Patents
Literature
30results about How to "Prevent unauthorized" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
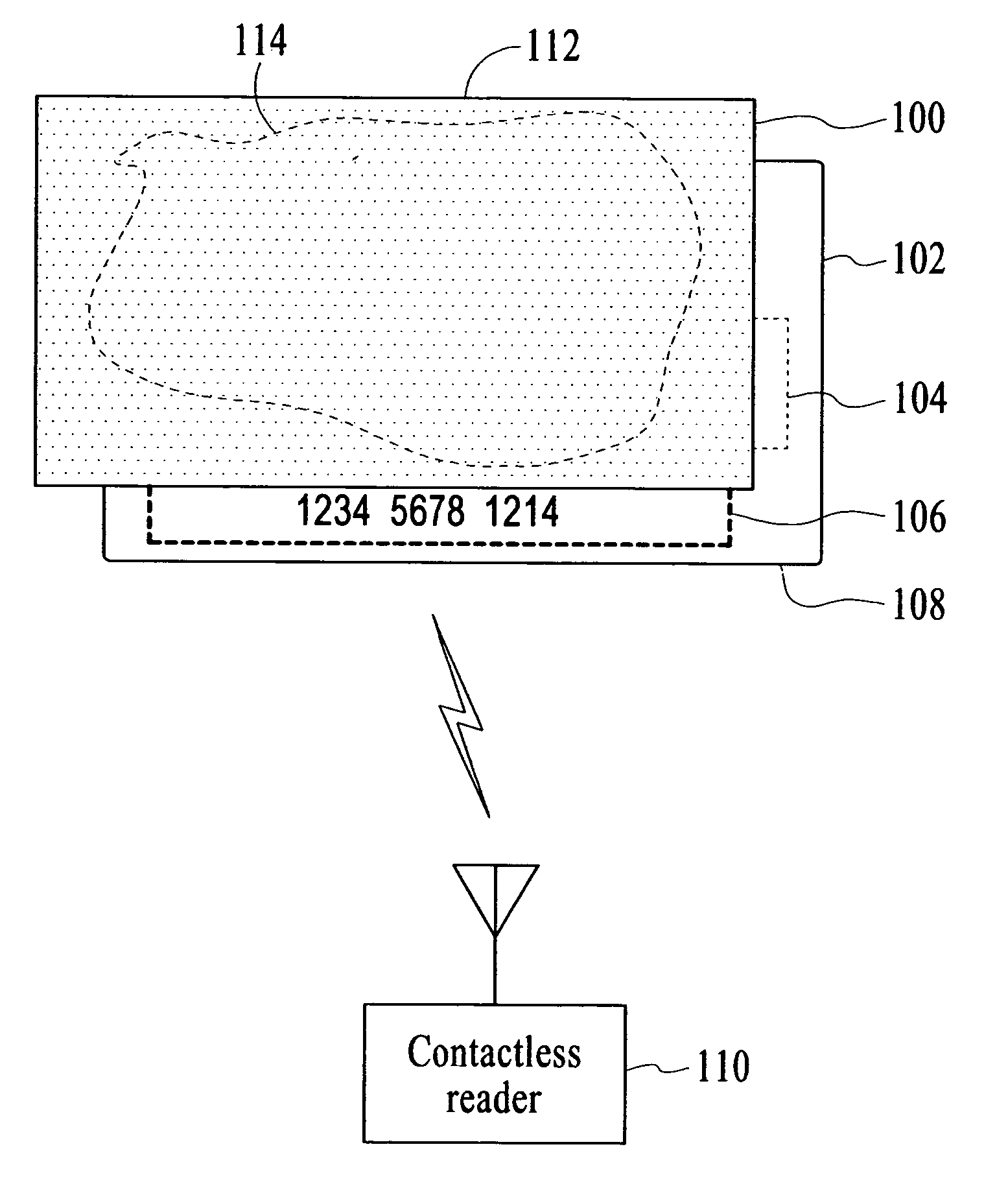
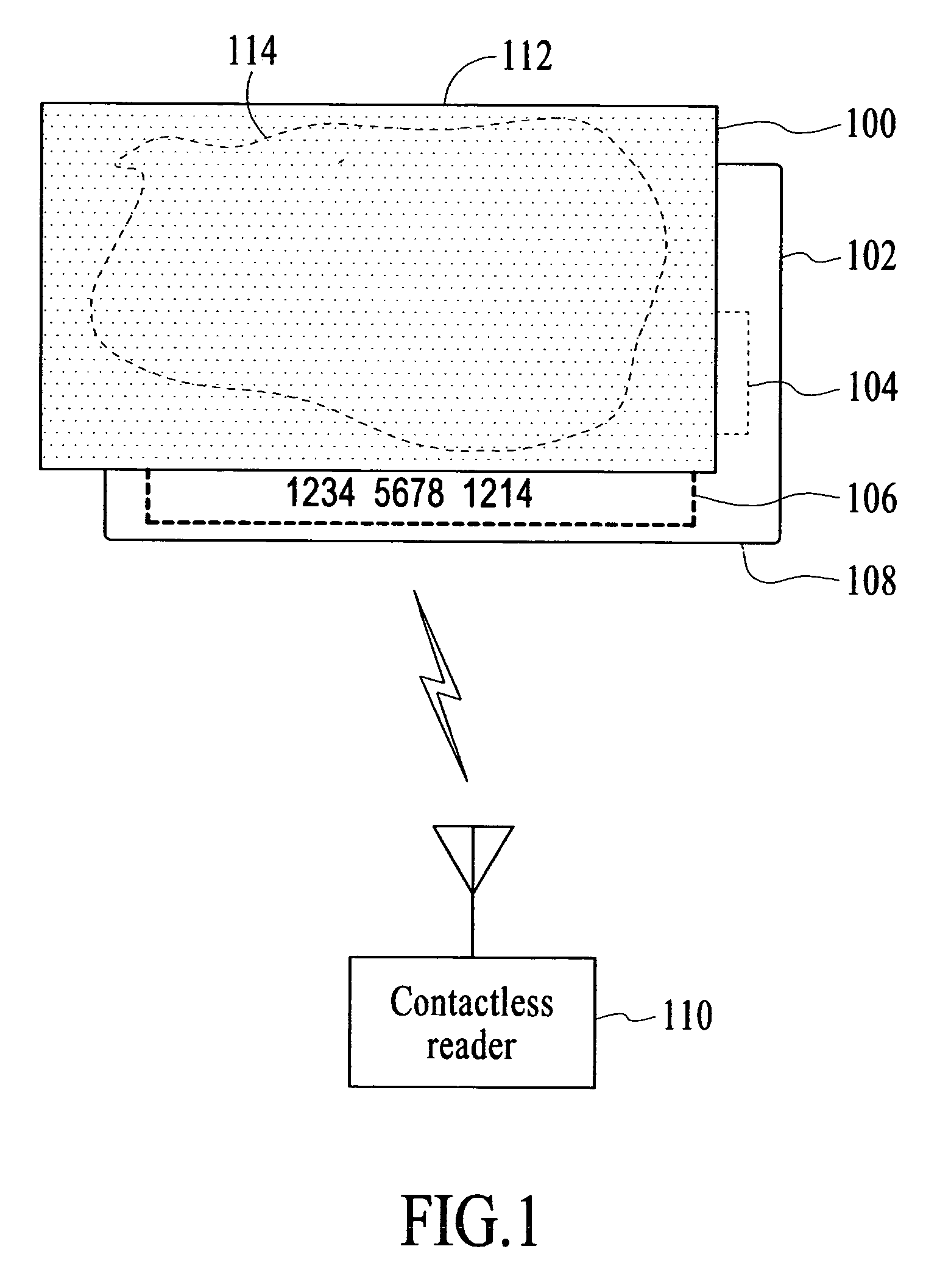
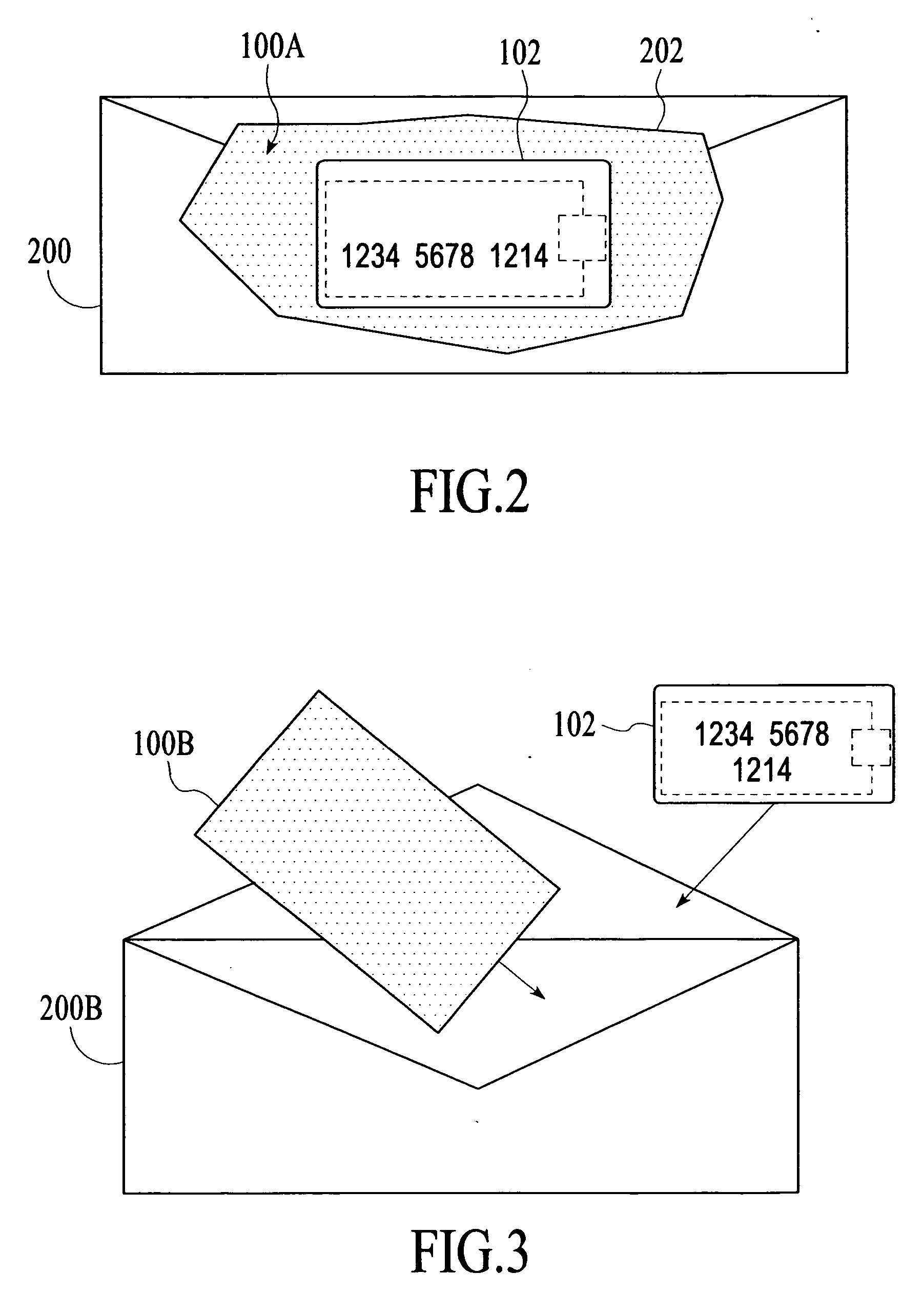
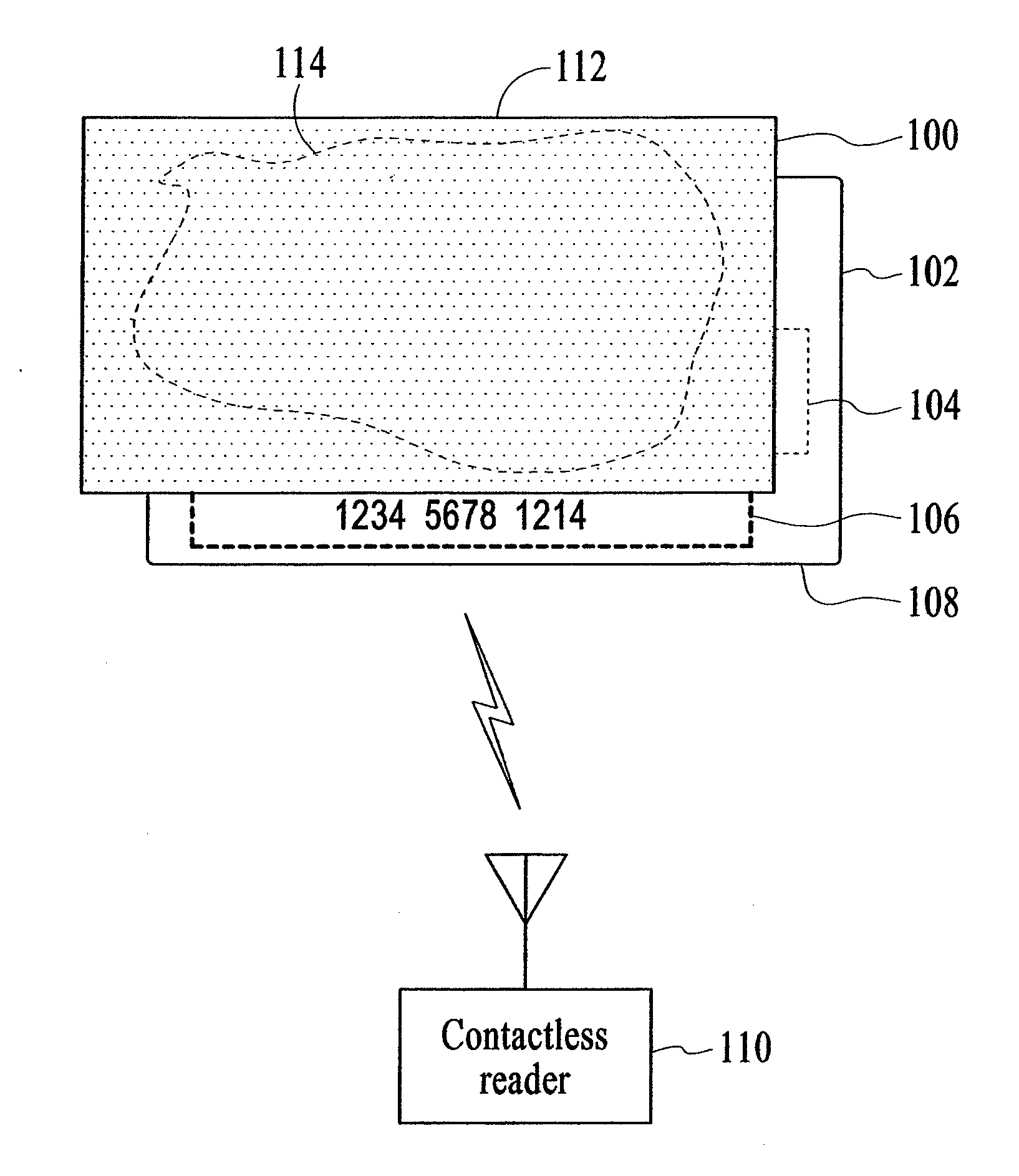
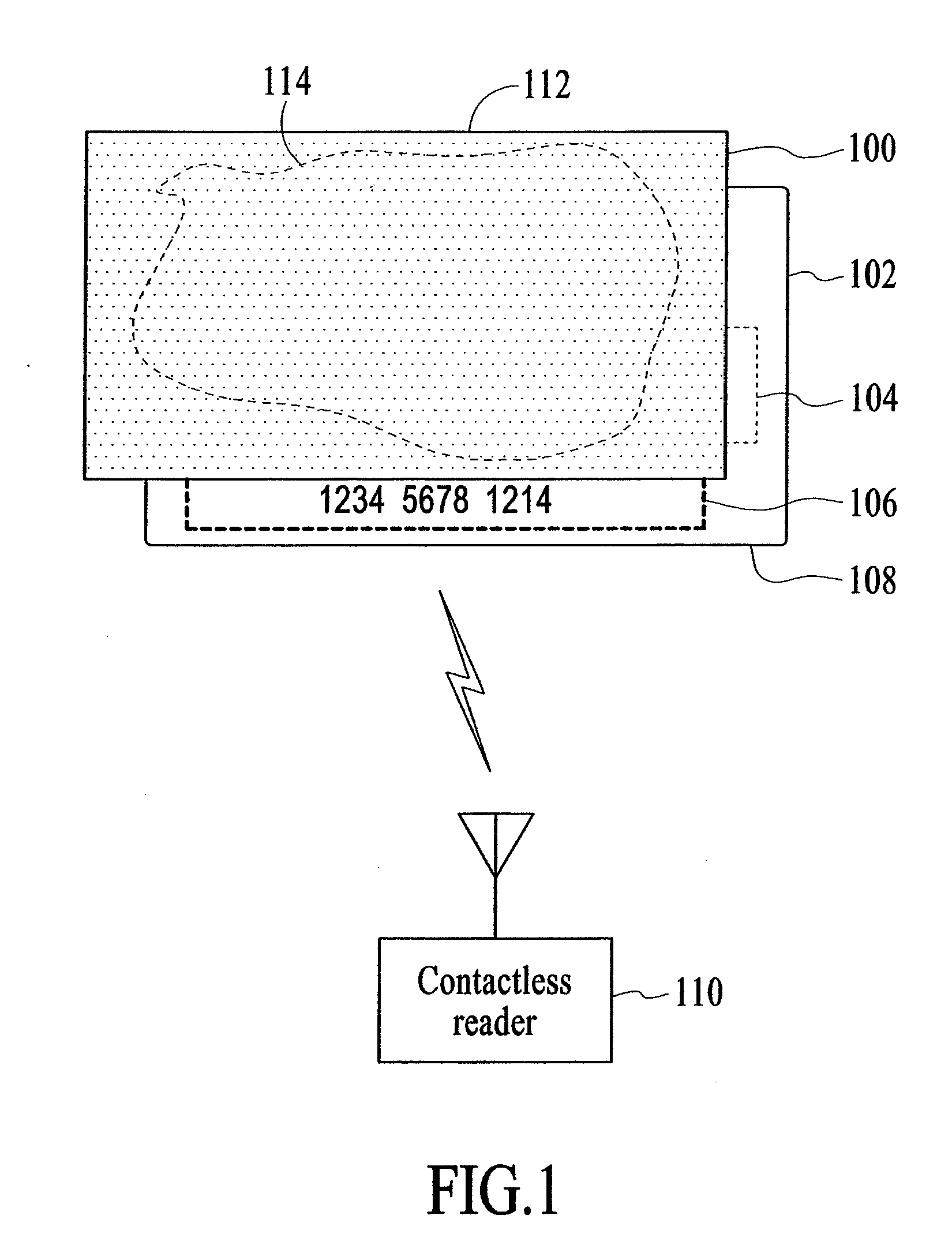
Apparatus and method to electromagnetically shield portable consumer devices
InactiveUS20060290501A1Prevent unauthorizedTicket-issuing apparatusUnauthorised/fraudulent call preventionRadio frequencyData transmission
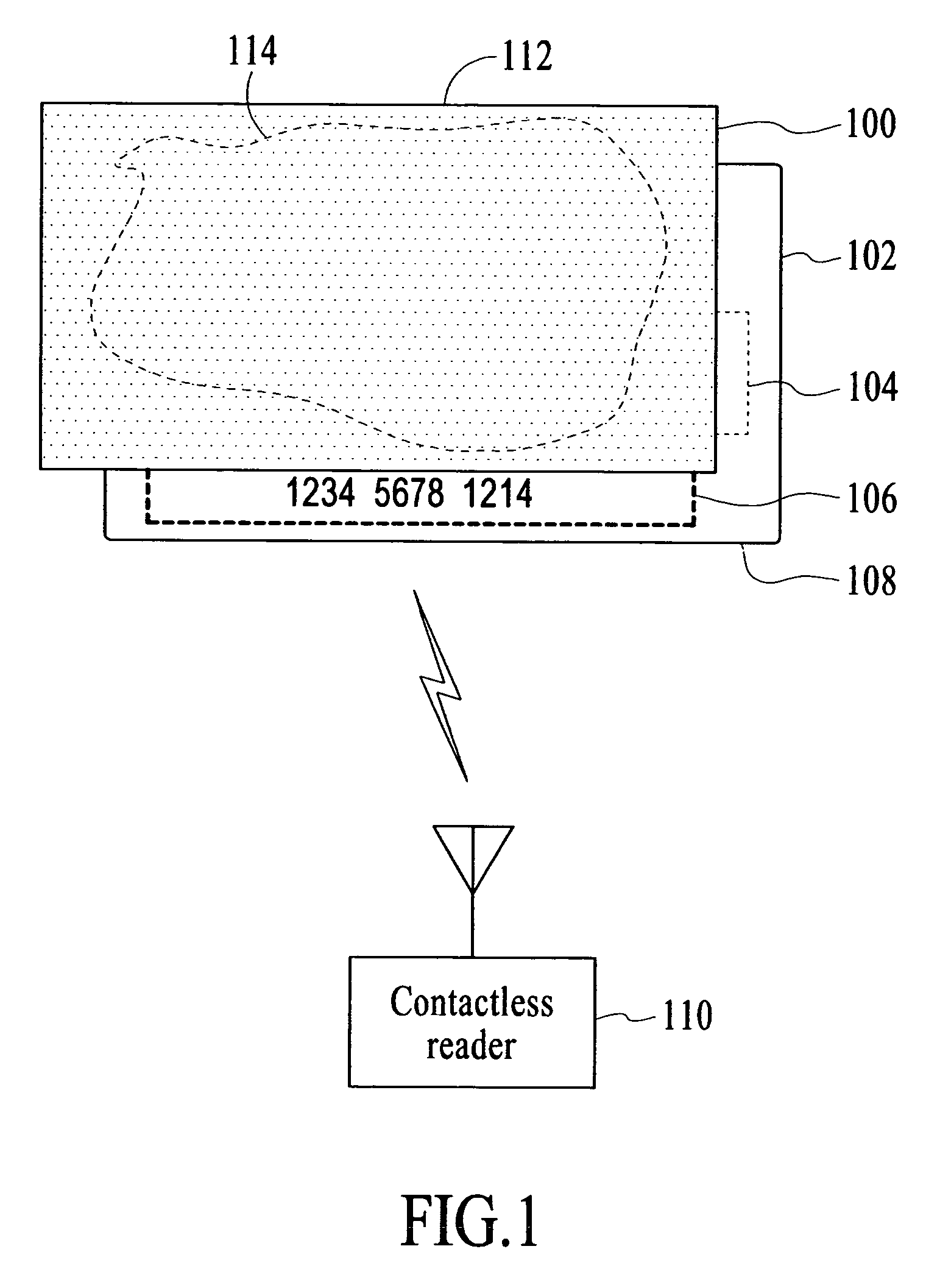
An apparatus and method is provided to shield contactless portable electronic consumer devices such as radio frequency identification devices (RFID), tokens, mini-cards, key fobs, cellular phones, smartcards, etc. from wireless interrogation. In one embodiment, a contactless portable consumer device which includes a first antenna is shielded from unauthorized wireless interrogation with a radio frequency (RF) shield. The RF shield includes electrically conductive, non-ferromagnetic material and is configured to prevent unauthorized data transfer between a second antenna external to the portable consumer device and the first antenna.
Owner:VISA USA INC (US)
Apparatus and method to electromagnetically shield portable consumer devices
InactiveUS7482925B2Prevent unauthorizedTicket-issuing apparatusUnauthorised/fraudulent call preventionEngineeringElectromagnetic shielding
An apparatus and method is provided to shield contactless portable electronic consumer devices such as radio frequency identification devices (RFID), tokens, mini-cards, key fobs, cellular phones, smartcards, etc. from wireless interrogation. In one embodiment, a contactless portable consumer device which includes a first antenna is shielded from unauthorized wireless interrogation with a radio frequency (RF) shield. The RF shield includes electrically conductive, non-ferromagnetic material and is configured to prevent unauthorized data transfer between a second antenna external to the portable consumer device and the first antenna.
