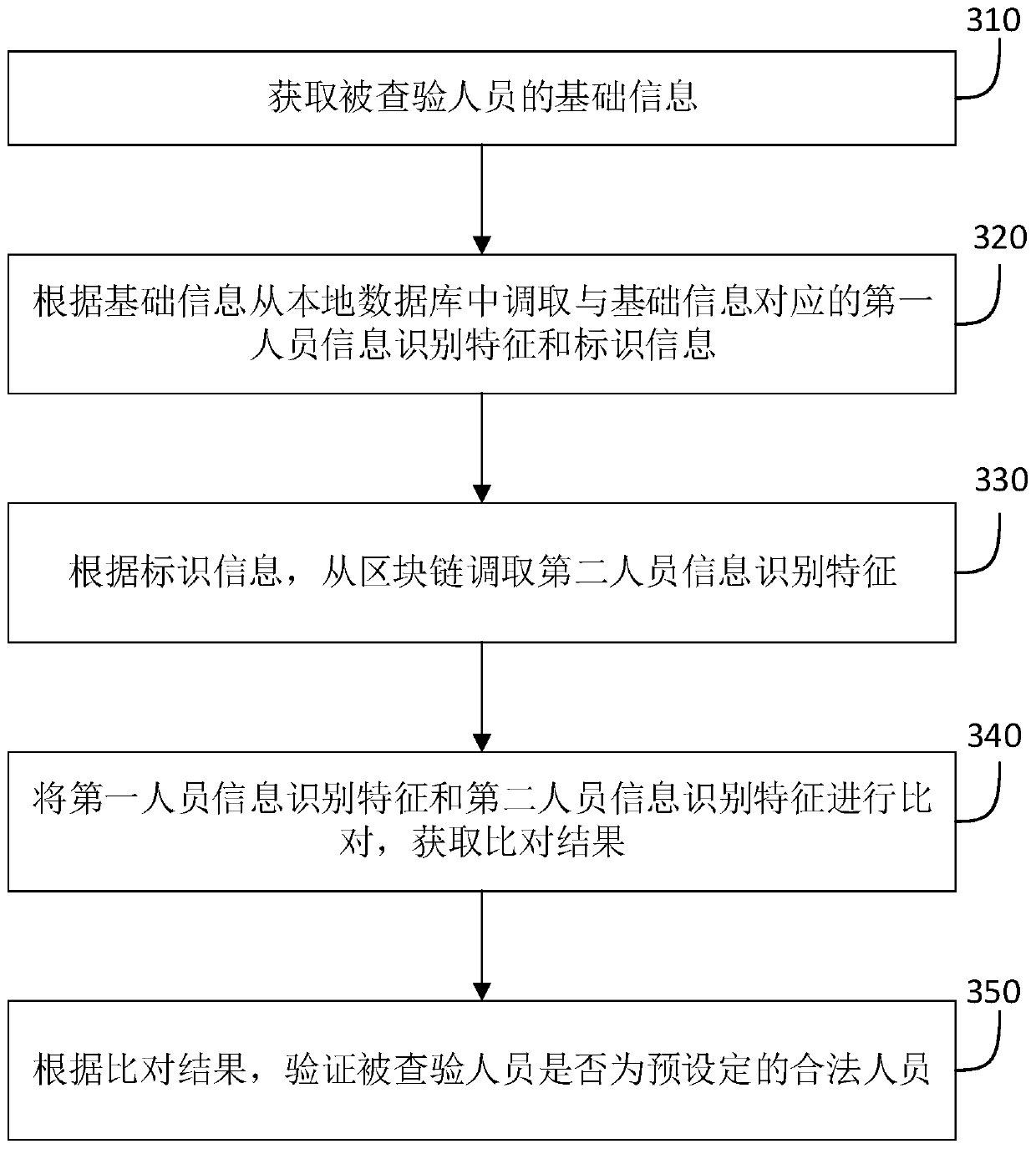
Personnel information storage and verification method and system and storage medium
The embodiment of the invention relates to a personnel information storage method and system and a storage medium. The method comprises the steps: acquiring the basic information of a registered personnel; preprocessing the basic information to obtain personnel information identification features corresponding to the registered person; sending the basic information and the personnel information identification features to a blockchain; receiving identification information which is fed back by the blockchain and corresponds to the personnel information identification feature; and storing the basic information, the personnel information identification features and the identification information of the registered person in a local database. By means of the mode, lawbreakers are prevented frompretending to fraud service personnel and crime in real time as much as possible, and therefore the risk of threatening personal and property safety of customers is reduced.
Owner:JD DIGITS HAIYI INFORMATION TECHNOLOGY CO LTD +1
Agricultural product traceability information storage method based on a block chain
ActiveCN109493045AAchieve compartmentalizationAchieve standardizationPayment protocolsCommerceData integrityProduct traceability
The invention discloses an agricultural product traceability information storage method based on a block chain, and the method comprises the steps: generating block data comprising the head part of ablock, a block body and other information, and achieving the streaked, normalized and persistent storage of the agricultural product traceability information; information such as a block number and forward Hash is added to the head part of the block, and information such as ontology Hash reality is added to the block body, so that all the blocks form a one-way linked list together. The invention discloses a traditional agricultural product tracing information storage technology. the storage of the tracing data can be realized; query and block-based data integrity verification can be realized;the prevention control, check control and recovery control capabilities of enterprises, consumers and administrative competent departments on agricultural product traceability information are improved, the transparency of the agricultural product traceability information is promoted, and the safety awareness and participation degree of all the society bounds on the quality of agricultural productsare enhanced.
