Group data completeness verification method based on proxy
A technology of data integrity and verification method, which is applied in proxy-based group data integrity verification and cloud group security, and can solve the problems of no encryption primitive and unforgeability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0042] The technical solutions provided by the present invention will be described in detail below in conjunction with specific examples. It should be understood that the following specific embodiments are only used to illustrate the present invention and are not intended to limit the scope of the present invention.
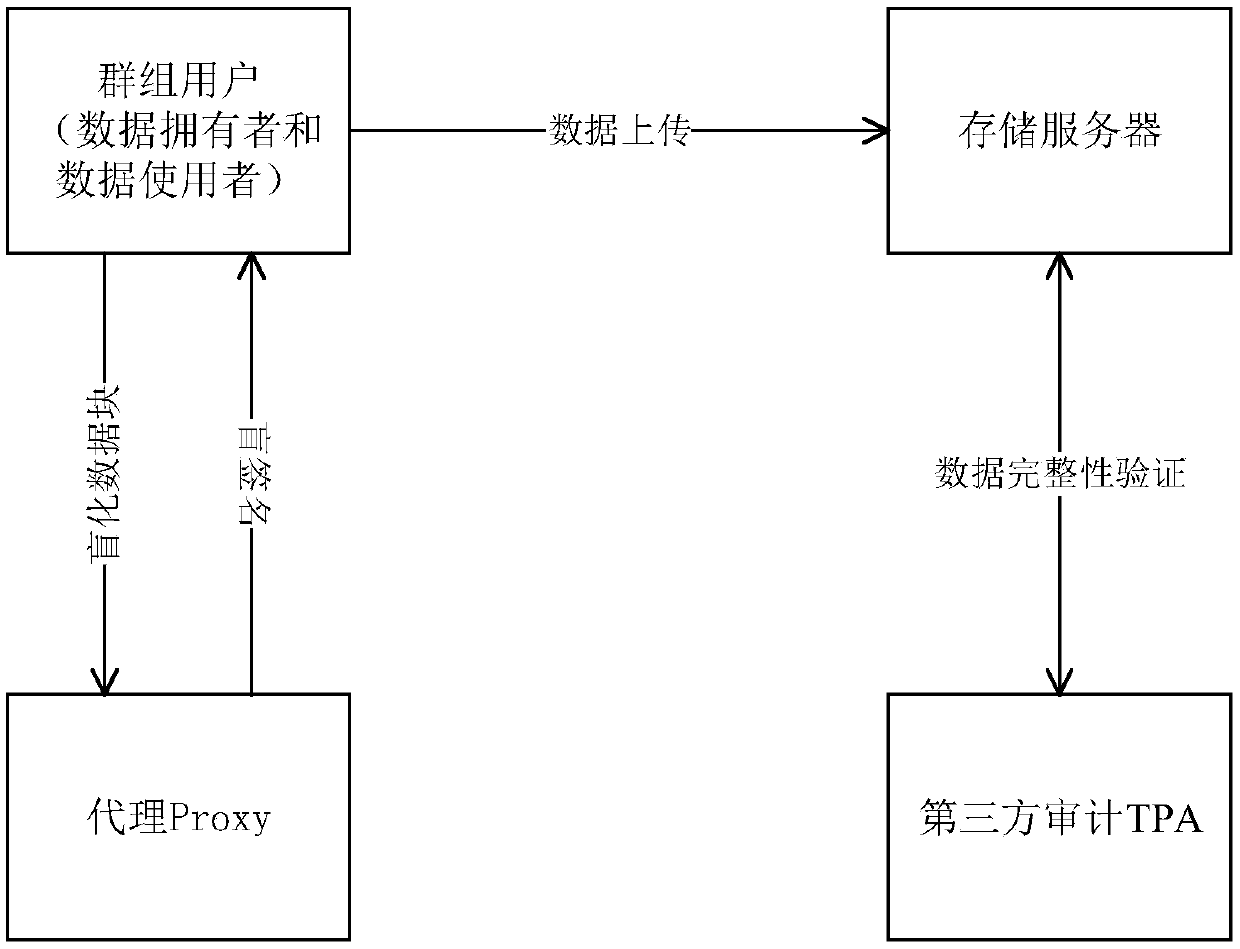
[0043] Data integrity verification protocol system model, such as figure 1 As shown, four entities are included: group users (data owner and data user), storage server, proxy Proxy, and third-party audit TPA.