Owner:VISA USA INC (US)
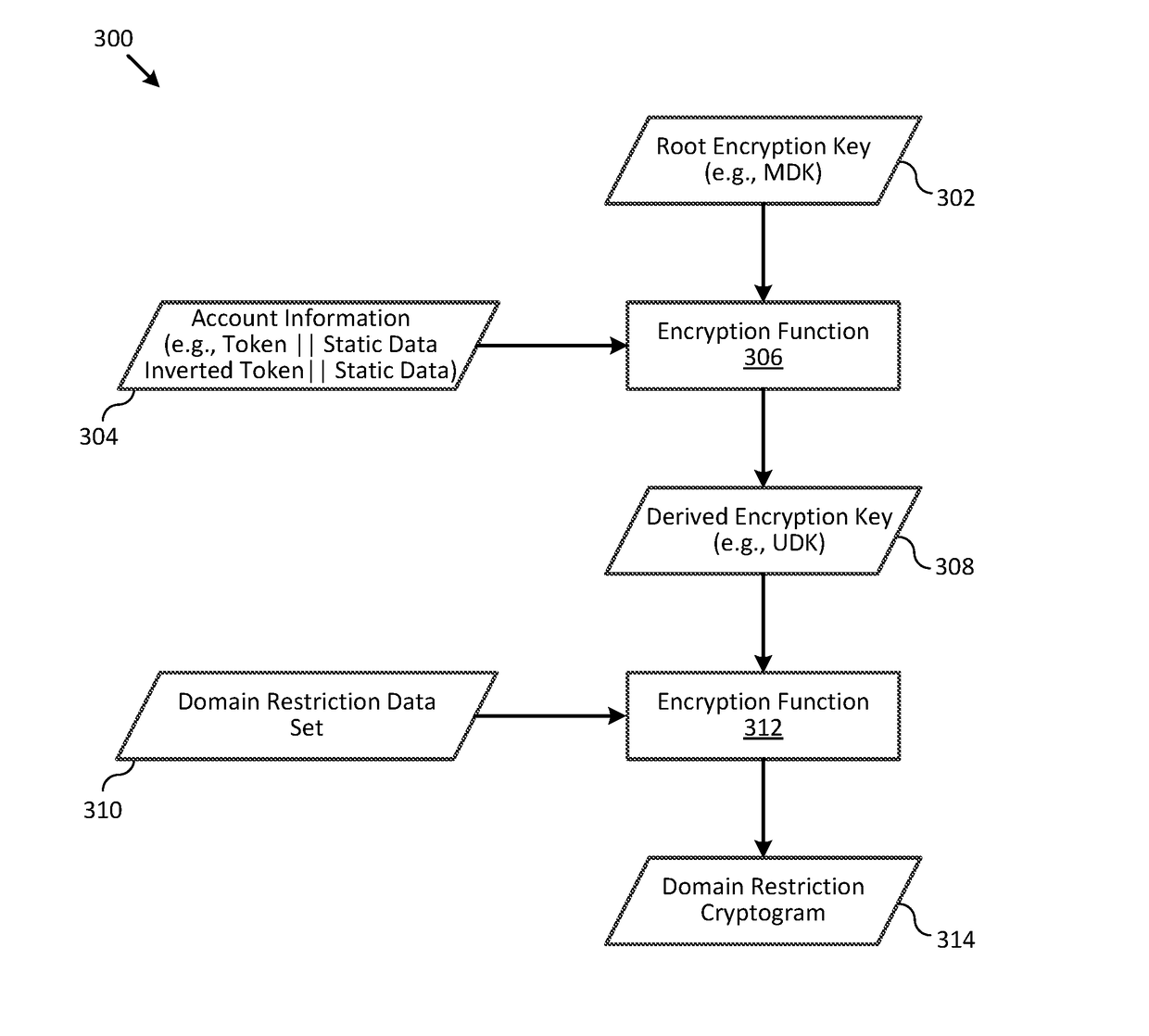
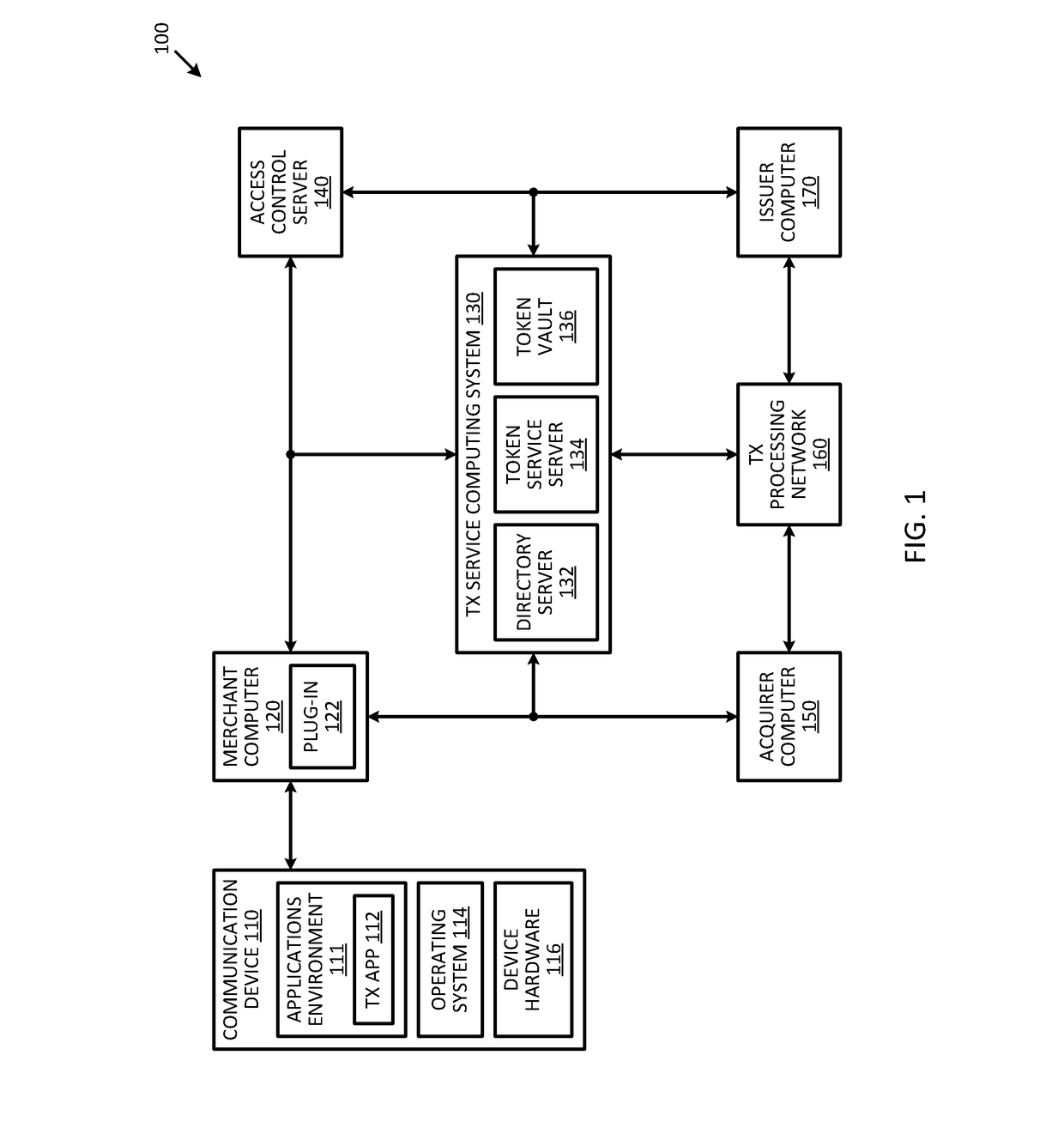
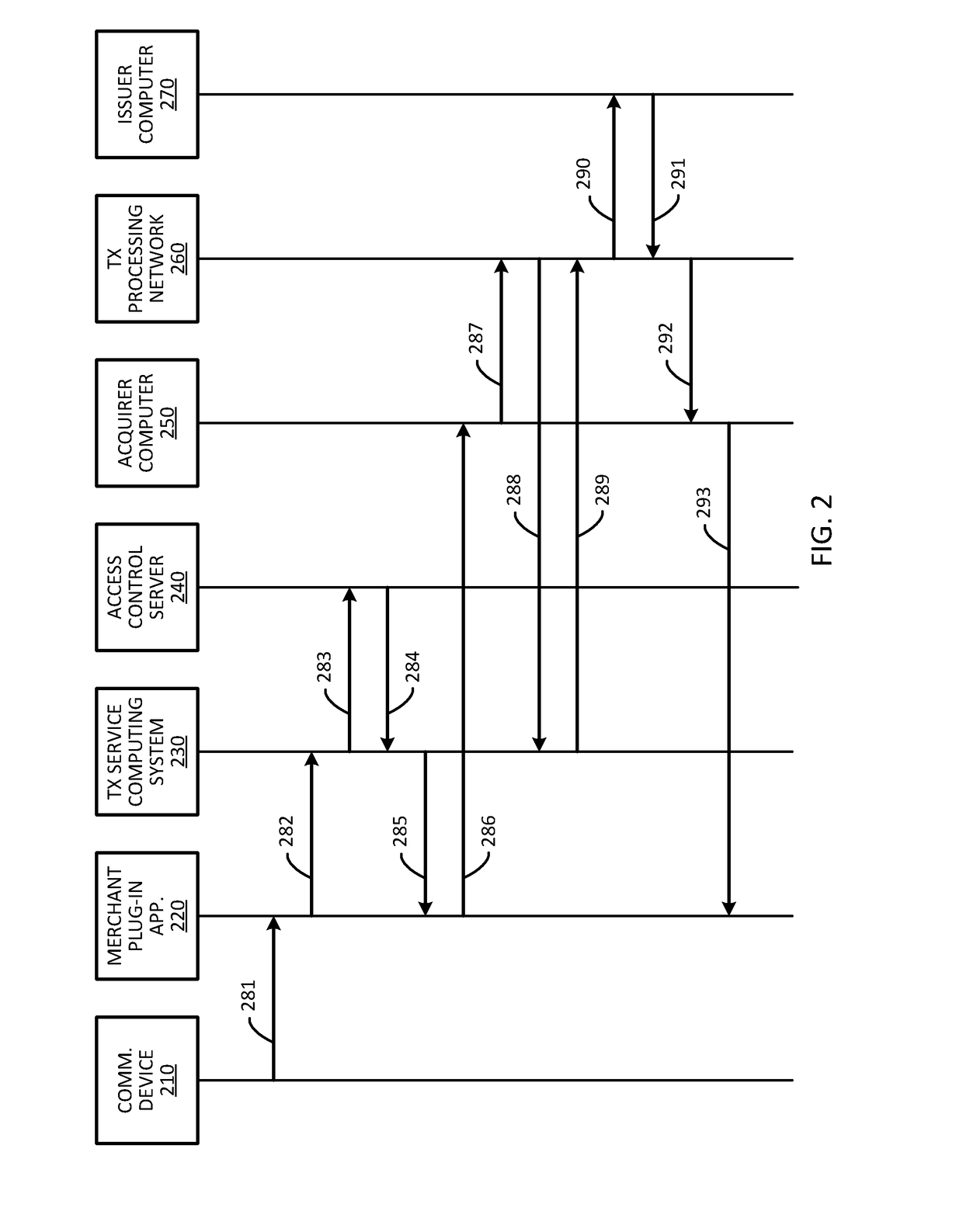
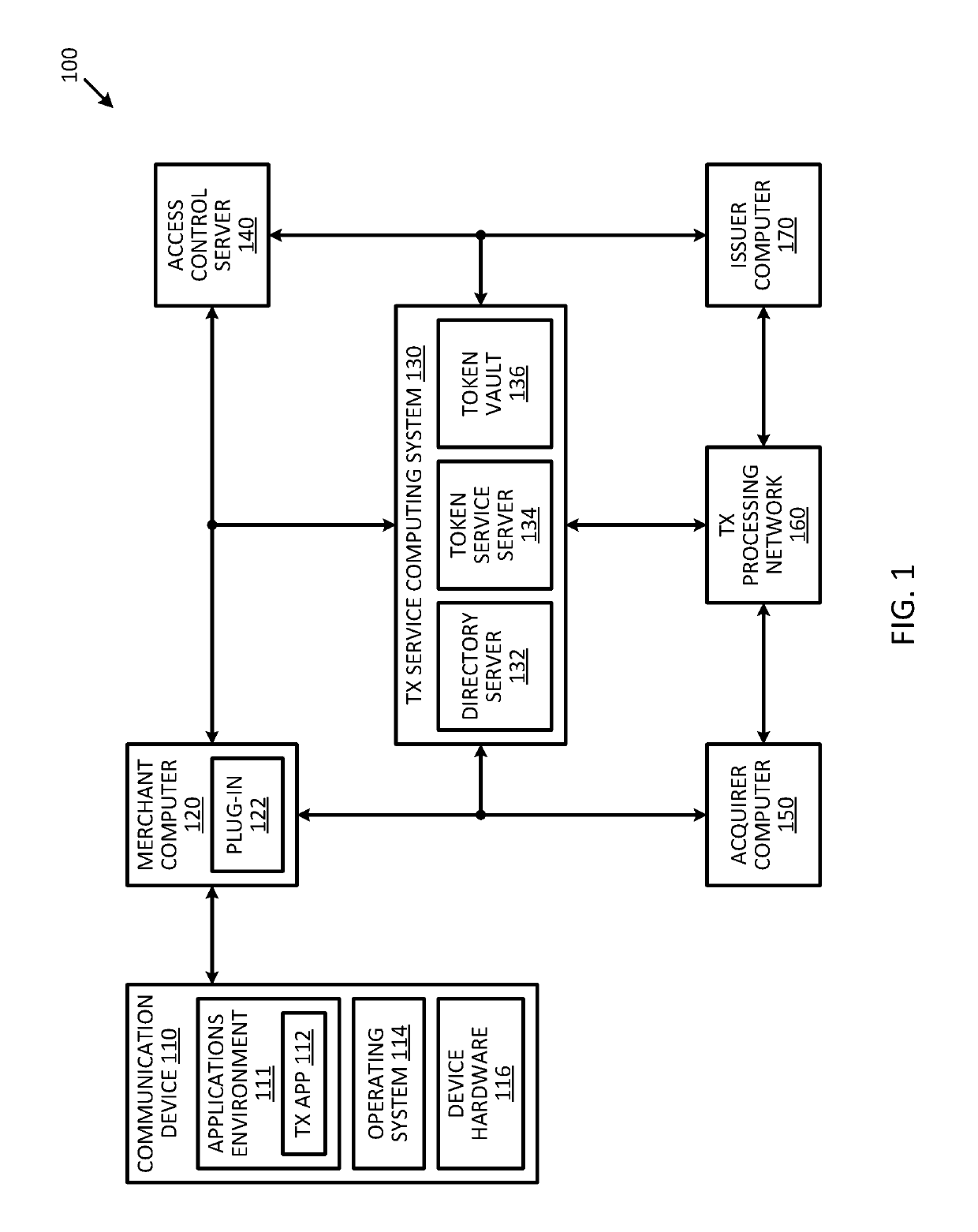
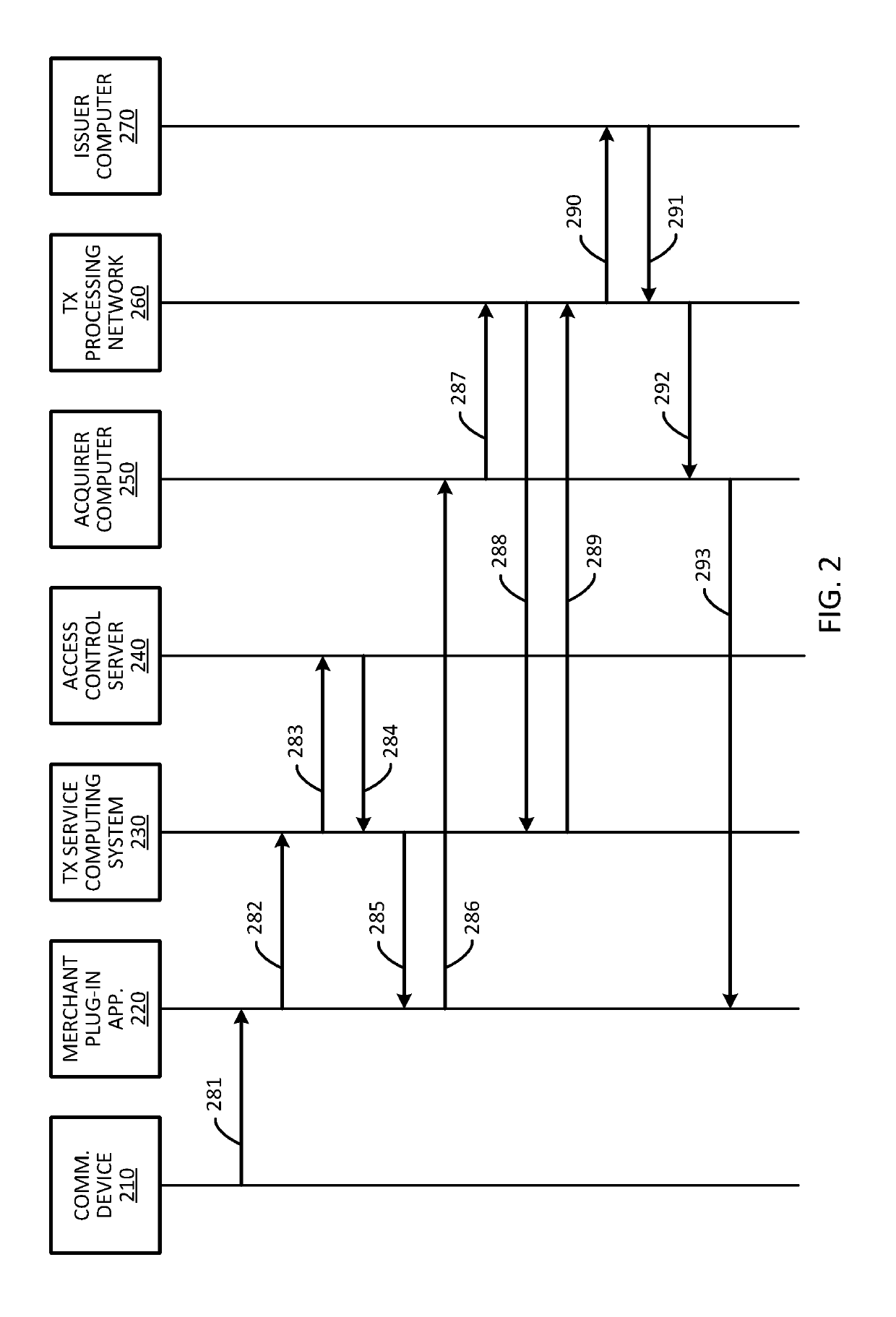
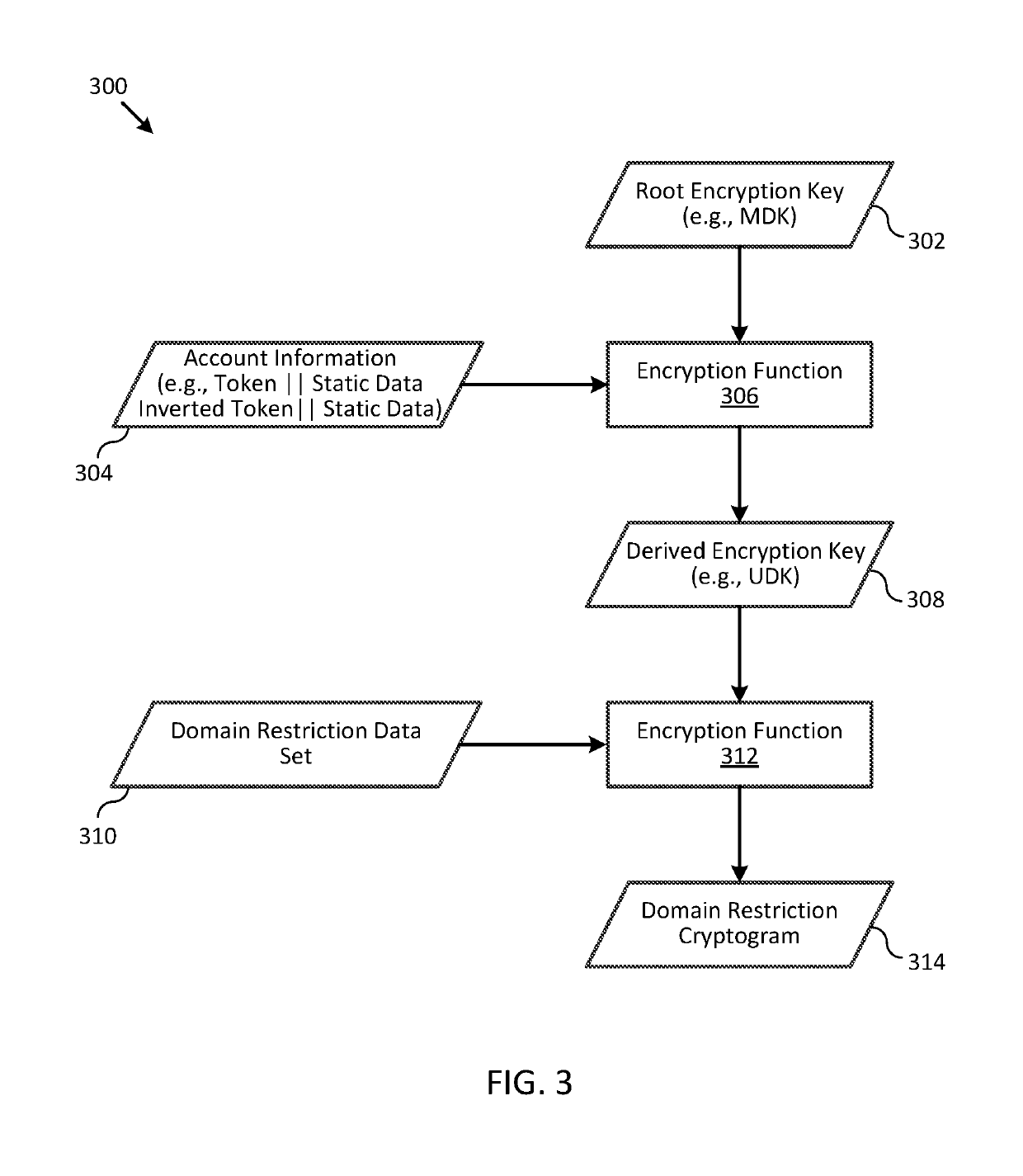
Systems and methods for domain restriction with remote authentication
ActiveUS20170255932A1Prevent unauthorizedReduce usageCryptography processingSecurity arrangementCryptogramA domain
A process for combining domain restriction and remote authentication may include receiving a token from a plug-in application to conduct a transaction associated with a user of a communicating device. The process may include sending an authentication request to a remote access control sever to authenticate the user, and receiving, from the remote access control server, an authentication tracking value that the remote access control server used in generation of an authentication cryptogram. The process may also include generating, using the authentication tracking value, a domain restriction cryptogram that is used for domain restriction of the token, and sending, to the plug-in application, the domain restriction cryptogram.
Owner:VISA INT SERVICE ASSOC
Apparatus and method to electromagnetically shield portable consumer devices
ActiveUS20090088229A1Prevent unauthorizedSubstation equipmentRecord carriers used with machinesElectromagnetic shieldingData transmission
An apparatus and method is provided to shield contactless portable electronic consumer devices such as radio frequency identification devices (RFID), tokens, mini-cards, key fobs, cellular phones, smartcards, etc. from wireless interrogation. In one embodiment, a contactless portable consumer device which includes a first antenna is shielded from unauthorized wireless interrogation with a radio frequency (RF) shield. The RF shield includes electrically conductive, non-ferromagnetic material and is configured to prevent unauthorized data transfer between a second antenna external to the portable consumer device and the first antenna.
Owner:VISA USA INC (US)
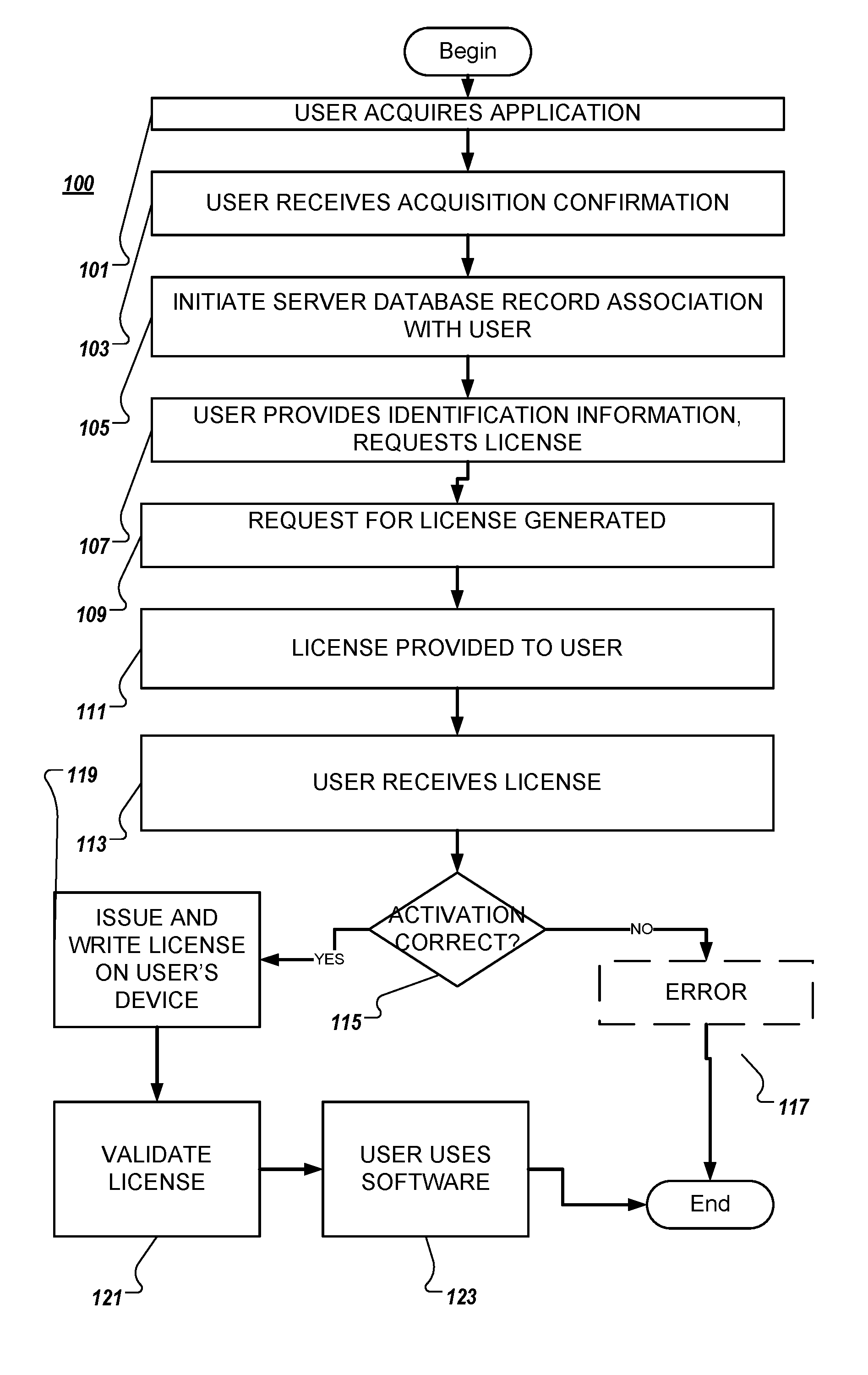
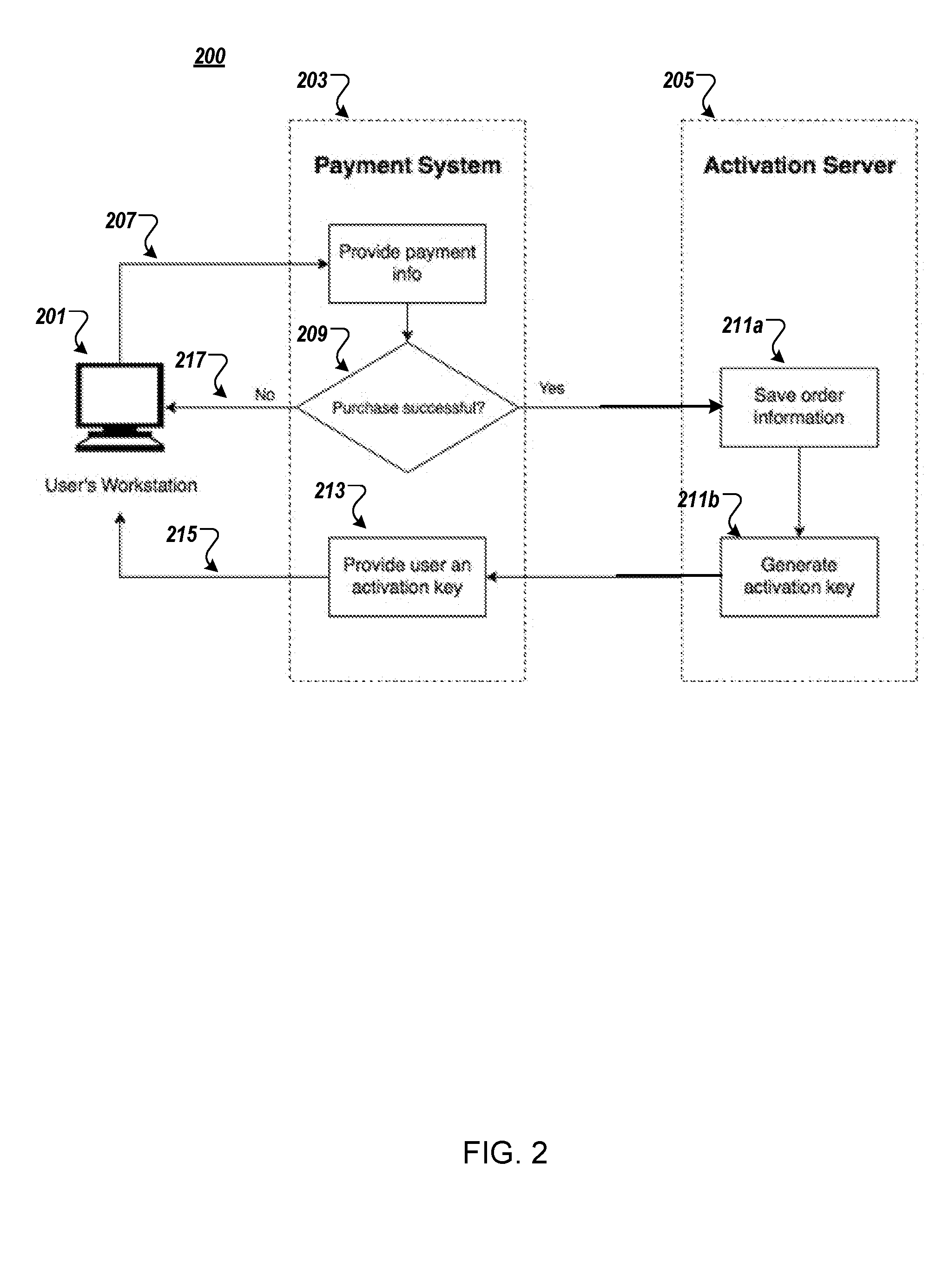