Owner:HOHAI UNIV +3
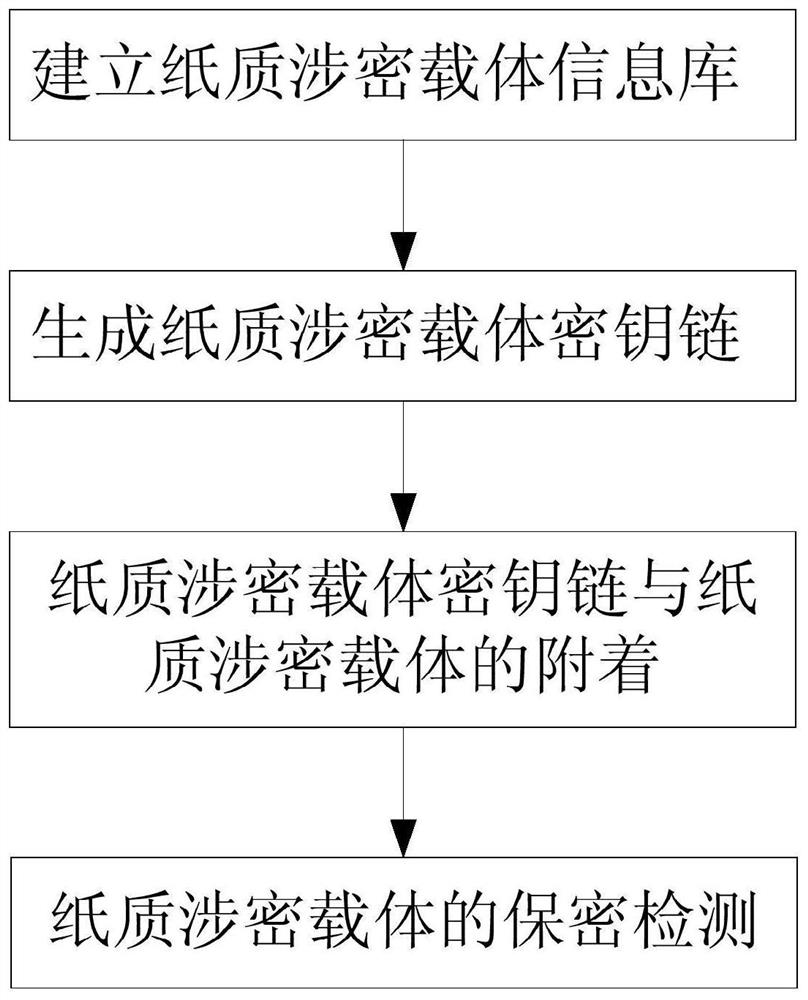
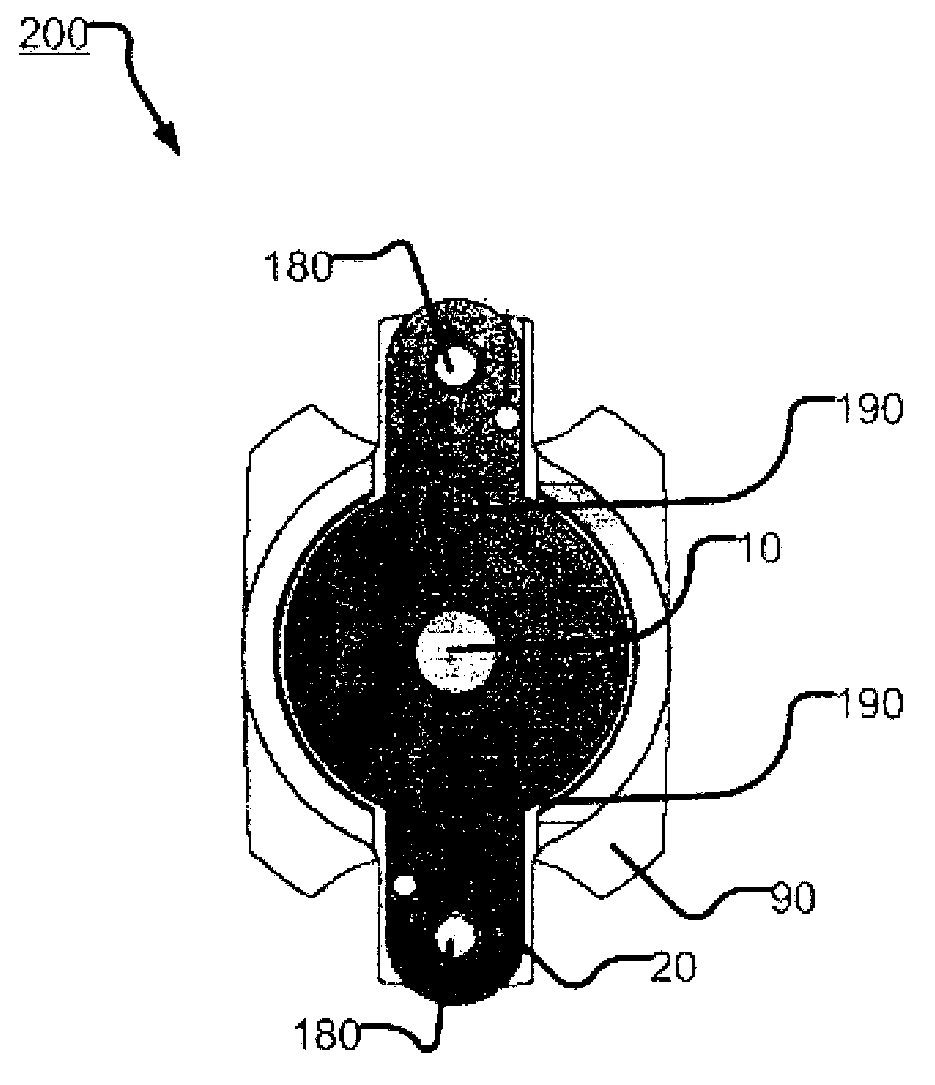
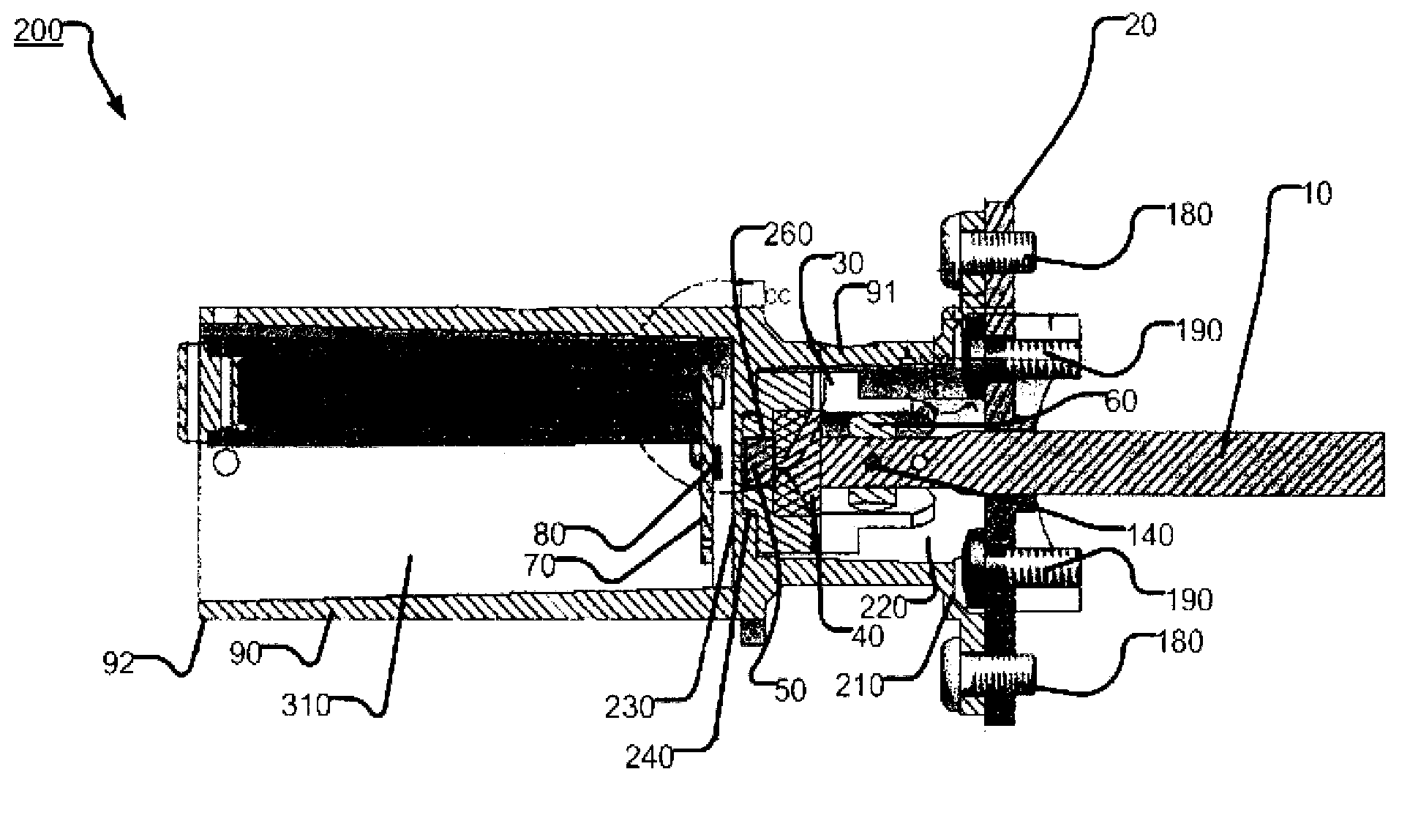
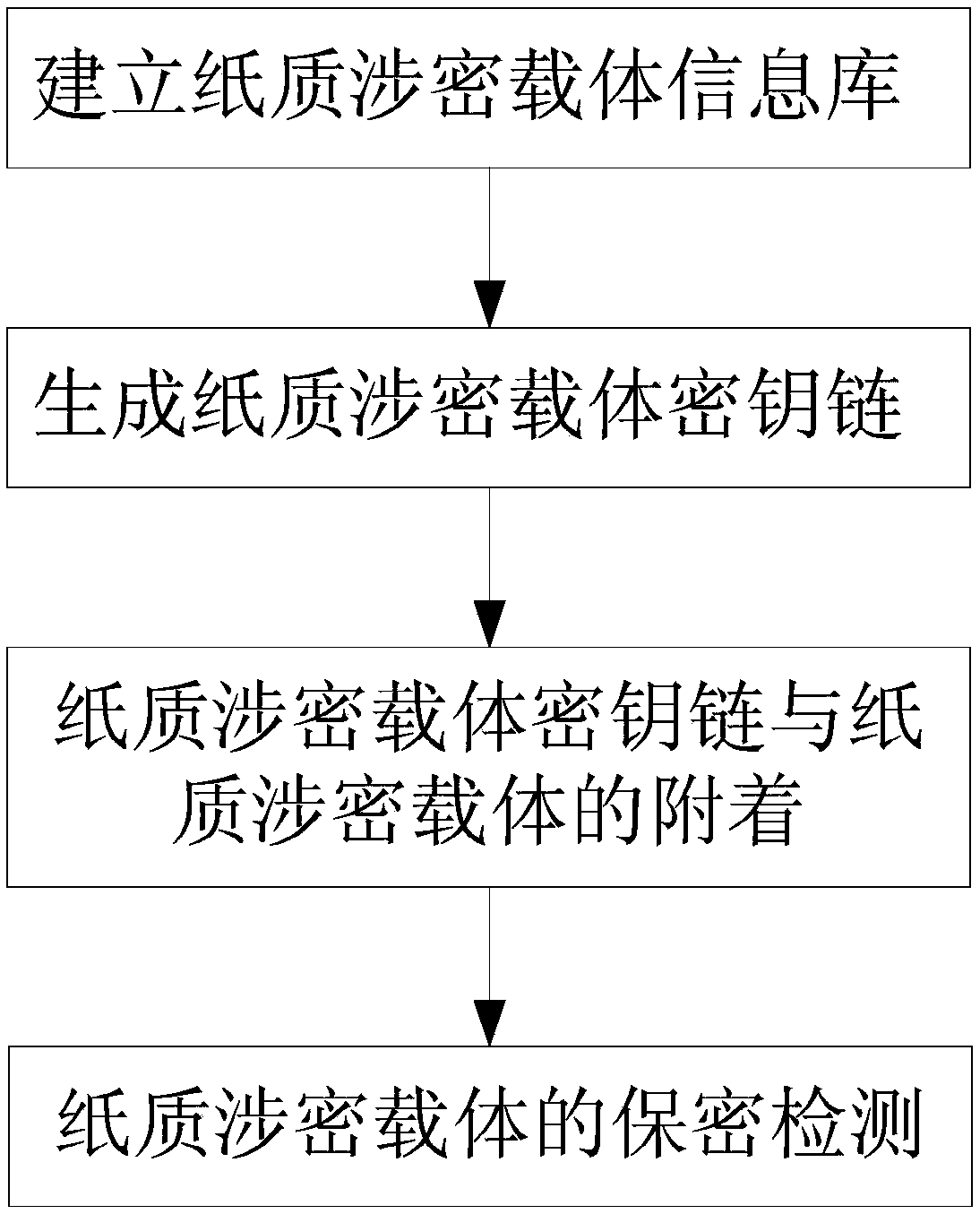
Anti-tampering and forgery method of paper-based confidential carrier based on rfid key chain
ActiveCN109299763BAchieving High Confidence InspectionEasy to tamper withKey distribution for secure communicationCo-operative working arrangementsComputer networkHash function
The present invention provides an RFID key chain-based anti-tampering and forgery method for a paper-based secret-related carrier, comprising the following steps: step S2, generating a paper-based secret-related carrier key chain; including: S2.1, generating a paper-based secret-related carrier The root key V0 of the key chain, the generation parameters of V0 include: the global information string of the paper-based secret-related carrier, denoted as G; the unique ID of the RFID tag corresponding to the paper-based secret-related carrier, denoted as RID; HASH function F, calculate and generate V0=F(G || RID), where || is a string