Method and apparatus for a distributed firewall
a distributed firewall and distributed technology, applied in the field of communication, can solve the problems of end-to-end encryption, threat to the traditional notion of firewalls, and inconvenient use of conventional firewalls to deal with these types of problems,
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
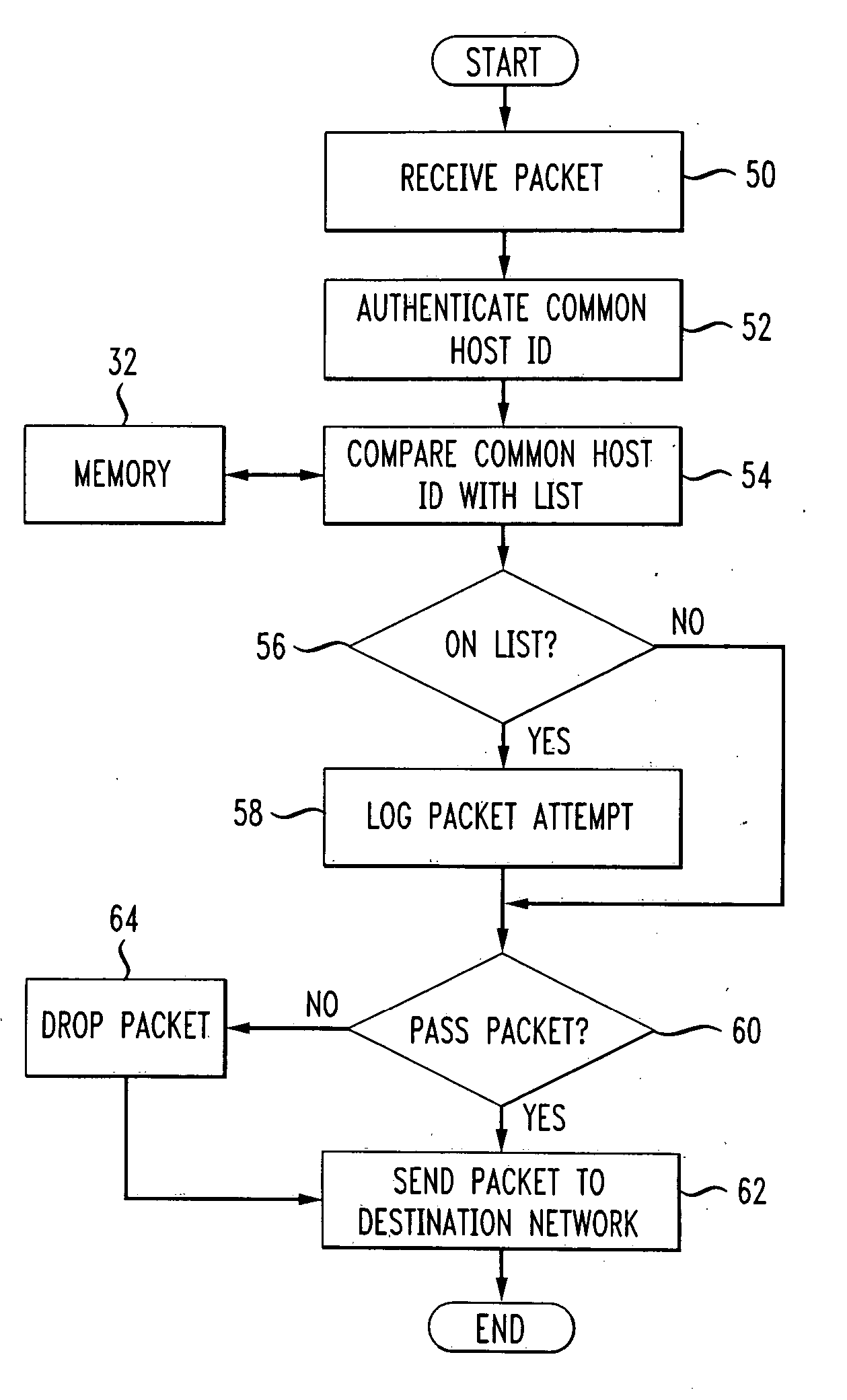
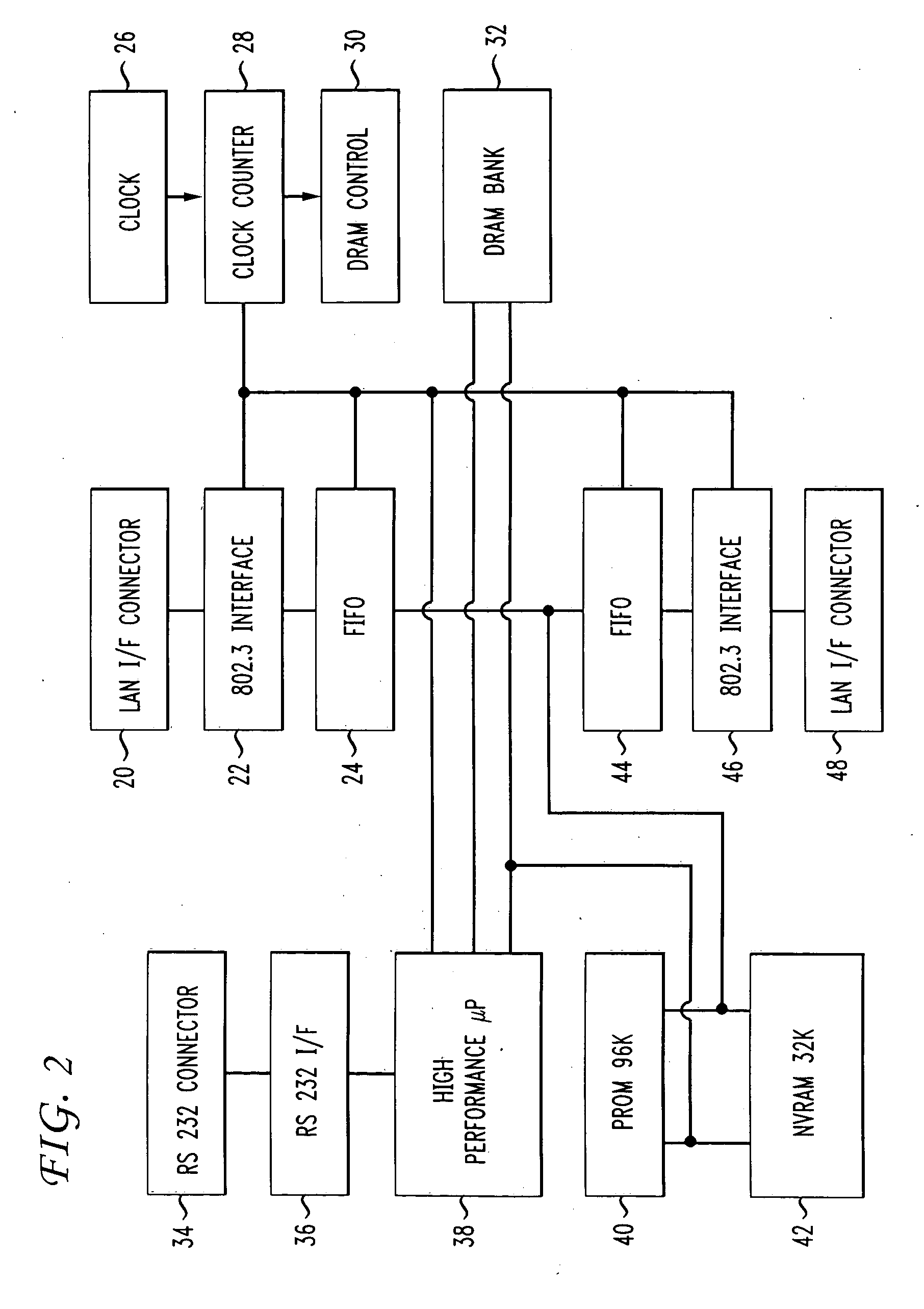
[0012] The embodiments of the invention include a distributed firewall that utilizes the following principles: a) a policy language that states what sort of connections are permitted or prohibited, b) an encryption mechanism; and c) any of a number of system management tools, such as Microsoft's Systems Management Server (SMS) or Automatic Software Distribution (ASD) to manage the distributed firewall. ASD is described in a paper authored by Andrew Koenig entitled “Automatic Software Distribution,” USENIX Conference Proceedings, Pages 312-322, Salt Lake City, Utah, Summer, 1984, and is incorporated by reference herein.