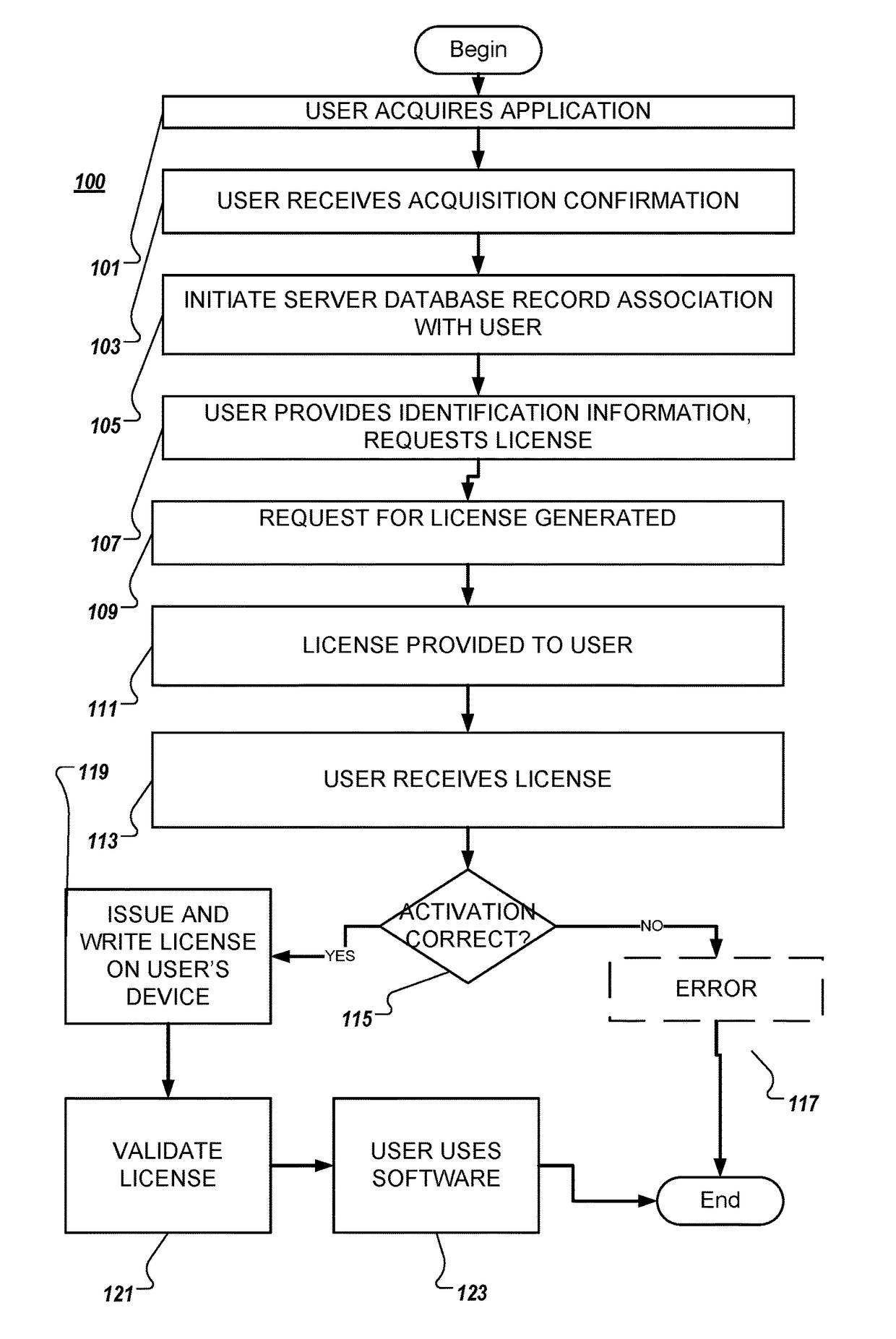
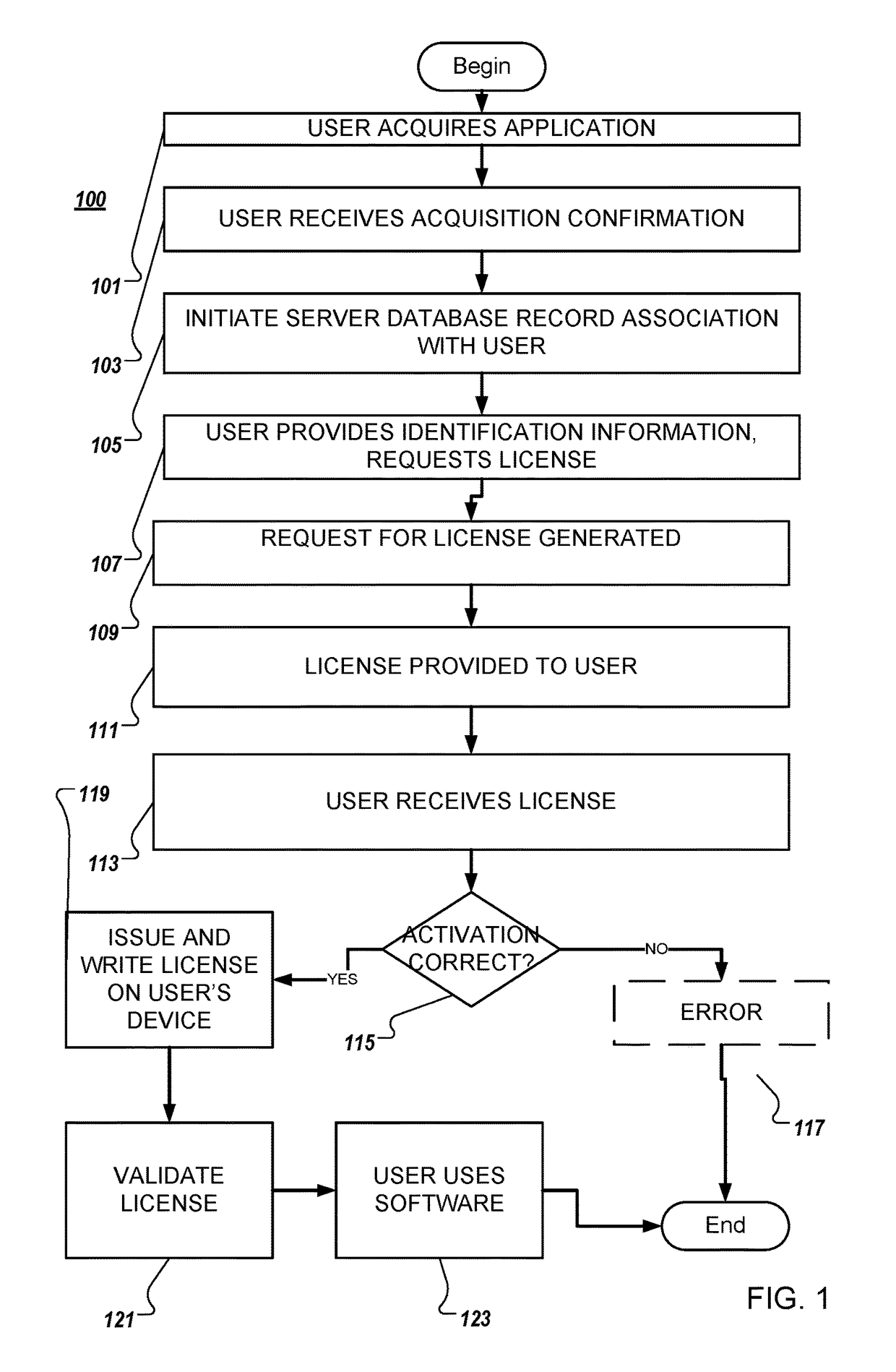
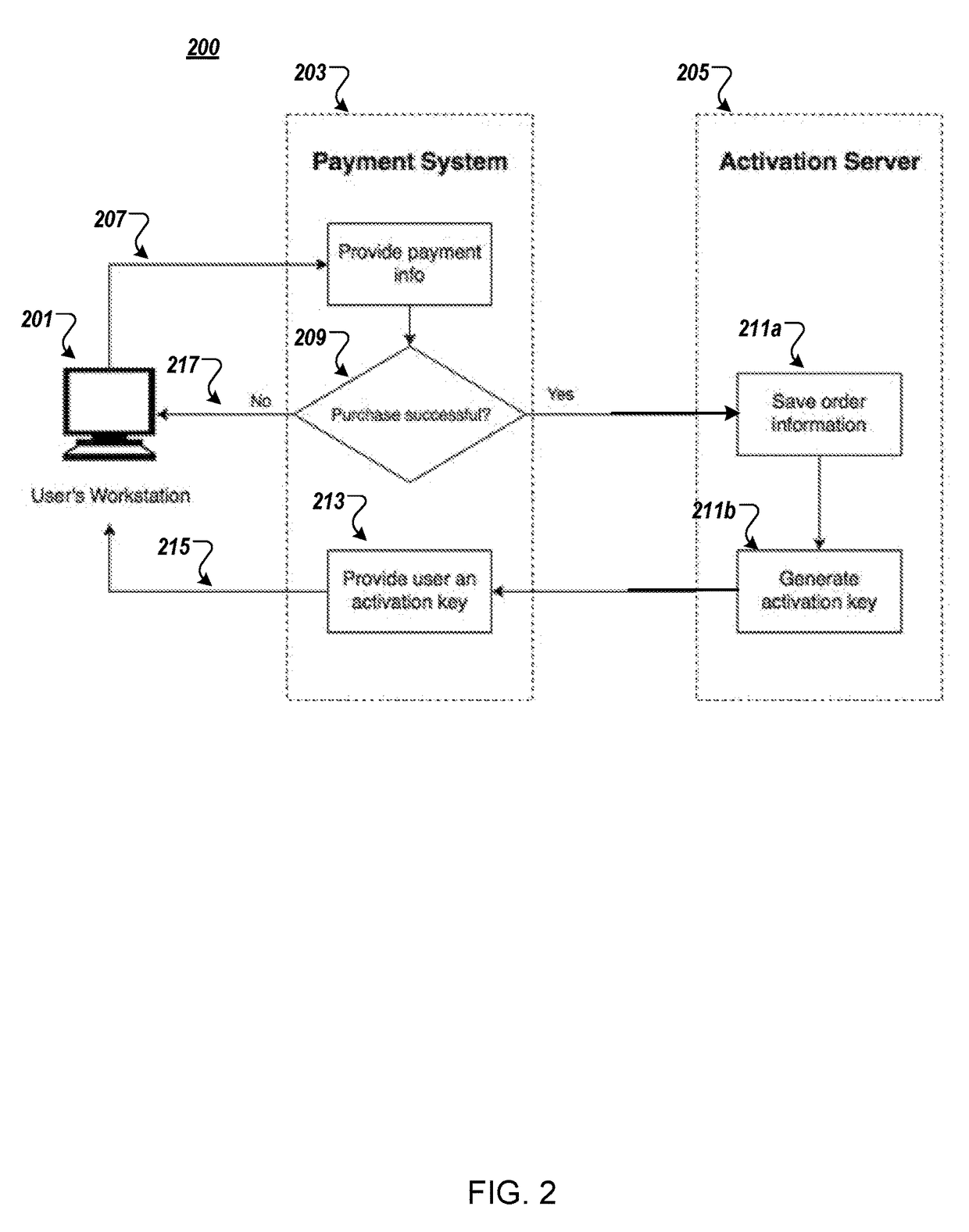
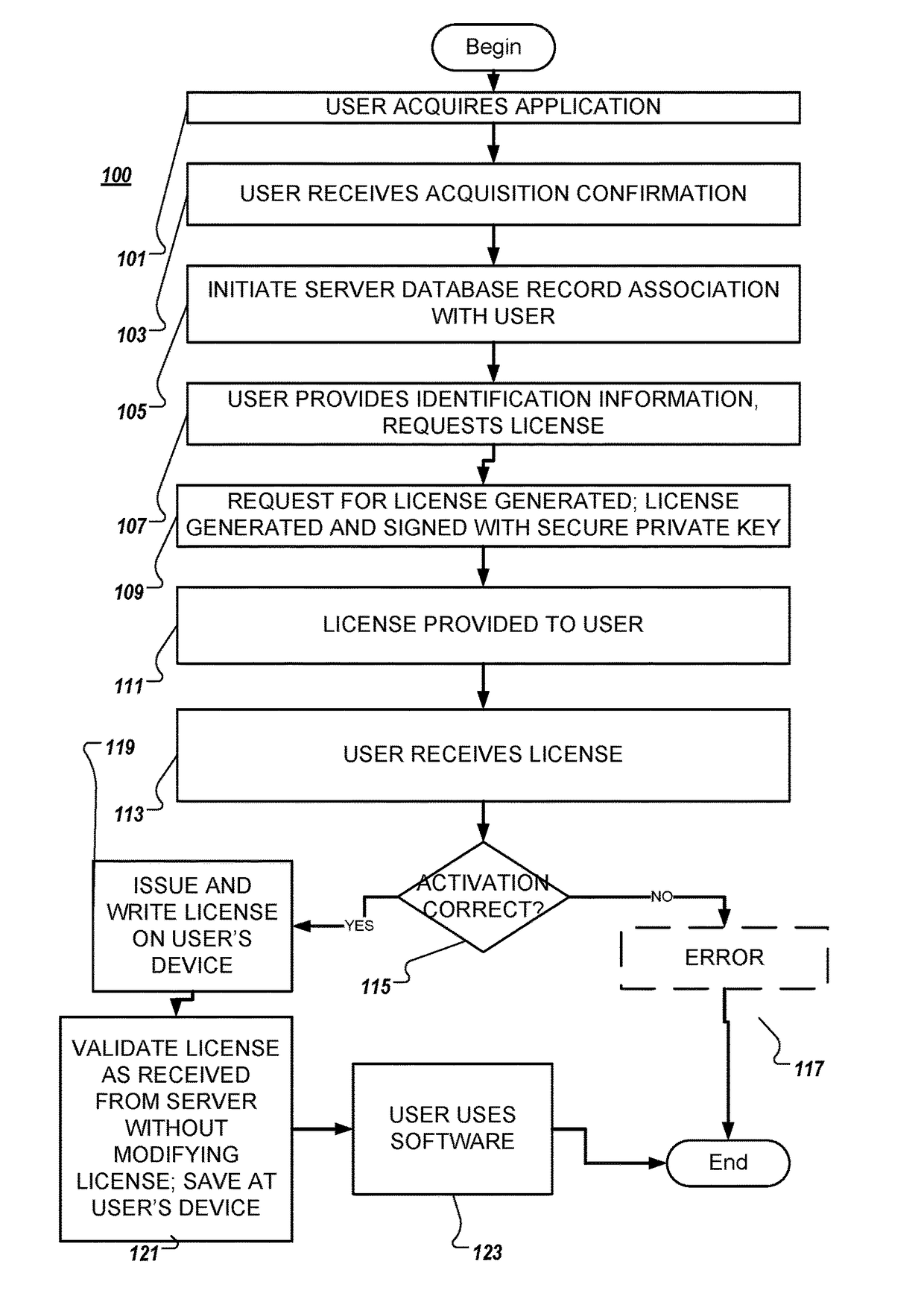
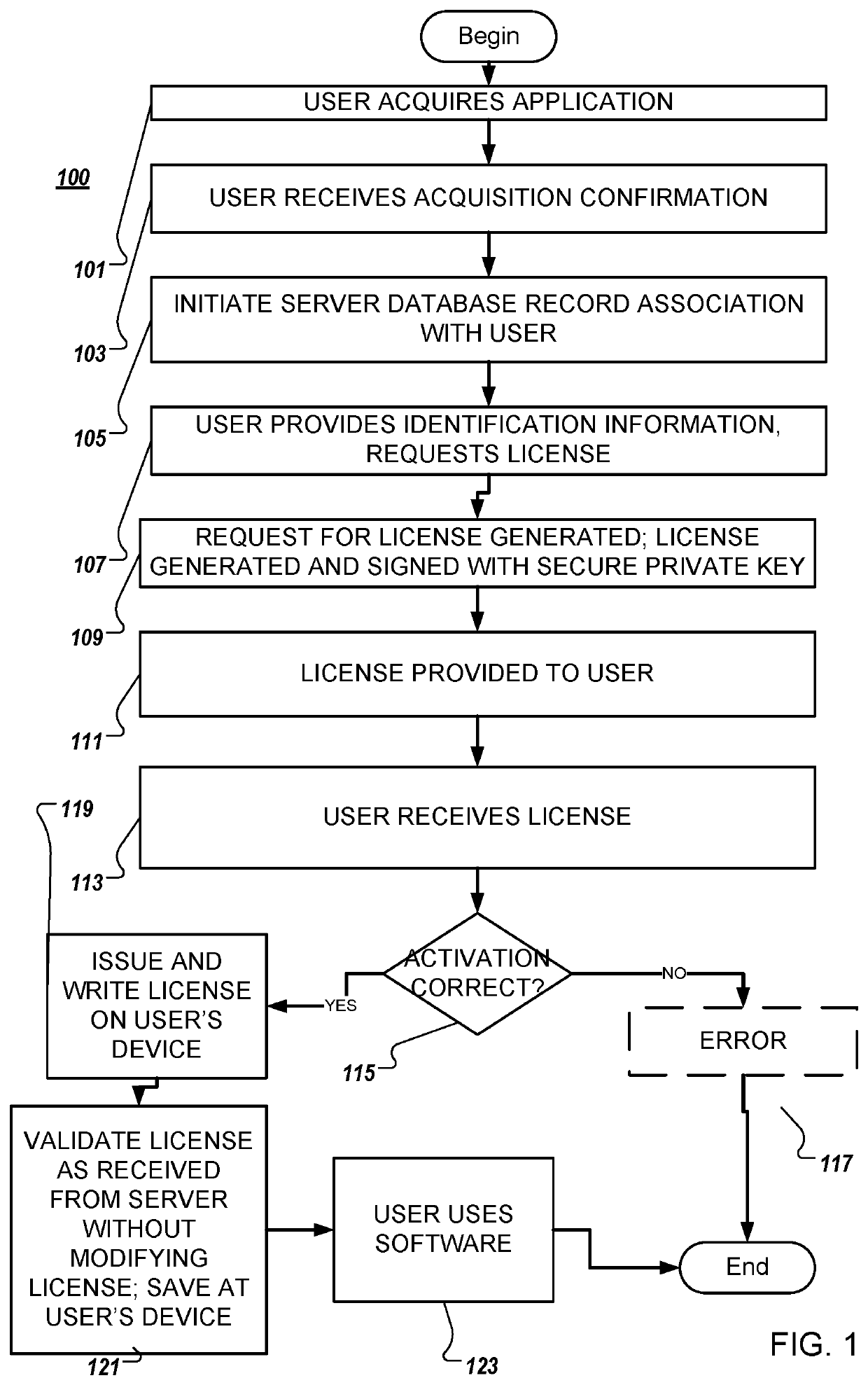
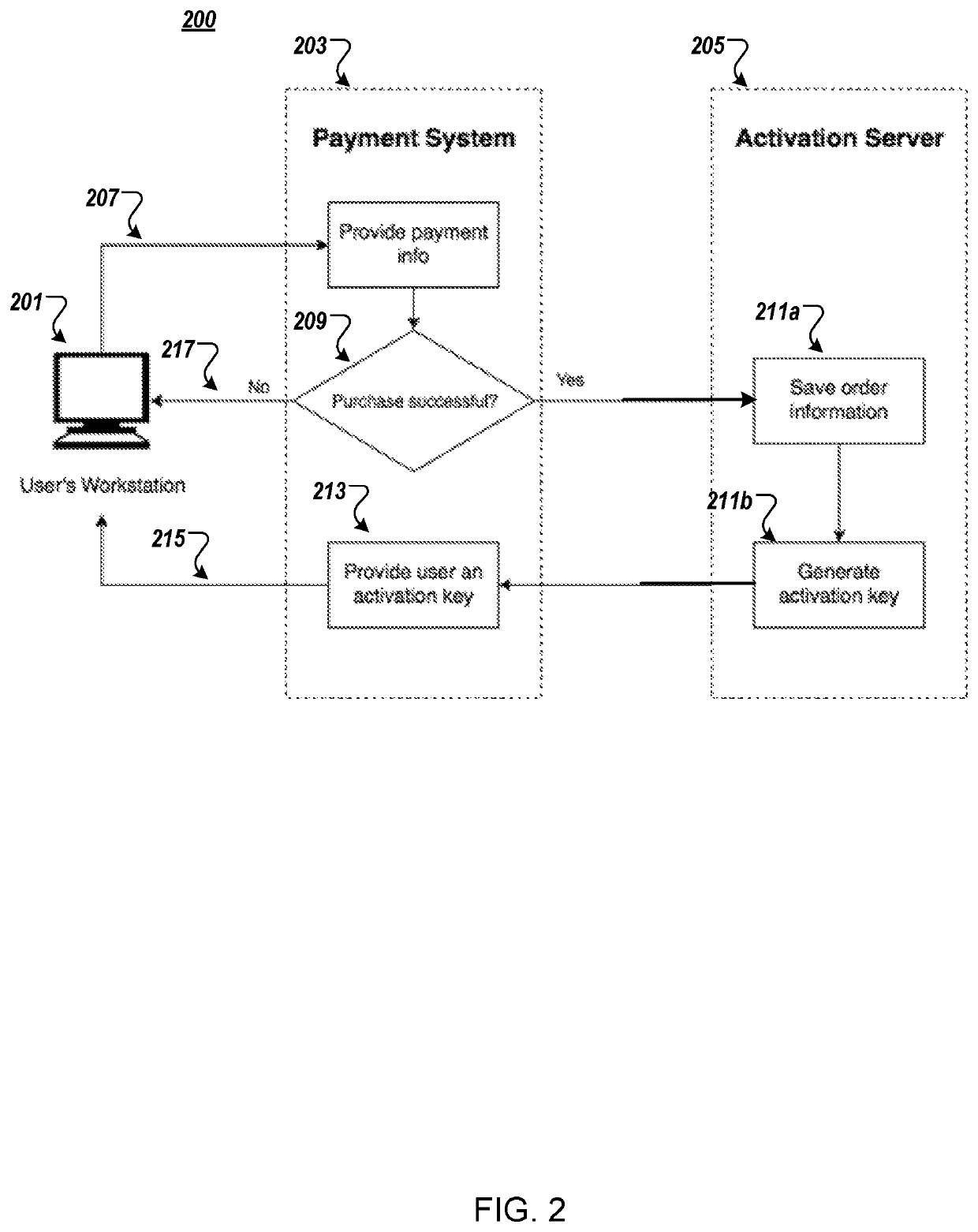
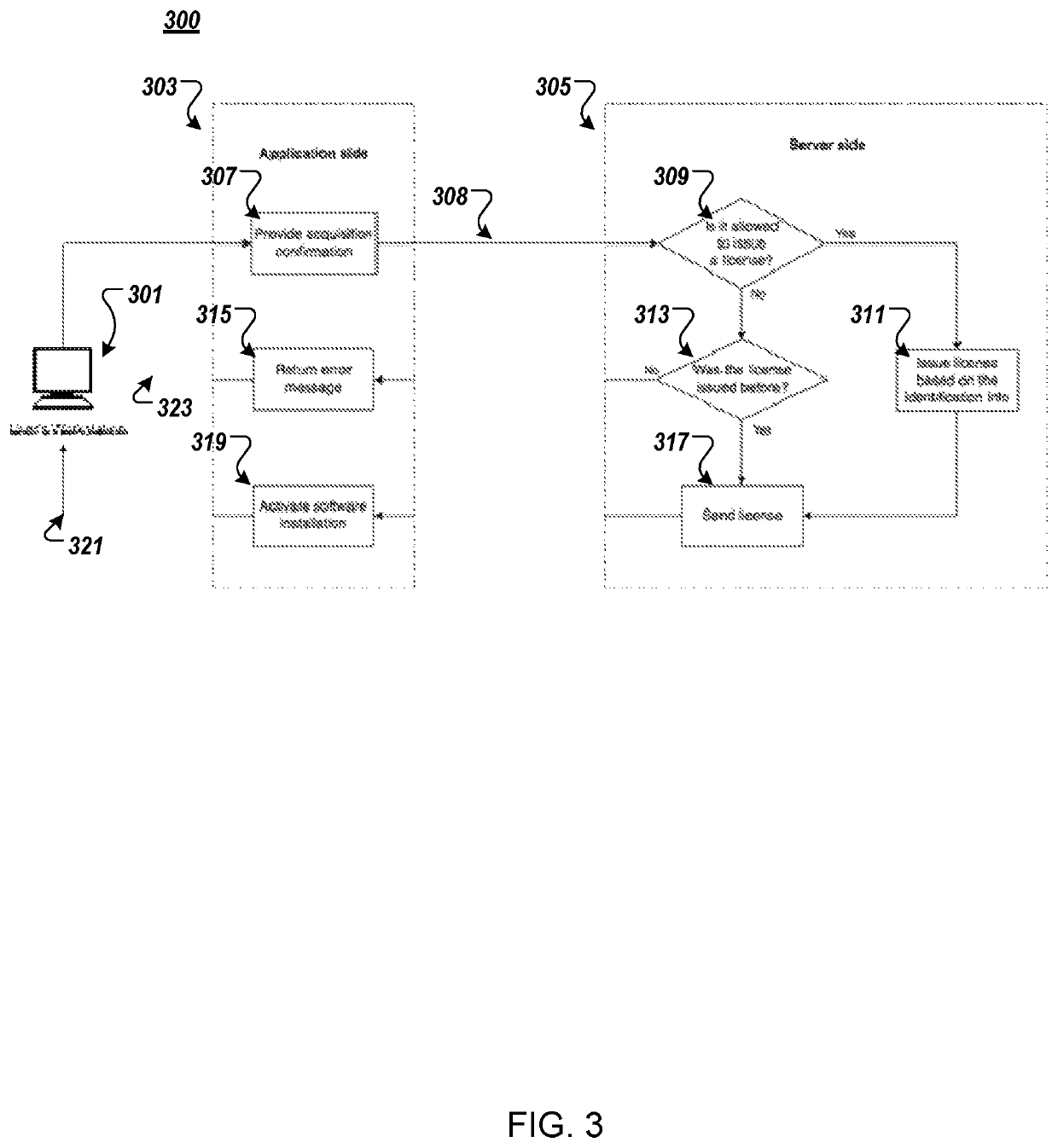
System and method for software activation and license tracking
ActiveUS20160232334A1Simplify the activation processPrevent unauthorizedUser identity/authority verificationProgram/content distribution protectionSoftware distributionSoftware development
System and method for software activation and further tracking of its states on an end-user computing device (computer) was developed to provide software developers a flexible and secure tool for software distribution and gathering statistics of usage of software activation. The method consists of the following logical steps: (a) obtaining an acquisition confirmation; (b) requesting for a license; (c) issuing and delivering the license to End User; (d) verification of license on the User's computer; (e) storing the license on the User's computer; (f) periodic tracking of activation state, (g) another action with the User's license.
Owner:MACPAW WAY LTD
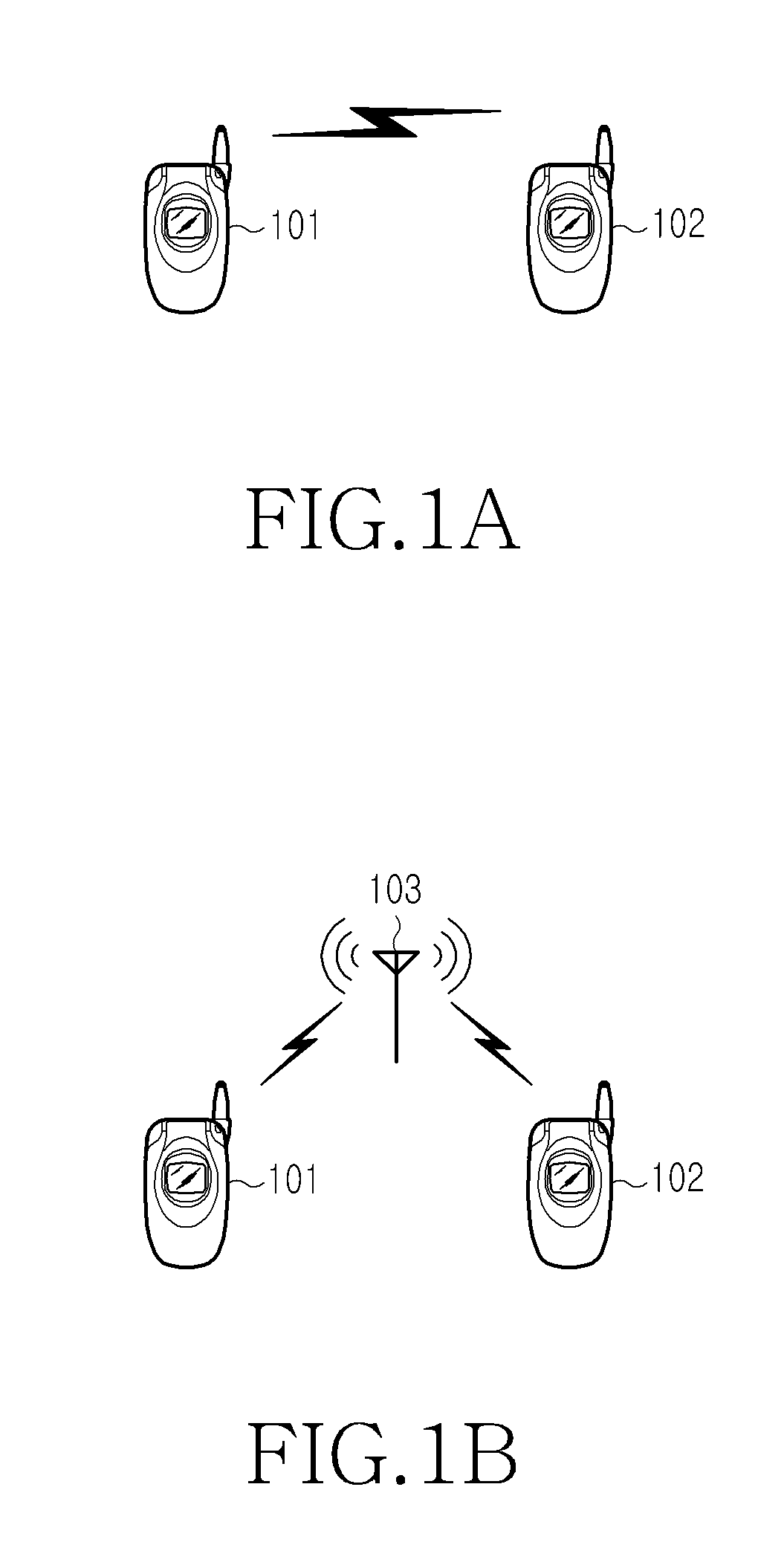
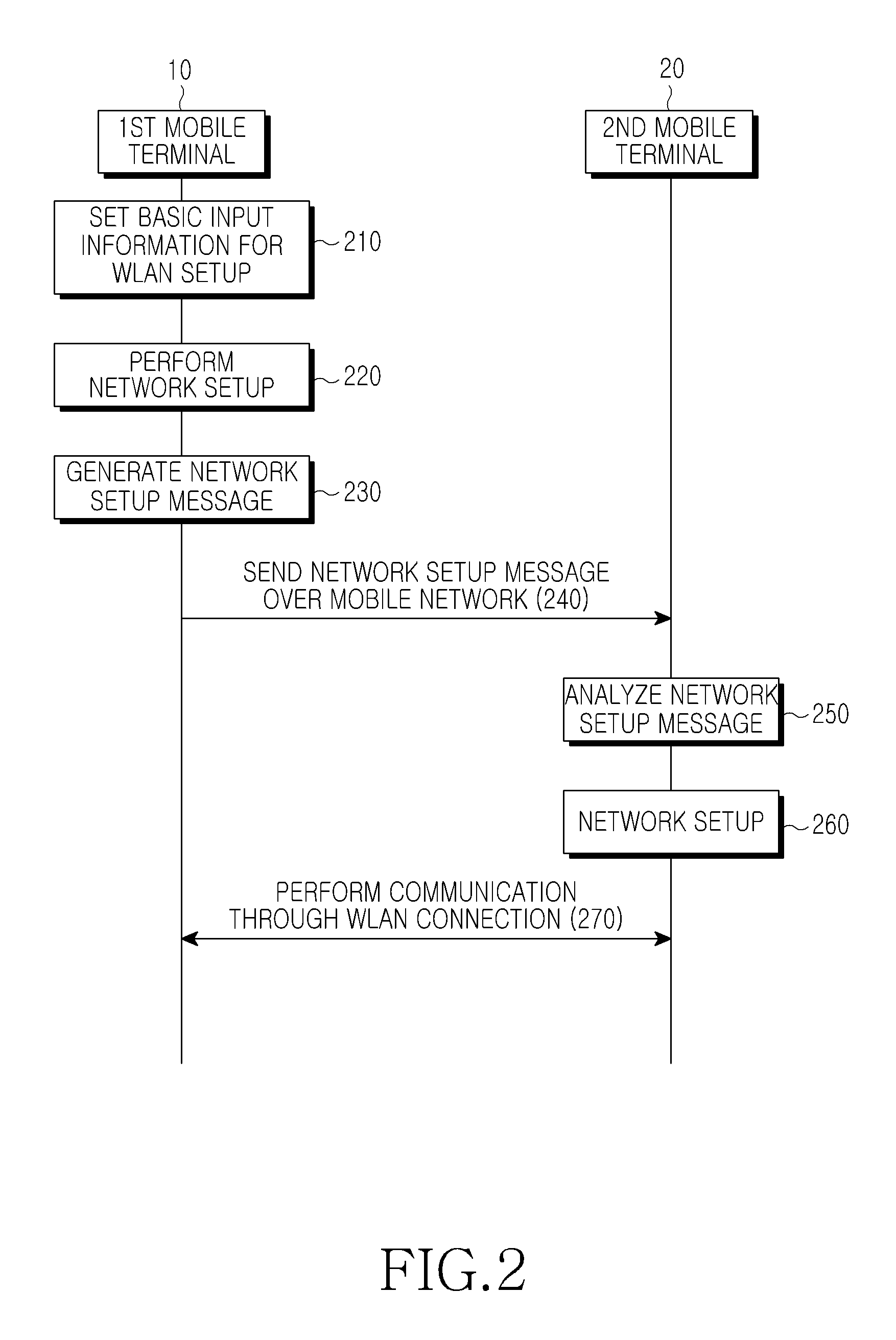
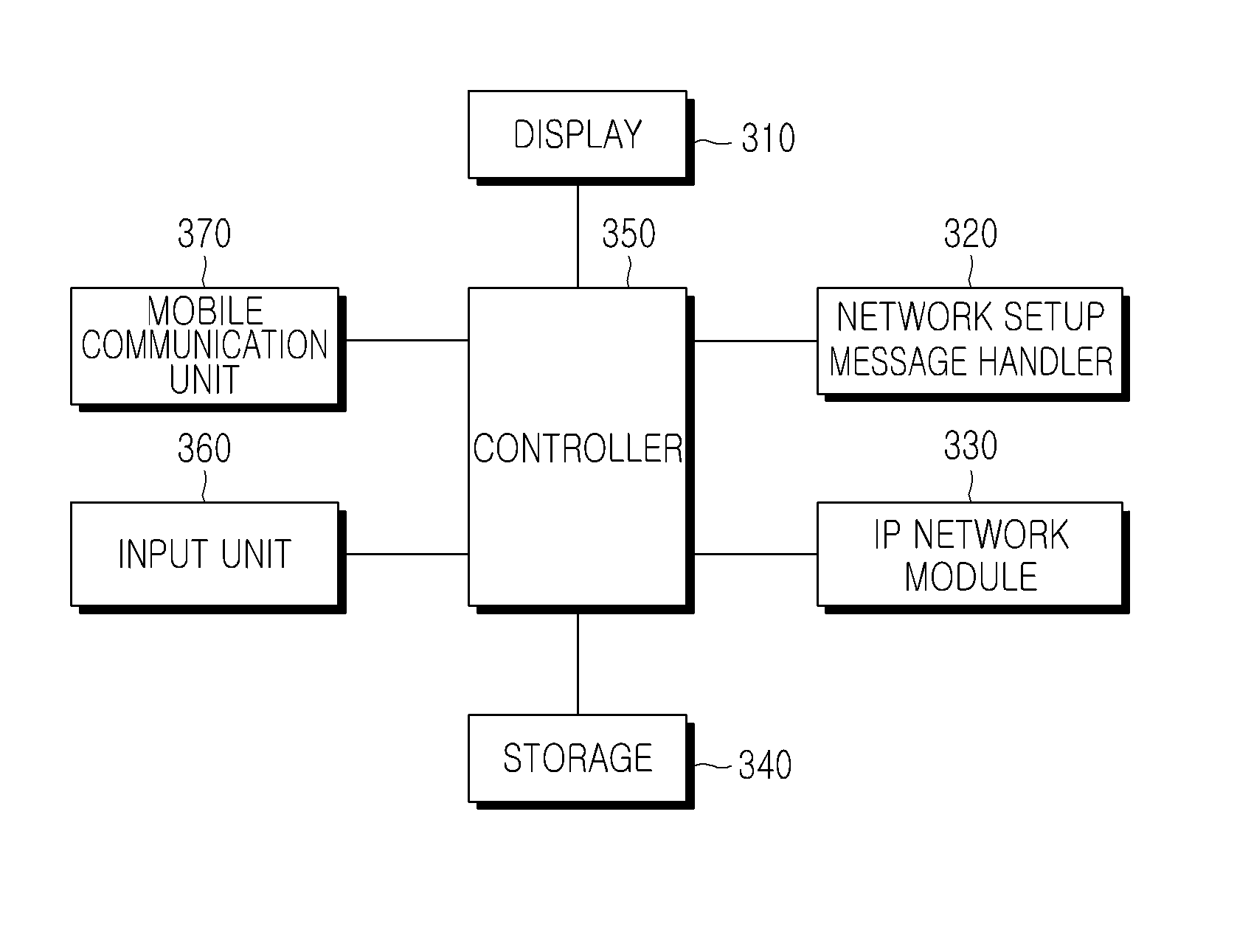
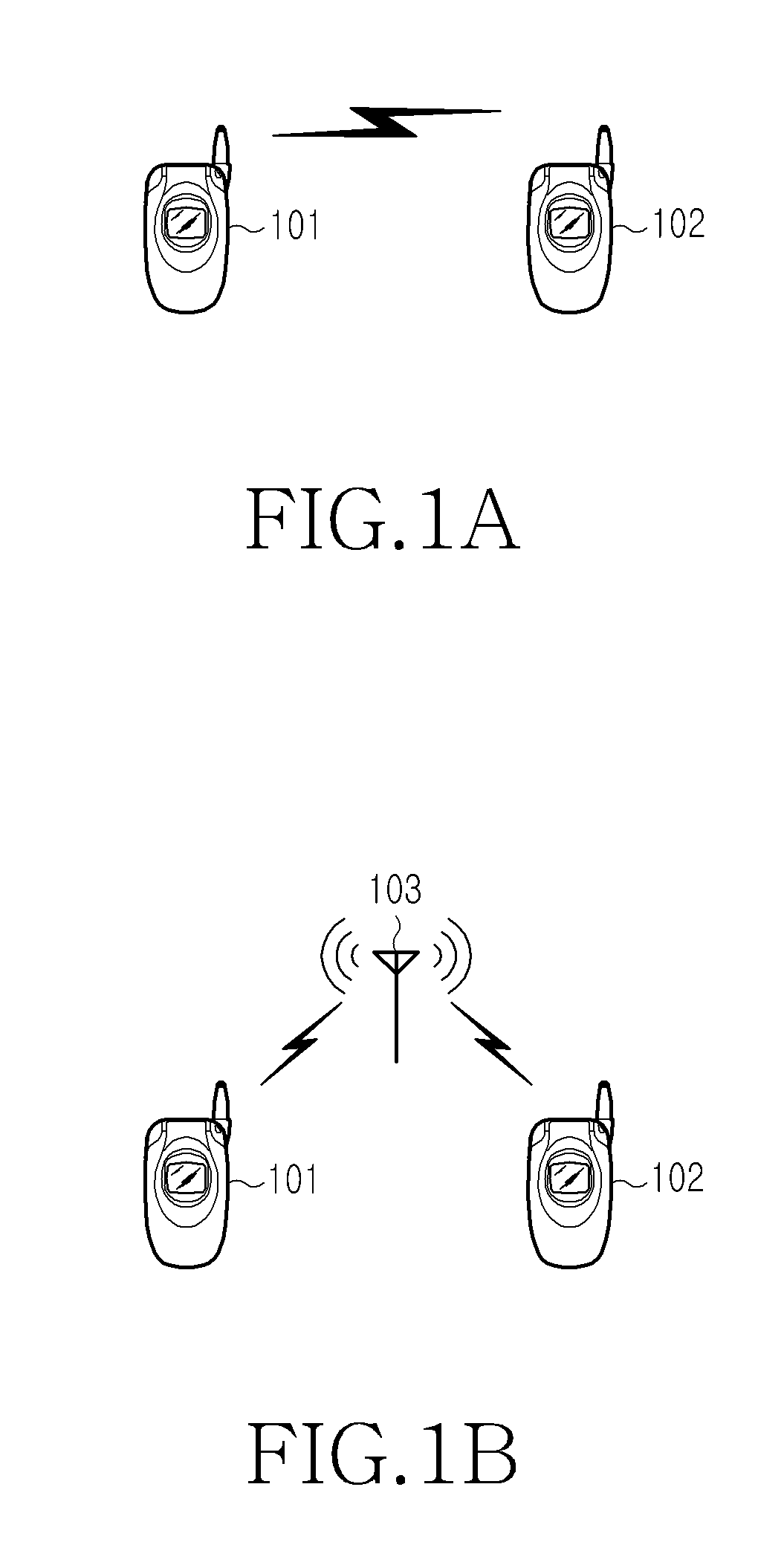
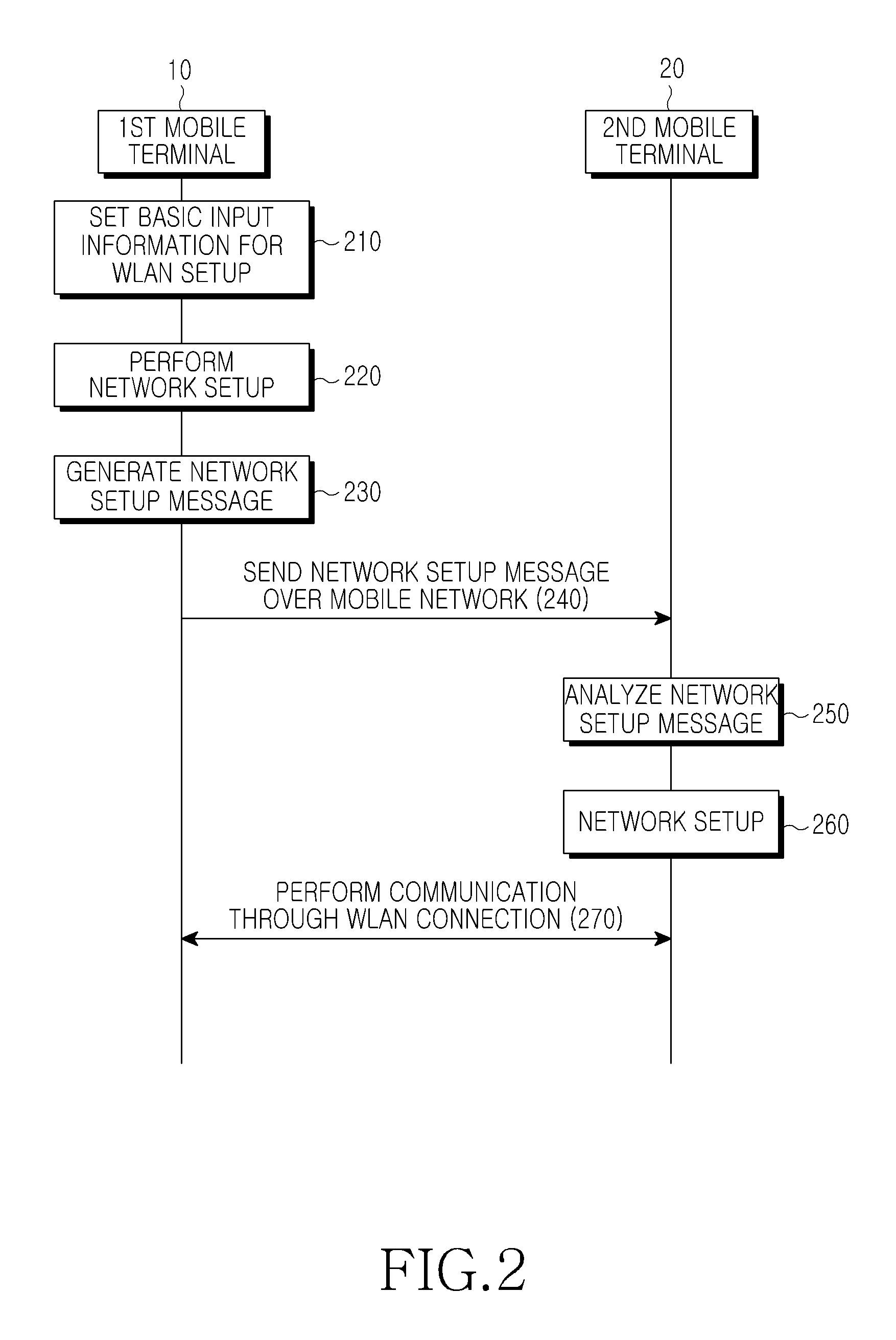
Method and apparatus for setting up network for IP communication in mobile terminal
ActiveUS20110228699A1Ensure safetyPrevent unauthorizedError preventionTransmission systemsTelecommunicationsComputer science
A method is provided for setting up a network for Internet Protocol (IP) communication between mobile terminals. A first mobile terminal determines a second mobile terminal that will communicate with the first mobile terminal. The first mobile terminal generates network setup information of the first mobile terminal for the IP communication and performs network setup using the network setup information. The first mobile terminal generates a network setup message including network setup information of the second mobile terminal, and sends the network setup message to the second mobile terminal.