connection operator; S2.2, construction of key chain; sequentially obtain the correspondence of each inner page of the paper secret-related carrier Use the one-way HASH function F to generate the key Vx of the page from the key string Vx-1 generated on the previous page of the page and the summary information string S of the inner page of the page; steps S3, the attachment of the paper secret-related carrier key chain and the paper secret-related carrier. The invention realizes the safety protection of the paper secret-related carrier.
Owner:JIANGSU ELECTRIC POWER CO
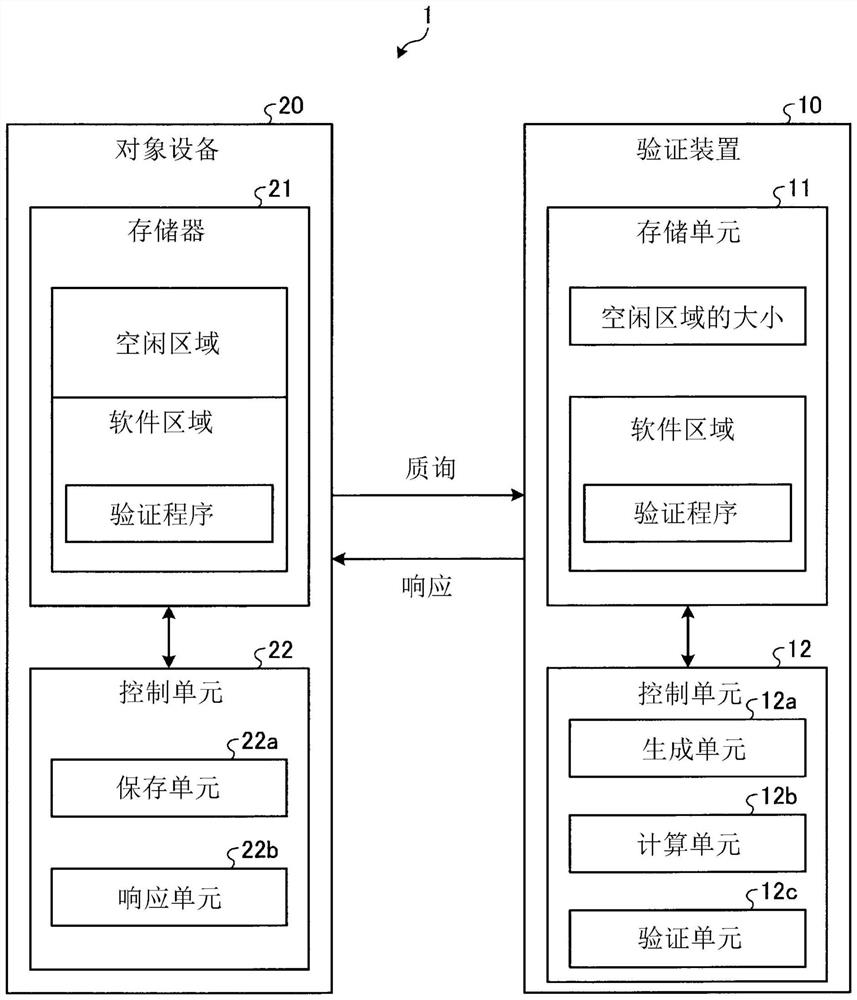
Verification device, verification system, verification method, and verification program
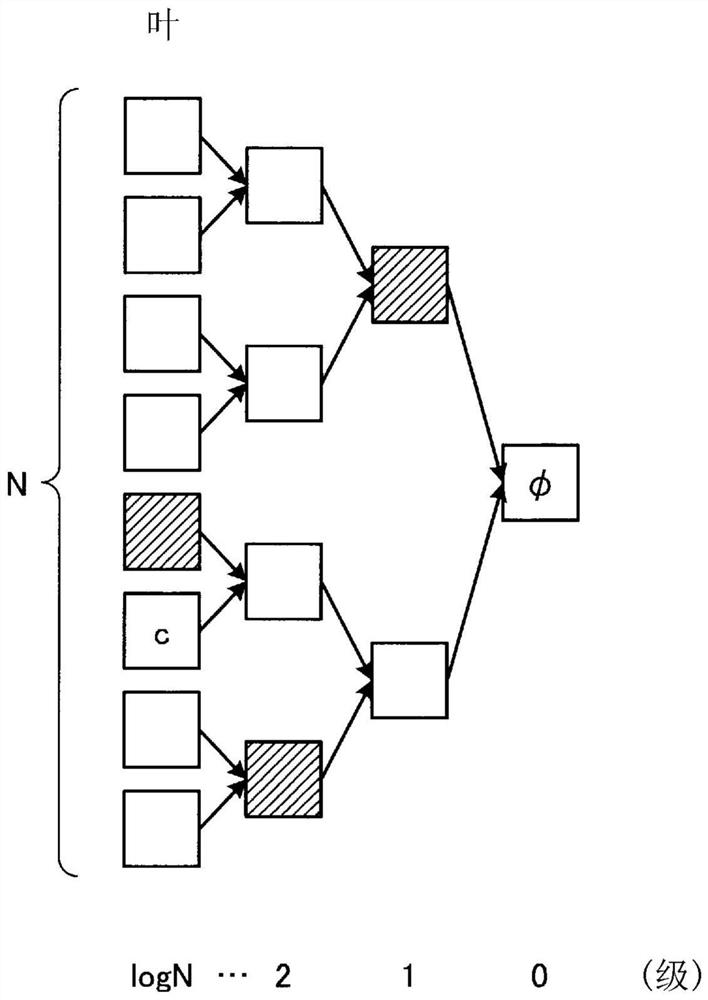
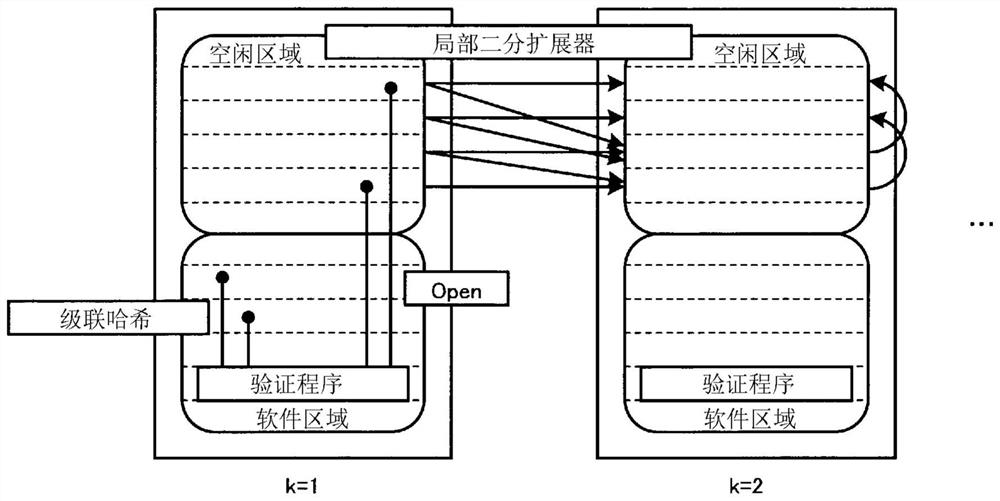
PendingCN114341849AEasy to tamper withDigital data protectionInternal/peripheral component protectionSystem verificationAlgorithm
A storage unit (11) stores the size of a free area of a memory (21) in a target device (20) and software stored in the memory (21). A generation unit (12a) generates a graph configured