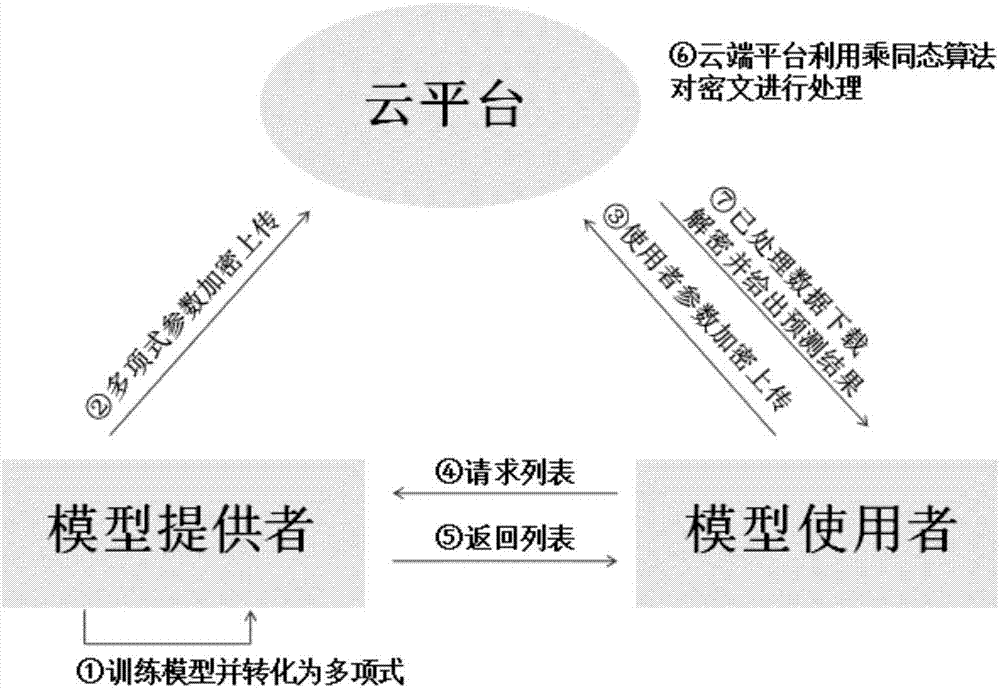
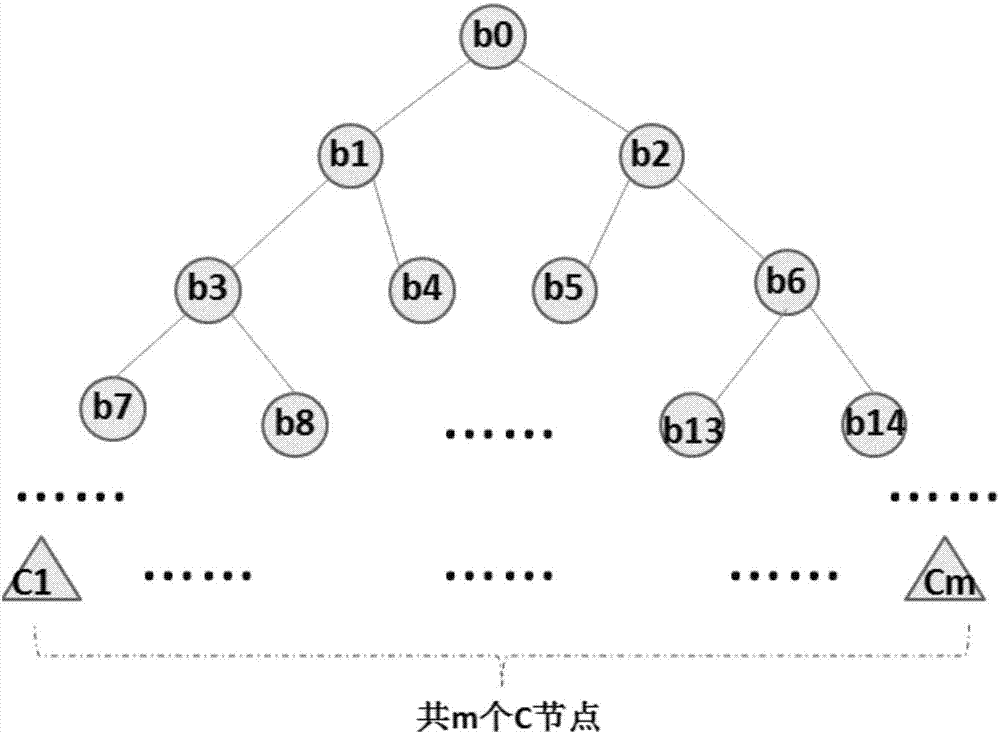
Safe data-outsourcing machine learning and data analysis method
A data outsourcing and machine learning technology, applied in the field of information security, can solve problems such as data leakage, reduce complexity, improve computing efficiency, and solve the contradiction between security and processability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
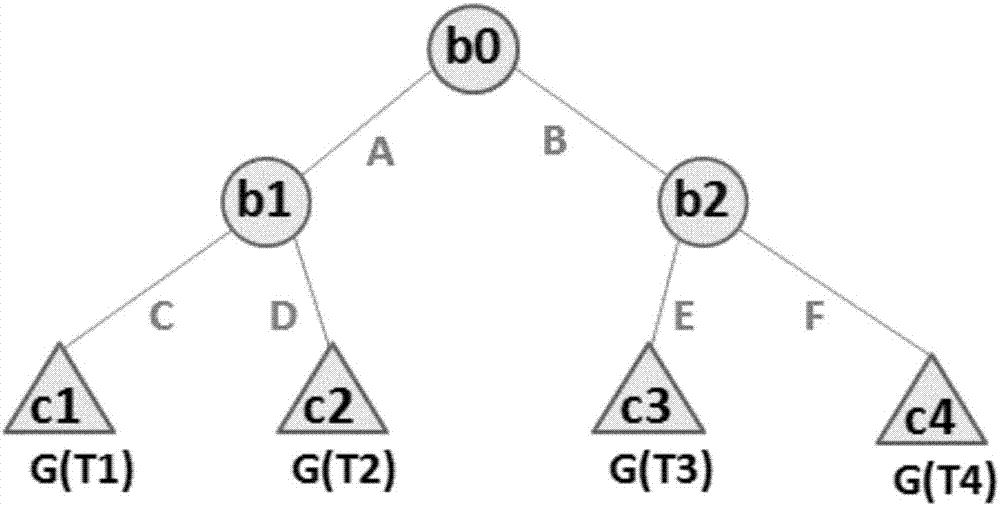
[0057] In Example 1, we use medical care as a scenario to simulate. In this scenario, the hospital is the model provider and the patient is the model user. The hypothetical model is as follows: Figure 4 shown.
[0058] First, the hospital converts its own 4-layer decision tree model into a polynomial and encrypts it. The polynomial calculation result is 1-8 corresponding to c1-c8, and the polynomial before encryption is
[0059] b0*b2*b6*8+b0*b2*(1-b6)*7+b0*(1-b2)*b5*6+b0*(1-b2)*(1-b5)*5+(1 -b0)*b1*b4*4+(1-b0)*b1*b4*3+(1-b0)*(1-b1)*b3*2+(1-b0)*(1-b1)* (1-b3)*1
[0060] After polynomial encryption is
[0061] b0*b2*b6*D522323233434223, b0*b2*(1-b6)*23343923822291EF,
[0062] b0*(1-b2)*b5*223DFD838D932BCB, b0*(1-b2)*(1-b5)*3343422323343923,
[0063] (1-b0)*b1*b4*838D9333434223D, (1-b0)*b1*b4*34342DFD83933343,
[0064] (1-b0)*(1-b1)*b3*32323FD838DD9333, (1-b0)*(1-b1)*(1-b3)*DFD832BCB3232323.
[0065] Then, the patient encodes his physiological data into a binary sequence ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com