Owner:SAMSUNG ELECTRONICS CO LTD
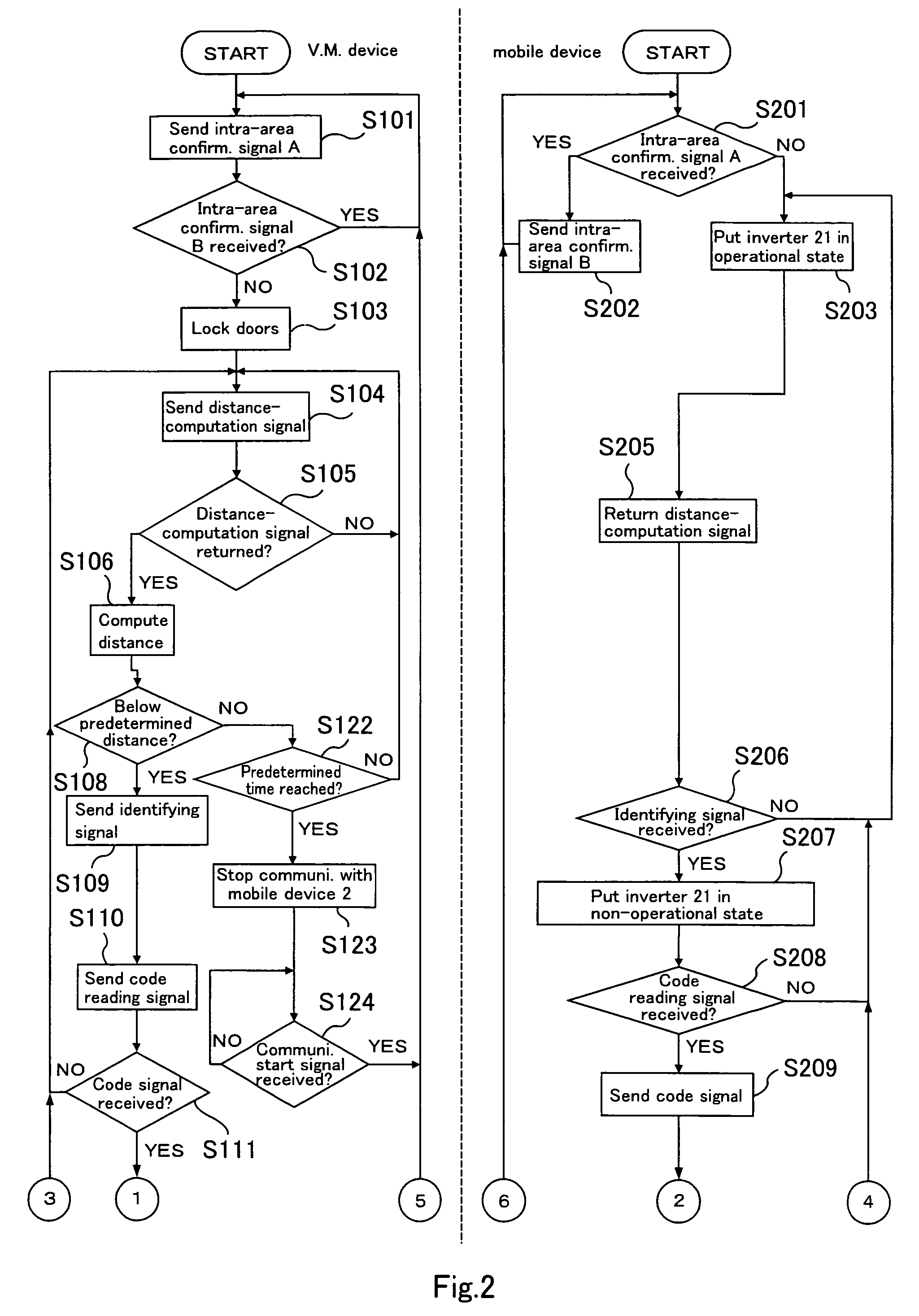
Communication device and distance calculation system
ActiveUS7466219B2Avoid communicationReliable calculationElectric signal transmission systemsDigital data processing detailsPhase differenceMobile device
A communication device (e.g., an vehicle-mounted device) comprises a transmitter that transmits a distance-calculation signal with which to calculate a distance to a partner communication device (e.g., a mobile device), a detector that receives the distance-calculation signal returned from the partner communication device and detects a phase difference between the distance-calculation signal when transmitted and the distance-calculation signal when received, and a calculator that calculates the distance to the partner communication device based on the phase difference detected by the detector.
Owner:SEMICON COMPONENTS IND LLC
System and method for software activation and license tracking
ActiveUS9659155B2Activation is simpleReduce in quantityUser identity/authority verificationProgram/content distribution protectionSoftware distributionSoftware development
System and method for software activation and further tracking of its states on an end-user computing device (computer) was developed to provide software developers a flexible and secure tool for software distribution and gathering statistics of usage of software activation. The method consists of the following logical steps: (a) obtaining an acquisition confirmation; (b) requesting for a license; (c) issuing and delivering the license to End User; (d) verification of license on the User's computer; (e) storing the license on the User's computer; (f) periodic tracking of activation state, (g) another action with the User's license.
Owner:MACPAW WAY LTD
System and method for software activation and license tracking
ActiveUS20170255762A1Activation is simpleReduce in quantityUser identity/authority verificationProgram/content distribution protectionSoftware distributionSoftware engineering
System and method for software activation and further tracking of its states on an end-user computing device (computer) was developed to provide software developers a flexible and secure tool for software distribution and gathering statistics of usage of software activation. The method consists of the following logical steps: (a) obtaining an acquisition confirmation; (b) requesting for a license; (c) issuing and delivering the license to End User, the license being secured with a private key by a server, and the private key is not stored at the client; (d) verification of license on the User's computer; (e) storing the license on the User's computer; (f) periodic tracking of activation state, (g) another action with the User's license, wherein the verifying the license comprises validating, at the client associated with the application, the license received from the server without any modifications, and saving the license to the client.
Owner:MACPAW WAY LTD
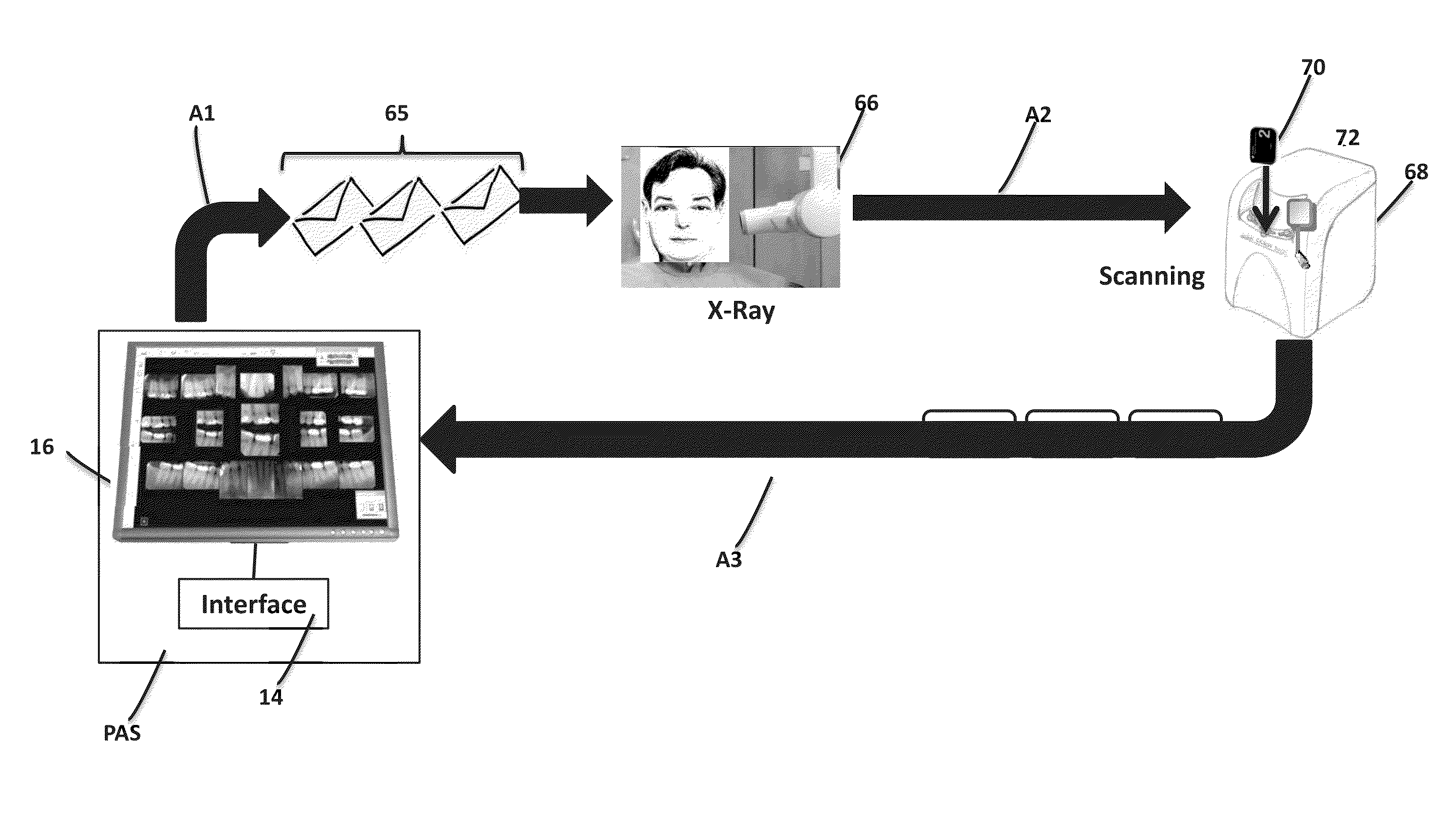
Computed radiography license method and system
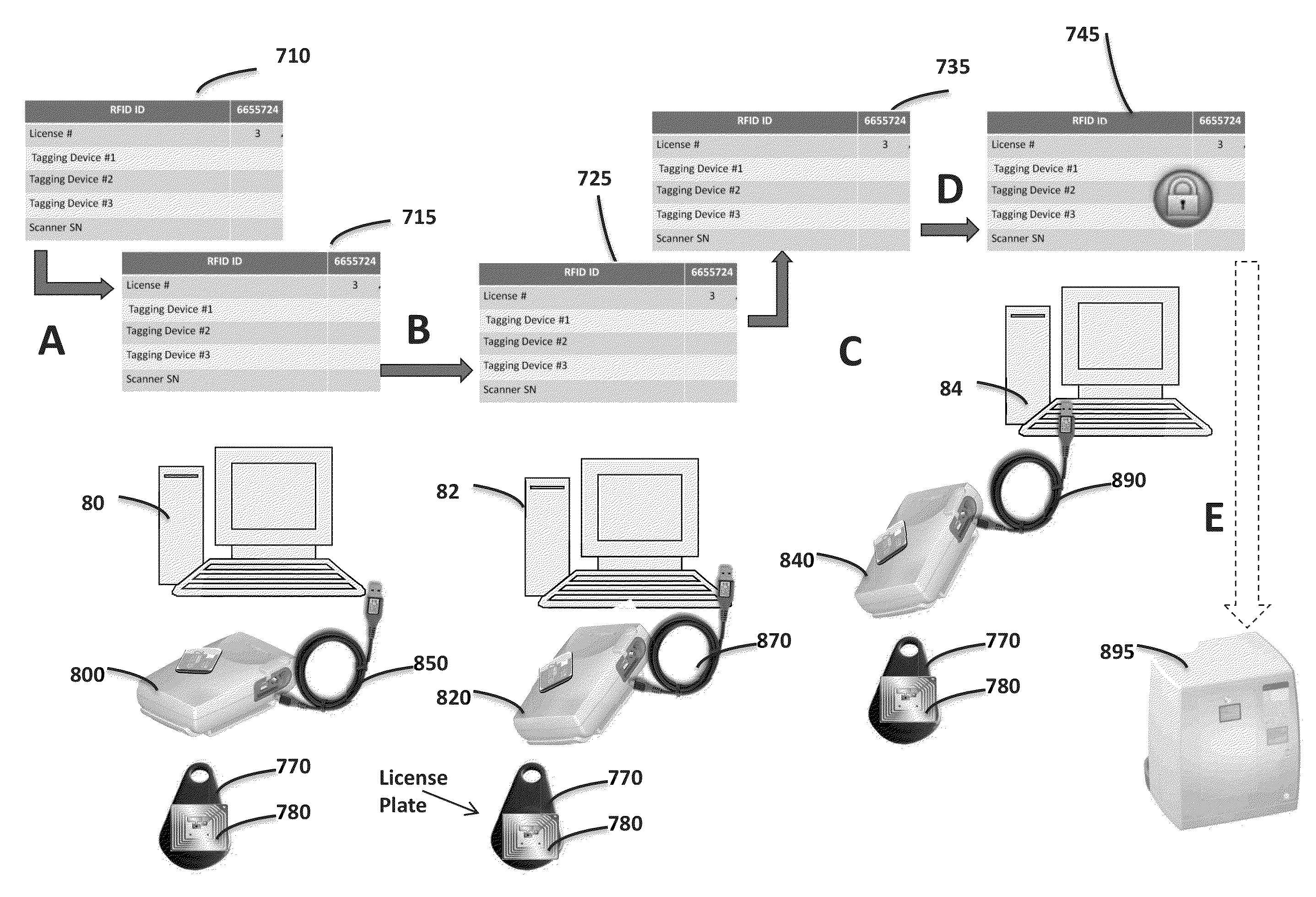
ActiveUS20130193206A1Simple and convenient and reliablePrevent unauthorized accessSurgeryX/gamma/cosmic radiation measurmentX ray imageLicense
A method for licensing a system for obtaining an X-ray image of a subject. The system employs flexible information carrier plates for computed radiography, which are exposed to X-rays and then scanned in a scanner. A license media is provided with a RFID transponder, which stores in its memory identification information referring to the system components as well as information referring to an amount of valid licenses available for use of the system components. When the identification information stored in the memory of the license media RFID transponder matches the identification information transmitted to the scanner by a processing and acquisition station the carrier plates are scanned automatically.
Owner:CARESTREAM DENTAL TECH TOPCO LTD
Computer data protecting method
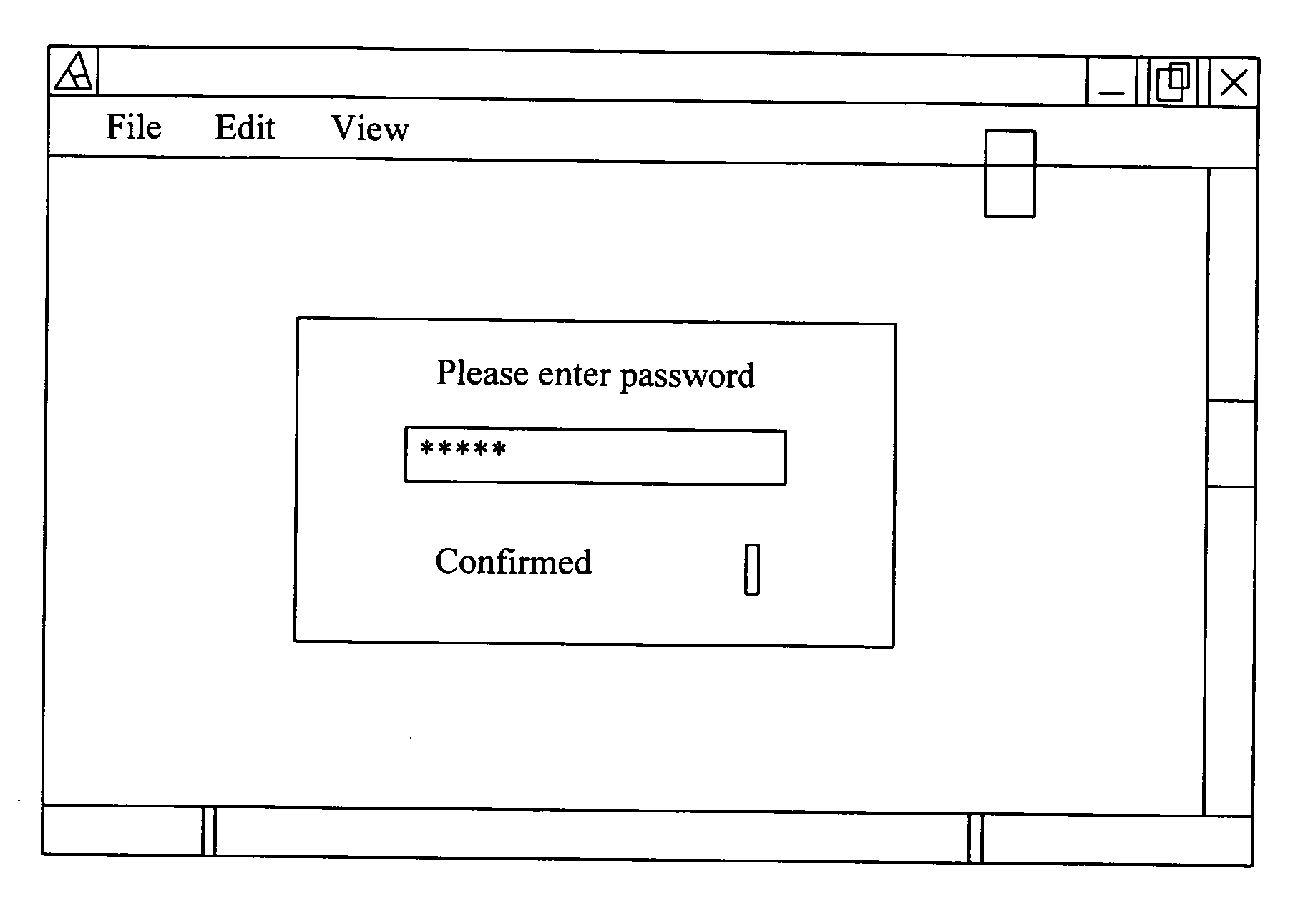
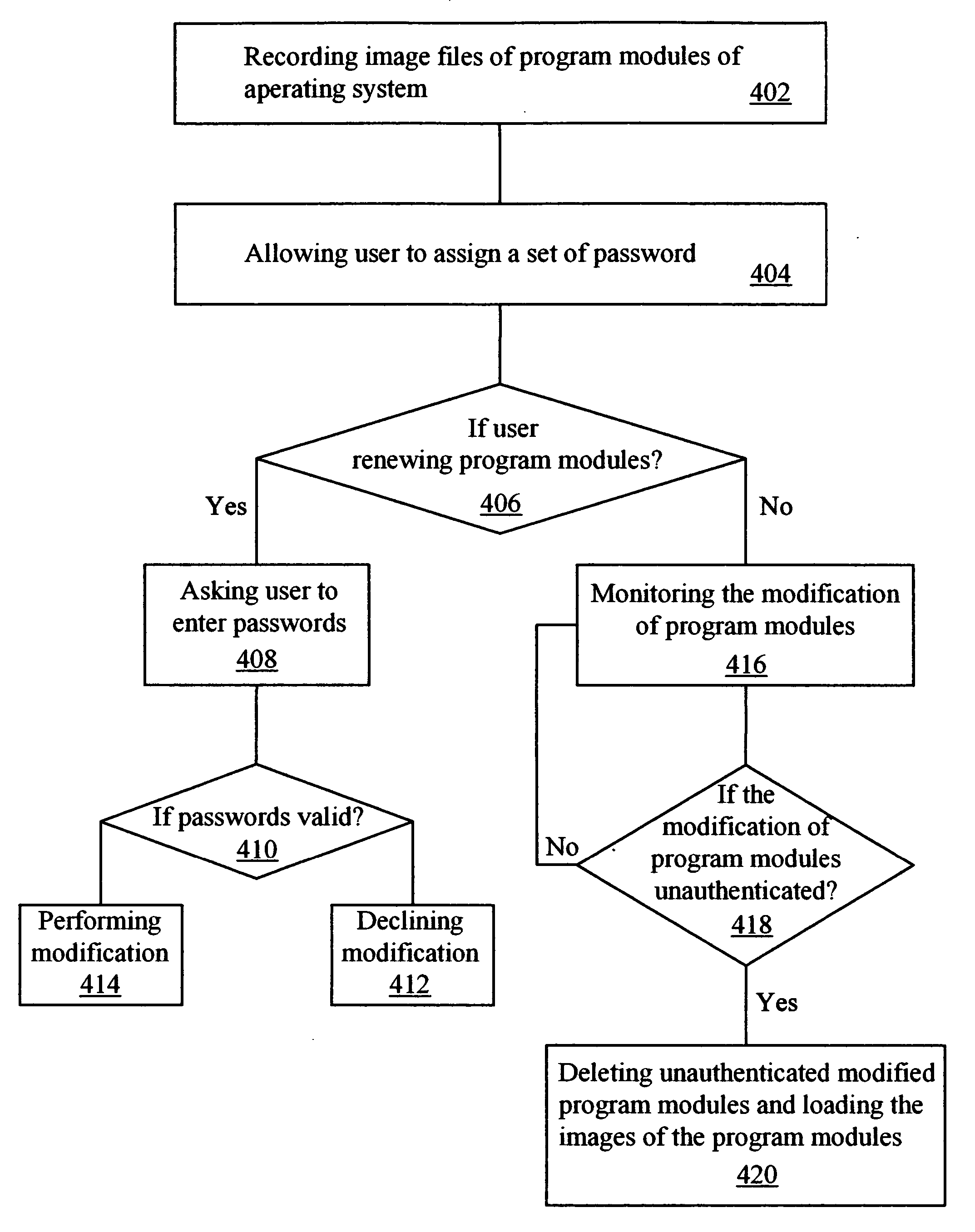
ActiveUS20060041757A1Accurately respondAvoid attackDigital data processing detailsUser identity/authority verificationOperational systemPassword
This computer data protection method of the present invention requires a user to enter a correct password for modifying any data. If wrong passwords are typed, this method forbids modification of any program modules. Further, if any program module is detected having unauthenticated modification, that program module is deleted and an original image of that program module is loaded to recover normal operation of the operation system. Additionally, a common password is also provided in the protection method. Some special function can use this common password to pass the detection of this method to perform any modification.
