Web back door detection method and device based on behavioral characteristics
A backdoor and behavioral technology, applied in the field of Internet security, can solve problems such as multiple false alarms, complex code logic, and large web access volume, and achieve the effect of increasing detection rate, improving detection efficiency, and reducing false alarm rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
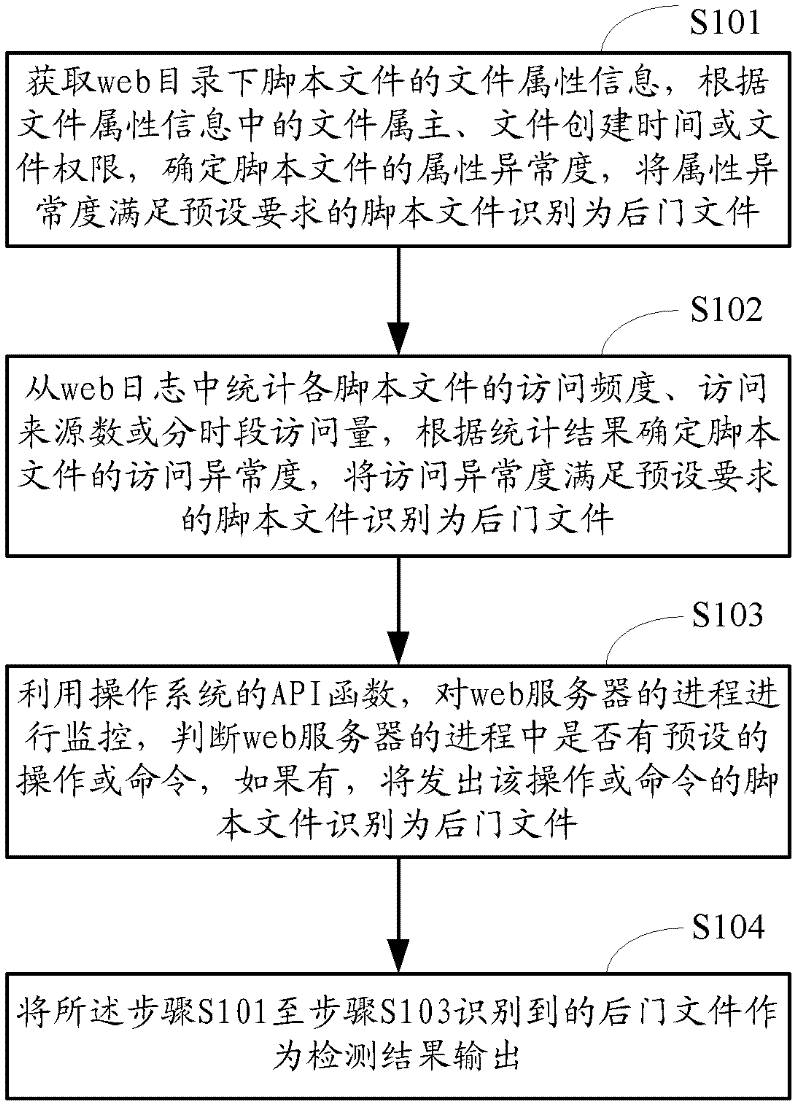
[0075] figure 1 It is the flowchart of the method for detecting web backdoors based on behavioral characteristics provided by this embodiment, such as figure 1 As shown, the method includes:
[0076] Step S101, obtain the file attribute information of the script file in the web directory, determine the attribute abnormality degree of the script file according to the file owner, file creation time or file authority in the file attribute information, and set the attribute abnormality degree to meet the preset The required script file is identified as a backdoor file.
[0077] All program scripts in the web application are basically saved on the web server in the form of files, and these files are called web script files, ie script files. In addition to the file content, the script file also includes a lot of file attribute information, such as: file name, file creation time, file modification time, file owner, file type, file permission and file size, etc. Since there is a un...
