Anti-tampering and forgery method of paper-based confidential carrier based on rfid key chain
A technology of secret-related carriers and RFID tags, which is applied in the field of security protection of secret-related carriers, can solve the problems of loose structure of paper-based secret-related carriers, heavy manual inspection work, and difficulty in ensuring the safety of inner pages, etc., and achieves high-intensity security inspection, Realize the effect of security check and high robustness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0040] The present invention will be further described below in conjunction with specific drawings and embodiments.
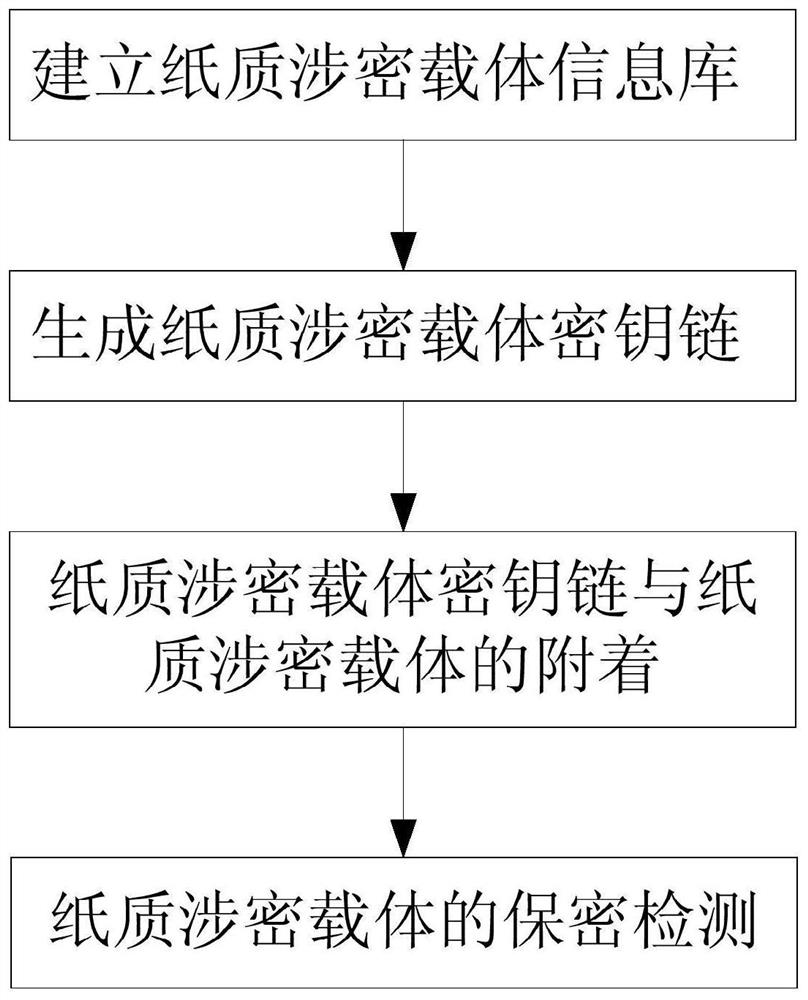
[0041] The present invention proposes a method for anti-tampering and counterfeiting of a paper-based secret-related carrier based on an RFID key chain, including:
[0042] (1) Establishing an information database of paper-based secret-related carriers;
[0043] The paper secret-related carrier information database mainly includes: the global information of the paper secret-related carrier, the RFID unique identification ID corresponding to the paper secret-related carrier, and the summary information string of the inner page of the paper secret-related carrier; among them:
[0044] The global information of the paper-based secret-related carrier includes but is not limited to: the secret-related number, level, name, carrier creator, creation date, etc. of the paper-based secret-related carrier;
[0045] The unique identification ID of the RFID tag correspondi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com