Owner:FANG KO CHENG
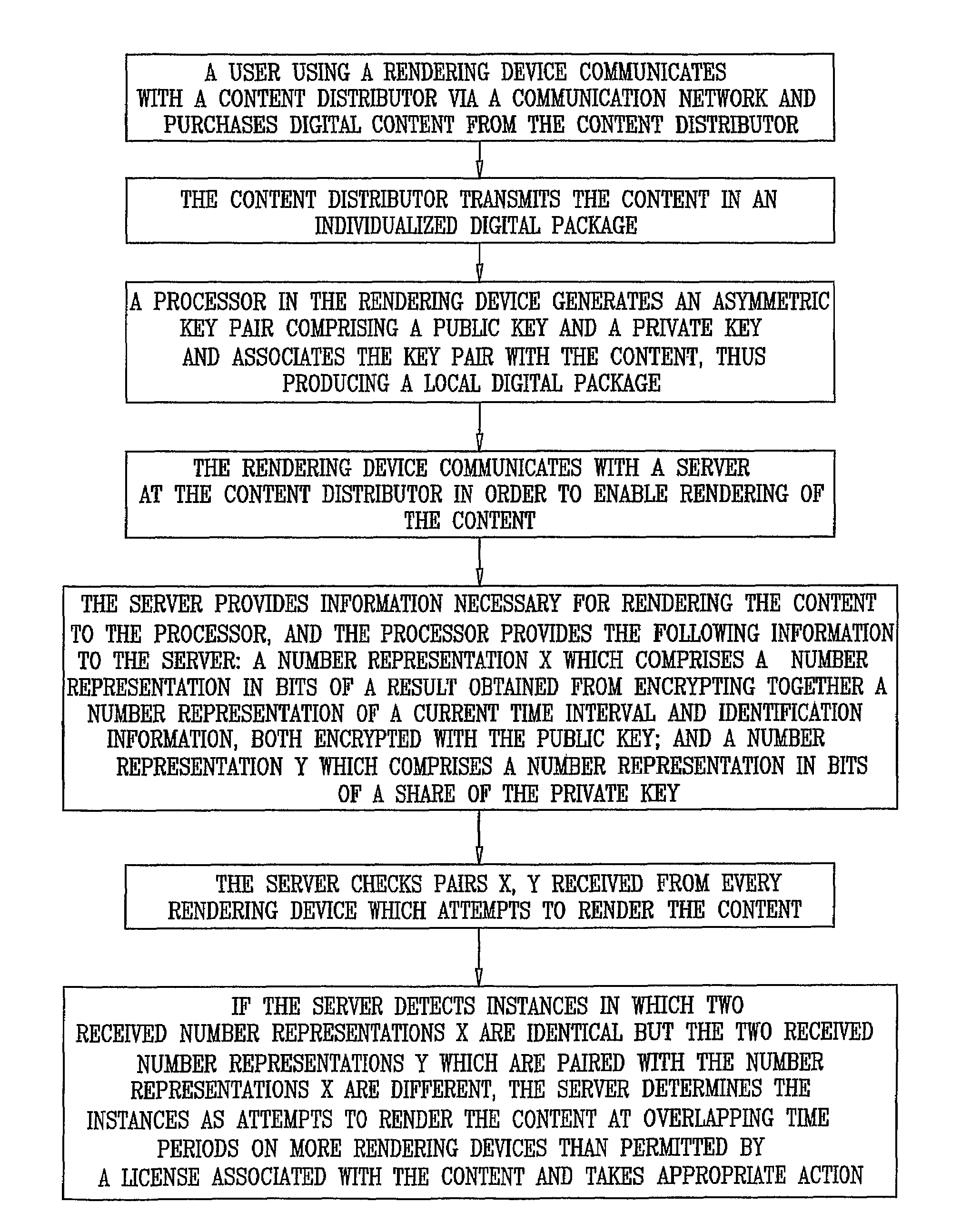
Privacy-aware content protection system
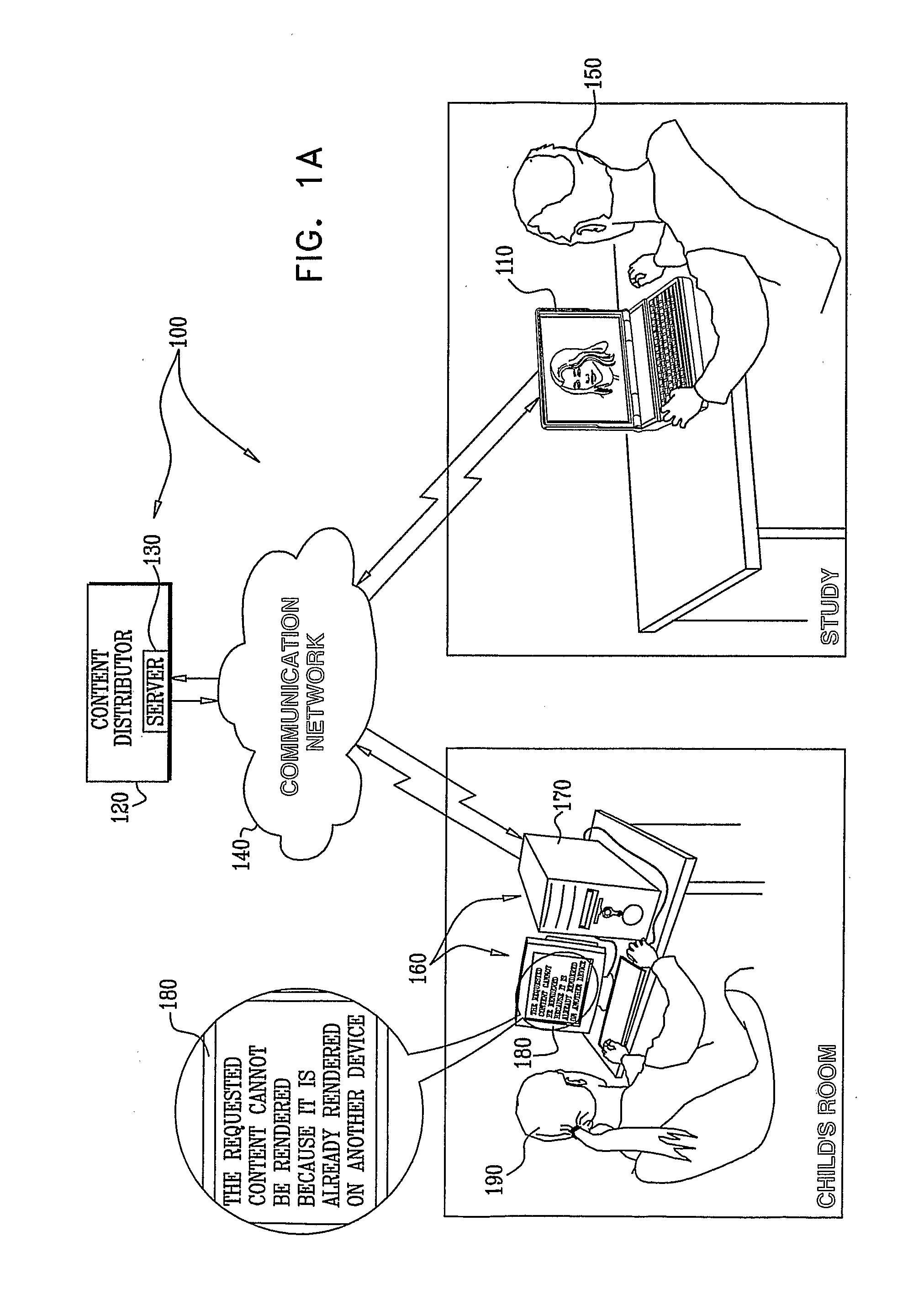
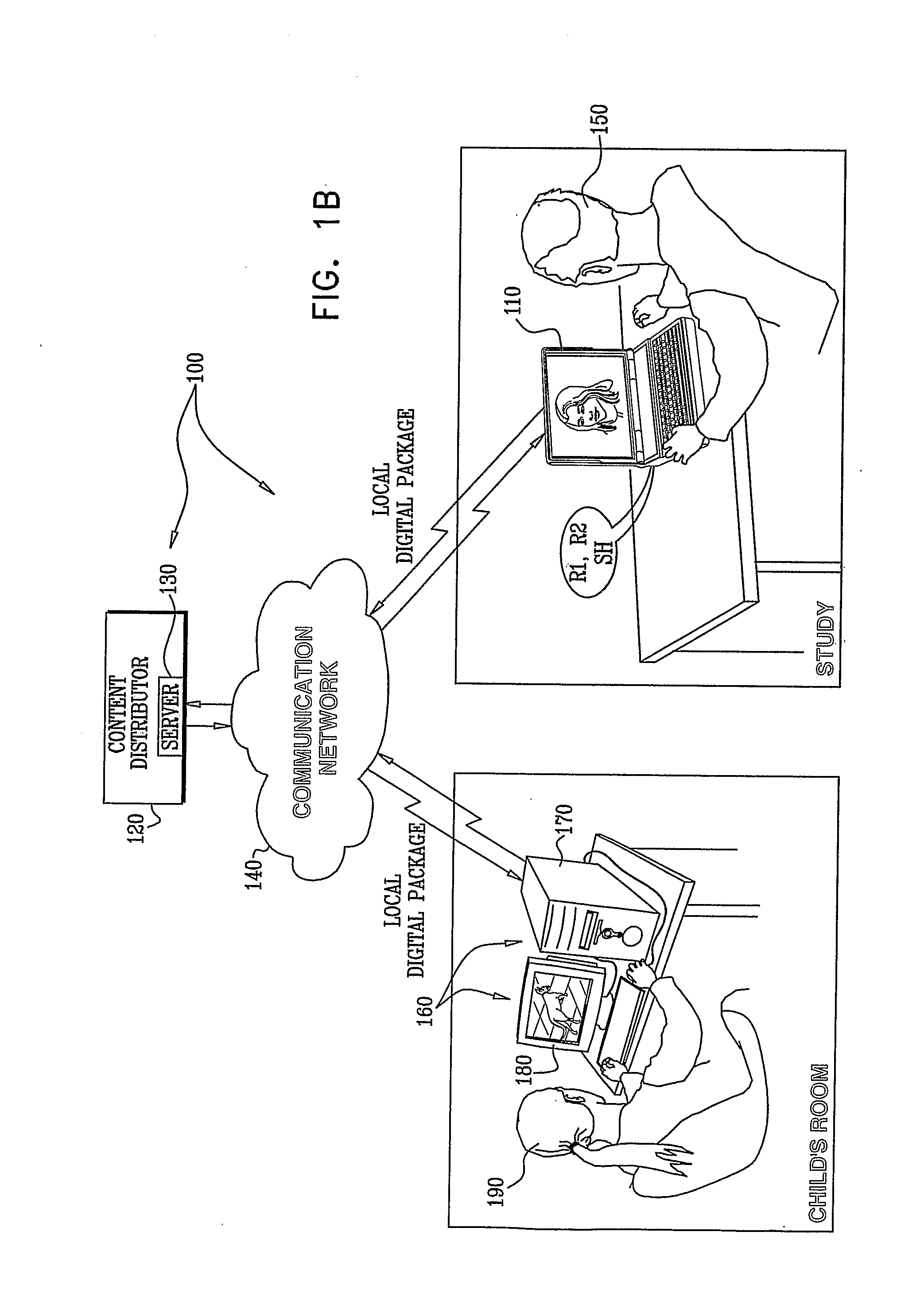
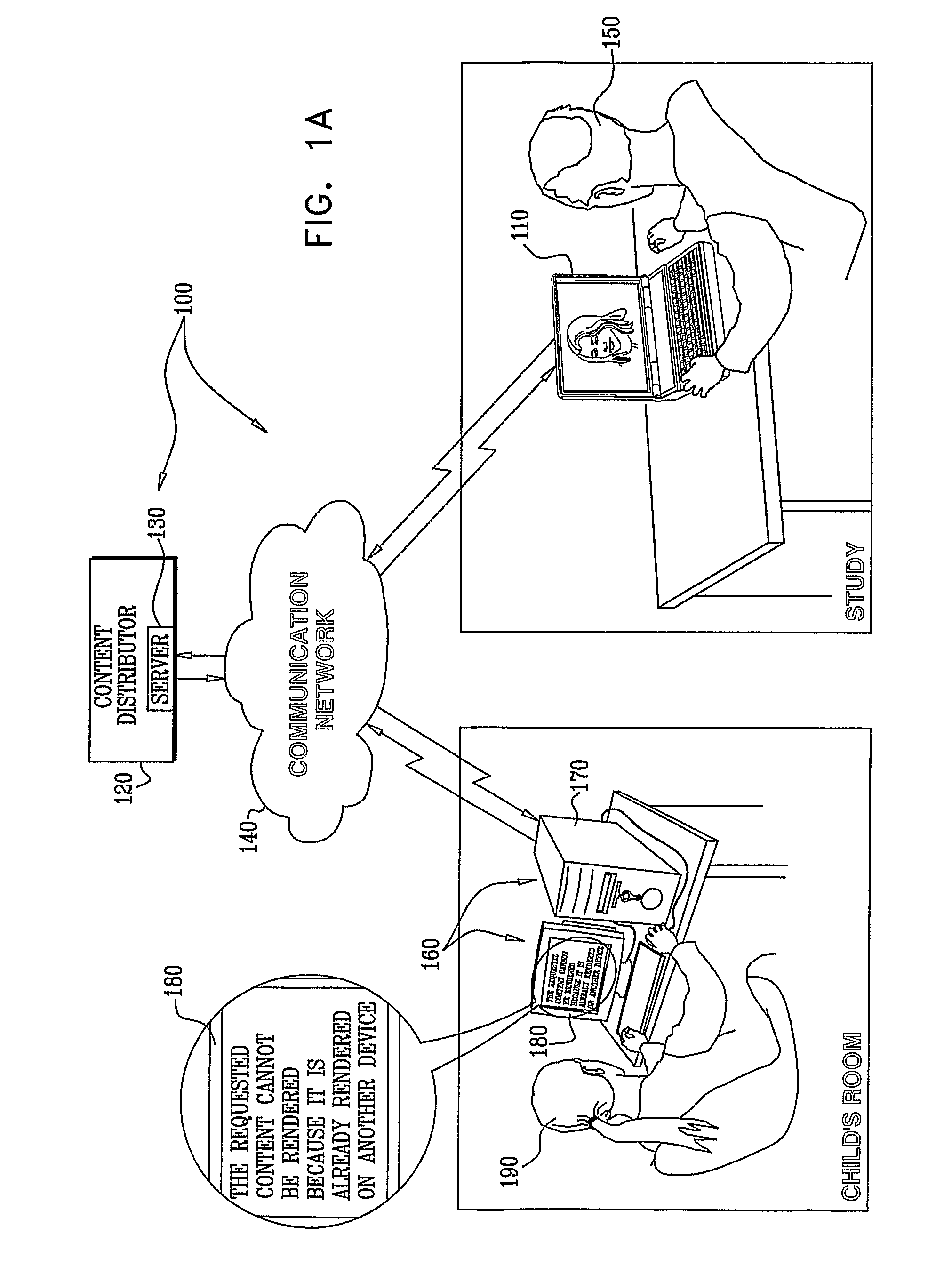
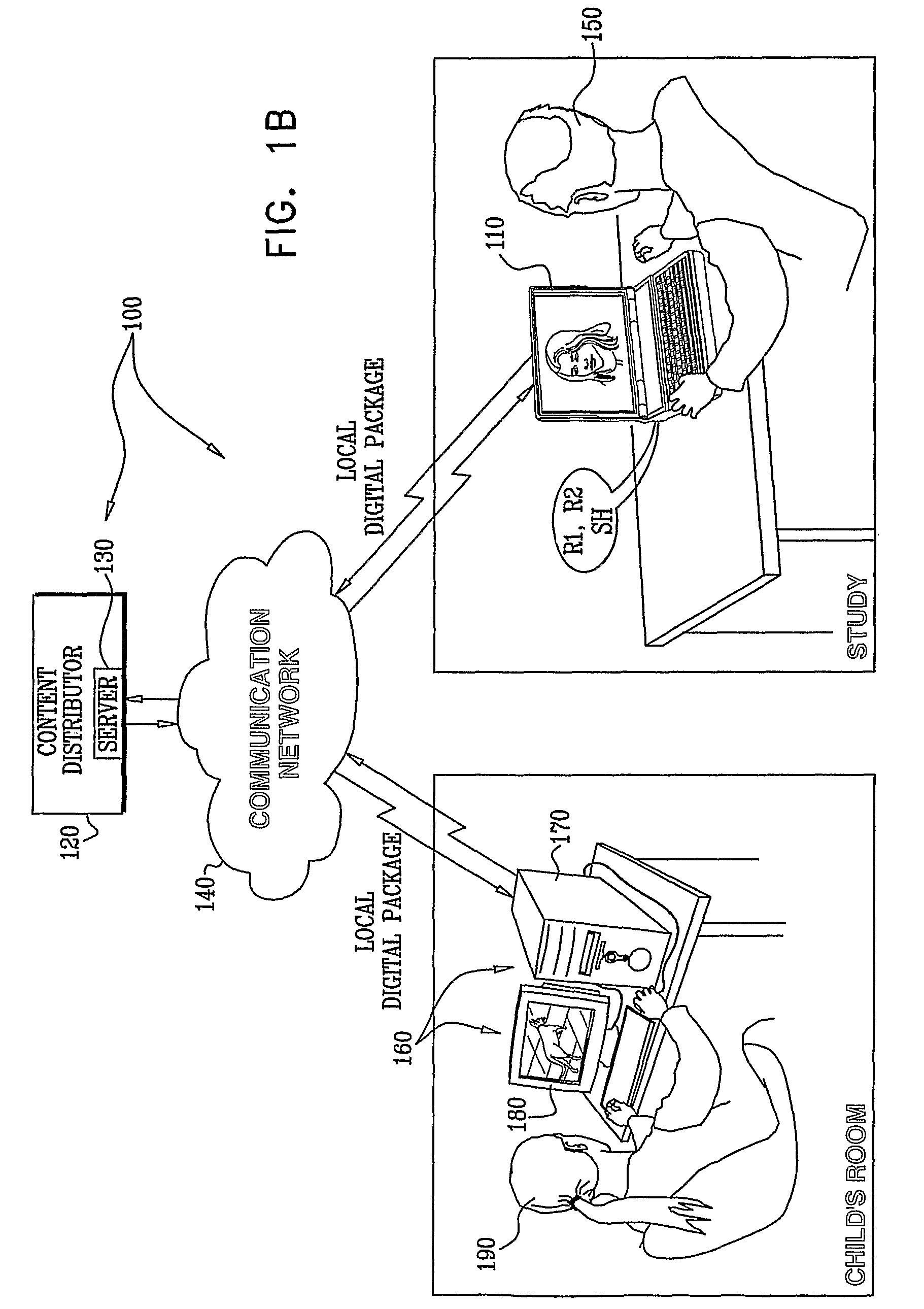
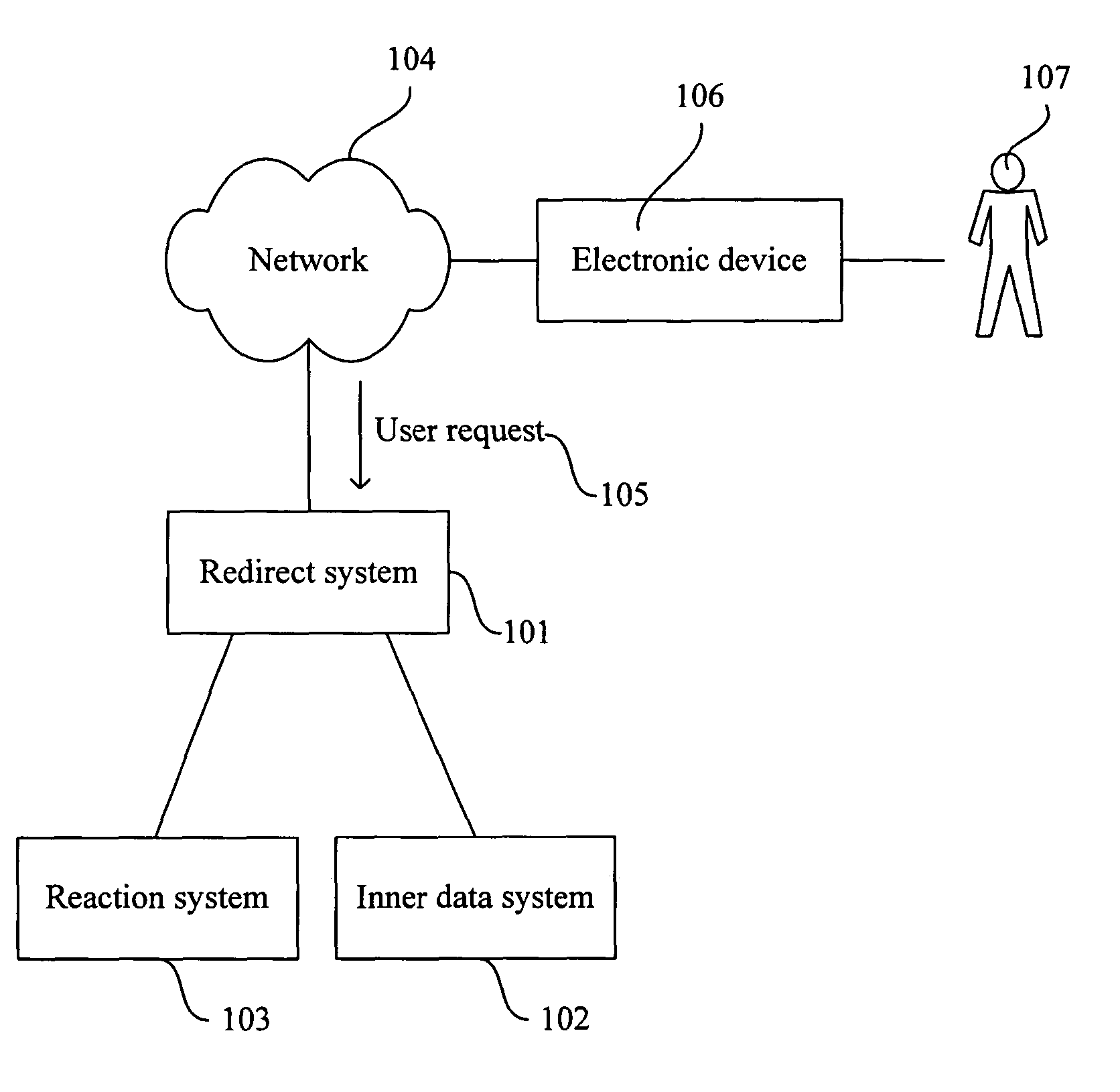
ActiveUS20090290713A1Preventing unauthorized rendering and useMaintaining anonymityDigital data processing detailsAnalogue secracy/subscription systemsComputer graphics (images)Protection system
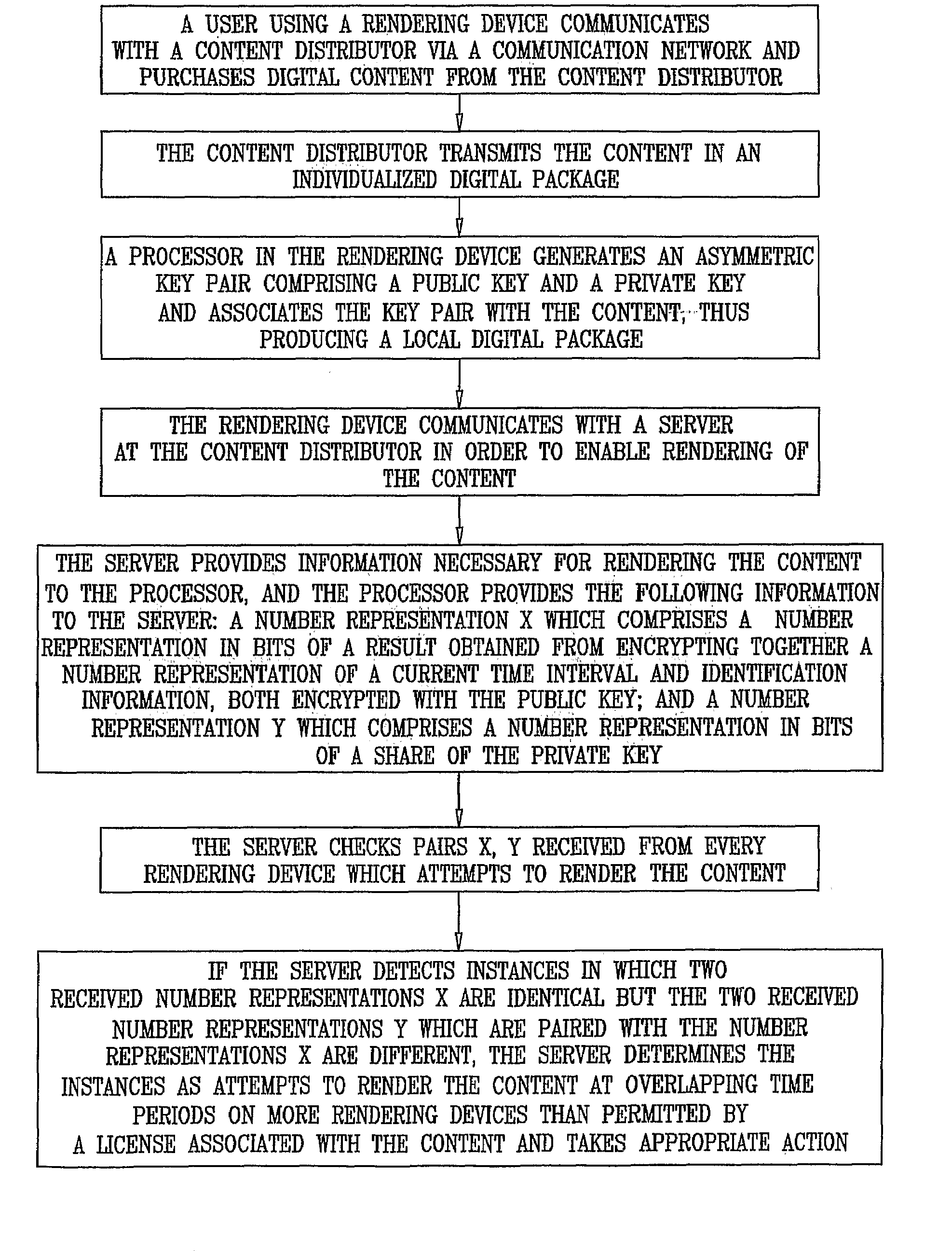
A method for preventing rendering of content at overlapping time periods on more rendering devices than permitted by a license associated with the content is disclosed. The method includes: transmitting the following to a rendering device of a user: the content, first software that is operative to receive the content and to associate keys with the content, identification information (ID) that is associated with the user, and second software that comprises a player for rendering the content, receiving the following information from the rendering device during rendering of the content: a number representation X which comprises a number representation in bits of a result obtained from encrypting together a number representation of a present time interval and the ID, both encrypted with a public key of a key pair generated at the rendering device, and a number representation which comprises a number representation in bits of a share (SH) of a private key of the key pair generated at the rendering device, and detecting an attempt to render the content at overlapping time periods on more rendering devices than permitted by the license associated with the content based on a determination that number representations X received from separate rendering devices are identical, and number representations Y received from the separate rendering devices and paired with the number representations X received from the separate rendering devices are different. Related apparatus and methods are also disclosed.
Owner:SYNAMEDIA LTD
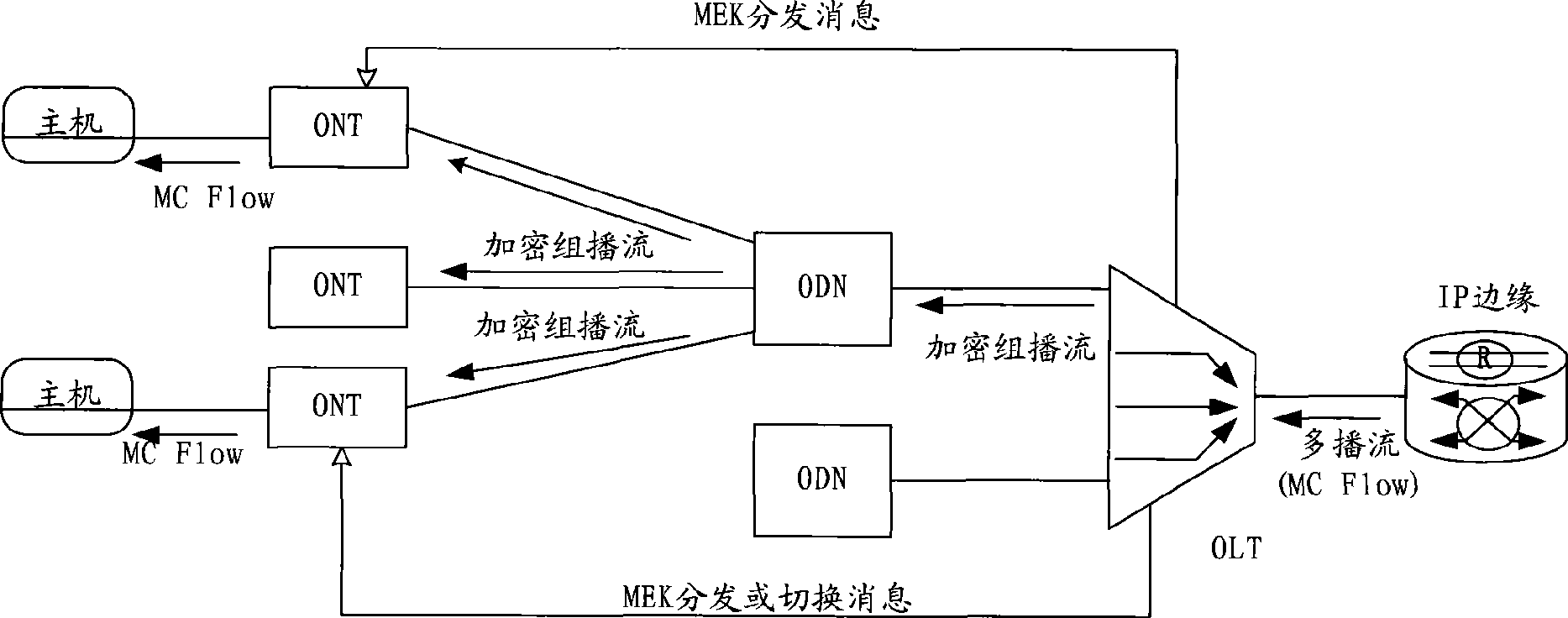
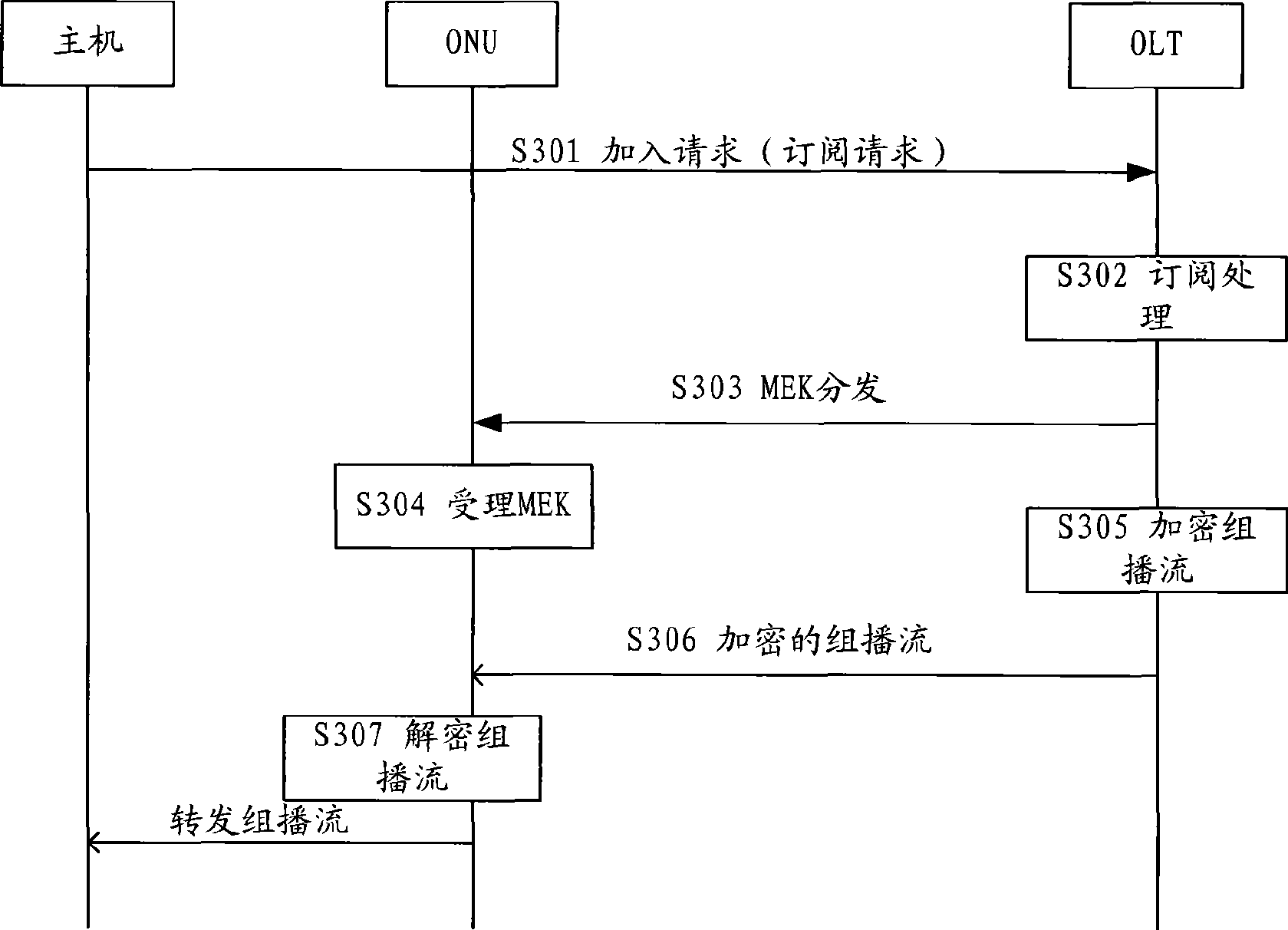
Method, system and device for broadband access network multicast control
InactiveCN101547086AInvestment protectionStrengthen multicast security controlSpecial service provision for substationSecuring communicationControl systemBroadband
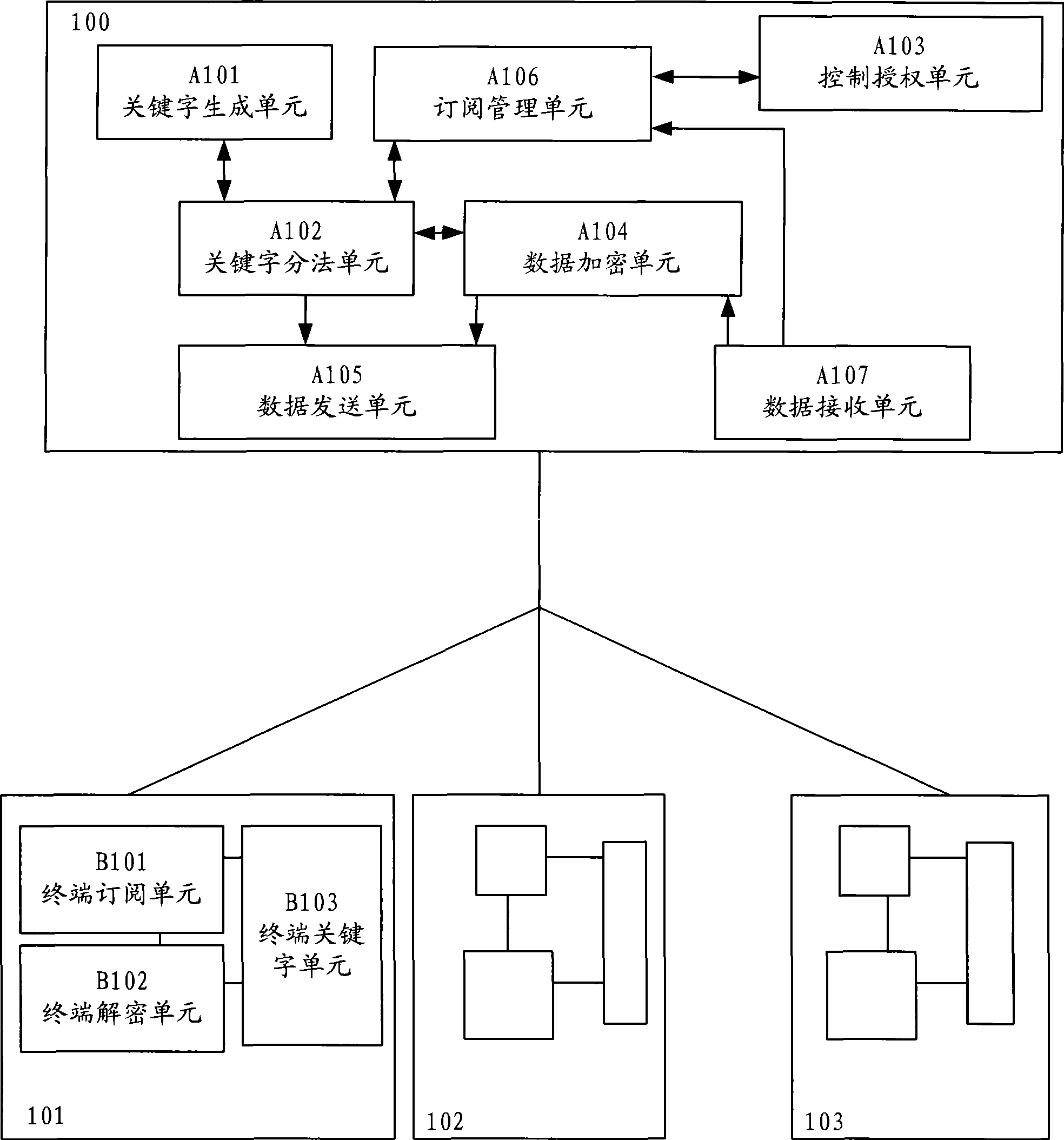
The embodiment of the invention discloses a system, a method and equipment for broadband access network multicast control. The system comprises an access control subsystem and a user subsystem, wherein the access control subsystem is used for generating multicast encryption keywords, sending the multicast encryption keywords to the user subsystem, encrypting multicast frames sent to the user subsystem through the multicast encryption keywords after receiving a subscription request sent by the user subsystem and sending the encrypted multicast frames to the user subsystem; and the user subsystem is used for sending the subscription request to the access control subsystem to request the multicast frames and decrypting the received multicast frames encrypted by the access control subsystem according to the received multicast encryption keywords sent by the access control subsystem. In radio type (shared media) access applications, only authorized users of the invention can use multicast service data to prevent illegal users from using the multicast services, and improve the security of multicast authority control.