from a plurality of nodes on the basis of the size of the free area in the memory (21), and transmits the graph to the target device (20). A calculation unit (12b) calculates a hash value corresponding to each block in the software stored in the memory (21). A verification unit (12c) verifies whether or not tampering to a memory (21) in the target device (20) has occurred using the calculated hash value corresponding to the block and a returned response to a challenge specifying a node of the graph calculated using the graph, and a hash value of the returned block in response to a challenge specifying the block.
Owner:NIPPON TELEGRAPH & TELEPHONE CORP
Data protection method and protection device based on block chain
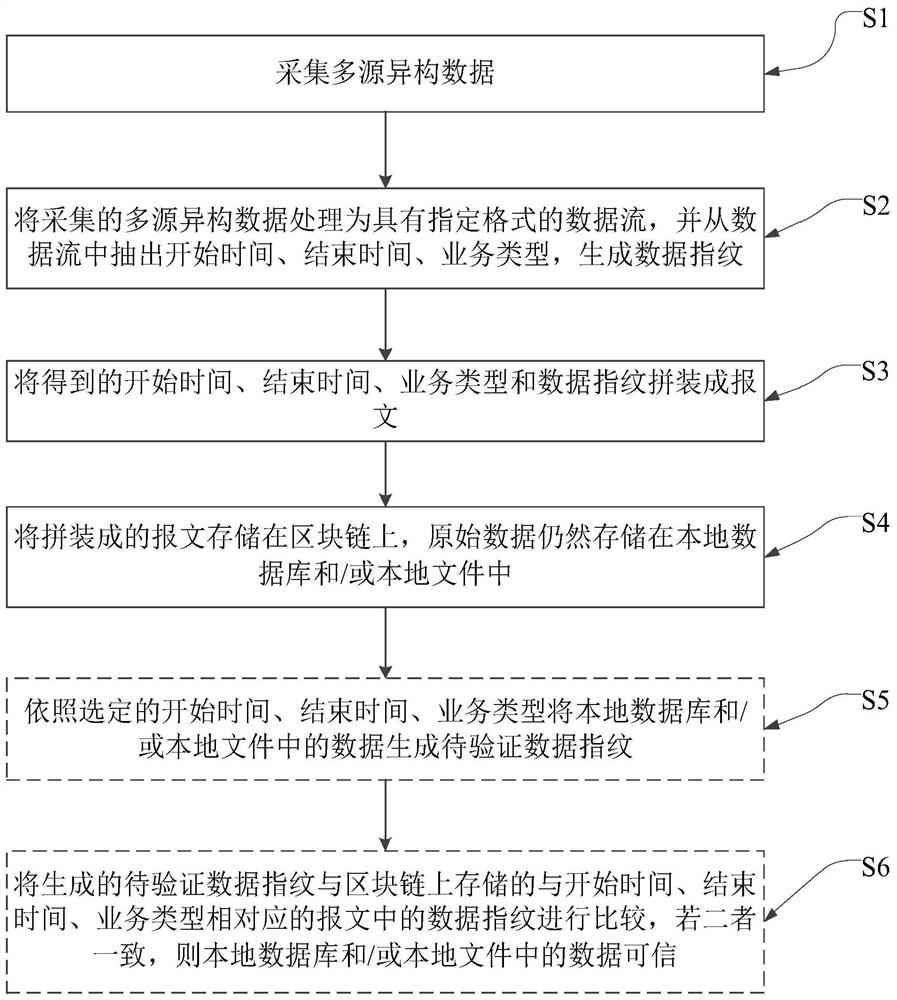
PendingCN114626849AEasy to removeMitigation of tamperingFinanceDatabase distribution/replicationData streamStart time
The invention discloses a data protection method based on a block chain. The method comprises the following steps: S1, collecting multi-source heterogeneous data; s2, processing the collected multi-source heterogeneous data into a data stream with a specified format, and extracting a starting time, an ending time and a service type from the data stream to generate a data fingerprint; s3, assembling the obtained start time, end time, service type and data fingerprint into a message; and S4, storing the generated message on the block chain, wherein the original data is still stored in the local database and / or the local file. According to the invention, the multi-source heterogeneous data is converted into the message only containing the start time, the end time, the service type and the data fingerprint, and the message is stored on the block chain, so that the technical problem that in the prior art, the overhead of computing resources, storage resources and bandwidth resources of the block chain is too large due to the fact that all data needs to be recorded and chained one by one is solved; and the problems that the interactive data between the client and the security company is easy to delete and tamper, and the security and completeness of the data cannot be ensured can be solved.