Embodiment 2
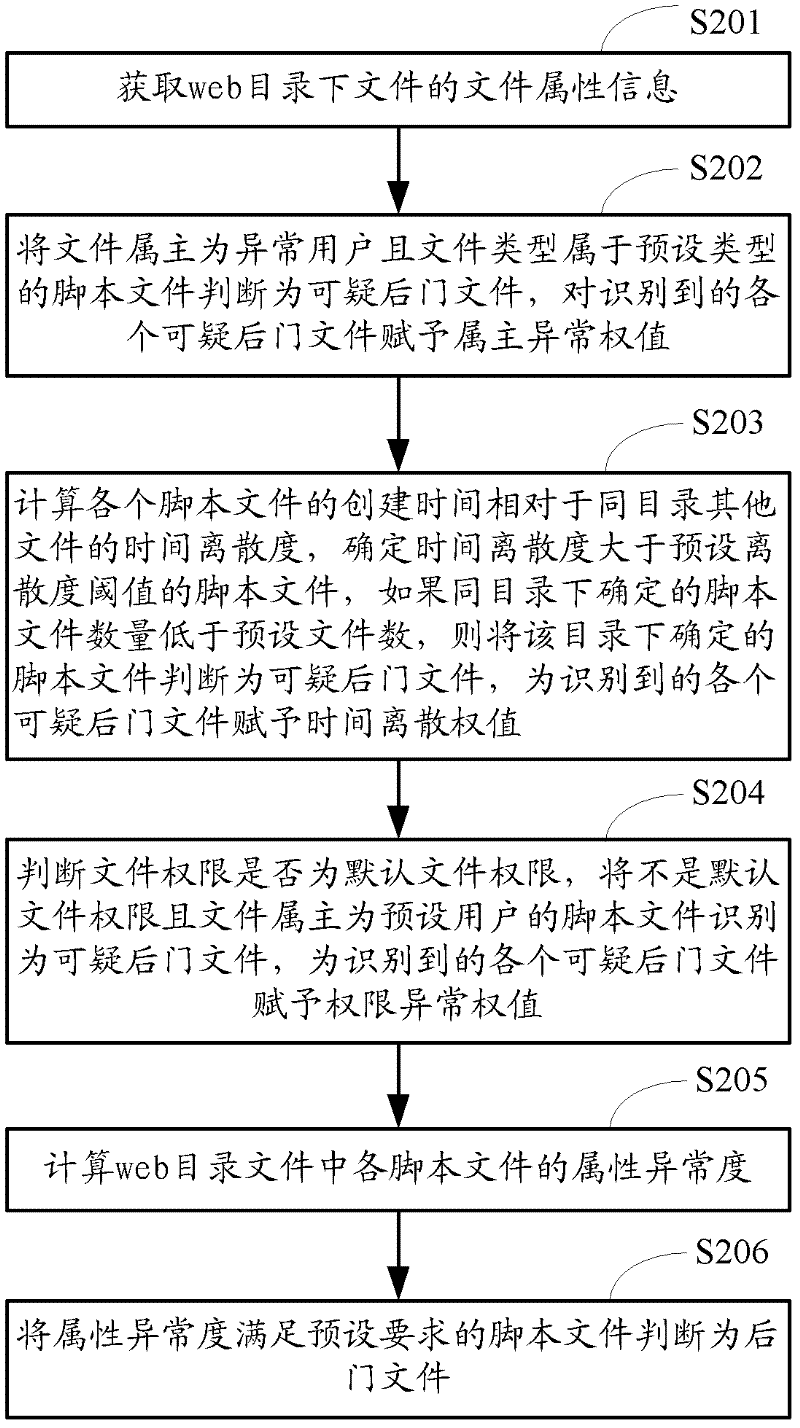
[0141] Figure 4 It is a flow chart of the web backdoor detection method based on behavioral characteristics provided in Embodiment 2. Such as Figure 4 As shown, the method includes:
[0142] Step S401, obtain the file attribute information of the script file in the web directory, determine the attribute abnormality degree of the script file according to the file owner, file creation time or file authority in the file attribute information, and use the attribute abnormality degree as the script file The first weight W1 of .
[0143] The calculation method of the attribute abnormality degree is the same as that in the first embodiment, so it will not be repeated here.