Owner:HUAWEI TECH CO LTD
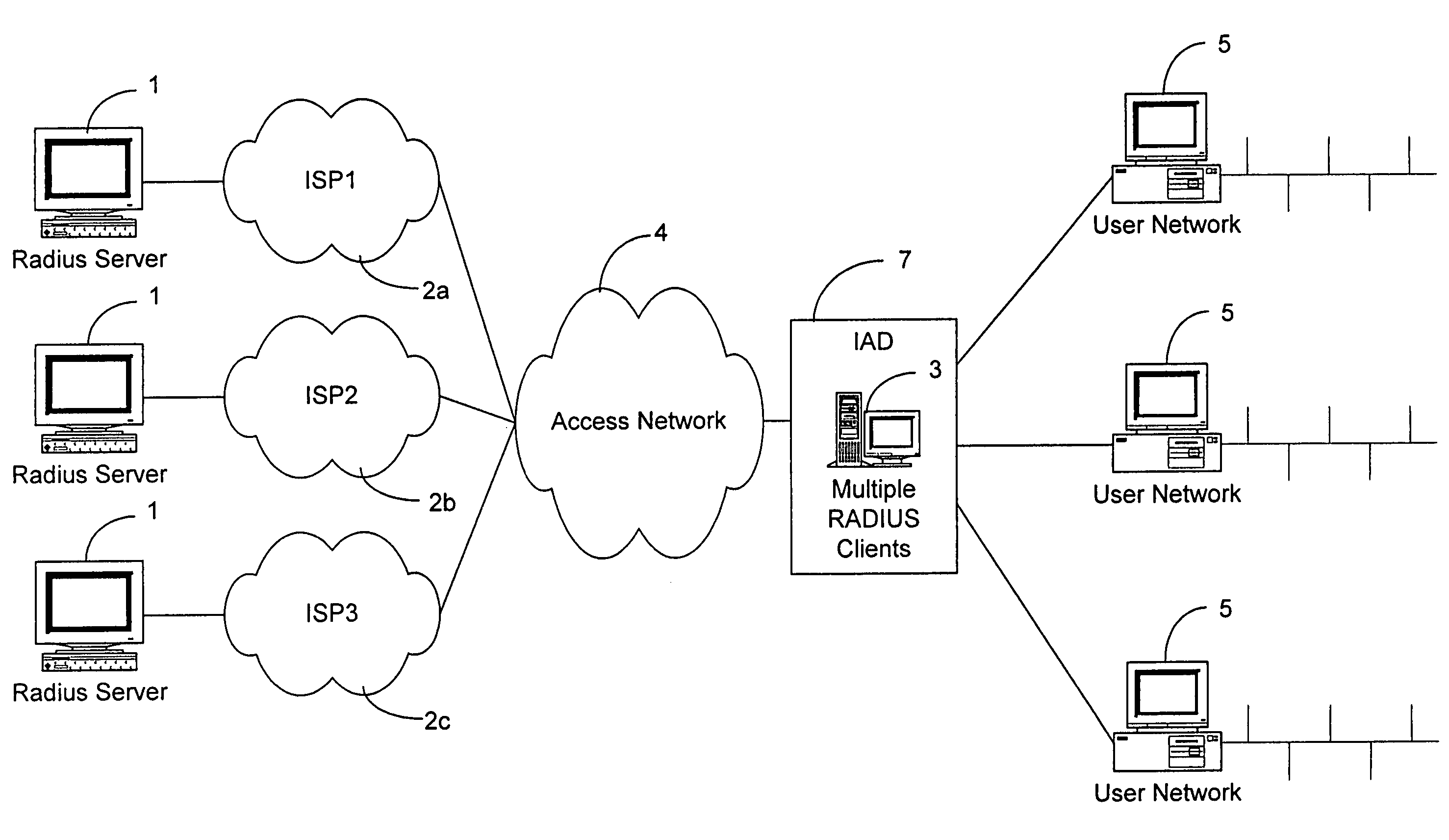
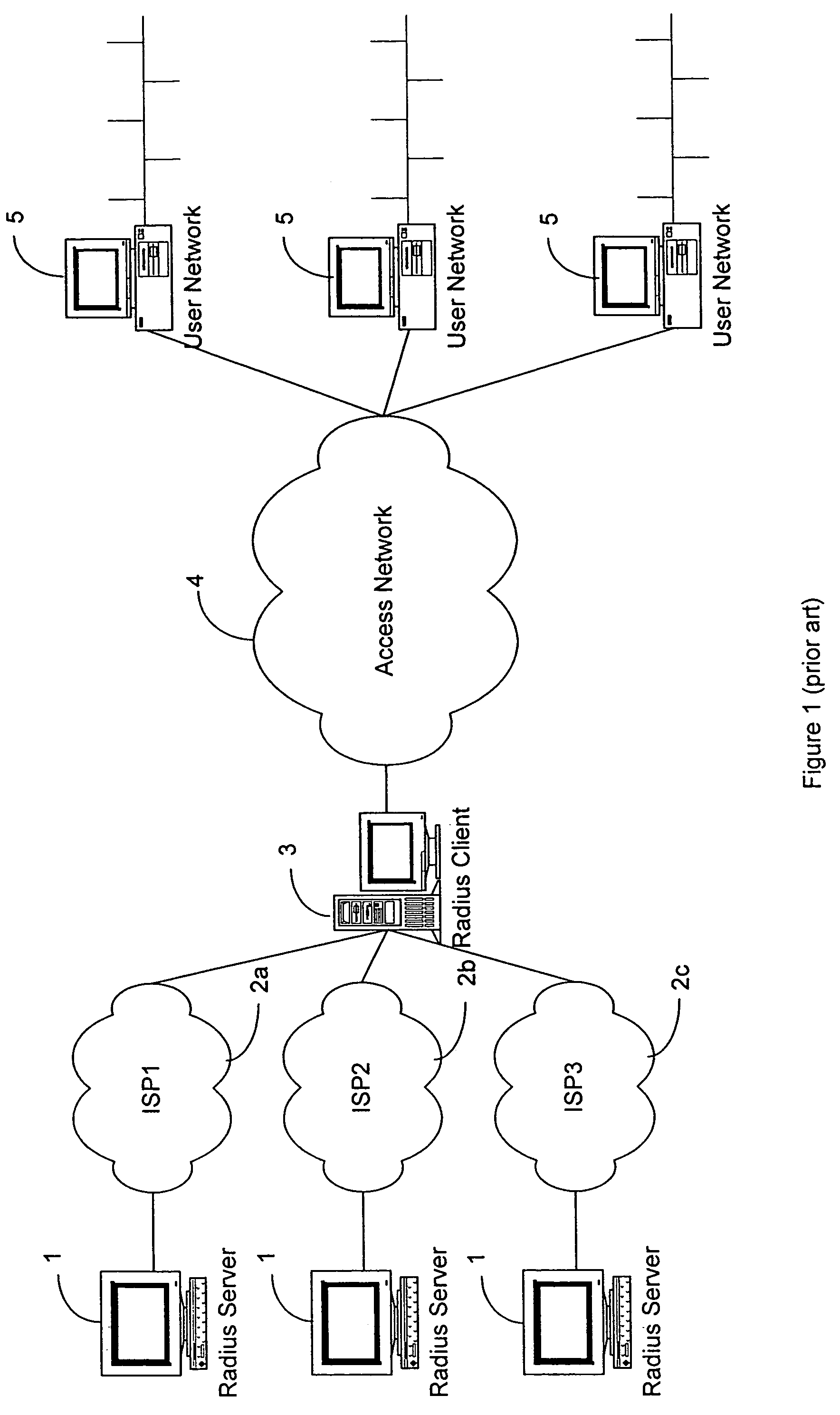
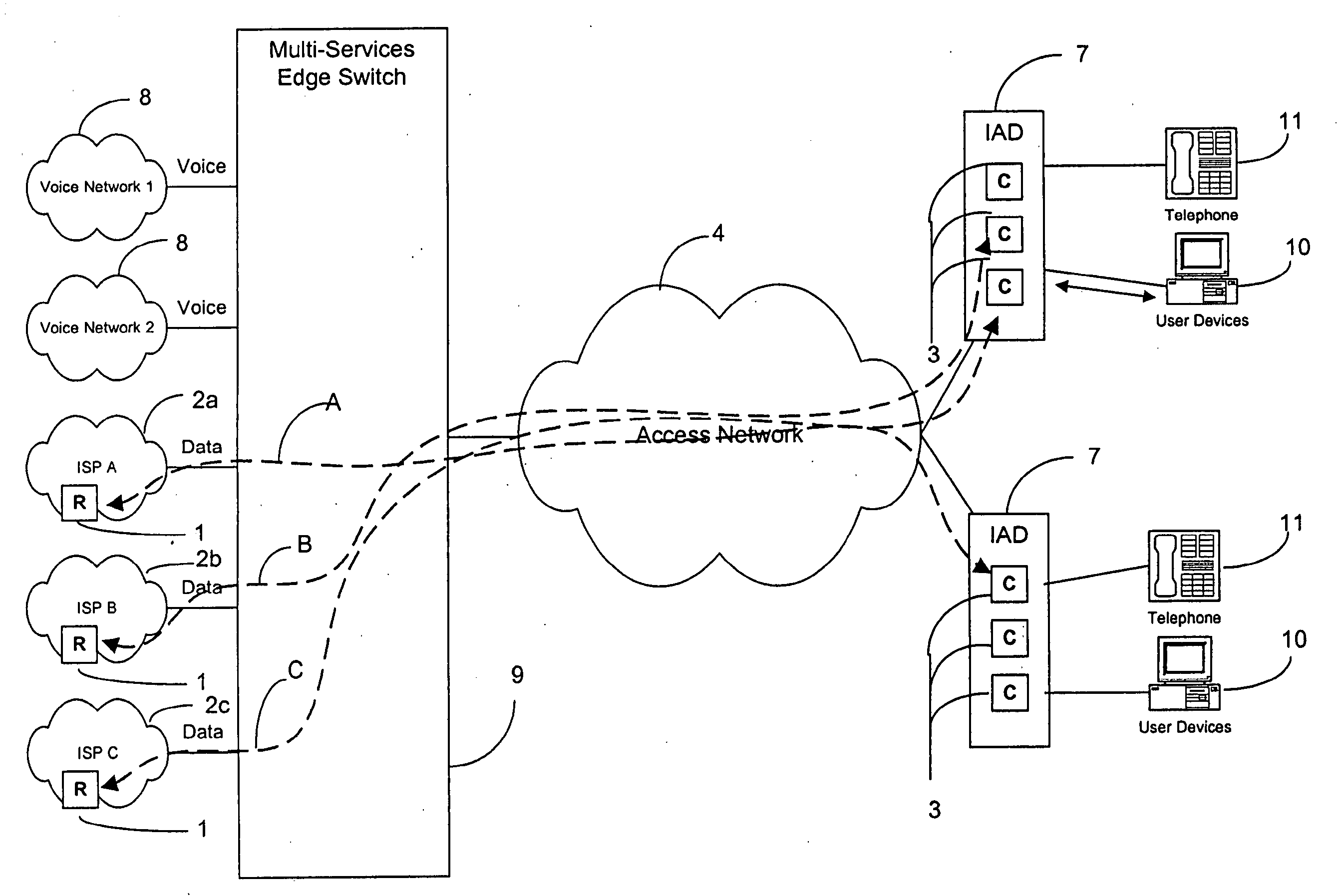
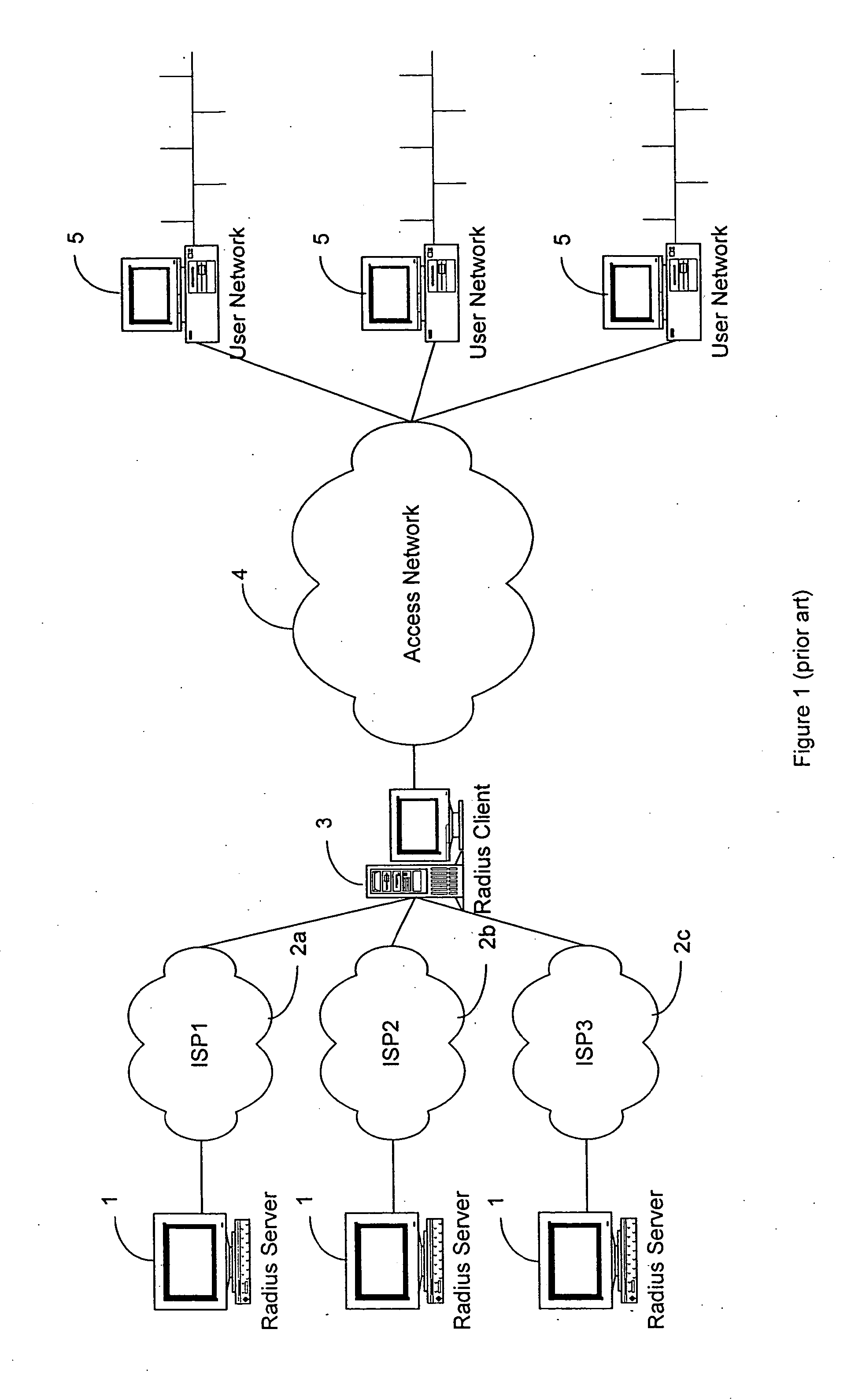
Distributed subscriber management system
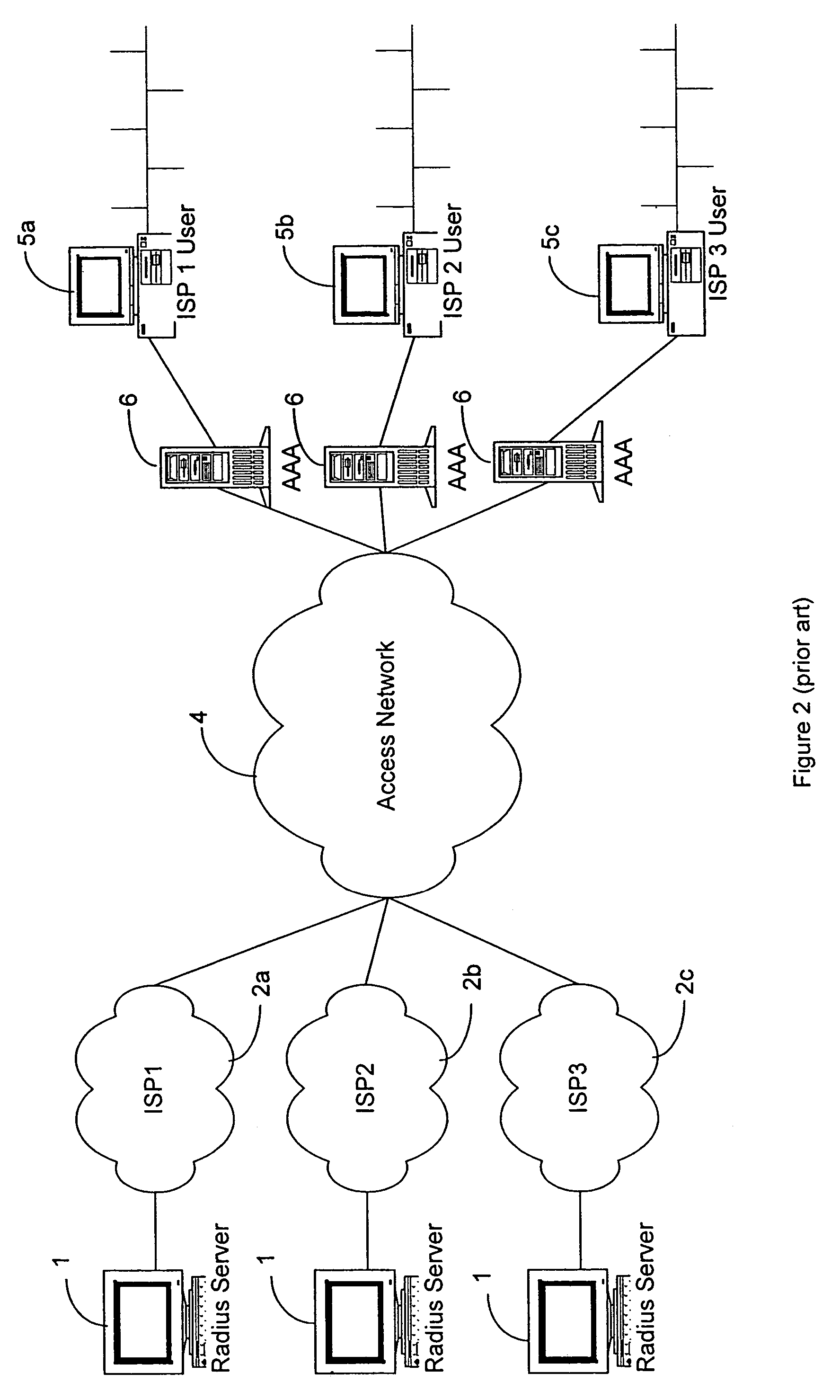
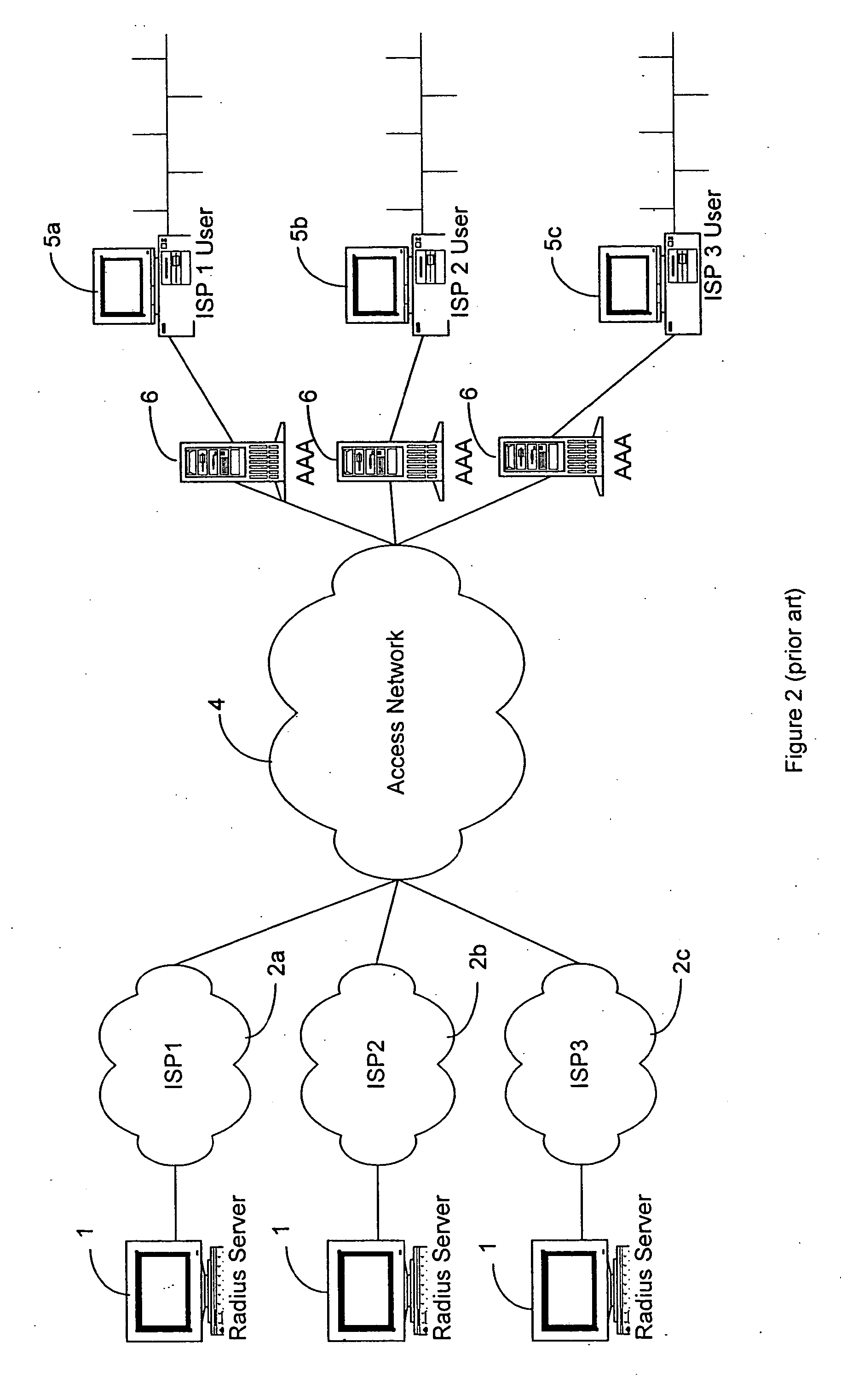
InactiveUS7512784B2Prevent unauthorizedAllow userRandom number generatorsCharacter and pattern recognitionRadio access networkUser authentication
A distributed subscriber management system and method that controls access to a network preventing unauthorized traffic through the access network and providing centralized access control between user networks. The system and method provide controlled access through the use of one of several technologies including user authentication, using PAP, CHAP, RADIUS, TACACS+, or other standard authentication means. The method includes the steps of receiving a connection request from a user located on one of the User Networks; interrogating the user for userid and password information; encrypting the userid and password information; transmitting the encrypted information, via the access network, to an authentication server attached to one of a plurality of external networks; decrypting the information at the authentication server; and transmitting an authentication message from the authentication server of the external network to the access control node via the access network. The preferred method includes the additional step of challenging all data leaving the access control node.
Owner:ALCATEL LUCENT CANADA +1
Computer data protecting method
InactiveUS20060041940A1Accurately respondAvoid attackMemory loss protectionError detection/correctionOperational systemUser input
This computer data protection method of the present invention requires a user to enter a correct password for modifying any data. If wrong passwords are typed, this method forbids modification of any program modules. Further, if any program module is detected having unauthenticated modification, that program module is deleted and an original image of that program module is loaded to recover normal operation of the operation system. Additionally, a common password is also provided in the protection method. Some special function can use this common password to pass the detection of this method to perform any modification.
Owner:FANG KO CHENG
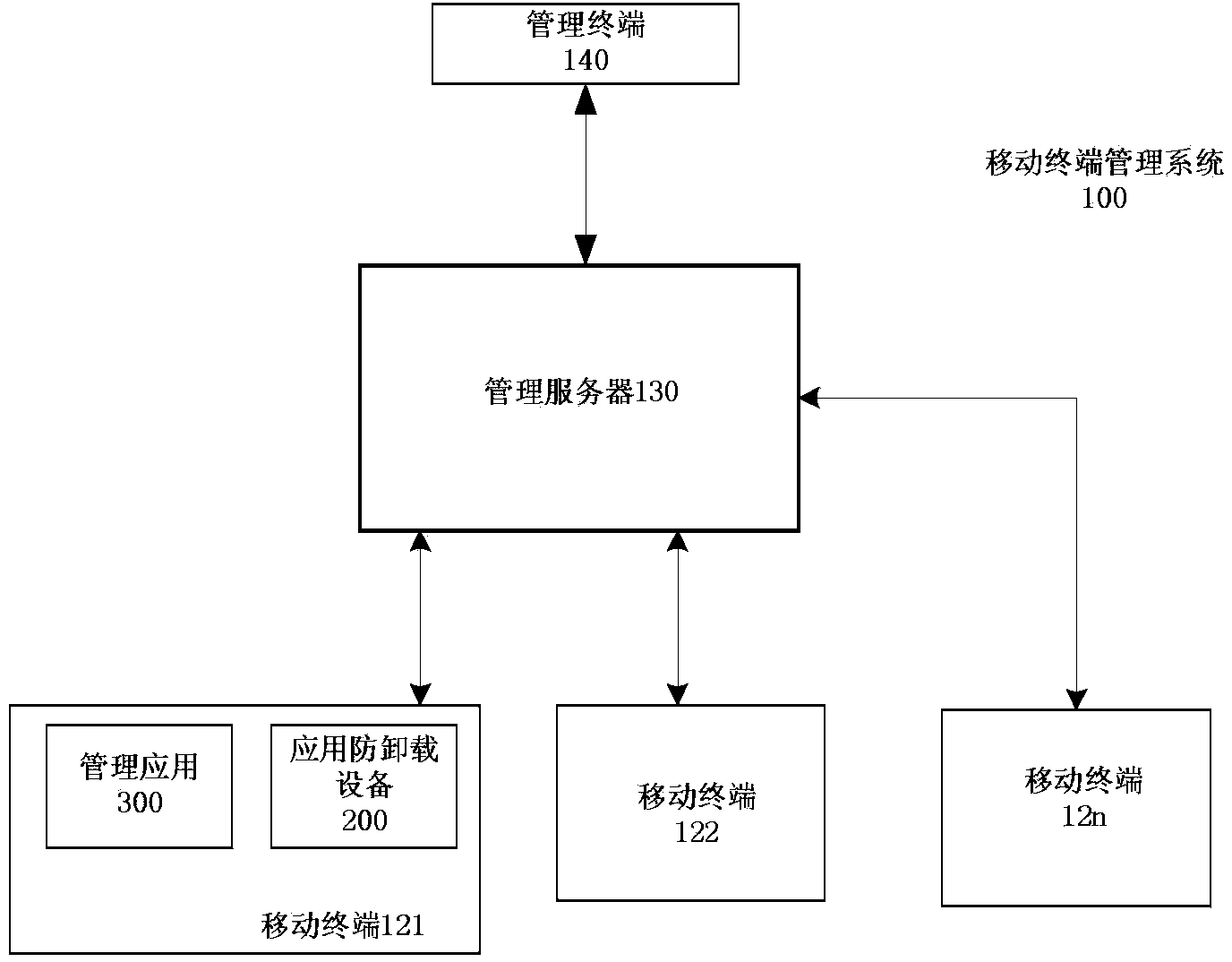
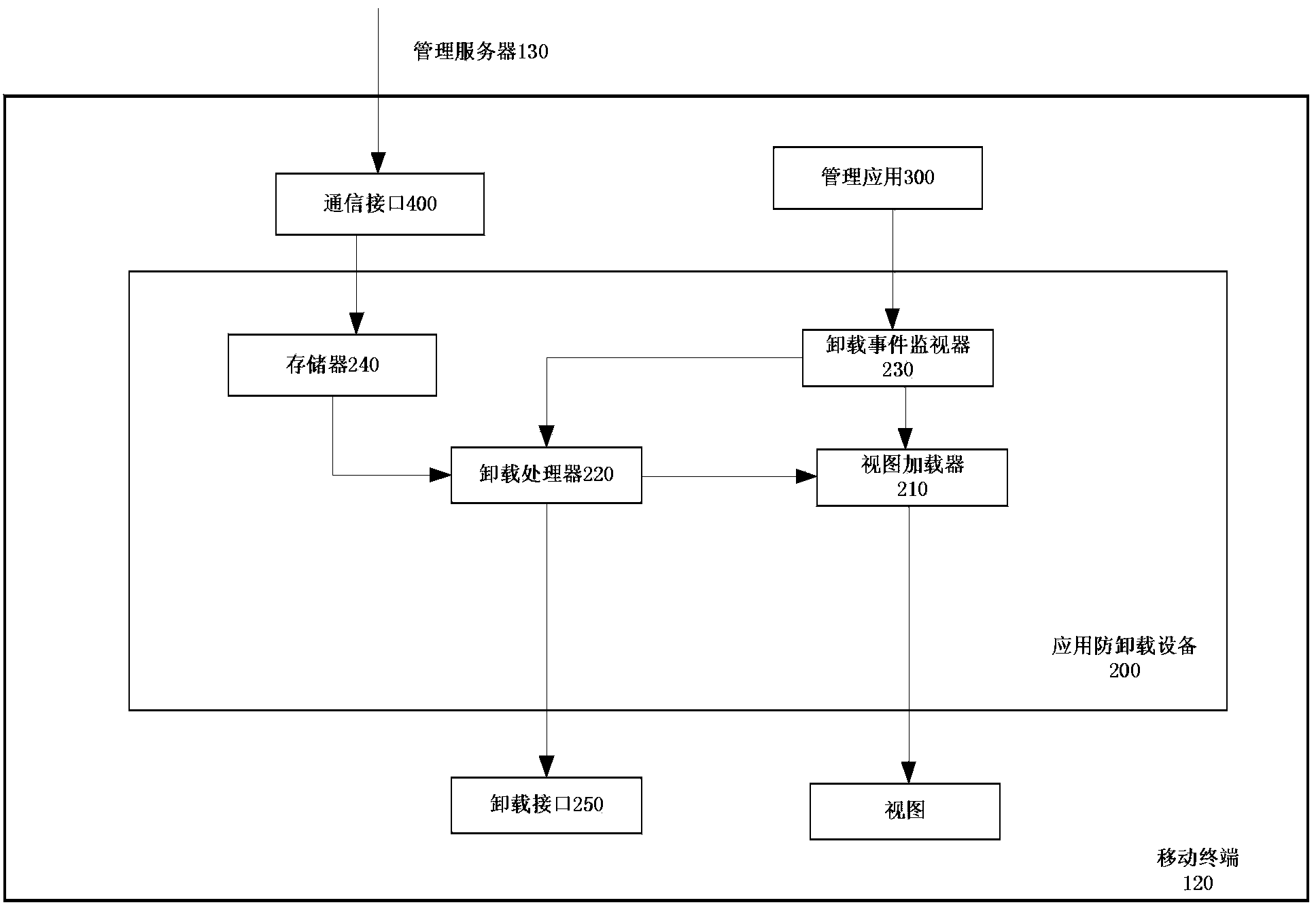
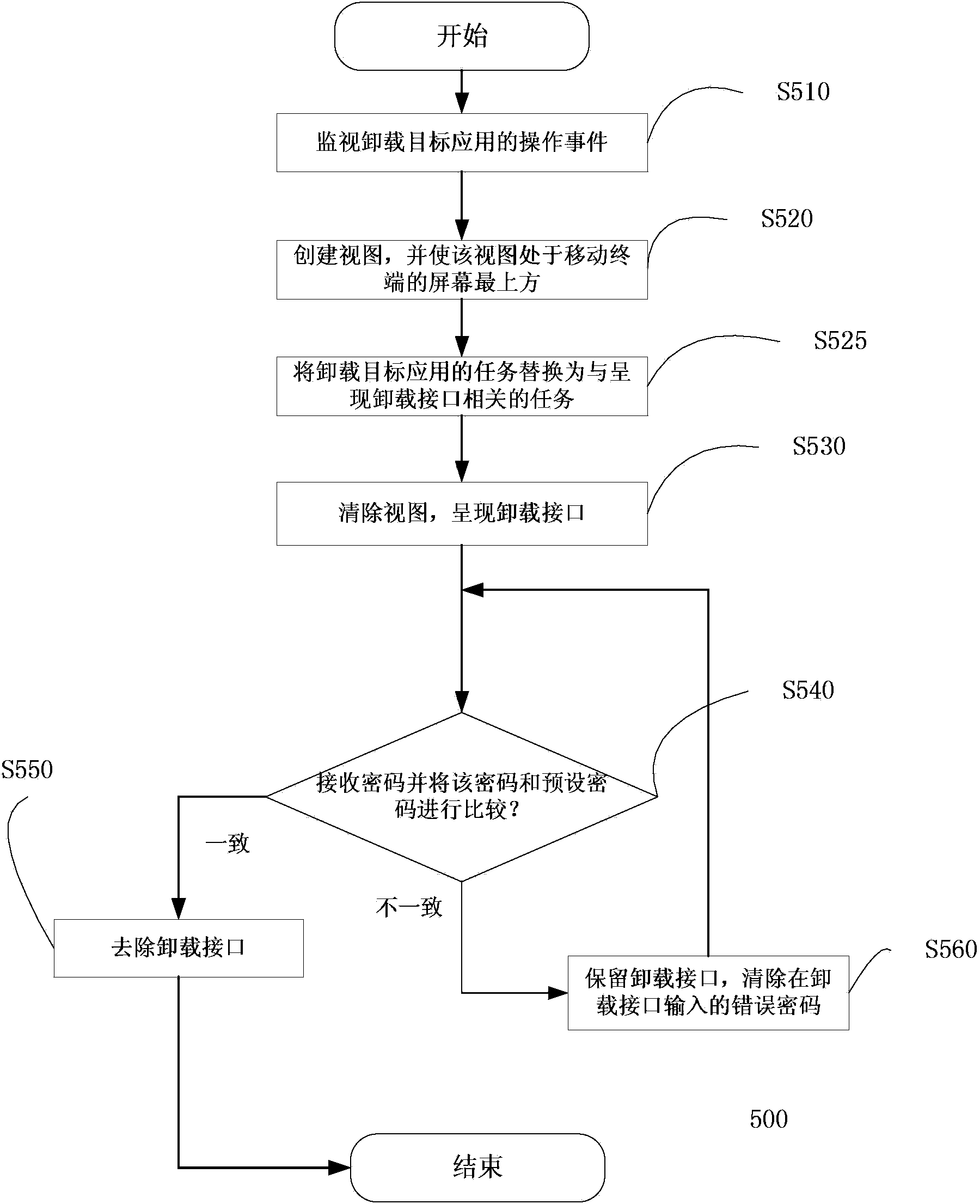
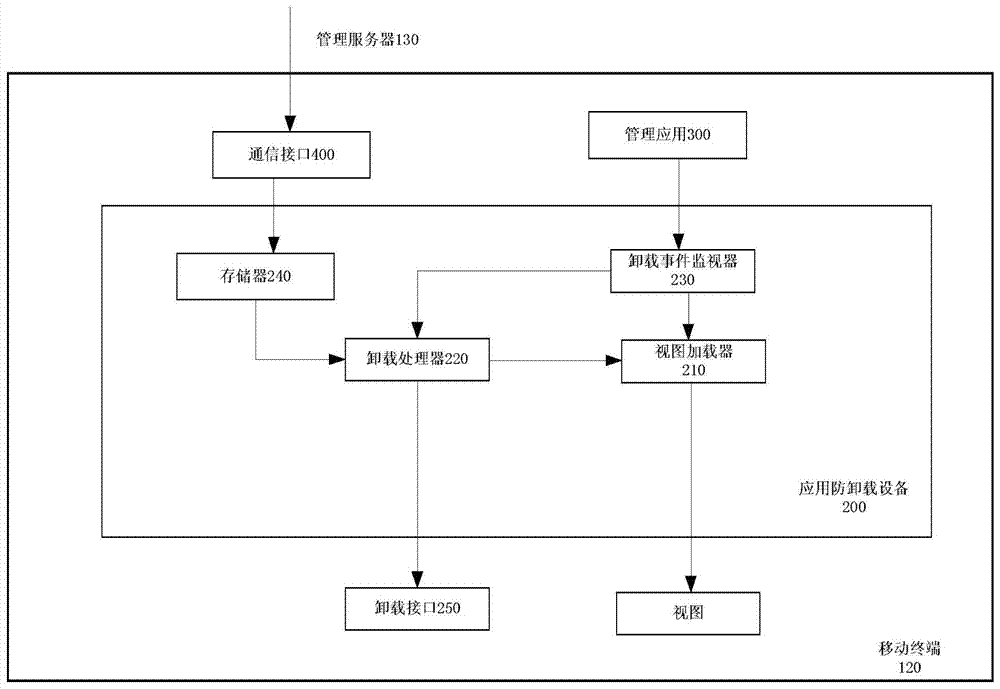
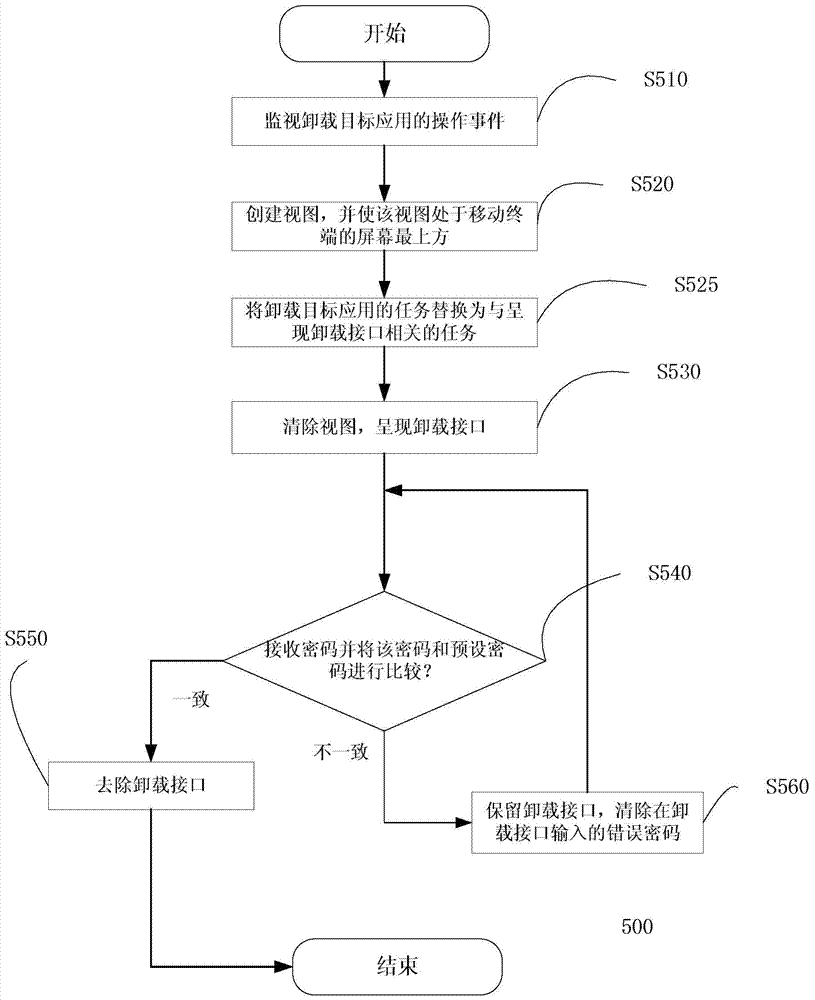
Application uninstall preventing method and equipment
The invention discloses application uninstall preventing equipment which is resident in a mobile terminal to prevent a target application from being uninstalled from the mobile terminal. The application uninstall equipment comprises a view loader, an uninstall processor and an uninstall event monitor, wherein the view loader is suitable for creating a view and enabling the view to be located at the uppermost portion of a screen of the mobile terminal, the uninstall processor is used for removing the view, presenting an uninstall interface for receiving password input on the screen of the mobile terminal and removing the uninstall interface and enabling the uninstall operation of the target application to go on when a received password is matched with a preset password, and the uninstall event monitor is suitable for monitoring operating events of uninstalling the target application and indicating the view loader to create the view and then activating the uninstall processor later when the operation of uninstalling the target application is monitored. The invention further discloses a corresponding application uninstall preventing method and the mobile terminal including the application uninstall preventing equipment.