Owner:中信建投证券股份有限公司
Information processing method and device, electronic equipment and computer storage medium
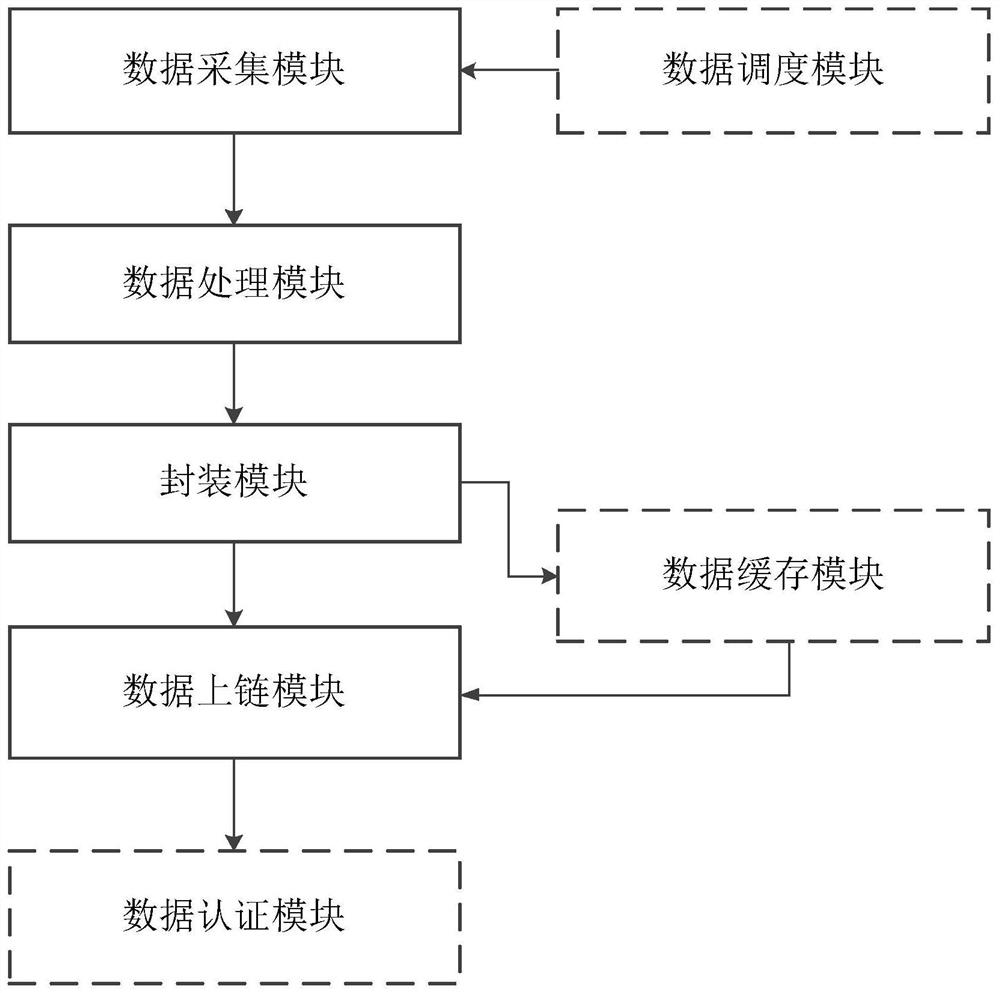
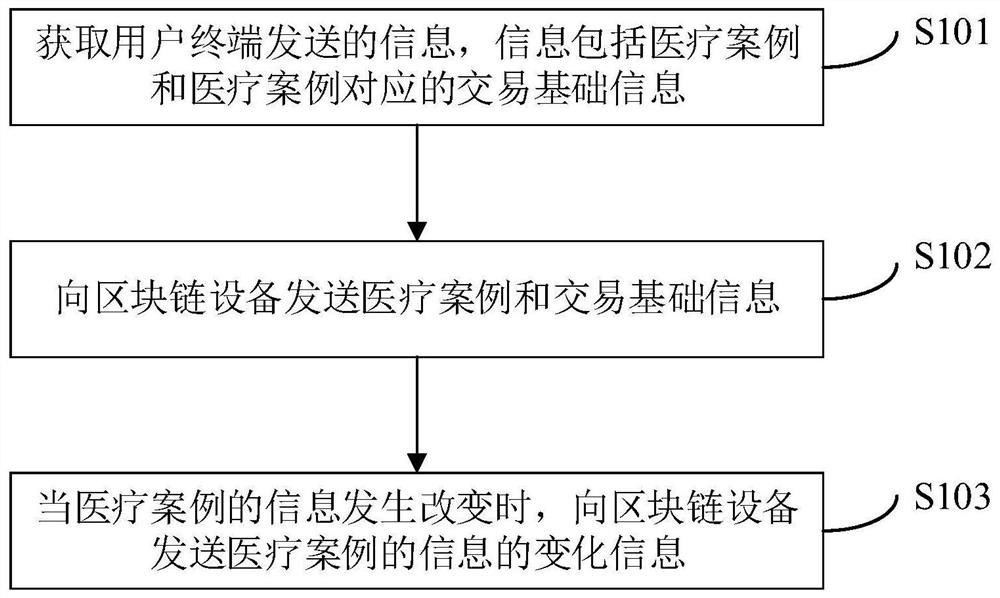
PendingCN113139202AAvoid easy tamperingImprove securityDigital data protectionEngineering managementServer
The embodiment of the invention discloses an information processing method and device, electronic equipment and a computer storage medium. The information processing method is applied to a server and comprises the steps of obtaining information sent by a user terminal, wherein the information comprises a medical case and transaction basic information corresponding to the medical case; sending the medical case and the transaction basic information to block chain equipment; and when the information of the medical case is changed, sending change information of the information of the medical case to block chain equipment. According to the embodiment of the invention, the medical case and transaction basic information can be prevented from being tampered easily, so that the security is improved.