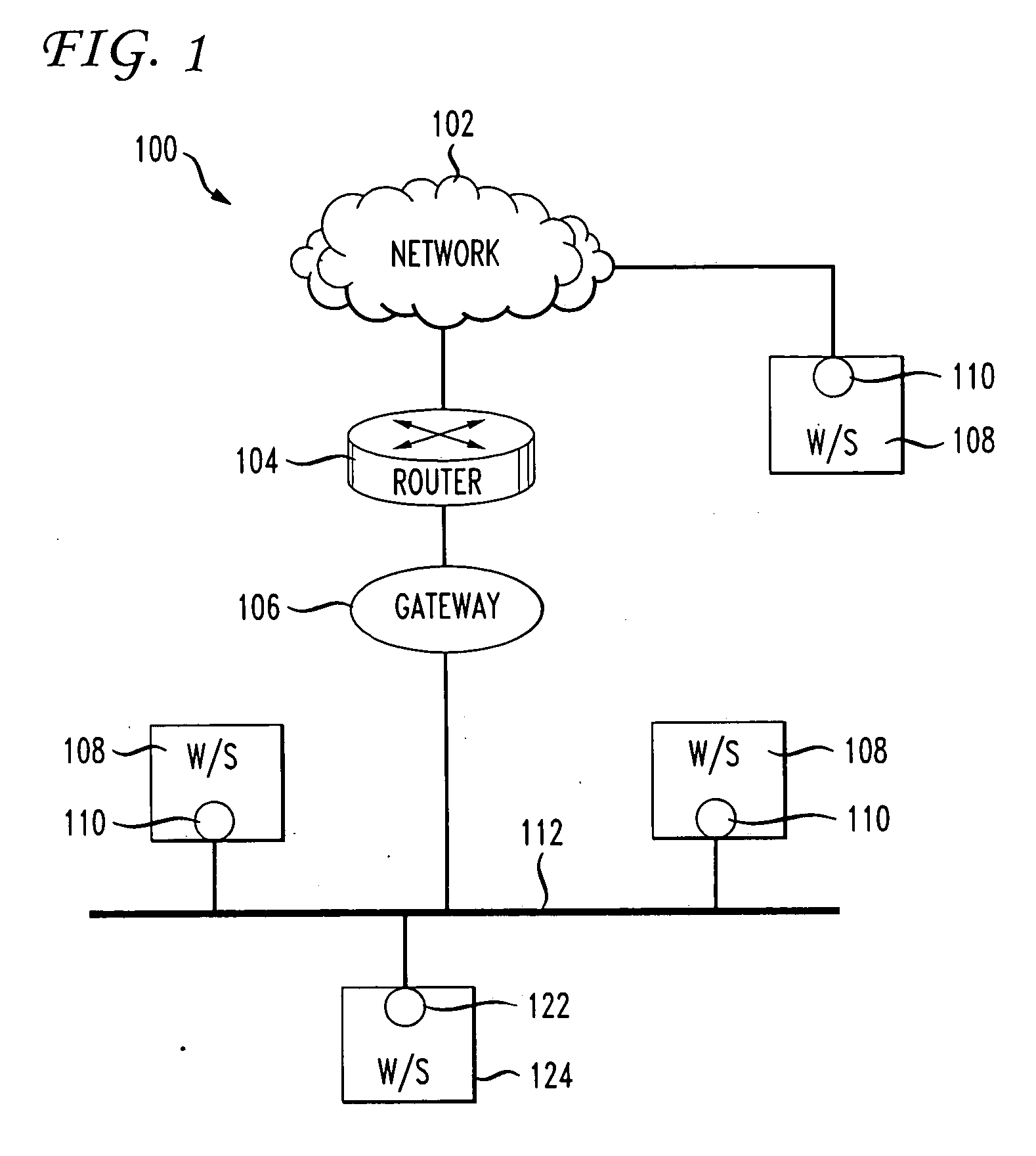
[0013] In one embodiment of the invention, a compiler translates the policy language into some internal format. The system management software distributes this policy file to all hosts that are protected by the firewall. Any incoming packets are accepted or rejected by each “inside” host, according to both the policy and the cryptographically-verified identity of each...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com