Owner:北京宝利明威软件股份有限公司
Privacy-aware content protection system
ActiveUS8239957B2Prevent unauthorizedPrevention of unauthorized renderingDigital data processing detailsAnalogue secracy/subscription systemsComputer graphics (images)Protection system
A method for preventing rendering of content at overlapping time periods on more rendering devices than permitted by a license associated with the content is disclosed. The method includes: transmitting the following to a rendering device of a user: the content, first software that is operative to receive the content and to associate keys with the content, identification information (ID) that is associated with the user, and second software that comprises a player for rendering the content, receiving the following information from the rendering device during rendering of the content: a number representation X which comprises a number representation in bits of a result obtained from encrypting together a number representation of a present time interval and the ID, both encrypted with a public key of a key pair generated at the rendering device, and a number representation which comprises a number representation in bits of a share (SH) of a private key of the key pair generated at the rendering device, and detecting an attempt to render the content at overlapping time periods on more rendering devices than permitted by the license associated with the content based on a determination that number representations X received from separate rendering devices are identical, and number representations Y received from the separate rendering devices and paired with the number representations X received from the separate rendering devices are different. Related apparatus and methods are also disclosed.
Owner:SYNAMEDIA LTD
Distributed subscriber management system
InactiveUS20090319777A1Prevent unauthorizedAllow userUser identity/authority verificationMultiple digital computer combinationsRadio access networkUser authentication
A distributed subscriber management system and method that controls access to a network preventing unauthorized traffic through the access network and providing centralized access control between user networks are disclosed. The controlled access is provided through the use of one of several technologies including user authentication, using PAP, CHAP, RADIUS, TACACS+. The method includes the steps of receiving a connection request from a user located on one of the User Networks; interrogating the user for userid and password information; encrypting the userid and password information; transmitting the encrypted information, via the access network, to an authentication server attached to one of a plurality of external networks; decrypting the information at the authentication server; and transmitting an authentication message from the authentication server of the external network to the access control node via the access network. Additionally, the method includes the step of challenging all data leaving the access control node.
Owner:WSOU INVESTMENTS LLC
Computer data protecting method
InactiveUS8060933B2Accurately respondAvoid attackMemory loss protectionDigital data processing detailsPasswordComputer module
Owner:FANG KO CHENG
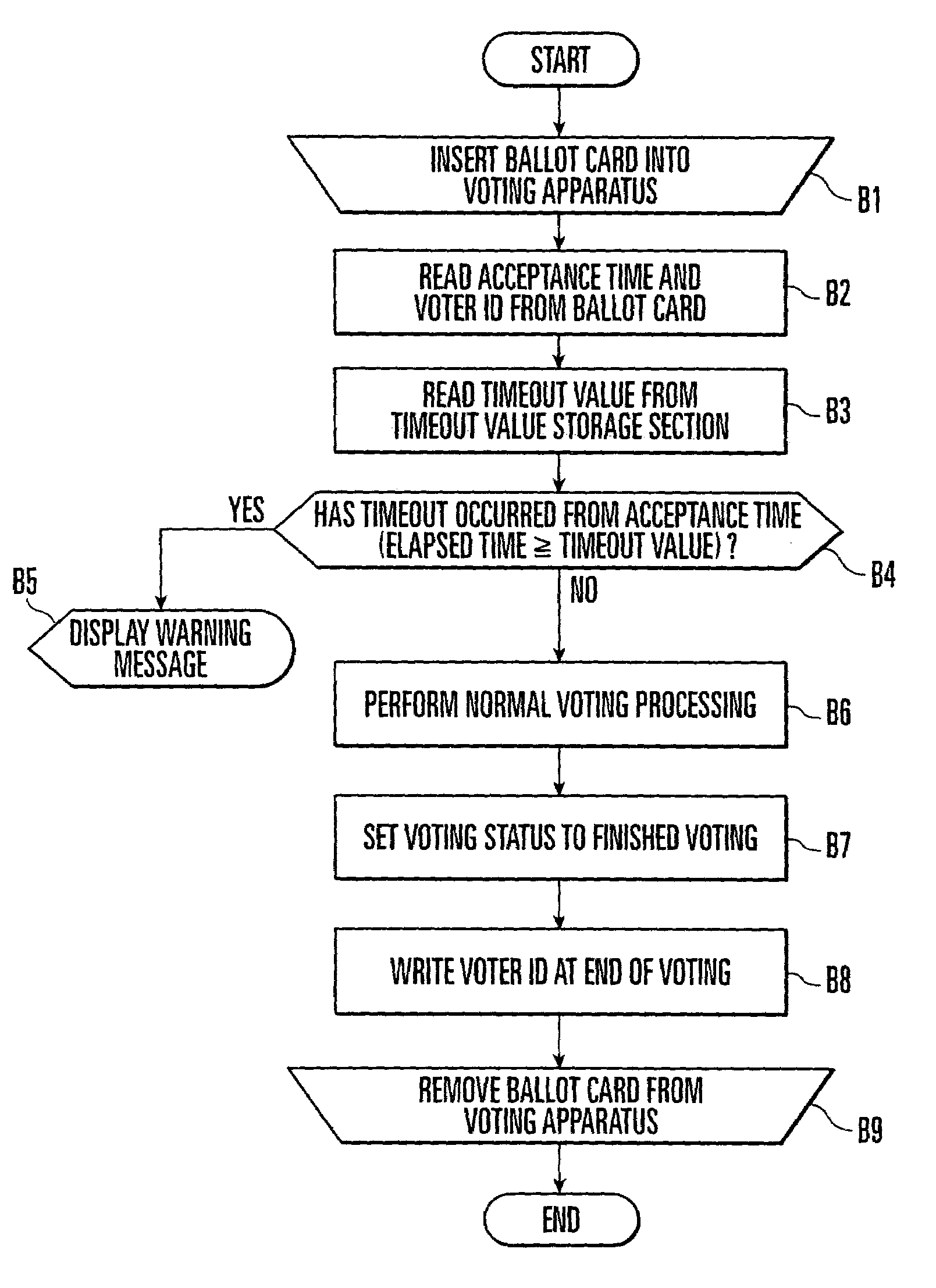
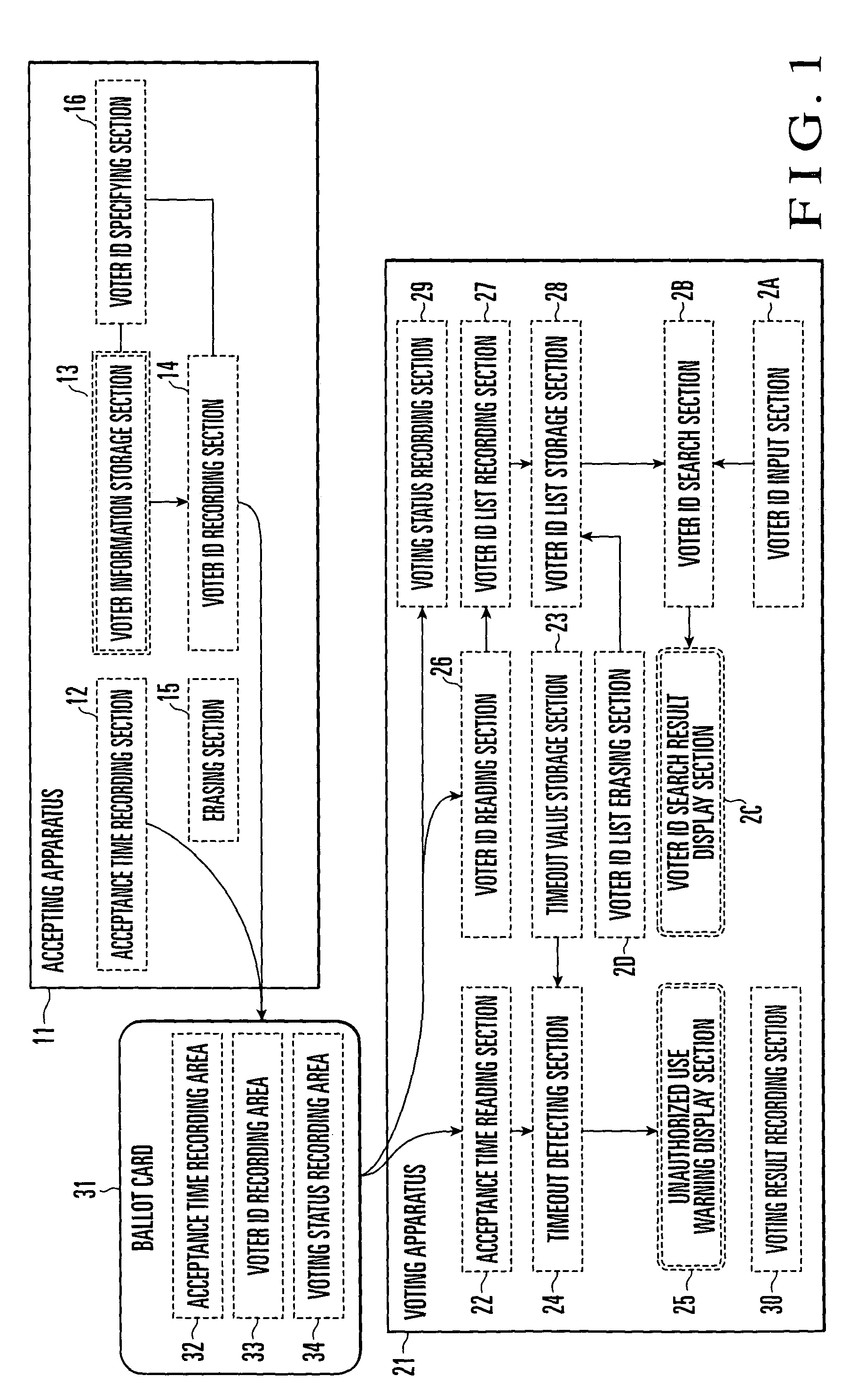
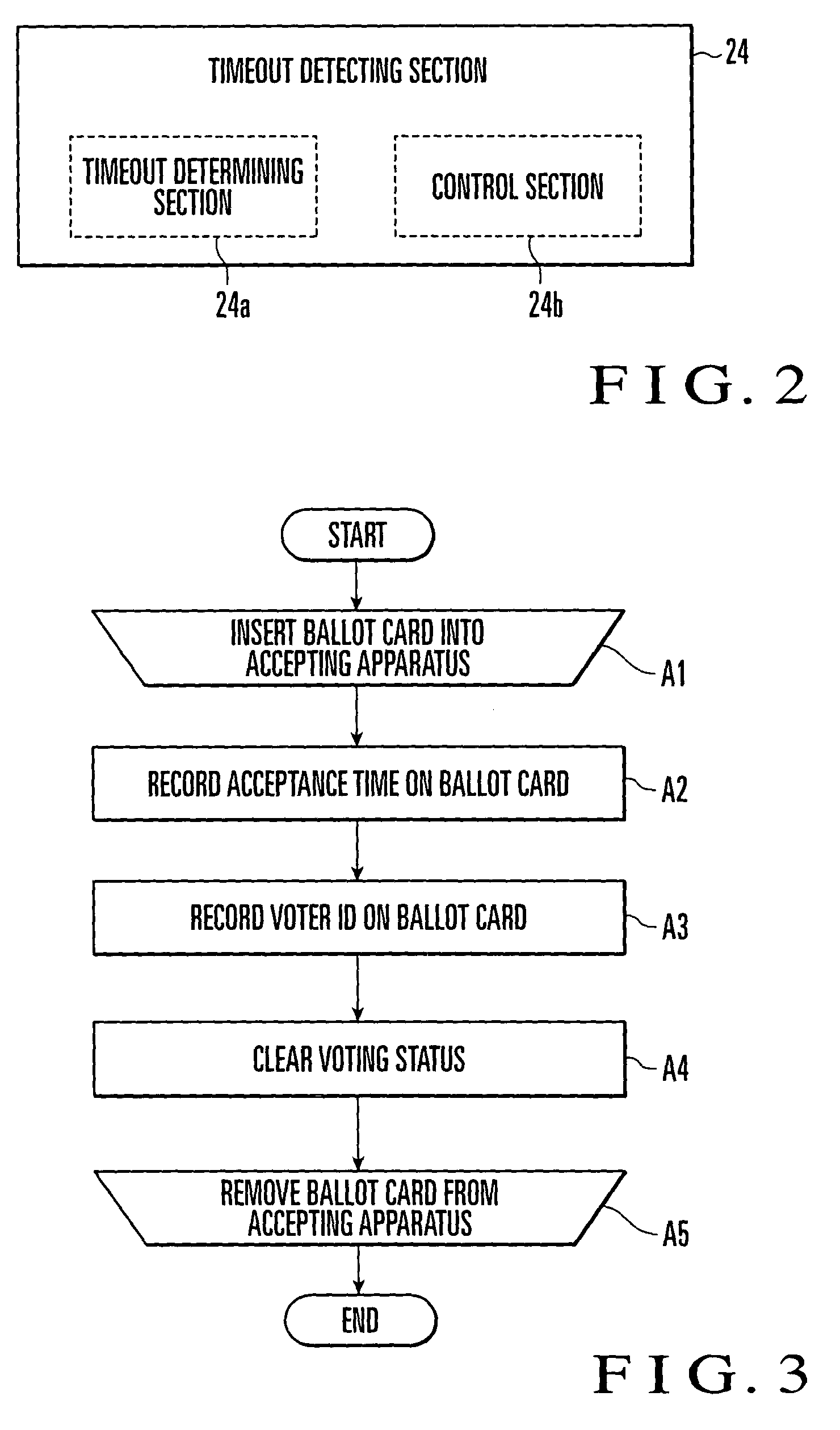
Electronic voting system and method of preventing unauthorized use of ballot cards therein
InactiveUS6997383B2Prevent unauthorized usePreventing unauthorized useVoting apparatusData processing applicationsReal-time computing
An electronic voting system includes a ballot card, accepting apparatus, and at least one voting apparatus. The accepting apparatus issues a ballot card in accordance with a vote acceptance request. The voting apparatus performs voting processing in accordance with a vote request using the ballot card. The accepting apparatus includes an acceptance time recording section which records the acceptance time on the ballot card when issuing the ballot card. The voting apparatus includes a timeout detecting section and unauthorized use warning display section. Before performing voting processing upon reception of a vote request, the timeout detecting section determines whether or not a preset timeout time has elapsed from the acceptance time recorded on the ballot card to the time of voting. The unauthorized use warning display section outputs a warning message when the timeout detecting section determines that the timeout time has elapsed.
Owner:NEC CORP
Method and apparatus for setting up network for IP communication in mobile terminal
ActiveUS8208472B2Ensure safetyPrevent unauthorizedError preventionFrequency-division multiplex detailsTelecommunicationsInternet Protocol
A method is provided for setting up a network for Internet Protocol (IP) communication between mobile terminals. A first mobile terminal determines a second mobile terminal that will communicate with the first mobile terminal. The first mobile terminal generates network setup information of the first mobile terminal for the IP communication and performs network setup using the network setup information. The first mobile terminal generates a network setup message including network setup information of the second mobile terminal, and sends the network setup message to the second mobile terminal.
Owner:SAMSUNG ELECTRONICS CO LTD
System and method for software activation and license tracking
ActiveUS10706130B2Activation is simpleReduce in quantityUser identity/authority verificationProgram/content distribution protectionSoftware distributionSoftware engineering
Owner:MACPAW WAY LTD
Systems and methods for domain restriction with remote authentication
ActiveUS10282726B2Prevent unauthorizedReduce usageCryptography processingUser identity/authority verificationCryptogramA domain
A process for combining domain restriction and remote authentication may include receiving a token from a plug-in application to conduct a transaction associated with a user of a communicating device. The process may include sending an authentication request to a remote access control sever to authenticate the user, and receiving, from the remote access control server, an authentication tracking value that the remote access control server used in generation of an authentication cryptogram. The process may also include generating, using the authentication tracking value, a domain restriction cryptogram that is used for domain restriction of the token, and sending, to the plug-in application, the domain restriction cryptogram.
Owner:VISA INT SERVICE ASSOC
Computed radiography license method and system
ActiveUS8833647B2Prevent unauthorizedSimple and convenient and reliableSurgeryRecord carriers used with machinesX-rayX ray image
A method for licensing a system for obtaining an X-ray image of a subject. The system employs flexible information carrier plates for computed radiography, which are exposed to X-rays and then scanned in a scanner. A license media is provided with a RFID transponder, which stores in its memory identification information referring to the system components as well as information referring to an amount of valid licenses available for use of the system components. When the identification information stored in the memory of the license media RFID transponder matches the identification information transmitted to the scanner by a processing and acquisition station the carrier plates are scanned automatically.
Owner:CARESTREAM DENTAL TECH TOPCO LTD
An application anti-uninstallation method and device
Owner:北京宝利明威软件股份有限公司
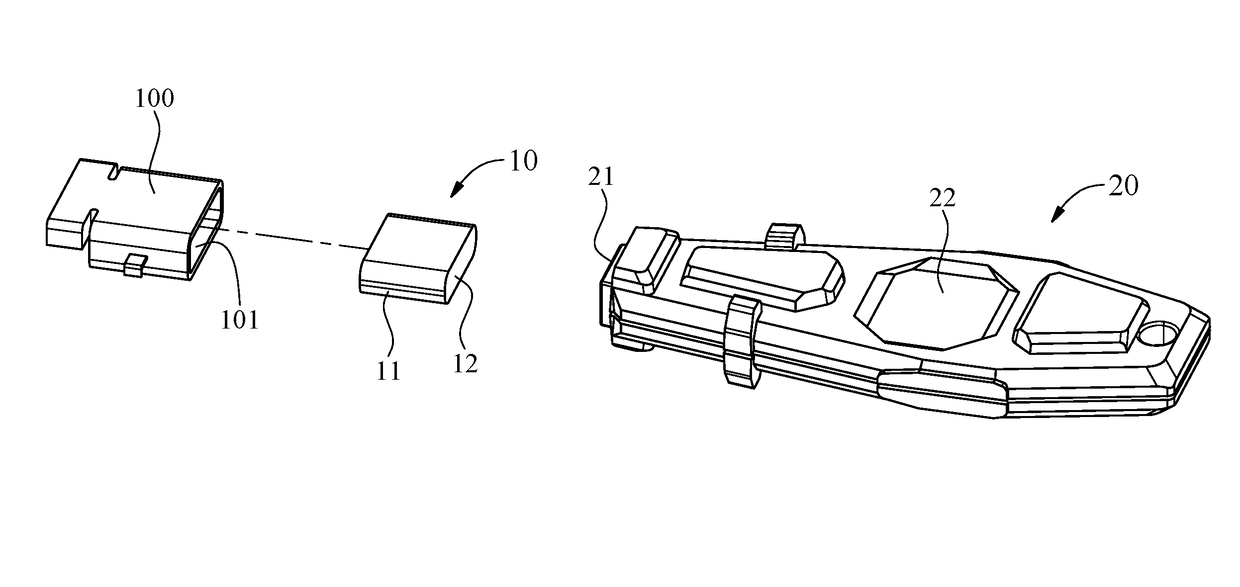
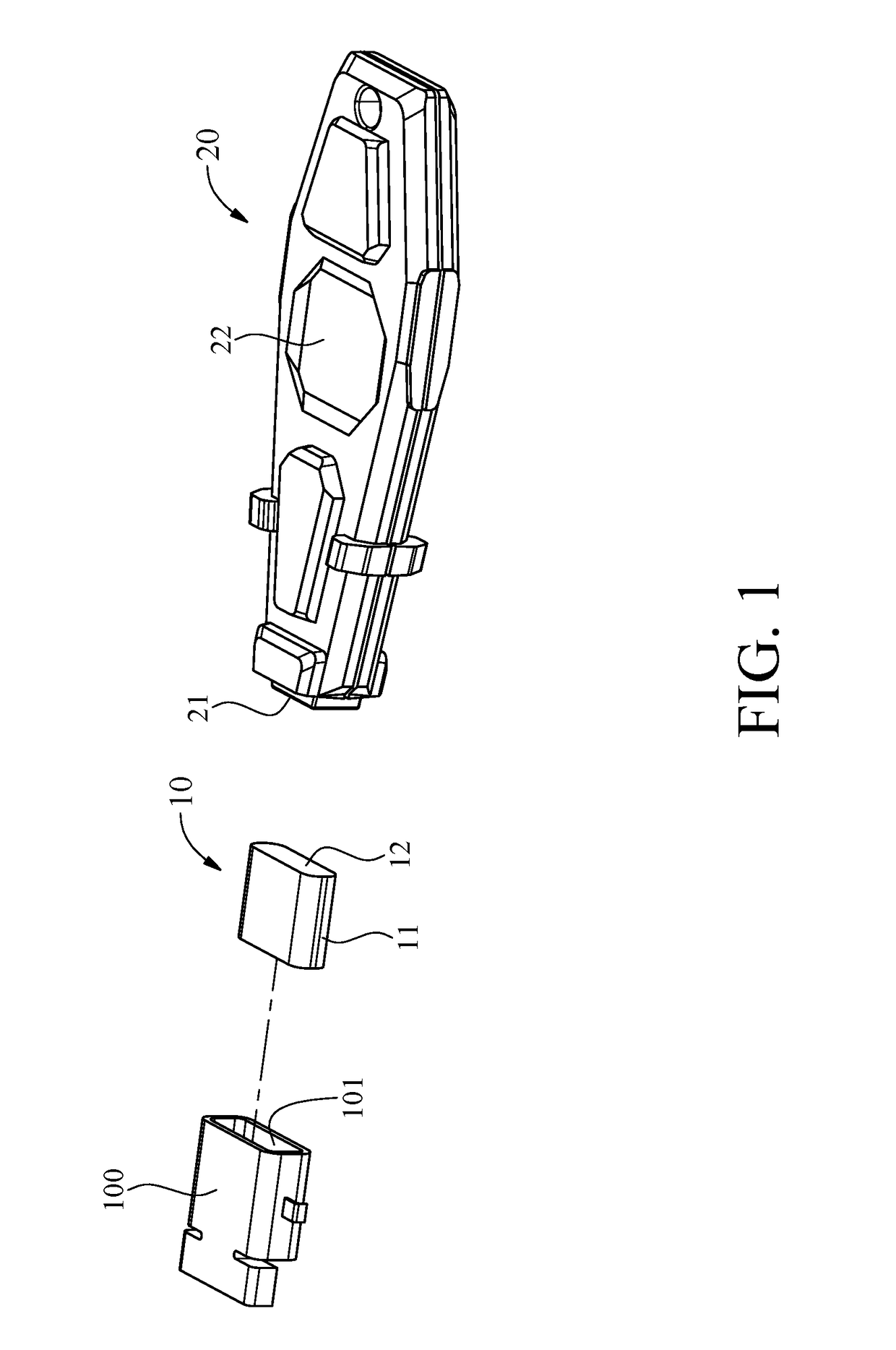
Protective module for data transmission port
ActiveUS9640896B1Improve usabilityPrevent intrusionDigital data processing detailsComputer periphery connectorsComputer moduleData transmission
A protective module for a data transmission port includes a plugging element and an unlocking element. The plugging element includes an extension portion and an end portion. The extension portion is inserted into the data transmission port. The end portion obstructs an opening of the data transmission port and is made of a first magnetically attracting material. The unlocking element includes an attraction portion adapted to attract the end portion and made of a second magnetically attracting material. The end portion of the plugging element escapes from the data transmission port as a result of magnetic attraction between the end portion of the plugging element and the unlocking element as soon as the unlocking element approaches the plugging element plugged into the data transmission port. Therefore, the protective module prevents external devices from getting connected to the data transmission port and prevents dust intrusion.
Owner:HSING CHAU INDAL
Share secret key management method
InactiveCN101193128BEasy to modifyImprove securityKey distribution for secure communicationCommunications systemPassword
The invention provides a managing method of a shared key, which is used for realizing preservation and use of the shared key in a terminal of a communication system, which comprises the following steps: step 602, distributing the shared key when a user adds a network, adopting a public cryptography of an initial user to encrypt the shared key, and writing the encrypted shared key into a nonvolatile memory of a PC card through an interface of the PC card; step 604, inputting a username and a public password of the initial user in a dialing software interface when the user starts the terminal for the first time to log on the network; and step 606, decrypting the encrypted shared key which is read by the interface with the dialing software to obtain the shared key, and utilizing the structureof the shared key to extend a judge right protocol message so as to pass the judge right. Therefore, the invention facilitates net-surfing convenience of the user, ensures the use safety of the shared key and at the same time allows a plurality of users to go online with one same PC card.