Owner:爱多特大健康科技有限公司
Optical disk, optical disk recording and reproducing apparatus, method for recording, reproducing and deleting data on optical disk, and information processing system
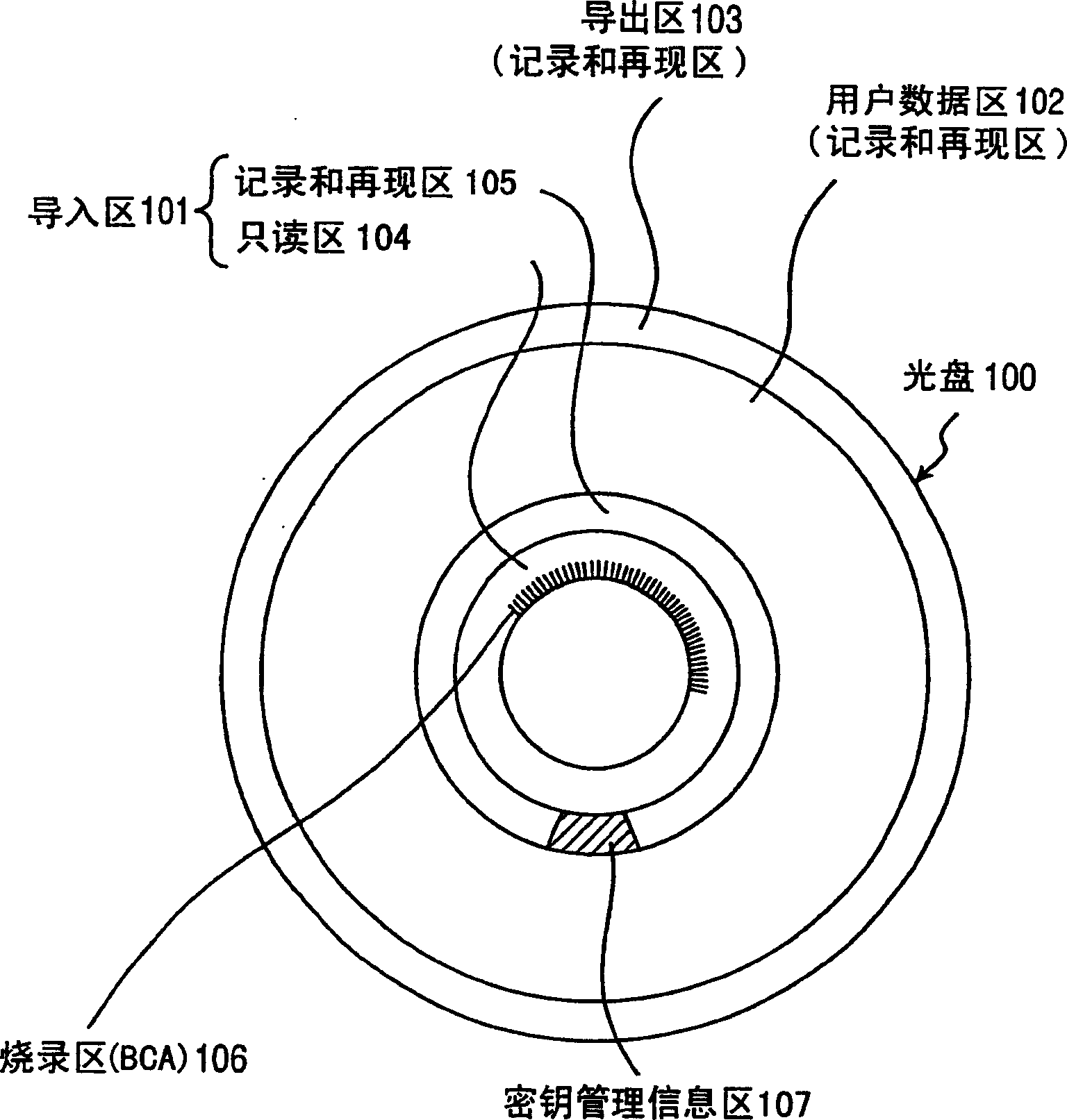
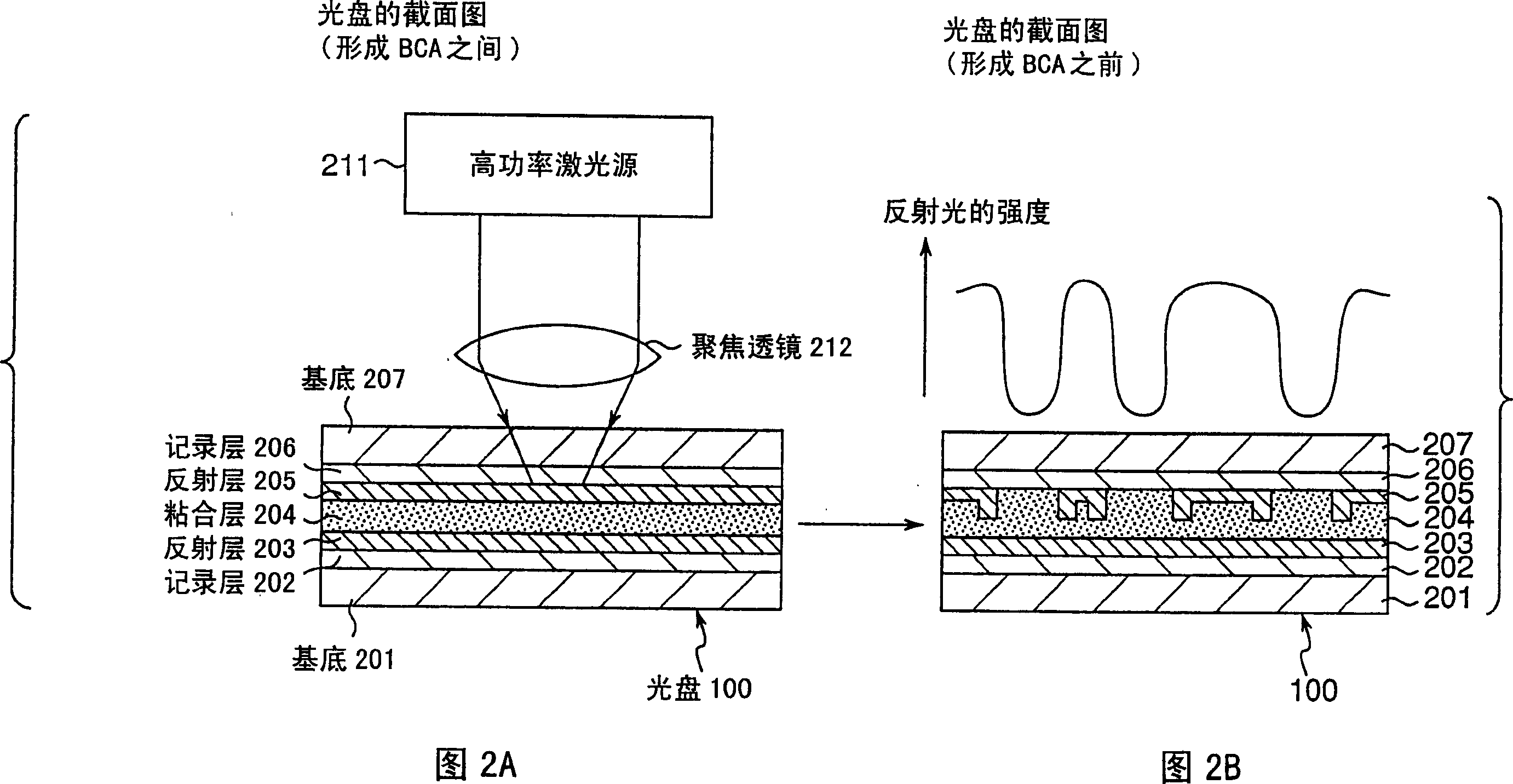
InactiveCN1831959AEasy to tamper withPrevent illegal copyingInformation arrangementAccessories for auxillary signalsInformation handling systemData recording
A recording type optical disk on which data is recordable includes a data recording and reproducing area for recording data therein and reproducing data therefrom, and a read-only disk identification information area for recording disk identification information for identifying the optical disk therein. In the optical disk, the disk identification information is formed by removing a reflection film that is formed on the optical disk in a strip shape. The disk identification information includes an inherent disk identifier for each optical disk, and the data recording and reproducing area includes an area for recording encrypted data therein. The encrypted data is encrypted by using information including the disk identification information for identifying the optical disk as a key.
Owner:PANASONIC CORP
Encoder Using Magnet Drop Out Feature For Theft Detection
ActiveCN102812325AEasy to tamper withValve arrangementsUsing electrical meansPrinted circuit boardPiston
An encoder to be mounted to a shaft extending from a piston meter configured to compute a volume of distributed fluid includes a magnet affixed to the shaft via a floating magnet holder, a magnetic sensor configured to sense the flux density and direction of a magnetic field created by the magnet and to output a signal indicating the flux density and direction of the magnetic field to a printed circuit board, and the printed circuit board configured to output a signal indicating the volume of distributed fluid if the encoder has not been tampered with and configured to output an error signal if the encoder has been tampered with.