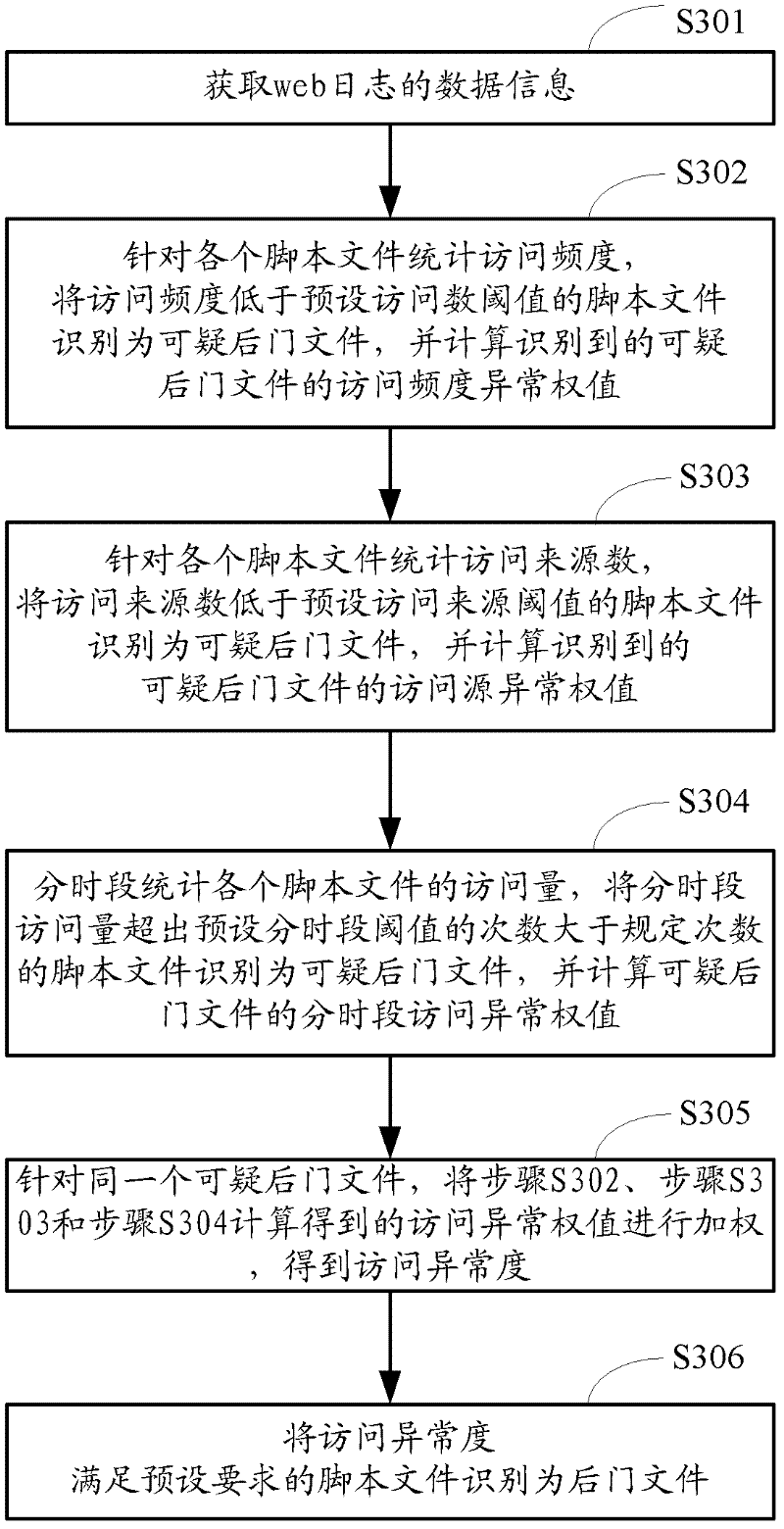
[0144] Step S402, counting the access frequency, the number of access sources, or the amount of visits by time period of each script file from the web log, determining the access abnormality of the script file according to the statistical results, and using the access abnormality as the second weight of the ...
Embodiment 3
[0155] Figure 5 is a schematic diagram of a web backdoor detection device based on behavioral features provided in this embodiment. Such as Figure 5 As shown, the device includes:
[0156] The judging module includes an attribute anomaly judging module 10 , an access anomaly judging module 20 and a process anomaly monitoring module 30 .
[0157] Attribute abnormal judgment module 10, is used for obtaining the file attribute information of script file under web directory, according to the file creation time in described file attribute information, file owner or file authority, determines the attribute abnormality degree of script file, attribute abnormality degree Script files that meet preset requirements are identified as backdoor files.
[0158] All program scripts in the web application are basically saved on the web server in the form of files, and these files are called web script files, ie script files. In addition to the file content, the script file also includes...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com