Owner:ZTE CORP
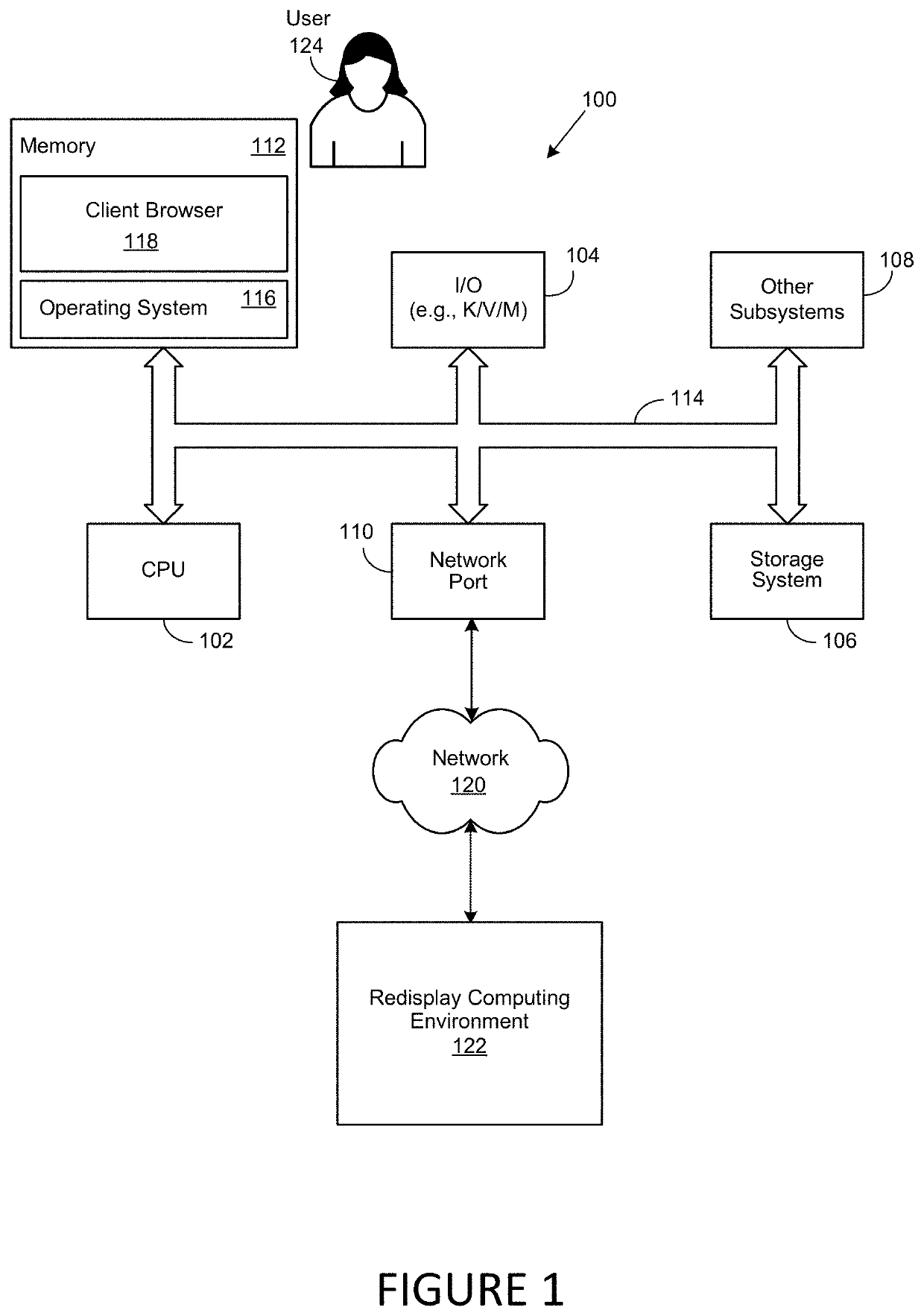
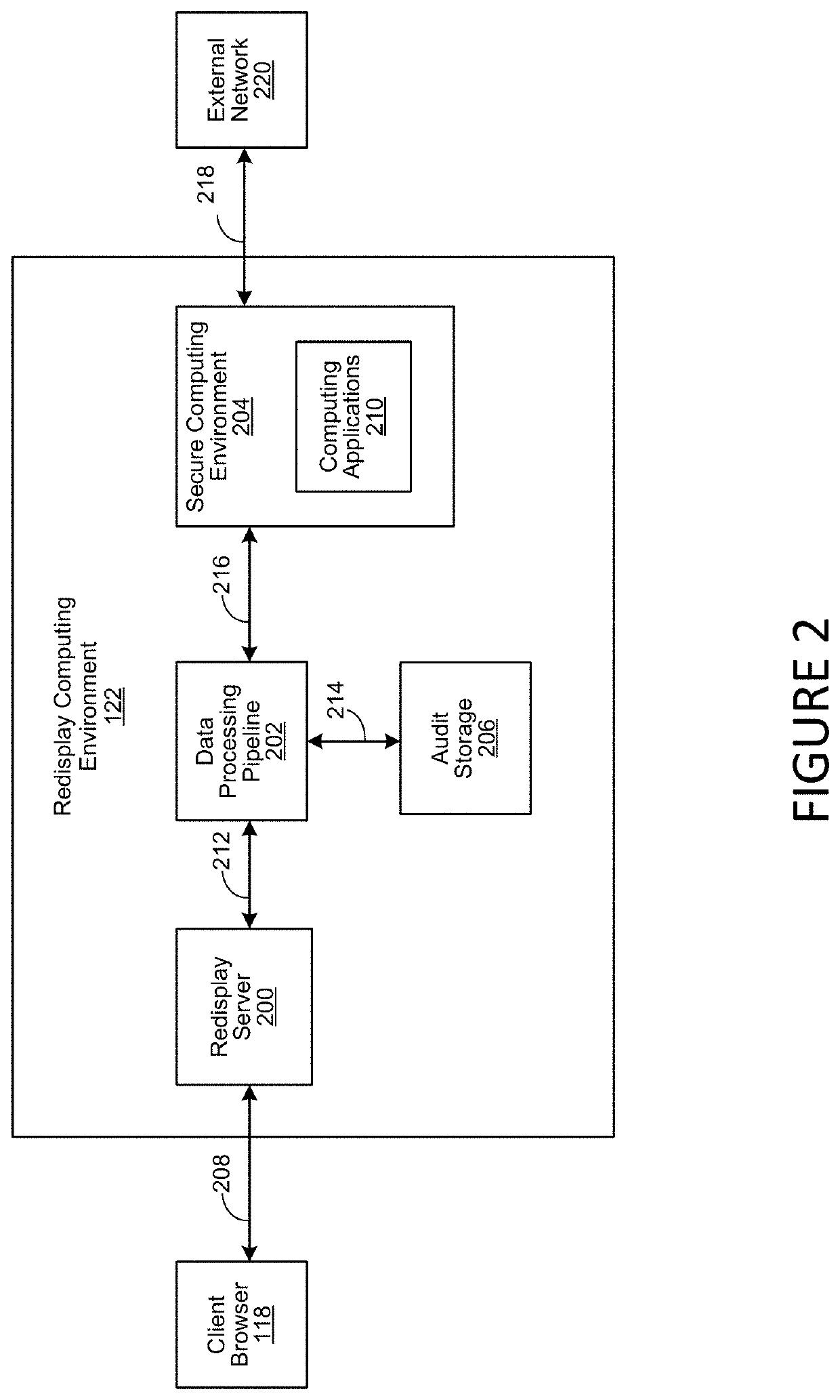
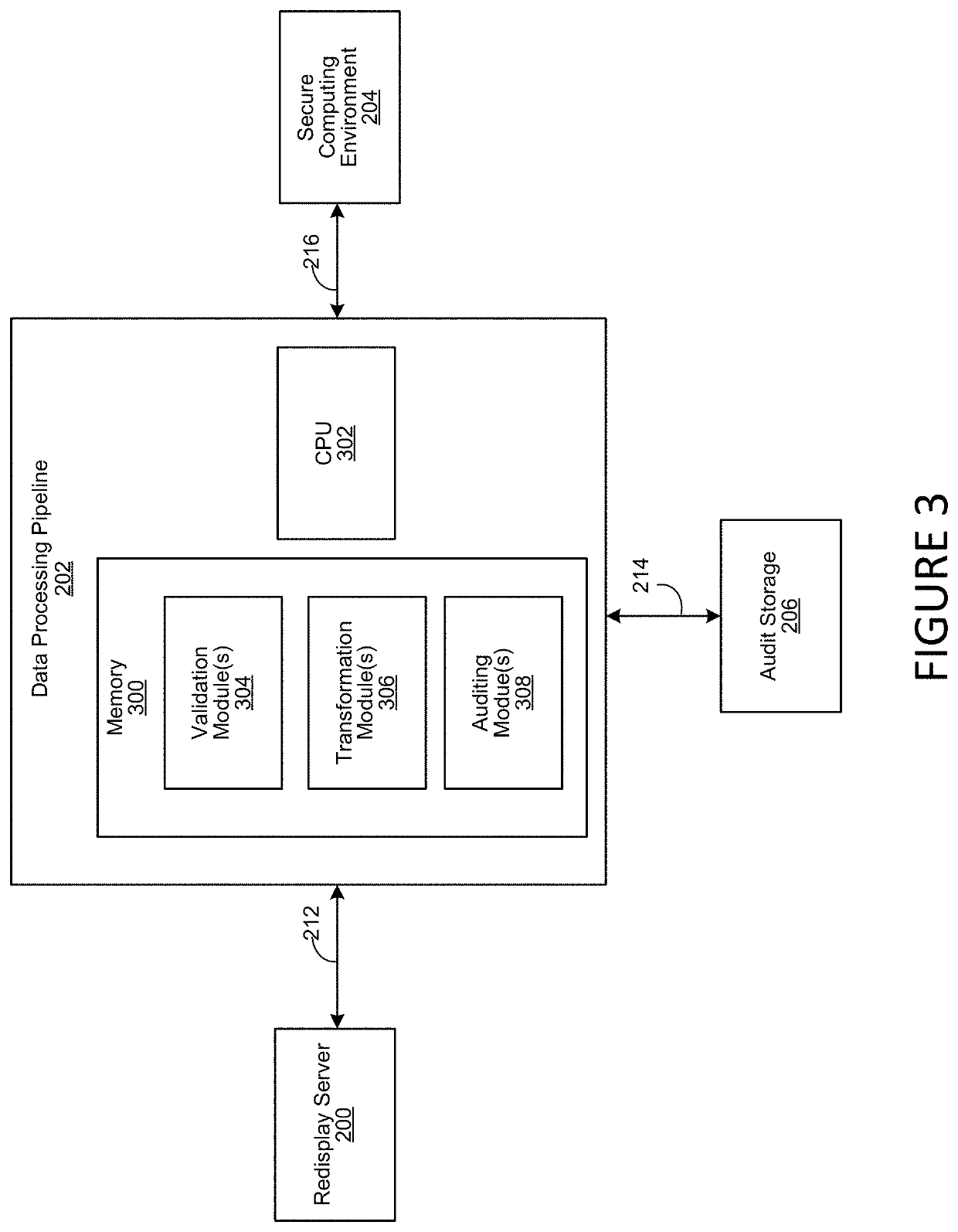
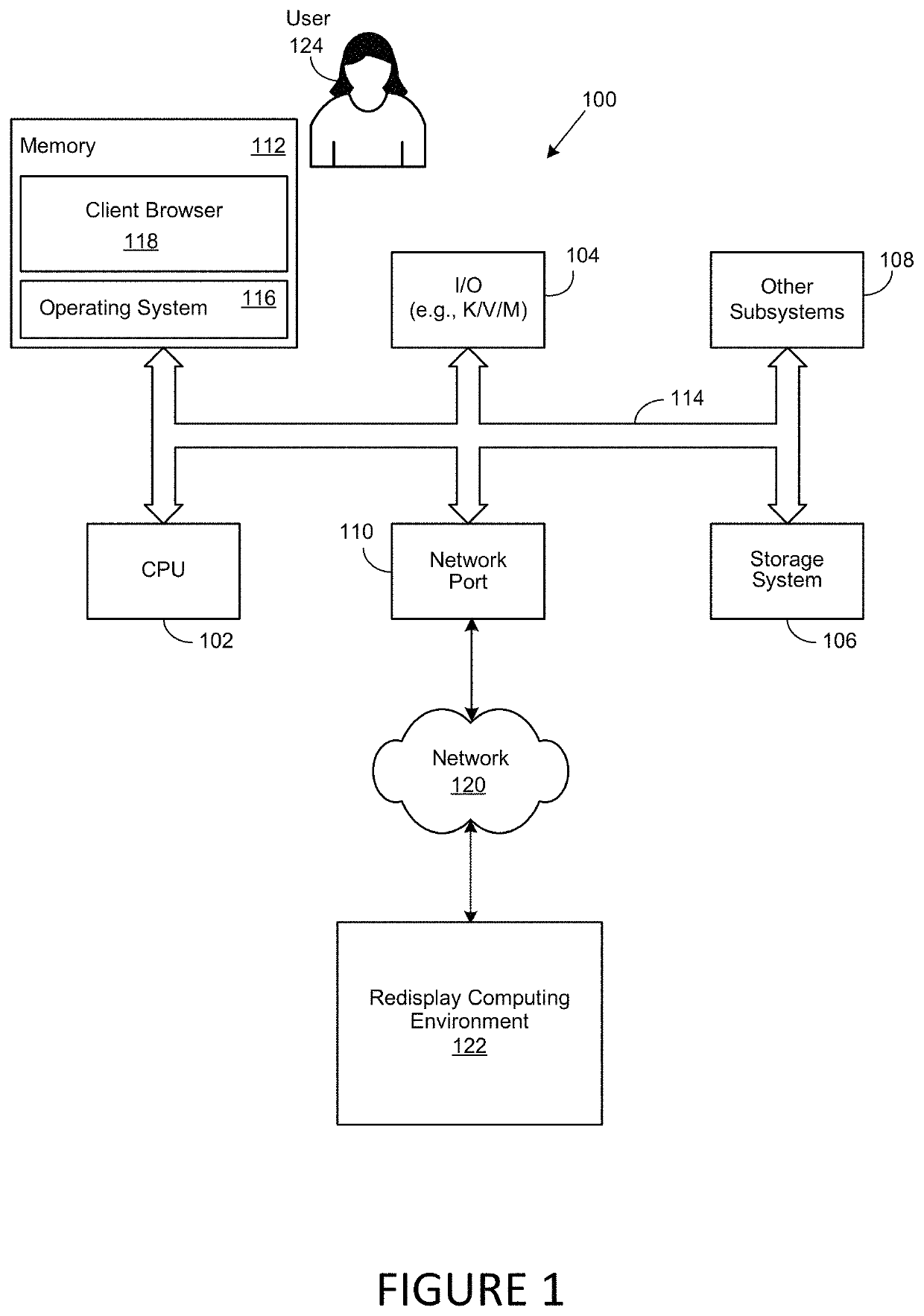
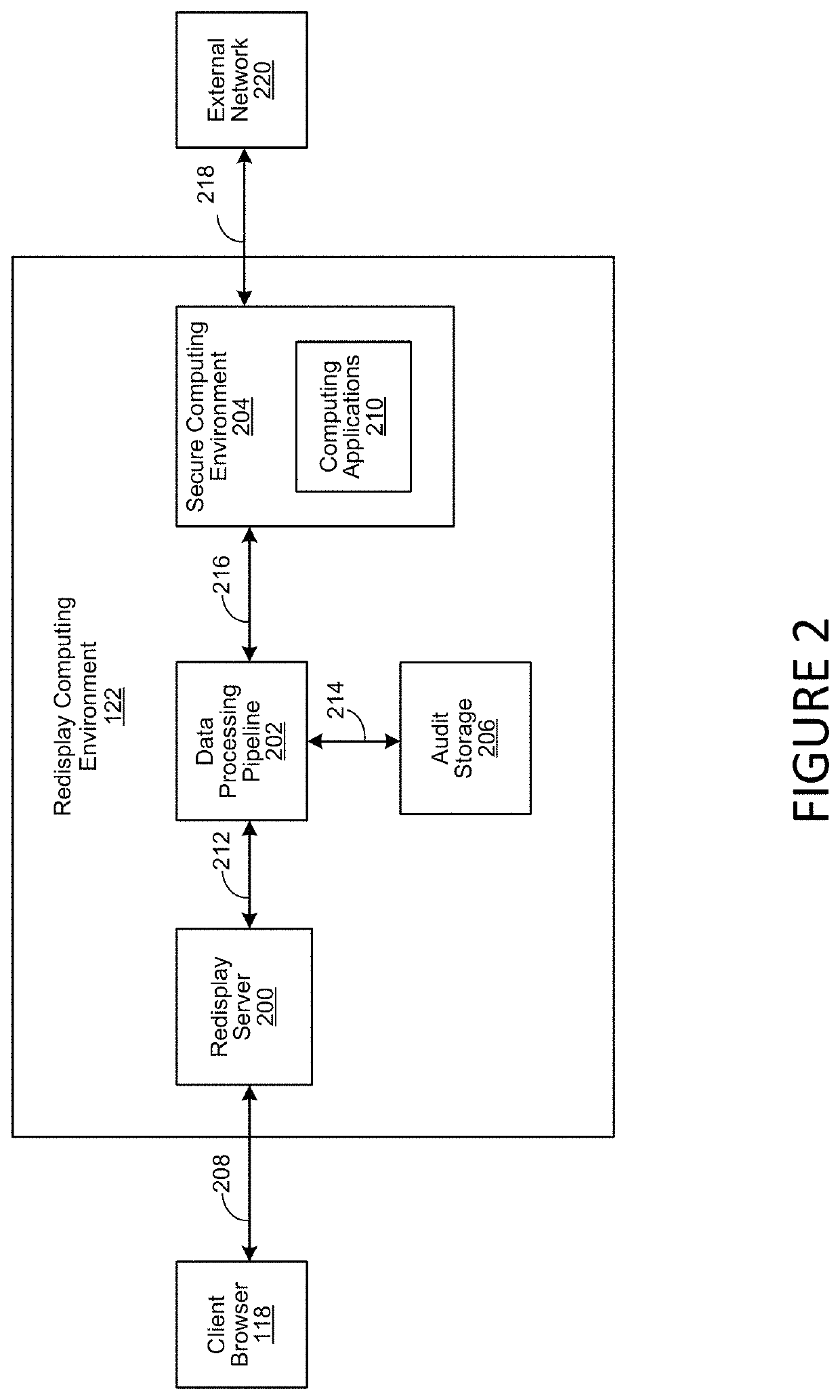
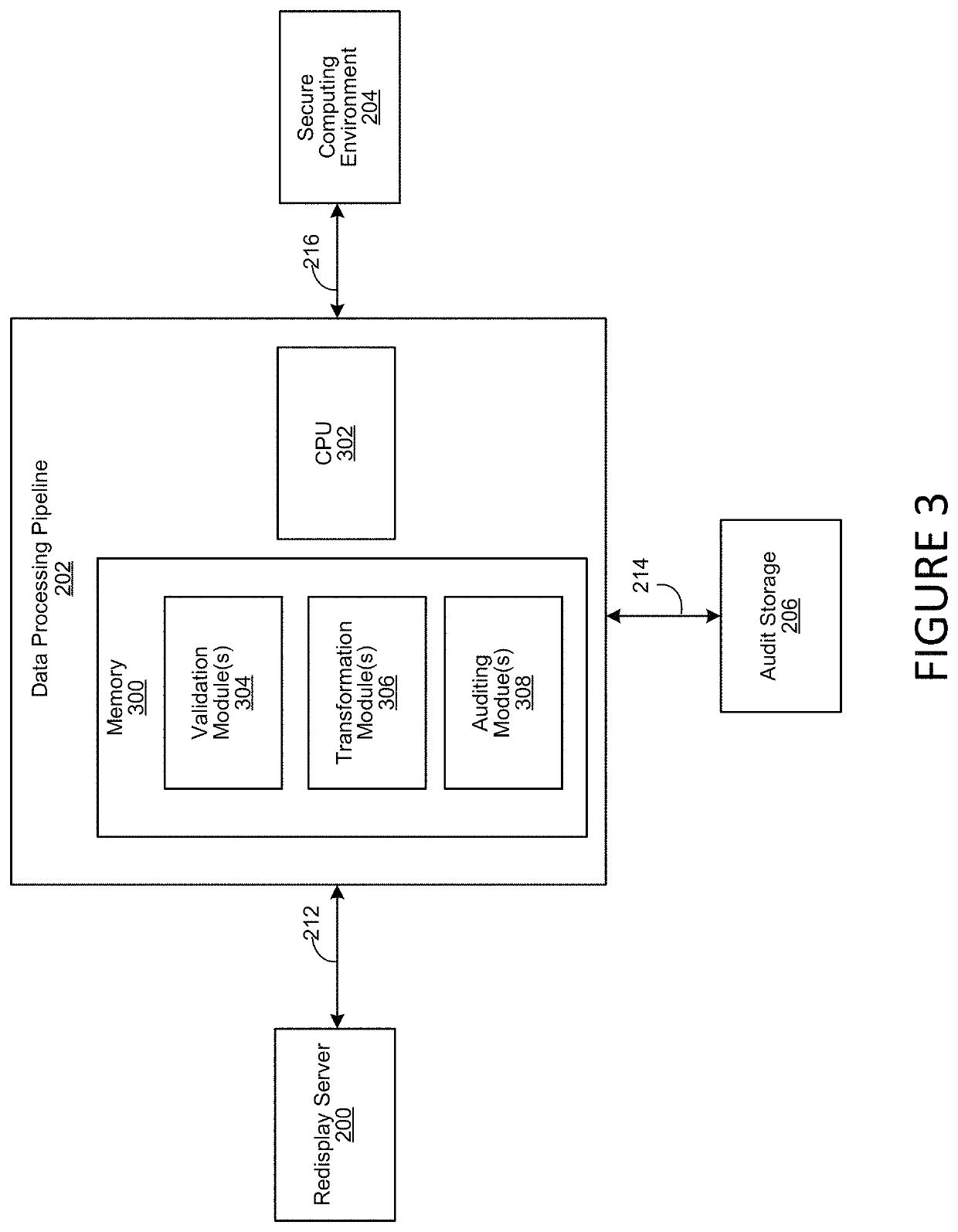
Redisplay Computing with Integrated Data Filtering
ActiveUS20200177627A1Prevent infiltration and exfiltrationMinimize abilityDigital data protectionTransmissionGraphicsEngineering
A method, system and computer-usable medium for redisplaying data at a remote access client system from a secure computing environment. The redisplaying data includes receiving a request form the remote access client system for data, inspecting the request for potential unauthorized or malicious retransmission. Modifying the data, by filtering audio data or transforming graphical data prior to sending the requested data is performed to prevent the unauthorized or malicious retransmission.
Owner:FORCEPOINT LLC
Redisplay computing with integrated data filtering
ActiveUS11297099B2Prevent infiltration and exfiltrationMinimize abilityDigital data protectionTransmissionGraphicsEngineering
A method, system and computer-usable medium for redisplaying data at a remote access client system from a secure computing environment. The redisplaying data includes receiving a request form the remote access client system for data, inspecting the request for potential unauthorized or malicious retransmission. Modifying the data, by filtering audio data or transforming graphical data prior to sending the requested data is performed to prevent the unauthorized or malicious retransmission.
Owner:FORCEPOINT LLC
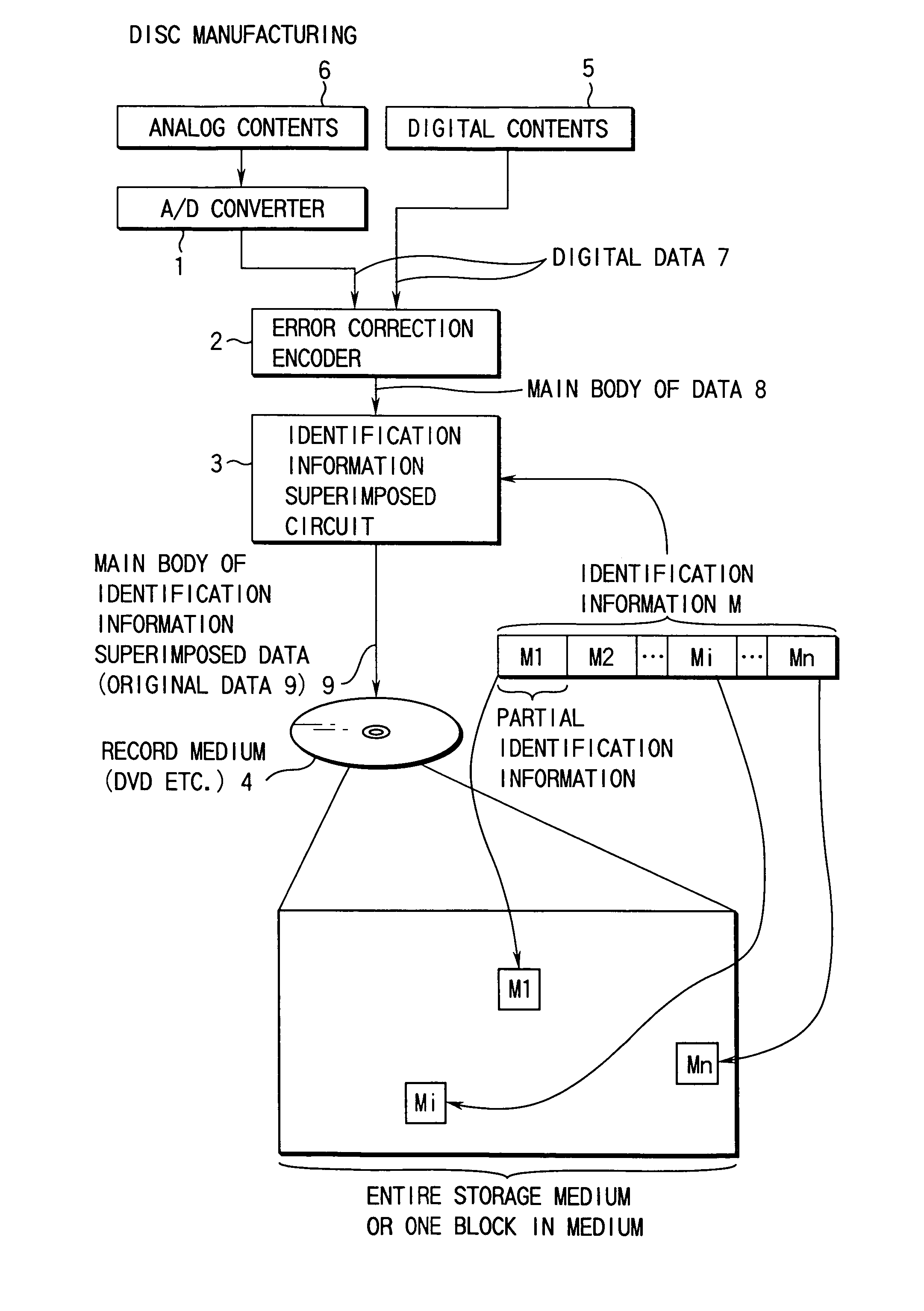
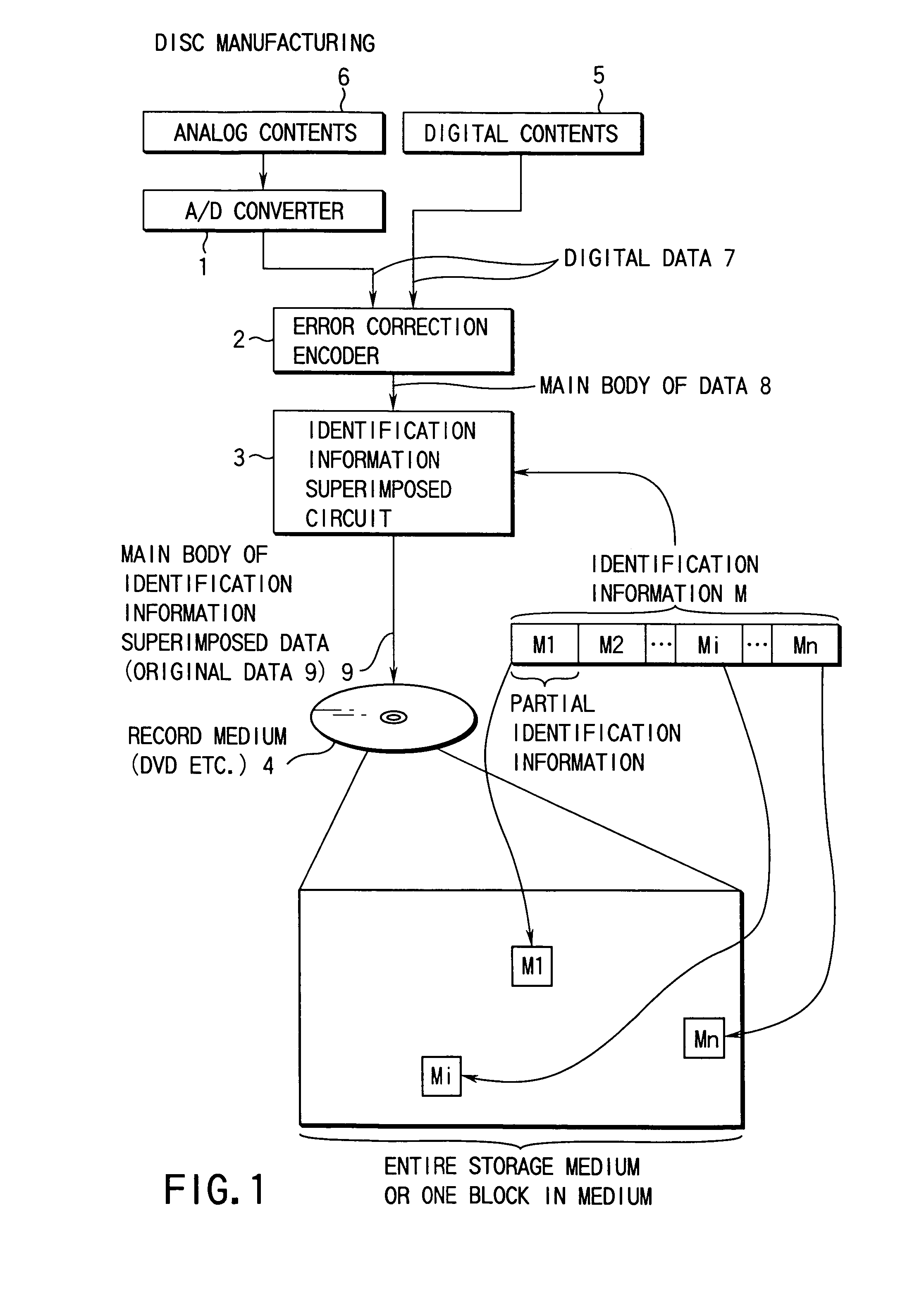
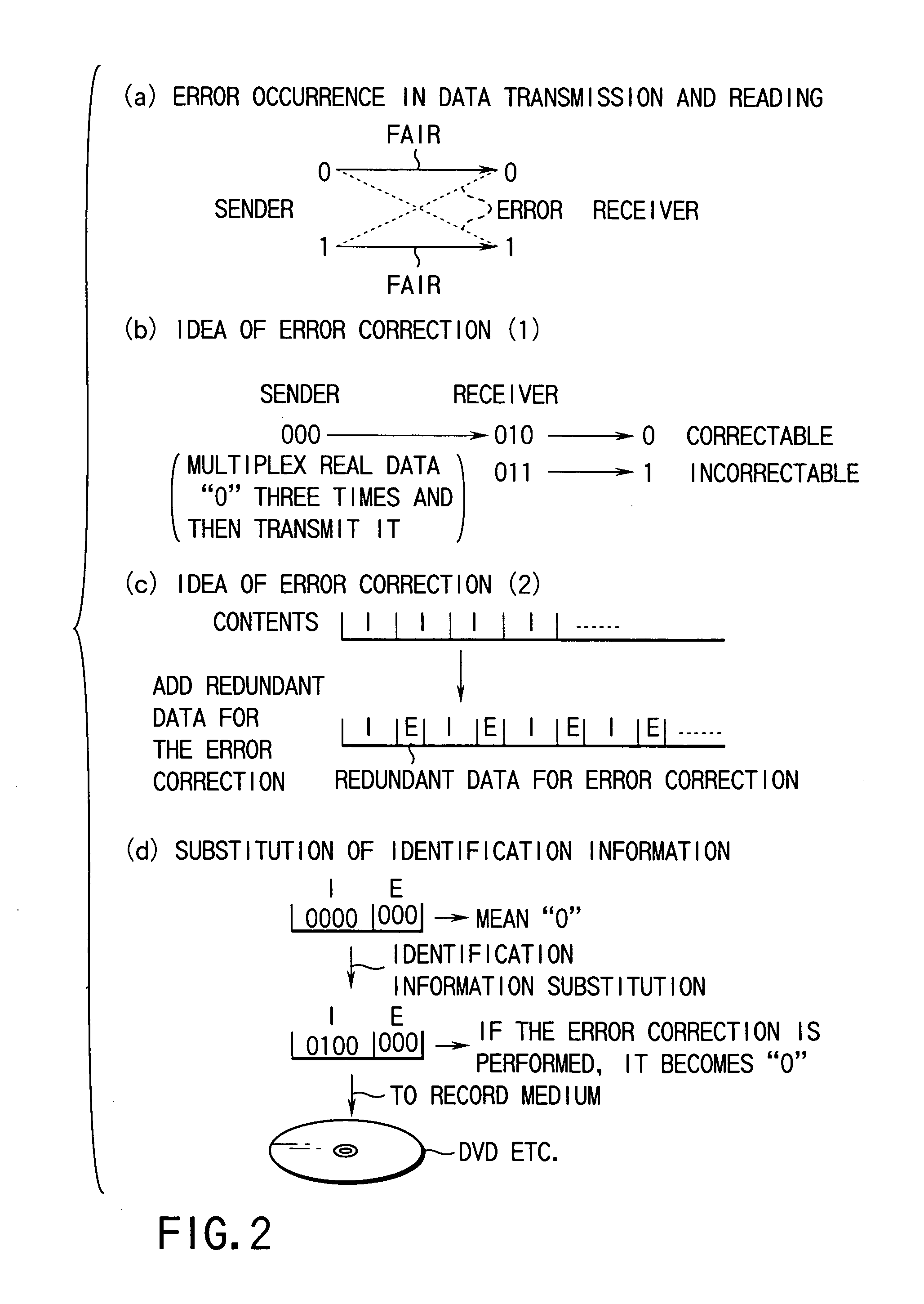
Record medium, record medium manufacturing device, computer readable record medium on which program is recorded, and data presentation device
InactiveUS7233667B1Prevent unauthorizedInput/output to record carriersError preventionOriginal dataComputer engineering
A record medium comprises an original data obtained by superimposing a presentation target data, to which an error correction encoding is performed and an identification information.
Owner:KK TOSHIBA
Popular searches
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com