Owner:精量电子(美国)有限公司
A blockchain-based agricultural product traceability information storage method
ActiveCN109493045BAchieve compartmentalizationAchieve standardizationPayment protocolsCommerceData integrityEngineering
Owner:HOHAI UNIV +3
Anti-tampering and forgery method of paper secret-related carrier based on RFID key chain
ActiveCN109299763AAchieving High Confidence InspectionEasy to tamper withKey distribution for secure communicationCo-operative working arrangementsHash functionGlobal information
The invention provides a paper secret-related carrier anti-tampering and forgery method based on RFID key chain, which comprises the following steps: step S2, generating a paper secret-related carrierkey chain; Includes S2.1, generating root key V0 of paper secret-related carrier key chain, generating parameters of V0 include: global information character string of paper secret-related carrier, recorded as G, The unique identification ID of RFID tag corresponding to the paper secret-related carrier is recorded as RID. A formula shown in the description is computed and generated by one-way HASH function F, where the symbol shown in the description is string join operator; S2.2, construction of key chain; A summary information string corresponding to a page in each page of that pap secret-related carrier is sequentially obtained, and the key string Vx generate on the previous page of the page is determined by using a one-way HASH function F. 1 and an inner page summary information string S of the page to generate a key Vx-1 of the page; Step S3, the key chain of the paper secret-related carrier is attached to the paper secret-related carrier. The invention realizes the safety protection of the paper secret-related carrier.
Owner:JIANGSU ELECTRIC POWER CO
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com