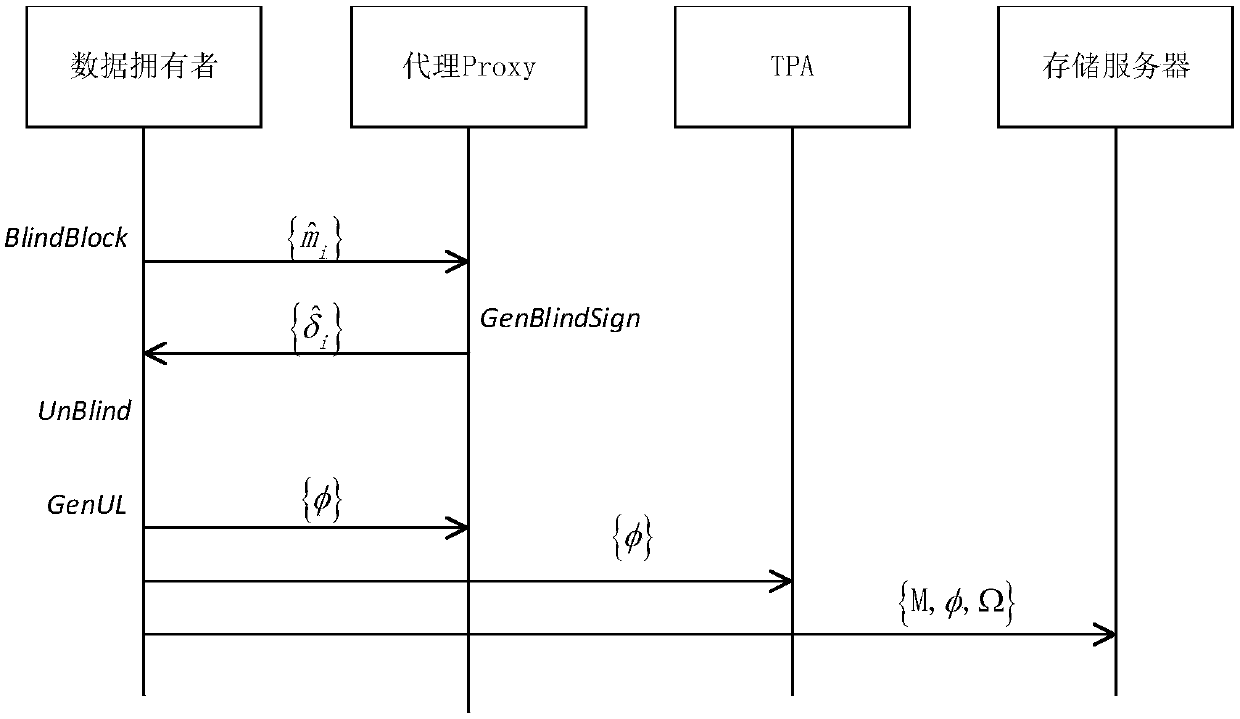
[0044] The present invention includes four major parts: an initialization stage, a data outsourcing stage, an integrity verification stage, and a group user member update stage.
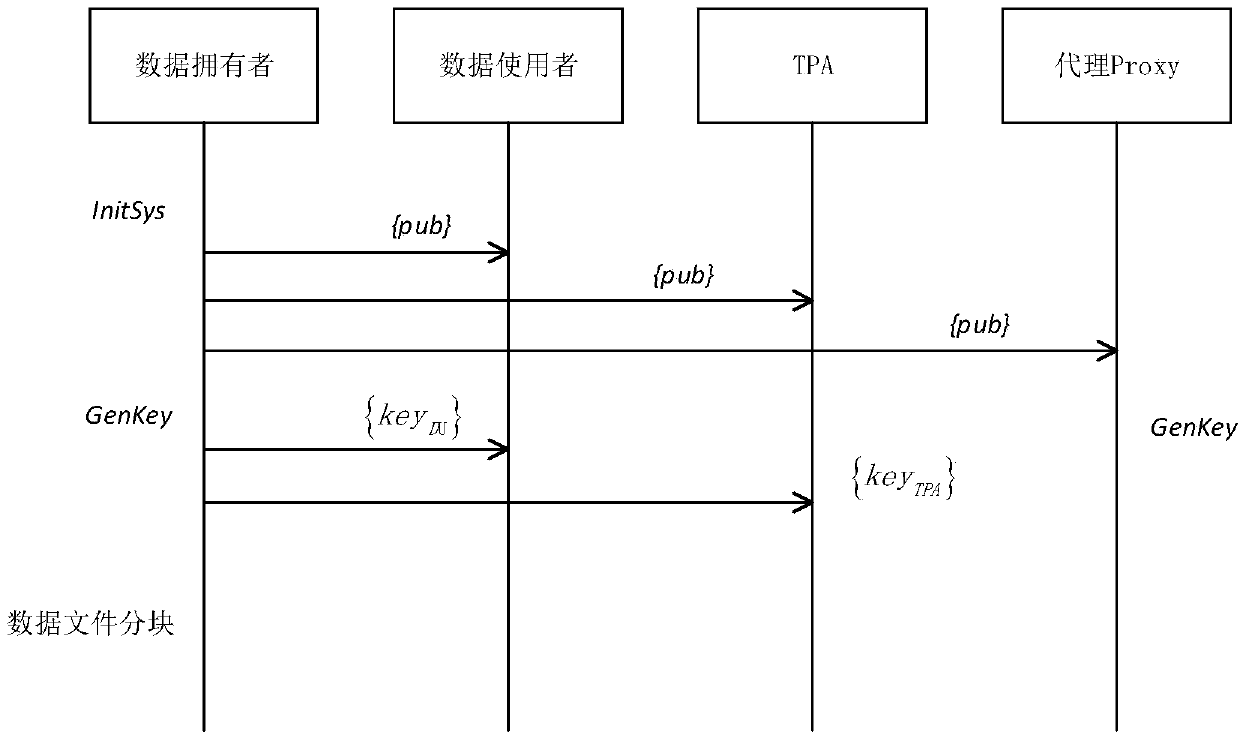
[0045] The process of the initialization phase is as follows figure 2 As shown, the system first initializes the public parameters, the data owner generates its own private key, public key, and other key parameters, and sends the key parameters to TPA and data users, and the pr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com